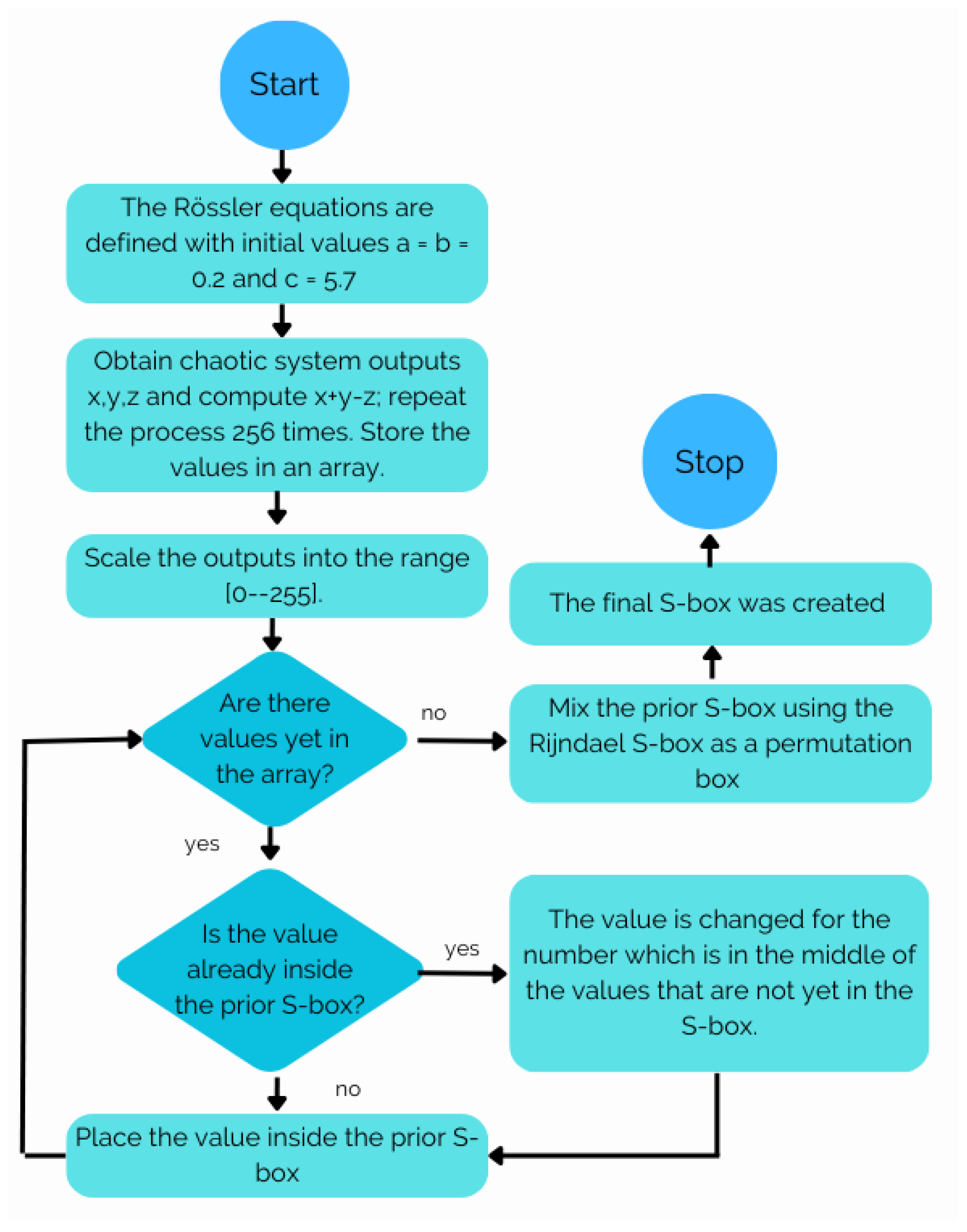
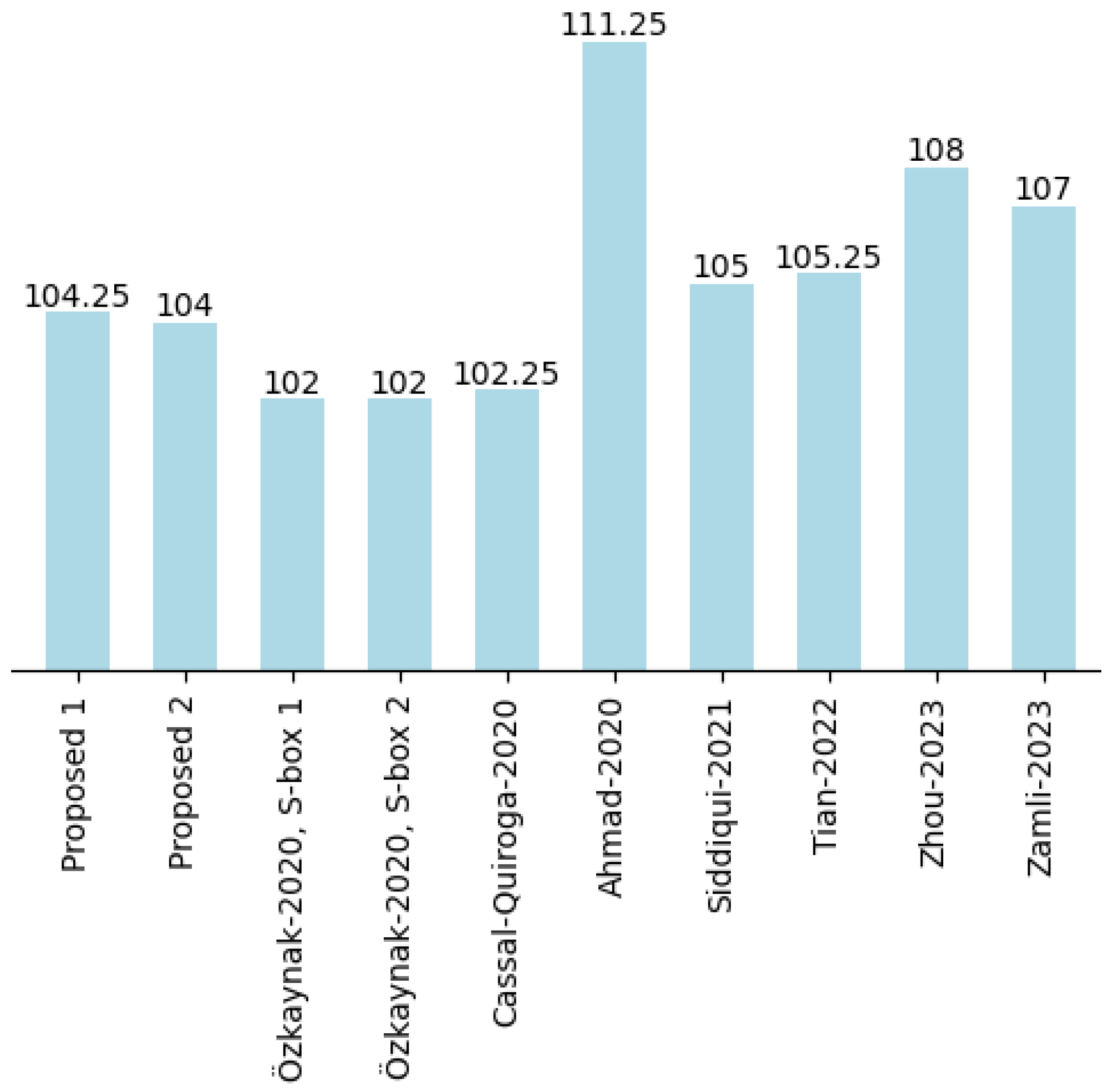
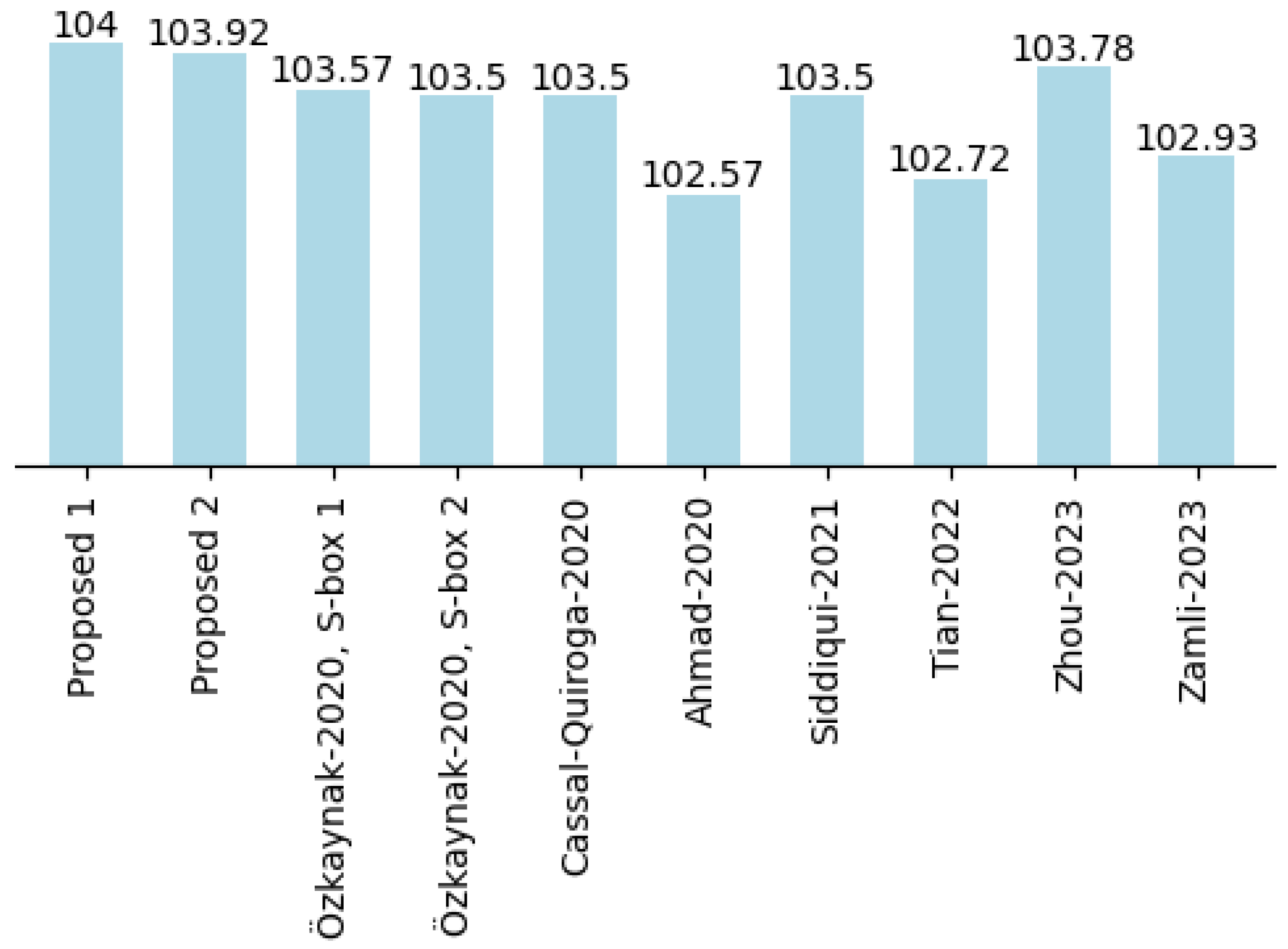
In this chapter, we delve into the fundamental building blocks of our study on S-boxes. We provide a background, offering insights into the preliminaries necessary to understand S-boxes.
2.1. Related Work
Numerous researchers have explored using chaotic systems to generate cryptographic tools, including S-boxes, cipher algorithms, and HASH functions [
12]. This endeavor aims to enhance the security of data transmission across networks. Furthermore, there are several methods available for their development, such as chaotics maps [
13,
14,
15], Lorenz equations [
16,
17], and cellular automata [
17,
18], among others.
In [
19], a novel key-dependent S-box is introduced and constructed through the iteration of continuous chaotic maps. The authors demonstrated that this S-box offers a substantially expanded key space compared to existing key-dependent chaotic S-boxes. Similarly, in [
