1. Introduction
The notion of unconditional secrecy was introduced by Claude Shannon in [
1] to describe an encryption system that is resistant to any passive attack on messages based on ciphertext. However, he showed, in the same paper, that the necessary condition for unconditional secrecy is that the secret key’s length must be at least as long as the message, which is impractical for most applications. To address this, various approaches have been developed to create secure ciphers with shorter keys. Shannon himself suggested the so-called ideal and strongly ideal cipher systems, where an adversary is left with many equally probable decryption options, rather than a unique solution.
In this paper, we address two main questions.
Is it possible to develop a general procedure for constructing ideal cipher systems with a predetermined minimum value of key equivocation, independent of the telecommunication environment or the probabilistic structure of the messages, and without additional infrastructure for generating and distributing secret keys?
Is it possible to apply this solution to any existing symmetric stream ciphering system without modifying it or knowing the key stream generation algorithm, except for the length of the applied secret key?
If feasible, such a system would possess the following properties:
Ideal secrecy—a guaranteed minimum value of key equivocation, regardless of the length of the ciphertext used by the adversary;
Autonomy—the autonomous ability to maintain a given minimum value of key equivocation by continuously refreshing secret keys without additional infrastructure for key generation and distribution;
Robustness—it retains the guaranteed properties regardless of the probabilistic structure of the messages.
We refer to this system as the ISAR (Ideally Secret Autonomous Robust) ciphering system. This paper presents a class of ISAR systems based on wiretap polar codes.
1.1. Related Works
Since key equivocation depends directly on the entropy of messages, the first group of works on ideal ciphering systems focuses on preprocessing messages before encryption to reduce redundancies (or, equivalently, to increase entropy). In this way, the minimum key equivocation available to a system attacker could be controlled. Compression and randomization techniques are standard for this approach and have a long tradition in cryptography [
1,
2,
3,
4,
5]. Unlike other works [
1,
2,
3,
4], the study in [
5] directly addressed the problem of constructing an ideal cipher system, not in terms of key equivocation, but rather message equivocation. In the first step, messages are transformed using Elias’s procedure for constructing unbiased random sequences into two subsets. The first, larger subset consists of independent and equiprobable symbols. The secret key is used in the form of a Vernam cipher to encrypt the second, smaller subset. The author demonstrated that, in this way, the message equivocation cannot fall below the threshold determined by the ratio of the cardinality of the second subset to the message length. It is important to note that this threshold depends on the probabilistic properties of the messages, as well as their length. Therefore, it is difficult to envision an operational procedure for synthesizing a symmetric cipher system with a given minimum value of key equivocation without prior knowledge of these values.
The homophonic coding technique, which transforms a sequence of message symbols into a uniquely decodable sequence where all symbols have the same frequency, also belongs to this approach [
2,
6,
7,
8]. The effectiveness of this approach depends on knowledge of the probabilistic properties of the message source being encrypted and reliable estimates of its statistical properties [
3].
Another approach, not much different from the first, is entropic security [
4,
9,
10,
11]. The main difference lies in the security metrics used as a criterion. The goal of this metric is that any function of the original message is unattainable by passive adversaries. In the limiting case, when the so-called leakage parameter is equal to zero, this criterion aligns with Shannon’s definition of a perfect ciphering system. However, all the obtained results for the length of the secret key then become practically unusable or give lengths equal to the length of the messages, reducing these procedures to the Vernam cipher.
The honey cipher, introduced in [
12], is similar to the concept of ideal cipher. The main goal of this approach is that an adversary is left with many highly probable hypotheses about the secret keys or messages. In [
13], the authors combined the ideas of honey ciphers and entropic security to create practically implementable short-key ciphering systems. The dependence of the efficiency of these systems on the knowledge of the probabilistic properties of the source being encrypted is even more critical than in previous approaches. This is a consequence of the very idea of the system that, in the process of brute force attacks, hypothetical messages are generated that are difficult to distinguish from the true ones. However, the future development of these systems will likely enhance an understanding of the relationship between the probabilistic properties of the source and the minimum length of secret keys that is sufficient to prevent brute force attacks by an unbounded adversary, which brings us back to Shannon’s original ideas about the meaning of non-zero equivocation values of secret keys.
The final group of methods, relevant to the construction of ideally secret systems, comes from the broad research domain of combining the methods of error correcting codes, especially wiretap codes and cryptography [
6,
14,
15,
16,
17,
18,
19]. In [
6], a system based on wiretap codes was proposed, which proved to improve the performance of an arbitrary stream cyphering system in the regime of short messages, but whose key equivocation drops to zero for sufficiently long messages. In one paper [
20], the authors integrated wiretap polar coding in encryption schemes based on learning with the problem of errors and showed that with appropriate refreshing of the secret key procedures, they achieved non-zero equivocation of the keys. In another paper [
21], the connection between ideal secrecy and the wiretap coding approach was clarified. The same authors, in [
22], proposed an encryption system over the MIMO wiretap channel, which, for an infinite lattice input alphabet, guarantees perfect security, while for finite constellations, it guarantees ideal secrecy with high probability. In [
23], the authors proposed a polar coding scheme which achieves maximal secrecy capacity for a secret key of an arbitrary non-zero rate, shared between the transmitter and legitimate receiver. In [
24], an encrypted secure polar coding scheme for general two-way wiretap channels is presented. To achieve strong security and reliability criteria, without any key pre-sharing, it is necessary to apply a complex cooperative jamming strategy.
On the basis of the presented analysis of the relevant published results, we can conclude the following.
According to this analysis, which includes all four approaches, we conclude that there is no example of an ISAR system in the available literature. Namely, all techniques of compression, randomization, and homophonic encoding of message sources, as well as honey ciphering techniques, do not meet our first specified requirement. Furthermore, techniques based on wiretap coding fail to satisfy the same requirement regarding independence from the means of telecommunication used for transmission of the ciphertext.
The paper is organized into the following sections.
Section 2 provides a basic conceptual and theoretical basis for understanding ISAR systems, particularly in the domain of wiretap channels, polar coding, privacy amplification techniques, and Shannon’s notion of ideal and strongly ideal systems.
Section 3 describes the system’s architecture and the security properties of the ISAR ciphering system.
Section 4 provides a security analysis of the ISAR ciphering system, including its resistance to passive attacks both on secret keys and messages.
Section 5 summarizes the practical aspects of the implementation and application of the ISAR system in the contemporary information and communication infrastructure.
Section 6 concludes the paper with a summary of the findings and suggestions for future research directions.
1.2. Notation
We define the integer interval as the integer set between and . We denote as random variables taking values in the alphabets and their realization is denoted as respectively. Also, we denote a -size vector and denote . Further, for any index set , we define denotes entropy, and denotes mutual information.
Table 1 presents the significant notation, along with the respective meanings.
