Securing Blockchain-Based Supply Chain Management: Textual Data Encryption and Access Control
Abstract
1. Introduction
- Examine the existing challenges in blockchain-based supply chain management and identify strategies to address them.
- To generate a secure event log, ensuring that only authorized parties or entities have the capability to verify its authenticity.
- To effectively manage the substantial volume of data and the various operations performed on this data.
2. Related Work
2.1. Blockchain-Based Supply Chain Management
2.2. Potential Security Threats in Blockchain-Based Supply Chain Systems Context
2.2.1. Sybil Attacks
2.2.2. Eclipse Attack
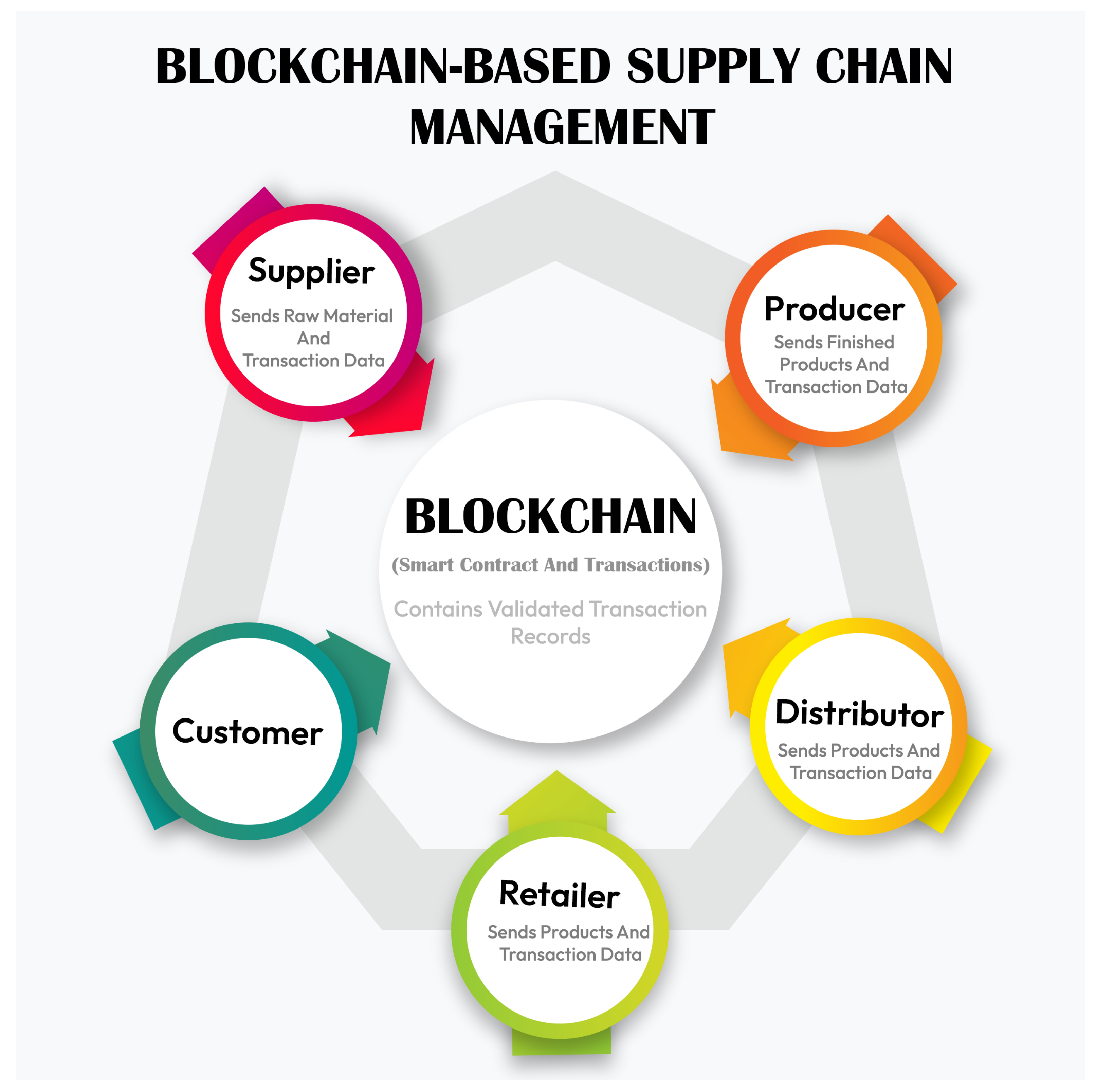
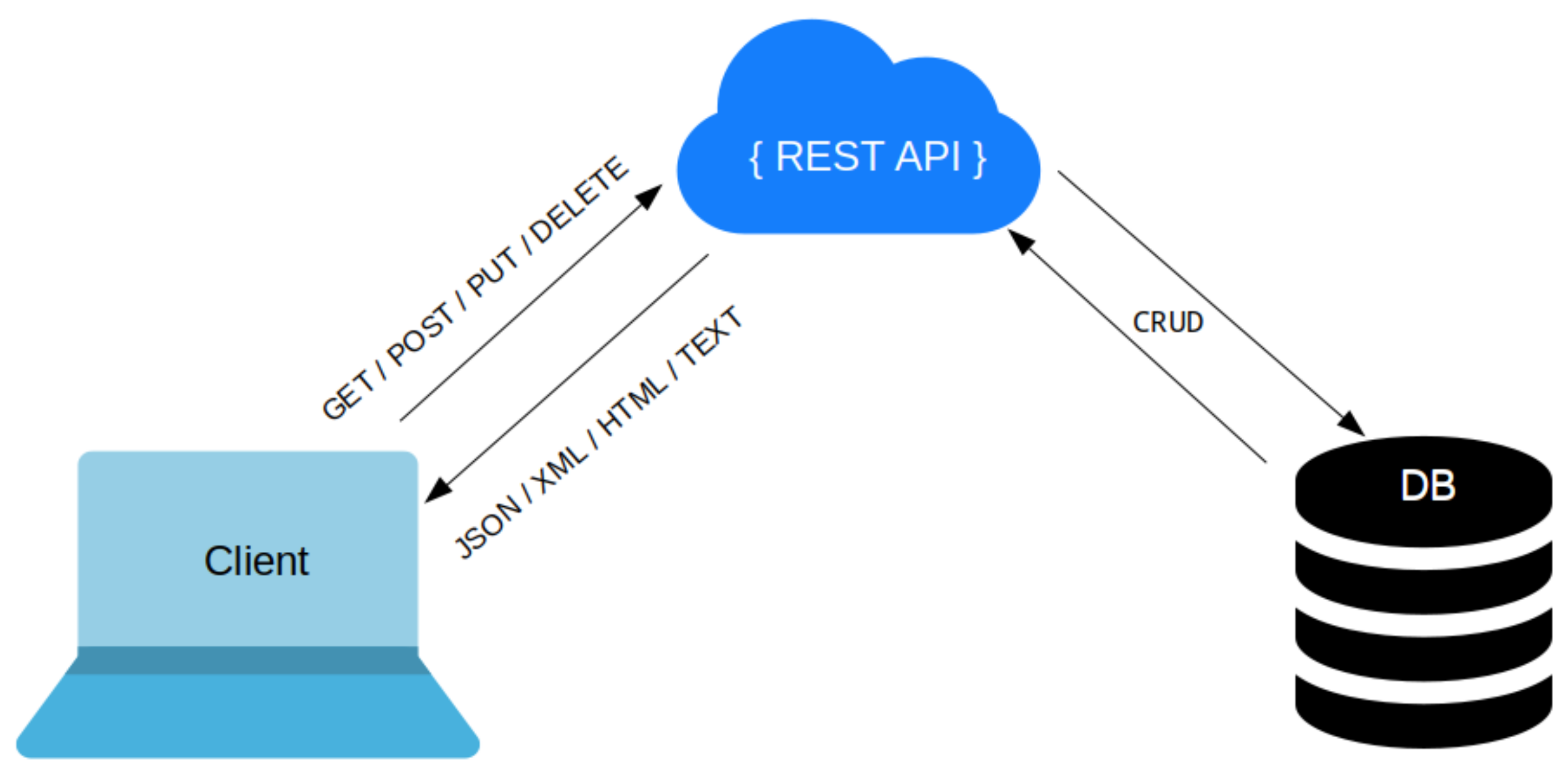
3. System Overview Model for Blockchain-Based Supply Chain Management
- Every participant in the supply chain—suppliers, producers, distributors, retailers, and customers—engages with the blockchain ecosystem through smart contracts and transactions.
- Transaction data encapsulates vital information, including product details, quantities, timestamps, and other pertinent data.
- The blockchain functions as a decentralized and immutable ledger, meticulously documenting all transactions. This setup ensures an elevated level of transparency, traceability, and accountability throughout the supply chain.
- Smart contracts play a pivotal role in automating and enforcing business rules and agreements among participants. These rules encompass payment terms, delivery conditions, and quality standards.
- Any alterations or updates within the supply chain, such as shipment notifications, quality inspections, or product recalls, can be seamlessly recorded on the blockchain. This real-time visibility benefits all participants.
- To facilitate real-time notifications, the system integrates Socket.io, a NodeJS library designed for instantaneous event emission and reception. This integration ensures prompt notifications during any updates or changes.
