Abstract
This paper introduces a class of symmetric ciphering systems with a finite secret key, which provides ideal secrecy, autonomy in key generation and distribution, and robustness against the probabilistic structure of messages (the Ideally Secret Autonomous Robust (ISAR) system). The ISAR system is based on wiretap polar codes constructed over an artificial wiretap channel with a maximum secrecy capacity of 0.5. The system autonomously maintains a minimum level of key equivocation by continuously refreshing secret keys without additional key generation and distribution infrastructure. Moreover, it can transform any stream ciphering system with a finite secret key of known length into an ISAR system without knowing and/or changing its algorithm. Therefore, this class of system strongly supports privacy, a critical requirement for contemporary security systems. The ISAR system’s reliance on wiretap polar coding for strong secrecy ensures resistance to passive known plaintext attacks. Furthermore, resistance to passive attacks on generated refreshing keys follows directly from ideal secrecy and autonomy. The results presented offer an efficient methodology for synthesizing this class of systems with predetermined security margins and a complexity of the order of , where is the block length of the applied polar code.
Keywords:
cryptography; ideal secrecy; polar coding; wiretap channel; key equivocation; privacy amplification MSC:
94A60
1. Introduction
The notion of unconditional secrecy was introduced by Claude Shannon in [1] to describe an encryption system that is resistant to any passive attack on messages based on ciphertext. However, he showed, in the same paper, that the necessary condition for unconditional secrecy is that the secret key’s length must be at least as long as the message, which is impractical for most applications. To address this, various approaches have been developed to create secure ciphers with shorter keys. Shannon himself suggested the so-called ideal and strongly ideal cipher systems, where an adversary is left with many equally probable decryption options, rather than a unique solution.
In this paper, we address two main questions.
- Is it possible to develop a general procedure for constructing ideal cipher systems with a predetermined minimum value of key equivocation, independent of the telecommunication environment or the probabilistic structure of the messages, and without additional infrastructure for generating and distributing secret keys?
- Is it possible to apply this solution to any existing symmetric stream ciphering system without modifying it or knowing the key stream generation algorithm, except for the length of the applied secret key?
If feasible, such a system would possess the following properties:
- Ideal secrecy—a guaranteed minimum value of key equivocation, regardless of the length of the ciphertext used by the adversary;
- Autonomy—the autonomous ability to maintain a given minimum value of key equivocation by continuously refreshing secret keys without additional infrastructure for key generation and distribution;
- Robustness—it retains the guaranteed properties regardless of the probabilistic structure of the messages.
We refer to this system as the ISAR (Ideally Secret Autonomous Robust) ciphering system. This paper presents a class of ISAR systems based on wiretap polar codes.
1.1. Related Works
Since key equivocation depends directly on the entropy of messages, the first group of works on ideal ciphering systems focuses on preprocessing messages before encryption to reduce redundancies (or, equivalently, to increase entropy). In this way, the minimum key equivocation available to a system attacker could be controlled. Compression and randomization techniques are standard for this approach and have a long tradition in cryptography [1,2,3,4,5]. Unlike other works [1,2,3,4], the study in [5] directly addressed the problem of constructing an ideal cipher system, not in terms of key equivocation, but rather message equivocation. In the first step, messages are transformed using Elias’s procedure for constructing unbiased random sequences into two subsets. The first, larger subset consists of independent and equiprobable symbols. The secret key is used in the form of a Vernam cipher to encrypt the second, smaller subset. The author demonstrated that, in this way, the message equivocation cannot fall below the threshold determined by the ratio of the cardinality of the second subset to the message length. It is important to note that this threshold depends on the probabilistic properties of the messages, as well as their length. Therefore, it is difficult to envision an operational procedure for synthesizing a symmetric cipher system with a given minimum value of key equivocation without prior knowledge of these values.
The homophonic coding technique, which transforms a sequence of message symbols into a uniquely decodable sequence where all symbols have the same frequency, also belongs to this approach [2,6,7,8]. The effectiveness of this approach depends on knowledge of the probabilistic properties of the message source being encrypted and reliable estimates of its statistical properties [3].
Another approach, not much different from the first, is entropic security [4,9,10,11]. The main difference lies in the security metrics used as a criterion. The goal of this metric is that any function of the original message is unattainable by passive adversaries. In the limiting case, when the so-called leakage parameter is equal to zero, this criterion aligns with Shannon’s definition of a perfect ciphering system. However, all the obtained results for the length of the secret key then become practically unusable or give lengths equal to the length of the messages, reducing these procedures to the Vernam cipher.
The honey cipher, introduced in [12], is similar to the concept of ideal cipher. The main goal of this approach is that an adversary is left with many highly probable hypotheses about the secret keys or messages. In [13], the authors combined the ideas of honey ciphers and entropic security to create practically implementable short-key ciphering systems. The dependence of the efficiency of these systems on the knowledge of the probabilistic properties of the source being encrypted is even more critical than in previous approaches. This is a consequence of the very idea of the system that, in the process of brute force attacks, hypothetical messages are generated that are difficult to distinguish from the true ones. However, the future development of these systems will likely enhance an understanding of the relationship between the probabilistic properties of the source and the minimum length of secret keys that is sufficient to prevent brute force attacks by an unbounded adversary, which brings us back to Shannon’s original ideas about the meaning of non-zero equivocation values of secret keys.
The final group of methods, relevant to the construction of ideally secret systems, comes from the broad research domain of combining the methods of error correcting codes, especially wiretap codes and cryptography [6,14,15,16,17,18,19]. In [6], a system based on wiretap codes was proposed, which proved to improve the performance of an arbitrary stream cyphering system in the regime of short messages, but whose key equivocation drops to zero for sufficiently long messages. In one paper [20], the authors integrated wiretap polar coding in encryption schemes based on learning with the problem of errors and showed that with appropriate refreshing of the secret key procedures, they achieved non-zero equivocation of the keys. In another paper [21], the connection between ideal secrecy and the wiretap coding approach was clarified. The same authors, in [22], proposed an encryption system over the MIMO wiretap channel, which, for an infinite lattice input alphabet, guarantees perfect security, while for finite constellations, it guarantees ideal secrecy with high probability. In [23], the authors proposed a polar coding scheme which achieves maximal secrecy capacity for a secret key of an arbitrary non-zero rate, shared between the transmitter and legitimate receiver. In [24], an encrypted secure polar coding scheme for general two-way wiretap channels is presented. To achieve strong security and reliability criteria, without any key pre-sharing, it is necessary to apply a complex cooperative jamming strategy.
On the basis of the presented analysis of the relevant published results, we can conclude the following.
- Wiretap coding provides a promising environment for implementing cryptographic systems with increased security.
- Works in which ideal secrecy has been proven are always related to a specific ciphering system, such as in [20], or are limited to a particular physical model of the wiretap channel, as in [22,24].
According to this analysis, which includes all four approaches, we conclude that there is no example of an ISAR system in the available literature. Namely, all techniques of compression, randomization, and homophonic encoding of message sources, as well as honey ciphering techniques, do not meet our first specified requirement. Furthermore, techniques based on wiretap coding fail to satisfy the same requirement regarding independence from the means of telecommunication used for transmission of the ciphertext.