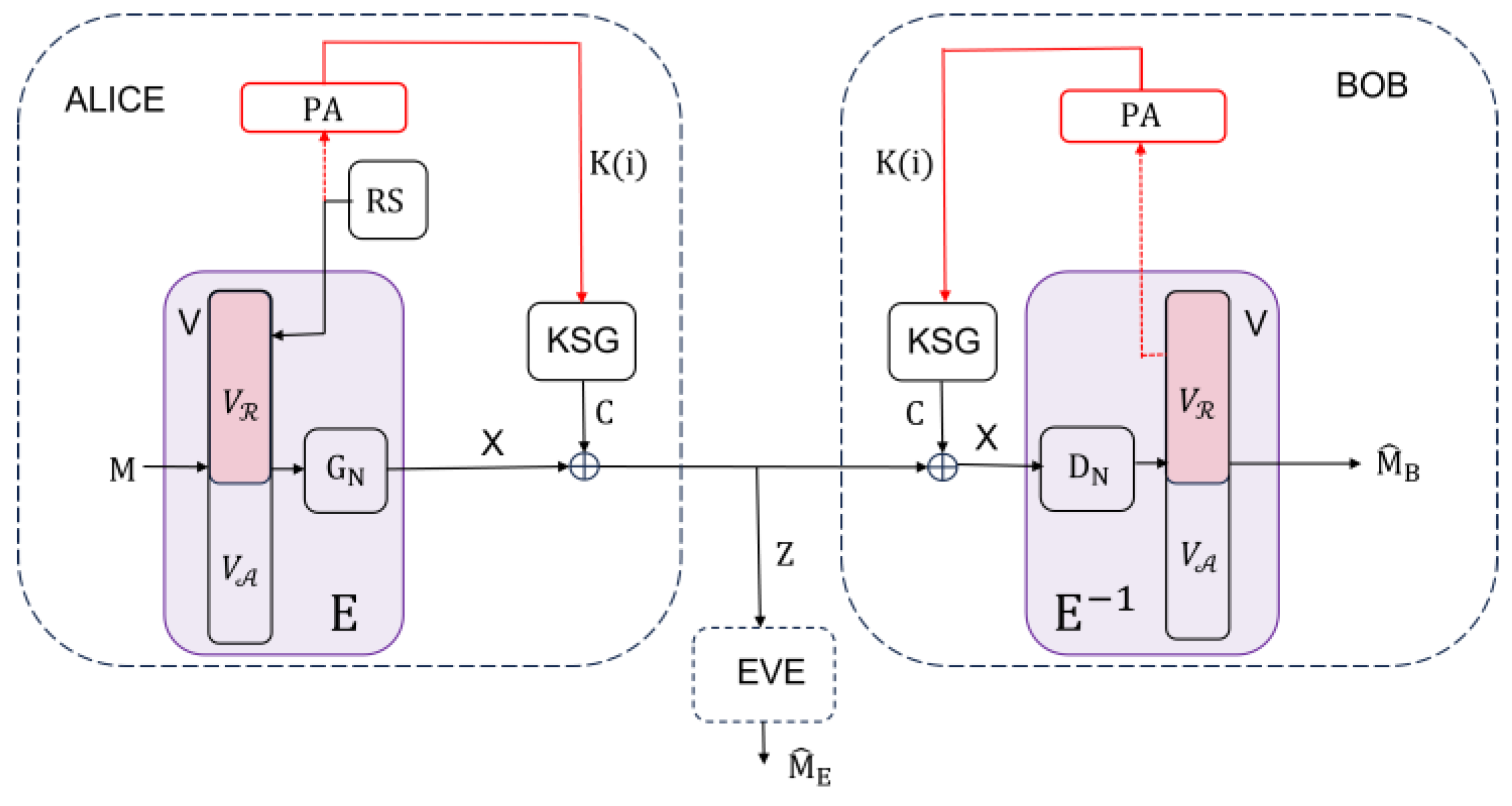
3. System Architecture and Security Properties of the ISAR Cyphering System
In this section, it will be shown that the ISAR cyphering system is equivalent to a wiretap model, whose main channel is error-free, while the wiretap channel is equivalent to an embedded symmetric stream cyphering system. In Theorem 1, it is shown how wiretap coding should be constructed in order to achieve strong secrecy and reliability. Theorem 3 gives the capacity of the wiretap channel, which turns out to decrease linearly with the length of the secret key. Theorem 4 gives the equivocation of secret key, while Theorem 5 gives the secrecy capacity of the proposed ISAR as a function of the polar code length and security margins for equivocation and privacy amplification. Then it is shown that for an arbitrary cipher system to be ideal with the same lower bound of key equivocation as the ISAR system, its secret key must be times greater than that of ISAR, where is proportional to message length. Thus, the superiority of the ISAR system increases with the length of the messages. The section concludes with a demonstration of how any symmetric stream ciphering system can be transformed into an ISAR.
Let the protected communication between the legitimate parties Alice and Bob take place in the successive exchange of messages
, which were previously divided into a series of blocks of length
. At their disposal is a symmetric stream cyphering system based on a key stream generator KSG(
) with a short secret key
that produces the key stream
(see
Figure 1). As is known [
1], such systems cannot provide strong security, and practical secrecy is measured by the amount of computer resources spent by the adversary (Eve) in arriving either at the message (partial system cracking) or the secret key (total system cracking). Block
denotes a polar coder, which performs a 1-1 transformation of message
into an
-dimensional codeword vector
, while the block
performs an inverse transformation of vector
into message
. Alice and Bob have local sources of randomness (denoted by RS on Alice’s side), as well as privacy amplification (PA) blocks, which, based on the input random string obtained in block
, generate a shorter random string that serves as a new secret key
for encrypting the vector
in block
. We will assume that the system uses a cryptographic hash function
from the class of universal hash functions, as well as that the seed
was previously exchanged between Alice and Bob. In the initial block,
, i.e., the initial secret key of the given KSG(
).
Remark 3. Additionally, we assume that the cipher system based on KSG() is semi-injective with respect to , i.e., that the knowledge of ciphers and messages uniquely determines , i.e., holds.
