A Comparison Survey Study on RFID Based Anti-Counterfeiting Systems
Abstract
:1. Introduction
2. RFID Technology and Some Implementations
2.1. RFID Technology
2.2. Some Implementations of RFID Technology in Industry
3. RFID Anti-Counterfeiting Methods and Technologies
- PUF Based ‘Unclonable’ RFID ICs and chipless RFID tags for anti-counterfeiting: Since PUF-based ‘Unclonable’ RFID ICs and chipless RFID tags both exploit the physical characteristics, we will include them both here.
- -
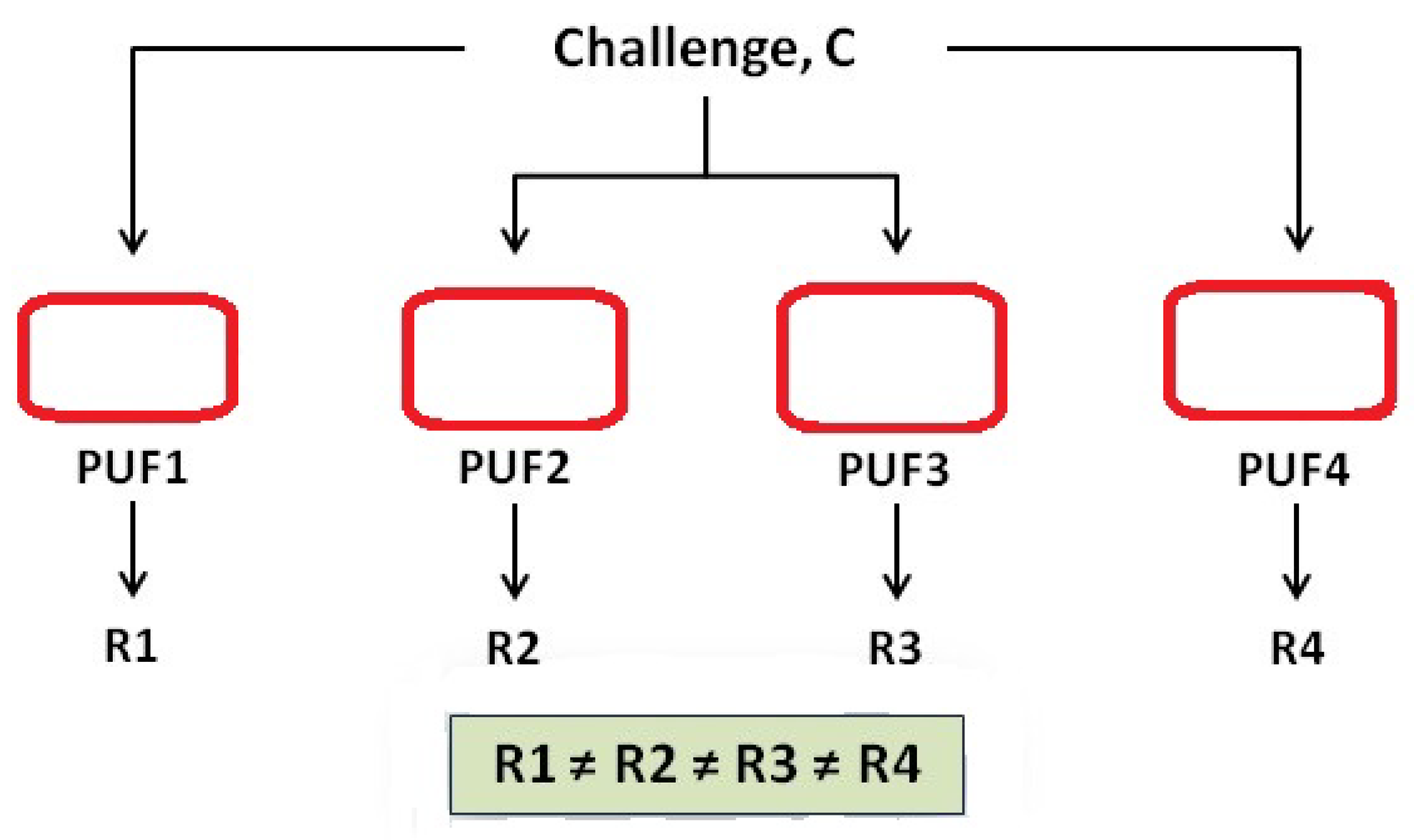
- Physical Unclonable Functions (PUFs) exploit the physical characteristics of the IC manufacturing process to characterise each and every chip [11] uniquely. This main characteristic will make it impossible to copy, clone or control these chips. This effect makes the RFID ICs attracted to characteristics that provide uniqueness and adequate security. In [12], the authors define the PUF as “a function that maps challenges to responses embodied in a physical object to achieve the simplicity of evaluation and hard to characterize”. By denoting the PUF response to a challenge, C, by and during the verification phase by as is a challenge-response pair. The PUF response according, to a fake PUF, is denoted by Z as the reactions are modeled as random variables with probability distribution . Also, the authors add two more definitions, one for the Integrated Physical Unclonable Function (I-PUF) which is a PUF bounded to a chip which prevents any attempt to separate or remove them from each other as it will lead to the chip destruction. In addition, it has the property of not allowing an attacker to tamper the communications between the chip and PUF as the output is not accessible to an attacker. The best examples for I-PUFs are the silicon PUFs [13] and coating PUFs [14]. Again in [12], the authors construct unclonable RFID tags by embedding I-PUF in the microchips and by using a PUF as a secure memory for storing secret key, as per Figure 1. In [15], the authors discuss the counterfeiting of goods and its implications and threats to health and security. The authors also discuss the incorporation of anti-counterfeiting tags with physical unclonable functions (PUFs) into products as they are unique random physical patterns of taggants which cannot be copied as the PUF tag is the key whereas the stored pattern is the lock. The authors assumed that the stochastic assembly of physical patterns made from taggants exhibiting molecular properties is an excellent approach for designing new PUF keys.
- -
