A Secure Certificate-Based Data Integrity Auditing Protocol with Cloud Service Providers
Abstract
1. Introduction
1.1. Related Works
1.2. Our Contributions
1.3. Outline of the Article
2. Preliminaries
2.1. Symmetric Bilinear Mapping
- Bilinear: , such that .
- Nondegeneracy: if g is the generator of , such that ( is the identity element in the group ) is the generator of .
- Computability: , such that can be calculated efficiently.
2.2. Security Assumptions
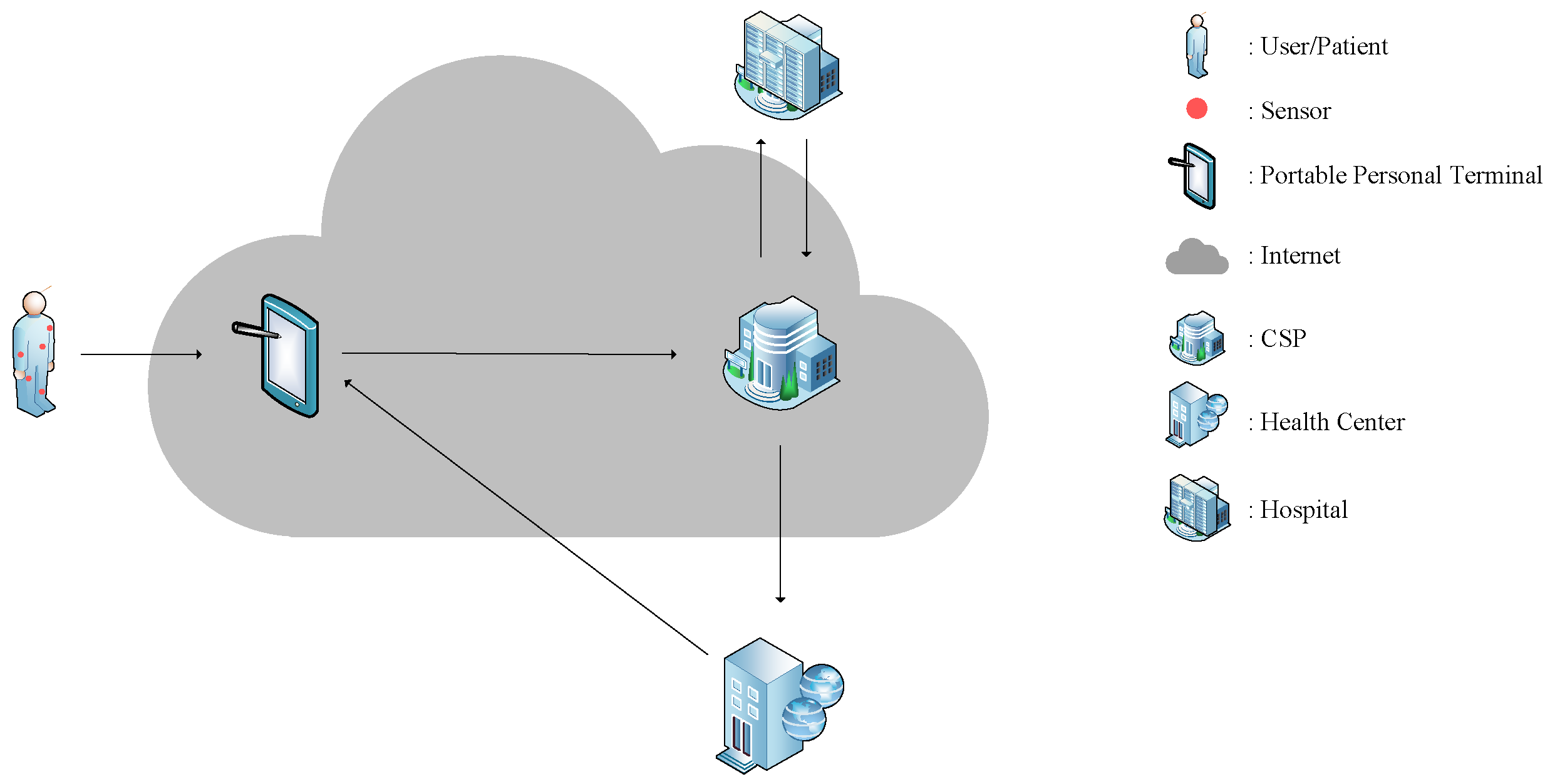
2.3. The Formal Definition of the CBDIAP
- 1.
- System setup with input security parameter λ, CSP initializes the data integrity auditing system to generate the system master private key and broadcast the system parameters .
- 2.
- User registration The user sends their and public key to the CSP. Then, the CSP returns a valid certificate to the user.
- 3.
- Outsourcing storage Given an encrypted dataset named , timestamp t, the user uploads the encrypted dataset , the dataset label τ, and the data block tags to the CSP.
- 4.
- Auditing (0/1): The TPA sends the user’s , , and the audit challenge to the CSP. The CSP generates a Data Integrity Proof to be returned to the TPA. The TPA output is one, which proves that the data are intact on the CSP, or, conversely, outputs zero.
2.3.1. Correctness
- 1.
- For the certificate returned by the CSP, the user must verify that the certificate sent by the CSP matches his or her own and to check whether the certificate is valid.
- 2.
