1. Introduction
With the development of cryptography research, some basic math skills and concepts are becoming more and more significant in the last decade. For instance, set theory, as one of theoretical foundations of computer science and engineering, has been widely used in database design [
1], large-scale data processing [
2], fault diagnosis [
3] and other areas. Wherein, the problem of determining whether or not an element belongs to a set is called set membership decision. It is not only the basis of set theory but also a common problem on the Internet, and has been widely concerned and applied in many fields, such as e-auction, blacklist and whitelist mechanism, anonymous certificate systems, and so forth [
4,
5,
6,
7]. For example, as a common access control technology, the blacklist mechanism allows access to any user in the system except those explicitly mentioned. This mechanism is essentially used to determine whether the user is in the blacklist set.
A naive method to solve the set membership decision problem is to compare a tested element
x with all elements in a set
S one-by-one. However, this method is very ineffective and does not meet the needs of large-scale membership determination on the Internet. In order to improve efficiency, Bloom Filter (BF) [
8] and Cryptographic Accumulator (CA) [
9] are applied to the membership decision by compressing the set into a compact representation. Usually, the following points need to be considered for a cryptographic membership decision scheme:
Specifically, the BF-based method maps each element in the set into k positions on an array by k different hash functions and sets the bits of these positions to 1. This array is called the representation of the set. When testing, the tested element is first mapped by the above k hash functions, the tested element must not be in the set if one of these mapped positions in the array is 0; otherwise, the tested element is likely to be in the set if these positions are all 1. The CA-based method works as follows. It first accumulates all of the elements in the set to a random value as the representation of the set. In the decision stage, a verifier can determine whether the tested element belongs to the set based on the algebraic relationship between the element’s witness and published accumulative value.
In the above methods, the way to solve the membership decision problem is one-time testing between the tested element and the compressed form of the set. Obviously, they are more efficient in comparison with one-by-one testing in the naive method. In order to further protect the privacy of tested element, Zero-Knowledge Proof (ZKP) technology [
10,
11,
12] is considered in [
7,
13,
14]. In these schemes, zero-knowledge property allows one to prove that a tested element belongs to a set without revealing its information. This feature has bright application prospects. For example, in the financial supervision, a user can prove to a bank that they belong to a public user set without disclosing their identity information, which will reduce the disclosure of the user’s privacy.
Although many remarkable results have been made on the membership decision and related problems, there are still some challenges, especially under the requirements of complex applications and the security required by large-scale and dynamic networks. For example, although the existing set representation has a certain compression feature, the more detailed and secure set compact representation still needs to be further studied to meet the needs of large-scale network applications. Furthermore, the research on cryptographic protocol supporting privacy protection remains a challenge for protecting a sensitive tested element in the membership decision.
In view of the above challenges, this paper aims to construct a secure representation of the set and design a Zero-Knowledge Dual Membership (Dual membership denotes two opposite set membership, i.e., ∈ and ∉, = and ≠) Proof (ZKDMP) protocol. The highlights of this paper can be described as follows: (a) defining the cryptographic representation of the set and formalizing its security, (b) proposing the concept of Secure Decision of Membership to decide the Pos-and-Neg membership, and (c) constructing the ZKDMP protocol to support strict Pos-and-Neg membership decisions.
1.1. Related Works
Bloom Filter (BF) is an efficient tool that can be used to test whether an element is a member of a set. In 2009, Nojima and Kadobayashi [
15] proposed a cryptographically secure privacy protection BF protocol. They adopted the blind signature and oblivious pseudorandom function to enhance the privacy of bit information in the array, and gave a simple security definition and analysis. Subsequently, Ramezanian [
16] enhanced the above work by using Goldwasser–Micali homomorphic encryption and blind RSA signature. Furthermore, he also proposed several membership testing schemes with privacy protection.
In 1993, Cryptographic Accumulator (CA) was introduced in [
9]. It accumulates a set of elements into a short commitment and generates a short witness for all the accumulated elements. These witnesses can be publicly verified with commitments, so as to prove the relationship between elements and sets. On this basis, Papamanthou et al. [
17] presented a
q-strong multilinear Diffie–Hellmann (
q-SMDH) accumulator construction. They combined this accumulator with a constant-depth tree in a nested way and proposed a cryptographic protocol for determining the membership of sets. Then, Papamanthou et al. [
18] further improved the above scheme and gave an accumulator based on bilinear mapping, as well as a more strict definition and security proof. Additionally, Derler et al. [
19] revised the concept of the accumulator by introducing indiscriminability and proposed an undeniable universal accumulator. Ghosh et al. [
20] paid attention to the privacy of accumulator and proposed a zero-knowledge accumulator, which would not disclose the information of the set in the execution process.
At the same time, CA is also used to decide the non-membership. Li et al. introduced the concept of the universal accumulator in [
21], different from traditional accumulative machines, this scheme can efficiently compute the non-membership witness for all elements that have not been accumulated. Furthermore, this scheme is proved to be secure under the strong RSA (sRSA) assumption. After that, Damgård and Triandopoulos [
22] completed the above scheme and presented a new accumulator construction based on bilinear mapping, which supports the proof of a set non-membership. The security of this scheme is reduced to the
q-strong Diffie–Hellman (
q-SDH) assumption. Then, Yu et al. [
23] constructed the first universal accumulator from the small integer solution (SIS) assumption in a standard lattice. Their scheme could not only generate short witnesses for non-accumulators but also made a zero-knowledge proof for non-accumulator witnesses.
Recently, some ZKP protocols for membership are proposed to prove that an element in or not a public set without disclosing the element. In 2008, Camenisch et al. [
24] presented two new approaches to building set-membership zero-knowledge proofs based on
q-SDH and RSA assumption, respectively. Furthermore, their protocols can be used to range proof in zero-knowledge. After that, Peng et al. [
25] constructed two new non-membership proof protocols to prove that a committed element is not in a finite set. Benarroch et al. [
7] also proposed an efficient ZKP protocol supporting membership or non-membership decisions based on the strong RSA (sRAS) assumption.
In addition, there are many other studies on membership decision. Guo et al. proposed a membership encryption scheme in [
26,
27]. By adding a set of tokens to the ciphertext, their scheme required the user to hold the token belonging to the token set when decrypting the message. In terms of design, their scheme adopted a construction based on polynomial root-value decision, which can be regarded as an extension of the broadcast encryption. Arfaoui et al. [
28] applied membership proof to Near-Field Communication and proposed a secure mobile ticketing protocol for the public transportation. This protocol ensured the anonymity of users, so as to prevent service providers from tracking users’ tracks. According to the zero-knowledge set membership proof, Baza et al. [
29] proposed a time-locked deposit protocol for ride sharing in order to ensure the privacy of both drivers and riders. Locher and Haenni [
30] also proposed an Internet voting protocol based on the same technology, which can ensure the anonymity of voting without authority. In summary, in the
Table 1, we list the comparison results between some related works [
7,
16,
17,
22,
24,
25] and ours in terms of technology, decision mode, zero-knowledge and hardness assumptions.