20], a method is proposed based on a piecewise linear chaotic map (PWLCM) incorporating optimization conditions. This approach effectively mitigates the linear propagation of information within a cryptosystem, consequently reducing the high differential probability encountered during the differential cryptanalysis of an S-box. Highly dispersive S-boxes are a sought-after component in cryptosystems, serving as non-linear confusion sub-layers to bolster resistance against modern attacks. For instance, Attaullah et al. introduced a scheme to create an S-box with a robust arithmetic foundation [
21]. This construction relies on the group action of a projective general linear group on units of a finite local ring, aligning its attributes with those of other S-boxes. Additionally, Zahid et al. proposed an innovative technique involving cubic fractional transformation (CFT) to construct substitution boxes [
22]. The cryptographic power of these S-boxes underwent rigorous assessment. In a similar vein, these authors in 2021 [
23] introduced a method incorporating a square polynomial transformation, coupled with an affine transformation and a permutation approach, to devise dynamic S-boxes. Moreover, they presented an approach utilizing a novel linear trigonometric transformation to develop dynamic and key-dependent S-boxes [
24]. Thorough performance and comparative analyses underscore the S-boxes’ profound efficacy for application in symmetric ciphers. On the other hand, image encryption is an efficient and vital means of safeguarding classified and confidential images. However, with the advancement of computer processing power, encryption methods such as AES, DES, or chaotic series, which were once considered secure, are now less robust [
25].