- , if the CSP received from the TPA, the CSP can generate . Then, the CSP sends PF to the TPA. Finally, the TPA checks whether the matches the dataset label τ and checks whether the is evidence of the dataset .
- 3.
- For , the TPA checks the integrity of the data in the CSP by testing whether and match.
2.3.2. Security Model
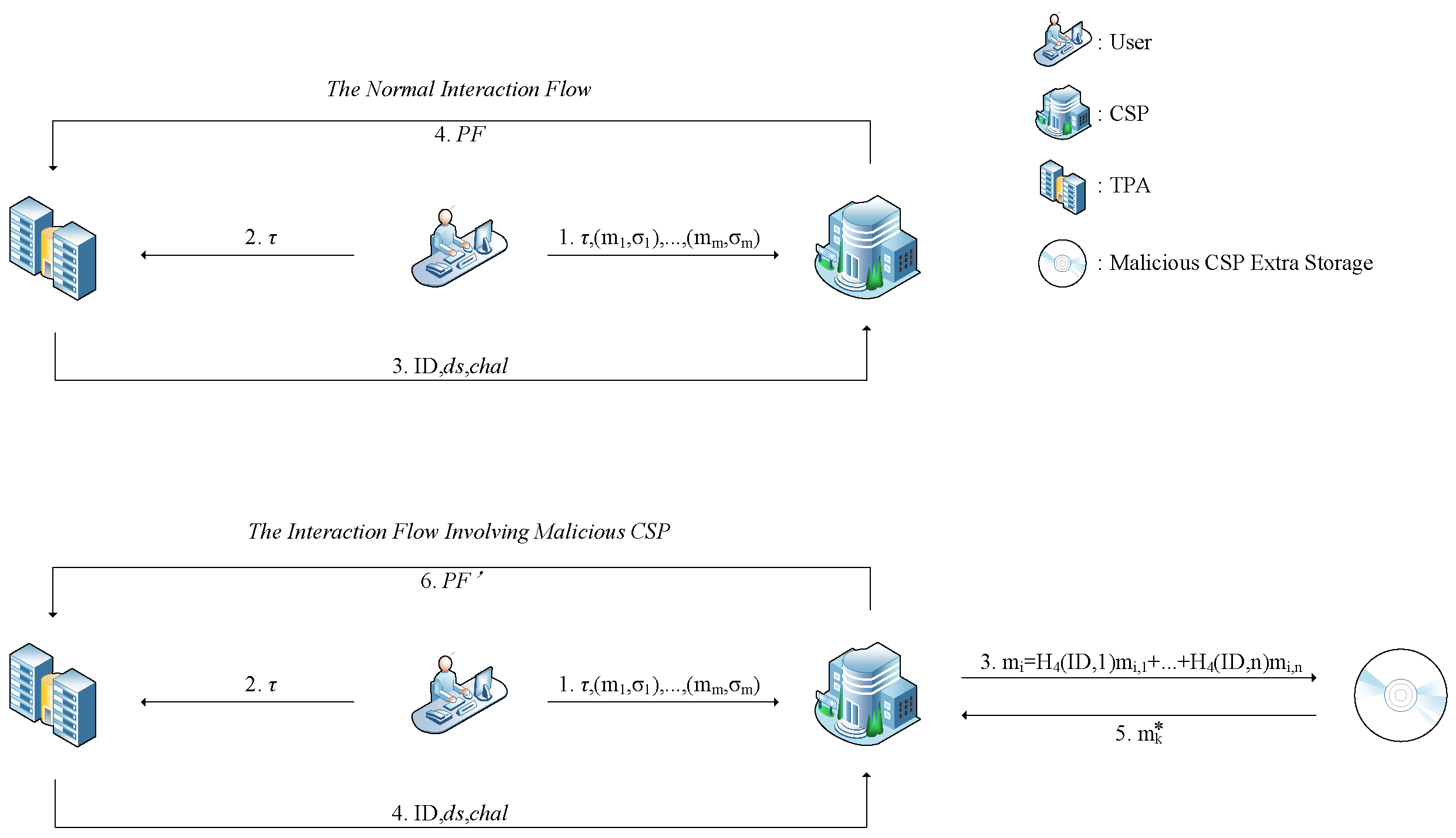
3. Data Block Forgery of LZ22 Protocol
3.1. Security Problems of LZ22
3.2. Data Block Forgery Experiments
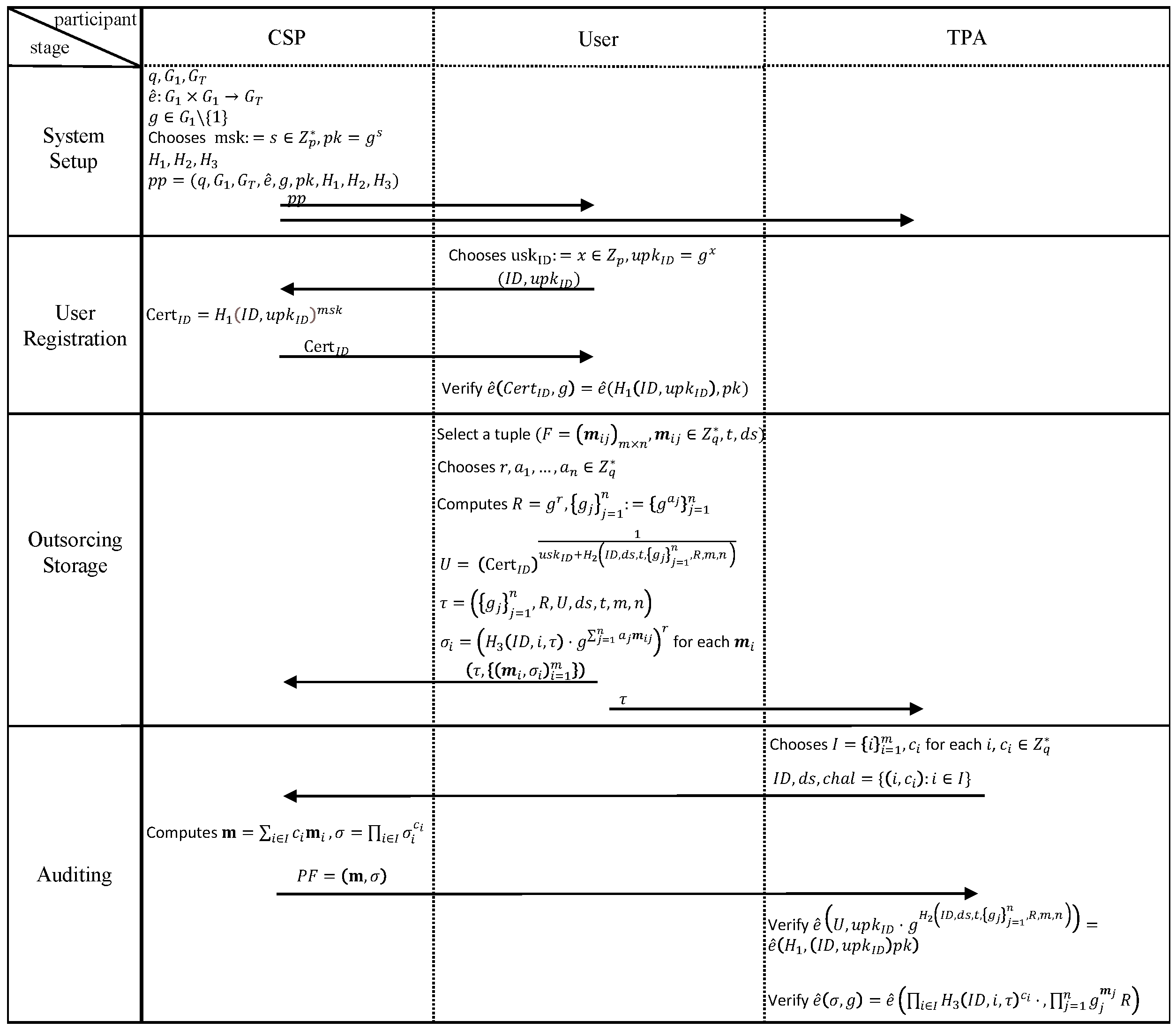
4. The Proposed Protocol
4.1. Concrete Structure
4.1.1. System Setup
4.1.2. User Registration
- UserKeyGen: the user randomly chooses as secret key , computes the user public key as , and then sends and to CSP.
- Certify: The CSP generates certificate and sends it to the user.
- Authentication: The user verifies the legitimacy of the certificate through equation .
4.1.3. Outsourcing Storage
- Data processing:
- (1)
- Given an encrypted dataset with timestamp t and dataset name , the user initially divides the dataset F into m data blocks , each comprising n sectors. Specifically, , where .
- (2)
- The user then randomly selects , calculates , and . The user assigns the label of dataset F and retains .
- (3)
- For each data block , the user computes the corresponding tag into Equation (2):
- Data uploading: The user uploads dataset label , data blocks , and corresponding tags to the CSP. At the same time, the user sends dataset label to the TPA.
