Spectrum Sensing in Cognitive Radio Internet of Things: State-of-the-Art, Applications, Challenges, and Future Prospects
Abstract
1. Introduction
2. Cognitive Radio Internet of Things
- (i)
- Handling the dynamic nature of the network environment: The wireless channel in which IoT devices operate changes dynamically, with the PU signal varying over time and space. Large-scale and flat fading, shadowing, and noise are common occurrences in the network environment. CR has the capability to intelligently switch IoT devices to the frequency band of wireless channel with less noise, coping with the stochastic nature of the network environment. In other words, CR can adapt to spatial temporal characteristics of wireless channels.
- (ii)
- Utilization of idle and underutilized spectrum: CR senses, adapts, and accesses spectral bands that are not used by the PUs, culminating in better utilization of the spectrum. CR also ensures that the SU hops to another frequency band if its occupation of certain band affects the operation of the PU. This prevents interference and disruption of the operation of the PU [2,3].
- (iii)
- Spectrum sharing: Another important aspect of CR is spectrum sharing, where the unused spectra are shared among the SUs without posing danger to the primary communication [3].
- (iv)
- Varying link capacity resistance: With CR, SUs can change to the frequency band with higher link capacity when there are changes in the channel’s condition and the operation of the PU is endangered.
3. SS in CRIoT Networks
3.1. Energy Detection (ED)
3.2. Cyclostationary Feature Detection (CFD)
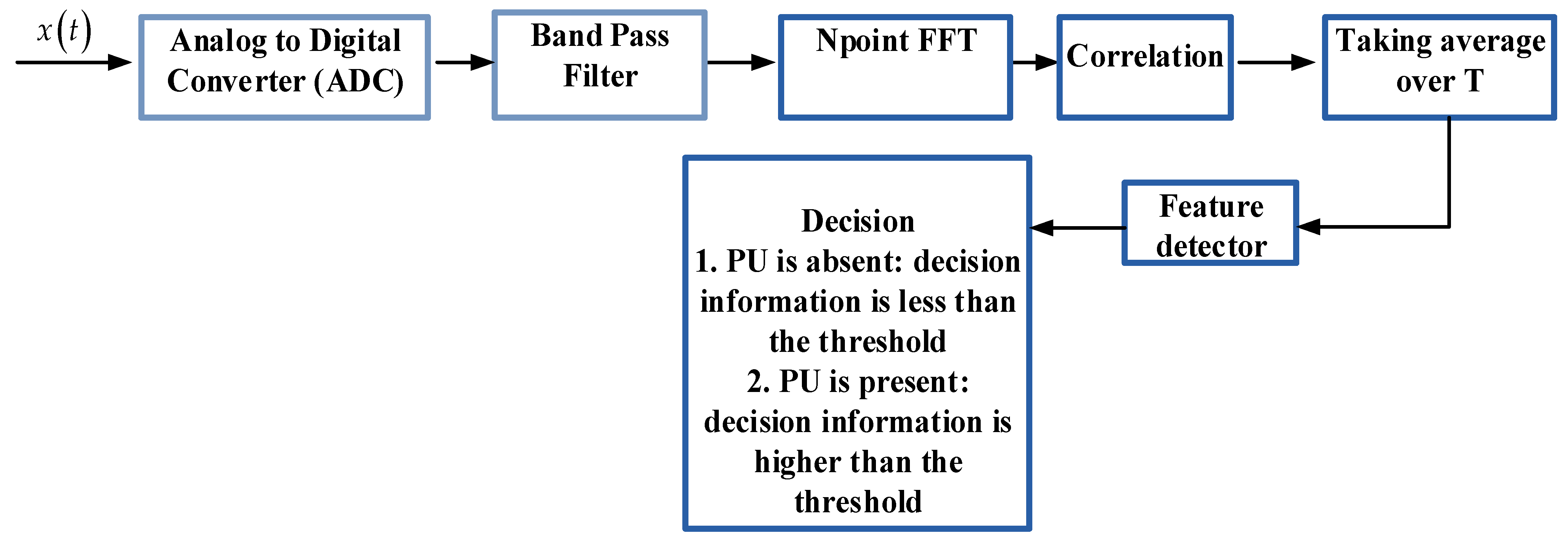
3.3. Matched Filter (MF)
3.4. Pietra–Ricci Index Detection
4. ML-Based SS Techniques
4.1. Supervised Learning
4.1.1. Support Vector Machine (SVM)
4.1.2. Logistic Regression
4.1.3. Decision Tree
4.1.4. Random Forest (RF)
4.1.5. K-Nearest Neighbor (KNN)
4.1.6. Naïve Bayes
4.2. Unsupervised Learning
4.2.1. K-Means Clustering
4.2.2. Bayesian Learning
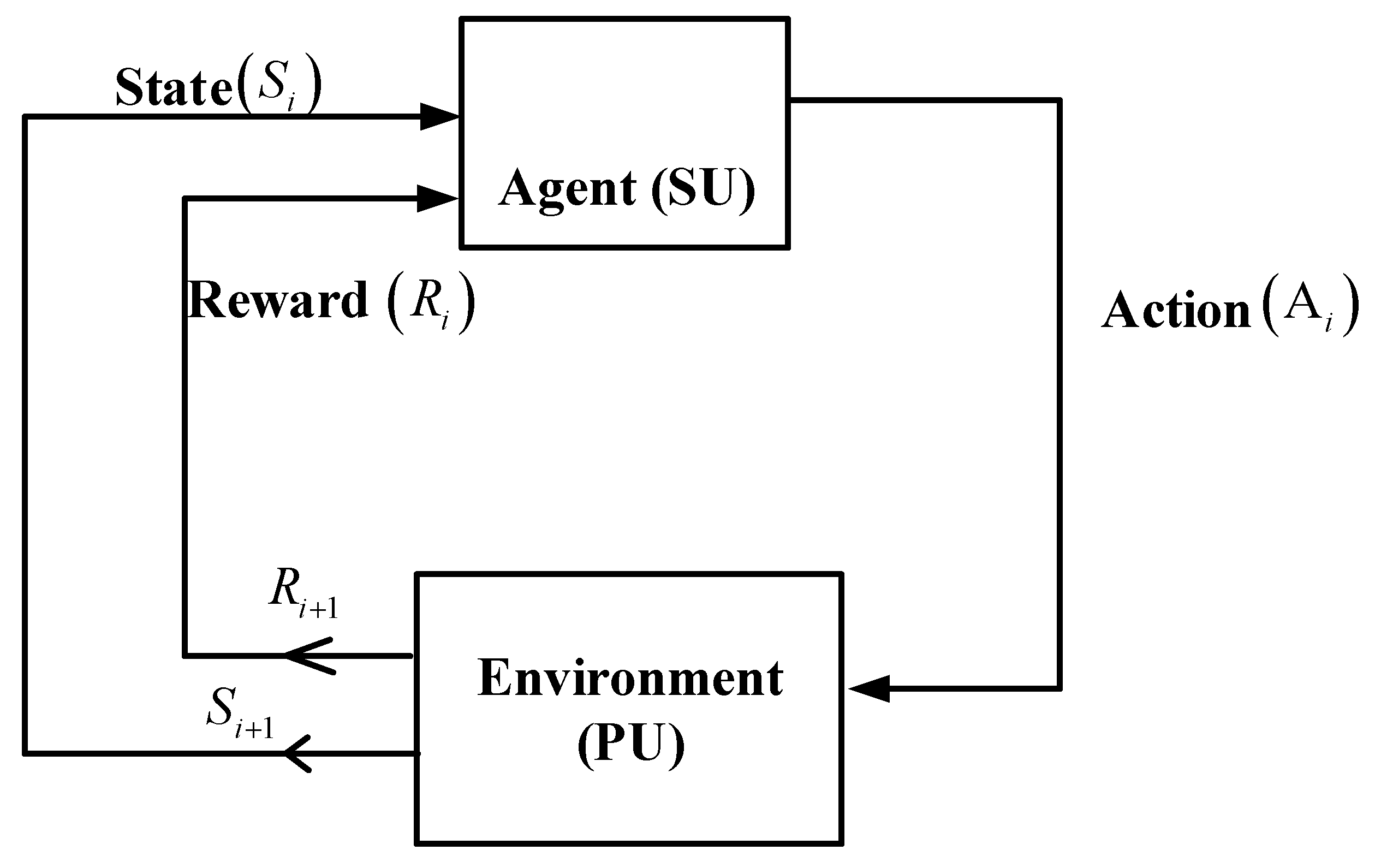