The paper is organized into the following sections. Section 2 provides a basic conceptual and theoretical basis for understanding ISAR systems, particularly in the domain of wiretap channels, polar coding, privacy amplification techniques, and Shannon’s notion of ideal and strongly ideal systems. Section 3 describes the system’s architecture and the security properties of the ISAR ciphering system. Section 4 provides a security analysis of the ISAR ciphering system, including its resistance to passive attacks both on secret keys and messages. Section 5 summarizes the practical aspects of the implementation and application of the ISAR system in the contemporary information and communication infrastructure. Section 6 concludes the paper with a summary of the findings and suggestions for future research directions.
1.2. Notation
We define the integer interval as the integer set between and . We denote as random variables taking values in the alphabets and their realization is denoted as respectively. Also, we denote a -size vector and denote . Further, for any index set , we define denotes entropy, and denotes mutual information.
Table 1 presents the significant notation, along with the respective meanings.

Table 1.
Notation.
2. Preliminaries
In order make it easier to understand the operation of the proposed system, in this section, we will present the basic concepts from the domain of wiretap channel models, polar coding, and privacy amplification, since these three elements are its basic building blocks. In the final part of the section, the definition of an ideal autonomous ciphering system is given as a kind of generalization of Shannon’s notions of ideal and strongly ideal ciphering systems [25].
2.1. Wiretap Channel Model
The wiretap model consists of two channels and , which are the main and wiretap channels, respectively, that were first introduced by Wyner [14]. With the help of random bits, the encoder maps the -bit message into a sequence of -bit channel symbols. This sequence is sent on the main and wiretap channels, giving the corresponding channel outputs and . On the legitimate user’s side, the decoder maps into an estimate of the original message. The basic purpose of wiretap coding is the design of encoders and decoders that provide the legitimate users (Alice and Bob) with reliability and security at the same time when the message length tends to infinity. The largest transmission rate at which both the reliability and secrecy conditions are simultaneously satisfied is commonly referred to as the secrecy capacity . In the case when the main and wiretap channels are binary symmetric channels (BSC) and the wiretap channel is degraded with respect to the main channel, was given by [26] as
where the random variable at the input to the channel is uniform over , while ( denote the capacities of the main and wiretap channels, respectively.
2.2. Wiretap Polar Coding
Polar codes, introduced by Erdal Arikan [27,28], are a class of error-correcting codes that achieve the capacity of binary-input symmetric memoryless (BSM) discrete channels. The key idea behind polar coding is to transform a set of communication channels into a set of polarized channels, where a subset of channels becomes nearly perfect (noiseless) and the others become completely noisy. If, with , we denote the BSM channel as , the Bhattacharyya parameter of is
Value (2) is equal to the upper bound probability of error of maximum likelihood (ML) decoding of a single use of the channel. It was shown that takes values from the interval [0,1]. Channels with small values are almost noiseless, while channels with values close to 1 are almost purely noise channels [28]. The essence of wiretap polar coding is the transformation of n instances of and into the n-input channels and , which are polarized either as good or bad channels depending on their Bhattacharyya parameters, and , respectively, and/or symmetric capacity . In order to achieve strong secrecy, the authors of [17,18] proposed the following definition of good and bad polarized channels
using the security function and a parameter . For a fixed , we can define next partition of as follows.
Next, let us partition the set into two subsets and ()
This process obtained subsets of the polarized channels, and their meanings in terms of transmission quality in the main and wiretap channels are shown in Table 2.

Table 2.
Partition of the index of the polarized channels and , according to (3)–(10), ensuring strong secrecy.
A polar wiretap encoder performs a 1-1 transformation of the original input vector into an -dimensional code vector
where is Arikan’s generator matrix, given by
is the bit-reversal permutation matrix defined in [28], while is the b-fold tensor product of with itself. The input vector has the following structure
The corresponding components of the input vector are set to the following values
where is a random vector, selected by Alice uniformly at random from {0, 1}. The vector of frozen bits is set to the 0 vector of dimension , where is the complement of in . As was mentioned in [28], in the case of symmetric channels, any choice of frozen values is as good as another. From now on, we will assume that it is
For the coding scheme described, Proposition 16 in [17] is proven to hold:
From here, the conclusion follows that by choosing the security function , we can bound the mutual information leaked to Eve for any message distribution. Specifically, according to [17] (see Theorem 17), for any security function such that
the described wiretap coding scheme guarantees strong security.
As for achieving reliability conditions, since, in the general case,
it is necessary to apply involving chaining construction [18] over multiple blocks to ensure reliability. Namely, since non-frozen channels in a strong security coding scheme are given by
it is necessary to ensure reliable transmission in the channels indexed in the index set . This is exactly what chaining construction achieves by taking a subset of indices from the set , i.e., , such that . Random bits that are placed in in the -th block are used in in the -th block for … In the first block, random bits are used that were distributed to Alice and Bob before starting communication. In this way, the Successive Cancellation (SC) decoder on Bob’s side in each block can successfully decode the contents in the channels with indices from (19), and therefore
The corresponding secrecy capacity is provided by Theorem 1 in [17].
2.3. Privacy Amplification (PA)
Privacy amplification is a technique used in cryptography to enhance the security of a shared secret key between two parties. The primary goal is to convert a partially secure or somewhat compromised key into a highly secure key, even in the presence of an eavesdropper who may have some knowledge about the original key [19,29]. In terms of practical application, hash functions called universal families have a special role [30].
Definition 1.
The family of functions , where and are two final sets, is 2—universal, or in short—universal, if the following holds
where is a random variable that represents a random choice of a function uniformly at random in .
An example of a frequently used class of universal hash functions is given by
In applications, a random choice of a hash function from a given set is implemented using a seeded pseudo-random generator. To emphasize this fact, we explicitly introduce seed notation. Therefore, a hash function from the class , is denoted as
where denotes a seed of adequate length. If is available only to legitimate users, the hash functions are typically known as cryptographic hash functions.
Definition 2.
The difference between the dimensions of the domain and codomain of a given class of hash functions will be referred to as its compression rate .
The compression rate of class , defined in (21), is
2.4. Ideal and Ideal Autonomous Cipher Systems
Consider a general symmetric cipher system , where is the input plaintext, is the ciphertext, and is the secret key.
According to Shannon, an ideal ciphering system is one in which the key equivocation, i.e., , remains non-zero even as the number of ciphertext symbols approaches infinity [25]. This means that the uncertainty about the key does not reduce to zero, regardless of how much ciphertext is available to an attacker. Important properties of ideal encryption systems are as follows.
- Non-zero key equivocation: the key remains partially unknown, no matter the length of the intercepted ciphertext.
- Security over time: the security of the system does not degrade with the amount of data encrypted and transmitted.
- Practical key length: the key length can be shorter than the message length, unlike a one-time pad, but must be sufficient to maintain key equivocation.
A strongly ideal system has a key equivocation constant at the entropy of the secret key, i.e., This implies an even higher level of security, ensuring that the key’s uncertainty remains unchanged from its a priori value, regardless of the volume of ciphertext available. The key characteristics are as follows.