- Another technology which received a lot of attention lately is the chip-less RFID tag [16], which is unique and has the advantage of low cost, adaptability and easy printing production. Such tags will be also hard to clone as they need special manufacturing measurements which are hard to determine, but they are not fully un-clonable like the PUF based unclonable RFID tags. As per [17] the chipless RFID tags have the following advantages:
- *
- the extremely low price (as low as 0.1 cents) makes them more appropriate to be used in the supply chain of low-cost commodities.
- *
- elimination of tag memory shelters them from denial-of-service (DoS) attack carried out in the form of overwriting tag memory.
- *
- chipless RFID tags can be directly printed on the products or their packages with conductive 3D printing materials.
The chipless RFID tag is not very well suited for general use, as it requires either removing or shorting some resonators, such as spirals or patch slots, on the tag substrate to represent data and those procedures will increase the manufacturing time and cost [17].
- Track and trace Anti-counterfeiting: This approach has attracted much attention from researchers due to its reliability. The method demands a trustworthy ‘e-pedigree’, or electronic pedigree, that records the product flow of items from manufacturer to retailers [18] to provide evidence of product authentication. To achieve this goal, it is imperative to have reliable creation of e-pedigree and synchronization throughout the supply chain. There are several critical problems addressed by researchers, especially during the generation of the e-pedigree when the products are tagged or during packaging line-transferring when some tags are not provided with the right programming. The synchronization between the tagged items and the back-end database must be carried in real time and with encryption to prevent eavesdropping or sniffing and to ensure uniqueness with the back end e-pedigree records. Examples of such a protocol that uses the track-and-trace method in anti-counterfeiting are shown in Figure 1. This anti-counterfeiting system is designed for supply chain operations where manufacturers, distributors, and retailers are linked to produce, transport and sell brands and products. Without such a system it is possible to import fake products. The system has been adapted and developed by adding TDPS (tag data processing and synchronization), an algorithm based on Gen2 UHF tags that aims to solve critical issues of product initial e-pedigree. The TDPS consists of five steps: EPC writing, EPC Verification and TID reading, tag locking, locking verification and initial e-pedigree creation and synchronization.