1.2. Our Contributions
The purpose of this work is to construct a novel Zero-Knowledge Dual Membership Proof (ZKDMP) protocol, which can support Pos-and-Neg membership decisions simultaneously. To that end, a new security representation of a subset using aggregation functions is introduced to achieve a secure membership decision. The contributions of this paper are listed below.
We first formalize the security requirements of the aggregator based on our previous work [
31], which refers to the security properties in easy or hard to compute aggregated values for a given set and a certain element. Based on them, two aggregation functions, ZeroAggr and PoleAggr, can achieve a secure representation of a subset in terms of zero-pole interpolation and reach the theoretical lower limit for the representation size of subsets. Moreover, the security of our aggregation functions are proved under the
t-SDH assumption (see
Section 3 and
Section 4).
We propose the concept of Secure Decision of Membership (SDM) and use the zeros-based and poles-based secure representation of the subset to decide the Pos-and-Neg membership, respectively. Thus, the security of membership decisions can be reduced to the security of ZeroAggr and PoleAggr. Furthermore, we verify the feasibility of combining these two secure representations of subset, so this kind of combination could act as the foundation for constructing a dual membership decision cryptosystem (see
Section 5).
Following the approach of the SDM, we construct a ZKDMP protocol for the dual membership decision, which can realize a cryptographic proof of the strict Pos-and-Neg membership. In contrast with a single membership decision, the proposed protocol can prevent elements outside the system from affecting the decision result. Furthermore, the zero-knowledge property of our protocol ensures that the information of the tested element will not be leaked during the interactive proof of the protocol. Moreover, we provide the complete security proofs of the ZKDMP protocol, including positive completeness, negative completeness, soundness and zero-knowledge (see
Section 6).
In addition, in our secure representation of the subset, there is no limit to the number of elements in the universal set (in fact, when the system parameter , the number of elements in the universal set is about and a set with so many elements can be considered almost infinite in a practical application). Finally, the performance evaluations show that our protocol has a simple and easy-to-understand structure.
1.3. Organization
Our approach for cryptographic Pos-and-Neg memberships is presented in
Section 2. Zeros-based and poles-based representation of the subset are introduced in
Section 3 and
Section 4, respectively. Moreover, the secure membership decision is discussed in
Section 5. We present the ZKDMP protocol and its security analysis in
Section 6. The performance evaluations are given in
Section 7. Finally, our conclusion is presented in
Section 8.
2. Our Approach
This paper aims to construct a new zero-knowledge protocol that can support dual membership (positive and negative, Pos-and-Neg) decisions, simultaneously. The basis of constructing such a protocol is to realize a secure representation of subsets. Next, we first show the core idea for designing cryptographic construction of a set-membership (∈ or ∉). The notations and abbreviations used throughout the paper are shown in
Table 2.
2.1. Secure Representation of the Subset (SRS)
Our basic idea is to cryptographically represent the subset by using the aggregation function. In fact, based on the aggregation function (in short, Aggregator) proposed in our previous work [
31], we can further define the security properties of the aggregation function, so as to take the output of the Aggregator as the
security representation of the subset (SRS). Specifically, for any set
, an Aggregator is a cryptographic function if it can map any subset of
into a fixed-size value. The specific definition of the aggregation function is described below.
Definition 1 (Aggregator).
Given a set , let be the power set of , that denotes the public key space. The algorithm satisfies:where is the public key, is a subset of and is a random element.
Note that the aggregation function is a publicly computable function because the public key is used as input of the Aggregator. Moreover, there is no restriction on the size of the set or the subset . In addition, this definition only presents the functional requirement of the Aggregator, and is not related to its security requirements. We give a simple description of the secure Aggregator with two security properties as follows.
Definition 2 (Secure Aggregator). Given a subset , a secure aggregation function can compress into a constant-size random element, and satisfies the following security properties.
Easy to compute the aggregated value for normal input, i.e.,
- -
try to add an element into where the element is not in ; or
- -
try to delete from an element which is already present in .
Hard to compute the aggregated value for abnormal input, i.e.,
- -
try to add an element into where the element is already present in ; or
- -
try to delete from an element which is not in .
2.2. Roadmap for SRS
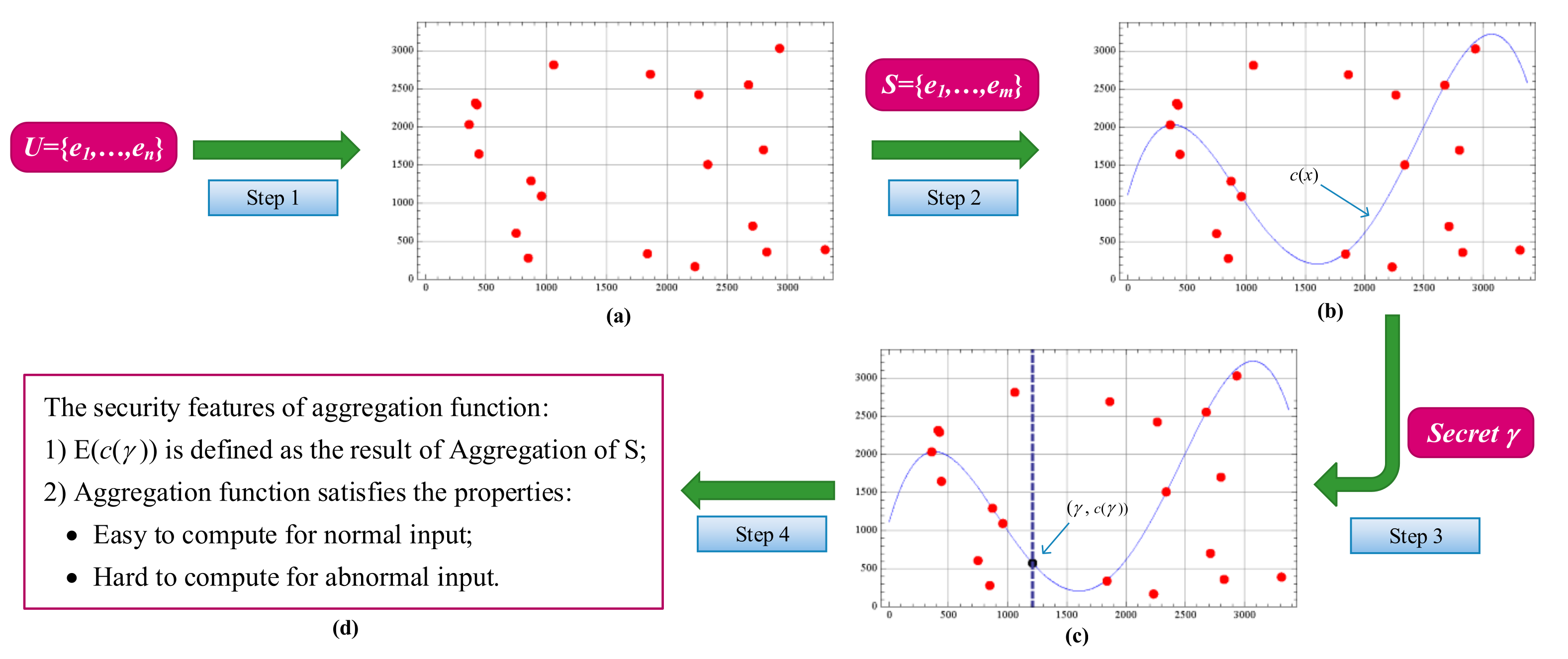
According to the security properties of the aggregate function defined in the last section, it is challenging to design a secure aggregation function for the security representation of the subset, especially for a subset of any size. We here present our intuition to solve this challenging problem. Our approach will be used to construct two secure aggregation functions in
Section 3 and
Section 4. For the convenience of explanation, as shown in
Figure 1, we describe this approach as follows.
