Quantum Security Multi-Party Extremum Protocol with Greenberger–Horne–Zeilinger States
Abstract
1. Introduction
2. Preliminary
2.1. Security Multi-Party Extremum
2.2. Greenberger–Horne–Zeilinger States
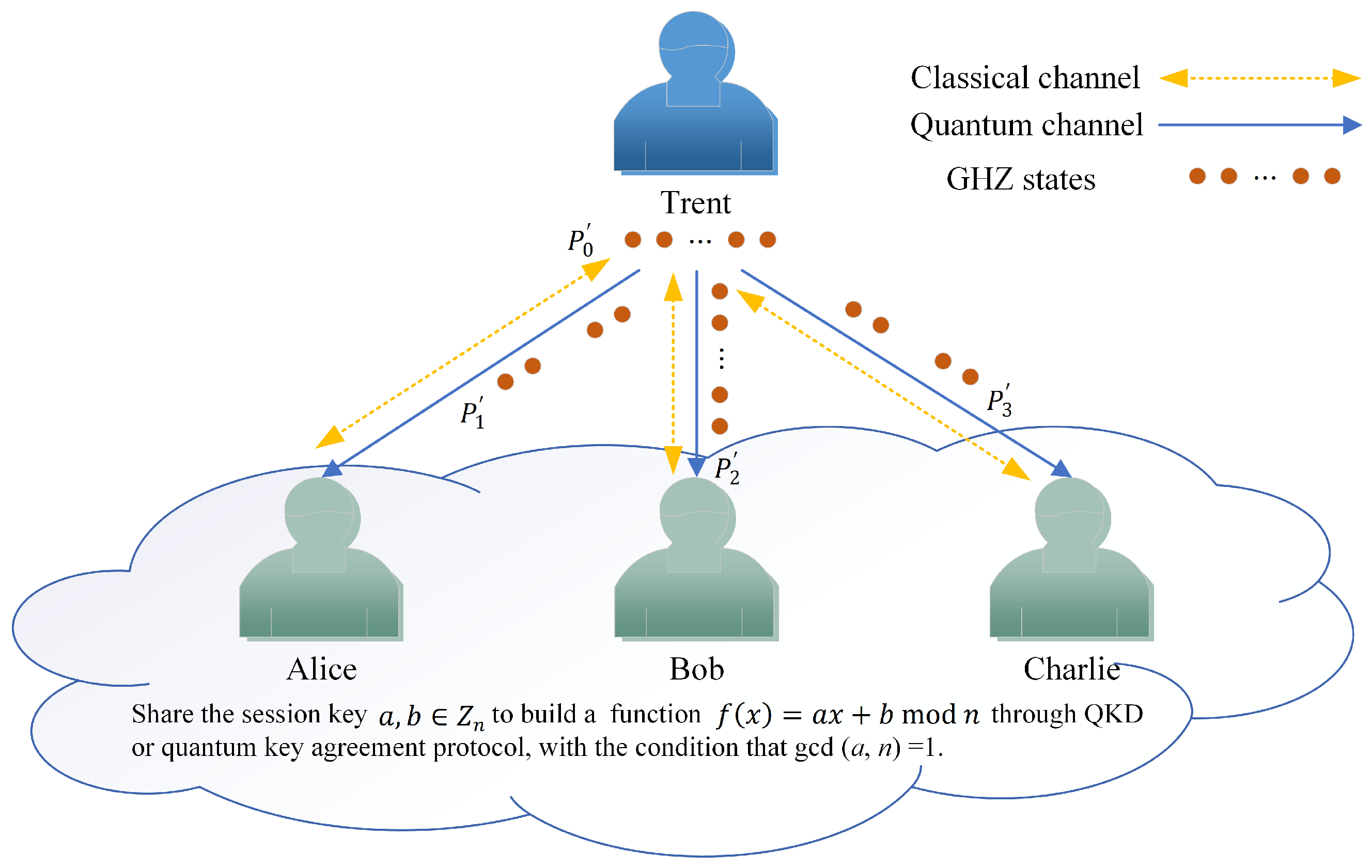
3. Three-Party Protocol
4. Security
4.1. External Attack
4.2. Internal Attack
4.2.1. Dishonest Participant’s Attack
4.2.2. Semi-Honest Third Party’s Attack
5. Scalability
6. Correctness
7. Performance Evaluation
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public-key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, India, 10–12 December 1984; IEEE Computer Society Press: Piscataway, NJ, USA, 1984; pp. 175–179. [Google Scholar]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145. [Google Scholar] [CrossRef]
- Scarani, V.; Pasquinucci, H.B.; Cerf, N.J.; Dusek, M.; Lutkenhaus, N.; Peev, M. The security of practical quantum key distribution. Rev. Mod. Phys. 2009, 81, 1301. [Google Scholar] [CrossRef]
- Meyer, J.; Reches, Y.; Gary Rozenman, G.; Oz, Y.; Suchowski, H.; Arie, A. Analogy of free-space quantum key distribution using spatial modes of light: Scaling up the distance and the dimensionality. Opt. Lett. 2025, 50, 3297. [Google Scholar] [CrossRef]
- Sisodia, M.; Venkataraman, V.; Ghosh, J. FSO-QKD protocols under free-space losses and device imperfections: A comparative study. Quantum Inf. Process. 2024, 23, 5. [Google Scholar] [CrossRef]
- Cleve, R.; Gottesman, D.; Lo, H.K. How to share a quantum secret. Phys. Rev. Lett. 1999, 83, 648. [Google Scholar] [CrossRef]
- Hillery, M.; Bužek, V.; Berthiaume, A. Quantum secret sharing. Phys. Rev. A 1999, 59, 1829. [Google Scholar] [CrossRef]
- Xiao, L.; Long, G.-L.; Deng, F.-G.; Pan, J.-W. Efficient multiparty quantum-secret-sharing schemes. Phys. Rev. A 2004, 69, 052307. [Google Scholar] [CrossRef]
- Lin, S.; Guo, G.; Xu, Y.; Sun, Y.; Liu, X. Cryptanalysis of quantum secret sharing with d-level single particles. Phys. Rev. A 2016, 93, 062343. [Google Scholar] [CrossRef]
- Boström, K.; Felbinger, T. Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 2002, 89, 187902. [Google Scholar] [CrossRef]
- Deng, F.G.; Long, G.L.; Liu, X.S. Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys. Rev. A 2003, 68, 042317. [Google Scholar] [CrossRef]
- Lin, S.; Wen, Q.; Gao, F.; Zhu, F. Quantum secure direct communication with χ-type entangled state. Phys. Rev. A 2008, 78, 064304. [Google Scholar] [CrossRef]
- Yang, Y.-G.; Wen, Q.-Y. An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A-Math. Theor. 2010, 43, 209801. [Google Scholar] [CrossRef]
- Chen, X.B.; Xu, G.; Niu, X.X.; We, W.Y.; Yang, Y.X. An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 2010, 283, 1561–1565. [Google Scholar] [CrossRef]