- Distance bounding protocols: In [19] the authors proposed leveraging broadcast and collisions to identify cloned tags, thus reducing the need to resort to complex cryptography techniques and tag IDs transmission. The authors argue this approach is the best for large-scale RFID systems and also claim the synchronized secret [20] where it assigns each tag a unique ID and a unique random number which is then stored on a back-end server. The use of leverage broadcast and collision to identify counterfeited tags follows the main idea of choosing a tag with a positive ID and then sending a response when there is a cloned or counterfeited tag peer or peers. If there were a collision or multiple responses then the system will detect these cloned peers. Although this idea is practical and more comfortable to use than complex cryptography techniques, and more pleasant to use in a large scale RFID system accommodating thousands of tagged objects, there is still the limitation when using such a system separately, or in different geographic areas, or in different time frames, as this will require continuous synchronization used with RFID tags in the same system.
- Other types of anti-counterfeiting protocols: These include the use of cryptography in general. There are several protocols which have attempted to address this issue, such as [21], where the authors proposed a system of two protocols as mentioned above. The basic idea is to make the tag handle a one way function F which is compatible with a low-cost RFID tag. The first protocol was the tag authentication protocol where the tag allows the customer “the reader” to inquire about the tag. There are four components of the RFID anti-counterfeiting system: the RFID tag, the reader, the server and the seller. The is a unique tag id for the tag that is attached to the product which also stores the corresponding secret s while the reader is a device used by a customer, such as a tablet or a cell phone, with the application downloaded from the product manufacturer containing the authentication protocol. The manufacturer has the tag database which includes the tag ID or , the secret S, the tag status which can be sold or unsold and the seller name . When issuing a tag, the manufacturer will assign to unsold in the database and every time the tagged product is sold or transferred the database will add the name of the seller to the record.Through this protocol, the server verifies if the product is genuine and notifies the reader if S is incorrect or the item was sold and the server sent invalid message to the reader. The database correction protocol, on the other hand, will correct the database when any legitimate change in the tag status needs to occur.The reader will initiate the procedure by sending the tag ID which can be found on the sticker on the product with the random number to the tag and the tag will check if is correct. The tag will respond with ; otherwise it will terminate. Once the reader has received X, it will generate another random number and send which is an encryption of the server public key. The server will then decrypt the message using a private key and check if the is there in the record; otherwise it terminates. If the is sold, the database sends ; if unsold, the server calculates and checks if . If true, the server sends message and changes tag status to sold. As can be observed, this sequence requires many computational processes as well as encryption, decryption and back-and-forth communications; however, this procedure is still more flexible and reliable than others as it will provide different logical shapes that can adapt to the situation required by the industry.
4. Related Work on Anti-Counterfeiting Systems and Techniques
4.1. Schemes and Frame Works to Address Anti-Counterfeiting
4.2. Anti-Counterfeiting Schemes in Different Industries
4.3. Track and Trace Anti-Counterfeiting Schemes
4.4. Distance Bounding and Collision in Identifying Coned RFID Tags
4.5. The Use of Physical Unclonable Function (PUF)
4.6. Using RFID Tag ID Verification for Anti-Counterfeiting
4.7. Anti-Counterfeiting and a Secure Tag Ownership Transfer Mechanism
5. Comparison Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Randhawa, P.; Calantone, R.J.; Voorhees, C.M. The pursuit of counterfeited luxury: An examination of the negative side effects of close consumer–brand connections. J. Bus. Res. 2015, 68, 2395–2403. [Google Scholar] [CrossRef]