- Constant key equivocation: the amount of information about the key that remains unknown does not diminish with increasing ciphertext.
- Enhanced security: it offers superior protection against extensive ciphertext analysis, maintaining key secrecy over an indefinite amount of encrypted data.
- Robust design: it typically requires more sophisticated cryptographic techniques to ensure that key equivocation remains constant.
By distinguishing these two concepts, Shannon’s theories provide a framework for evaluating and designing cryptographic systems based on the desired level of security and practical constraints.
Starting from these foundational Shannon definitions, we will define a new term—the ideally secret autonomous robust ciphering system.
Definition 3.
An ideally secret autonomous robust (ISAR) ciphering system is one which can maintain minimal key equivocation at a predefined value , i.e.,
independently of the message’s probability distribution and without an additional secret key distribution system.
If several different secret keys are used during operation of one cipher system, which correspond to ciphertexts, we say that the system is ideally secret autonomous and robust if it is able to maintain a predetermined minimum value of equivocation for each of the applied keys, i.e.,
independently of the message’s probability distribution and without additional secret key distribution system.
Remark 1.
In Shannon’s definition of an ideal system, it is important that the key equivocation is not reduced to zero with an unlimited increase in the available ciphertext. On the other hand, a strongly ideal cipher system requires constant maintenance of key equivocation at the entropy level of the secret key. An ideally secret autonomous robust cipher system is, in a certain sense, between these two extremes. It maintains the minimum value of key equivocation at a predetermined value, which, in general, belongs to the open interval .
Remark 2.
Since is a non-increasing function of the number of observed ciphertext symbols n, the minimum in (23) is always reached at the maximum available n.
3. System Architecture and Security Properties of the ISAR Cyphering System
In this section, it will be shown that the ISAR cyphering system is equivalent to a wiretap model, whose main channel is error-free, while the wiretap channel is equivalent to an embedded symmetric stream cyphering system. In Theorem 1, it is shown how wiretap coding should be constructed in order to achieve strong secrecy and reliability. Theorem 3 gives the capacity of the wiretap channel, which turns out to decrease linearly with the length of the secret key. Theorem 4 gives the equivocation of secret key, while Theorem 5 gives the secrecy capacity of the proposed ISAR as a function of the polar code length and security margins for equivocation and privacy amplification. Then it is shown that for an arbitrary cipher system to be ideal with the same lower bound of key equivocation as the ISAR system, its secret key must be times greater than that of ISAR, where is proportional to message length. Thus, the superiority of the ISAR system increases with the length of the messages. The section concludes with a demonstration of how any symmetric stream ciphering system can be transformed into an ISAR.
Let the protected communication between the legitimate parties Alice and Bob take place in the successive exchange of messages , which were previously divided into a series of blocks of length . At their disposal is a symmetric stream cyphering system based on a key stream generator KSG() with a short secret key that produces the key stream (see Figure 1). As is known [1], such systems cannot provide strong security, and practical secrecy is measured by the amount of computer resources spent by the adversary (Eve) in arriving either at the message (partial system cracking) or the secret key (total system cracking). Block denotes a polar coder, which performs a 1-1 transformation of message into an -dimensional codeword vector , while the block performs an inverse transformation of vector into message . Alice and Bob have local sources of randomness (denoted by RS on Alice’s side), as well as privacy amplification (PA) blocks, which, based on the input random string obtained in block , generate a shorter random string that serves as a new secret key for encrypting the vector in block . We will assume that the system uses a cryptographic hash function from the class of universal hash functions, as well as that the seed was previously exchanged between Alice and Bob. In the initial block, , i.e., the initial secret key of the given KSG().
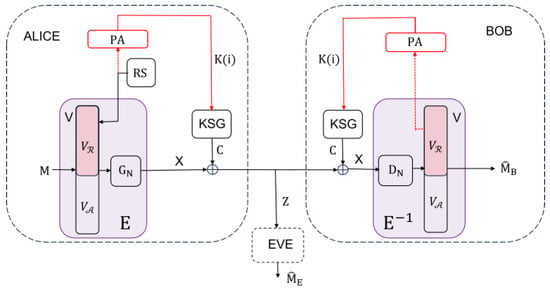
Figure 1.
ISAR ciphering system for secure communication without explicit secret key exchange.
Remark 3.
Additionally, we assume that the cipher system based on KSG() is semi-injective with respect to , i.e., that the knowledge of ciphers and messages uniquely determines , i.e., holds.
A system conceived of in this way can also be viewed as a kind of wiretap model. The legitimate users Alice and Bob are communicating over an equivalent noiseless main channel , where is the identity matrix (see Figure 2). An eavesdropper, Eve, is wiretapping over an equivalent wiretap channel , where is an matrix, with being the probability of receiving , given that was sent (see Figure 3). In order to be able to apply the results presented in Section 2, we have to prove that the equivalent wiretap channel is a BSC.
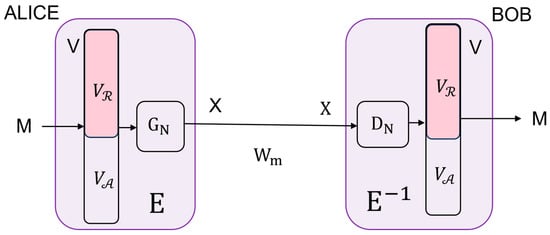
Figure 2.
Equivalent main channel.
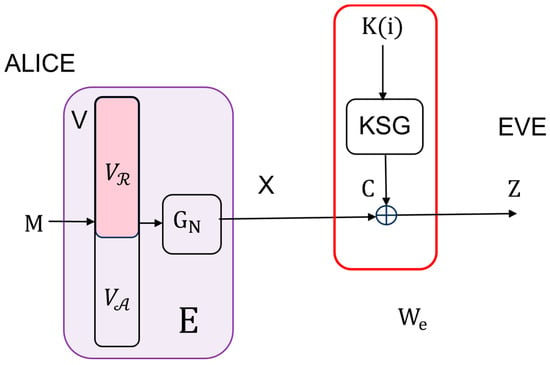
Figure 3.
Equivalent wiretap channel.
Lemma 1.
The equivalent wiretap channel is a BSC.
Proof.
According to the proposed scheme (Figure 1),
Since is independent of , (25) is equivalent to BSC ( where the crossover probability is given by . □
We can now formulate the main result of this part of the work.
Theorem 1.
Let be an arbitrary security function that satisfies Condition (17). Let the index sets and be given by and , while is a random vector, selected by Alice uniformly at random from {0, 1}. If, in the ISAR system, the input vector is structured as follows
then it satisfies both the reliability and strong security criteria precisely.
Proof.