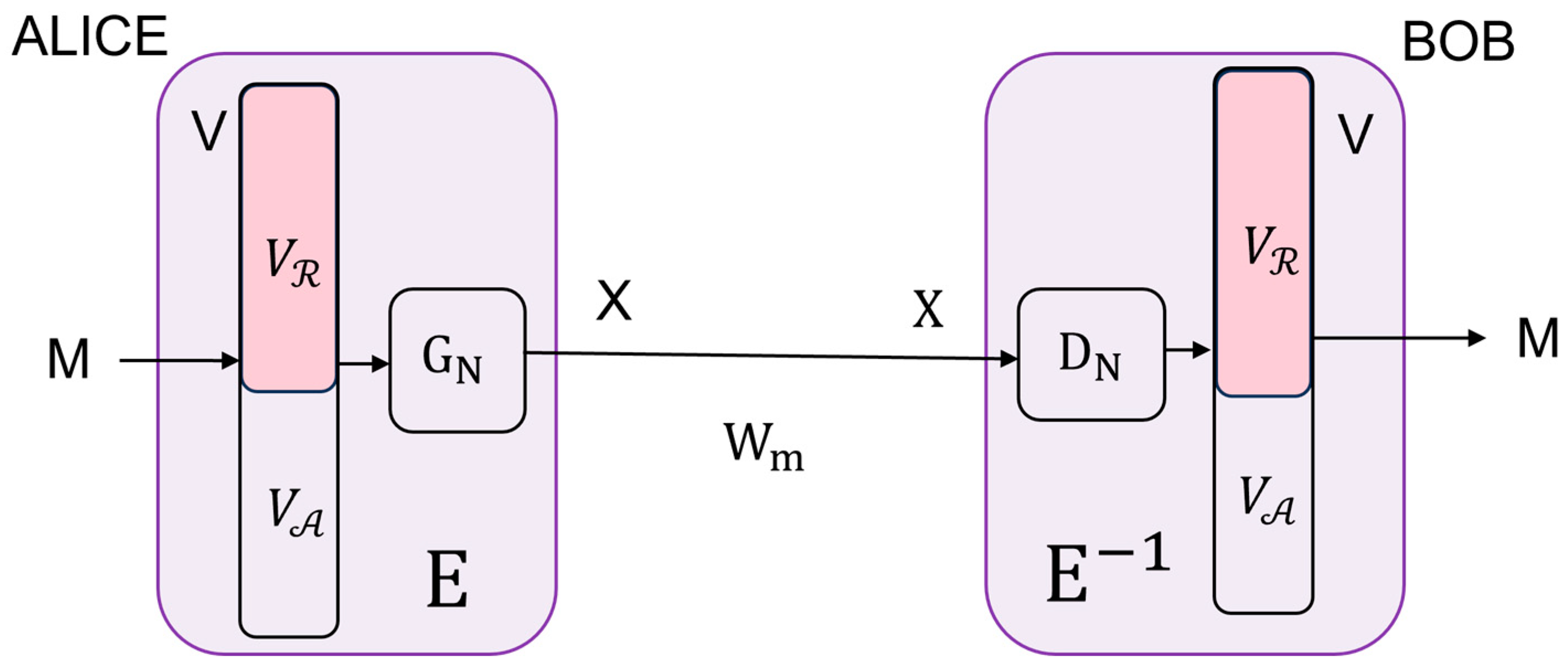
A system conceived of in this way can also be viewed as a kind of wiretap model. The legitimate users Alice and Bob are communicating over an equivalent noiseless main channel
, where
is the identity matrix (see
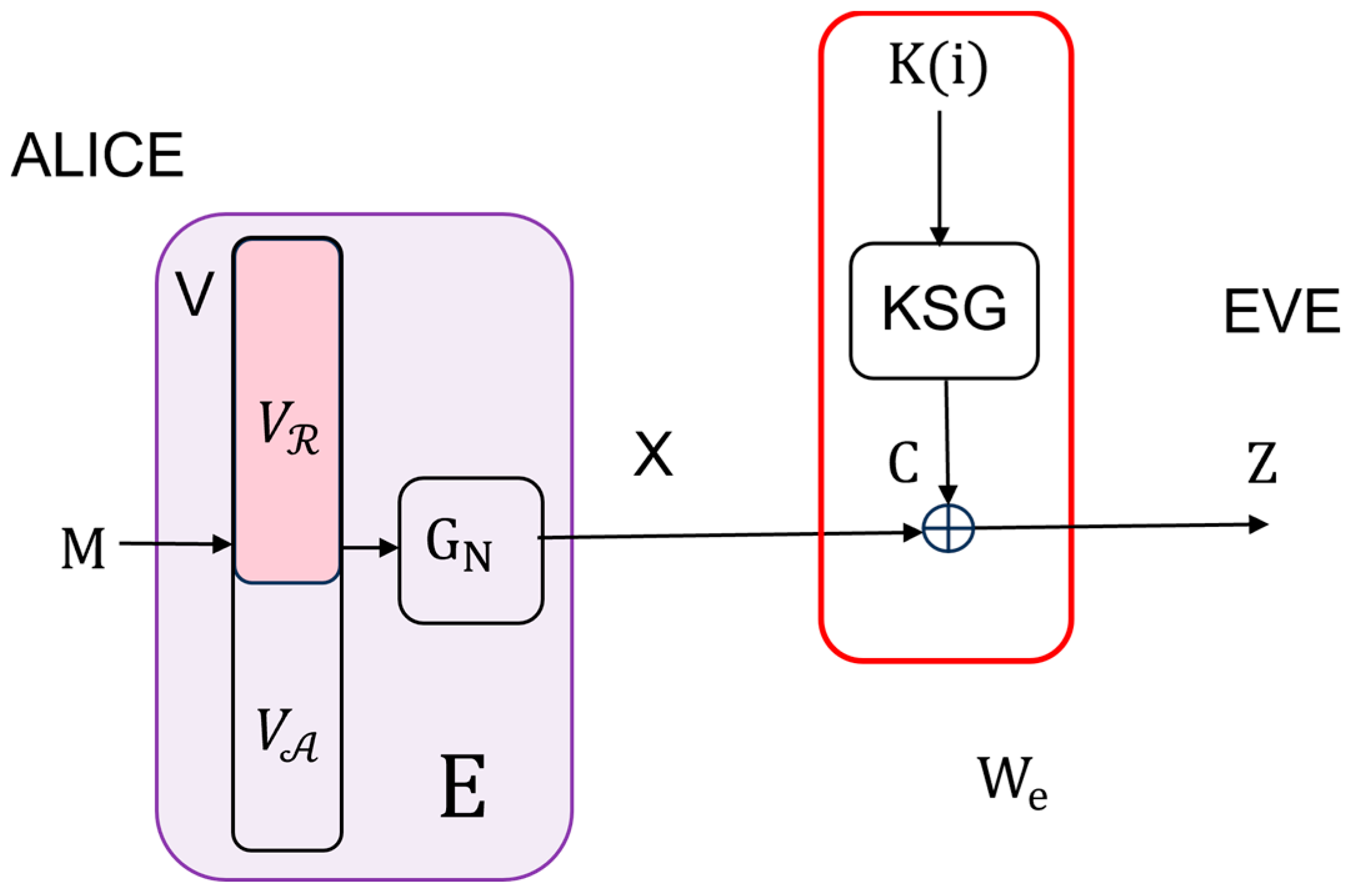
Figure 2). An eavesdropper, Eve, is wiretapping over an equivalent wiretap channel
, where
is an
matrix, with
being the probability of receiving
, given that
was sent (see
Figure 3). In order to be able to apply the results presented in
Section 2, we have to prove that the equivalent wiretap channel is a BSC.
Lemma 1. The equivalent wiretap channel is a BSC.
Proof. According to the proposed scheme (
Figure 1),
Since
is independent of
, (25) is equivalent to BSC (
where the crossover probability is given by
. □
We can now formulate the main result of this part of the work.
Theorem 1. Let be an arbitrary security function that satisfies Condition (17). Let the index sets and be given by and , while is a random vector, selected by Alice uniformly at random from {0, 1}. If, in the ISAR system, the input vector is structured as followsthen it satisfies both the reliability and strong security criteria precisely. Proof. Bearing in mind that the equivalent main channel for the ISAR system is noiseless, the wiretap coding scheme for strong secrecy is determined by the sets of polarized channel indices found by (3)–(10), which now have the following values
According to (35), the problematic set of indices
is an empty set; therefore, it is not necessary to apply the chaining scheme. By structuring the input vector
according to (26), where the sets of indices
and
are given by (32) and (33), respectively, we conclude that the proposed polar coding scheme is merely an instantiation of the general polar wiretap coding scheme from
Section 2.2, which, under the assumptions of Theorem 1, ensures both reliability and strong secrecy. Since the main channel is noiseless, decoding on Bob’s side is not performed using the SC decoder, but rather by a simple inverse operation with respect to the encoding, i.e.,
given that Arikan’s generator matrix
is its own inverse over the Galois field
. Therefore, the reliability condition expressed by (27) is actually deterministically satisfied. This completes the proof. □
Theorem 2. For any security function and the constants that satisfies Condition (17), , , and , the rate of the coding scheme of the proposed system from Figure 1 approaches the secrecy capacity, namely Proof. The proof follows directly from Theorem 1 of [
17], and the fact that the capacity of main channel is
. □
Remark 4. Eve’s optimal strategy is to attempt to decode the wiretapped using the SC decoder after receiving it [28]. The average block error probability on Eve’s side can be lower-bounded, applying Lemma 2.9 of [31] by Koradawhere is the information set. Considering that Eve does not know the frozen bits on her side, the information set includes all indices, i.e., and the polar code applied is of rate 1; see the similar argumentation in [32]. The maximum value of is very close to 1, bearing in mind that includes bad channels as well. Therefore, according to (39), it follows thatwhere is small. From this, we conclude that Eve’s optimal decoding strategy of using the SC decoder results in the maximum decoding error, preventing her from obtaining both the message and the purely random sequence . It is evident that the key properties of the proposed system depend on the capacity of the wiretap channel . The following theorem determines the value of this quantity, depending on the length of the polar code and the length of the secret key .