4.3. Reinforcement Learning (RL)
- (i)
- Agent: This is a device that explores the environment.
- (ii)
- Environment: This refers to the circumstances in which the agent operates, providing states and actions.
- (iii)
- State: This describes the current status of the environment as seen by the agent.
- (iv)
- Action: It refers to the choices that are available to the agent in an environment.
- (v)
- Reward: It denotes the feedback received based on the actions of the agent.
- (vi)
- Policy: This is the strategy that guides the agent’s behavior. It maps states to actions.
- (vii)
- Value function: This measures the cumulative reward an agent receives by following a particular policy.
- (viii)
- Model: This is a representation of the environment that the agent explores to forecast the outcome of its actions.
| Algorithm 1: Algorithm for training R. |
| #step 1: start #step 2: define the environment #step 3: state the reward #step 4: define the agent #step 5: train or validate the agent #step 6: implement the policy #step 7: end |
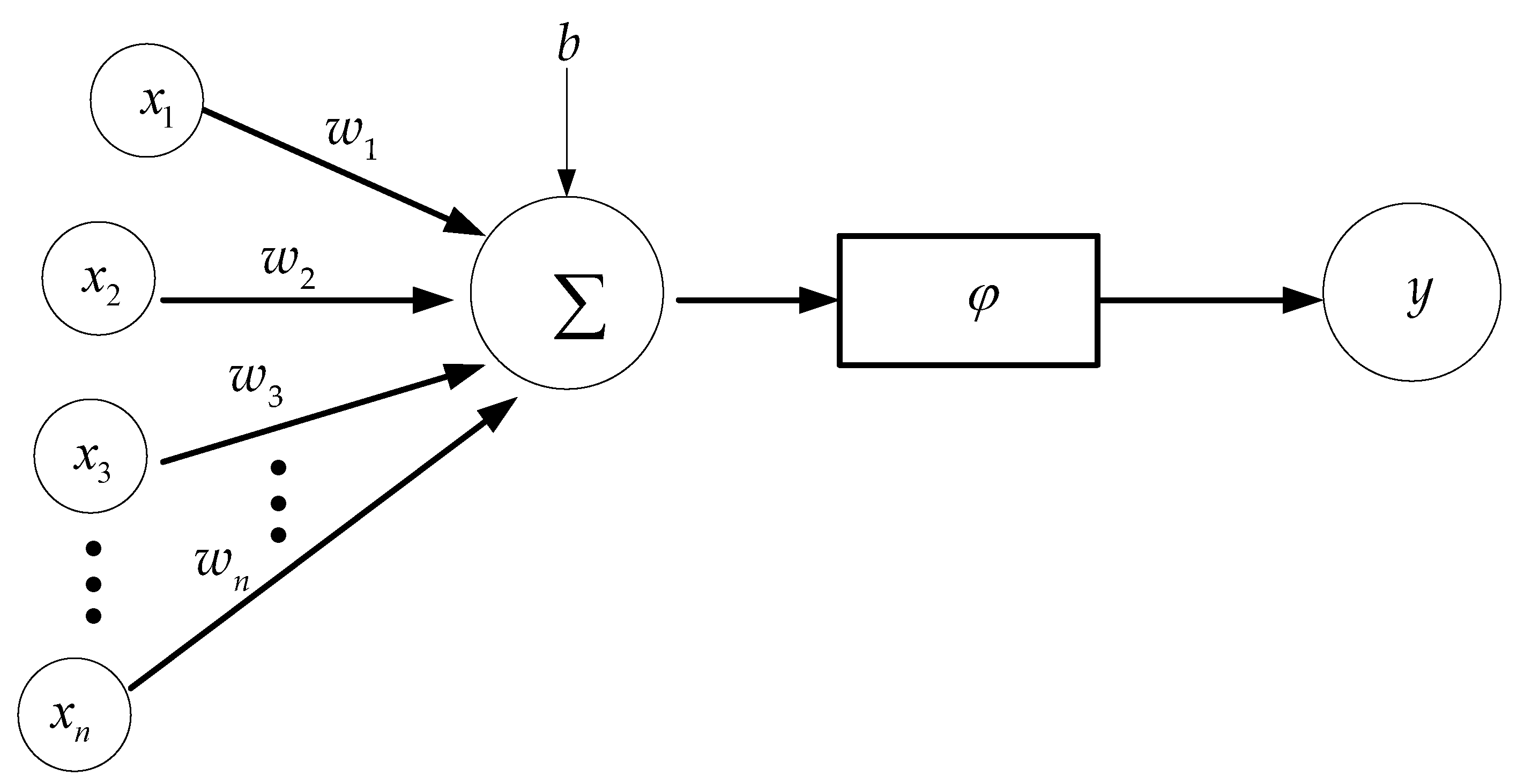
4.4. Deep Learning (DL)
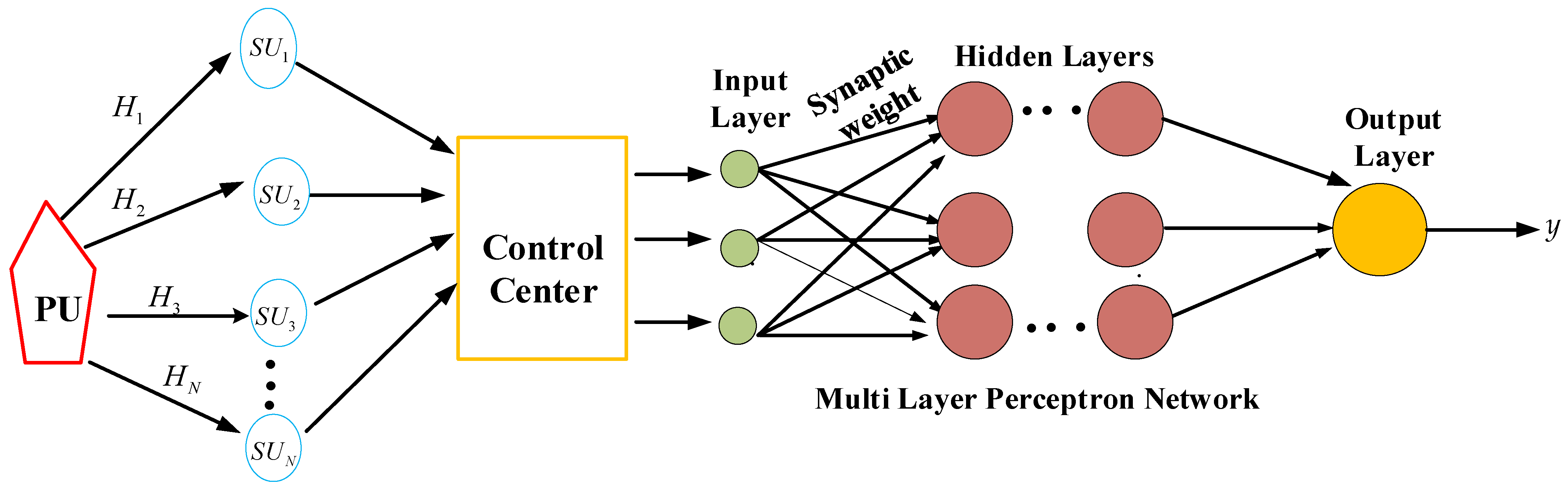
4.4.1. Multilayer Perceptron
4.4.2. Convolutional Neural Network
4.4.3. Recurrent Neural Network
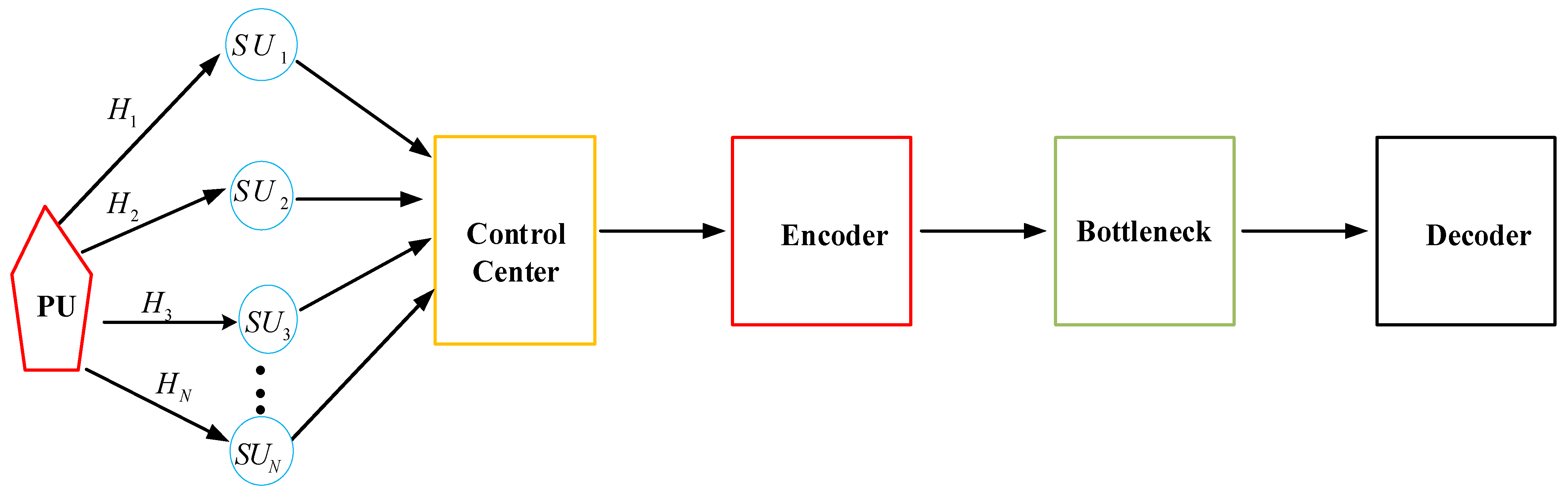
4.4.4. Autoencoder
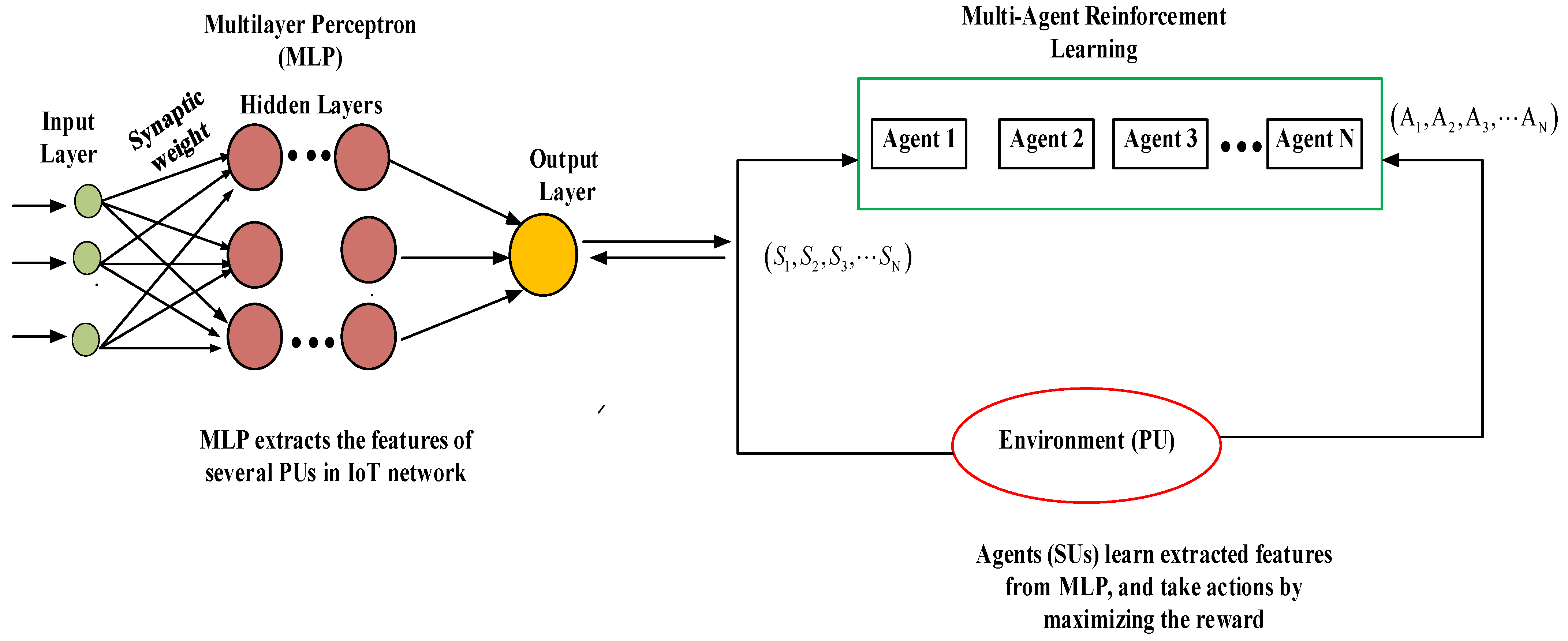
4.4.5. Multi-Agent Deep Reinforcement Learning (MADRL)
5. Review of the Application of ML for SS in Cognitive Radio Networks
6. Importance of SS in 5G and Beyond IoT Networks
- (i)
- Management of existing data spectrum: SS encourages efficient usage of spectrum resources by identifying vacant portions of primary channels that may be deployed for communication [123,124]. This preserves the cost of developing a new bandwidth for accommodating an upsurge in mobile connectivity and upcoming data-intensive applications.
- (ii)