Bearing that in mind, development is highlighted in [
26], where an encryption algorithm employing a chaos-based S-box is devised for efficient and secure image encryption. Initially, a chaos-based random number generator is crafted by applying the suggested chaotic system. Evaluation of test outcomes attests that the proposed image encryption algorithm excels in both security and speed for diverse image encryption applications. Furthermore, Khan et al. introduced a dynamic S-box-based watermarking scheme in [
27]. A piecewise linear chaotic map generates a 16 × 16 dynamic substitution box (S-box), enabling the extraction of the original image at the recipient’s end without compromising sensitive information. The scheme’s resilience, efficiency, and security are substantiated through several assessments, including the structure similarity index, structure dissimilarity index, structure content, mutual information, energy, entropy, correlation tests, and comprehensive analysis of classical attacks. In addition, Ref. [
28] presents an innovative approach centered on inverses and permutations, allowing for the easy construction of numerous highly non-linear S-boxes with minimal alterations to transformation parameters. Furthermore, an image encryption algorithm was introduced, utilizing the generated S-box to execute pixel shuffling and substitution, enhancing its statistical robustness and differential encryption capabilities.
In the realm of substitution, modern block ciphers leverage one or more substitution boxes (S-boxes), making runtime efficiency a pivotal consideration. In [
29], a novel S-box was crafted using a 1D logistic map chaotic system. The chaotic sequence derived from the 1D logistic map was harnessed to produce hexadecimal code values, which were subsequently used in the construction of the new S-box. The algorithm passes all statistical tests executed in a few milliseconds.
Finally, cellular automata (CA) represents an interesting approach for designing substitution boxes (S-boxes) due to having good cryptographic properties and low implementation costs. In 2017, ref. [
30] introduced the concept of evolving cellular automata rules that can be translated into S-boxes. With it, it was possible to find optimal S-boxes for sizes from 4 × 4 to 7 × 7. Building on this foundation, furthermore, Mariot et al. [
31] have systematically investigated the cryptographic properties of S-boxes defined by CA, proving some upper bounds on their non-linearity and differential uniformity. In particular, they propose a “reverse engineering” method based on De Bruijn graphs to determine whether a specific S-box is expressible through a single CA rule. The results show that genetic programming can find much smaller CA rules defining the same S-box up to the size 7 × 7.
2.2. Preliminaries
This section is devoted to introducing the preliminaries related to S-boxes’ design and the evaluation metrics used to test their effectiveness. In addition, it includes a brief description of chaotic systems and the Rössler attractor, which is used in the design of our proposed S-box.
2.2.1. S-Box
An S-box, denoted as
S, with dimensions
, is a mapping defined as
. It can be expressed as a search table with
rows,
, where
for
[
32,
33,
34]. The mapping occurs by taking the
i-th row, where
i is the decimal value of the input, and then, the output is given by the
value. Depending on the size of
n, this representation could have a large amount of rows; for example, with
, the table will have 256 rows. This is why another representation has been adopted. The input
is split into two parts, keeping the bits sequence, let us say
, where ⊕ is a concatenation. Then, rows in a table are represented by all the combinations generated by
and columns by combinations of
; that is, we generate a table of size
, where the content of the cell will be the mapping associated with the input formed by its row with its column, which is,
. This form of S-box coding also contains all the possible combinations but with a reduced number of rows.
2.2.2. Criteria for Evaluating an S-Box
The evaluation of an S-box’s strength hinges on its cryptographic characteristics, encompassing non-linearity, bijection, adherence to strict avalanche criterion (SAC), compliance with bit independence criterion (BIC), as well as linear and differential approximation probabilities. An ideal or near-optimal S-box attains the maximum values for these attributes. Furthermore, an S-box exhibiting elevated non-linearity and a minimal differential probability (DP) value is recognized as cryptographically strong [
20].