Theorem 3. The capacity of Eve’s channel in the proposed system in Figure 1 is given bywhere is the length of the secret key of the given symmetric stream cyphering system based on KSG(), while is the length of the polar code. Proof. For a discrete memoryless symmetric channel
with the input
and the output
, the channel capacity is defined as
where the maximum is taken over all possible input distributions
[
33]. Furthermore, we have
The input to the wiretap channel
is also the input (messages) to the symmetric stream ciphering system based on KSG(
). Message equivocation is equal to key equivocation
for every symmetric ciphering system, semi-injective with respect to
(see Theorem 1 in [
34]). On the other hand, it well known that (see, for example, [
25])
which, by substituting into (44) and then into (43), gives
One of the primary goals in designing any cipher system is for the ciphertext to appear to be totally random for as long as possible, i.e.,
This holds for larger values of
. The assumption in (47) is referred to by Massey in [
35] as the “total randomness” assumption, and it is shown to be valid as long as
where
is the unicity distance of a given cipher system [
1]. Considering (47) and the fact that
since the secret keys are chosen as purely random sequences, from (46), we obtain
or, normalized per bit,
which had to be proven. □
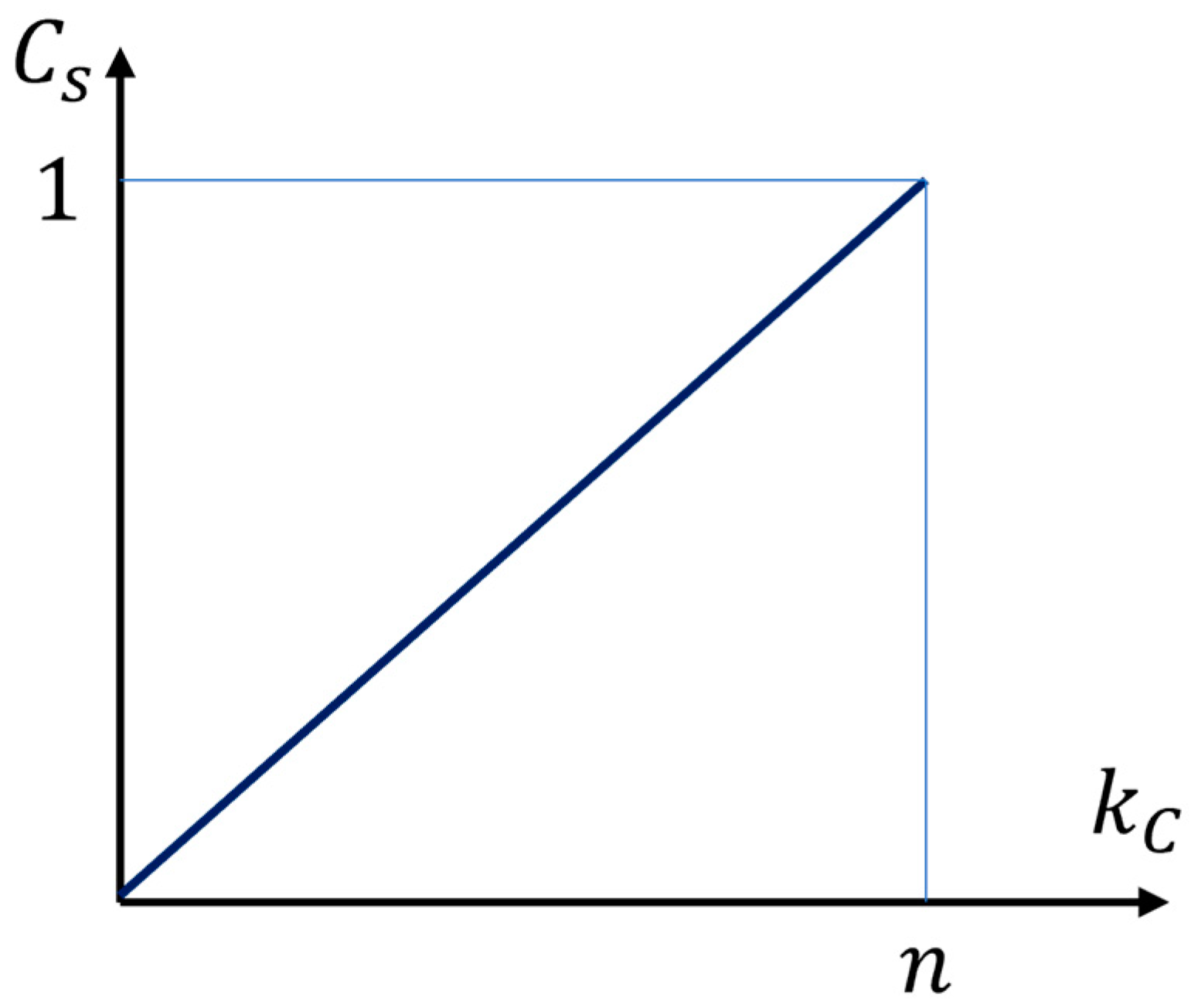
Remark 5. Given Theorems 2 and 3, the secrecy capacity of the proposed system isFrom this, the fundamental impact of the secret key length is clearly evident (see Figure 4). For , the system does not provide any security, while for , . This means that in the latter case, we can choose all n bits of polar code for secure transmission of n message bits. In order to examine the properties of ideally secret autonomous cipher systems, we need the following theorem, which provides a lower bound on the equivocation of the system’s secret keys.
Theorem 4. The equivocation of the secret keys of KSG(), when the ciphertext is known, satisfies the inequalitywhere n is the length of the polar code, is the entropy of the secret key, and is a purely random vector of dimension . Proof. Generally, according to [
25], for any cipher system with a secret key
, the input
, and the ciphertext (output)
, it holds that
. On the basis of (11), the output vector
can be written in the form
where
and
are submatrices of the polar code generator matrix
consisting of the corresponding rows in
.
The ranks of the matrices
and
are
and
, respectively, because the generator matrix
has the full rank
. Therefore,
and
can be uniquely represented by a set of basis vectors of dimensions
and
. These base vectors are some of the column vectors of the matrices
and
. We will denote these sets of column indices as
and
. Then there exists a one-to-one correspondence between
and
, and between
and
. Hence
According to the data processing properties of entropy [
35], we conclude that in the PA procedure, there is a limitation,
, from which it follows that the secrecy capacity in the ISAR system must be
Thus, it holds that
given the condition
and the fact that
is a purely random vector with the maximum entropy equal to
Since it is always true that
we finally obtain
which had to be proven. □
To ensure that the system has autonomy in generating secret keys, we need to limit the polar code rate, because some of the polar code bits must be used for generating and distributing secret keys. Additionally, for the system to be ideal and autonomous, a further reduction in secrecy capacity is necessary to maintain the desired minimum level of key equivocation. These facts are summarized in Theorem 5 below.