- Lin, S.; Sun, Y.; Liu, X.-F.; Yao, Z.-Q. Quantum private comparison protocol with d-dimensional Bell states. Quantum Inf. Process. 2013, 12, 559–568. [Google Scholar] [CrossRef]
- Giovannetti, V.; Lloyd, S.; Maccone, L. Quantum private queries. Phys. Rev. Lett. 2008, 100, 230502. [Google Scholar] [CrossRef] [PubMed]
- Jakobi, M.; Simon, C.; Gisin, N.; Branciard, C.; Bancal, J.; Walenta, N.; Zbinden, H. Practical private database queries based on a quantum-key-distribution protocol. Phys. Rev. A 2011, 83, 022301. [Google Scholar] [CrossRef]
- Gao, F.; Qin, S.J.; Huang, W.; Wen, Q. Quantum private query: A new kind of practical quantum cryptographic protocol. Sci. China-Phys. Mech. Astron. 2019, 62, 070301. [Google Scholar] [CrossRef]
- Shi, R.; Mu, Y.; Zhong, H.; Cui, J.; Zhang, S. An efficient quantum scheme for private set intersection. Quantum Inf. Process. 2016, 15, 363–371. [Google Scholar] [CrossRef]
- Liu, W.; Yin, H.W. A novel quantum protocol for private set intersection. Int. J. Theor. Phys. 2021, 60, 2074–2083. [Google Scholar] [CrossRef]
- Chen, Y.M.; Situ, H.; Huang, Q.; Zhang, C. A novel quantum private set intersection scheme with a semi-honest third party. Quantum Inf. Process. 2023, 22, 429. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, W.F.; Zhang, S.B. Quantum multi-party private set intersection using single photons. Physica A 2024, 649, 129974. [Google Scholar] [CrossRef]
- Chen, X.B.; Xu, G.; Yang, Y.X.; Wen, Q.Y. An efficient protocol for the secure multi-party quantum summation. Int. J. Theor. Phys. 2010, 49, 2793–2804. [Google Scholar] [CrossRef]
- Liu, W.; Wang, Y.B.; Fan, W.Q. An novel protocol for the quantum secure multi-party summation based on two-particle bell states. Int. J. Theor. Phys. 2017, 56, 2783–2791. [Google Scholar] [CrossRef]
- Zhang, C.; Situ, H.; Huang, Q.; Yang, P. Multi-party quantum summation without a trusted third party based on single particles. Int. J. Quantum Inform. 2017, 15, 1750010. [Google Scholar] [CrossRef]
- Yang, H.Y.; Ye, T.Y. Secure multi-party quantum summation based on quantum Fourier transform. Quantum Inf. Process. 2018, 17, 129. [Google Scholar] [CrossRef]
- Wang, Y.; Hu, P.; Xu, Q. Quantum secure multi-party summation based on entanglement swapping. Quantum Inf. Process. 2021, 20, 319. [Google Scholar] [CrossRef]
- Peng, Z.; Shi, R.; Zhong, H.; Cui, J.; Zhang, S. A novel quantum scheme for secure two-party distance computation. Quantum Inf. Process. 2017, 16, 316. [Google Scholar] [CrossRef]
- Tian, Y.; Li, J.; Chen, X.B.; Ye, C.Q.; Li, C.Y.; Hou, Y.Y. An efficient semi-quantum private comparison without pre-shared keys. Quantum Inf. Process. 2021, 20, 360. [Google Scholar] [CrossRef]