- Enhancement of capacity and spectral efficiency of the wireless network: SS in 5G and beyond IoT networks has the potential to free up space for communication, increasing throughput and spectral efficiency [15]. With SS, new IoT devices will not be short of spectral bands and the development of IoT will not be endangered in any way.
- (iii)
- Avoidance of interference with primary communication: SUs are opportunistic users and they become active when PU bands are free or inactive. Thus, IoT devices will only occupy unused spectrums of inactive primary channels. This process reduces interference [125], prevents network delays, and reduces potential attacks on the operation of the PUs.
- (iv)
- Optimization of spectrum usage: SS supports efficient optimization of usage of the spectrum in CRIoT networks [126]. This importance prevents spectrum wastage and guarantees availability of spectral bands for communication in 5G and beyond IoT networks.
7. Lessons Learnt
- (i)
- Robustness of SS models: The wireless channel is characterized by fading, shadowing, and terrestrial disturbances. As a result, SS models must be able to withstand variation or changes in communication channels. The application of RL in such an environment suffices. The agent is trained to understand and interact perfectly with the environment. The decision is based on the maximization of the reward, which guides the training process.
- (ii)
- Training data: The performance of ML algorithms for SS depends on the number of datasets that is used to train the models. Supervised ML exhibits high accuracy and converges faster if the training data are high.
- (iii)
- Difficulty in the optimization of the models: Because of large computational resources required for training RL and DRL models, the training process can be slow, boring, unstable, and may be difficult to optimize, leading to inaccurate and inconsistent spectrum detection results.
- (iv)
- Generalization: Model-free RL algorithms may struggle to generalize beyond their training environment and may be unable to adapt to new conditions.
- (v)
- Real world applications: The trial-and-error approach of RL and DRL may create problems in real-world implementation.