Theorem 5. The proposed system is ideally secret, autonomous, and robust, with the maximal secrecy capacitywhere is a given minimum value of key equivocation and is the compression rate of the applied class of universal hash functions. The length of the secret key of the given symmetric stream cyphering system is , while is the length of the polar code. Proof. To prove that the proposed system is ideal, it is necessary to show that for given
(23) and (24) hold. Consider the general case where Alice sends a message
of arbitrary length
to Bob. The message
will be divided into blocks of length
The total number of blocks will be
, where
is the length of the polar code, so
The last block, if it is not of length
, can be padded with arbitrary content. According to the proposed coding scheme that provides strong security,
. According to (37), in addition to the transmitted message
, Bob decodes, without error, a purely random vector
, which is of length
, which was written on the indices from the set
given in (32) during the encoding process on Alice’s side. Thus, Alice and Bob, after decoding, possess identical random sequences
in each of the
transmitted blocks of the polar code. Eve’s optimal strategy is to decode her received signal at the output of the wiretap channel using the SC decoder. Eve knows the parameters of the applied polar code, such as the length
and the index sets
and
, but does not know the values of the bits at those positions. This situation is equivalent to the SC decoder operating in the mode of unknown so-called frozen bits. As noted in Remark 4, Eve’s error in optimal decoding is close to the maximum, so it can be said that Eve’s information about the sequence
is close to zero. By applying PA to the common random sequences
, Alice and Bob can further reduce Eve’s residual information about these sequences. In each current block, a secret key of length
is generated for the next block using some chosen PA algorithm
Given that
is the compression rate of the class of universal hash functions applied in the PA process, it follows that
Having in mind that
from (59) and (60), it follows that
For the system to be ideal, it is sufficient to ensure that the right-hand side of (57) equals a predetermined minimum value of key equivocation
in each block, i.e.,
That is, assuming that the ergodicity of the local randomness source, i.e.,
, it follows that
By substituting (61) into (63), it is obtained that
which had to be proven. □
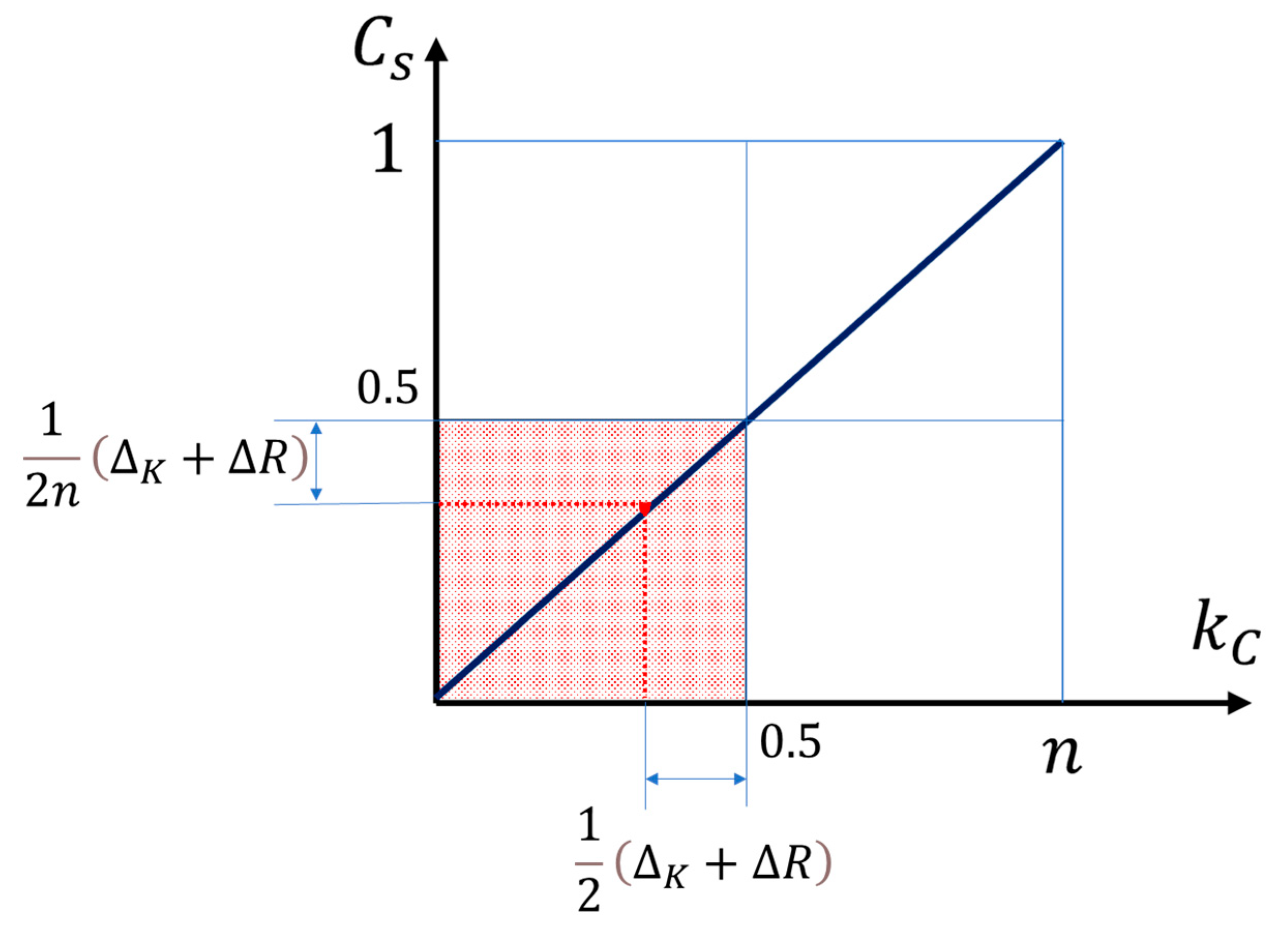
Figure 5 gives a graphical presentation of the interdependence of the quantities
,
,
,
, and
from Theorem 5. If we compare
Figure 4 and
Figure 5, the restrictions imposed by ideality and autonomy on the possible values of secrecy capacity, secret key length, and polar code length can be clearly seen.
