Abstract
The efficiency with which an integer may be factored into its prime factors determines several public key cryptosystems’ security in use today. Although there is a quantum-based technique with a polynomial time for integer factoring, on a traditional computer, there is no polynomial time algorithm. We investigate how to enhance the wheel factoring technique in this paper. Current wheel factorization algorithms rely on a very restricted set of prime integers as a base. In this study, we intend to adapt this notion to rely on a greater number of prime integers, resulting in a considerable improvement in the execution time. The experiments on composite numbers n reveal that the proposed algorithm improves on the existing wheel factoring algorithm by about .
MSC:
11A41; 11A51
1. Introduction
The complexity of the integer factorization issue affects the security of several public key cryptosystems, such as [1,2,3,4,5], while the exponentiation problem determines the effectiveness of such cryptosystems [6,7,8].
Algorithms for factoring a big odd composite number fall into two broad kinds, called special-purpose and general-purpose algorithms [9,10,11,12,13,14,15,16,17,18]. The special-purpose factoring algorithms [10,19] find tiny prime factors rapidly, regardless of the value of n. If n has no tiny factors, employing one of the special-purpose factoring algorithms will almost certainly fail, which is the primary issue with them. Examples of such factoring algorithms include the Fermat technique [9] with time complexity of , Pollard’s elliptic curve method, Pollard’s wheel factoring method, Pollard’s p-method with time complexity of , and Pollard’s method [20]. The general-purpose factorization techniques factor n regardless of the size of the prime factors, albeit they require exponential or subexponential time. Examples of such algorithms include the quadratic sieve with time complexity of , the continuous fraction method with time complexity of , and the number field sieve [12]. Recently, subexponential-time factoring methods utilizing binary decision and the Pisano period were proposed by Raddum, Varadharajan, and Wu [21] and Wu et al. [22], respectively. The number field sieve method with time complexity of [23,24] has been shown to be the most effective method so far for factoring big n with large prime factors.
There are more factoring techniques, but they require more knowledge of cryptosystems or specific requirements for the prime factors (see [25,26,27,28]). Utilizing high-performance computing systems, such as multicore systems [20,29,30,31], cloud computing systems [23], and graphics processing units [32,33], is one method for accelerating factoring algorithms.
In this paper, we focus on the challenge of factoring odd composite integers n. We investigate a new way to enhance the recent wheel factoring technique [34]. We expand the wheel method by using a greater number of prime integers as a basis rather than a limited number of prime integers.
The rest of the paper is organised as follows: In the second section, we provide an overview of the most important works on the subject under consideration. The proposed algorithm is presented in the third section. In the fourth section, we provide a numerical illustration of the suggested method in action. The implementation of the algorithms is presented in the fifth section. The results of the practical implementation of the algorithms are examined in the sixth section. Finally, in the final section, we summarize what we have accomplished.
2. Related Work
In this section, we present the three most important algorithms related to our research: the wheel factorization method (WFM), the forward wheel factorization method (FWFM), and the backward wheel factorization method (BWFM) [34].
2.1. Traditional Wheel Factorization Method (WFM)
In this subsection, we present a brief explanation of the WFM’s central concept as well as its pseudocode for finding two factors for a composite integer. The WFM depends on picking the first k primes, known as the basis, say , where k is a tiny number, say 3 or 4. Then, WFM creates a list T, referred to as the turn or wheel, of integers that are coprime with every number in B. The product of the basis integers equals the circumference of the wheel (also known as the primorial) . Next, The integers in the wheel/turn are used by WFM to discover the lowest divisor of the integer to be factorised. To explain how WFM works to find a factor of n, B, and the circumference of a turn is . n must be divided by 2, 3, 5, and all other numbers that are congruent to 1, 7, 11, 13, 17, 19, 23, and 29, modulo 30, until a factor is discovered or is reached. We begin by dividing n by 2, 3 and 5, and, if it is not divisible by any of them, we go to the first iteration. In the first iteration, we divide n by 7, 11, 13, 17, 19, 23, 29 and 31, and, if it is not divisible by any of them, we go to the second iteration. In the second iteration, we divide n by 37, 41, 43, 47, 49, 53, 59 and 61, and, if it is not divisible by any of them, we go to the third iteration and so on. The difference between the matching items in any two successive turns is 30. The loop ends when we find a factor of n or reach a . If we reach the without encountering a factor, then n is a prime number.