4. Proposed Technique for Advanced Integration in Supply Chain Management
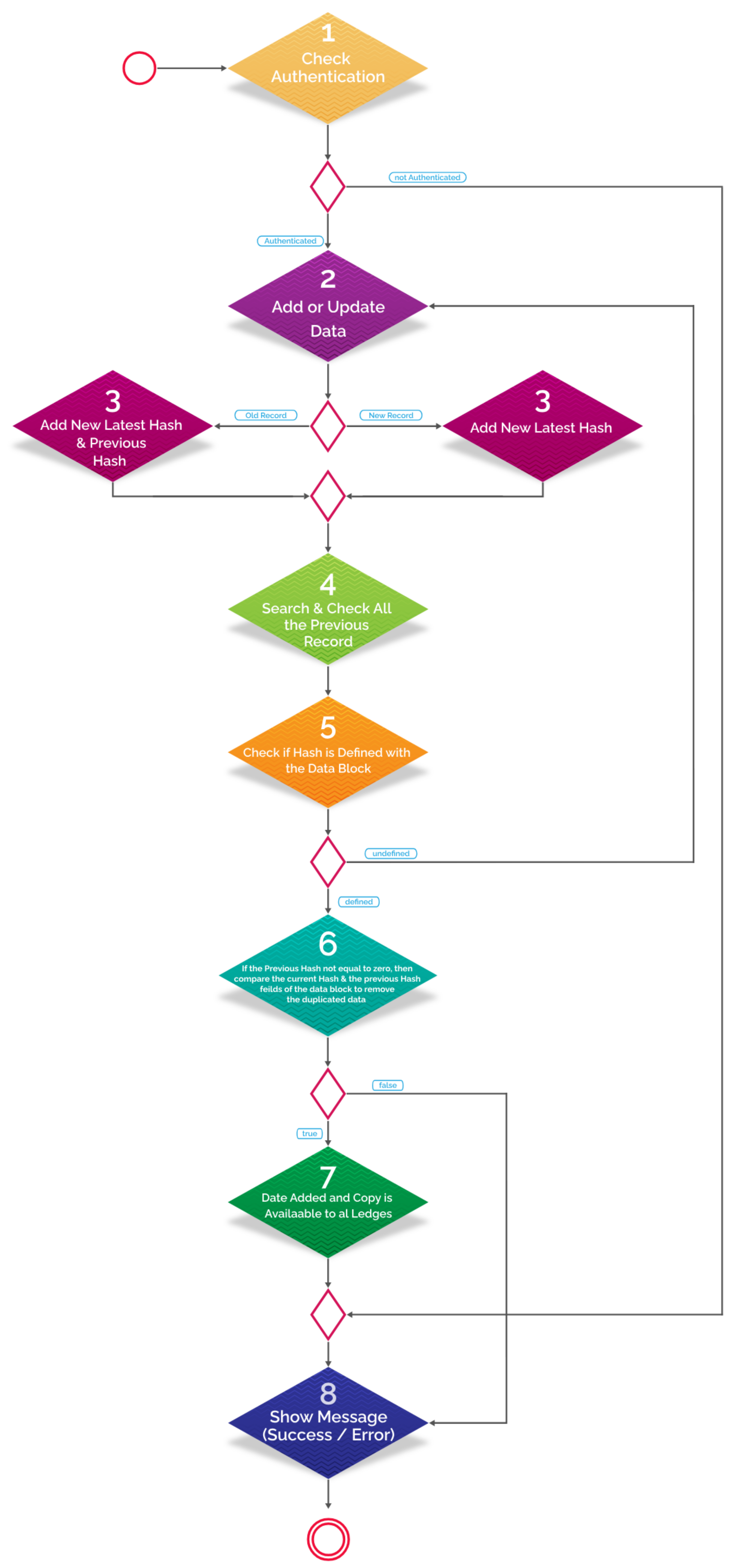
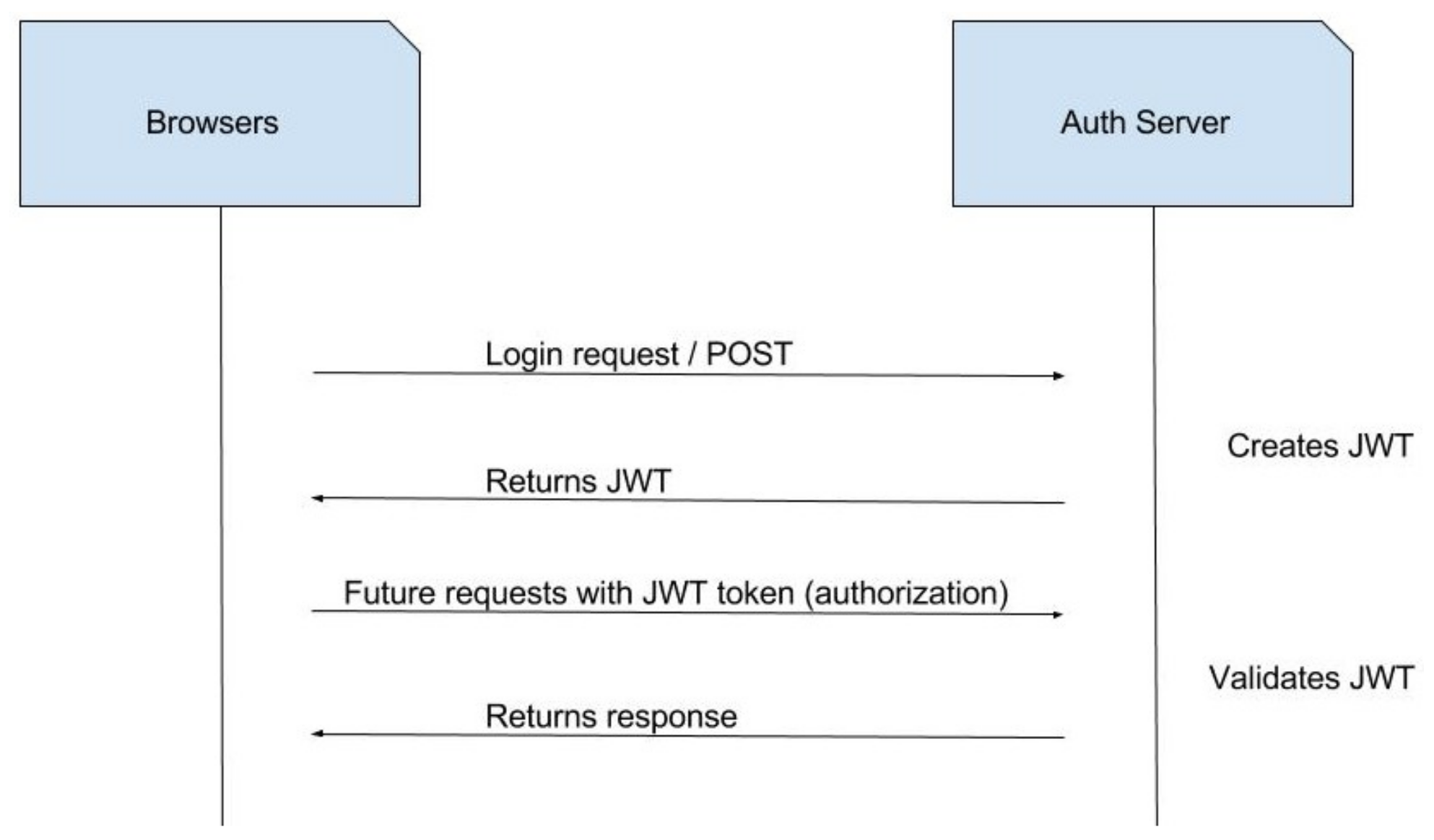
4.1. Authentication
4.2. Authorized User Role
4.3. Search and Check the Data
4.4. Hash Defined/Undefined
| Algorithm 1 Hash defined/undefined |
|
| Algorithm 2 Enhanced Validate Previous BlockHash |
|
5. Results and Discussion
5.1. Enhancing Application Requirements in the Proposed Technique
5.2. Authentication of User
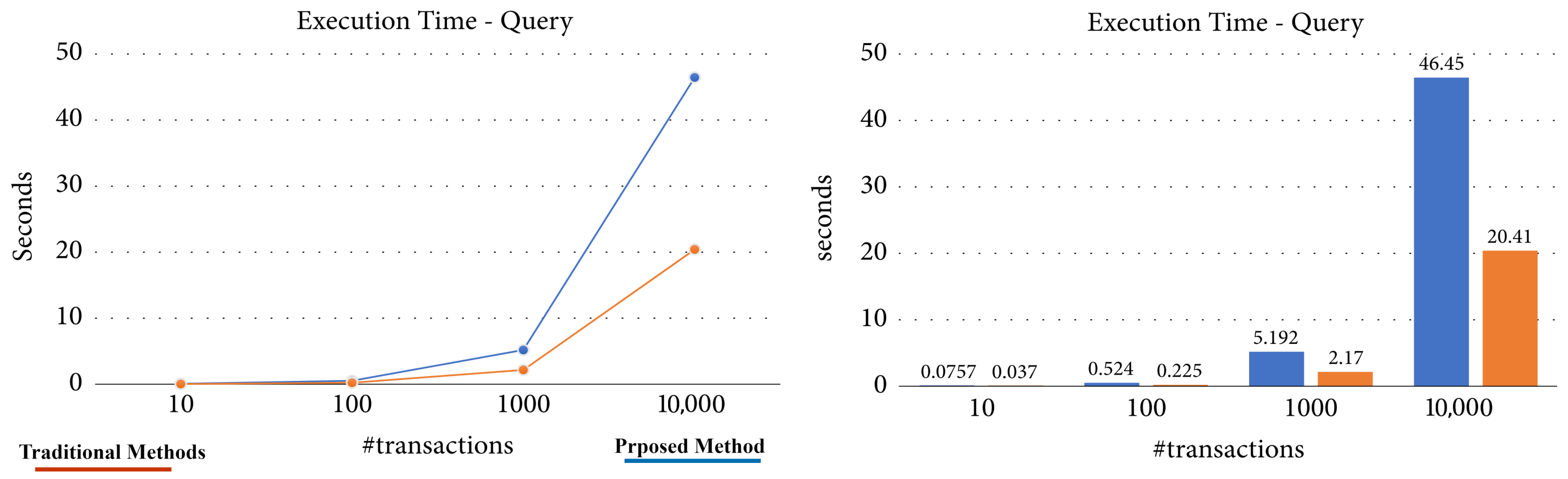
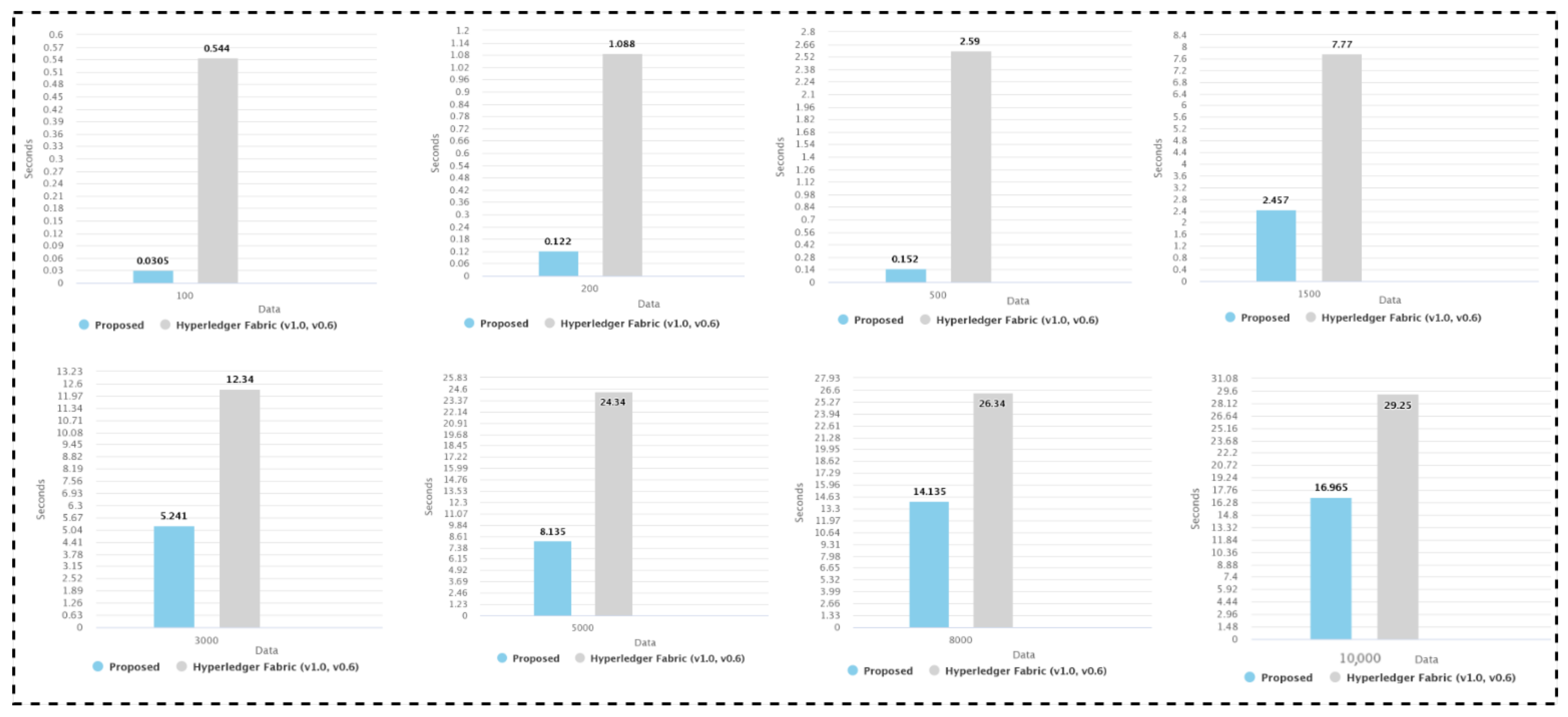
5.3. Performance Evaluation of Existing Literature
5.4. Results and Comparative Analysis with Prior Studies
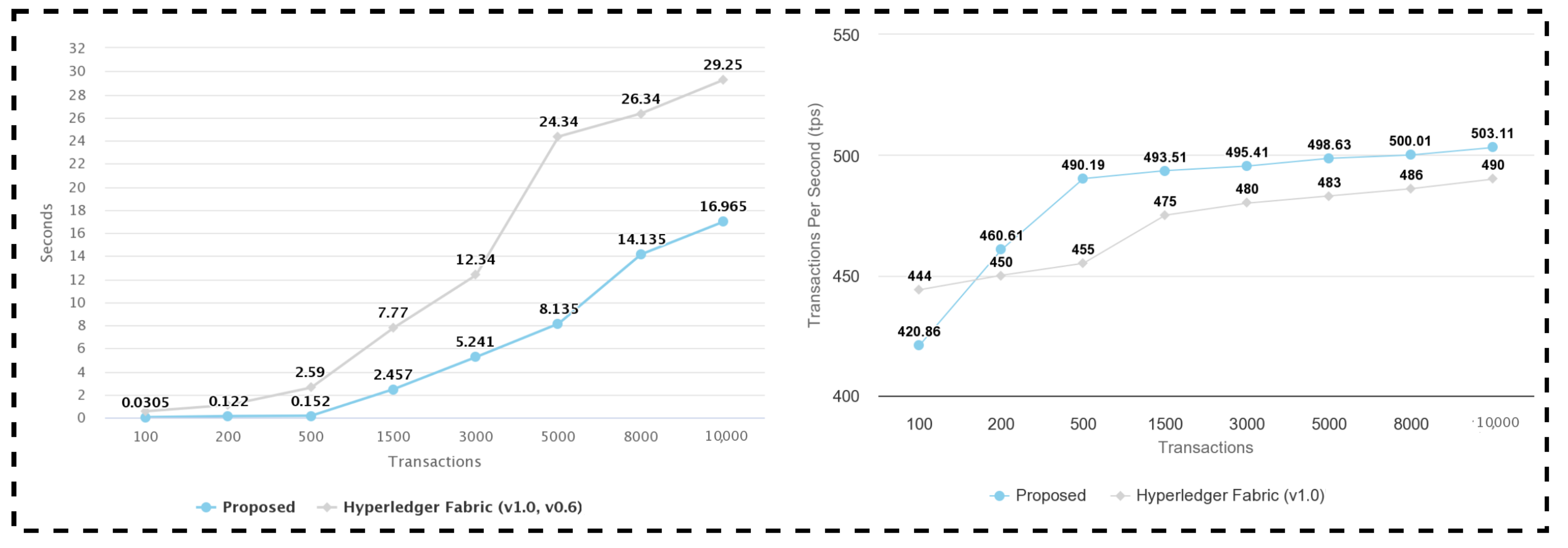
5.5. Latency
5.6. Throughput
5.7. Security Model
5.8. Security Metrics
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ronaghi, M.H. A blockchain maturity model in agricultural supply chain. Inf. Process. Agric. 2021, 8, 398–408. [Google Scholar] [CrossRef]
- Saba, T.; Haseeb, K.; Rehman, A.; Jeon, G. Blockchain-Enabled Intelligent IoT Protocol for High-Performance and Secured Big Financial Data Transaction. IEEE Trans. Comput. Soc. Syst. 2024, 11, 1667–1674. [Google Scholar] [CrossRef]
- Chang, S.E.; Chen, Y. When blockchain meets supply chain: A systematic literature review on current development and potential applications. IEEE Access 2020, 8, 62478–62494. [Google Scholar] [CrossRef]
- Wu, H.; Jiang, S.; Cao, J. High-efficiency blockchain-based supply chain traceability. IEEE Trans. Intell. Transp. Syst. 2023, 24, 3748–3758. [Google Scholar] [CrossRef]
- Aslam, J.; Saleem, A.; Kim, Y.B. Blockchain-Enabled Supply Chain Management: Integrated Impact on Firm Performance and Robustness Capabilities. Bus. Process. Manag. J. 2023, 29, 1680–1705. [Google Scholar] [CrossRef]
- Khan, A.S.; Yahya, M.I.B.; Zen, K.B.; Abdullah, J.B.; Rashid, R.B.A.; Javed, Y.; Khan, N.A.; Mostafa, A.M. Blockchain-Based Lightweight Multifactor Authentication for Cell-Free in Ultra-Dense 6G-Based (6-CMAS) Cellular Network. IEEE Access 2023, 11, 20524–20541. [Google Scholar] [CrossRef]
- Tokkozhina, U.; Lucia Martins, A.; Ferreira, J.C. Uncovering dimensions of the impact of blockchain technology in supply chain management. Oper. Manag. Res. 2023, 16, 99–125. [Google Scholar] [CrossRef]
- Li, K.; Lee, J.Y.; Gharehgozli, A. Blockchain in food supply chains: A literature review and synthesis analysis of platforms, benefits and challenges. Int. J. Prod. Res. 2023, 61, 3527–3546. [Google Scholar] [CrossRef]