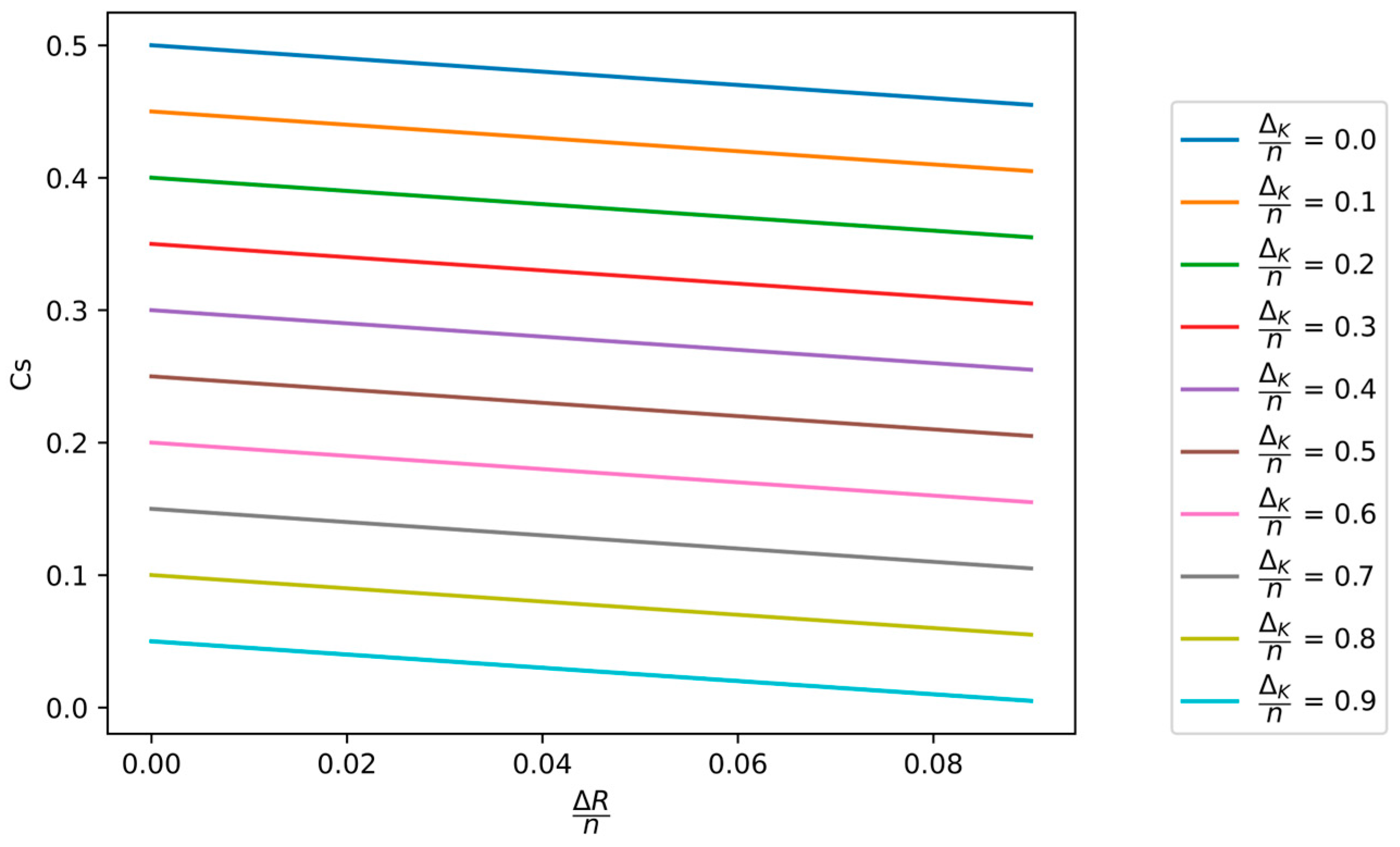
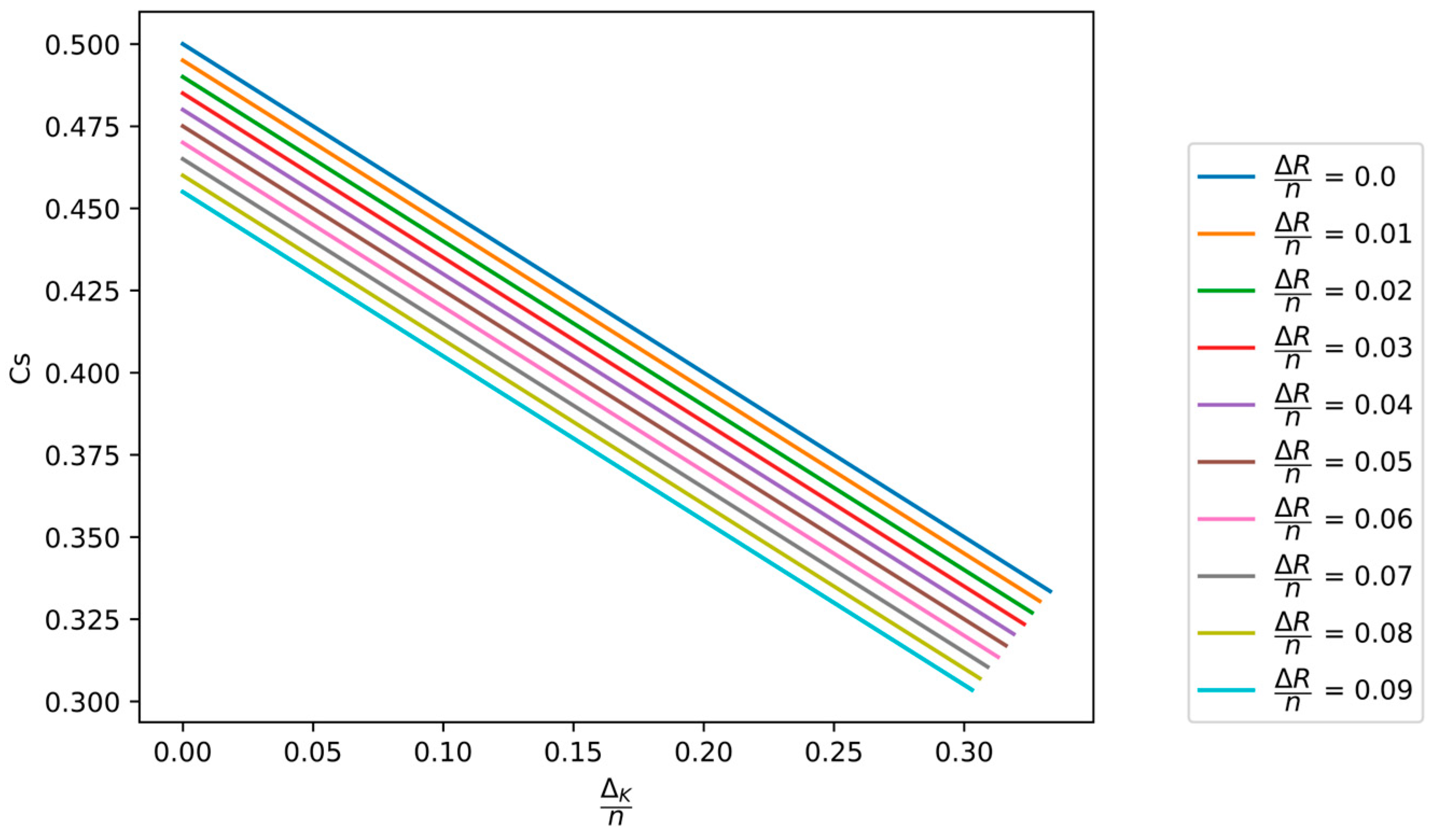
In
Figure 6 and
Figure 7, the dependence of the secrecy capacity
on the normalized minimum value of key equivocation
and the normalized compression rate
of the hash function applied in the PA process is shown.
Note that if the security margins and are fixed constants, then, on the basis of Theorem 5, we conclude that holds, which is the maximum possible value of the secret capacity of the ISAR system.
The presented theory offers an effective methodology for synthesizing this class of systems with predetermined security margins. The algorithms for configuring the ISAR system and for enciphering/deciphering messages of arbitrary length are described below. On the basis of the initial values of parameters
and
, the secrecy capacity
and the length of the secret key
are determined. If these parameters are acceptable, the synthesis of the corresponding wiretap polar code proceeds. Identifying the index sets
and
requires the polarization of the wiretap channel. For practical purposes, it is simpler to replace this channel with an equivalent
channel of the same capacity. Consequently, the crossover probability must satisfy the condition
where
is the binary entropy function, and
is its inverse. The polarization procedure under SC decoding can be performed using various methods, such as Monte Carlo [
28], density evolution (DE) [
36,
37], and DE with Gaussian approximation (GA) [
38], among others. In the ISAR system, where the wiretap channel is designed by the system developer, all essential parameters for the wiretap channel are much more accessible and accurately estimated compared with a scenario involving real wiretap channels. For instance, in determining the Bhattacharyya parameters
using the Monte Carlo method for polarization, generating an ensemble of wiretap channel output samples is manageable. This process is facilitated by the precise knowledge of the crossover probability (65), allowing for an accurate assessment of the results.