Bijectivity
An
S-box is said to be bijective if all its
n Boolean functions have an equal number of 0 and 1. As a result, all
output values of the S-box are distinct and are also in the range of
. A Boolean function is 0/1 balanced if it satisfies Equation (
1), where
and hwt() is the Hamming weight [
35].
In other words, if the Hamming weight of the linear combination of all Boolean functions of the designed S-box equals , then the S-box is bijective.
Nonlinearity (NL)
Non-linearity is measured by how closely the S-box approximates a linear function; the S-box operation must avoid being a linear transformation from input to output, as it undermines the security of encryption methods. Furthermore, a greater degree of non-linearity suggests enhanced resistance against linear attacks. The non-linearity of a Boolean function
f with
n bits is computed using Equation (
2), where
represents the Walsh spectrum of the coordinate Boolean function
f, which is measured as Equation (
3), and
is the dot product in a bit-by-bit way [
22,
35].
Strict Avalanche Criterion (SAC)
The strict avalanche criterion (SAC) assesses how changes in the input bits affect the changes in the output bits of a cryptographic function. Moreover, SAC is an essential criterion because it measures the ability of the cryptographic function to introduce diffusion and confusion in data. This criterion requires that if an input has a single-bit flip, it should flip
bits out of
n output bits [
28]. A dependence matrix is calculated to test the SAC; Equation (
4) describes how to calculate the dependence matrix [
20].
Bit Independence Criterion (BIC)
The bit independence criterion was introduced by Webster and Tavares [
36]; it necessitates that the output bits exhibit no correlation and that all input–output variables are mutually independent across all avalanche vectors [
20]. Consider the Boolean functions
, which constitute an
S-box. It has been observed that when the S-box satisfies the bit independence criterion (BIC), the Boolean function
(where
and
,
) exhibits a high degree of non-linearity and effectively meets the avalanche criterion. This ensures that if any individual input bit is inverted, the correlation coefficient between every pair of output bits will be close to zero.
Lineal Approximation Probability (LAP)
Block cipher algorithms aim to scramble input data bits thoroughly; a robust S-box contributes to this goal by offering a non-linear transformation from plaintext to ciphertext. On the other hand, linear cryptanalysis is an attacker’s attempt to uncover the weak connection between plaintext and ciphertext [
28]. The effectiveness of this transformation is quantified by the linear approximation probability (LAP), as expressed in Equation (
6).
where
X is a set of all possible inputs
x, whose cardinality is
for an
S-box. Any S-box having a lower LP score tends to have better resistance to linear cryptanalysis [
35].
2.2.3. Rijndael S-Box
The Rijndael S-box is generated through a series of well-defined mathematical operations.
Substitute Bytes: In this step, each byte of the S-box is replaced by another byte based on a fixed lookup table. The lookup table is constructed using a mathematical transformation known as the finite field inversion. This transformation involves a combination of bitwise operations like substitution, addition, and multiplication in the finite field of Galois.
Affine Transformation: After the substitution step, an affine transformation is applied to each byte in the S-box. This transformation involves bitwise XOR operations with fixed constants. The purpose of this step is to further enhance the diffusion properties of the S-box, ensuring that small changes in the input result in significant changes in the output.
Permutation: The permutation step involves swapping the positions of the bytes in the S-box to create confusion and diffusion within the cipher. The permutation is designed to be efficient to compute and reversible, ensuring that the S-box can be easily inverted during decryption. The combination of these steps results in a highly non-linear and secure S-box that is resistant to various cryptanalysis techniques.