4.1.4. Auditing
- Challenge: The TPA randomly selects a non-empty subset I with element . For each i, the TPA randomly chooses . Subsequently, the TPA transmits the user , dataset name and challenge to the CSP.
- Proof generation: Upon reception of , the CSP computes and in Equation (3):Subsequently, the CSP sends back to the TPA.
- Proof verification: Upon receipt of , the TPA initially verifies the validity of the label using Equation (4).
4.2. Correctness
4.2.1. Certificate Validity
4.2.2. Legitimacy of Dataset Label
4.2.3. Data Integrity Verification
4.3. Security Analysis
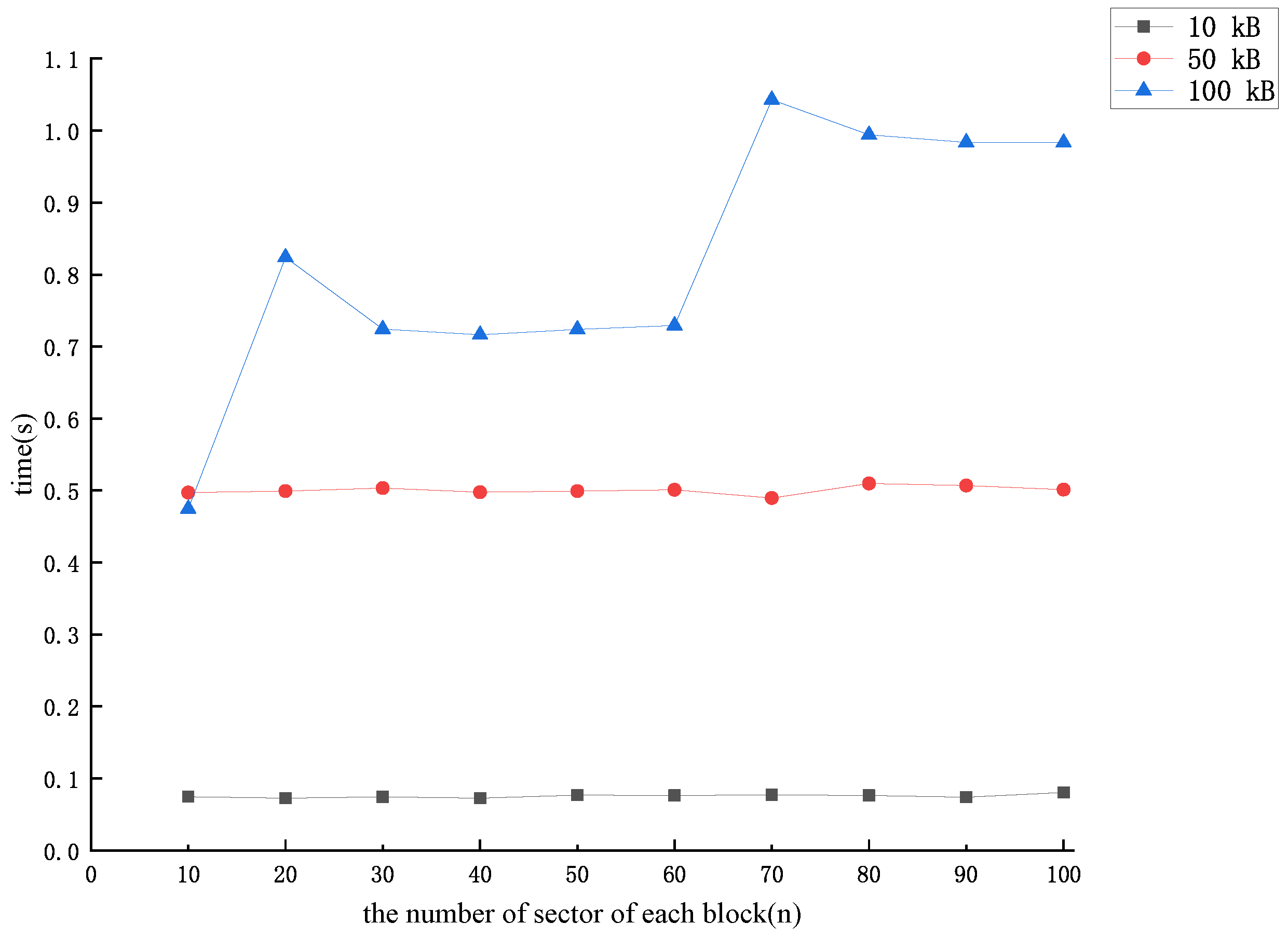
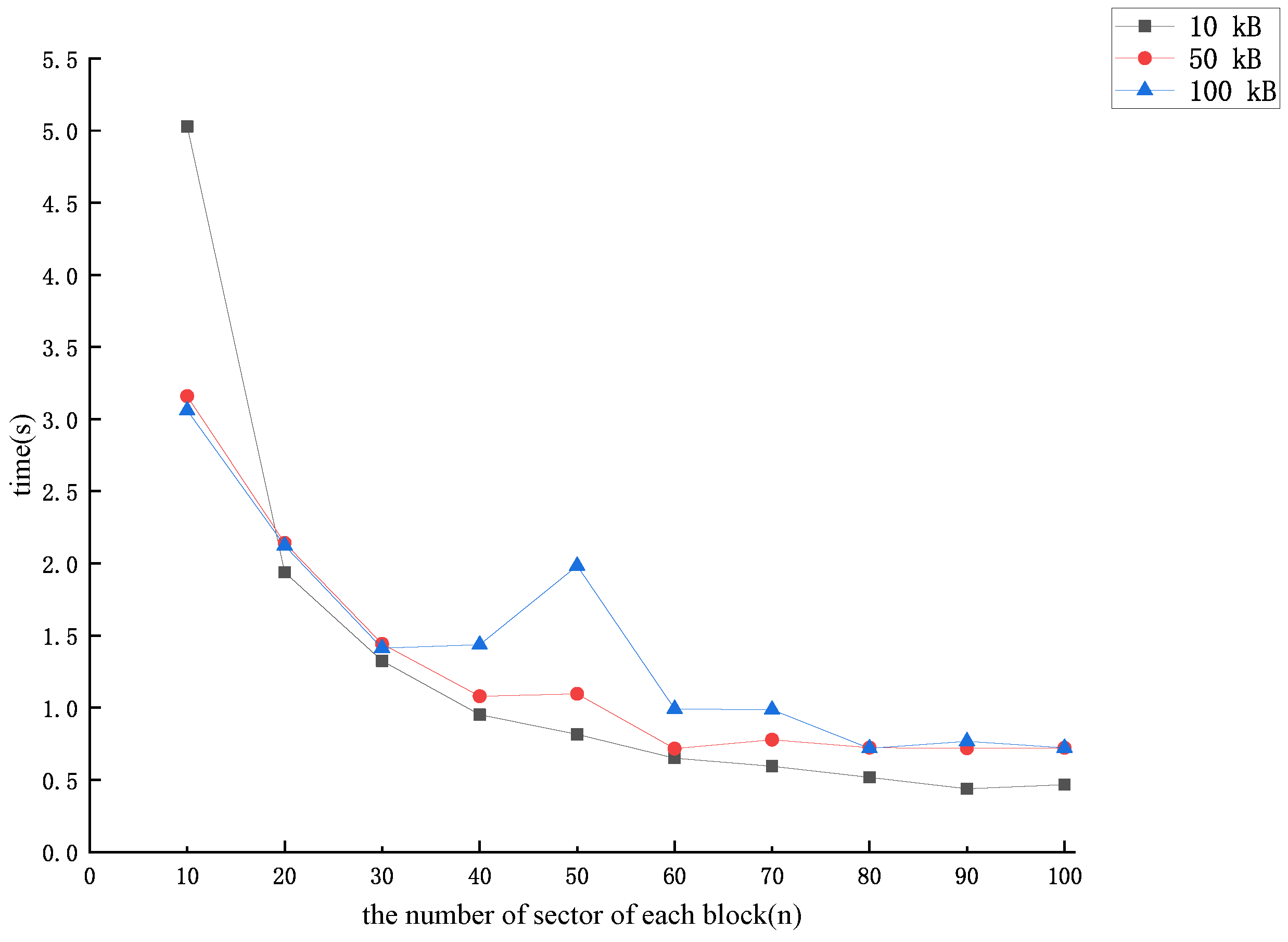
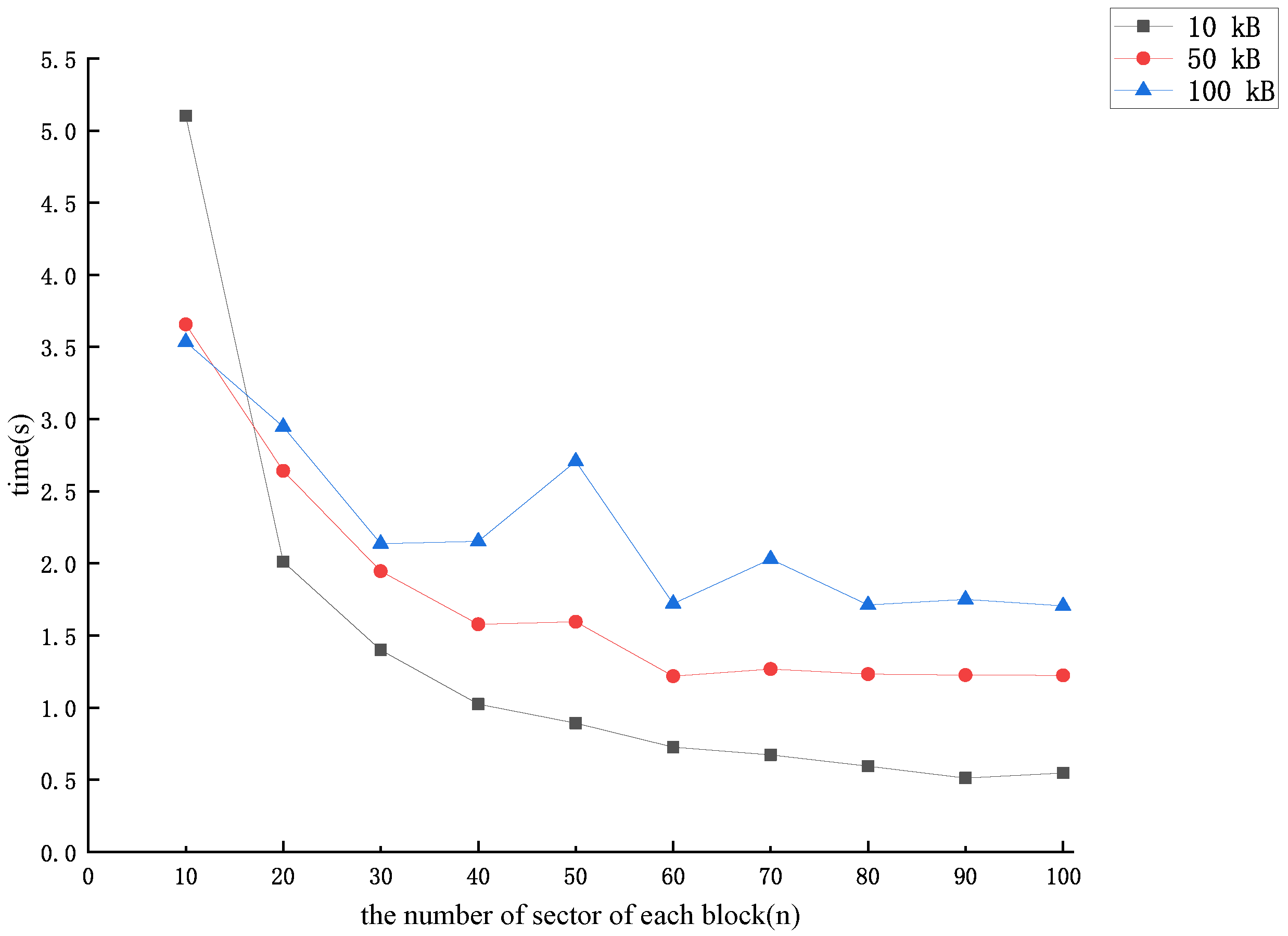
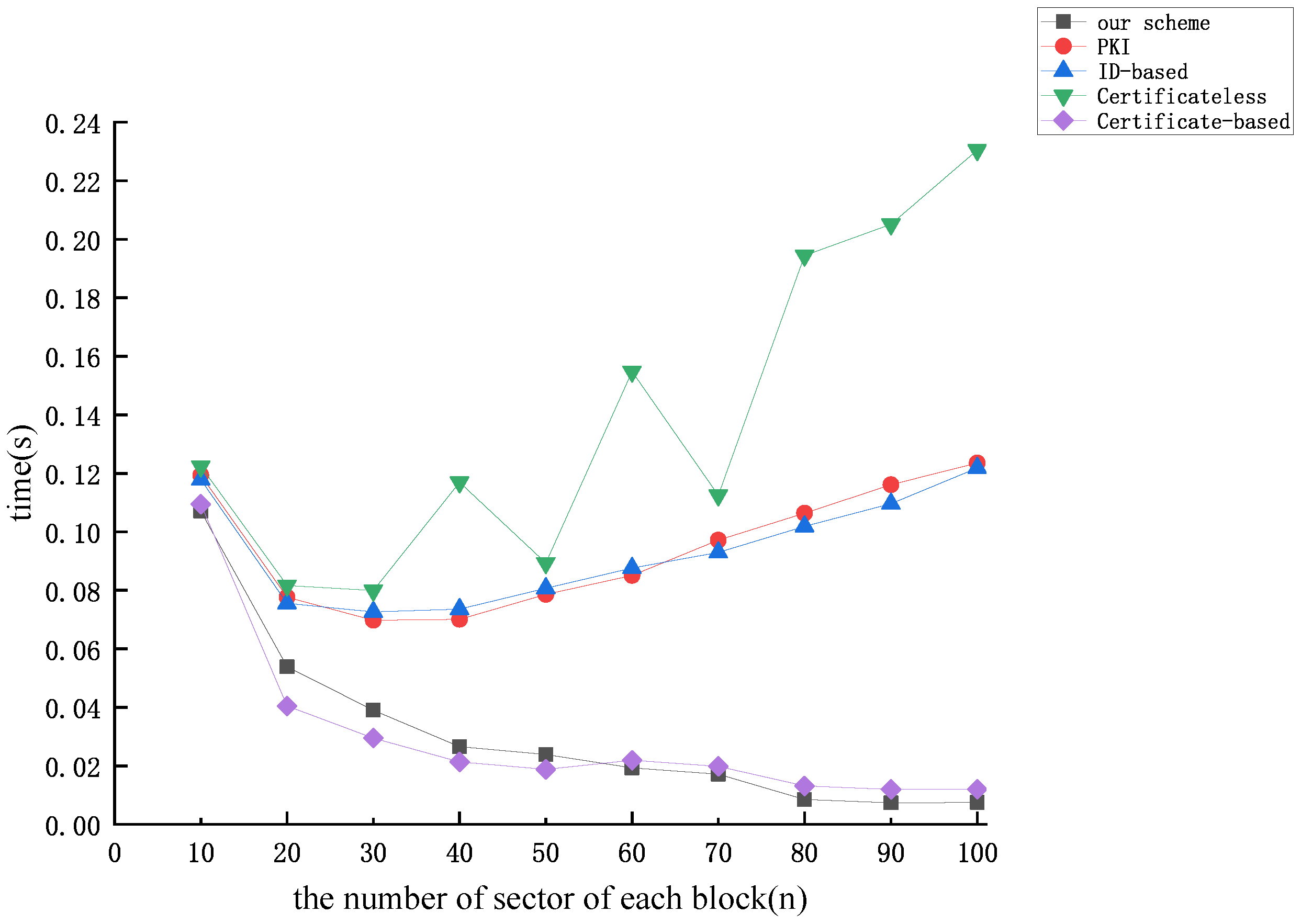
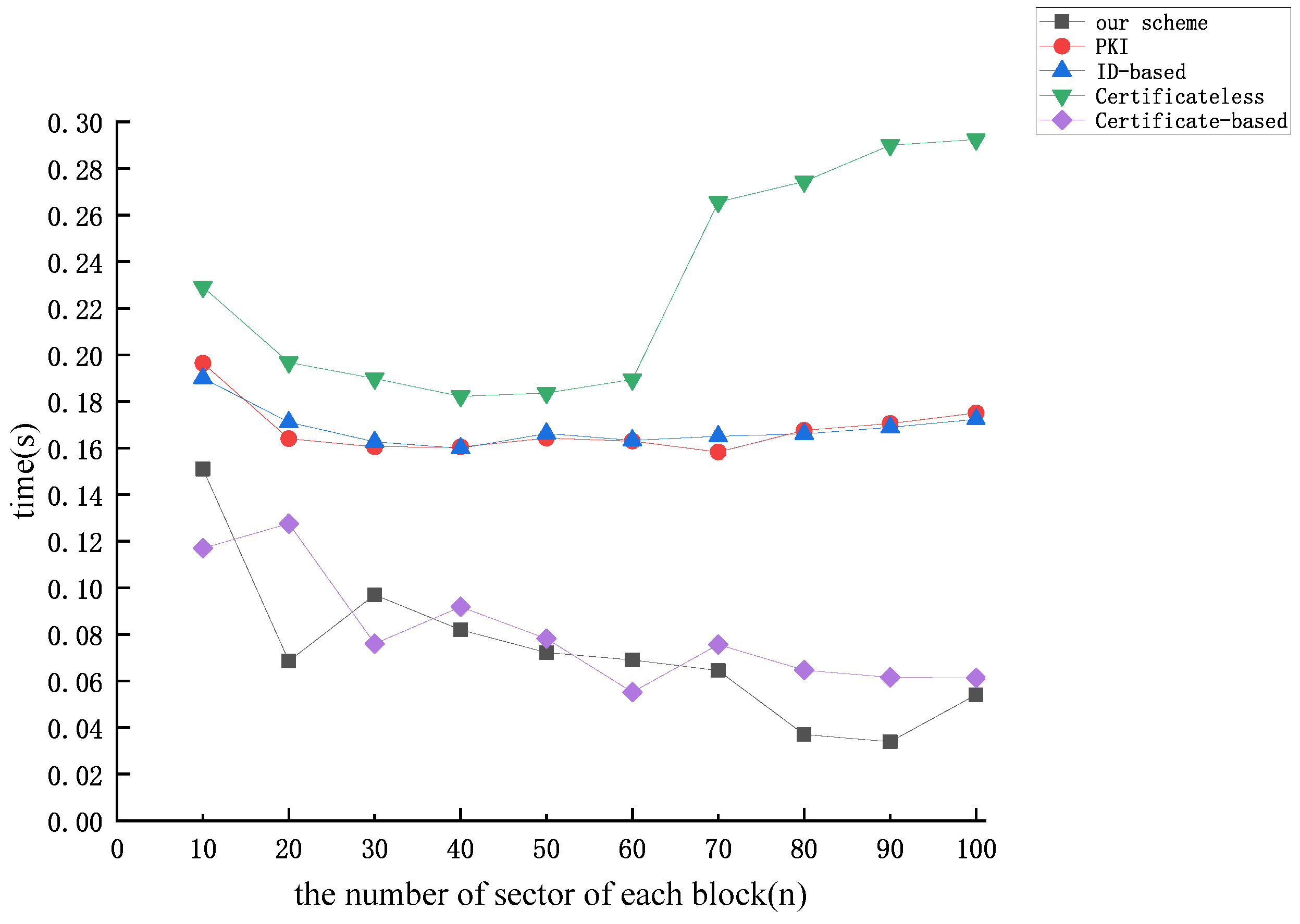
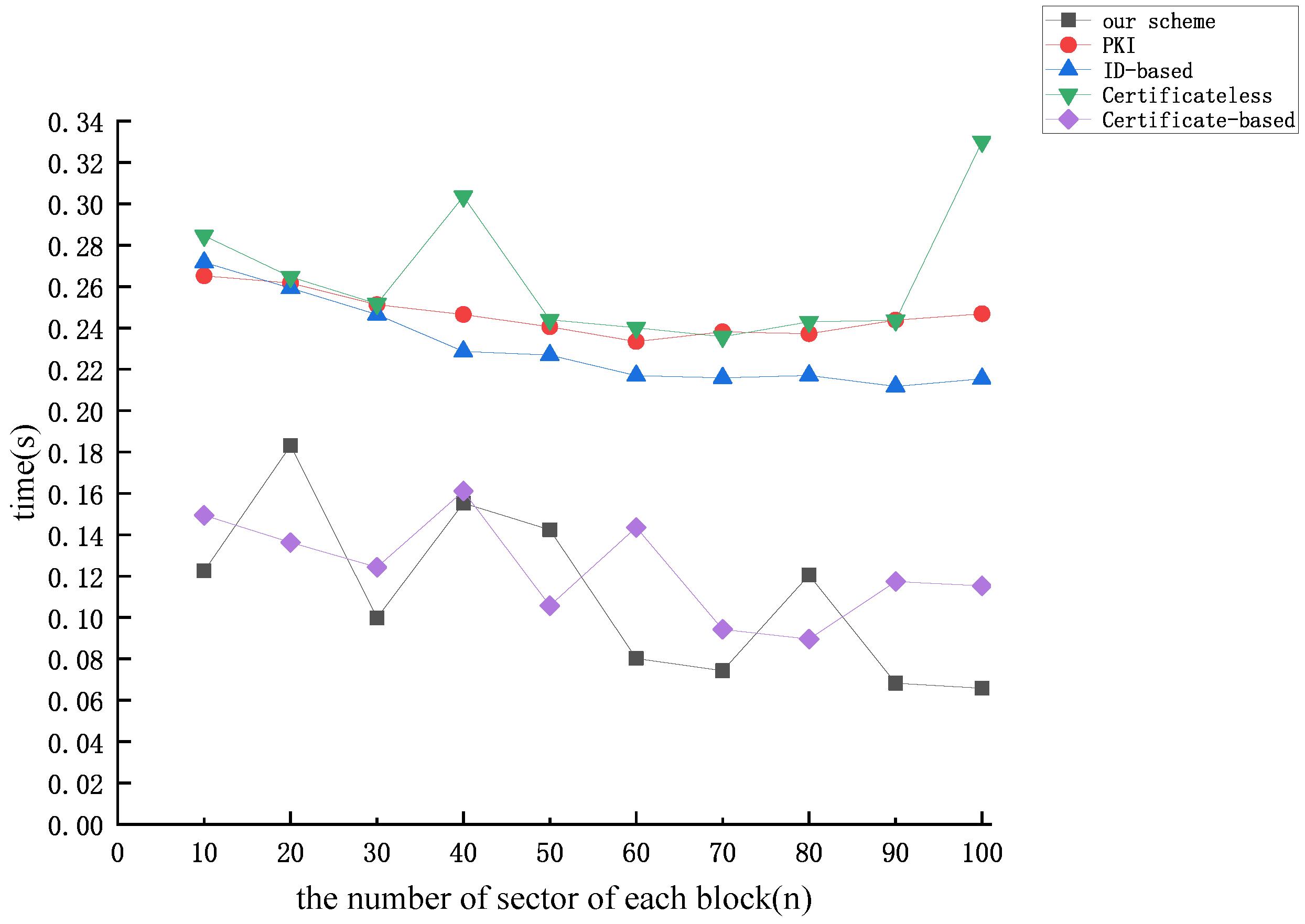
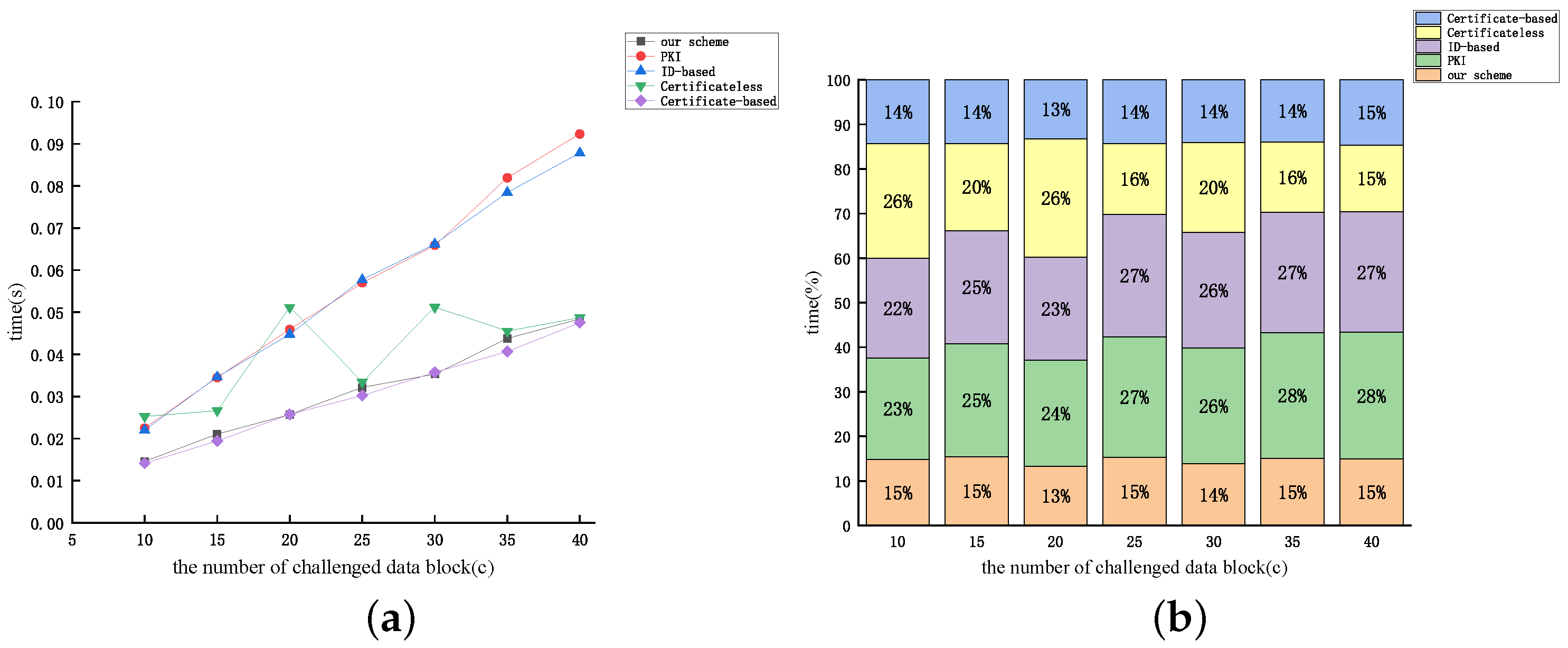
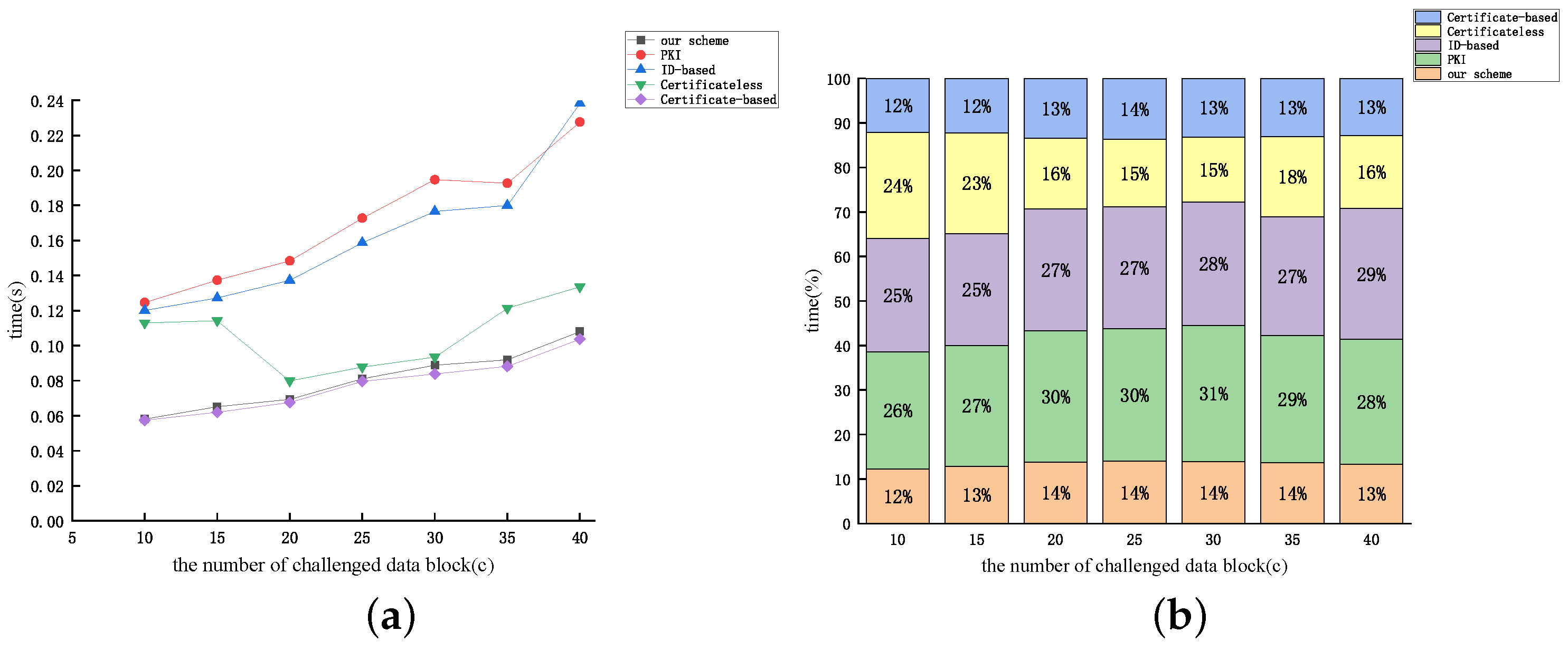
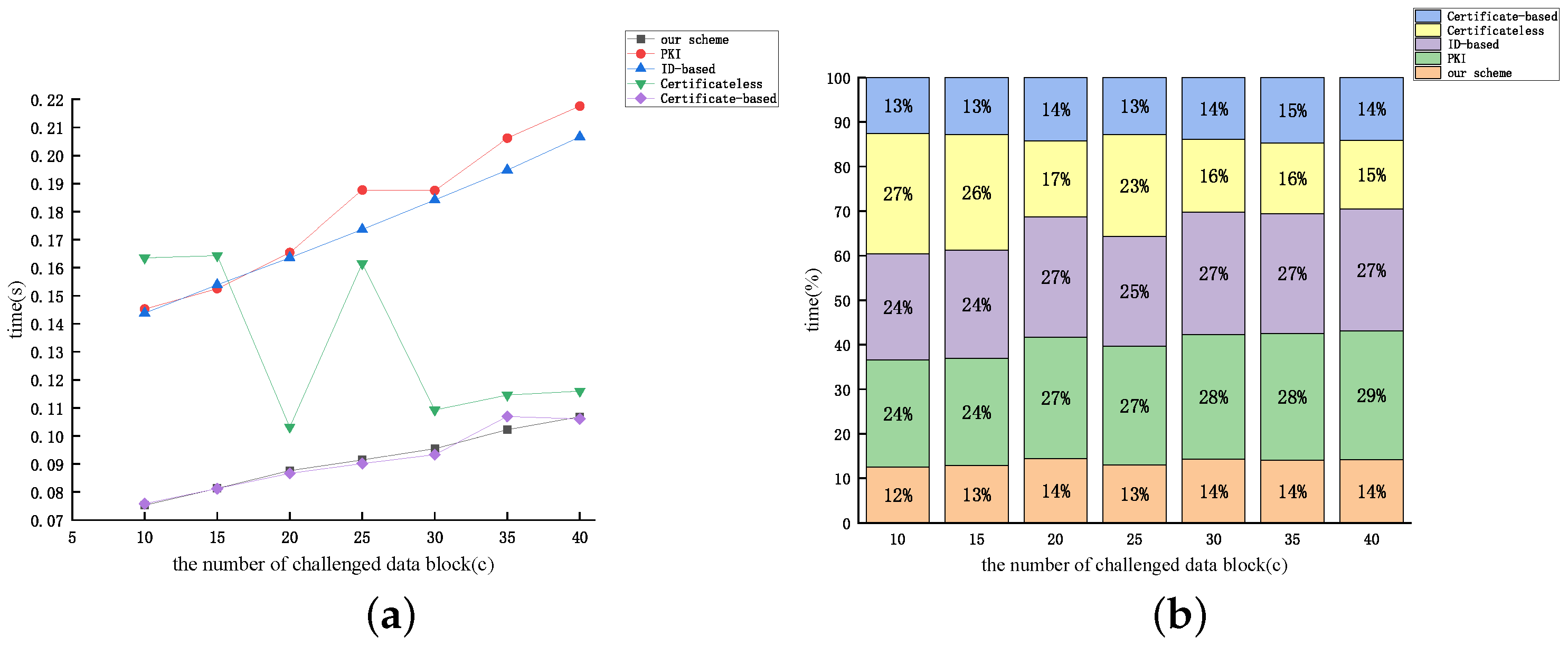
5. Performance Analysis
5.1. Analysis of Theoretical Effectiveness
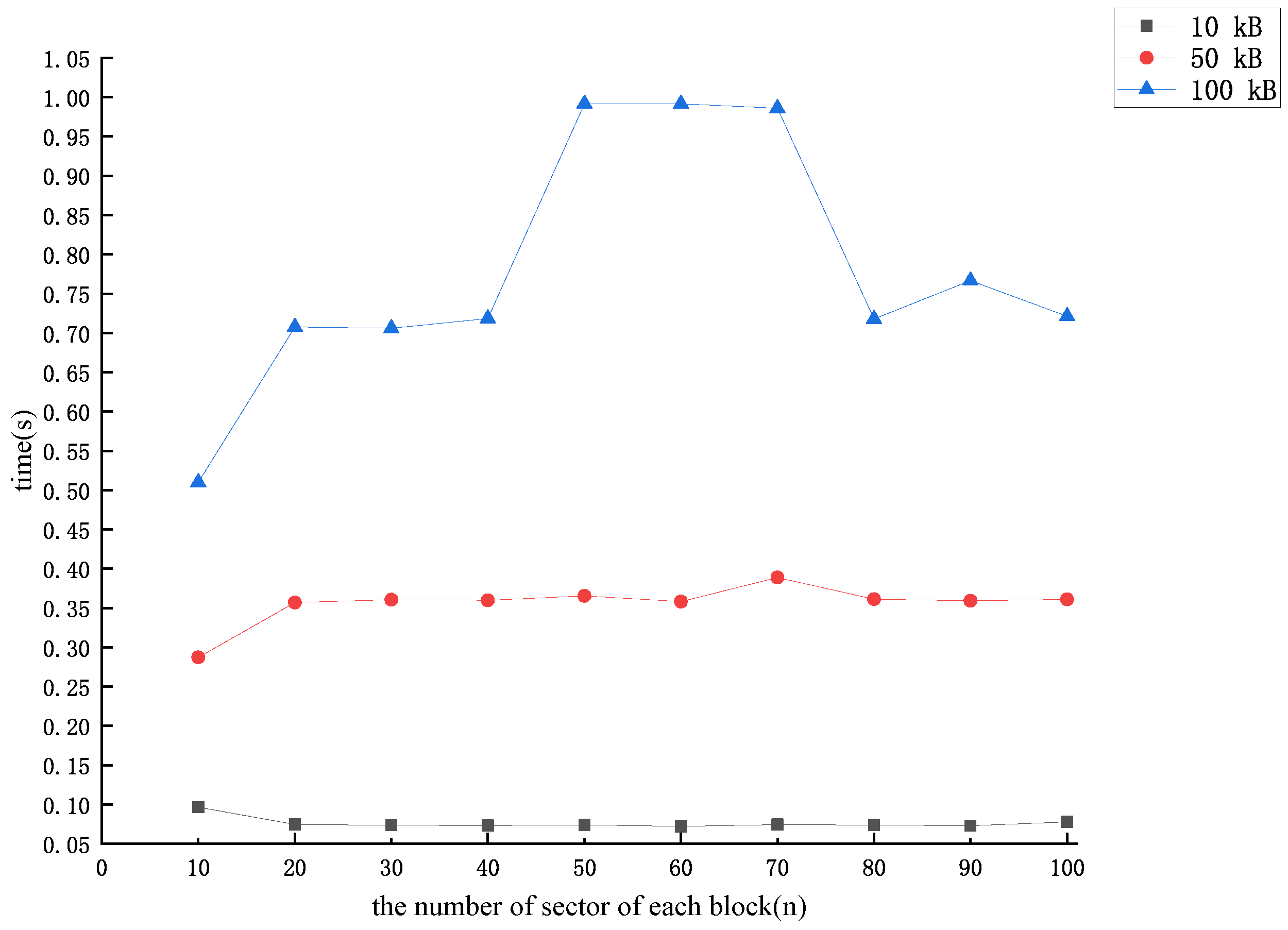
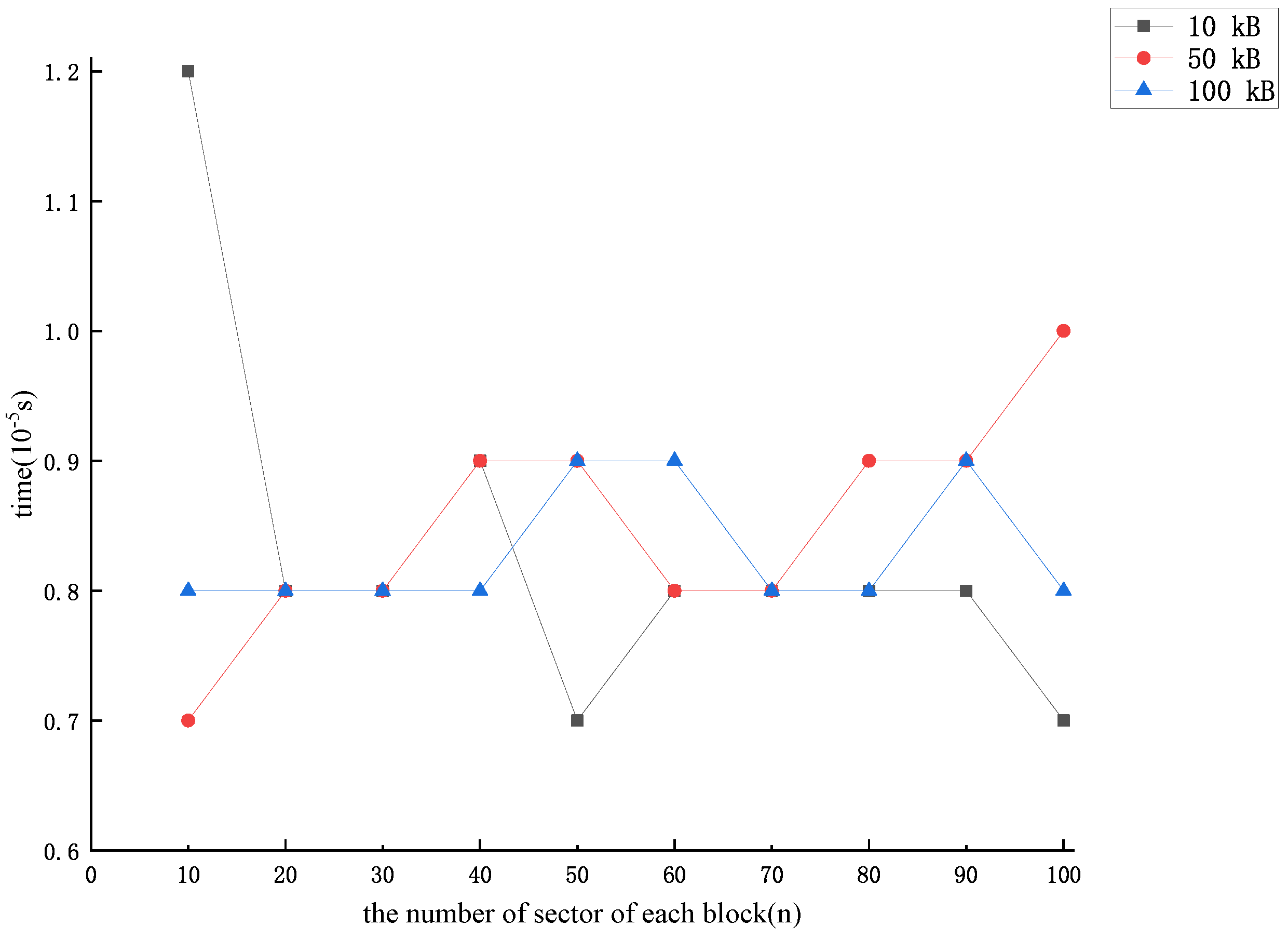
5.2. Analysis of Experimental Simulations
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
- Initialize: sets and creates a list of public parameters . Then, gives public parameters .
- Random oracle queries: randomly chooses and assumes denotes the tth time query to the oracle. responds to the query from as follows:
- (1)