8. Challenges of SS in CRIoT Network
- (i)
- Requirement for large training data: Supervised ML algorithms require a huge amount of training data for accurate SS results. It may be impossible to obtain huge training data that will capture the true characteristics of the ever-dynamic network environment in real-life scenarios. Current efforts in this regard utilize computer-generated data, which are fashioned based on simplified assumptions of the network environment and may not model the nuanced and complicated features of wireless channels in the real world [127].
- (ii)
- Huge computational resources: Supervised DL techniques like CNN and RNN require significant amounts of computational resources. This requirement can be a challenge in real time processing, especially in computer systems with limited computational facilities.
- (iii)
- Overfitting: DL techniques are susceptible to overfitting due to high levels of modeling. This may result in poor performance.
- (iv)
- Poor understanding of ML models: ML techniques are black boxes that may be hard to understand. In some cases, there may be the need to know why certain SS decisions are taken.
- (v)
- Hardware consideration: RL and DRL require fast computing power and specialized hardware like graphics processing units (GPUs) for smooth operation and implementation. Their computational complexity in real-time applications may cause difficulty when deployed in large-scale networks. This factor also limits their deployment in computer devices with constrained hardware resources.
- (vi)
- Dynamic propagation channel: The network environment changes from time to time, ensuring that SS techniques adapt to the nature of the network environment is still a concern in real-world applications. This may necessitate training, retraining, and fine tuning of the existing models.
- (vii)
- ML architecture: The nature of the architecture of the ML algorithm plays a great role in its performance. A poor choice of architecture may lead to a bad result.