Bearing in mind that the equivalent main channel for the ISAR system is noiseless, the wiretap coding scheme for strong secrecy is determined by the sets of polarized channel indices found by (3)–(10), which now have the following values
According to (35), the problematic set of indices is an empty set; therefore, it is not necessary to apply the chaining scheme. By structuring the input vector according to (26), where the sets of indices and are given by (32) and (33), respectively, we conclude that the proposed polar coding scheme is merely an instantiation of the general polar wiretap coding scheme from Section 2.2, which, under the assumptions of Theorem 1, ensures both reliability and strong secrecy. Since the main channel is noiseless, decoding on Bob’s side is not performed using the SC decoder, but rather by a simple inverse operation with respect to the encoding, i.e.,
given that Arikan’s generator matrix is its own inverse over the Galois field . Therefore, the reliability condition expressed by (27) is actually deterministically satisfied. This completes the proof. □
Theorem 2.
For any security function and the constants that satisfies Condition (17), , , and , the rate of the coding scheme of the proposed system from Figure 1 approaches the secrecy capacity, namely
Proof.
The proof follows directly from Theorem 1 of [17], and the fact that the capacity of main channel is . □
Remark 4.
Eve’s optimal strategy is to attempt to decode the wiretapped using the SC decoder after receiving it [28]. The average block error probability on Eve’s side can be lower-bounded, applying Lemma 2.9 of [31] by Korada
where is the information set. Considering that Eve does not know the frozen bits on her side, the information set includes all indices, i.e., and the polar code applied is of rate 1; see the similar argumentation in [32]. The maximum value of is very close to 1, bearing in mind that includes bad channels as well. Therefore, according to (39), it follows that
where is small. From this, we conclude that Eve’s optimal decoding strategy of using the SC decoder results in the maximum decoding error, preventing her from obtaining both the message and the purely random sequence .
It is evident that the key properties of the proposed system depend on the capacity of the wiretap channel . The following theorem determines the value of this quantity, depending on the length of the polar code and the length of the secret key .
Theorem 3.
The capacity of Eve’s channel in the proposed system in Figure 1 is given by
where is the length of the secret key of the given symmetric stream cyphering system based on KSG(), while is the length of the polar code.
Proof.
For a discrete memoryless symmetric channel
with the input and the output , the channel capacity is defined as
where the maximum is taken over all possible input distributions [33]. Furthermore, we have
The input to the wiretap channel is also the input (messages) to the symmetric stream ciphering system based on KSG(). Message equivocation is equal to key equivocation
for every symmetric ciphering system, semi-injective with respect to (see Theorem 1 in [34]). On the other hand, it well known that (see, for example, [25])
which, by substituting into (44) and then into (43), gives
One of the primary goals in designing any cipher system is for the ciphertext to appear to be totally random for as long as possible, i.e.,
This holds for larger values of . The assumption in (47) is referred to by Massey in [35] as the “total randomness” assumption, and it is shown to be valid as long as
where is the unicity distance of a given cipher system [1]. Considering (47) and the fact that since the secret keys are chosen as purely random sequences, from (46), we obtain or, normalized per bit,
which had to be proven. □
Remark 5.
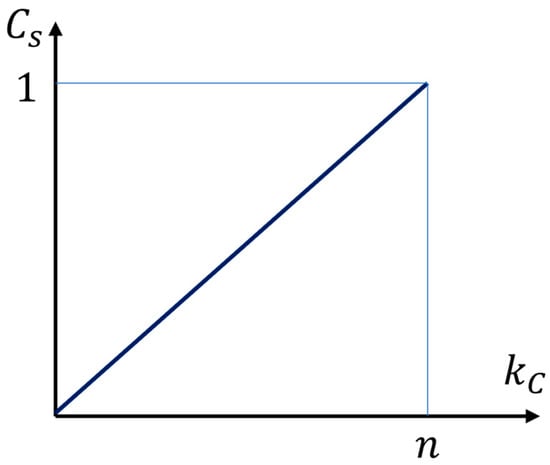
Given Theorems 2 and 3, the secrecy capacity of the proposed system is
From this, the fundamental impact of the secret key length is clearly evident (see Figure 4). For , the system does not provide any security, while for , . This means that in the latter case, we can choose all n bits of polar code for secure transmission of n message bits.

Figure 4.
The linear dependence of the secrecy capacity of the proposed system on the secret key length, without imposing restrictions that the system must be ideal and autonomous.
In order to examine the properties of ideally secret autonomous cipher systems, we need the following theorem, which provides a lower bound on the equivocation of the system’s secret keys.
Theorem 4.
The equivocation of the secret keys of KSG(), when the ciphertext is known, satisfies the inequality
where n is the length of the polar code, is the entropy of the secret key, and is a purely random vector of dimension .
Proof.
Generally, according to [25], for any cipher system with a secret key , the input , and the ciphertext (output) , it holds that . On the basis of (11), the output vector can be written in the form
where and are submatrices of the polar code generator matrix consisting of the corresponding rows in .
The ranks of the matrices and are and , respectively, because the generator matrix has the full rank . Therefore, and can be uniquely represented by a set of basis vectors of dimensions and . These base vectors are some of the column vectors of the matrices and . We will denote these sets of column indices as and . Then there exists a one-to-one correspondence between and , and between and . Hence
According to the data processing properties of entropy [35], we conclude that in the PA procedure, there is a limitation, , from which it follows that the secrecy capacity in the ISAR system must be Thus, it holds that
given the condition and the fact that is a purely random vector with the maximum entropy equal to Since it is always true that
we finally obtain
which had to be proven. □
To ensure that the system has autonomy in generating secret keys, we need to limit the polar code rate, because some of the polar code bits must be used for generating and distributing secret keys. Additionally, for the system to be ideal and autonomous, a further reduction in secrecy capacity is necessary to maintain the desired minimum level of key equivocation. These facts are summarized in Theorem 5 below.
Theorem 5.
The proposed system is ideally secret, autonomous, and robust, with the maximal secrecy capacity
where is a given minimum value of key equivocation and is the compression rate of the applied class of universal hash functions. The length of the secret key of the given symmetric stream cyphering system is , while is the length of the polar code.
Proof.
To prove that the proposed system is ideal, it is necessary to show that for given (23) and (24) hold. Consider the general case where Alice sends a message of arbitrary length to Bob. The message will be divided into blocks of length The total number of blocks will be , where is the length of the polar code, so The last block, if it is not of length , can be padded with arbitrary content. According to the proposed coding scheme that provides strong security, . According to (37), in addition to the transmitted message , Bob decodes, without error, a purely random vector , which is of length , which was written on the indices from the set
given in (32) during the encoding process on Alice’s side. Thus, Alice and Bob, after decoding, possess identical random sequences in each of the transmitted blocks of the polar code. Eve’s optimal strategy is to decode her received signal at the output of the wiretap channel using the SC decoder. Eve knows the parameters of the applied polar code, such as the length and the index sets and , but does not know the values of the bits at those positions. This situation is equivalent to the SC decoder operating in the mode of unknown so-called frozen bits. As noted in Remark 4, Eve’s error in optimal decoding is close to the maximum, so it can be said that Eve’s information about the sequence is close to zero. By applying PA to the common random sequences , Alice and Bob can further reduce Eve’s residual information about these sequences. In each current block, a secret key of length is generated for the next block using some chosen PA algorithm
Given that is the compression rate of the class of universal hash functions applied in the PA process, it follows that
Having in mind that from (59) and (60), it follows that
For the system to be ideal, it is sufficient to ensure that the right-hand side of (57) equals a predetermined minimum value of key equivocation in each block, i.e.,
That is, assuming that the ergodicity of the local randomness source, i.e., , it follows that
By substituting (61) into (63), it is obtained that
which had to be proven. □
Figure 5 gives a graphical presentation of the interdependence of the quantities , , , , and from Theorem 5. If we compare Figure 4 and Figure 5, the restrictions imposed by ideality and autonomy on the possible values of secrecy capacity, secret key length, and polar code length can be clearly seen.