WFM does not have to begin from 1. For instance, we can start at 11, making the first turn set as follows: . In this situation, to begin, we must divide n by the elements of B and the number 7, i.e., 2, 3, 5, and 7. WFM checks whether n can be divided by the numbers in the following turn set, which are .
The first 15 turn sets when WFM starts from 11 are shown in Table 1. The initial integer of the kth turn is clearly equivalent to and the following components of the kth turn are , and . The disparities between two consecutive integers in any turn are 2, 4, 2, 4, 6, 2, and 6, respectively; however, the difference between the last number in any round and the first integer in the next turn is 4. To handle all turns, these differences can be kept in an array, say . Algorithm 1 displays the WFM pseudocode. As seen in Algorithm 2, the algorithm employs a function called FactorBasis to determine whether or not n has a factor from the basis set B.

Table 1.
The first fifteen turns of circumference 30 starting from 11.
| Algorithm 1: WFM [34] |
 |
| Algorithm 2: FactorBasis [34] |
1Input: A composite integer 2 if return 2 3 if return 3 4 if return 5 5 if return 7 6 Otherwise return 1 7Output: Either a prime number or 1. |
2.2. Forward WFM (FWFM)
In WFM, every while–loop iteration, Lines 6–17 of Algorithm 1, checks if m may be divided by the integer f. The value of f fluctuates with each turn depending on the value of , Lines 10–15. The value of is used to establish the following turn’s start.
With the FWFM, complete the while–loop in a single iteration rather than eight separate iterations for each turn. There is no reason to utilize the array inc because the idea can be accomplished by performing eight tests during every while–loop iteration. Additionally, there is no need to run the while–loop repeatedly while updating the counter i and testing its value. As a result, we can get rid of Lines 11–15 from the while–loop. Forward WFM (FWFM) is shown in Algorithm 3. FWFM tests each turn j of length 30 starting from using the subroutine TurnTest, Algorithm 4. If a factor of m is present, the function TurnTest returns it; otherwise, it returns 1. The function begins with f, the initial element of each round, and updates f by the numbers 2, 4, 2, 4, 6, 2, accordingly. Algorithms 3 and 4 present the complete pseudocodes for the FWFM and TurnTest algorithms, respectively.
2.3. Backward WFM (BWFM)
In several public-key cryptosystems, the lowest prime factor is near to , such as RSA [4], where the public modulus m is the product of two equal-sized prime numbers. Therefore, it is preferable to look for the factor between and 2. (backward direction).
is the total number of turns in the search space, counting from 11. The algorithm begins with the turn that was made at . The algorithm comes to an end if it discovers the factor of m. Otherwise, the algorithm searches in reverse order for a factor of m in the following turn by subtracting the circumference of turn 30 from i, i.e., . This process is repeated for all turns. The algorithm looks for the factors 7, 5, 3, and 2 if the iterations do not yield a factor. Algorithm 5 provides the whole pseudocode for the backward wheel factoring method (BWFM).