- Singh, S.K.; Jenamani, M. ProcessChain: A blockchain-based framework for privacy preserving cross-organizational business process mining from distributed event logs. Bus. Process. Manag. J. 2023, 30, 239–269. [Google Scholar] [CrossRef]
- Guo, Y.; Liang, C. Blockchain application and outlook in the banking industry. Financ. Innov. 2016, 2, 1–12. [Google Scholar] [CrossRef]
- Rijanto, A. Blockchain technology adoption in supply chain finance. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 3078–3098. [Google Scholar] [CrossRef]
- Perboli, G.; Musso, S.; Rosano, M. Blockchain in logistics and supply chain: A lean approach for designing real-world use cases. IEEE Access 2018, 6, 62018–62028. [Google Scholar] [CrossRef]
- Vishwakarma, A.; Dangayach, G.; Meena, M.; Gupta, S.; Luthra, S. Adoption of blockchain technology-enabled healthcare sustainable supply chain to improve healthcare supply chain performance. Manag. Environ. Qual. Int. J. 2023, 34, 1111–1128. [Google Scholar] [CrossRef]
- Tapscott, D.; Tapscott, A. Blockchain Revolution: How the Technology Behind Bitcoin Is Changing Money, Business, and the World; Penguin Random House: New York, NY, USA, 2016. [Google Scholar]
- Choi, T.M.; Siqin, T. Blockchain in logistics and production from Blockchain 1.0 to Blockchain 5.0: An intra-inter-organizational framework. Transp. Res. Part E Logist. Transp. Rev. 2022, 160, 102653. [Google Scholar] [CrossRef]
- Taj, S.; Imran, A.S.; Kastrati, Z.; Daudpota, S.M.; Memon, R.A.; Ahmed, J. IoT-based supply chain management: A systematic literature review. Internet Things 2023, 24, 100982. [Google Scholar] [CrossRef]
- Andrew, J.; Isravel, D.P.; Sagayam, K.M.; Bhushan, B.; Sei, Y.; Eunice, J. Blockchain for healthcare systems: Architecture, security challenges, trends and future directions. J. Netw. Comput. Appl. 2023, 215, 103633. [Google Scholar]
- Khedekar, V.B.; Hiremath, S.S.; Sonawane, P.M.; Rajput, D.S. Protection to Personal Data Using Decentralizing Privacy of Blockchain. In Research Anthology on Convergence of Blockchain, Internet of Things, and Security; IGI Globa: New York, NY, USA, 2023; pp. 570–587. [Google Scholar]
- Ravi, D.; Ramachandran, S.; Vignesh, R.; Falmari, V.R.; Brindha, M. Privacy preserving transparent supply chain management through Hyperledger Fabric. Blockchain Res. Appl. 2022, 3, 100072. [Google Scholar] [CrossRef]