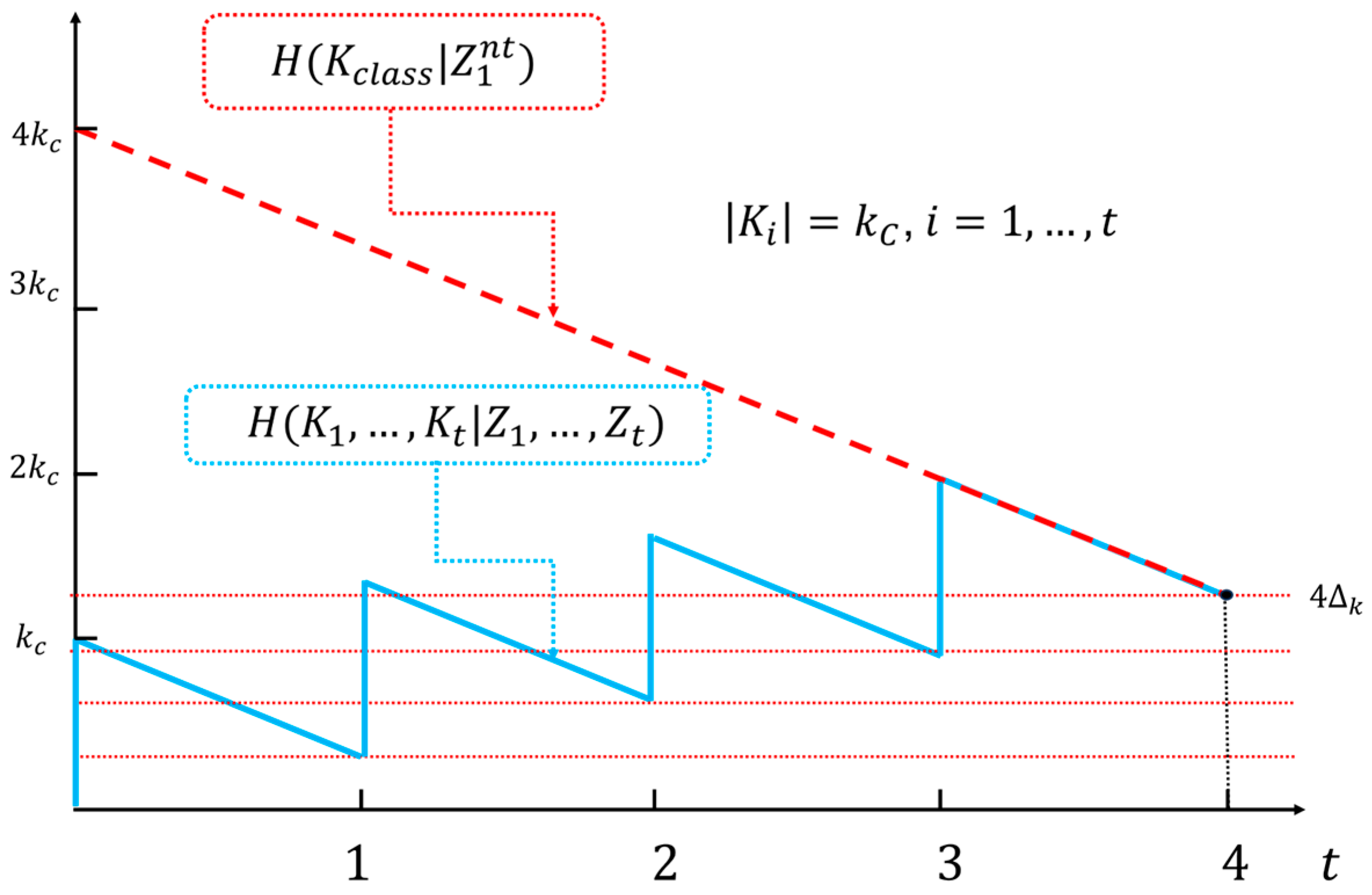
Remark 6. Let us compare the proposed ISAR system with a classic ideal cipher system that has the same minimal key equivocation value for the same length of observed ciphertext. To ensure a fair comparison, we assume that the entropy of the input messages is identical in both systems. After encrypting t blocks of messages, and assuming that the blocks are independent, the ISAR system has a total equivocation of all applied keys equal tosince the formation of each block in the polar code is independent of the previously formed blocks. A classic ideal cipher system with the secret key under the same conditions and for the same length of ciphertext has an equivocation given byEquating the same lower bounds in (67) and (68) yields the condition thatThat isassuming that all secret keys in both systems have maximum entropy. To ensure that a classic encryption system achieves the same lower bound on key equivocation as the ISAR system for the same observed ciphertext length, it would need a secret key t times longer than the key length of the KSG(
) (see
Figure 8). Additionally,
must be pre-distributed to legitimate parties. The length of this key scales linearly with the message length
, specifically with
. In contrast, the proposed ideal autonomous system requires only a fixed-length secret key K, independent of the message length, and requires only an initial exchange of the key values
. Therefore, the benefits of the ISAR system become more significant as the length of the messages increases.
Remark 7. The ISAR system can be obtained by a suitable transformation of any given stream ciphering system based on KSG() with a known secret key length . The procedure includes the following steps.
On the basis of the expression in (58) for the given value of the length of the secret key , we can directly obtain the required length of the polar code, i.e.,
Since the length of the polar code must be a power of 2, it is necessary to correct (71) to the value bearing in mind the limitation Since all elements for the ISAR system’s setup are available at this step, i.e., , further operation of the system takes place according to Algorithms 1–3.
| Algorithm 1 System setup |
Choose . Calculate and based on (58).
Form the corresponding equivalent wiretap channel, , and perform polarization. Determine the set of indices . Determine the set of indices and . Agree on initial secret key , and seed of hash function .
|
| Algorithm 2 Enciphering |
Split message into blocks so that , , with padding of the last block with random bits if necessary.
Creation of ciphertext, .
For
// generate random sequence of length
If then
else
end
KSG // generate stream ciphering sequence of length
// polar coding
// enciphering
end |
| Algorithm 3 Deciphering |
If then
else
end
KSG // generate stream ciphering sequence of length
// deciphering
// deciphered random sequence
// deciphered message
// completly deciphered message
end |
4. Security Analysis of the ISAR Ciphering System
The standard assumptions common in cryptography were used in the analysis of the ISAR system. The Kirchhoff principle dictates that the attacker knows the entire system operation algorithm, except for the initial secret key K of KSG(K). Further, the security integrity of cyphering and deciphering devices is an obvious assumption in cryptography. Therefore, the computation processes on the side of the legitimate sender (the dot-framed square named Alice) are inaccessible to the attacker during the execution of the polar coding and encryption operations. Otherwise, the attacker would have direct access to the messages and/or the key stream . The same applies to the computation processes on the side of the legitimate recipient (the dot-framed square named Bob) during polar code decoding and decryption.