- : maintains an initially empty list ; is used to store the following triples . If queries in , returns to . Otherwise, performs the following steps. If , randomly chooses and computes . Then, returns to and stores in . If , terminates the query.
- (2)
- : when received a new pair for (it can be any ID already in ), and holds, stores in .
- (3)
- maintains an initially empty list ; is used to store the following triples . If queries in , returns to . Otherwise, performs the following steps. If , randomly chooses and sets . If , sets . Then, returns to and stores in .
- (4)
- maintains an initially empty list ; is used to store the following binary group . If queries in , returns to . Otherwise, performs the following steps. If , sets . Then, returns to and stores in . If , terminates the query.
- (5)
- : If or , terminates the query. Otherwise, sends to from .
- (6)
- maintains an initially empty list ; is used to store the following pluralist group . If queries in , returns to . Otherwise, performs the following steps. Firstly, tosses a coin, whose . We specify that during the coin toss, . If , we randomly choose and set . If and , we randomly choose ; else, we randomly choose . Then, returns to and stores in .
- (7)
- maintains an initially empty list ; is used to store the following pluralist group . If queries in , returns to . Otherwise, randomly chooses . Then, returns to and stores in .
- (8)
- : maintains an initially empty list ; is used to store the following pluralist group . Firstly, randomly chooses an encrypted dataset with timestamp t. The dataset name is . Secondly, randomly chooses and sets . Then, performs the following steps. If , we set and . If and , we set ; else, terminates the query. Finally, sends to and stores in .
- (9)
- : maintains an initially empty list ; is used to store the following pluralist group . If queries tags in for dataset , is returned to . Otherwise, performs the following steps. If and , terminates the query; else, sets and stores in .Finally, sends to .
- (10)
- : First, generates a to . Then, generates a proof to , where . Finally, audits and sends or to .
- Forge: wins in Game A1 if the following conditions are met:
- (1)
- can forge a tuple .
- (2)
- has never queried on .
- (3)
- has never queried U on .
- (4)
- has never queried on .
- (5)
- outputs 1.
Therefore, wants to win Game A1 by constructing that satisfies the condition via Equation (A1).That is, can forge to win Game A1. - Outputs: From the above steps, it follows that can solve for by forging when satisfies the following two conditions:
- (1)
- does not terminate the query.
- (2)
- wins Game A1.
From Game A1, the following conditions need to be satisfied simultaneously to fulfill Condition (1):- (1)
- The probability that does not terminate the is minimized as .
- (2)
- The probability that does not terminate the is minimized as .
- (3)
- The probability that does not terminate the is minimized as .
- (4)
- The probability that does not terminate the is minimized as .
- (5)
- The probability that does not terminate the is minimized as .
From Game A1, the following conditions need to be satisfied simultaneously to fulfill Condition (2):- (1)
- In the , can ask within the number of queries, whose probability is minimized to .
- (2)
- In the , can ask within the number of queries, whose probability is minimized to .
Appendix B
- Initialize: randomly chooses , sets , and creates a list of public parameters . Then, gives public parameters and s.
- Random oracle queries: randomly chooses and assumes denotes the tth time query to the oracle. responds to the query from as follows:
- (1)
- : maintains an initially empty list , is used to store the following triples . If queries in , returns to . Otherwise, performs the following steps. If , randomly chooses , and computes . And then, returns to and stores in . If , terminate the query.
- (2)
- maintains an initially empty list ; is used to store the following triples . If queries in , returns to . Otherwise, randomly chooses and sets . Then, returns to and stores in .
- (3)
- : If or , terminates the query. Otherwise, sends to from
- (4)
- maintains an initially empty list ; is used to store the following pluralist group . If queries in , returns to . Otherwise, performs the following steps. First, tosses a coin, whose . We specify that during the coin toss, . If , we randomly choose and set . If and , we randomly choose ; else, we randomly choose . Then, returns to and stores in .
