An Effective Security Requirements Engineering Framework for Cyber-Physical Systems
Abstract
1. Introduction
1.1. Why Security Requirements Engineering for CPS
1.2. Security Issues around Sensor Networks
2. Related Work
3. Risk Assessment, Security Goals and Threats for CPS
3.1. Security Goals of Cyber-Physical System
3.1.1. Authentication
3.1.2. Availability
3.1.3. Integrity
3.1.4. Confidentiality
3.2. Threats of Cyber-Physical Systems
3.2.1. Eavesdropping
3.2.2. Compromised-Key Attack
3.2.3. Man-in-the-Middle Attack
3.2.4. Denial-of-Service Attack
3.2.5. Physical Attack & Natural Disaster
3.2.6. Unauthorized Access
3.2.7. Radio Frequency Jamming
3.2.8. Protocol Failures
4. Proposed Security Requirements Engineering Framework for CPS
5. How to Apply CPS Framework
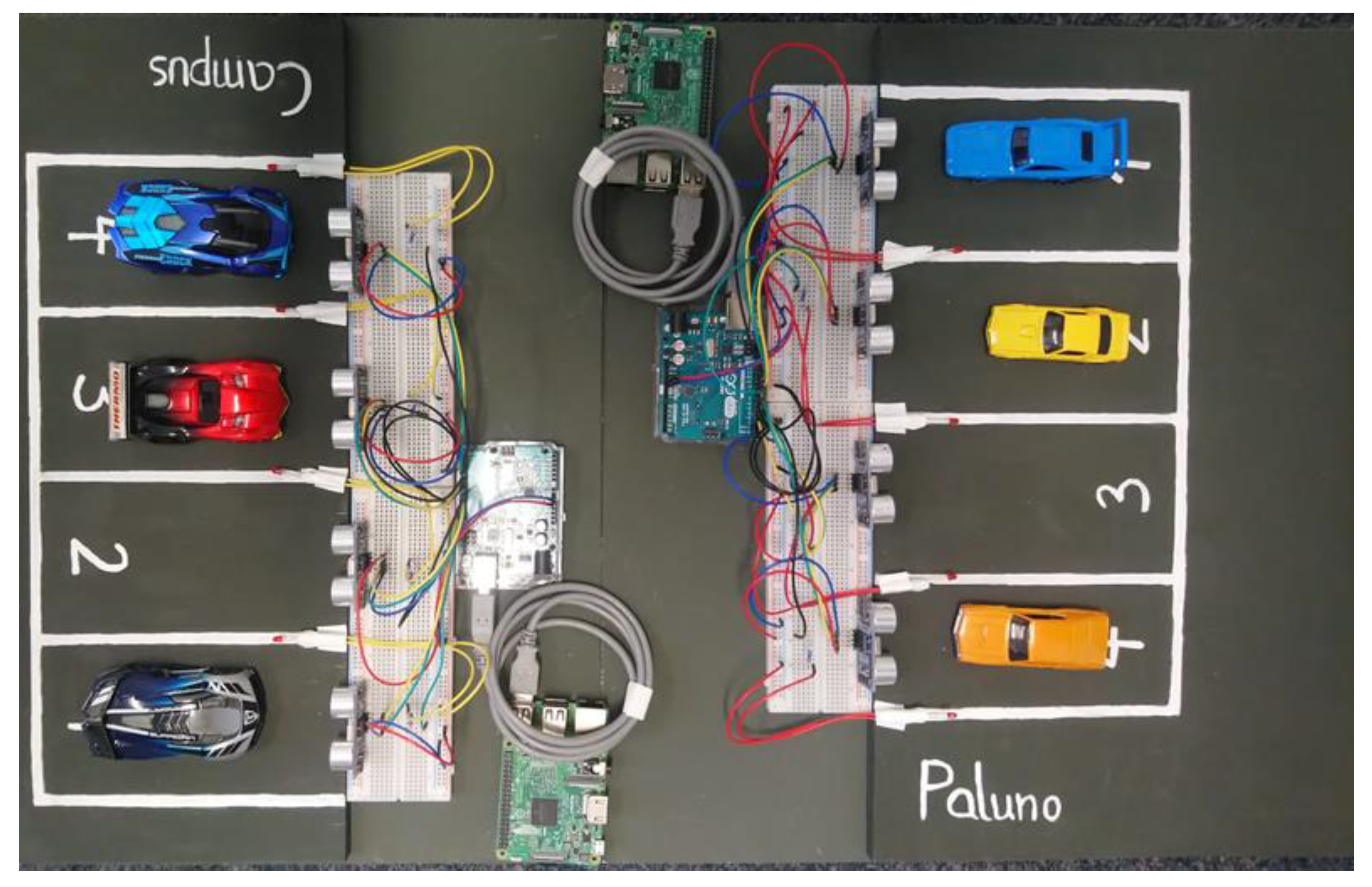
6. Case Study
- Confidentiality: confidentiality is the major element of security goals. The user and vehicle data shall not disclose personal information to an unauthorized person.