| Algorithm 3: Forward Wheel Factoring Method (FWFM) [34] |
 |
| Algorithm 4: TurnTest [34] |
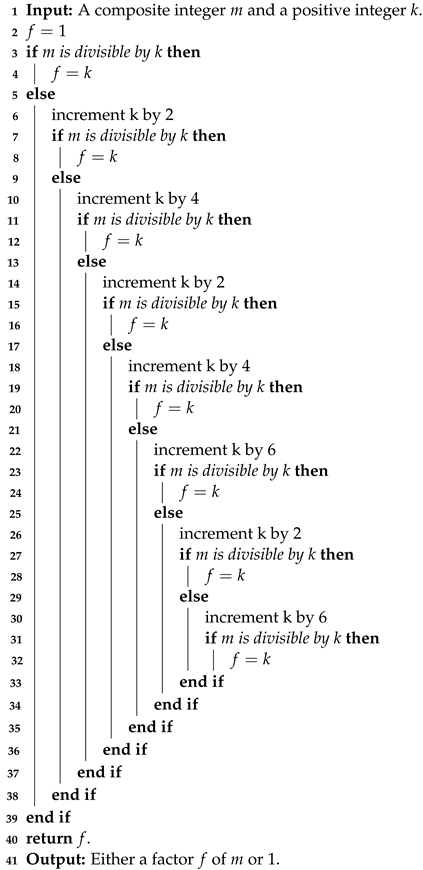 |
| Algorithm 5: Backward Wheel Factoring Method (BWFM) [34] |
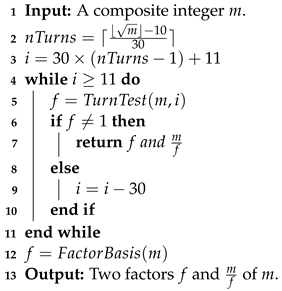 |
3. The Modified Wheel Factorization Method (MWFM)
The idea is based on the generalization of the WFM algorithm, which is based on an array of length 3 only. The main idea is to generalize the length of the array by reading of prime numbers from a file containing the first million prime numbers and storing them in the array, then calculating , which is the product of the array elements. The next step is to read all the primes up to , excluding the elements of the array, and store those elements in an array called .
Using a function called NewFactorBasis, we begin the steps of the proposed algorithm by determining whether n is divisible by any of the elements of the array. We perform several iterations with a maximum of iterations in the absence of any factor of n in the array. We test whether n is divisible by any of the array elements in each iteration. If there is no any factor of n within the array, the array elements are incremented by . This is accomplished through the use of a function known as NewTurnTest.
The full descriptions of NewFactorBasis, NewTurnTest and MWFM are shown in Algorithms 6–8.
| Algorithm 6: NewFactorBasis |
 |
| Algorithm 7: NewTurnTest |
 |
| Algorithm 8: Modified Wheel Factorization Method (MWFM) |
 |
The NewFactorBasis algorithm runs in because there are comparisons and divisions and does not depend on n. Moreover, the NewTurnTest algorithm runs in because there are l comparisons and divisions and l does not depend on n. The MWFM algorithm runs in because the while loop in line 10 performs iterations in the worst case.
4. An Example
In this section, we give two examples to show how the MWFM algorithm works. The first example is for the worst case in which n is a prime number. Let and . In line 2, four prime numbers are read and stored in B. In line 3, is computed, . In line 4, all prime numbers which are greater than 7 and up to 210 are read and stored in the array T. In addition, the actual length l of T is computed. T = {11, 13, 17, 19, 23, 29, 31, 37, 41, 43, 47, 53, 59, 61, 67, 71, 73, 79, 83, 89, 97, 101, 103, 107, 109, 113, 127, 131, 137, 139, 149, 151, 157, 163, 167, 173, 179, 181, 191, 193, 197, 199} and . In line 5, we determine whether n is divisible by any of the elements of B by calling the function NewFactorBasis. n is not divisible by any of the elements of B. So, NewFactorBasis returns 1 in Because we skip line 7 and execute from line 9. In line 9, the square root of n is computed and stored in m. In lines 10–15, we perform several iterations depending on the value of . In each iteration, the NewTurnTest function is called to determine whether n is divisible by any of the current elements of T. If any factor p is found, the algorithm will return p and as in line 12–14. If we do not find any factors, the elements of the array T will be modified by an increment of . The while loop will end when the value of exceeds .