For , is mapped to a random point in a cryptographic space. In this step, we also pick partial information of these mapped points and publish them as public keys ;
For a subset , we construct a curve through random points mapped from elements in ;
We pick a secret and define the output of the aggregation function as an encapsulation of the point , , where denotes a cryptographic encapsulation function;
Two security features of the aggregate function are defined to ensure that the aggregation is secure against malicious adversary attacks.
According to secure aggregation functions, we can achieve a secure representation of subsets. Before introducing secure aggregate functions, we first recall the definitions of zeros and poles in rational polynomials.
Definition 3 (Zeros and Poles). Let be a rational polynomial. Then, z is called a zero of the polynomial if , and z is a pole of the polynomial if .
3. Zeros-Based Representation of Subset
Given a polynomial-sized set of elements , we first translate these elements into some random points in a one-dimensional plane; that is, , where we assume each element is denoted as a binary string and is a collision-resistant hash function. We utilize the cryptographic hash to ensure that all points are distributed uniformly in the whole space and each point is unique and nonzero, i.e., and for all , . Since the size of is usually far less than that of , we do not limit the size of (e.g., for a secure elliptic curve).
Next, for
, we wish to find an effective method to compress the corresponding points
in
into a random point
in a two-dimensional plane. To do so, an
-order polynomial
is defined over
.
It is easy to find that will be different if a different subset is used. We map the subset into a point . Given an unknown and random x, is random and unpredictable. An adversary cannot guess the correct value when x is unknown.
We further introduce the Discrete Logarithm Problem (DLP) into the above-mentioned construction in order to guarantee the privacy of x and the unpredictability of . That is, given a multiplicative cyclic group , where g is a generator of , we map the subset into the point rather than . Based on the assumption of DLP, the privacy of x, as well as the unpredictability of , will be guaranteed even when keeps public.
For a secret and a subset , we next define the aggregation function by the above based on the above polynomial . Since the hash values of all elements in the subset are used for the (negative) zeros in (), this aggregation function is named Zeros-based Aggregator (ZeroAggr). In addition, it can aggregate all elements of to .
Definition 4 (ZeroAggr).
Let g be a generator in the group and . The Zeros-based Aggregator (ZeroAggr) inputs the public key and a subset outputs an element in as follows.where γ is the secret, the public key and .
Security Definition and Analysis
Let be a polynomial, we make use of a simple polynomial division with monomial in order to remove a certain (negative) zero from this polynomial, i.e., . Two cases may arise. In the first case, is not a root of , such that we define and , where and are two polynomials and the remainder . In the second case, is a root of , such that the remainder is equal to 0. Hence, we are able to convert the decisional problem of membership into a new problem: whether or not the remainder is equal to 0?
According to the above-mentioned discussions, we define the set subtraction as
and the corresponding subtraction of the Zeros-based aggregation is expressed as:
where
. Let
. According to
or
, we have the two following cases:
Case means that and , such that ;
Case means that is not one root of and , such that .
It is easy to find that can be computed by zeros-based aggregation algorithm for , otherwise we must have the ability to compute from . Hence, we continue to transfer the problem of set membership into a computational problem: whether or not can be computed in a polynomial time.
Based on the above discussion, the security definition of zeros-based aggregation under the dividing polynomial with a monomial is defined below.
Definition 5 (Security of ZeroAggr). Given an element and a subset , a ZeroAggr function on is called a secure zeros-based aggregation if it has the following two properties:
Easy to compute for . The value of can be computed by the ZeroAggr algorithm within a polynomial time, that is, Hard to compute for . Any probabilistic polynomial-time adversary computing succeeds with negligible probability ϵ, that is,
We next prove that our ZeroAggr function is a secure zeros-based aggregation under the Strong Diffie–Hellman (SDH) assumption. The following is the description of the
t-SDH problem [
32].
Definition 6 (t-SDH Problem). Given some elements in , find a pair such that .
The SDH assumption holds in some infinite family of groups, if the aforementioned t-SDH problem is hard for any t that is polynomially bounded in the security parameter, where the group size p grows exponentially with the security parameter. According to this assumption, we prove the security of ZeroAggr in a straightforward manner.
Theorem 1. Our ZeroAggr function is a secure zeros-based aggregator under the t-SDH assumption.
Proof. Let be an instance of t-SDH. We convert this instance into a ZeroAggr function: let and ( is an unknown secret), such that we have and , where we assume that . We have the two following cases for any and ():
Easy to compute for. Given a subset
and an element
, we define
based on
. This information is sufficient to compute the value:
Hard to compute for. If there is a PPT algorithm
can compute
but
. Then we can solve the SDH problem as follows. Let
be defined as above, where
and
are two known polynomials. Hence, we can compute:
because we have
and
. This means we forge a valid solution
for the
t-SDH problem. However, this is a contradiction with the
t-SDH assumption.