- (viii)
- Powering IoT devices: IoT devices are run on batteries with a limited lifecycle, amid these, are the challenges of greenhouse effects due to improper disposal of the batteries, and large operational cost, owing to constant replacement of the batteries. Alas, this is not sustainable. Other ways of energizing IoT devices as proposed in the literature are to equip them with energy harvesters. The authors in [128] have theoretically described various energy sources that can be used, which include ambient environments, mechanical sources, thermoelectric generators, and tribo-electric nanogenerators. The authors in [129,130] have shown that small amount of D.C voltage (order of milli-volt) is obtained from an ambient environment by deploying an energy harvester, consisting of a rectifier circuit and antenna. This voltage is not enough to power a large-scale IoT network. Other sources theoretically proposed apart from ambient sources are in the budding stage of practical deployment.
9. Future Prospects
- (i)
- Interference measurement: Because the PUs are passive devices, SUs may not be aware of their precise location in the communication network. This phenomenon may cause SUs to interfere with the operation of the PUs. To the best of our knowledge, a device that allows SUs to estimate the interference at nearby PUs is currently non-existent. This device is essential in real-time implementation. Purposeful research efforts should be devoted to address this concern.
- (ii)
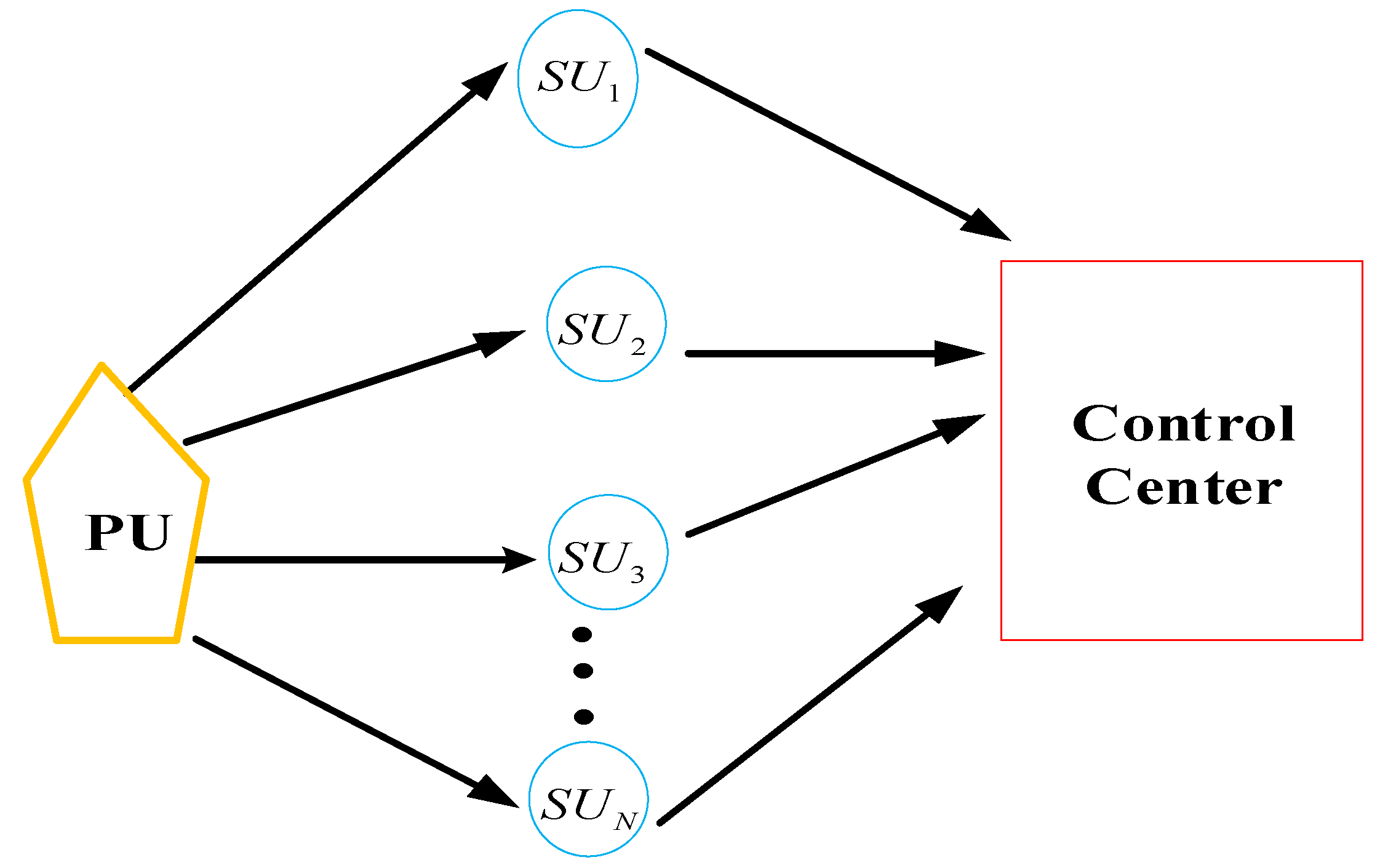
- Huge data transfer: The transfer of overall sensing data to the control center in CRIoT networks with many IoT devices may necessitate the need for huge amount of data in real-time applications. Wireless transfer of information without interfering with the operation of the PU may be impossible to achieve. Efforts should be geared towards addressing this concern without affecting primary communication.
- (iii)
- SS in multi-user environments: Most works in the literature have considered a single PU and multiple SUs as design model for investigation. IoT devices operate in multi-user network environments, where multiple PUs and SUs are present. There is a need to explore the spatial diversity inherent in multi-dimensional network environments for SS, where multiple PUs and SUs are seen to be present.
- (iv)
- Reduced time for SS: Critical attention should be paid to the reduction in time taken to sense an unused spectrum of the PUs. Future work should focus on further reducing sensing time, where less samples are utilized to detect the PU without compromising accuracy and without increasing and .
- (v)
- Fallacious result: Malicious attacks from the SUs reduce the accuracy of SS results. The attack may be in the form of false sensing results that are sent by the SUs to mislead the control center. Though the authors in [114,131] consider this scenario in their investigations, there is a need for more robust SS techniques that will notice and demystify this conundrum.
- (vi)
- Emulation of the PU: A mischievous SU may emulate and exhibit the characteristics of the PU in order to prevent other SUs from accessing the primary channel [132]. This challenge necessitates the need for novel SS techniques that will give all SUs the same leverage and ensure fairness among the SUs [133].