- Integrity: data is strongly related to the accuracy of the system. Therefore, its integrity is important. Any unwanted update can cause extreme issues, such as two users claiming one parking space, which can cause an issue over vehicle and user ownership, or even accidents by providing improper free lot information.
- Authorization: the system shall require strong authorization while accessing data, as it manages several user’s information simultaneously. Third-party sensor authorization is also needed because it affects the system’s accuracy and privacy. Therefore, it is important to ensure the device’s good operation due to system criticality.
- Role-based access control: different authorized users have various roles in the system. These roles define the access limit to a diverse data set, hardware, or screens present in the system. The system maintains the access control list to define the assigned task of reachability in the resources. This can be facilitated by login id, profile detail, port, network channel, and important addresses.
- Robustness: the system should have a backup or alternate servers, sensors, and electricity sources to provide a timely response if any failure occurs.
- Availability of data: this means that requested data shall be available when it is needed. Therefore, it is important that the system should be responsive all the time or at a specified time.
- Contractual integrity: third-party hardware, software, and network providers should properly follow a written contractual definition.
- User data
- Vehicular data
- Channel of data
- Server
- Database system
- Arduino
- Raspberry pi
- Sensors
- Data sniffing: over the channel or from the server, a sniffer can get user data over the transfer channel of the user app or database server. This could happen if encryption is absent.
- Data manipulation without backup.
- Data tampering: through unauthorized or authorized access. This needs a strong authorization process for critical data.
- Physical sensor not responding: an attacker could steal or damage the sensor.
- Data conversion is not working: the digital to analogue conversion after vehicle “id” is processed could face issues. This could happen because its hardware system or software is malfunctioning.
- Electricity breakdown: intentional or unintentional electricity blackouts cause smooth processing of the process.
- Data transfer is diverted to unauthorized alternative database: an attacker can transfer stored data to an alternative, unauthorized database.
- Weak internet connection while updating: poor network bandwidth. Low bandwidth can cause slow updating or data transfer.
- The central server is not responding: central server does not respond to user or app server because of a malicious action. This could lead to data loss.
- Database storage system hardware.
- Sensor nodes.
- Network wires.
- Routers.
- Hubs.
- Receiver.
- Senses.
- Computers that provides facility for software manipulation.
- User tablets, iphone or android devices.
7. Comparison of Results
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Rehman, S.; Gruhn, V. Recommended Architecture for Car Parking Management System based on Cyber-Physical System. In Proceedings of the International Conference on Engineering & MIS, Monastir, Tunisia, 8–10 May 2017. [Google Scholar]
- Kalloniatis, C.; Kavakli, E.; Gritzalis, S. Addressing privacy requirements in system design: The PriS method. Requir. Eng. 2008, 13, 241–255. [Google Scholar] [CrossRef]
- Zhang, L. A framework to specify big data driven complex cyber physical control systems. In Proceedings of the 2014 IEEE International Conference on 2014 Information and Automation (ICIA), Hailar, China, 28–30 July 2014; pp. 548–553. [Google Scholar]
- Beckers, K.; Faßbender, S.; Hatebur, D.; Heisel, M.; Côté, I. Common criteria compliant software development (CC-CASD). In Proceedings of the 28th Annual ACM Symposium on Applied Computing, Coimbra, Portugal, 18–22 March 2013; pp. 1298–1304. [Google Scholar]
- Lund, M.S.; Solhaug, B.; Stølen, K. Model-Driven Risk Analysis: The CORAS Approach; Springer Science & Business Media: New York, NY, USA, 2010. [Google Scholar]
- CC: ISO/IEC 15408 Information Technology—Security Technology—Evaluation Criteria for IT Security V2.1. Available online: https://www.iso.org/standard/50341.html (accessed on 1 December 2009).