- Yan, L.; Zhang, S.; Chang, Y.; Wan, G.; Yang, F. Semi-quantum private comparison protocol with three-particle G-like states. Quantum Inf. Process. 2021, 20, 17. [Google Scholar] [CrossRef]
- Li, Q.; Li, P.; Xie, L.; Chen, L.; Quan, J. Security analysis and improvement of a semi-quantum private comparison protocol with three-particle G-like states. Quantum Inf. Process. 2022, 21, 127. [Google Scholar] [CrossRef]
- Wang, B.; Liu, S.-Q.; Gong, L.-H. Semi-quantum private comparison protocol of size relation with d-dimensional GHZ states. Chin. Phys. B 2022, 31, 010302. [Google Scholar] [CrossRef]
- Wu, W.; Guo, L.; Xie, M. Multi-party semi-quantum private comparison based on the maximally entangled GHZ-type states. Front. Phys. 2022, 10, 1048325. [Google Scholar] [CrossRef]
- Yang, C.-W.; Huang, Y.-Y.; Lin, J.; Tsai, C.-W. Efficient and secure semi-quantum private comparison protocol using three-particle GHZ-like states against participant attack. Mod. Phys. Lett. A 2024, 39, 2450037. [Google Scholar] [CrossRef]
- Yang, C.-W.; Huang, Y.-Y.; Tsai, C.-W.; Lin, J. Reflecting attack and improvement of a semi-quantum private comparison protocol with three-particle GHZ-like states. Mod. Phys. Lett. A 2024, 39, 2450175. [Google Scholar] [CrossRef]
- Zhang, X.; Wei, C.; Gao, F.; Li, W.; Qin, S. Efficient semi-quantum private set intersection cardinality protocol without pre-shared key. Quantum Inf. Process. 2025, 24, 213. [Google Scholar] [CrossRef]
- Shi, R.H.; Li, Y.F. Privacy-preserving quantum protocol for finding the maximum value. EPJ Quantum Technol. 2022, 9, 1–14. [Google Scholar] [CrossRef]
- Kong, H.-X.; Jia, H.-Y.; Wu, X.; Li, G.-Q. Robust quantum secure multiparty computation protocols for minimum value calculation in collective noises and their simulation. Int. J Theor. Phys. 2023, 62, 172. [Google Scholar] [CrossRef]
- Lu, Y.H.; Ding, G.Y. A novel quantum security multi-party extremum protocol in a d-dimensional quantum system. Phys. Scr. 2024, 99, 095111. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Grover, L.K. Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 1997, 79, 325–328. [Google Scholar] [CrossRef]
- Feng, W.; Guo, G.; Lin, S.; Xu, Y. Quantum Isomap algorithm for manifold learning. Phys. Rev. Appl. 2024, 22, 014049. [Google Scholar] [CrossRef]
- Su, J.; Fan, J.; Wu, S.; Li, G.; Qin, S.; Gao, F. Topology-driven quantum architecture search framework. Sci. China Inf. Sci. 2025, 68, 180507. [Google Scholar] [CrossRef]
- Wu, S.; Li, R.; Song, Y.; We, Q.; Gao, F. Quantum-Assisted Hierarchical Fuzzy Neural Network for Image Classification. IEEE Trans. Fuzzy Syst. 2025, 33, 491–502. [Google Scholar] [CrossRef]