After the first iteration, we do not find any factor of n in T and the values of the elements are modified as follows:
- T = {221, 223, 227, 229, 233, 239, 241, 247, 251, 253, 257, 263, 269, 271, 277, 281, 283, 289, 293, 299, 307, 311, 313, 317, 319, 323, 337, 341, 347, 349, 359, 361, 367, 373, 377, 383, 389, 391, 401, 403, 407, 409}.
After the second iteration, we do not find any factor of n in T and the values of the elements are modified as follows:
- T = {431, 433, 437, 439, 443, 449, 451, 457, 461, 463, 467, 473, 479, 481, 487, 491, 493, 499, 503, 509, 517, 521, 523, 527, 529, 533, 547, 551, 557, 559, 569, 571, 577, 583, 587, 593, 599, 601, 611, 613, 617, 619}.
After the third iteration, we do not find any factor of n in T and the values of the elements are modified as follows:
- T = {641, 643, 647, 649, 653, 659, 661, 667, 671, 673, 677, 683, 689, 691, 697, 701, 703, 709, 713, 719, 727, 731, 733, 737, 739, 743, 757, 761, 767, 769, 779, 781, 787, 793, 797, 803, 809, 811, 821, 823, 827, 829}.
Because the value of is still less than , another iteration will be performed and T will be modified as follows:
- T = {851, 853, 857, 859, 863, 869, 871, 877, 881, 883, 887, 893, 899, 901, 907, 911, 913, 919, 923, 929, 937, 941, 943, 947, 949, 953, 967, 971, 977, 979, 989, 991, 997, 1003, 1007, 1013, 1019, 1021, 1031, 1033, 1037, 1039}.
The condition of the while loop has been broken and we have reached line 17 and the value of p is still 1, so the algorithm will return 1 and n = 505,301.
The second example is for when n is a composite number. Let n = 912,673 and . Five prime numbers are read and stored in B. is computed, . All prime numbers which are greater than 11 and up to 2310 are read and stored in the array T. In addition, the actual length l of T is computed. T = {13, 17, 19, 23, 29, 31, 37, 41, 43, 47, 53, 59, 61, 67, 71, 73, 79, 83, 89, 97, 101, 103, 107, 109, 113, 127, 131, 137, 139, 149, 151, 157, 163, 167, 173, 179, 181, 191, 193, 197, 199, 211, 223, 227, 229, 233, 239, 241, 251, 257, 263, 269, 271, 277, 281, 283, 293, 307, 311, 313, 317, 331, 337, 347, 349, 353, 359, 367, 373, 379, 383, 389, 397, 401, 409, 419, 421, 431, 433, 439, 443, 449, 457, 461, 463, 467, 479, 487, 491, 499, 503, 509, 521, 523, 541, 547, 557, 563, 569, 571, 577, 587, 593, 599, 601, 607, 613, 617, 619, 631, 641, 643, 647, 653, 659, 661, 673, 677, 683, 691, 701, 709, 719, 727, 733, 739, 743, 751, 757, 761, 769, 773, 787, 797, 809, 811, 821, 823, 827, 829, 839, 853, 857, 859, 863, 877, 881, 883, 887, 907, 911, 919, 929, 937, 941, 947, 953, 967, 971, 977, 983, 991, 997, 1009, 1013, 1019, 1021, 1031, 1033, 1039, 1049, 1051, 1061, 1063, 1069, 1087, 1091, 1093, 1097, 1103, 1109, 1117, 1123, 1129, 1151, 1153, 1163, 1171, 1181, 1187, 1193, 1201, 1213, 1217, 1223, 1229, 1231, 1237, 1249, 1259, 1277, 1279, 1283, 1289, 1291, 1297, 1301, 1303, 1307, 1319, 1321, 1327, 1361, 1367, 1373, 1381, 1399, 1409, 1423, 1427, 1429, 1433, 1439, 1447, 1451, 1453, 1459, 1471, 1481, 1483, 1487, 1489, 1493, 1499, 1511, 1523, 1531, 1543, 1549, 1553, 1559, 1567, 1571, 1579, 1583, 1597, 1601, 1607, 1609, 1613, 1619, 1621, 1627, 1637, 1657, 1663, 1667, 1669, 1693, 1697, 1699, 1709, 1721, 1723, 1733, 1741, 1747, 1753, 1759, 1777, 1783, 1787, 1789, 1801, 1811, 1823, 1831, 1847, 1861, 1867, 1871, 1873, 1877, 1879, 1889, 1901, 1907, 1913, 1931, 1933, 1949, 1951, 1973, 1979, 1987, 1993, 1997, 1999, 2003, 2011, 2017, 2027, 2029, 2039, 2053, 2063, 2069, 2081, 2083, 2087, 2089, 2099, 2111, 2113, 2129, 2131, 2137, 2141, 2143, 2153, 2161, 2179, 2203, 2207, 2213, 2221, 2237, 2239, 2243, 2251, 2267, 2269, 2273, 2281, 2287, 2293, 2297, 2309} and . n is not divisible by any of the elements of B, but n is divisible by 97, which is an element of T, so the algorithm will return 97 and 9409.