- Van Lamsweerde, A. Goal-Oriented Requirements Engineering: A Guided Tour. In Proceedings of the RE’01: 5th International Symposium on Requirements Engineering, Toronto, ON, Canada, 27–31 August 2001. [Google Scholar]
- Jürjens, J. UMLsec: Extending UML for secure systems development. In Proceedings of the «UML» 2002—The Unified Modeling Language, Dresden, Germany, 20 September 2002; pp. 1–9. [Google Scholar]
- Leitão, P.; Colombo, A.W.; Karnouskos, S. Industrial automation based on cyber-physical systems technologies: Prototype implementations and challenges. Comput. Ind. 2016, 81, 11–25. [Google Scholar] [CrossRef]
- Cleveland, F. Cyber Security Issues for Advanced Metering Infrastructure (AMI). In Proceedings of the IEEE Power and Energy Society General Meeting-Conversion and Delivery of Electrical energy in the 21st Century, Pittsburgh, PA, USA, 20–24 July 2008. [Google Scholar]
- Rehman, S.; Gruhn, V. Security Requirements Engineering (SRE) Framework for Cyber-Physical Systems (CPS): SRE for CPS. In Proceedings of the 16th International Conference on Intelligent Software Methodologies, Tools, and Techniques (SOMET_17), Kyushu, Japan, 26–28 September 2017. [Google Scholar]
- Ramachandran, M. Software security requirements management as an emerging cloud computing service. Int. J. Inf. Manag. 2016, 36, 580–590. [Google Scholar] [CrossRef]
- Mead, N.R. How to Compare the Security Quality Requirements Engineering (SQUARE) Method with Other Methods (No. CMU/SEI-2007-TN-021); Carnegie Mellon University Software Engineering Institute: Pittsburgh, PA, USA, 2007. [Google Scholar]
- Yoo, H.; Shon, T. Challenges and research directions for heterogeneous cyber–physical system based on IEC 61850: Vulnerabilities, security requirements, and security architecture. Future Gener. Comput. Syst. 2016, 61, 128–136. [Google Scholar] [CrossRef]
- Liu, Y.; Peng, Y.; Wang, B.; Yao, S.; Liu, Z. Review on cyber-physical systems. IEEE/CAA J. Autom. Sinica 2017, 4, 27–40. [Google Scholar] [CrossRef]
- Subramanian, N.; Zalewski, J. Quantitative assessment of safety and security of system architectures for cyber-physical systems using the NFR approach. IEEE Syst. J. 2016, 10, 397–409. [Google Scholar] [CrossRef]
- Conforti, R.; de Leoni, M.; La Rosa, M.; van der Aalst, W.M.; ter Hofstede, A.H. A recommendation system for predicting risks across multiple business process instances. Decis. Support Syst. 2015, 69, 1–19. [Google Scholar] [CrossRef]
- Slay, J.; Miller, M. Lessons learned from the maroochy water breach. In Proceedings of the International Conference on Critical Infrastructure Protection, Boston, MA, USA, 19 March 2007; pp. 73–82. [Google Scholar]
- Cárdenas, A.A.; Amin, S.; Lin, Z.S.; Huang, Y.L.; Huang, C.Y.; Sastry, S. Attacks Against Process Control Systems: Risk Assessment, Detection, and Response. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 22–24 March 2011; ACM: New York, NY, USA, 2011; pp. 355–366. [Google Scholar]
- Ashford, W. On-Demand Service Aims to Cut Cost of Fixing Software Security Flaws. Available online: http://www.computerweekly.com/Articles/2009/07/14/236875/on-demand-service-aims-to-cut-cost-of-fixing-software-security.htm (accessed on 10 July 2018).
- Gartner. Available online: http://www.gartner.com/newsroom/id/2828722 (accessed on 1 August 2014).
- CERT-SEI. Available online: www.cert.org (accessed on 1 September 2016).
- CERT-UK. Available online: https://www.cert.gov.uk/ (accessed on 1 March 2016).