- Melo, C.; Oliveira, F.; Dantas, J.; Araujo, J.; Pereira, P.; Maciel, R.; Maciel, P. Performance and availability evaluation of the blockchain platform hyperledger fabric. J. Supercomput. 2022, 78, 12505–12527. [Google Scholar] [CrossRef]
- Sultana, J.; Teoh, S.Y.; Karanasios, S. The impact of blockchain on supply chains: A systematic review. Australas. J. Inf. Syst. 2022, 26, 1–38. [Google Scholar] [CrossRef]
- Jadhav, J.S.; Deshmukh, J. A review study of the blockchain-based healthcare supply chain. Soc. Sci. Humanit. Open 2022, 6, 100328. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance and proactive recovery. ACM Trans. Comput. Syst. (TOCS) 2022, 20, 398–461. [Google Scholar] [CrossRef]
- Jabbar, S.; Lloyd, H.; Hammoudeh, M.; Adebisi, B.; Raza, U. Blockchain-enabled supply chain: Analysis, challenges, and future directions. Multimed. Syst. 2021, 27, 787–806. [Google Scholar] [CrossRef]
- Wang, Y.; Singgih, M.; Wang, J.; Rit, M. Making sense of blockchain technology: How will it transform supply chains? Int. J. Prod. Econ. 2019, 211, 221–236. [Google Scholar] [CrossRef]
- Liu, Y.; He, D.; Obaidat, M.S.; Kumar, N.; Khan, M.K.; Choo, K.K.R. Blockchain-based identity management systems: A review. J. Netw. Comput. Appl. 2020, 166, 102731. [Google Scholar] [CrossRef]
- Abdirad, M.; Krishnan, K. Industry 4.0 in logistics and supply chain management: A systematic literature review. Eng. Manag. J. 2021, 33, 187–201. [Google Scholar] [CrossRef]
- Sharma, R.; Shishodia, A. Blockchain Technology Enablers in Physical Distribution and Logistics Management. In Big Data and Blockchain for Service Operations Management; Springer: Berlin/Heidelberg, Germany, 2022; pp. 329–344. [Google Scholar]
- Kamble, S.S.; Gunasekaran, A.; Subramanian, N.; Ghadge, A.; Belhadi, A.; Venkatesh, M. Blockchain technology’s impact on supply chain integration and sustainable supply chain performance: Evidence from the automotive industry. Ann. Oper. Res. 2023, 327, 575–600. [Google Scholar] [CrossRef]
- Alzahrani, N.; Bulusu, N. A new product anti-counterfeiting blockchain using a truly decentralized dynamic consensus protocol. Concurr. Comput. Pract. Exp. 2020, 32, e5232. [Google Scholar] [CrossRef]
- Babar, M.; Qureshi, B.; Koubaa, A. Review on Federated Learning for Digital Transformation in Healthcare through Big Data Analytics. Future Gener. Comput. Syst. 2024, 160, 14–28. [Google Scholar] [CrossRef]