- (vii)
- Cost of implementation: The requirement for specialized hardware for implementing DRL and RL models may impact on the cost of the hardware resources for SS in 5G and beyond networks. Energy-efficient hardware design, consisting of miniaturized elements and less power consumption will be vital for detecting vacant spectrums in multi-dimensional network environments. This is necessary for reducing the overall cost of implementation and execution.
- (viii)
- Role of transfer learning: Transfer learning can be used to accelerate the process of detecting unoccupied spectrums in CRIoT networks, where pre-trained CNNs (or other deep learning models) are utilized for extracting the features of the input data. The learned characteristics in the hidden layers of pre-trained CNNs or MLPs are further used as features for fresh and related tasks, leading to improved performance [134]. Though the authors in [104] have cascaded hybrid CNNs and RNNs with transfer learning to improve spectrum detection at low SNRs, there is a need for more research that will leverage on transfer learning to reduce spectrum detection time.
10. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation |
| ANN | Artificial neural network |
| ASK | Amplitude shift keying |
| AWGN | Additive white Gaussian noise |
| BER | Bit error rate |
| CFD | Cyclostationary feature detection |
| CNN | Convolutional neural network |
| CR | Cognitive radio |
| CRIoT | Cognitive radio internet of things |
| CSS | Cooperative spectrum sensing |
| DL | Deep learning |
| DNN | Deep neural network |
| DRL | Deep reinforcement learning |
| ED | Energy detection |
| FSK | Frequency shift keying |
| GM | Gaussian mixture model |
| GPU | Graphics processing unit |
| ICA | Independent component analysis |
| IoT | Internet of Things |
| KNN | K-nearest neighbor |
| LTE | Long term evolution |
| LR | Logistic regression |
| LSTM | Long short-term memory |
| MBPO | Model-based policy optimizer |
| MDP | Markov decision process |
| MIMO | Multiple input multiple output |
| MRC | Maximum ratio combining |
| MF | Matched filter |
| ML | Machine learning |
| MLP | Multi-layer perceptron |
| MSE | Mean square error |
| MADRL | Multi-agent deep reinforcement learning |
| NB | Naïve Bayes |
| NCSS | Non-cooperative spectrum sensing |
| PCA | Principal component analysis |
| PILCO | Probabilistic inference for learning control |
| PSO | Particle swarm optimization |
| PU | Primary user |
| ReLU | Rectified linear unit |
| RF | Random forest |
| RL | Reinforcement learning |
| RMSProp. | Root mean square propagation |
| RNN | Recurrent neural network |
| SGD | Stochastic gradient descent |
| SNR | Signal to noise ratio |
| SS | Spectrum sensing |
| SARSA | State-action-reward–state-action |
| SU | Secondary user |
| SVM | Support vector machine |
References
- Colakovic, A.; Hadzialic, M. Internet of Things (IoT): A review of enabling technologies, challenges and open research issues. Comput. Netw. 2018, 144, 17–39. [Google Scholar] [CrossRef]
- Muzaffar, M.M.; Sharqi, R. A review of spectrum sensing in modern cognitive radio networks. Telecommun. Syst. 2024, 85, 347–363. [Google Scholar] [CrossRef]
- Yucek, T.; Arslan, H. A survey of spectrum sensing algorithms for cognitive radio applications. IEEE Commun. Surv. Tutor. 2009, 11, 116–130. [Google Scholar] [CrossRef]
- Islam, H.; Das, S.; Bose, T.; Ali, T. Diode based reconfigurable microwave filter for cognitive radio applications: A review. IEEE Access 2020, 8, 185429–185444. [Google Scholar] [CrossRef]
- Chae, K.; Kim, Y. DS2MA, A deep learning based spectrum sensing scheme for a multi-antenna receiver. IEEE Wirel. Commun. Lett. 2023, 12, 952–956. [Google Scholar] [CrossRef]
- Hlapsi, N.M. Enhancing hybrid spectrum access in CR-IoT networks: Reducing sensing time in Low SNR environments. Mesopotamian J. Comput. Sci. 2023, 2023, 47–52. [Google Scholar] [CrossRef]
- Patil, P.; Pawar, P.R.; Jain, P.P.; Manoranjan, K.V.; Pradhan, D. Enhanced spectrum sensing based on Cyclo-stationary Feature Detection (CFD) in cognitive radio network using Fixed & Dynamic Thresholds Levels. Saudi J. Eng. Technol. 2020, 5, 271–277. [Google Scholar] [CrossRef]
- Kumar, A.; Venkatesh, J.; Gaur, N.; Alsharif, M.H.; Uthansakul, P.; Uthansakul, M. Cyclostationary and energy detection spectrum sensing beyond 5G waveforms. Electron. Res. Arch. 2023, 31, 3400–3416. [Google Scholar] [CrossRef]
- Kumar, A.; Venkatesh, J.; Gaur, N.; Alsharif, M.H.; Jahid, A.; Raju, K. Analysis of hybrid spectrum sensing for 5G and 6G waveforms. Electronics 2022, 12, 138. [Google Scholar] [CrossRef]
- Solanki, S.; Dehalwar, V.; Choudhary, J. Deep learning for spectrum sensing in cognitive radio. Symmetry 2021, 13, 147. [Google Scholar] [CrossRef]
- Gao, J.; Yi, X.; Zhong, C.; Chen, X.; Zhang, Z. Deep learning for spectrum sensing. IEEE Wirel. Commun. Lett. 2019, 8, 1727–1730. [Google Scholar] [CrossRef]
- Bkassiny, M.; Li, Y.; Jayaweera, S.K. A survey on machine-learning techniques in cognitive radios. IEEE Commun. Surv. Tutor. 2012, 15, 1136–1159. [Google Scholar] [CrossRef]
- Lee, W.; Kim, M.; Cho, D. Deep cooperative sensing: Cooperative spectrum sensing based on convolutional neural networks. IEEE Trans. Veh. Technol. 2019, 68, 3005–3009. [Google Scholar] [CrossRef]