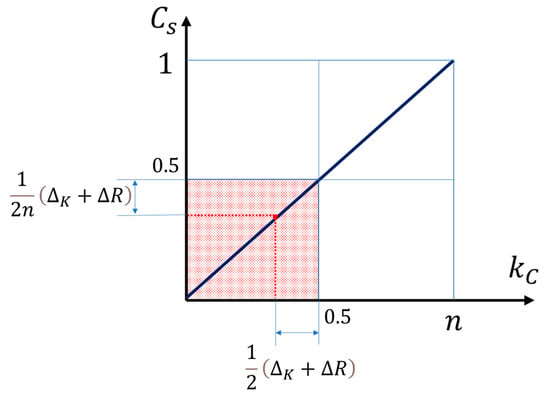
Figure 5.
Dependence of secrecy capacity on the secret key length, when ideality and autonomy are imposed. The red shaded region shows the possible values of (, ), as well as the corresponding dependence of these quantities on and , according to (58).
In Figure 6 and Figure 7, the dependence of the secrecy capacity on the normalized minimum value of key equivocation and the normalized compression rate of the hash function applied in the PA process is shown.
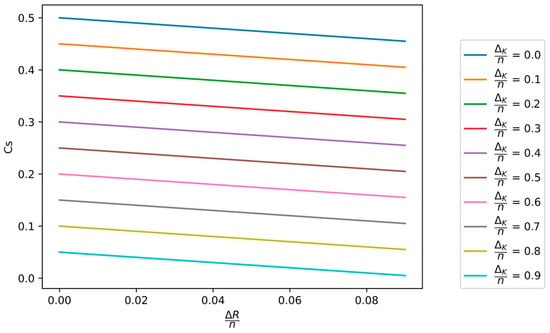
Figure 6.
The dependence of the secrecy capacity on the normalized compression rate of the hash function applied in the PA process, for different values of the normalized minimum key equivocation .
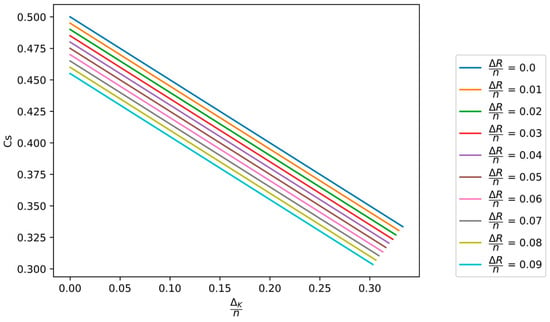
Figure 7.
The dependence of the secrecy capacity on the normalized minimum key equivocation for different values of the normalized compression rate of the hash function applied in the PA process.
Note that if the security margins and are fixed constants, then, on the basis of Theorem 5, we conclude that holds, which is the maximum possible value of the secret capacity of the ISAR system.
The presented theory offers an effective methodology for synthesizing this class of systems with predetermined security margins. The algorithms for configuring the ISAR system and for enciphering/deciphering messages of arbitrary length are described below. On the basis of the initial values of parameters and , the secrecy capacity and the length of the secret key are determined. If these parameters are acceptable, the synthesis of the corresponding wiretap polar code proceeds. Identifying the index sets
and
requires the polarization of the wiretap channel. For practical purposes, it is simpler to replace this channel with an equivalent channel of the same capacity. Consequently, the crossover probability must satisfy the condition
where
is the binary entropy function, and is its inverse. The polarization procedure under SC decoding can be performed using various methods, such as Monte Carlo [28], density evolution (DE) [36,37], and DE with Gaussian approximation (GA) [38], among others. In the ISAR system, where the wiretap channel is designed by the system developer, all essential parameters for the wiretap channel are much more accessible and accurately estimated compared with a scenario involving real wiretap channels. For instance, in determining the Bhattacharyya parameters using the Monte Carlo method for polarization, generating an ensemble of wiretap channel output samples is manageable. This process is facilitated by the precise knowledge of the crossover probability (65), allowing for an accurate assessment of the results.
Remark 6.
Let us compare the proposed ISAR system with a classic ideal cipher system that has the same minimal key equivocation value for the same length of observed ciphertext. To ensure a fair comparison, we assume that the entropy of the input messages is identical in both systems. After encrypting t blocks of messages, and assuming that the blocks are independent, the ISAR system has a total equivocation of all applied keys equal to
since the formation of each block in the polar code is independent of the previously formed blocks. A classic ideal cipher system with the secret key under the same conditions and for the same length of ciphertext has an equivocation given by
Equating the same lower bounds in (67) and (68) yields the condition that
That is
assuming that all secret keys in both systems have maximum entropy.
To ensure that a classic encryption system achieves the same lower bound on key equivocation as the ISAR system for the same observed ciphertext length, it would need a secret key t times longer than the key length of the KSG() (see Figure 8). Additionally, must be pre-distributed to legitimate parties. The length of this key scales linearly with the message length , specifically with . In contrast, the proposed ideal autonomous system requires only a fixed-length secret key K, independent of the message length, and requires only an initial exchange of the key values . Therefore, the benefits of the ISAR system become more significant as the length of the messages increases.
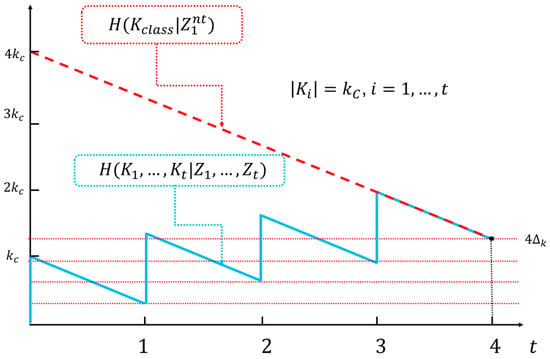
Figure 8.
An example of the relationship between the key equivocation of the ISAR system (blue line) and the classic cipher system (red line) as a function of the number of encrypted blocks for a given minimum value , provided that, after four blocks, both systems have the same minimum key equivocation value. The identical slopes of both equivocations are a consequence of the same probabilistic properties of the source being encrypted. Note that the classic system must have a secret key four times longer than the ISAR System.
Remark 7.
Since the length of the polar code must be a power of 2, it is necessary to correct (71) to the value
bearing in mind the limitation
The ISAR system can be obtained by a suitable transformation of any given stream ciphering system based on KSG() with a known secret key length . The procedure includes the following steps.