- Meyer, T. Anti-Counterfeiting Trade Agreement: 2010–2012 European Parliament Discussions. In The Politics of Online Copyright Enforcement in the EU; Springer: Berlin/Heidelberg, Germany, 2017; pp. 247–280. [Google Scholar]
- Kamaladevi, B. RFID-The best technology in supply chain management. Int. J. Innov. Manag. Technol. 2010, 1, 198. [Google Scholar]
- Al, T.; Al, G.K. A Case Study in Developing the ICT Skills for a Group of Mixed Abilities and Mixed Aged Learners at ITEP in Dubai-UAE and Possible Future RFID Implementations. In Envisioning the Future of Online Learning; Springer: Berlin/Heidelberg, Germany, 2016; pp. 133–146. [Google Scholar]
- Al, G. RFID Technology: Design Principles, Applications and Controversies; Nova Science Publishers, Inc.: Commack, NY, USA, 2018. [Google Scholar]
- Peppa, V.P.; Moschuris, S.J. RFID technology in supply chain management: a review of the literature and prospective adoption to the Greek market. Glob. J. Eng. Educ. 2013, 15, 61–68. [Google Scholar]
- Soon, C.B.; Gutiérrez, J.A. Effects of the RFID mandate on supply chain management. J. Theor. Appl. Electron. Commer. Res. 2008, 3, 81. [Google Scholar]
- Yang, L.; Peng, P.; Dang, F.; Wang, C.; Li, X.Y.; Liu, Y. Anti-counterfeiting via federated rfid tags’ fingerprints and geometric relationships. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 1966–1974. [Google Scholar]
- Michael, K.; McCathie, L. The pros and cons of RFID in supply chain management. In Proceedings of the International Conference on Mobile Business (ICMB’05), Sydney, Australia, 11–13 July 2005; pp. 623–629. [Google Scholar]
- Gomez, L.; Laurent, M.; El Moustaine, E. Risk assessment along supply chain: A RFID and wireless sensor network integration approach. Sens. Transducers 2012, 14, 269. [Google Scholar]
- Devadas, S.; Suh, E.; Paral, S.; Sowell, R.; Ziola, T.; Khandelwal, V. Design and implementation of PUF-based “unclonable” RFID ICs for anti-counterfeiting and security applications. In Proceedings of the 2008 IEEE International Conference on RFID, Las Vegas, NV, USA, 16–17 April 2008; pp. 58–64. [Google Scholar]
- Tuyls, P.; Batina, L. RFID tags for Anti-Counterfeiting. In Proceedings of the Cryptographers Track at the RSA Conference, San Jose, CA, USA, 13–17 February 2006; pp. 115–131. [Google Scholar]
- Gassend, B.; Clarke, D.; Van Dijk, M.; Devadas, S. Silicon physical random functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 148–160. [Google Scholar]
- Tuyls, P.; Škorić, B. Secret key generation from classical physics: Physical uncloneable functions. In AmIware Hardware Technology Drivers of Ambient Intelligence; Springer: Berlin, Germany, 2006; pp. 421–447. [Google Scholar]
- Arppe, R.; Sørensen, T.J. Physical unclonable functions generated through chemical methods for anti-counterfeiting. Nat. Rev. Chem. 2017, 1, 0031. [Google Scholar] [CrossRef]
- Preradovic, S.; Karmakar, N.C. Chipless RFID: Bar Code of the Future. IEEE Microw. Mag. 2010, 11, 87–97. [Google Scholar] [CrossRef]
- Yang, K.; Botero, U.; Shen, H.; Woodard, D.L.; Forte, D.; Tehranipoor, M.M. UCR: An Unclonable Environmentally Sensitive Chipless RFID Tag For Protecting Supply Chain. ACM Trans. Des. Autom. Electron. Syst. 2018, 23, 74. [Google Scholar] [CrossRef]
- Choi, S.; Yang, B.; Cheung, H.; Yang, Y. RFID tag data processing in manufacturing for track-and-trace anti-counterfeiting. Comput. Ind. 2015, 68, 148–161. [Google Scholar] [CrossRef]
- Bu, K.; Liu, X.; Xiao, B. Approaching the time lower bound on cloned-tag identification for large RFID systems. Ad Hoc Netw. 2014, 13, 271–281. [Google Scholar] [CrossRef]
- Lehtonen, M.; Ostojic, D.; Ilic, A.; Michahelles, F. Securing RFID systems by detecting tag cloning. In Proceedings of the International Conference on Pervasive Computing, Nara, Japan, 11–14 May 2009; pp. 291–308. [Google Scholar]
- Tran, D.T.; Hong, S.J. RFID anti-counterfeiting for retailing systems. J. Appl. Math. Phys. 2015, 3, 1. [Google Scholar] [CrossRef]
- Hofman, C.; Keates, S. An Overview of Branding and its Associated Risks. In Countering Brandjacking in the Digital Age; Springer: Berlin, Germany, 2013; pp. 9–35. [Google Scholar]
- Food and Drug Administration. Compliance Policy Guid 160.900 Prescription Drug Marketing Act-Pedigree Requirement under 21 CFR Part 203. 2006. Available online: https://www.fda.gov/regulatory-information/search-fda-guidance-documents/cpg-sec-160900-prescription-drug-marketing-act-pedigree-requirements-under-21-cfr-part-203 (accessed on 30 September 2016).