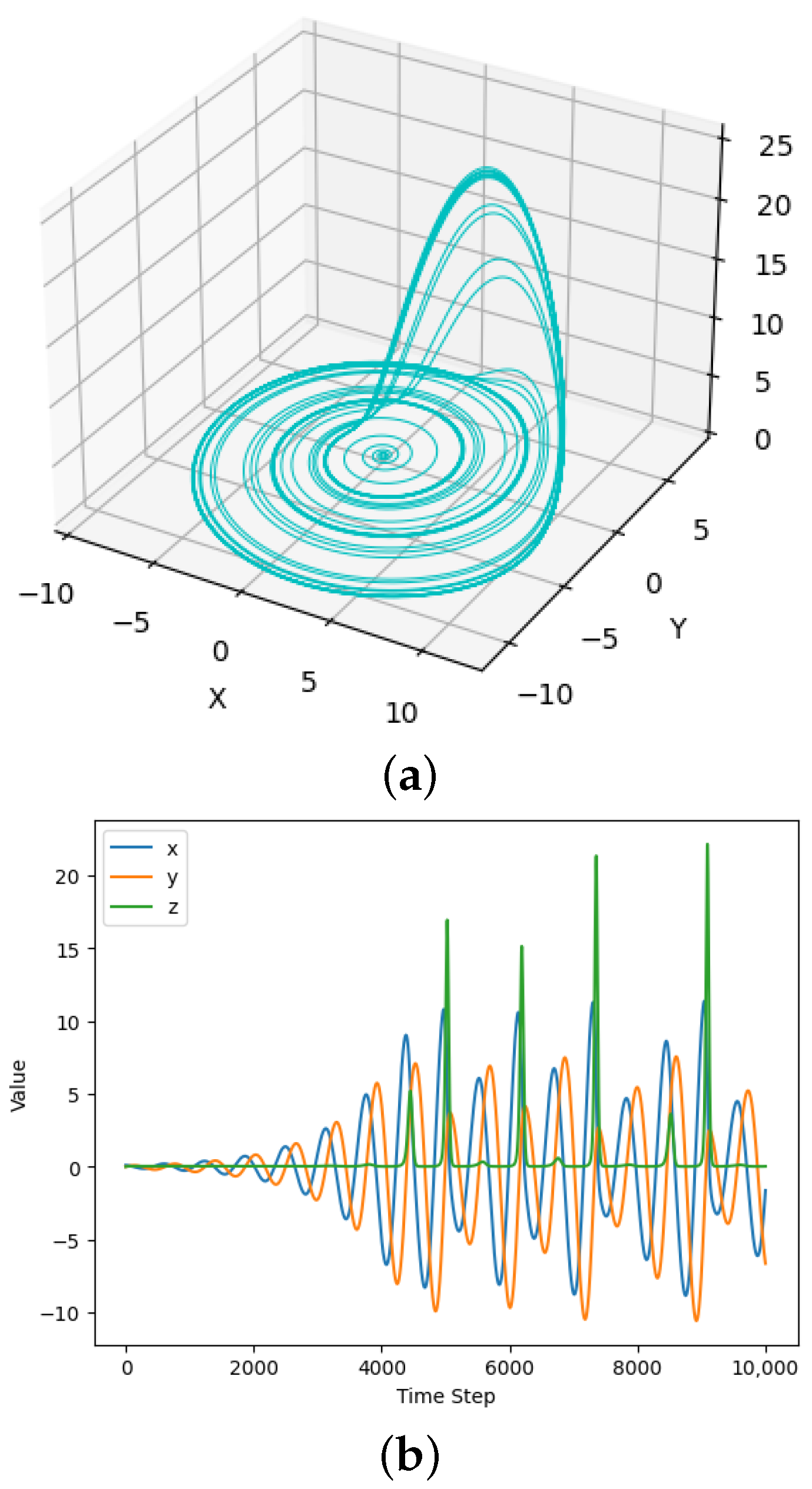
2.2.4. Rössler Attractor
The Rössler attractor, discovered by the German biochemist and mathematician Otto Rössler in 1976, is an example of a chaotic dynamical system. This kind of system exhibits complex, unpredictable behavior. The Equations that define the Rössler system are (
7)–(
9), where
x,
y, and
z are the state variables of the system, and
a,
b, and
c are parameters that determine the behavior of the system that can form both a chaotic (but deterministic) and an ordered process in the three-dimensional phase space of the parameters [
37,
38]. On the other hand, it is often associated with chaotic or irregular motion, where the trajectory of a point in the three-dimensional space governed by the Rössler equations can display complex patterns that are highly sensitive to initial conditions,
where
a = 0.2,
b = 0.2, and
c = 5.7. The attractor’s trajectory in a three-dimensional space exhibits complex, swirling patterns and never settles into a stable equilibrium, as is shown in
Figure 1a. This is a hallmark of chaotic systems, where small changes in initial conditions can lead to drastically different outcomes over time; in other words, tiny differences in the starting conditions can amplify over time and result in entirely different paths within the attractor, shown in
Figure 1b.