- On the basis of the expression in (58) for the given value of the length of the secret key , we can directly obtain the required length of the polar code, i.e.,
- The corrected value of the length of the polar code block (72) allows the eventual correction of the total security margin to the new value
- Since all elements for the ISAR system’s setup are available at this step, i.e., , further operation of the system takes place according to Algorithms 1–3.
| Algorithm 1 System setup |
|
| Algorithm 2 Enciphering |
// generate random sequence of length If then else end KSG // generate stream ciphering sequence of length // polar coding // enciphering end |
| Algorithm 3 Deciphering |
else end KSG // generate stream ciphering sequence of length // deciphering // deciphered random sequence // deciphered message // completly deciphered message end |
4. Security Analysis of the ISAR Ciphering System
The standard assumptions common in cryptography were used in the analysis of the ISAR system. The Kirchhoff principle dictates that the attacker knows the entire system operation algorithm, except for the initial secret key K of KSG(K). Further, the security integrity of cyphering and deciphering devices is an obvious assumption in cryptography. Therefore, the computation processes on the side of the legitimate sender (the dot-framed square named Alice) are inaccessible to the attacker during the execution of the polar coding and encryption operations. Otherwise, the attacker would have direct access to the messages and/or the key stream . The same applies to the computation processes on the side of the legitimate recipient (the dot-framed square named Bob) during polar code decoding and decryption.
In the following analysis, we focus on the examination of passive attacks on the system. This implies that the attacker has access to the output of the wiretap channel and all information related to the architecture and operation of the system, except for the initial value and the seed of the chosen hash function According to the primary objective of the attack, we can distinguish three types: message attacks, attacks on locally generated random sequences, and attacks on the secret key.
4.1. Attacks on Messages
In this type of attack, Eve attempts to obtain the message in each block, based on the observation of the wiretap channel output . According to Theorem 1, the proposed system satisfies the strong security criterion (28), which means that, asymptotically, with an increase in the codeword length , Eve can only acquire a negligible amount of information about the messages . In the case of codewords of final lengths n, the amount of information leaking to the attacker is not only limited in quantity but is also not localized to specific bit positions in the ciphertext, which further complicates potential cryptanalysis.
4.2. Attacks on Locally Generated Random Sequences
In this type of attack, Eve first tries to obtain one of the random sequences locally generated by Alice based on the observation of the wiretap channel outputs . In the second step, using some obtained value , Alice could potentially generate the correct secret key for the next block . Knowing the secret key for block , Eve could successfully decode all subsequent blocks, thereby obtaining all messages in the sequence . However, this scenario is not feasible. The first step cannot be realized efficiently since, according to Remark 4, the average block error probability on Eve’s side is close to maximal (see (40)). Of course, in this step, Eve can apply a brute force attack, which requires attempts. This means that this number of active hypotheses for will proceed to the next step. The second step is not possible without knowing the seed of the chosen hash function As the success of this attack depends on the success of both steps, this type of attack is practically unfeasible because the overall difficulty of the attack is equal to the product of the difficulties of both steps.
4.3. Attacks on the Secret Key KSG()
A far more powerful cryptanalytic attack than an attack on individual messages is an attack on the secret key of the KSG. If Eve were to obtain the secret key in block where , she would be able to access message , the random sequence , and, consequently, the secret key for the next block. This would allow her to repeat the same process for each subsequent block, thereby gaining access to all subsequent transmitted messages , the random sequence , and the generated secret keys From the system designer’s perspective, it is crucial to prevent this scenario. The information-theoretic quantity that quantifies the likelihood of such an attack is the equivocation of the secret keys for a given wiretap channel’s output. As the ISAR system is ideally secret, its secret key equivocation, according to (62), never falls below the value , which is the security parameter in the synthesis process of the ISAR. It is important to mention that, from the cryptanalyst’s point of view, possible values for keys/messages exist with equal probabilities. Therefore, the system’s designer can render this attack unsuccessful with any chosen margin of security. It is important to note that increasing the margin of security leads to a reduction in the secrecy capacity of ISAR (see Theorem 5 and Figure 7).
Remark 8.
An attack on the secret key of KSG(K), both as an independent entity and as part of an ISAR system, requires additional clarification. It is logical to assume that doubling the length m of the secret key increases the cryptanalyst’s effort by times in a brute force attack if a ciphertext of length greater than the unicity point is available. The outcome of this attack is a unique secret key, given that . In the case of an ISAR system, however, key equivocation never falls below the value , meaning the cryptanalyst is left with equally likely hypotheses, regardless of the ciphertext length. Additionally, according to (71), for any secret key length (including a doubled one), it is possible, by increasing the length of the polar code n, to independently select a security margin .
From this brief analysis, we can conclude that classic cryptographic systems with a finite secret key and the ISAR system must be carefully compared, since the work of the cryptanalyst in the case of the ISAR system does not lead to a unique solution.
Example 1.
To understand the order of magnitude of the difficulty of executing this attack, let us consider a typical example of an ISAR with the parameters (expressed in bits) . According to (58), , and the key length is bits. Let us assume that Eve’s optimal strategy for each block of the polar wiretap code reaches the lower bound of equivocation of 100 bits of the key. This means that Eve cannot resolve this uncertainty in any way. Recall that in a brute force attack examining all possible keys, all decrypted messages would be equally likely and valid as potential final solutions.
The example above shows that for the polar code length n of order , the key length of KSG() is of order . These lengths are not common for commercial stream ciphering systems. However, this does not mean that such systems cannot be relatively easily upgraded to the required key lengths. As an example, we cite a generic model of a pseudo-random generator described in [39]. If the address and selection sequences are chosen so that they are the outputs of two multiple linear shift registers, then the lengths of the equivalent secret key of this pseudo-random generator can easily be set in ranges of order .
The cryptanalysis presented here may cause some doubt regarding the level of security of the ISAR system. Specifically, wiretap polar encoding enables perfect secrecy of the messages, while the ISAR, on the other hand, guarantees only ideal secrecy. The explanation is simple. The security of the entire system is equal to the security of the weakest link in the chain. In this case, it is KSG(K), which can only provide ideal security.
To confirm this, let us show that the ISAR cannot be perfectly secret. For perfect secrecy, it is necessary for the following to be valid
That is, in the case of symmetrical semi-injective systems
According to (57), it follows that
or
The last equality holds if and only if is a binary symmetric source (BSS) with maximum entropy. Taking (11) into account, as well as the fact that Arikan’s generator matrix is nonsingular, it follows that
In other words, must be a BSS, and, therefore, must also be a BSS. Considering that, according to (14), , we conclude that the message must be a BSS. This contradicts the robustness of the ISAR, which requires that its properties must be independent of the probability distribution of the messages. In addition to this difficulty, perfect secrecy of the ISAR would require that the entropy rate of the secret keys must be greater than or equal to the entropy rate of the input sequence in KSG(, or
According to (50) in Remark 5, for , which corresponds to the fact that must be a BSS, it follows that, in this case, would have to hold. This contradicts the property of the ISAR stated in Theorem 5, namely that .
5. Practical Aspects
This section shows that the complexity of the system is , where n is the length of the polar code. For point-to-point protection, the initial exchange of the secret key and the hash function seed is performed only once, regardless of the number of sessions or communication disruptions.