- Ur Rehman, S.; Khan, M.U. Security and Reliability Requirements for a Virtual Classroom. Procedia Comput. Sci. 2016, 94, 447–452. [Google Scholar] [CrossRef]
- Robles, R.J.; Kim, T.H. Applications, Systems and Methods in Smart Home Technology: A review. Int. J. Adv. Sci. Technol. 2010, 15, 37–48. [Google Scholar]
- Tondel, I.A.; Jaatun, M.G.; Meland, P.H. Security requirements for the rest of us: A survey. IEEE Softw. 2008, 2, 20–25. [Google Scholar] [CrossRef]
- Shahzad, M.; Shafiq, M.Z.; Liu, A.X. A large scale exploratory analysis of software vulnerability life cycles. In Proceedings of the 34th International Conference on Software Engineering, Zurich, Switzerland, 2–9 June 2012; pp. 771–781. [Google Scholar]
- Almorsy, M.; Grundy, J.; Müller, I. An analysis of the cloud computing security problem. arXiv, 2016; arXiv:1609.01107. [Google Scholar]
- Salini, P.; Kanmani, S. Survey and analysis on security requirements engineering. Comput. Electr. Eng. 2012, 38, 1785–1797. [Google Scholar] [CrossRef]
- Khan, M.U.A.; Zulkernine, M. Quantifying security in secure software development phases. In Proceedings of the 2008 32nd Annual IEEE International Computer Software and Applications Conference, Turku, Finland, 28 July–1 August 2008; pp. 955–960. [Google Scholar]
- Khan, M.U.A.; Zulkernine, M. On selecting appropriate development processes and requirements engineering methods for secure software. In Proceedings of the 2009 33rd Annual IEEE International Computer Software and Applications Conference, Seattle, WA, USA, 20–24 July 2009; Volume 2, pp. 353–358. [Google Scholar]
- McGraw, G. Software Security: Building Security In, Addison Wesley. In Proceedings of the 2006 17th International Symposium on Software Reliability Engineering, Raleigh, NC, USA, 7–10 November 2006. [Google Scholar]
- Perrig, A.; Stankovic, J.; Wagner, D. Security in wireless sensor networks. Commun. ACM 2004, 47, 53. [Google Scholar] [CrossRef]
- Yan, Q.; Yu, F.R.; Gong, Q.; Li, J. Software-defined networking (SDN) and distributed denial of service (DDoS) attacks in cloud computing environments: A survey, some research issues, and challenges. IEEE Commun. Surv. Tutor. 2016, 18, 602–622. [Google Scholar] [CrossRef]
- Martins, D.; Guyennet, H. Wireless sensor network attacks and security mechanisms: A short survey. In Proceedings of the 13th International Conference on 2010 Network-Based Information Systems (NBiS), Gifu, Japan, 14–16 September 2010; pp. 313–320. [Google Scholar]
- Mead, N.R.; Stehney, T. Security Quality Requirements Engineering (SQUARE) Methodology; ACM: New York, NY, USA, 2005; Volume 30, pp. 1–7. [Google Scholar]
- Mead, N.; Viswanathan, V.; Padmanabhan, D. Incorporating Security Quality Requirements Engineering (SQUARE) into Standard Life-Cycle Models; Technical Note, CMU/SEI-2008-TN-006; Software Engineering Institute, Carnegie Mellon University: Pittsburgh, PA, USA, 2008. [Google Scholar]
- Mellado, D.; Fernández-Medina, E.; Piattini, M. Applying a security requirements engineering process. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2006; pp. 192–206. [Google Scholar]
- Mellado, D.; Fernández-Medina, E.; Piattini, M. A common criteria based security requirements engineering process for the development of secure information systems. Comput. Stand. Interfaces 2007, 29, 244–253. [Google Scholar] [CrossRef]
- Lee, J.; Lee, J.; Lee, S.; Choi, B. A CC-based security engineering process evaluation model. In Proceedings of the 27th Annual International Computer Software and Applications Conference on COMPAC 2003, Dallas, TX, USA, 3–6 November 2003; pp. 130–135. [Google Scholar]
- Feng, N.; Wang, H.J.; Li, M. A security risk analysis model for information systems: Causal relationships of risk factors and vulnerability propagation analysis. Inf. Sci. 2014, 56, 57–73. [Google Scholar] [CrossRef]