- Kumar, N.; Tyagi, M.; Sachdeva, A.; Kazancoglu, Y.; Ram, M. Impact analysis of COVID-19 outbreak on cold supply chains of perishable products using a SWARA based MULTIMOORA approach. Oper. Manag. Res. 2022, 15, 1290–1314. [Google Scholar] [CrossRef]
- Bhutta, M.N.M.; Ahmad, M. Secure identification, traceability and real-time tracking of agricultural food supply during transportation using internet of things. IEEE Access 2021, 9, 65660–65675. [Google Scholar] [CrossRef]
- Li, Y.; Wang, J.; Zhang, H. A survey of state-of-the-art sharding blockchains: Models, components, and attack surfaces. J. Netw. Comput. Appl. 2023, 217, 103686. [Google Scholar] [CrossRef]
- Geepthi, D.; Columbus, C.C.; Jeyanthi, C. Peer to peer sybil and eclipse attack detection via fuzzy kademlia. J. Intell. Fuzzy Syst. 2023, 44, 6925–6937. [Google Scholar] [CrossRef]
- Hafid, A.; Hafid, A.S.; Samih, M. A tractable probabilistic approach to analyze sybil attacks in sharding-based blockchain protocols. IEEE Trans. Emerg. Top. Comput. 2022, 11, 126–136. [Google Scholar] [CrossRef]
- Hadi, H.J.; Cao, Y.; Li, S.; Xu, L.; Hu, Y.; Li, M. Real-time fusion multi-tier DNN-based collaborative IDPS with complementary features for secure UAV-enabled 6G networks. Expert Syst. Appl. 2024, 252, 124215. [Google Scholar] [CrossRef]
- Dai, Q.; Zhang, B.; Dong, S. Eclipse attack detection for blockchain network layer based on deep feature extraction. Wirel. Commun. Mob. Comput. 2022, 2022, 1451813. [Google Scholar] [CrossRef]
- Hadi, H.J.; Hayat, U.; Musthaq, N.; Hussain, F.B.; Cao, Y. Developing Realistic Distributed Denial of Service (DDoS) Dataset for Machine Learning-based Intrusion Detection System. In Proceedings of the 2022 9th International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Milan, Italy, 29 November–1 December 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- Schmarzo, B. Big Data: Understanding How Data Powers Big Business; John Wiley & Sons: Hoboken, NJ, USA, 2013. [Google Scholar]
- Ban, T.Q.; Anh, B.N.; Son, N.T.; Van Dinh, T. Survey of Hyperledger blockchain frameworks: Case study in FPT university’s cryptocurrency wallets. In Proceedings of the 2019 8th International Conference on Software and Computer Applications, Penang, Malaysia, 19–21 February 2019; pp. 472–480. [Google Scholar]