5. Experiments
This section describes the implementation of the proposed improvement on the best-known algorithm (BWFM). It is split into two subsections. The first subsection outlines the setup of the experimental investigation, which comprises the hardware, software, and data collection. The average execution times of BWFM and MWFM are included in the second subsection.
5.1. Experimental Specifications
The studies were conducted on a computer having a processor (Intel(R) Core(TM) ). Memory capacity of 8 GB.
Under the Ubuntu operating system, the algorithms are implemented using the C++ language and the OpenMP library [35]; parallel loops are implemented using the OpenMP library. To operate huge numbers greater than 64 bits, the GMP (GNU Multiple Precision) library [36] is utilised.
The experimental study used composite numbers with sizes of 11–20 digits. The average time for 20 random numbers is the running time of each implemented algorithm for each fixed number of digits.
5.2. Execution Time
The running times of the algorithms BWFM and MWFM (which are considered the latest wheel factorization algorithms [34]) are displayed in this section. The average running times (in seconds) for BWFM and MWFM are shown in Table 2. The percentage of improvement for MWFM over BWFM is shown in Table 3, while Table 4 depicts the execution time of MWFM as the wheel size increases.

Table 2.
Execution time (s) for BWFM and MWFM.

Table 3.
Percentage of improvement of MWFM over BWFM.

Table 4.
The execution time of MWFM as the wheel size increases.
6. Discussion
This section discusses and analyses the results of implementing the BWFM and MWFM algorithms on the data set in terms of running time, as shown in Table 2, Table 3 and Table 4.
- MWFM takes less time to execute than BWFM, except when the size equals 11 digits. See Table 2.
- On average, the percentage improvement for MWFM over BWFM is . For all cases, the minimal and highest improvements are and , respectively. See Table 3.
- The running time of MWFM decreases as the wheel size increases from 4 to 8. See Table 4.
- The main disadvantage of MWFM is that it requires an array T, which will be very large if we use more than 8 prime integers as a basis.
- Another flaw is that the method does not employ a theoretical foundation to identify the optimal number of prime integers to use as a basis.
7. Conclusions
In this paper, we addressed the integer factorization problem, which is one of the difficult problems associated with cryptanalysis of some public-key cryptosystems. The goal of integer factorization is to divide a composite number into prime factors. We have presented a new approach for improving the most recent wheel factoring method, BWFM. The approach is based on increasing the size of the Base array. The proposed algorithm performs significantly better when implemented on composite integers ranging in size from 11 to 20 digits. On average, MWFM outperforms BWFM by . In the future, we will try to establish theoretically the ideal size of the Base array.