Thus, the ZeroAggr function is secure under the t-SDH assumption. □
4. Poles-Based Representation of Subset
We have presented an effective approach to deal with the decisional problem of positive membership (∈) based on zeros-based aggregation, but it is not enough to realize the decisional problem of negative membership (∉). To solve this problem, we expect to build a “conversely” aggregation function that is easy to compute for but hard to compute for . We will use the poles-based aggregation to deal with this problem in this section.
Similar to zeros-based aggregation, we next show the construction of the Poles-based Aggregator (PoleAggr). For
, this function can compress elements of
into a random point
even if the size of
is large. Then, we use hash values of elements in the subset
as the poles of the polynomial, such that the
m-order polynomial
is defined as follows, where
.
In the above polynomial, is the results of . The output of is random and unpredictable for a unknown and random x. Note that give a random value x, the probability of collision between x and all cryptographic hash values is negligible when p is large enough. This means that the probability of or division by zero errors is also negligible.
We next define the PoleAggr based on the above-mentioned polynomial . In this definition, we let h be a generator in the cyclic group . Our goal is to compute for a secret in terms of the public parameter . This definition is expressed as follows:
Definition 7 (PoleAggr).
Let h be a generator in the group and . The Poles-based Aggregator () inputs the public key and the subset , outputs an element in as follows.where γ is the secret, the public key and .
When
and
are known, we can easily obtain:
iff
(or
).
Security Definition and Analysis
We define the addition of the set and element as
and the corresponding addition of poles-based aggregation is expressed as the equation:
where
. Depending on whether
is an element of
or not, we have the following two cases:
Case. This means that for all and a collision-resistant , such that ;
Case. This means that is a double pole of , such that .
It is easy to find that
can be computed by the poles-based aggregation algorithm for
, otherwise we must have ability to compute the value
from the public parameter
. However, it is improbable to calculate this value by Equation (
11) because of the “divided by zero” exception. We will provide a rigorous proof in the proof of Theorem 2. Therefore, the following is a security definition of poles-based aggregation by dividing the polynomial with the monomial.
Definition 8 (Security of PoleAggr). Given an element and a subset , a PoleAggr function on is called a secure poles-based aggregation if it has the following two properties:
Easy to compute for . The value of can be computed by PoleAggr algorithm within a polynomial time, that is, Hard to compute for . Any probabilistic polynomial-time adversary computing succeeds with negligible probability ϵ, that is,
Although the two functions, ZeroAggr and PoleAggr, are dramatically different in form, they have the same security foundation, called the strong Diffie–Hellman (SDH) assumption. We can prove the security of PoleAggr in a more subtle way, where the value , built on the polynomial , could be used as a generator in .
Theorem 2. Our PoleAggr function is a secure poles-based aggregator under the t-SDH assumption.
Proof. Let be an instance of t-SDH. We convert this instance into a PoleAggr function: Let and for . We define and ( is an unknown secret), such that we have and , where and for all . We have the two following cases for any and ():
Easy to compute for . Given a subset
and an element
, we define:
based on
. Such that, we can compute the value of
by using:
Hard to compute for . Assume that there exists a PPT algorithm
can compute the value
but
, where
. We construct a PPT algorithm solving the SDH problem as follows: Let
be defined as above, where
and
are two known polynomials. Hence, we can compute the value:
because we have
and
. The value
is a valid output of the
t-SDH problem, but it is contradiction with SDH assumption.
Therefore, the PoleAggr function is secure under the t-SDH assumption. □
5. Secure Decision of Membership
The zeros-based and poles-based representation of the subset have exhibited an ability for the decision of (positive and negative) membership. In this section, we further show that our method is able to provide a clear and concise form for the decision problem of either positive or negative membership when both representations of the subset are used together.
We first present a simple definition for the membership predicate, which is the fundamental principle in our construction of the dual membership decision protocol. Informally, a predicate is a statement that may be true or false according to the values of its variables. Generally, a predicate over membership is defined as follows:
Definition 9 (Membership Predicate). For , a membership predicate is a binary function whose result represents the truth or falsehood of the condition () or (), where , and the subscript of P denotes the set-membership.
If the condition is defined as , it is called a positive membership predicate . Similarly, if the condition is , it is called a negative membership predicate . Next, we define the cryptographic decision problem of positive and negative membership below.
Definition 10 (Secure Decision of Membership, SDM). Let denote a membership predicate for ∈ or ∉. Given an element e and a subset , we say that a probabilistic polynomial time (PPT) algorithm is a secure decision of membership if,
Completeness: if holds, then the verifier will accept the proof, that is, Soundness: if holds, then the verifier will accept the proof with negligible probability ϵ, that is,
where, denotes a cryptographic representation of element e and is a cryptographic representation of subset .
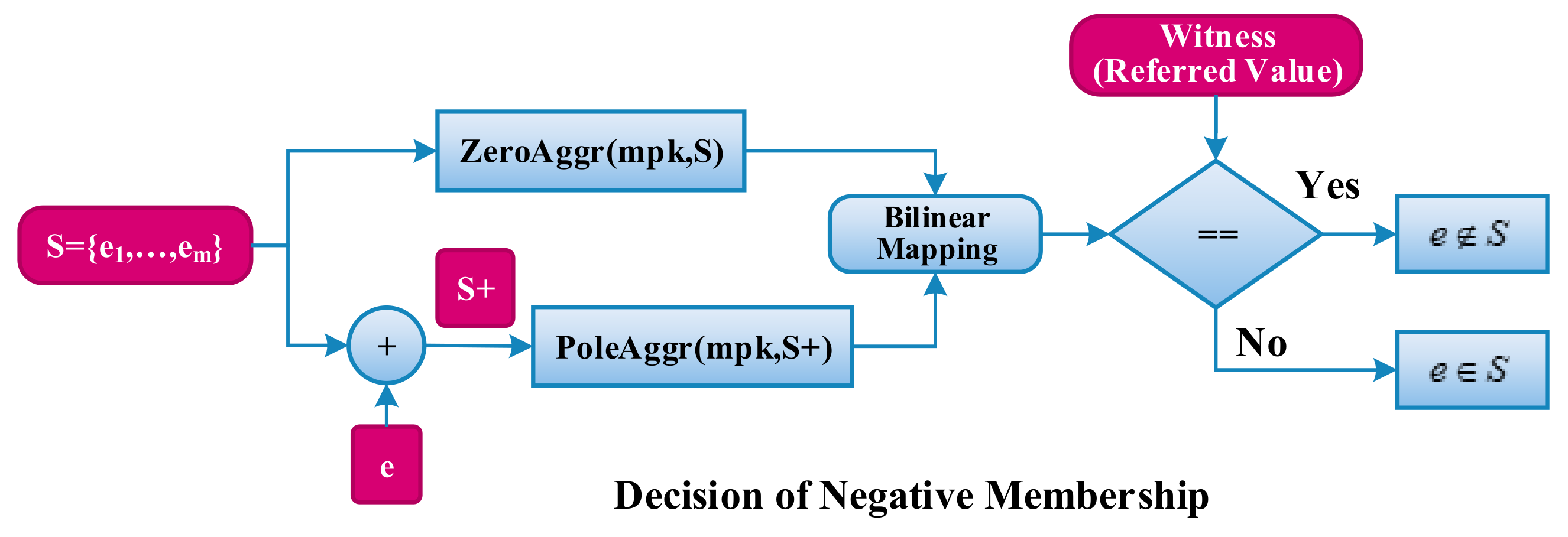
Before discussing the SDM problem, we can observe the fact that ‘zeros’ and ‘poles’ in a rational polynomial function could cancel each other out if and only if zeros and poles are equal. It is this fundamental truth that compels us to combine ZeroAggr and PoleAggr functions together, such that we can verify whether or not the same ‘zeros’ and ‘poles’ exist in these two functions.