- Stolen, K.; den Braber, F.; Dimitrakos, T.; Fredriksen, R.; Gran, B.A.; Houmb, S.H.; Aagedal, J.O. Model-based risk assessment–the CORAS approach. In Proceedings of the NIK (2002) Informatics Conference, Kongsberg, Norway, 25–27 November 2002. [Google Scholar]
- Dimitrakos, T.; Ritchie, B.; Raptis, D.; Stølen, K. Model-based security risk analysis for Web applications: The CORAS approach. In Proceedings of the EuroWeb, Oxford, UK, 17–18 December 2002. [Google Scholar]
- Viega, J. Building security requirements with CLASP. In Proceedings of the ACM SIGSOFT Software Engineering Notes, St. Louis, Missouri, 15–16 May 2005; ACM: New York, NY, USA, 2005; Volume 30, pp. 1–7. [Google Scholar]
- De Win, B.; Scandariato, R.; Buyens, K.; Grégoire, J.; Joosen, W. On the secure software development process: CLASP, SDL and Touchpoints compared. Inf. Softw. Technol. 2009, 51, 1152–1171. [Google Scholar] [CrossRef]
- Mouratidis, H.; Argyropoulos, N.; Shei, S. Security requirements engineering for cloud computing: The secure tropos approach. In Domain-Specific Conceptual Modeling; Springer: Cham, Switzerland, 2016; pp. 357–380. [Google Scholar]
- Pavlidis, M.; Mouratidis, H.; Panaousis, E.; Argyropoulos, N. Selecting Security Mechanisms in Secure Tropos. In Proceedings of the International Conference on Trust and Privacy in Digital Business, Lyon, France, 28–31 August 2017; Springer: Cham, Switzerland, 2017; pp. 99–114. [Google Scholar]
- Hatebur, D.; Heisel, M.; Jürjens, J.; Schmidt, H. Systematic development of UMLsec design models based on security requirements. In Proceedings of the International Conference on Fundamental Approaches to Software Engineering 2011, Saarbrücken, Germany, 26 March–3 April 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 232–246. [Google Scholar]
- Mouratidis, H.; Jurjens, J. From goal-driven security requirements engineering to secure design. Int. J. Intell. Syst. 2010, 25, 813–840. [Google Scholar] [CrossRef]
- Mellado, D.; Mouratidis, H.; Fernández-Medina, E. Secure Tropos framework for software product lines requirements engineering. Comput. Stand. Interfaces 2014, 36, 711–722. [Google Scholar] [CrossRef]
- Ericsson, G.N. Cyber security and power system communication essential parts of a smart grid infrastructure. IEEE Trans. Power Deliv. 2010, 25, 1501–1507. [Google Scholar] [CrossRef]
- Sridhar, S.; Manimaran, G. Data integrity attacks and their impacts on SCADA control system. In Proceedings of the IEEE PES General Meeting, Providence, RI, USA, 25–29 July 2010; pp. 1–6. [Google Scholar]
- Oh, S.-R.; Kim, Y.-G. Security Requirements Analysis for the IoT. In Proceedings of the 2017 International Conference on Platform Technology and Service (PlatCon), Busan, South Korea, 13–15 February 2017; pp. 1–6. [Google Scholar]
- Burmester, M.; Magkos, E.; Chrissikopoulos, V. Modeling security in cyber–physical systems. Int. J. Crit. Infrastruct. Prot. 2012, 5, 118–126. [Google Scholar] [CrossRef]
- Zeng, K. Physical layer key generation in wireless networks: Challenges and opportunities. IEEE Commun. Mag. 2015, 53, 33–39. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Wen, S. The fog computing paradigm: Scenarios and security issues. In Proceedings of the 2014 Federated Conference on Computer Science and Information Systems (FedCSIS), Warsaw, Poland, 7–10 September 2014; pp. 1–8. [Google Scholar]
- Zhu, B.; Joseph, A.; Sastry, S. A taxonomy of cyber-attacks on SCADA systems. In Proceedings of the Internet of Things (iThings/CPSCom) 2011 International Conference on and 4th International Conference on Cyber, Physical and Social Computing, Washington, DC, USA, 9–22 October 2011; pp. 380–388. [Google Scholar]
- Rajkumar, R.R.; Lee, I.; Sha, L.; Stankovic, J. Cyber-physical systems: The next computing revolution. In Proceedings of the 47th Design Automation Conference, Anaheim, CA, USA, 13–18 June 2010; ACM: New York, NY, USA, 2010; pp. 731–736. [Google Scholar]