Author Contributions
Software and writing—original draft, A.M.Z., K.A.F. and M.E.B.; writing—review and editing, A.M.A. and S.K.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by King Saud University. Research Supporting Project number (RSPD2023R538), King Saud University, Riyadh, Saudi Arabia.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Fujioka, A.; Suzuki, K.; Xagawa, K.; Yoneyama, K. Strongly secure authenticated key exchange from factoring, codes, and lattices. Des. Codes Cryptogr. 2015, 76, 469–504. [Google Scholar] [CrossRef]
- Nimbalkar, A.B. The digital signature schemes based on two hard problems: Factorization and discrete logarithm. In Cyber Security; Bokhari, M., Agrawal, N., Saini, D., Eds.; Springer: Singapore, 2018; Volume 729, pp. 493–498. [Google Scholar]
- Poulakis, D. A public key encryption scheme based on factoring and discrete logarithm. J. Discrete Math. Sci. Cryptogr. 2009, 2, 745–752. [Google Scholar] [CrossRef]
- Rivest, R.L.; Shamir, A.; Adleman, L.M. A method for obtaining digital signatures and public key cryptosystems. Commun. ACM 1987, 21, 120–126. [Google Scholar] [CrossRef]
- Zheng, M. Revisiting the Polynomial-Time Equivalence of Computing the CRT-RSA Secret Key and Factoring. Mathematics 2022, 10, 2238. [Google Scholar] [CrossRef]
- Fathy, K.; Bahig, H.; Farag, M. Speeding up multi- exponentiation algorithm on a multicore system. J. Egypt Math. Soc. 2018, 26, 235–244. [Google Scholar] [CrossRef]
- Fathy, K.A.; Bahig, H.M.; Ragab, A.A. A fast parallel modular exponentiation algorithm. Arab. J. Sci. Eng. 2018, 43, 903–911. [Google Scholar] [CrossRef]
- Bahig, H.M.; Nassr, D.I.; Mahdi, M.A.; Bahig, H.M. Small Private Exponent Attacks on RSA Using Continued Fractions and Multicore Systems. Symmetry 2022, 14, 1897. [Google Scholar] [CrossRef]
- Bahig, H.M.; Mahdi, M.A.; Alutaibi, K.A.; AlGhadhban, A.; Bahig, H.M. Performance analysis of fermat factorization algorithms. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2020, 11, 340–350. [Google Scholar] [CrossRef]
- Lenstra, A.K. Integer factoring. Designs Codes Cryptogr. 2000, 19, 101–128. [Google Scholar] [CrossRef]
- Menezes, A.J.; Katz, J.; van Oorschot, P.C.; Vanstone, S.A. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 1996. [Google Scholar]
- Montgomery, P.L. A survey of modern integer factorization algorithms. CWI Quart 1994, 7, 337–366. [Google Scholar]
- Peng, W.C.; Wang, B.N.; Hu, F.; Wang, Y.J.; Fang, X.J.; Chen, X.Y.; Wang, C. Factoring larger integers with fewer qubits via quantum annealing with optimized parameters. Sci. China Phys. Mech. Astron. 2019, 62, 60311. [Google Scholar] [CrossRef]
- Rubinstein-Salzedo, S. Clever factorization algorithms and primality testing. In Cryptography; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Yan, S.Y. Primality testing and integer factorization in public-key cryptography. In Advances in Information Security; Springer: Berlin/Heidelberg, Germany, 2009; Volume 11. [Google Scholar]
- Yan, S.Y. Factoring Based Cryptography. In Cybercryptography: Applicable Cryptography for Cyberspace Security; Springer: Berlin/Heidelberg, Germany, 2019; pp. 217–286. [Google Scholar]
- Yan, S.Y.; James, G. Can integer factorization be in p? In Proceedings of the International Conference on Computational Inteligence for Modelling Control and Automation and International Conference on Intelligent Agents Web Technologies and International Commerce (CIMCA’06), Sydney, Australia, 28 November–1 December 2006; p. 266. [Google Scholar]