We now show how to put zeros-based aggregation and poles-based aggregation together. We use a bilinear mapping to implement this combination. For any generators in and any elements in , then we have . Therefore, let ZeroAggr and PoleAggr work in the group in such a bilinear system, so that we integrate two aggregation functions into an element in . Such a result value will be further used to make the decision of set-membership.
5.1. SDM for Positive Membership
We now present a practical solution for the SDM problem on positive membership. This solution is built on three algorithms, Setup, Extract, and Verify , as follows:
Setup: this is a probabilistic algorithm that generates the public key and a secure representation of subset
; that is,
, where
. Firstly, we randomly pick a secret
and a positive integer
, and then generate the public key:
as well as the private key
. Next, given the arbitrary subset
and
, we make use of the poles-based aggregation function to compute the value:
where
and
.
Extract: this is an algorithm that yields the witness of an arbitrary element . We can extract the witness of from the private key by using the equation .
Verify : this is a verification algorithm that tests membership of an element that is in the subset , that is, , where is the witness of and is secure representation of .
- -
Firstly, we check the relation
. If it holds, we compute
and:
- -
Secondly, we check whether or not the witness
is equal to
, that is:
If the above equation holds, we say that ; otherwise, we say that .
The above solution for SDM over the positive membership is described by
Figure 2. Firstly, the poles-based representation of subset
is generated by using
for a given subset
. Secondly, given an element
, we extract the value
as the witness of
. Next, the zeros-based representation
of
is also yielded if
is in
. Then, the bilinear map between
and
is used to remove all of the same elements between the two corresponding subsets,
and
. Finally, the final decision is realized by matching the above result of the bilinear map and witness
.
In this solution, any adversary cannot cheat or forge the final decisional result based on the theorem below.
Theorem 3. The above construction is a secure decision of positive membership if the ZeroAggr function is a secure zeros-based aggregator.
Proof. According the Definition 10, we prove that our construction satisfies the two following properties:
This means that the adversary’s advantage to break a secure decision of positive membership is equal to the advantage of breaking the secure zeros-based aggregator. □
5.2. SDM for Negative Membership
We next present a practical solution for the SDM problem over negative membership. This solution is similar to the previous SDM over positive membership. We also present this solution by the three following algorithms:
Setup: this algorithm generates the public key and a secure representation of subset
; that is,
. Firstly, we randomly pick a secret
and a positive integer
, and generates the public key:
as well as the private key
. Next, given an arbitrary subset
, we make use of the zeros-based aggregation function to compute the value:
where
and
.
Extract: this is an algorithm that yields the witness of element . We can extract the witness of from as .
Verify : this is a verification algorithm that tests the membership of an element that is in the subset ; that is, , where is the witness of and is a secure representation of .
- -
Firstly, we check the relation
. If it holds, we compute
and:
- -
Secondly, we check whether or not the witness
is equal to
, that is:
If the above equation holds, we say that ; otherwise, we say that .
As shown above,
Figure 3 has almost the same structure as that in
Figure 2. It is an important property to help us combine them (SDMP and SDMN) into one cryptographic protocol (see our membership decision ZKP protocol in next section). However, when we carefully inspect the details, there also exist two differences between SDM for Pos-and-Neg membership. One is that both positions of two aggregation functions, ZeroAggr and PoleAggr, are swapped with each other; and another is that the ‘+’ operation in
Figure 3 takes the place of the ‘–’ operation in
Figure 2.
Next, we prove that our solution is secure against cheating or forgery according to the theorem below.
Theorem 4. The above construction is a secure decision of negative membership if the PoleAggr function is a secure poles-based aggregator.
Proof. In terms of the definition of SDM, we prove tha our construction satisfies the two following properties:
Completeness: When
, the Equation (
31) holds for all valid
in terms of:
Soundness: According to the precondition of this theorem, we assume that the ZeroAggr function is a secure zeros-based aggregation. This means that for every PPT adversary
(see Definition 8):
for a given element
. We will prove that the verifier accepts the verification with negligible probability
; that is,
, where
and
are two assured and unchanged values. We also know that
and
, where
. In this case, the adversary can forge a valid
to meet the equation:
. Without loss of generality, we let
, so that:
In this equation, we require the relation to make the probability , such that and .
This means that the adversary’s advantage to break secure decisions of negative membership is equal to the advantage of breaking secure poles-based aggregation. □
Based on the above security analysis of SDM, the computational complexity of is operations in the group and the complexity of space is , where p is the order of the group and d is a factor of . Obviously, the number of elements in the subset is determined by d, and the security of the SDM is ensured by p, which contains a large factor (e.g., ). For example, when and , the complexity of recovering the secret in the private key is still . At this time, the number of elements in the set can reach , which means that the number of elements is unlimited in practical applications.
In all, it is easy to see that the decision problems of Pos-and-Neg membership are converted into the problems of effective computation of
and
from the two above-mentioned solutions. More importantly, these two solutions have nearly the same structure from the view of
Figure 2 and
Figure 3, for the reason that we easily combine the predicate ∈ and ∉ into a cryptosystem. In the next section, we also apply for this approach to construct a dual membership proof protocol.
6. Zero-Knowledge Dual Membership Proof Protocol
Our ZKDMP protocol is described by an interactive proof system between the prover and verifier. We assume that the verifier holds a public set of elements and the prover owns a secret element e. The prover proves to the verifier the element or without revealing the element itself.