- Farooq, M.U.; Waseem, M.; Khairi, A.; Mazhar, S. A critical analysis on the security concerns of internet of things (IoT). Int. J. Comput. Appl. 2015, 111. Available online: http://www.pcporoje.com/filedata/592496.pdf (accessed on 10 July 2018).
- Khoo, B. RFID as an enabler of the internet of things: Issues of security and privacy. In Proceedings of the Internet of Things (iThings/CPSCom), 2011 International Conference on and 4th International Conference on Cyber, Physical and Social Computing, Dalian, China, 19–22 October 2011; pp. 709–712. [Google Scholar]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Sindre, G.; Opdahl, A.L. Eliciting security requirements with misuse cases. Requir. Eng. 2005, 10, 34–44. [Google Scholar] [CrossRef]
- Suleiman, H.; Svetinovic, D. Evaluating the effectiveness of the security quality requirements engineering (SQUARE) method: A case study using smart grid advanced metering infrastructure. Requir. Eng. 2013, 18, 251–279. [Google Scholar] [CrossRef]
- Zafar, N.; Arnautovic, E.; Diabat, A.; Svetinovic, D. System security requirements analysis: A smart grid case study. Syst. Eng. 2014, 17, 77–88. [Google Scholar] [CrossRef]
- Gopal, T.; Subbaraju, M.; vivek Joshi, R.; Dey, S. MAR (S) 2: Methodology to articulate the requirements for security in SCADA. In Proceedings of the 2014 Fourth International Conference on Innovative Computing Technology (INTECH), Luton, UK, 13–15 August 2014; pp. 103–108. [Google Scholar]
- Souag, A.; Mazo, R.; Salinesi, C.; Comyn-Wattiau, I. Reusable knowledge in security requirements engineering: A systematic mapping study. Requir. Eng. 2016, 21, 251–283. [Google Scholar] [CrossRef]
- Mir, T.M.; Revuru, A.K.V.; Manohar, D.J.; Batta, V. Microsoft Corporation, 2012. Threat Analysis and Modeling during a Software Development Lifecycle of a Software Application. U.S. Patent 8,091,065, 3 January 2012. [Google Scholar]
- Jürjens, J. Secure Systems Development with UML; Springer Science & Business Media: Berlin, Germany, 2005. [Google Scholar]
- Mouratidis, H.; Giorgini, P. Secure tropos: A security-oriented extension of the tropos methodology. Int. J. Softw. Eng. Knowl. Eng. 2007, 17, 285–309. [Google Scholar] [CrossRef]
- Labunets, K.; Massacci, F.; Paci, F. An experimental comparison of two risk-based security methods. In Proceedings of the 2013 ACM/IEEE International Symposium on Empirical Software Engineering and Measurement, Baltimore, MD, USA, 10–11 October 2013; pp. 163–172. [Google Scholar]
- Fredriksen, R.; Kristiansen, M.; Gran, B.A.; Stølen, K.; Opperud, T.A.; Dimitrakos, T. The CORAS framework for a model-based risk management process. In Proceedings of the InInternational Conference on Computer Safety, Reliability, and Security, Catania, Italy, 10–13 September 2002; Volume 2, pp. 94–105. [Google Scholar]



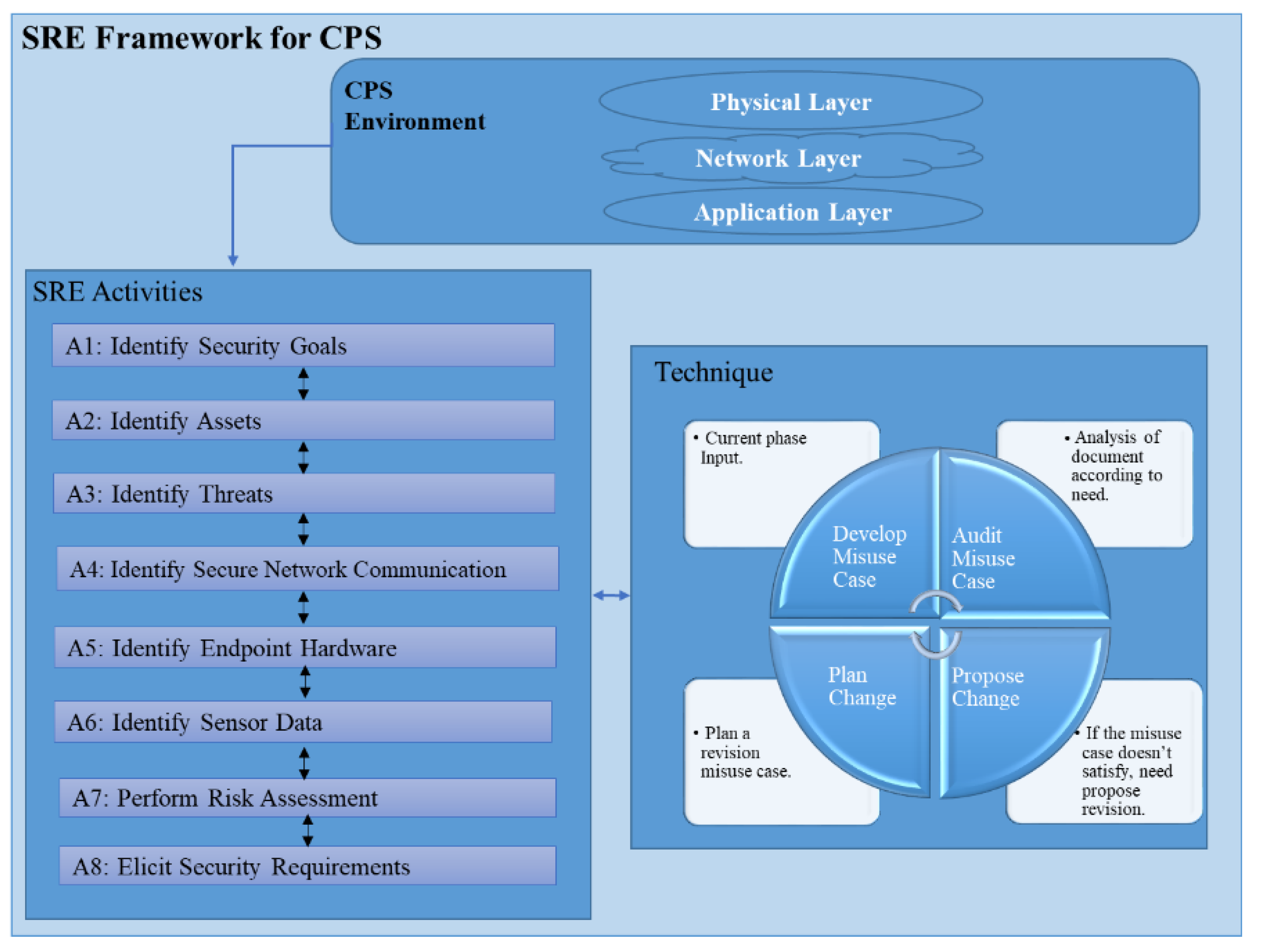
| Activity | Input | Technique | Output |
|---|---|---|---|
| A1: Identify security goals | Business goals, quality attributes | Misuse case, workshop session, interview, survey | List of security goals |
| A2: Identify assets | Entity of properties & their interaction | Misuse case, workshop session, detail analysis | List of CPS assets |
| A3: Identify threats | General list of CPS, list of security goals & assets | Misuse case, brainstorming session, questionnaire | List of CPS threats |
| A4: Identify secure network communication | Types of communication, protocol | Misuse case, analysis and comparison | List of secure network communication |
| A5: Identify endpoints hardware | All possible endpoints hardware, list of hardware vendors | Misuse case, group discussion | List of endpoint hardware and accepted vendors |
| A6: Identify sensor communication medium | Types of sensor | Misuse case, analysis and comparison | List of sensor types |
| A7: Perform Risk assessment | Impact of attacker capabilities, list of assets & threats | Risk cost factor calculation based on impact, risk ranking | Risk cost factor, risk rank result |