5.1. Complexity of the ISAR
The computational complexity of the ISAR system includes the total complexity of polar coding and decoding, as well as the complexity of the PA block.
Polar codes are attractive in practice due to their relatively low complexity compared with other coding schemes, especially when considering the powerful error-correcting capabilities they offer. The complexity of encoding a polar code of block size n is . This efficient complexity is due to the structured way in which the polar transform combines inputs, leveraging the recursive nature of the polar code’s construction, and can be performed using the Fast Fourier Transform (FFT) approach. To be precise, let denotes the worst-case complexity over all polar codes with the given block length . Arikan, in [28], showed that . Starting with the initial value , by induction, it is obtained that for all , where . Thus, the encoding complexity is indeed .
In general, the decoding complexity depends on the applied decoding algorithm. However, in the ISAR system, decoding is a deterministic procedure identical to encoding since Arikan’s generator matrix is involutory. Therefore, the complexity of decoding is identical to the complexity of encoding, i.e., [28].
The PA block was implemented using random binary matrices of dimension n × , which have the Toeplitz structure. It is known that this class of hash functions belongs to the universal family of hash functions (see [40,41]). The Toeplitz hash functions are particularly suitable for typical values for n in polar coding (in the order of ). Namely, the PA block can be efficiently implemented with a complexity of , instead of O(), in the case of hash functions in the form of random binary matrices without the Toeplitz structure. The choice of ΔR is closely related to the leakage of the secret key to Eve. Practical methodologies for selecting this parameter, based on the estimation of a conditional Renyi entropy of order 2, have been developed in other works [42,43].
Consequently, we can say that the complexity of the ISAR system, without taking the complexity of KSG() into account, is of the order of , which indicates that the implementation of the proposed algorithm does not require special memory and computational resources. This makes it very attractive for practical implementation and use.
5.2. Integration of the ISAR Ciphering System in Contemporary Information and Communication Infrastructure
When applying the ISAR in modern information and communication infrastructure, one should keep in mind the two most important advantages of this system:
- Guaranteed security margins in terms of key equivocation (ideality);
- Independence of the length of the keys from the length of the messages.
The ideal position of the ISAR system is within the framework of permanent point-to-point protection of large-capacity information flows. That is when ideality and the independence of the length of the keys from the length of the messages come into play. As already mentioned, the start of communication requires the exchange of the secret key of KSG() and the seed of the applied crypto hash function. It is interesting to note that the disruption of protected communication or its regular termination does not require an additional exchange of these values for subsequent communication. Namely, the decoded random sequences of the last block of polar code can be memorized and used to generate the initial key for subsequent communication. This raises the autonomy of the ISAR system to an even higher level.
The ISAR can also be viewed as an autonomous key generation and distribution system based on a local source of pure randomness (denoted by RS in Figure 1). In such an application, the decoded random sequences can be accumulated, stored, and then used independently of the ISAR, for the purposes of any legitimate party’s cyphering system which requires previously exchanged secret keys.
6. Conclusions
In this paper, we introduced a class of symmetric ciphering systems termed ISAR (Ideally Secret Autonomous Robust) systems. These systems are designed to provide ideal secrecy, autonomy in key generation and distribution, and robustness to the probabilistic structure of messages. These systems address the longstanding challenge in cryptography of balancing security with practicality, particularly by eliminating the need for lengthy secret keys and additional key distribution infrastructure. By ensuring a predetermined minimum value of key equivocation and continuous key refreshing, ISAR systems provide robust security against passive attacks on both keys and messages.
Our work demonstrates that ISAR systems can be applied to any existing symmetric stream ciphering system without requiring changes to the original encryption algorithm, thus offering a versatile and efficient solution for enhancing the security of current cryptographic practices. This transformation greatly supports privacy, a critical requirement for modern security systems. Overall, the ISAR system represents an advancement in cryptographic security, offering an efficient methodology for creating ciphering systems with predetermined security margins.
The main limitation of the ISAR system is its dependence on the encoding and decoding of the chosen polar code. Particularly, the constraint that the block length must be of the form may cause some practical problems. Although recent advancements have proposed efficient modifications for polar codes of arbitrary block lengths, their application within the ISAR system requires more careful analysis and assessment of potential security breaches. Another potential limitation of the ISAR system is its current applicability to symmetric stream ciphering systems only.
Future research directions include exploring optimizations in the ISAR architecture, extending its applicability to a broader range of cryptographic scenarios, and investigating additional techniques for enhancing its resistance to more sophisticated attack vectors. Also, the potential extension to block cipher systems is of great practical and theoretical significance. The continued development of ISAR systems holds the promise of ensuring stronger privacy and security measures in an increasingly digital world.
Author Contributions
Conceptualization, M.M.; methodology, M.M., T.U. and J.R.; software, J.R.; validation, M.M., J.R. and B.B.; formal analysis, M.M., J.R. and T.U.; investigation, M.M. and J.R.; resources, B.B.; data curation, J.R. and B.B.; writing—original draft preparation, M.M. and J.R.; writing—review and editing, M.M. and J.R.; visualization, M.M. and J.R.; supervision, M.M. and B.B.; project administration, J.R.; funding acquisition, B.B. All authors have read and agreed to the published version of the manuscript.
Funding
The research is funded by the Vlatacom Institute of High Technologies under Project #164 EEG_Keys.
Data Availability Statement
The original contributions presented in the study are included in the article, further inquiries can be directed to the corresponding author.