- (5)
- maintains an initially empty list ; is used to store the following pluralist group . If queries in , returns to . Otherwise, randomly chooses . Then, returns to and stores in .
- (6)
- : maintains an initially empty list ; is used to store the following pluralist group . Firstly, randomly chooses encrypted dataset with timestamp t. The dataset name is . Secondly, randomly chooses , and sets . Then, performs the following steps. If , we set and set . If and , we set , else terminates the query. Finally, sends to and stores in .
- (7)
- : maintains an initially empty list ; is used to store the following pluralist group . If queries tags in for dataset , it returns to . Otherwise, performs the following steps. If and , terminates the query; else, sets and stores in .Finally, sends to .
- (8)
- : First, generates a to . Then, generates a proof to , where . Finally, audits and sends 0 or 1 to .
- Forge: For to win in Game A2, the following conditions need to be met.
- (1)
- can forge a tuple .
- (2)
- has never queried on .
- (3)
- has never queried U on .
- (4)
- has never queried on .
- (5)
- outputs 1.
Therefore, wants to win Game A2 by constructing that satisfies the condition via Equation (A2).That is, can forge to win Game A2. - Outputs: From the above steps, it follows that can solve for by forging when satisfies the following two conditions:
- (1)
- does not terminate the query.
- (2)
- wins Game A2.
From Game A2, the following conditions need to be satisfied simultaneously to fulfill Condition (1):- (1)
- The probability that does not terminate the is minimized as .
- (2)
- The probability that does not terminate the is minimized as .
- (3)
- The probability that does not terminate the is minimized as .
- (4)
- The probability that does not terminate the is minimized as .
From Game A2, the following conditions need to be satisfied simultaneously to fulfill Condition (2):- (1)
- In the , can ask within the number of queries, whose probability is minimized to .
- (2)
- In the , can ask within the number of queries, whose probability is minimized to .
Appendix C
- Initialize: sets and creates a list of public parameters . Then, gives public parameters .
- Random oracle queries: randomly chooses and assumes denotes the tth time query to the oracle. responds to the query from as follows:
- (1)
- : maintains an initially empty list ; is used to store the following triples . If queries in , returns to . Otherwise, performs the following steps. If , randomly chooses , and computes . Then, returns to and stores in . If , terminates the query.
- (2)
- : If queries in , returns to . Otherwise, performs the following steps.
- (1)
- If , randomly chooses , sets and , and then returns , to . stores in .
- (2)
- If , sets , and . Then, stores in and terminates the query.
- (3)
- : If queries in , returns it to . Otherwise, randomly chooses and performs the following steps:
- (1)
- If , sets andthen returns to . stores in .
- (2)
- If , tosses a coin, whose . We specify that during the coin toss, , and we terminate the query if and only if . When , we set . When , we set . Then, returns to and stores in .
- (4)
- : If queries U in , returns U to . Otherwise, performs the following steps:
- (1)
- If , performs the following steps. Firstly, extracts from ; if it does not exist, C extracts after executing the . Secondly, extracts from ; if not present, extracts after executing the . Then, extracts from ; if not present, extracts after executing the . Finally, calculates and stores in .
- (2)
- If , tosses a coin, whose . We specify that during the coin toss, . When , we set and terminate the query. When , extracts from ; if not present, extracts after executing . Then, extracts from ; if not present, extracts after executing . Finally, sets and stores in .
- (5)
- : If queries in , returnsit to . Otherwise, performs the following steps. randomly chooses and sets . Then, stores in and returns to .
- (6)
- : If queries in , returnsit to . Otherwise, performs the following steps. Firstly, randomly chooses and sets . Secondly, extracts from ; if it does not exist, executes the and then extracts . Thirdly, extracts r from ; if not present, extracts r after executing the . Then, looks at the corresponding coin value, and when , calculates and stores in . When , calculates and stores in . Finally, sends to .
- Auditing: We suppose that can forge for by the above steps and can pass the challenge of .
- (1)
- constructs by calculating Equation (A3).That is, can forge to pass the check.
- (2)
- derives for by calculating the following equation.
- (1)
- If , , that is, can forge = to pass the check.
- (2)
- If , , that is, can forge = to pass the check.
- Outputs: From the above steps, it follows that can solve for by forging when satisfies the following two conditions:
- (1)
- does not terminate the query.
- (2)
- wins Game A3.
From Game A3, the following conditions need to be satisfied simultaneously to fulfill Condition (1):- (1)
- The probability that does not terminate the is minimized as .
- (2)
- The probability that does not terminate the is minimized as .
- (3)
- The probability that does not terminate the is minimized as .
From Game A3, the following conditions need to be satisfied simultaneously to fulfill Condition (2):- (1)
- In the , can ask within the number of queries, whose probability is minimized to .
- (2)
- In the , can ask within the number of queries, whose probability is minimized to .
References
- Kim, H.; Rigo, B.; Wong, G.; Lee, Y.J.; Yeo, W.H. Advances in Wireless, Batteryless, Implantable Electronics for Real-Time, Continuous Physiological Monitoring. Nano-Micro Lett. 2023, 16, 52. [Google Scholar] [CrossRef] [PubMed]
- Microsoft/SEAL. Microsoft. 2024. Available online: https://github.com/microsoft/SEAL (accessed on 18 April 2024).
- Di Matteo, S.; Gerfo, M.L.; Saponara, S. VLSI Design and FPGA Implementation of an NTT Hardware Accelerator for Homomorphic SEAL-Embedded Library. IEEE Access 2023, 11, 72498–72508. [Google Scholar] [CrossRef]
- Homenc/HElib. Homenc. 2024. Available online: https://github.com/homenc/HElib (accessed on 15 March 2024).
- PALISADE Homomorphic Encryption Software Library—An Open-Source Lattice Crypto Software Library. Available online: https://palisade-crypto.org/ (accessed on 15 March 2024).
- Deswarte, Y.; Quisquater, J.J.; Saïdane, A. Remote Integrity Checking. In Integrity and Internal Control in Information Systems VI, Proceedings of the IFIP TC11/WG11.5 Sixth Working Conference on Integrity and Internal Control in Information Systems (IICIS), Lausanne, Switzerland, 13–14 November 2003; Jajodia, S., Strous, L., Eds.; Springer: Boston, MA, USA, 2004; pp. 1–11. [Google Scholar] [CrossRef]
- Oprea, A.; Reiter, M. Space-Efficient Block Storage Integrity. In Proceedings of the Network and Distributed System Security Symposium, NDSS 2005, San Diego, CA, USA, 1 January 2005. [Google Scholar]
- Schwarz, T.; Miller, E. Store, Forget, and Check: Using Algebraic Signatures to Check Remotely Administered Storage. In Proceedings of the 26th IEEE International Conference on Distributed Computing Systems (ICDCS’06), Lisboa, Portugal, 4–7 July 2006; p. 12. [Google Scholar] [CrossRef]
- Ateniese, G.; Burns, R.; Curtmola, R.; Herring, J.; Kissner, L.; Peterson, Z.; Song, D. Provable Data Possession at Untrusted Stores. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 31 October–2 November 2007; pp. 598–609. [Google Scholar] [CrossRef]
- Shacham, H.; Waters, B. Compact Proofs of Retrievability. In Proceedings of the Advances in Cryptology—ASIACRYPT 2008, Melbourne, Australia, 7–11 December 2008; Pieprzyk, J., Ed.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 90–107. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short Signatures from the Weil Pairing. J. Cryptol. 2004, 17, 297–319. [Google Scholar] [CrossRef]
- Armknecht, F.; Bohli, J.M.; Karame, G.; Li, W. Outsourcing Proofs of Retrievability. IEEE Trans. Cloud Comput. 2018, 9, 286–301. [Google Scholar] [CrossRef]
- Bowers, K.D.; Juels, A.; Oprea, A. Proofs of Retrievability: Theory and Implementation. In Proceedings of the 2009 ACM Workshop on Cloud Computing Security, Chicago, IL, USA, 13 November 2009; CCSW’09. pp. 43–54. [Google Scholar] [CrossRef]
- Cash, D.; Küpçü, A.; Wichs, D. Dynamic Proofs of Retrievability Via Oblivious RAM. J. Cryptol. 2017, 30, 22–57. [Google Scholar] [CrossRef]
- Cui, H.; Wan, Z.; Gao, R.; Wang, H. Outsourced Privately Verifiable Proofs of Retrievability Via Blockchain. IEEE Trans. Dependable Secur. Comput. 2023, 1–18. [Google Scholar] [CrossRef]
- Hao, Z.; Zhong, S.; Yu, N. A Privacy-Preserving Remote Data Integrity Checking Protocol with Data Dynamics and Public Verifiability. IEEE Trans. Knowl. Data Eng. 2011, 23, 1432–1437. [Google Scholar] [CrossRef]
- Nayak, S.K.; Tripathy, S. SEPDP: Secure and Efficient Privacy Preserving Provable Data Possession in Cloud Storage. IEEE Trans. Serv. Comput. 2018, 14, 876–888. [Google Scholar] [CrossRef]
- Wang, H. Proxy Provable Data Possession in Public Clouds. IEEE Trans. Serv. Comput. 2013, 6, 551–559. [Google Scholar] [CrossRef]
- Wang, Q.; Wang, C.; Ren, K.; Lou, W.; Li, J. Enabling Public Auditability and Data Dynamics for Storage Security in Cloud Computing. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 847–859. [Google Scholar] [CrossRef]