- Huang, W.; Wen, Q.-Y.; Liu, B. Quantum anonymous ranking. Phys. Rev. A 2014, 89, 032325. [Google Scholar] [CrossRef]
- Lo, H.K.; Chau, H.F. Is quantum bit commitment really possible? Phys. Rev. Lett. 1997, 78, 3410. [Google Scholar] [CrossRef]
- Mayers, D. Unconditionally secure quantum bit commitment is impossible. Phys. Rev. Lett. 1997, 78, 3414. [Google Scholar] [CrossRef]
- Hou, M.; Wu, Y.; Zhang, S. Efficient Quantum Private Comparison Based on GHZ States. Entropy 2024, 26, 413. [Google Scholar] [CrossRef]
- Pont, M.; Corrielli, G.; Fyrillas, A.; Agresti, I.; Carvacho, G.; Maring, N.; Emeriau, P.; Ceccarelli, F.; Albiero, R.; Ferreira, P.H.D.; et al. High-fidelity Four-Photon GHZ States on Chip. npj Quantum Inf. 2024, 10, 50. [Google Scholar] [CrossRef]
| Trent | Alice | Bob | Charlie | |
|---|---|---|---|---|
| Step 1 | ||||
| Step 4 | ||||
| Step 5 | , , | , , | , , | |
| Step 6 | , | |||
| Step 7 | , , | , , | , , |
| Protocols | Ref. [37] | Ref. [39] | The Proposed Protocol |
|---|---|---|---|
| Quantum resource | single particles | single particles | multi-particle GHZ states |
| Quantum bits | |||
| Classical bits | 0 | ||
| Communication complexity | |||
| Quantum operation | Single-particle operation | Single-particle operation | Single-particle measurement |
| Computation task | Maximum | Maximum and Minimum | Maximum and Minimum |
| Resistant to external attacks | Yes | Yes | Yes |
| Resistant to internal attacks | Yes | No | Yes |
| Security model | Semi-honest model | Malicious model | Malicious model with a semi-honest third party |
| Deterministic or probabilistic | Probabilistic | Deterministic | Deterministic |
| Other requirement | Authenticated quantum channels | Decoy qudits | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, P.; Guo, G.-D.; Lin, S.-X.; Zhang, X.; Lin, S. Quantum Security Multi-Party Extremum Protocol with Greenberger–Horne–Zeilinger States. Technologies 2025, 13, 431. https://doi.org/10.3390/technologies13100431
Wang P, Guo G-D, Lin S-X, Zhang X, Lin S. Quantum Security Multi-Party Extremum Protocol with Greenberger–Horne–Zeilinger States. Technologies. 2025; 13(10):431. https://doi.org/10.3390/technologies13100431
Chicago/Turabian StyleWang, Ping, Gong-De Guo, Shu-Xin Lin, Xin Zhang, and Song Lin. 2025. "Quantum Security Multi-Party Extremum Protocol with Greenberger–Horne–Zeilinger States" Technologies 13, no. 10: 431. https://doi.org/10.3390/technologies13100431
APA StyleWang, P., Guo, G.-D., Lin, S.-X., Zhang, X., & Lin, S. (2025). Quantum Security Multi-Party Extremum Protocol with Greenberger–Horne–Zeilinger States. Technologies, 13(10), 431. https://doi.org/10.3390/technologies13100431