- Liu, C.; Wang, J.; Liu, X.; Liang, Y.-C. Deep CM-CNN for spectrum sensing in cognitive radio. IEEE J. Sel. Areas Commun. 2019, 37, 2306–2321. [Google Scholar] [CrossRef]
- Soni, B.; Patel, D.K.; López-Benítez, M. Long short-term memory based spectrum sensing scheme for cognitive radio using primary activity statistics. IEEE Access 2020, 8, 97437–97451. [Google Scholar] [CrossRef]
- Sarikhani, R.; Keynia, F. Cooperative spectrum sensing meets machine learning: Deep reinforcement learning approach. IEEE Commun. Lett. 2020, 24, 1459–1462. [Google Scholar] [CrossRef]
- Pati, B.M.; Kaneko, M.; Taparugssanagorn, A. A deep convolutional neural network based transfer learning method for non-cooperative spectrum sensing. IEEE Access 2020, 8, 164529–164545. [Google Scholar] [CrossRef]
- Zeng, Y.; Liang, Y.-C. Spectrum-sensing algorithms for cognitive radio based on statistical covariances. IEEE Trans. Veh. Technol. 2009, 58, 1804–1815. [Google Scholar] [CrossRef]
- Arshad, K.; Imran, M.A.; Moessner, K. Collaborative spectrum sensing optimization algorithms for Cognitive Radio Networks. Int. J. Digit. Multimed. Broadcast. 2010, 2010, 1–20. [Google Scholar] [CrossRef]
- Mahapatra, R.; Krusheel, M. Cyclostationary detection for cognitive radio with multiple receivers. IEEE ISWCS 2008, 493–497. [Google Scholar]
- Guimaraes, D.A. Pietra-Ricci index detector for centralized data fusion cooperative spectrum sensing. IEEE Trans. Veh. Technol. 2020, 69, 12354–12358. [Google Scholar] [CrossRef]
- Yawada, P.S.; Dong, M.T. Performance analysis of new spectrum sensing scheme using multi antennas with multiuser diversity in cognitive radio networks. Wirel. Commun. Mob. Comput. 2018, 2018, 8560278. [Google Scholar] [CrossRef]
- Jaronde, P.; Vyas, A.; Gaikwal, M. Spectrum efficient cognitive radio sensor network for IoT with low energy consumption. Int. J. Recent Innov. Trends Comput. Commun. 2023, 11, 469–479. [Google Scholar] [CrossRef]
- Guo, H.; Jiang, W.; Luo, W. Linear soft combination for cooperative spectrum sensing in cognitive radio networks. IEEE Commun. Lett. 2017, 21, 1573–1576. [Google Scholar] [CrossRef]
- Do, N.T.; An, B. A soft-hard combination- based cooperative spectrum sensing scheme for cognitive radio networks. Sensors 2015, 15, 4388–4407. [Google Scholar] [CrossRef]
- Nasser, A.; Hassan, H.A.; Chaaya, J.A.; Mansour, A.; Yao, K.-C. Spectrum sensing for cognitive radio: Recent advances and future challenges. Sensors 2021, 21, 2408. [Google Scholar] [CrossRef]
- Jerry, R.; Adekogba, O.O.; Maxwell, F.; Usman, A.D. A review of spectrum sensing times in cognitive radio networks. Adv. Engr. Des. Technol. 2023, 5, 29–49. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Raji, A.A.; Orimolade, J.F.; Ewetola, I.A. Design and implementation of internet of things based scheme for testing loamy soil. Turk. J. Eng. 2025, 9, 323–333. [Google Scholar] [CrossRef]
- Bhuiyan, M.N.; Rahman, M.M.; Billah, M.M.; Saha, D. Internet of Things (IoT): A review of its enabling technologies in healthcare applications, standards protocols, security, and market opportunities. IEEE Internet Things J. 2021, 8, 10474–10498. [Google Scholar] [CrossRef]
- Yang, H.; Zhong, W.-D.; Chen, C.; Alphones, A.; Xie, X. Deep-reinforcement-learning-based energy-efficient resource management for social and cognitive internet of things. IEEE Internet Things J. 2020, 7, 5677–5689. [Google Scholar] [CrossRef]
- Perera, C.; Liu, C.H.; Jayawardena, S. The emerging Internet of Things marketplace from an industrial perspective: A survey. IEEE Trans. Emerg. Top. Comput. 2015, 3, 585–598. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A survey on enabling technologies, protocols and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Shaikh, F.K.; Zeadally, S.; Exposito, E. Enabling technologies for green Internet of Things. IEEE Syst. J. 2017, 11, 983–994. [Google Scholar] [CrossRef]
- Ahan, M.S.; Pathan, A.-S.K. A comprehensive survey on the requirements, applications, and future challenges for access control models in IoT: The state of the art. IoT 2025, 6, 9. [Google Scholar] [CrossRef]
- Zhu, C.; Leung, V.C.M.; Shu, L.; Ngai, E.D.C. Green Internet of Things for Smart World. IEEE Access 2015, 3, 2151–2162. [Google Scholar] [CrossRef]
- Raji, A.A.; Orimolade, J.F.; Adejumobi, I.A.; Amusa, K.A.; Olajuwon, B.I. Channel estimation via compressed sampling matching pursuit for hybrid MIMO architectures in millimeter wave communication. Int. J. Electron. Lett. 2025, 13, 56–70. [Google Scholar] [CrossRef]
- Al-Turjman, F.M. Information-centric sensor networks for cognitive IoT: An overview. Ann. Telecommun. 2016, 72, 3–18. [Google Scholar] [CrossRef]
- Miah, M.S.; Schukat, M.; Barrett, E. A throughput analysis of an energy-efficient spectrum sensing scheme for the cognitive radio based internet of things. EURASIP J. Wirel. Commun. Netw. 2021, 201, 1–36. [Google Scholar] [CrossRef]
- Liu, X.; Li, Y.; Zhang, X.; Lu, W.; Xiong, M. Energy efficient resource optimization in green cognitive internet of things. Mob. Netw. Appl. 2020, 25, 2527–2535. [Google Scholar] [CrossRef]
- Wu, Q.; Ding, G.; Xu, Y.; Feng, S.; Du, Z.; Wang, J.; Long, K. Cognitive Internet of Things: A new paradigm beyond connection. IEEE Internet Things J. 2014, 1, 129–143. [Google Scholar] [CrossRef]
- Garhwal, A.; Bhattacharya, P.P. A survey on dynamic spectrum access technologies for cognitive radio. Int. J. Next-Gener. Netws. 2012, 3, 15–32. [Google Scholar] [CrossRef]