| A8: Elicit security requirements | list of security goals, assets & threats, risk result | Analysis, group discussion, interviews | List of security requirements |
| Risk ID | Event | Threat | Asset | Impact | Risk Cost |
|---|---|---|---|---|---|
| Rk1 | Data authorized access | Misuse of data | Database | 4: Critical data integrity lost. Information is no longer confidential | 4 + 4 + 4 + 4 = 16 |
| User | 4: Data can be misused, Misguidance to the user | ||||
| Parking | 4: Misguidance | ||||
| Vehicular data | 4: Can cause stealing | ||||
| Rk2 | Vehicular no. reading publication/stolen | Pass to unauthorized channel/data base | Database | 4: No record | 4 + 4 + 3 + 3 = 14 |
| 4: Malicious record | |||||
| Communication channel | 3: No direct impact, however it’s been tampered | ||||
| User | 3: private data | ||||
| Rk3 | Data conversion malfunction | Wrong record updated. | User | 3: Wrong information across valid user | 3 + 3 + 3 = 9 |
| Garbage data store | Database | 3: no data updated | |||
| parking | 3: Wrong information across valid user | ||||
| Rk4 | Sensor not responding | Sensor stolen | Database | 2: No direct effect, no data update, hence no working process | 2 + 1 + 4 + 1 + 4 = 12 |
| Communication channel | 1: No data transfer | ||||
| User | 4: No information generated | ||||
| Parking location | 1: No information generated and no information transfer | ||||
| sensor | 4: No functional system | ||||
| RK6 | Unencrypted channel | Critical data disclosed | Communication channel | 4: Lost of trust | 4 + 4 + 4 + 4 + 3 = 19 |
| Database | 4: Not updated | ||||
| User | 4: Lost of trust and user data is disclosed | ||||
| Parking | 3: Not function properly | ||||
| App and webpage | 4: Loss of trust and malfunctioning | ||||
| Rk5 | Internet connection failed | Weak internet connection while updating | Database | 4: No data processing | 4 + 4 + 4 = 12 |
| App and webpage | 4: No Application usage | ||||
| User | 4: Dissatisfaction | ||||
| Rk7 | Sensor data- not generated/encrypted | Sensor malfunction or stolen | Sensor | 4: Not function properly | 4 + 2 + 3 + 3 = 12 |
| User | 2: frustration | ||||
| 3: Private data lost | |||||
| Database | 3: Data privacy compromise | ||||
| Rk8 | Data manipulated | Channel diverted | Database | 4: Noise data | 4 + 4 + 4 + 3 + 4 + 3 = 22 |
| 4: Data integrity lost | |||||
| User | 4: User data privacy effected | ||||
| Communication channel | 3: Malicious data transfer | ||||
| Parking location | 4: Malicious information generated and no information transfer | ||||
| Server | 3: May receive error code or useless data | ||||
| Rk9 | Overloaded channel | Channel diverted | Database | 3: Unwanted data generated | 3 + 4 + 4 + 3 + 4 + 4 + 3 = 25 |
| User | 4: User data privacy effected | ||||
| Car | 4: User data privacy effected | ||||
| Communication channel | 3: Malicious data transfer | ||||
| 4: data transfer to another server | |||||
| Parking location | 4: Malicious information generated and no information transfer | ||||
| Server | 3: Not receiving any data or malicious data |
| No. | Security Requirements (SR) |
|---|---|
| SR-1 | The system shall have strong authentication. |
| SR-2 | The system shall be knowledgeable of spoofing in the car parking database. |
| SR-3 | The system shall monitor unauthorized modification of car parking database. |
| SR-4 | The system shall prevent malicious malware in the car parking database. |
| SR-5 | The system shall control unauthorized access of car parking database. |
| SR-6 | The system shall control unauthorized modification to the communication between a server and user application. |
| SR-7 | The system shall monitor unauthorized access to communication between a server and user application. |
| SR-8 | The system shall monitor Denial-of-Service (DoS) attacks on the car parking database. |
| SR-9 | The system shall require special security that should be maintained for hardware supports. |