Definition 11. Given two parties, Prover (P) and Verifier (V), the protocol is a secure membership decision over the universal set for a certain element e and a subset , if it satisfies the three following properties:
Note that the output of ZKDMP protocol involves three cases: denotes positive membership (), denotes negative membership ( and ) and ⊥ denotes invalid membership (). We call it a strict Pos-and-Neg membership decision.
6.1. The Proposed Protocol
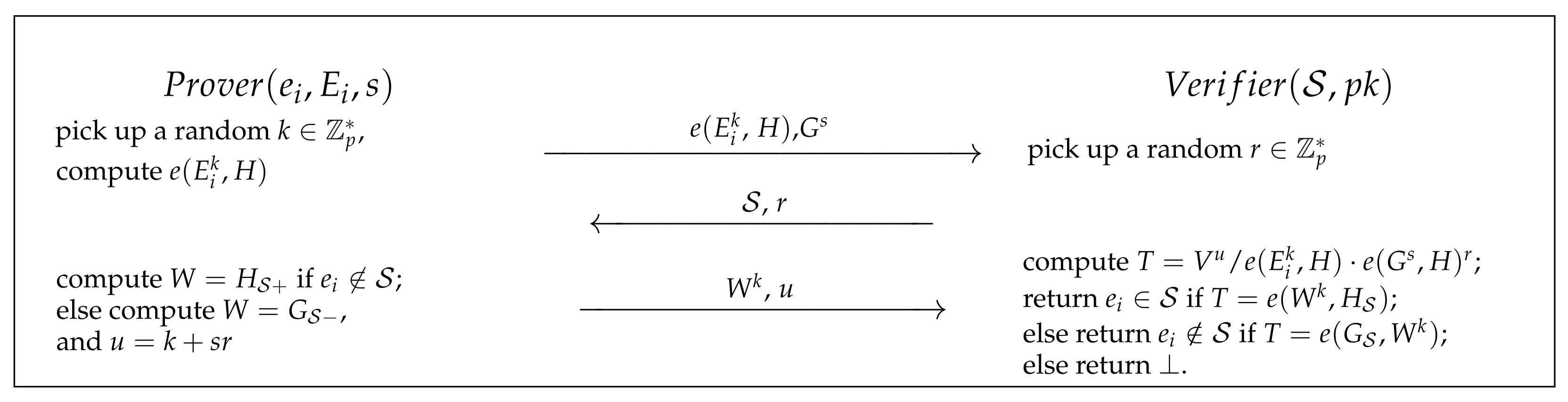
In our ZKDMP protocol, as shown in
Figure 4, we choose
,
G is a generator in
and the prime
p is the order of the group. Furthermore, for any identity
, the hash function can compute
, where a collision-resistant hash function is used to prevent two different elements from mapping into a same value, i.e., for any
,
. Detailed construction of our protocol can be found below.
Setup (). Let G denote a generator in , the Setup algorithm chooses in , then it sets and . Furthermore, the algorithm picks in and sets for . For any , this algorithm computes and and outputs the master key . Finally, it publishes
Protocol. The complete protocol is divided into the following three stages:
Initial stage: The prover random chooses and , then the manager computes the witness and the commitment by using the master key. Finally, the manager sends and to the prover and the verifier, respectively. The verifier also chooses a subset from the universal set .
Interactive-proof stage: Based on the three-move structure in -protocols, our proposed protocol is described below.
- -
Commitment: Prover randomly picks and computes , then it sends this calculation result to the verifier;
- -
Challenge: Verifier randomly selects r in , then sends to the prover;
- -
Response: Prover computes
and sends them to the verifier as the responses, where
,
Verification stage: The verifier computes , and returns True if , else False if , otherwise ⊥, where and .
6.2. Security Analysis
According the Definition 11, we prove that the proposed membership decision protocol satisfies the following four properties.
(1) Positive Completeness: When
, we have the following equation:
Then, the verifier can output
with probability:
(2) Negative Completeness: When
, we have the following equation:
Then, the verifier can output
with probability:
(3) Soundness: Before proving the soundness of the proposed protocol, we firstly define the following events.
Event denotes .
Event denotes .
Event A denotes .
Event denotes .
Event denotes , i.e., .
Event B denotes , i.e., B is the joint of events and , .
In this case,
and
are mutual exclusive events, i.e.,
, the Equation (
37) can be written as:
For any
, we get
. Thus, the above equation:
Let and . Assuming that both and are neglectable, then is also neglectable. In this case, the soundness of our protocol can be proven. In the following, we show that the above assumption is correct, i.e., both and are neglectable.
Proof. For any
, we have
and
. Thus, we have:
We prove that the verifier accepts the positive verification with probability
for the given
. It means that a PPT adversary
can forge
W to make the verifier successfully verify
with probability
. We know that
is an assured and unchanged value. This means that the adversary
can forge a valid
W to meet the equation:
. Without loss of generality, let
, so we have the following probability.
In the above equation, we require
to make:
such that
and
. If the probability
is non-neglectable, this means that the adversary
can secure zeros-based aggregation with a non-neglectable advantage
, that is contradictory to the Theorem 1. Thus,
is neglectable.
For any
, we have
and
, so that we have the probability:
We next prove that the verifier accepts the negative verification with probability
for given
, i.e.,
or
. It means that a PPT adversary
can forge
W to make the verifier successfully verify
with probability
. We know that
is an assured and unchanged value. This means that the adversary
can forge a valid
W to meet the equation:
. Without loss of generality, let
, that we have the following probability.
In this equation, we require
to make:
such that
and
. For any
(
or
) the Equation (
50) holds. If
and the probability
is non-neglectable, this means that the adversary
can break secure poles-based aggregation with a non-neglectable advantage
, that is contradictory to the Theorem 2. Thus,
is neglectable.
Therefore,
and
are neglectable, so
is also neglectable, it means that:
The soundness of our ZKDMP protocol is proved. □
(4) Zero-knowledge: The zero-knowledge of our membership decision protocol implies that the verifier cannot learn any information of the tested element e beyond that , or .
Theorem 5. The proposed dual membership decision is a zero-knowledge proof protocol.
Proof. Let
be the output of the interactive proof system in
view on common input
, the distribution of
during the correct executing of our protocol can be denoted as:
In the above equation, and is the power set of . Next, we construct the PPT machine as follows.
Randomly pick a subset .
Randomly pick .
Randomly pick , , then it computes and .