- Xiong, L.; Goryczka, S.; Sunderam, V. Adaptive, Secure, and Scalable Distributed Data Outsourcing: A Vision Paper. In Proceedings of the 2011 Workshop on Dynamic Distributed Data-Intensive Applications, Programming Abstractions, and Systems, San Jose, CA, USA, 8 June 2011; 3DAPAS ’11. pp. 1–6. [Google Scholar] [CrossRef]
- Zhang, X.; Zhao, J.; Xu, C.; Li, H.; Wang, H.; Zhang, Y. CIPPPA: Conditional Identity Privacy-Preserving Public Auditing for Cloud-Based WBANs against Malicious Auditors. IEEE Trans. Cloud Comput. 2019, 9, 1362–1375. [Google Scholar] [CrossRef]
- Zheng, Q.; Xu, S. Fair and Dynamic Proofs of Retrievability. In Proceedings of the First ACM Conference on Data and Application Security and Privacy, San Antonio, TX, USA, 21–23 February 2011; CODASPY’11. pp. 237–248. [Google Scholar] [CrossRef]
- Zhu, Y.; Hu, H.; Ahn, G.J.; Yu, M. Cooperative Provable Data Possession for Integrity Verification in Multicloud Storage. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 2231–2244. [Google Scholar] [CrossRef]
- Zhu, Y.; Hu, H.; Ahn, G.J.; Han, Y.; Chen, S. Collaborative Integrity Verification in Hybrid Clouds. In Proceedings of the 7th International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom), Orlando, FL, USA, 15–18 October 2011; pp. 191–200. [Google Scholar]
- Zhu, Y.; Wang, H.; Hu, Z.; Ahn, G.J.; Hu, H.; Yau, S.S. Efficient Provable Data Possession for Hybrid Clouds. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; CCS’10. pp. 756–758. [Google Scholar] [CrossRef]
- Han, J.; Li, Y.; Yu, Y.; Ding, Y. Cloud Auditing Scheme with Dynamic Revocation of Users and Real-Time Updates of Data. J. Softw. 2020, 31, 578–596. [Google Scholar] [CrossRef]
- Diffie, W. New Directions in Cryptography. IEEE Trans. Inf. Theory 1976, IT-22, 644–654. [Google Scholar] [CrossRef]
- Chang, J.; Shao, B.; Ji, Y.; Bian, G. Efficient Identity-Based Provable Multi-Copy Data Possession in Multi-Cloud Storage, Revisited. IEEE Commun. Lett. 2020, 24, 2723–2727. [Google Scholar] [CrossRef]
- Chen, D.; Yuan, H.; Hu, S.; Wang, Q.; Wang, C. BOSSA: A Decentralized System for Proofs of Data Retrievability and Replication. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 786–798. [Google Scholar] [CrossRef]
- Li, J.; Yan, H.; Zhang, Y. Efficient Identity-Based Provable Multi-Copy Data Possession in Multi-Cloud Storage. IEEE Trans. Cloud Comput. 2022, 10, 356–365. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Yu, Y.; Yang, T. Identity-Based Provable Data Possession From RSA Assumption for Secure Cloud Storage. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1753–1769. [Google Scholar] [CrossRef]
- Shen, W.; Qin, J.; Yu, J.; Hao, R.; Hu, J. Enabling Identity-Based Integrity Auditing and Data Sharing With Sensitive Information Hiding for Secure Cloud Storage. IEEE Trans. Inf. Forensics Secur. 2018, 14, 331–346. [Google Scholar] [CrossRef]
- Wang, H.; He, D.; Tang, S. Identity-Based Proxy-Oriented Data Uploading and Remote Data Integrity Checking in Public Cloud. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1165–1176. [Google Scholar] [CrossRef]
- Wang, H. Identity-Based Distributed Provable Data Possession in Multicloud Storage. IEEE Trans. Serv. Comput. 2015, 8, 328–340. [Google Scholar] [CrossRef]
- Wang, H.; He, D.; Yu, J.; Wang, Z. Incentive and Unconditionally Anonymous Identity-Based Public Provable Data Possession. IEEE Trans. Serv. Comput. 2019, 12, 824–835. [Google Scholar] [CrossRef]
- Wang, H.; Wu, Q.; Qin, B.; Domingo-Ferrer, J. Identity-Based Remote Data Possession Checking in Public Clouds. IET Inf. Secur. 2014, 8, 114–121. [Google Scholar] [CrossRef]
- Wang, Y.; Wu, Q.; Qin, B.; Shi, W.; Deng, R.H.; Hu, J. Identity-Based Data Outsourcing with Comprehensive Auditing in Clouds. IEEE Trans. Inf. Forensics Secur. 2016, 12, 940–952. [Google Scholar] [CrossRef]
- Yang, Y.; Chen, Y.; Chen, F.; Chen, J. An Efficient Identity-Based Provable Data Possession Protocol with Compressed Cloud Storage. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1359–1371. [Google Scholar] [CrossRef]
- Yu, Y.; Au, M.H.; Ateniese, G.; Huang, X.; Susilo, W.; Dai, Y.; Min, G. Identity-Based Remote Data Integrity Checking with Perfect Data Privacy Preserving for Cloud Storage. IEEE Trans. Inf. Forensics Secur. 2016, 12, 767–778. [Google Scholar] [CrossRef]
- Zhang, Y.; Yu, J.; Hao, R.; Wang, C.; Ren, K. Enabling Efficient User Revocation in Identity-Based Cloud Storage Auditing for Shared Big Data. IEEE Trans. Dependable Secur. Comput. 2018, 17, 608–619. [Google Scholar] [CrossRef]
- Pang, X.; Wang, T.; Chen, W.; Ren, M. Batch Provable Data Possession Scheme with Error Locating. J. Softw. 2018, 30, 362–380. [Google Scholar] [CrossRef]
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. In Advances in Cryptology; Blakley, G.R., Chaum, D., Eds.; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53. [Google Scholar] [CrossRef]
- Deng, L.; Chen, Z.; Ruan, Y.; Zhou, H.; Li, S. Certificateless Provable Data Possession Scheme Suitable for Smart Grid Management Systems. IEEE Syst. J. 2023, 17, 4245–4256. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Zeadally, S.; Wang, H. Certificateless Provable Data Possession Scheme for Cloud-Based Smart Grid Data Management Systems. IEEE Trans. Ind. Inform. 2017, 14, 1232–1241. [Google Scholar] [CrossRef]
- Li, J.; Yan, H.; Zhang, Y. Certificateless Public Integrity Checking of Group Shared Data on Cloud Storage. IEEE Trans. Serv. Comput. 2018, 14, 71–81. [Google Scholar] [CrossRef]
- Shen, J.; Zeng, P.; Choo, K.K.R.; Li, C. A Certificateless Provable Data Possession Scheme for Cloud-Based EHRs. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1156–1168. [Google Scholar] [CrossRef]
- Wang, B.; Li, B.; Li, H.; Li, F. Certificateless Public Auditing for Data Integrity in the Cloud. In Proceedings of the 2013 IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 136–144. [Google Scholar] [CrossRef]
- Zhou, L.; Fu, A.; Yang, G.; Wang, H.; Zhang, Y. Efficient Certificateless Multi-Copy Integrity Auditing Scheme Supporting Data Dynamics. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1118–1132. [Google Scholar] [CrossRef]
- Al-Riyami, S.S.; Paterson, K.G. Certificateless Public Key Cryptography. In Advances in Cryptology—ASIACRYPT 2003; Laih, C.S., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar] [CrossRef]
- Gentry, C. Certificate-Based Encryption and the Certificate Revocation Problem. In Advances in Cryptology—EUROCRYPT 2003; Biham, E., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; pp. 272–293. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, F. An Efficient Certificate-Based Data Integrity Auditing Protocol for Cloud-Assisted WBANs. IEEE Internet Things J. 2022, 9, 11513–11523. [Google Scholar] [CrossRef]
- Milnor, J.W.; Husemoller, D. Symmetric Bilinear Forms; Springer: Berlin/Heidelberg, Germany, 1973; Volume 73. [Google Scholar] [CrossRef]
- Mitsunari, S.; Sakai, R.; Kasahara, M. A New Traitor Tracing. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2002, 85, 481–484. [Google Scholar]
- Liu, J.K.; Bao, F.; Zhou, J. Short and Efficient Certificate-Based Signature. In NETWORKING 2011 Workshops; Casares-Giner, V., Manzoni, P., Pont, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 167–178. [Google Scholar] [CrossRef]
- Wang, C.; Chow, S.S.; Wang, Q.; Ren, K.; Lou, W. Privacy-Preserving Public Auditing for Secure Cloud Storage. IEEE Trans. Comput. 2013, 62, 362–375. [Google Scholar] [CrossRef]
- Maas, M. Pairing-Based Cryptography. Master’s Thesis, Technische Universiteit Eindhoven, Department of Mathematics and Computing Science, Eindhoven, The Netherlands, 2004. [Google Scholar]
| Notation | Meaning |
|---|---|
| Multiplication operations on the group | |
| Multiplication operations on the group | |
| Multiplication operations on the domain | |
| Exponential operations on the group | |
| Exponential operations on the group | |
| Exponential operations on the domain | |
| Mapping to the hash operation on the group | |
| Mapping to the hash operation on the domain | |
| Bilinear pairing operation | |
| m | Number of data blocks |
| n | Number of sectors for each data block |
| c | Number of audit challenges |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, Y.; Zhou, X.; Zhou, T.; Zhong, W.; Li, R.; Yang, X. A Secure Certificate-Based Data Integrity Auditing Protocol with Cloud Service Providers. Mathematics 2024, 12, 1964. https://doi.org/10.3390/math12131964
Tian Y, Zhou X, Zhou T, Zhong W, Li R, Yang X. A Secure Certificate-Based Data Integrity Auditing Protocol with Cloud Service Providers. Mathematics. 2024; 12(13):1964. https://doi.org/10.3390/math12131964
Chicago/Turabian StyleTian, Yuan, Xuan Zhou, Tanping Zhou, Weidong Zhong, Ruifeng Li, and Xiaoyuan Yang. 2024. "A Secure Certificate-Based Data Integrity Auditing Protocol with Cloud Service Providers" Mathematics 12, no. 13: 1964. https://doi.org/10.3390/math12131964
APA StyleTian, Y., Zhou, X., Zhou, T., Zhong, W., Li, R., & Yang, X. (2024). A Secure Certificate-Based Data Integrity Auditing Protocol with Cloud Service Providers. Mathematics, 12(13), 1964. https://doi.org/10.3390/math12131964