| SR-10 | The system shall protect 3rd-party software for sensor support. |
| SR-11 | The system shall provide alternative sensors for smooth processing. |
| SR-12 | The system shall provide alarm notification in case of missing hardware. |
| SR-13 | The system shall require network communications to be protected. Encryption should be established. |
| SR-14 | The system shall require network communication receivers that should be audited on a frequent basis. To ensure its security from viruses and data sniffers. |
| SR-15 | Data channels should be encrypted. |
| SR-16 | A continuous data channel audit mechanism should be present. |
| SR-17 | Channel load should be monitored. |
| SR-18 | A channel-dedicated IP list should be maintained. |
| SR-19 | Data receiving IPs should be checked from the authorized ones to ensure the absence of unsecure recovery. |
| SR-20 | The system database should have different access levels per stakeholders.Critical data should be encrypted and password protected. |
| SR-21 | Car data (user information) should be protected with passwords. |
| SR-22 | Role-based access control over the data should be ensured. |
| SR-23 | Alternative sensors, recovery routers and network cables should be in place to ensure timely recovery and minimal response time. |
| SR-24 | The system shall provide a stable internet connection. |
| SR-25 | The internet connection should be secured by a password. Internet must be protected through a passcode based on car id or user id to ensure use by a dedicated user. |
| SR-26 | The system shall provide automatic connection to an alternative internet that should be ensured in times of failure. |
| SR-27 | In the case of sensors/actuators damage or theft, the system shall be protected with an alarm, and the administrator shall be notified. |
| SR-28 | The data should not be diverted or transferred through the network communication. |
| SR-29 | The sending of data from sensor to gateway cannot be readable by an unauthorized user. |
| SR-30 | The sending of data from gateway to server cannot be readable by an unauthorized user. |
| SR-31 | There should be an alternate solution, in case sensor or actuator is damaged/stolen. |
| SR-32 | The sensor shall not be able to read the incorrect data from the car parking lot. |
| SR-33 | The sensor shall not be able to send the incorrect data to the data acquisition board. |
| SR-34 | The data acquisition board shall not be able to send incorrect data to the server/controller. |
| SR-35 | The system shall monitor unauthorized replacement of sensors/actuators in the parking lot. |
| SR-36 | The system shall monitor interruption of sensor/actuator. |
| SR-37 | The sensor shall not divert the data into another data acquisition board/server. |
| SR-38 | The system shall provide the necessary damage/theft protection of sensors/actuators. |
| SR-39 | The system shall monitor car parking reservation information from authorized access/modification. |
| SR-40 | The system shall monitor parking lot status information from unauthorized access/modification. |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rehman, S.U.; Gruhn, V. An Effective Security Requirements Engineering Framework for Cyber-Physical Systems. Technologies 2018, 6, 65. https://doi.org/10.3390/technologies6030065
Rehman SU, Gruhn V. An Effective Security Requirements Engineering Framework for Cyber-Physical Systems. Technologies. 2018; 6(3):65. https://doi.org/10.3390/technologies6030065
Chicago/Turabian StyleRehman, Shafiq Ur, and Volker Gruhn. 2018. "An Effective Security Requirements Engineering Framework for Cyber-Physical Systems" Technologies 6, no. 3: 65. https://doi.org/10.3390/technologies6030065
APA StyleRehman, S. U., & Gruhn, V. (2018). An Effective Security Requirements Engineering Framework for Cyber-Physical Systems. Technologies, 6(3), 65. https://doi.org/10.3390/technologies6030065