- Pritchard, P. Explaining the wheel sieve. Acta Inform. 1982, 17, 477–485. [Google Scholar] [CrossRef]
- Koundinya, A.K.; Harish, G.; Srinath, N.K.; Raghavendra, G.E.; Pramod, Y.V.; Sandeep, R.; Punith, K.G. Performance analysis of parallel pollard’s RHO factoring algorithm. Int. J. Comput. Sci. Inform. Technol. 2013, 5, 157–164. [Google Scholar] [CrossRef]
- Varadharajan, S.; Raddum, H. Factorization using binary decision diagrams. Cryptogr. Commun. 2019, 11, 443–460. [Google Scholar]
- Wu, L.; Cai, H.J.; Gong, Z. The integer factorization algorithm with pisano period. IEEE Access 2019, 7, 167250–167259. [Google Scholar] [CrossRef]
- Valenta, L.; Cohney, S.; Liao, A.; Fried, J.; Bodduluri, S.; Heninger, N. Factoring as a service. In Financial Cryptography and Data Security; Grossklags, J., Preneel, B., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 6903, pp. 321–338. [Google Scholar]
- Lenstra, A.K.; Lenstra, H.W., Jr.; Manasse, M.S.; Pollard, J.M. The Number Field Sieve; Lecture Notes in Mathematics; Springer: Berlin/Heidelberg, Germany, 1993; p. 1554. [Google Scholar]
- Akchiche, O.; Khadir, O. Factoring RSA moduli with primes sharing bits in the middle. Appl. Algebra Eng. Commun. Comput. 2018, 29, 245–259. [Google Scholar] [CrossRef]
- Bahig, H.M.; Nassr, D.I.; Bhery, A. Factoring RSA modulus with primes not necessarily sharing least significant bits. Appl. Math. Inform. Sci. 2017, 11, 243–249. [Google Scholar] [CrossRef]
- Bahig, H.M.; Nassr, D.I.; Bhery, A.; Nitaj, A. A unified method for private exponent attacks on RSA using lattices. Int. J. Found. Comput. Sci. 2020, 31, 207–231. [Google Scholar] [CrossRef]
- Nassr, D.I.; Bahig, H.M.; Bhery, A.; Daoud, S.S. A new rsa vulnerability using continued fractions. In Proceedings of the AICCSA 08—6th IEEE/ACS International Conference on Computer Systems and Applications, Doha, Qatar, 31 March–4 April 2008; pp. 694–701. [Google Scholar]
- Bahig, H.M.; Bahig, H.M.; Kotb, Y. Fermat factorization using a multi-core system. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 323–330. [Google Scholar] [CrossRef]
- Brent, R.P. Some parallel algorithms for integer factorisation. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinfor-Matics); Springer: Berlin/Heidelberg, Germany, 1999; Volume 1685, pp. 1–22. [Google Scholar]
- Gulida, K.R.; Ultanov, I.R. Comparative analysis of integer factorization algorithms using CPU and GPU. MANAS J. Eng. 2017, 5, 53–63. [Google Scholar]
- Atanassov, E.; Georgiev, D.; Manev, N. Number theory algorithms on GPU clusters. In Modeling and Optimization in Science and Technologies; Springer: Berlin/Heidelberg, Germany, 2014; pp. 131–138. [Google Scholar]
- Durmus, O.; Cabuk, U.C.; Dalkilic, F. A study on the performance of base-m polynomial selection algorithm using GPU. In Proceedings of the International Conference on Artificial Intelligence and Applied Mathematics in Engineering (ICAIAME 2019), Antalya, Turkey, 20–22 April 2019. [Google Scholar]
- Bahig, H.M.; Nassr, D.I.; Mahdi, M.A.; Hazber, M.A.; Al-Utaibi, K.; Bahig, H.M. Speeding up wheel factoring method. J. Supercomput. 2022, 78, 15730–15748. [Google Scholar] [CrossRef]
- OpenMP. Available online: https://www.openmp.org/ (accessed on 14 November 2020).
- GMP. Library, GNU Multiple Precision Arithmetic Library. Available online: https://gmplib.org/ (accessed on 14 November 2020).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).