- Al, G.; Doss, R.; Chowdhury, M.; Ray, B. Secure RFID Protocol to Manage and Prevent Tag Counterfeiting with Matryoshka Concept. In Proceedings of the International Conference on Future Network Systems and Security, Paris, France, 23–25 November 2016; pp. 126–141. [Google Scholar]
- Al, G.; Doss, R.; Chowdhury, M. Adjusting Matryoshka Protocol to Address the Scalability Issue in IoT Environment. In Proceedings of the International Conference on Future Network Systems and Security, Gainesville, FL, USA, 31 August–2 September 2017; pp. 84–94. [Google Scholar]
- Chen, Y.C.; Wang, W.L.; Hwang, M.S. RFID authentication protocol for anti-counterfeiting and privacy protection. In Proceedings of the 9th International Conference on Advanced Communication Technology, Kobe, Japan, 12–14 February 2007; Volume 1, pp. 255–259. [Google Scholar]
- Zhu, Y.; Gao, W.; Yu, L.; Li, P.; Wang, Q.; Yang, Y.; Du, J. Research on RFID-based anti-counterfeiting system for agricultural production. In Proceedings of the World Automation Congress (WAC), Kobe, Japan, 19–23 September 2010; pp. 351–353. [Google Scholar]
- Yuan, Y.; Cao, L. Liquor Product Anti-counterfeiting System Based on RFID and Two-dimensional Barcode Technology. J. Converg. Inf. Technol. 2013, 8, 88–96. [Google Scholar]
- Mackey, T.K.; Nayyar, G. A review of existing and emerging digital technologies to combat the global trade in fake medicines. Expert Opin. Drug Saf. 2017, 16, 587–602. [Google Scholar] [CrossRef] [PubMed]
- Cheung, H.; Choi, S. Implementation issues in RFID-based anti-counterfeiting systems. Comput. Ind. 2011, 62, 708–718. [Google Scholar] [CrossRef]
- Duc, D.N.; Lee, H.; Kim, K. Enhancing Security of EPCglobal Gen-2 RFID against Traceability and Cloning. In Proceedings of the SCIS 2006, Hiroshima, Japan, 17–20 January 2006. [Google Scholar]
- Choi, E.Y.; Lee, D.H.; Lim, J.I. Anti-cloning protocol suitable to EPCglobal Class-1 Generation-2 RFID systems. Comput. Stand. Interfaces 2009, 31, 1124–1130. [Google Scholar] [CrossRef]
- Johnston, R.G. An anticounterfeiting strategy using numeric tokens. Int. J. Pharm. Med. 2005, 19, 163–171. [Google Scholar] [CrossRef]
- Choi, S.; Yang, B.; Cheung, H.; Yang, Y. Data management of RFID-based track-and-trace anti-counterfeiting in apparel supply chain. In Proceedings of the 2013 8th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 9–12 December 2013; pp. 265–269. [Google Scholar]
- Koh, R.; Schuster, E.W.; Chackrabarti, I.; Bellman, A. Securing the Pharmaceutical Supply Chain; White Paper; Auto-ID Labs, Massachusetts Institute of Technology: Cambridge, MA, USA, 2003; pp. 1–19. [Google Scholar]
- Staake, T.; Thiesse, F.; Fleisch, E. Extending the EPC network: the potential of RFID in anti-counterfeiting. In Proceedings of the 2005 ACM Symposium on Applied Computing, Santa Fe, NW, USA, 13–17 March 2005; pp. 1607–1612. [Google Scholar]
- Staake, T.; Michahelles, F.; Fleisch, E.; Williams, J.R.; Min, H.; Cole, P.H.; Lee, S.G.; McFarlane, D.; Murai, J. Anti-counterfeiting and supply chain security. In Networked RFID Systems and Lightweight Cryptography; Springer: Berlin, Germany, 2008; pp. 33–43. [Google Scholar]
- Kim, J.; Kim, H. Anti-Counterfeiting Solution Employing Mobile RFID Environment; World Academy of Science, Engineering and Technology: Paris, France, 2005. [Google Scholar]
- Lehtonen, M.; Staake, T.; Michahelles, F. From identification to authentication–a review of RFID product authentication techniques. In Networked RFID Systems and Lightweight Cryptography; Springer: Berlin, Germany, 2008; pp. 169–187. [Google Scholar]
- Choi, S.; Poon, C. An RFID-based anti-counterfeiting system. IAENG Int. J. Comput. Sci. 2008, 35, 80–91. [Google Scholar]
- Brock, D.L. Integrating the Electronic Product Code (EPC) and the Global Trade Item Number (GTIN). White Paper. 2001. Volume 25. Available online: www.autoidcenter.org/pdfs/MIT-WUTOID-WH-004.pdf (accessed on 1 September 2007).