- Sharma, P.; Jindal, R.; Borah, M.D. Blockchain-based distributed application for multimedia system using Hyperledger Fabric. Multimed. Tools Appl. 2023, 83, 2473–2499. [Google Scholar] [CrossRef]
- Bucko, A.; Vishi, K.; Krasniqi, B.; Rexha, B. Enhancing JWT Authentication and Authorization in Web Applications Based on User Behavior History. Computers 2023, 12, 78. [Google Scholar] [CrossRef]
- Cui, Y.; Gaur, V.; Liu, J. Supply chain transparency and blockchain design. Manag. Sci. 2023, 70, 3245–3263. [Google Scholar] [CrossRef]
- Nasir, Q.; Qasse, I.A.; Abu Talib, M.; Nassif, A.B. Performance analysis of hyperledger fabric platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef]
- Dasaklis, T.K.; Voutsinas, T.G.; Tsoulfas, G.T.; Casino, F. A systematic literature review of blockchain-enabled supply chain traceability implementations. Sustainability 2022, 14, 2439. [Google Scholar] [CrossRef]
- Ali, Q.E.; Ahmad, N.; Malik, A.H.; Rehman, W.U.; Din, A.U.; Ali, G. ASPA: Advanced strong pseudonym based authentication in intelligent transport system. PLoS ONE 2019, 14, e0221213. [Google Scholar] [CrossRef] [PubMed]
- Andola, N.; Yadav, V.K.; Venkatesan, S.; Verma, S. Anonymity on blockchain-based e-cash protocols—A survey. Comput. Sci. Rev. 2021, 40, 100394. [Google Scholar] [CrossRef]
| Paper | Research Work | Problem |
|---|---|---|
| [1] | Smart contracts play a critical role in connecting business logic and progress monitoring in supply chain operations through blockchain-based platforms | Throughput, security and scalability |
| [9] | Reliable, authentic and secure system | Visibility and transparency of product flows are the principal challenges |
| [12] | All transactions on the network are only visible to organizations or individuals that hold a licensing certificate | Enhancing product safety and security; improving quality management are not mentioned |
| [32] | Accurate data collection and reliable data tracking using SWARA maturity model | Does not mention how to control the growing volume of data |
| [11] | Payment confirmation, product delivery permit, and proof of delivery until product receipt is confirmed | Supply chain financing securitization |
| [13] | Reducing fraud and errors, reducing work delays, increase client and partner trust in the Pharmaceutical Industry | Fails to validate each ledger record w.r.t manufacturer and the proposed techniques are not deployed |