In the above equation, y is a random element chosen in . Obviously, the above construction is a valid protocol simulation. Y has always been a random element in no matter , or . Therefore, we have and . Thus, the zero-knowledge property of our ZKDMP protocol is proved. □
7. Performance Evaluation
As shown in
Table 3, the comparisons of computation and communication overheads are provided between four existing zero-knowledge membership proof protocols [
24,
25,
28,
34] and ours. In this paper,
n,
and
denote the number of elements in
, exponentiation operations in
and
, respectively.
and
are multiplication and devision operations in
.
and
B are multiplication operation in
and the bilinear pairing operation, respectively. The lengths of elements in
,
and
are defined as
,
and
, respectively. In addition, the operations in
, multiplication in
and hash take less time than the other operations, we neglect them in our evaluation.
In terms of computation overheads, the prover’s costs in [
24,
28,
34] are constants. However, computation costs of the verifier are linear with the number of elements in the subset. In our protocol, for positive membership decisions, i.e.,
, the prover’s computation cost is exponential with the number of elements in
; for negative membership decisions, i.e.,
, the prover’s computation overheads are linear with the number of elements in
. However, the computation costs of our verifier is constant for either the positive or negative set membership. Furthermore, let us turn our attention to communication costs. Obviously, in
Table 3, all of the provers’ communication costs are constants in [
24,
28,
34] and ours, while that of the verifiers are linear with the number of elements in the subset.
In order to evaluate the performance of membership decision protocols in [
24,
25,
28,
34] and ours, we implement them based on the Java Pairing Based Cryptography Library (JPBC) and IntelliJ IDEA 2020.3.3. All programs run on a 64-bit Windows 10 PC with Intel Core i5-4590S processor (Qual Core, 3.00 GHz). Moreover, we choose the SHA-256 cryptographic algorithm as the hash function in our experiments. Let the tested set,
, be any
in a random arbitrary-length string, i.e.,
. Note that in order to reduce the experimental error, all of our experiments are repeated 100 times arithmetically averaging the final results. The simulation parameters are shown in
Table 4.
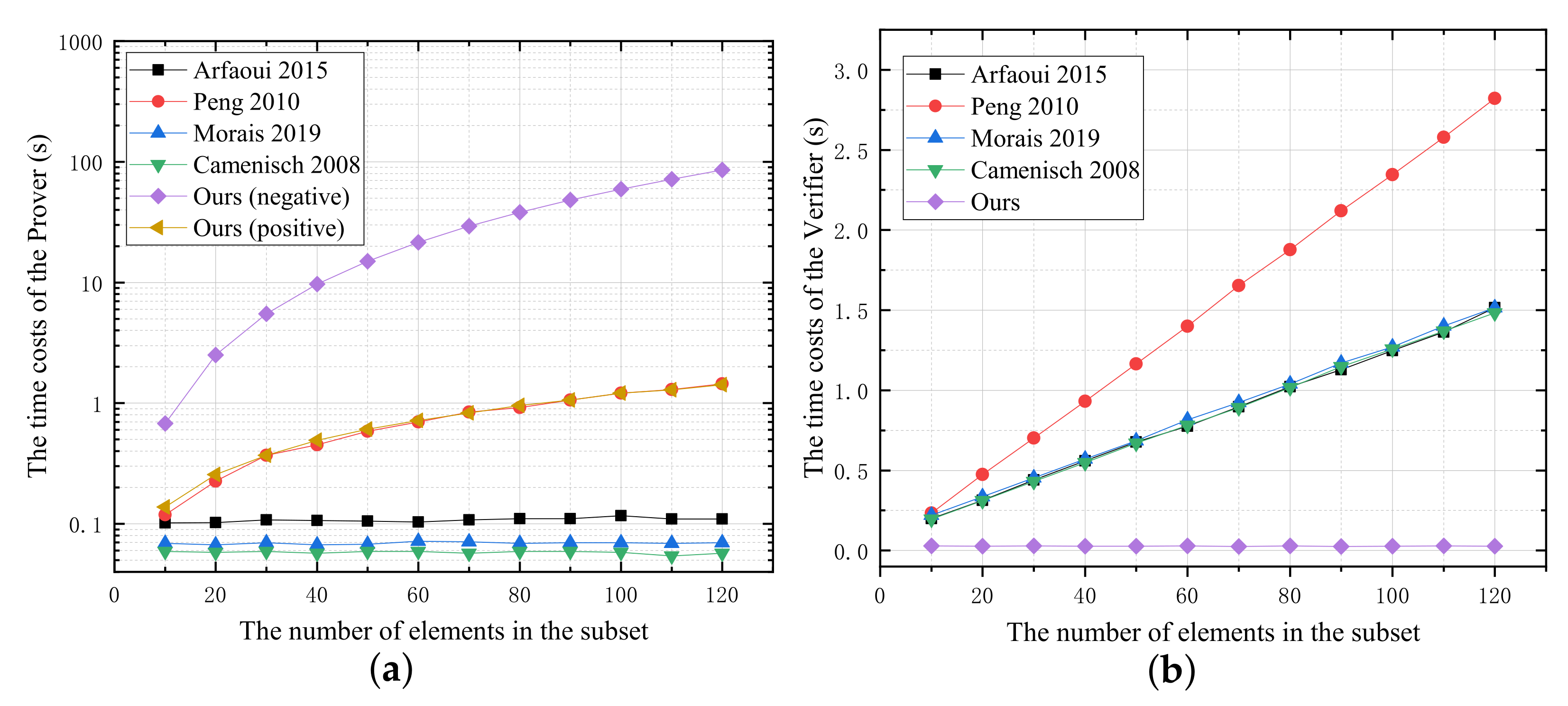
As shown in
Figure 5, we compare the computation overheads of these protocols in the experiments. From
Figure 5a, it is obvious that the time costs of the prover in the negative membership decision in our protocol is more expensive than those of the others. The reason is that the prover in our interactive protocol will compute the poles-based aggregation function, which requires a lot of exponentiation operations in
. In our positive membership decision, the time costs of the prover are similar to that in [
25], which is higher than that in [
24,
28,
34]. In the other hand, as shown in
Figure 5b, the time costs of our verifier are constant and less than that of the other four protocols, which are consistent with the theoretical analysis.
By using the aforementioned setup and tools, we simulate the aggregation algorithms (see [
31]) and show the results of experiments in
Figure 6. As shown in this figure, our poles-based aggregation takes longer than the zeros-based aggregation for the same number of elements in the subset. This is because, the PoleAggr needs to perform more exponential operations than that of ZeroAggr and this operation is more time-consuming than others. Specifically, in the PoleAggr, the number of exponential operations is exponentially related to the number of subset elements, however, that of ZeroAggr is linear with the number of subset elements.