In the following analysis, we focus on the examination of passive attacks on the system. This implies that the attacker has access to the output of the wiretap channel and all information related to the architecture and operation of the system, except for the initial value and the seed of the chosen hash function According to the primary objective of the attack, we can distinguish three types: message attacks, attacks on locally generated random sequences, and attacks on the secret key.
4.1. Attacks on Messages
In this type of attack, Eve attempts to obtain the message in each block, based on the observation of the wiretap channel output . According to Theorem 1, the proposed system satisfies the strong security criterion (28), which means that, asymptotically, with an increase in the codeword length , Eve can only acquire a negligible amount of information about the messages . In the case of codewords of final lengths n, the amount of information leaking to the attacker is not only limited in quantity but is also not localized to specific bit positions in the ciphertext, which further complicates potential cryptanalysis.
4.2. Attacks on Locally Generated Random Sequences
In this type of attack, Eve first tries to obtain one of the random sequences locally generated by Alice based on the observation of the wiretap channel outputs . In the second step, using some obtained value , Alice could potentially generate the correct secret key for the next block . Knowing the secret key for block , Eve could successfully decode all subsequent blocks, thereby obtaining all messages in the sequence . However, this scenario is not feasible. The first step cannot be realized efficiently since, according to Remark 4, the average block error probability on Eve’s side is close to maximal (see (40)). Of course, in this step, Eve can apply a brute force attack, which requires attempts. This means that this number of active hypotheses for will proceed to the next step. The second step is not possible without knowing the seed of the chosen hash function As the success of this attack depends on the success of both steps, this type of attack is practically unfeasible because the overall difficulty of the attack is equal to the product of the difficulties of both steps.
4.3. Attacks on the Secret Key KSG()
A far more powerful cryptanalytic attack than an attack on individual messages is an attack on the secret key
of the KSG. If Eve were to obtain the secret key
in block
where
, she would be able to access message
, the random sequence
, and, consequently, the secret key
for the next block. This would allow her to repeat the same process for each subsequent block, thereby gaining access to all subsequent transmitted messages
, the random sequence
, and the generated secret keys
From the system designer’s perspective, it is crucial to prevent this scenario. The information-theoretic quantity that quantifies the likelihood of such an attack is the equivocation of the secret keys for a given wiretap channel’s output. As the ISAR system is ideally secret, its secret key equivocation, according to (62), never falls below the value
, which is the security parameter in the synthesis process of the ISAR. It is important to mention that, from the cryptanalyst’s point of view,
possible values for keys/messages exist with equal probabilities. Therefore, the system’s designer can render this attack unsuccessful with any chosen margin of security. It is important to note that increasing the margin of security leads to a reduction in the secrecy capacity of ISAR (see Theorem 5 and
Figure 7).
Remark 8. An attack on the secret key of KSG(K), both as an independent entity and as part of an ISAR system, requires additional clarification. It is logical to assume that doubling the length m of the secret key increases the cryptanalyst’s effort by times in a brute force attack if a ciphertext of length greater than the unicity point is available. The outcome of this attack is a unique secret key, given that . In the case of an ISAR system, however, key equivocation never falls below the value , meaning the cryptanalyst is left with equally likely hypotheses, regardless of the ciphertext length. Additionally, according to (71), for any secret key length (including a doubled one), it is possible, by increasing the length of the polar code n, to independently select a security margin .
From this brief analysis, we can conclude that classic cryptographic systems with a finite secret key and the ISAR system must be carefully compared, since the work of the cryptanalyst in the case of the ISAR system does not lead to a unique solution.
Example 1. To understand the order of magnitude of the difficulty of executing this attack, let us consider a typical example of an ISAR with the parameters (expressed in bits) . According to (58), , and the key length is bits. Let us assume that Eve’s optimal strategy for each block of the polar wiretap code reaches the lower bound of equivocation of 100 bits of the key. This means that Eve cannot resolve this uncertainty in any way. Recall that in a brute force attack examining all possible keys, all decrypted messages would be equally likely and valid as potential final solutions.
The example above shows that for the polar code length n of order
, the key length of KSG(
) is of order
. These lengths are not common for commercial stream ciphering systems. However, this does not mean that such systems cannot be relatively easily upgraded to the required key lengths. As an example, we cite a generic model of a pseudo-random generator described in [
39]. If the address and selection sequences are chosen so that they are the outputs of two multiple linear shift registers, then the lengths of the equivalent secret key of this pseudo-random generator can easily be set in ranges of order
.
The cryptanalysis presented here may cause some doubt regarding the level of security of the ISAR system. Specifically, wiretap polar encoding enables perfect secrecy of the messages, while the ISAR, on the other hand, guarantees only ideal secrecy. The explanation is simple. The security of the entire system is equal to the security of the weakest link in the chain. In this case, it is KSG(K), which can only provide ideal security.
To confirm this, let us show that the ISAR cannot be perfectly secret. For perfect secrecy, it is necessary for the following to be valid
That is, in the case of symmetrical semi-injective systems
According to (57), it follows that
or
The last equality holds if and only if
is a binary symmetric source (BSS) with maximum entropy. Taking (11) into account, as well as the fact that Arikan’s generator matrix
is nonsingular, it follows that
In other words,
must be a BSS, and, therefore,
must also be a BSS. Considering that, according to (14),
, we conclude that the message must be a BSS. This contradicts the robustness of the ISAR, which requires that its properties must be independent of the probability distribution of the messages. In addition to this difficulty, perfect secrecy of the ISAR would require that the entropy rate of the secret keys must be greater than or equal to the entropy rate of the input sequence
in KSG(
, or
According to (50) in Remark 5, for
, which corresponds to the fact that
must be a BSS, it follows that, in this case,
would have to hold. This contradicts the property of the ISAR stated in Theorem 5, namely that
.
6. Conclusions
In this paper, we introduced a class of symmetric ciphering systems termed ISAR (Ideally Secret Autonomous Robust) systems. These systems are designed to provide ideal secrecy, autonomy in key generation and distribution, and robustness to the probabilistic structure of messages. These systems address the longstanding challenge in cryptography of balancing security with practicality, particularly by eliminating the need for lengthy secret keys and additional key distribution infrastructure. By ensuring a predetermined minimum value of key equivocation and continuous key refreshing, ISAR systems provide robust security against passive attacks on both keys and messages.
Our work demonstrates that ISAR systems can be applied to any existing symmetric stream ciphering system without requiring changes to the original encryption algorithm, thus offering a versatile and efficient solution for enhancing the security of current cryptographic practices. This transformation greatly supports privacy, a critical requirement for modern security systems. Overall, the ISAR system represents an advancement in cryptographic security, offering an efficient methodology for creating ciphering systems with predetermined security margins.
The main limitation of the ISAR system is its dependence on the encoding and decoding of the chosen polar code. Particularly, the constraint that the block length must be of the form may cause some practical problems. Although recent advancements have proposed efficient modifications for polar codes of arbitrary block lengths, their application within the ISAR system requires more careful analysis and assessment of potential security breaches. Another potential limitation of the ISAR system is its current applicability to symmetric stream ciphering systems only.
Future research directions include exploring optimizations in the ISAR architecture, extending its applicability to a broader range of cryptographic scenarios, and investigating additional techniques for enhancing its resistance to more sophisticated attack vectors. Also, the potential extension to block cipher systems is of great practical and theoretical significance. The continued development of ISAR systems holds the promise of ensuring stronger privacy and security measures in an increasingly digital world.