| [33] | Blockchain-based SCM architecture with a focus on the secure identification, traceability, and real-time tracking of food supply during transportation using IoT and blockchain | Fault tolerance, equipment failure, and very costly in terms of software and hardware |
| This work | Blockchain technology enhances supply chains, making them more flexible, transparent, and efficient | Engaged in overseeing security logs and managing substantial volumes of data |
| Feature | Traditional System | Public Blockchain | Hyperledger Fabric |
|---|---|---|---|
| Blockchain log | No | Yes | Yes |
| Extensible event storage | Yes | No | Yes |
| Distributed ledger | No | Yes | Yes |
| Flexible transparency | No | No | Yes |
| Immutability | No | Yes | Yes |
| Private data sharing | No | No | Yes |
| Confidentiality | No | No | Yes |
| Modularity | No | No | Yes |
| Approval process that plugs in | No | No | Yes |
| Sr# | Requirement | Version |
|---|---|---|
| 1 | PC or Laptop | 2 Cores |
| 2 | RAM | 4GB |
| 3 | Nodejs (Server side language) | 14.0 (LTS) |
| 4 | Mongodb (Database) | 4.0 (LTS) |
| 5 | Mongoose (Mongodb library for schema definitions) | 6.0.0 (LTS) |
| 6 | JWT(JSON Web Token) For User Authentication | 4.2.2 |
| 7 | Nginx (Proxy Server) | 1.20 (Stable) |
| 8 | Environment (Ubuntu or Windows), Recommended (Ubuntu) | 20.04 (LTS) Windows ≥ 7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, I.; Ali, Q.E.; Hadi, H.J.; Ahmad, N.; Ali, G.; Cao, Y.; Alshara, M.A. Securing Blockchain-Based Supply Chain Management: Textual Data Encryption and Access Control. Technologies 2024, 12, 110. https://doi.org/10.3390/technologies12070110
Khan I, Ali QE, Hadi HJ, Ahmad N, Ali G, Cao Y, Alshara MA. Securing Blockchain-Based Supply Chain Management: Textual Data Encryption and Access Control. Technologies. 2024; 12(7):110. https://doi.org/10.3390/technologies12070110
Chicago/Turabian StyleKhan, Imran, Qazi Ejaz Ali, Hassan Jalil Hadi, Naveed Ahmad, Gauhar Ali, Yue Cao, and Mohammed Ali Alshara. 2024. "Securing Blockchain-Based Supply Chain Management: Textual Data Encryption and Access Control" Technologies 12, no. 7: 110. https://doi.org/10.3390/technologies12070110
APA StyleKhan, I., Ali, Q. E., Hadi, H. J., Ahmad, N., Ali, G., Cao, Y., & Alshara, M. A. (2024). Securing Blockchain-Based Supply Chain Management: Textual Data Encryption and Access Control. Technologies, 12(7), 110. https://doi.org/10.3390/technologies12070110