Our ZKDMP is executed by a three-move interaction between a prover and a verifier. In order to clearly describe the protocol, we split the interaction into three functions, i.e.,
,
and
. Specifically, the first two functions are run by the prover and the last one is by the verifier. The details of these three functions are described in Algorithms 1 and 2. The pseudocodes of our protocol is provided in Algorithm 3. It is not difficult to see that three aforementioned functions are simple and concise. Therefore, our ZKDMP protocol (Algorithm 4) has a simple and easy-to-understand structure.
| Algorithm 1: |
- 1:
randomly pick - 2:
- 3:
- 4:
|
| Algorithm 2: |
- 1:
ifthen - 2:
- 3:
else - 4:
- 5:
end if - 6:
- 7:
|
| Algorithm 3: |
- 1:
- 2:
ifthen - 3:
- 4:
- 5:
else - 6:
- 7:
end if
|
| Algorithm 4: |
- 1:
Prover runs and sends to Verifier - 2:
Verifier randomly picks and subset and sends them to Prover - 3:
Prover runs and sends to Verifier - 4:
Verifier runs and outputs
|
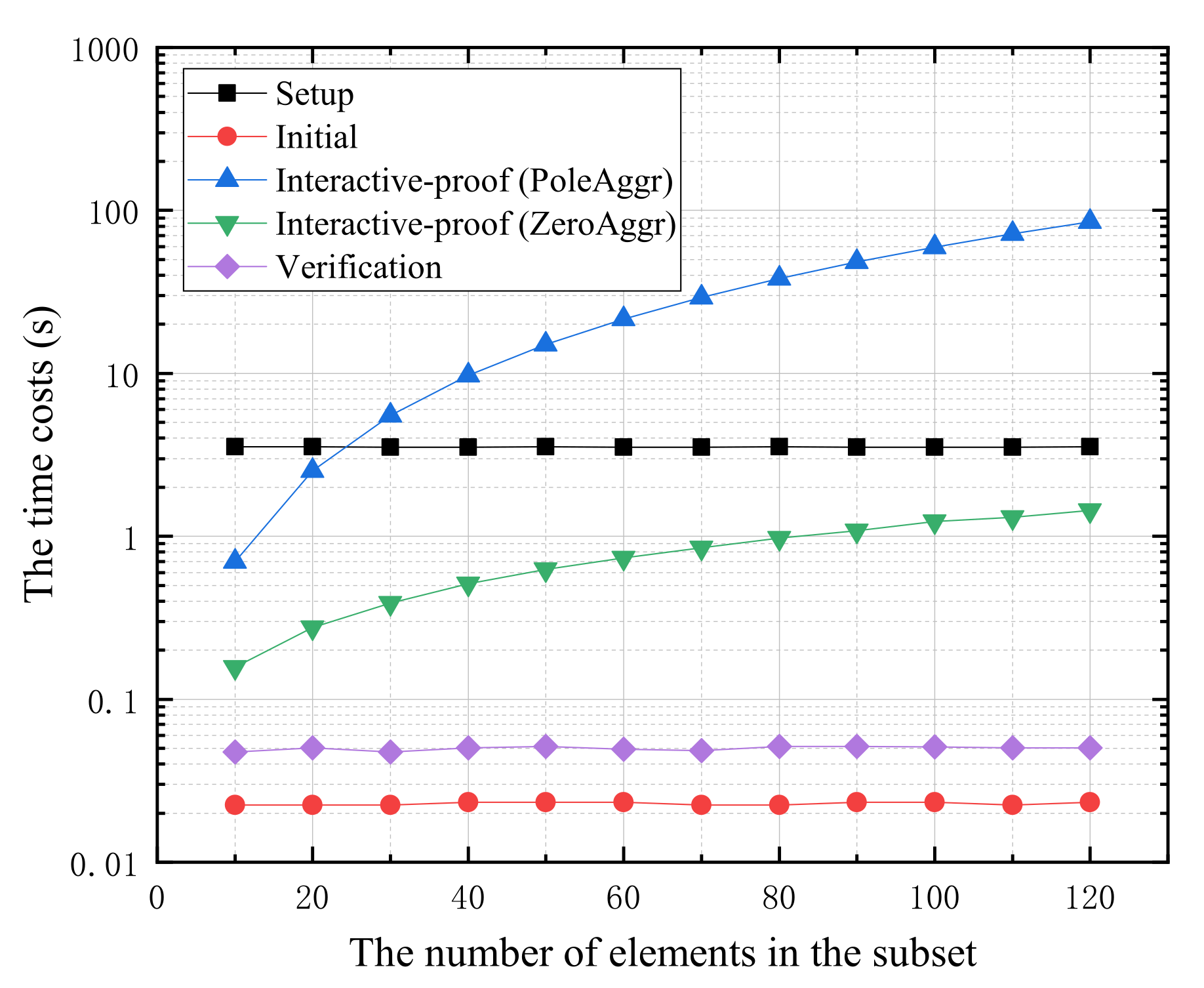
Moreover, we implement our ZKDMP and evaluate the overheads of the Setup and three stages in the interactive protocol, including initial, interactive-proof and verification. As shown in
Figure 7, the time costs of the Setup, initial and verification are constants. In the interactive-proof stage, the main overheads come from the calculation of the aggregation functions. Specifically, the time costs of the positive set membership is exponential with the number of elements in
, that of negative set membership is linear with the number of elements in
.
8. Conclusions
In this paper, we focus on the cryptographic principle and construction for secure membership decision in set theory. Firstly, we formalize the security of the aggregator, and then use ZeroAggr and PoleAggr to compress an arbitrary-size subset into an element in the cryptospace for achieving the secure representation of the subset. Secondly, this paper provides the concept of SDM and uses the zeros-based and poles-based secure representation of the subset to decide the Pos-and-Neg membership, respectively. Finally, we propose the ZKDMP protocol for supporting strict Pos-and-Neg membership decisions. In addition, our aggregation functions are proved to be secure under the t-SDH assumption and the proposed ZKDMP protocol has positive completeness, negative completeness, soundness and zero-knowledge. Moreover, the performance evaluation shows that the ZKDMP protocol has a simple and easy-to-understand structure. In future work, the aggregation complexity will be optimized, i.e., parallelized algorithm, to improve the decision efficiency of the ZKDMP protocol. On the other hand, the secure aggregation functions should be widely applied to construct other cryptosystems, such as attribute-based encryption, broadcast encryption and role-based encryption.