Acknowledgments
M.M. would like to express gratitude to his son and his family, in whose backyard in Pleasant Hill California, under the tree where the squirrel house is, he first thought of the ISAR system concept. At the same time, the authors explain why Theorem 5 is called the Squirrel House Theorem in their internal communication.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Gunther, C.G. A universal algorithm for homophonic coding. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1988; pp. 405–414. [Google Scholar]
- Massey, J. Some Applications of Source Coding in Cryptography. Eur. Trans. Telecommun. 1994, 5, 421–429. [Google Scholar] [CrossRef]
- Ryabko, B. Unconditionally secure short key ciphers based on data compression and randomization. Des. Codes Cryptogr. 2023, 91, 2201–2212. [Google Scholar] [CrossRef]
- Ryabko, B.Y. A simply realizable ideal cryptographic system. Probl. Inf. Transm. 2000, 36, 84–89. [Google Scholar]
- Oggier, F.; Mihaljević, M.J. An information-theoretic security evaluation of a class of randomized encryption schemes. IEEE Trans. Inf. Forensics Sec. 2014, 9, 158–168. [Google Scholar] [CrossRef]
- Ryabko, B.; Fionov, A. Efficient homophonic coding. IEEE Trans. Inform. Theory 1999, 45, 2083–2091. [Google Scholar] [CrossRef][Green Version]
- Agrikola, T.; Couteau, G.; Ishai, Y.; Jarecki, S.; Sahai, A. On pseudorandom encodings. In Theory of Cryptography Conference; Springer: Cham, Switzerland, 2020; pp. 639–669. [Google Scholar]
- Russell, A.; Wang, H. How to fool an unbounded adversary with a short key. IEEE Trans. Inf. Theory 2006, 52, 1130–1140. [Google Scholar] [CrossRef]
- Dodis, Y.; Smith, A. Entropic security and the encryption of high entropy messages. In Theory of Cryptography Conference; Springer: Berlin/Heidelberg, Germany, 2005; pp. 556–577. [Google Scholar]
- Ryabko, B. Unconditionally Secure Ciphers with a Short Key for a Source with Unknown Statistics. Entropy 2023, 25, 1406. [Google Scholar] [CrossRef]
- Juels, A.; Ristenpart, T. Honey encryption: Security beyond the brute-force bound. In Advances in Cryptology-EUROCRYPT 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 293–310. [Google Scholar]
- Li, X.; Tang, Q.; Zhang, Z. Fooling an Unbounded Adversary with a Short Key, Repeatedly: The Honey Encryption Perspective. In Proceedings of the 2nd Conference on Information-Theoretic Cryptography, Virtual, 23–26 July 2021; Schloss Dagstuhl—Leibniz-Zentrum für Informatik: Wadern, Germany, 2021; pp. 23:1–23:21. [Google Scholar]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Bellare, M.; Tessaro, S.; Vardy, A. Semantic security for the wiretap channel. In International Cryptology Conference (CRYPTO); Springer: Berlin/Heidelberg, Germany, 2012; pp. 294–311. [Google Scholar]
- Harrison, W.K.; Almeida, J.; Bloch, M.R.; McLaughlin, S.W.; Barros, J. Coding for secrecy: An overview of error-control coding techniques for physical-layer security. IEEE Signal Process. Mag. 2013, 30, 41–50. [Google Scholar] [CrossRef]
- Mahdavifar, H.; Vardy, A. Achieving the secrecy capacity of wiretap channels using polar codes. IEEE Trans. Inf. Theory 2011, 57, 6428–6443. [Google Scholar] [CrossRef]
- Sasoglu, E.; Vardy, A. A new polar coding scheme for strong security on wiretap channels. In Proceedings of the 2013 IEEE Information Theory Proceedings (ISIT), Istanbul, Turkey, 7–12 July 2013; pp. 1117–1121. [Google Scholar]
- Bloch, M.; Barros, J. Physical-Layer Security: From Information Theory to Security Engineering; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Rajagopalan, A.; Thangaraj, A.; Agrawal, S. Wiretap polar codes in encryption schemes based on learning with errors problem. In Proceedings of the 2018 IEEE International Symposium on Information Theory (ISIT), Vail, CO, USA, 17–22 June 2018; pp. 1146–1150. [Google Scholar]
- Liu, S.; Hong, Y.; Viterbo, E. Unshared secret key cryptography: Achieving Shannon’s ideal secrecy and perfect secrecy. In Proceedings of the 2014 IEEE Information Theory Workshop (ITW 2014), Hobart, TAS, Australia, 2–5 November 2014; pp. 636–640. [Google Scholar]
- Liu, S.; Hong, Y.; Viterbo, E. Unshared Secret Key Cryptography. IEEE Trans. Wirel. Commun. 2014, 13, 6670–6683. [Google Scholar] [CrossRef]
- Wang, H.; Tao, X.; Li, N.; Han, Z. Polar Coding for the Wiretap Channel with Shared Key. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1351–1360. [Google Scholar] [CrossRef]
- Zhao, Y.; Xu, S.; Chi, H. Encrypted Secure Polar Coding Scheme for General Two-way Wiretap Channel. IET Inf. Secur. 2019, 13, 393–403. [Google Scholar] [CrossRef]
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Leung-Yan-Cheong, S. On a special class of wire-tap channels. IEEE Trans. Inform. Theory 1977, 23, 625–627. [Google Scholar] [CrossRef]
- Arikan, E. A performance comparison of polar codes and Reed-Muller codes. IEEE Comm. Lett. 2008, 12, 447–449. [Google Scholar] [CrossRef]
- Arikan, E. Channel polarization: A method for constructing capacity achieving codes for symmetric binary-input memoryless channels. IEEE Trans. Inform. Theory 2009, 55, 3051–3073. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G.; Crepeau, C.; Maurer, U.M. Generalized privacy amplification. IEEE Trans. Inf. Theory 1995, 41, 1915–1923. [Google Scholar] [CrossRef]
- Carter, J.L.; Wegman, M.N. Universal classes of hash functions. J. Comput. Syst. Sci. 1979, 18, 143–154. [Google Scholar] [CrossRef]
- Korada, S.B. Polar Codes for Channel and Source Coding. Ph.D. Thesis, Ecole Polytechnique Federale de Lausanne, Lausanne, Switzerland, 2009. [Google Scholar]
- Kim, Y.S.; Kim, J.H.; Kim, S.H. A Secure Information Transmission Scheme With a Secret Key Based on Polar Coding. IEEE Commun. Lett. 2014, 18, 937–940. [Google Scholar] [CrossRef]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory, 2nd ed.; John Wiley & Sons: Hoboken, NJ, USA, 2006. [Google Scholar]
- Biondi, F.; Given-Wilson, T.; Legay, A. Attainable unconditional security for shared-key cryptosystems. Inf. Sci. 2016, 369, 80–99. [Google Scholar] [CrossRef]
- Massey, J.L. Applied Digital Information Theory II, Lecture Notes. Available online: https://www.isiweb.ee.ethz.ch/archive/massey_scr/ (accessed on 31 July 2024).
- Tal, I.; Vardy, A. How to construct polar codes. IEEE Trans. Inf. Theory 2013, 59, 6562–6582. [Google Scholar] [CrossRef]
- Mori, R.; Tanaka, T. Performance of polar codes with the construction using density evolution. IEEE Commun. Lett. 2009, 13, 519–521. [Google Scholar] [CrossRef]
- Trifonov, P. Efficient design and decoding of polar codes. IEEE Trans. Commun. 2012, 60, 3221–3227. [Google Scholar] [CrossRef]
- Unkašević, T.; Banjac, Z.; Milosavljević, M. A Generic Model of the Pseudo-Random Generator Based on Permutations Suitable for Security Solutions in Computationally-Constrained Environments. Sensors 2019, 19, 5322. [Google Scholar] [CrossRef]
- Tsurumaru, T.; Hayashi, M. Dual universality of hash functions and its applications to quantum cryptography. IEEE Trans. Inf. Theory 2013, 59, 4700–4717. [Google Scholar] [CrossRef]
- Hayashi, M.; Tsurumaru, T. More efficient privacy amplification with less random seeds via dual universal hash function. IEEE Trans. Inf. Theory 2016, 62, 2213–2232. [Google Scholar] [CrossRef]
- Radomirović, J.; Milosavljević, M.; Kovačević, B.; Jovanović, M. Privacy amplification strategies in sequential secret key distillation protocols based on machine learning. Symmetry 2022, 14, 2028. [Google Scholar] [CrossRef]
- Radomirović, J.; Milosavljević, M.; Banjac, Z.; Jovanović, M. Secret Key Distillation with Speech Input and Deep Neural Network-Controlled Privacy Amplification. Mathematics 2023, 11, 1524. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).