- Abawajy, J. Enhancing RFID tag resistance against cloning attack. In Proceedings of the Third International Conference on Network and System Security, Gold Coast, Australia, 19–21 October 2009; pp. 18–23. [Google Scholar]
- Dimitriou, T. A lightweight RFID protocol to protect against traceability and cloning attacks. In Proceedings of the First International Conference on Security and Privacy for Emerging Areas in Communications Networks (SECURECOMM’05), Athens, Greece, 5–9 September 2005; pp. 59–66. [Google Scholar]
- Sarma, S. Some issues related to RFID and Security. In Proceedings of the Vortrag am zweiten Workshop über RFID Security (RFIDSec’06), Graz, Austria, July 2006. [Google Scholar]
- Spiekermann, S.; Evdokimov, S. Privacy enhancing technologies for RFID-A critical investigation of state of the art research. IEEE Priv. Secur. 2009, 7, 56–62. [Google Scholar] [CrossRef]
- Klair, D.K.; Chin, K.W.; Raad, R. A survey and tutorial of RFID anti-collision protocols. IEEE Commun. Surv. Tutor. 2010, 12, 400–421. [Google Scholar] [CrossRef]
- Lakafosis, V.; Traille, A.; Lee, H.; Orecchini, G.; Gebara, E.; Tentzeris, M.M.; Laskar, J.; DeJean, G.; Kirovski, D. An RFID system with enhanced hardware-enabled authentication and anti-counterfeiting capabilities. In Proceedings of the 2010 IEEE MTT-S International Microwave Symposium Digest (MTT), Anaheim, CA, USA, 23–28 May 2010; pp. 840–843. [Google Scholar]
- Berman, B. Strategies to detect and reduce counterfeiting activity. Bus. Horizons 2008, 51, 191–199. [Google Scholar] [CrossRef]
- Jeng, A.B.; Chang, L.C.; Wei, T.E. Survey and remedy of the technologies used for RFID tags against counterfeiting. In Proceedings of the 2009 International Conference on Machine Learning and Cybernetics, Baoding, China, 12–15 July 2009; Volume 5, pp. 2975–2981. [Google Scholar]
- Juels, A. Strengthening EPC tags against cloning. In Proceedings of the 4th ACM workshop on Wireless Security, Cologne, Germany, 2 September 2005; pp. 67–76. [Google Scholar]
- Schapranow, M.P.; Müller, J.; Zeier, A.; Plattner, H. Costs of authentic pharmaceuticals: Research on qualitative and quantitative aspects of enabling anti-counterfeiting in RFID-aided supply chains. Pers. Ubiquitous Comput. 2012, 16, 271–289. [Google Scholar] [CrossRef]
- Pyun, G. 2008 Pro-IP Act: The Inadequacy of the Property Paradigm in Criminal Intellectual Property Law and Its Effect on Prosecutorial Boundaries. DePaul J. Art Tech. Intell. Prop. L. 2008, 19, 355. [Google Scholar]
- Lee, Y.S.; Kim, T.Y.; Lee, H.J. Mutual authentication protocol for enhanced RFID security and anti-counterfeiting. In Proceedings of the 2012 26th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Fukuoka, Japan, 26–29 March 2012; pp. 558–563. [Google Scholar]
- Kardaş, S.; Çelik, S.; Bingöl, M.A.; Kiraz, M.S.; Demirci, H.; Levi, A. k-strong privacy for radio frequency identification authentication protocols based on physically unclonable functions. Wirel. Commun. Mob. Comput. 2015, 15, 2150–2166. [Google Scholar] [CrossRef]
- Yan, B.; Huang, G. Application of RFID and Internet of Things in Monitoring and Anti-counterfeiting for Products. In Proceedings of the International Seminar on Business and Information Management, Wuhan, China, 19 December 2008; Volume 1, pp. 392–395. [Google Scholar]
- Rahman, F.; Ahamed, S.I. Efficient detection of counterfeit products in large-scale RFID systems using batch authentication protocols. Pers. Ubiquitous Comput. 2014, 18, 177–188. [Google Scholar] [CrossRef]
- Bansal, D.; Malla, S.; Gudala, K.; Tiwari, P. Anti-counterfeit technologies: A pharmaceutical industry perspective. Sci. Pharm. 2013, 81, 1–13. [Google Scholar] [CrossRef] [PubMed]
- Li, L. Technology designed to combat fakes in the global supply chain. Bus. Horizons 2013, 56, 167–177. [Google Scholar] [CrossRef]
- Power, G. Anti-Counterfeit Technologies for the Protection of Medicines; World Health Organization: Geneva, Switzerland, 2008. [Google Scholar]
- Cimino, M.G.; Marcelloni, F. Autonomic tracing of production processes with mobile and agent-based computing. Inf. Sci. 2011, 181, 935–953. [Google Scholar] [CrossRef]
- Al, T.; Al, G.K.; Ram Mohan Doss, R. A Survey on RFID tag ownership transfer protocols. In RFID Technology: Design Principles, Applications and Controversies; Al, G.K., Ed.; Nova Science Publishers: Hauppage, NY, USA, 2018; pp. 83–92. [Google Scholar]
- Al, T.; Al, G.K.; Ram Mohan Doss, R. Survey on RFID Security Issues and Scalability; Al, G.K., Ed.; Nova Science Publishers: Hauppage, NY, USA, 2018; pp. 37–50. [Google Scholar]
- Al, G.; Ray, B.; Chowdhury, M. Multiple Scenarios for a Tag Ownership Transfer protocol for A Closed Loop System. IJNDC 2015, 3, 128–136. [Google Scholar] [CrossRef]
| Properties | Physical | Track and Trace | Distance Bounding Protocols | Cryptography |
|---|---|---|---|---|
| Use of Resources | High | Medium | Medium | Low |
| Complexity | Medium | Medium | Low | High |
| Security | High | Medium | High | Medium |
| Limitations | High | Low | High | Low |
| Adaptability | Low | High | Low | High |
| Research | Medium | High | Low | Medium |
| Physical | Track and Trace | Distance Bounding | Cryptography | |
|---|---|---|---|---|
| Concept | Exploits physical Characteristics | Need trusted e-pedigree for tagged product authentication | Uses broadcast and collisions to identify cloned tags | Relay on the use of cryptography |
| Pros | Impossible to clone | More reliable in industry | Best for large scale RFID tags | Low cost |
| Cons | Expensive and not adaptable for every industry | Issues in synchronization between e-pedigree | Distance limitations | Weak security |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khalil, G.; Doss, R.; Chowdhury, M. A Comparison Survey Study on RFID Based Anti-Counterfeiting Systems. J. Sens. Actuator Netw. 2019, 8, 37. https://doi.org/10.3390/jsan8030037
Khalil G, Doss R, Chowdhury M. A Comparison Survey Study on RFID Based Anti-Counterfeiting Systems. Journal of Sensor and Actuator Networks. 2019; 8(3):37. https://doi.org/10.3390/jsan8030037
Chicago/Turabian StyleKhalil, Ghaith, Robin Doss, and Morshed Chowdhury. 2019. "A Comparison Survey Study on RFID Based Anti-Counterfeiting Systems" Journal of Sensor and Actuator Networks 8, no. 3: 37. https://doi.org/10.3390/jsan8030037
APA StyleKhalil, G., Doss, R., & Chowdhury, M. (2019). A Comparison Survey Study on RFID Based Anti-Counterfeiting Systems. Journal of Sensor and Actuator Networks, 8(3), 37. https://doi.org/10.3390/jsan8030037