- Saad, M.A.; Mustafa, S.T.; Ali, M.H.; Hashim, M.M.; Bin Ismail, M.; Ali, A.H. Spectrum sensing and energy detection in cognitive networks. Indones. J. Electr. Eng. Comput. Sci. 2020, 17, 465–472. [Google Scholar] [CrossRef]
- Geng, X.; Hu, B. Maritime spectrum sensing based on cyclostationary features and convolutional neural networks. Entropy 2025, 27, 809. [Google Scholar] [CrossRef]
- Damodaram, D.; Venkateshwarlu, T. Performance analysis of cyclostationary spectrum sensing in cognitive radio. Int. J. Appl. Eng. Res. 2020, 10, 43603–43610. [Google Scholar]
- Zhang, X.; Chai, R.; Gao, F. Matched filter based spectrum sensing and power detection for cognitive radio network. In Proceedings of the 2014 IEEE Global Conference on Signal and Information Processing (GlobalSIP), Atlanta, GA, USA, 3–5 December 2014; pp. 1267–1270. [Google Scholar]
- Salahdine, F.; ElGhazi, H.; Kaabouch, N.; Fihri, W.F. Matched filter detection with dynamic threshold for cognitive radio networks. In Proceedings of the 2015 International Conference on Wireless Networks and Mobile Communications (WINCOM), Marrakesh, Morocco, 20–23 October 2015. [Google Scholar]
- Geete, P.; Gupta, M.K. Matched filter spectrum sensing technique for various fading channels of cognitive radio network. J. Emerg. Technol. Innov. Res. (JETIR) 2019, 6, 551–559. [Google Scholar]
- Kalhoro, S.; Umrani, F.A.; Khanzada, M.A.; Ali Rahoo, L. Matched filter based spectrum sensing technique for 4G cellular network. Mehran Univ. Res. J. Eng. Technol. 2019, 38, 973–978. [Google Scholar] [CrossRef]
- Maza, D.; Ojo, J.O.; Akinlade, G.O. A predictive machine learning framework for diabetes. Turk. J. Eng. 2024, 8, 583–592. [Google Scholar] [CrossRef]
- Bhardwaj, P.; Gupta, P.K.; Panwar, H.; Siddiqui, M.K.; Morales-Menendez, R.; Bhaik, A. Applications of deep learning on student engagement in e-learning environment. Comput. Electr. Eng. 2021, 93, 107277. [Google Scholar] [CrossRef]
- Hastings, P.; Hughes, S.; Britt, M.A. Active learning for improving machine learning of students. Int. Conf. Artif. Intell. Educ. 2018, 10947, 140–153. [Google Scholar]
- Siddiqui, M.K.; Morales-Menendez, R.; Gupta, P.K.; Iqbai, H.; Hussain, F.; Khatoon, K.; Ahmad, S. Correlation between temperature and CoVID-19 (suspected, confirmed and death) cases based on machine learning analysis. J. Pure Appl. Microbiol. 2020, 14, 1017–1024. [Google Scholar] [CrossRef]
- Albahri, A.S.; Khaleel, Y.L.; Habeeb, M.A.; Ismael, R.D.; Hameed, Q.A.; Deveci, M.; Homo, R.Z.; Alhbahri, O.S.; Alamoodi, A.H.; Alzubaidi, L. A systematic review of trustworthy artificial intelligence applications in natural disasters. Comput. Electr. Eng. 2024, 118, 1–53. [Google Scholar] [CrossRef]
- Wang, H.; Barone, G.; Smith, A. Current and future role of data fusion and machine learning in infrastructural health monitoring. Struct. Infrastruct. Eng. 2023, 20, 1853–1882. [Google Scholar] [CrossRef]
- De vries, A.; Blinznyuk, N.; Pinedo, P. Invited review: Examples and opportunities for artificial intelligence (AI) in dairy farms. Appl. Anim. Sci. 2023, 3, 14–22. [Google Scholar] [CrossRef]
- Hyder, U.; Talpur, M.-R.-H. Detection of cotton leaf disease with machine learning model. Turk. J. Eng. 2024, 8, 380–393. [Google Scholar] [CrossRef]
- Sinap, V. Comparative analysis of machine learning techniques for credit card fraud detection: Dealing with imbalanced datasets. Turk. J. Eng. 2024, 8, 196–208. [Google Scholar] [CrossRef]
- Praveen Kumar, D.; Amgoth, T.; Annavarapu, C.S.R. Machine learning algorithms for wireless sensor networks: A survey. Inf. Fusion 2019, 49, 1–25. [Google Scholar] [CrossRef]
- Sun, Y.; Peng, M.; Zhou, Y.; Huang, Y.; Mao, S. Application of machine learning in wireless networks: Key techniques and open issues. IEEE Commun. Surv. Tutor. 2019, 21, 3072–3108. [Google Scholar] [CrossRef]
- Kaur, J.; Khan, M.A.; Iftikhar, M.; Imran, M.; Haq, Q.E.U. Machine learning techniques for 5G and beyond. IEEE Access 2021, 9, 23472–23488. [Google Scholar] [CrossRef]
- Wang, J.; Jiang, C.; Zhang, H.; Ren, Y.; Chen, K.-C.; Hanzo, L. Thirty years of machine learning: The road to Pareto-optimal wireless networks. IEEE Commun. Surv. Tutor. 2020, 22, 1472–1514. [Google Scholar] [CrossRef]
- Alamu, O.; Olwal, T.O.; Migabo, M. Machine learning applications in energy harvesting Internet of Things Networks: A review. IEEE Access 2025, 13, 4235–4266. [Google Scholar] [CrossRef]
- Yazici, İ.; Shayea, I.; Din, J. A survey of applications of artificial intelligence and machine learning in future mobile networks-enabled systems. Eng. Sci. Technol. Int. J. 2023, 44, 101455. [Google Scholar] [CrossRef]
- Yang, X.; Song, Z.; King, I.; Xu, Z. A survey on deep semi-supervised learning. IEEE Trans. Knowl. Data Eng. 2022, 35, 8934–8954. [Google Scholar] [CrossRef]
- Arjoune, Y.; Kaabouch, N. On spectrum sensing, a machine learning method for cognitive radio systems. In Proceedings of the 2019 IEEE International Conference on Electro Information Technology (EIT), Brookings, SD, USA, 20–22 May 2019; pp. 333–338. [Google Scholar]
- Kavya, R.K.; Talmilsevi, T. Machine learning techniques in spectrum sensing. Int. J. Sci. Res. Sci. Eng. Technol. 2023, 10, 739–746. [Google Scholar]
- Eren, E.; Censur, I. Comparative analysis of machine learning models for CO emission prediction in engine performance. Sak. Univ. J. Comput. Inf. Sci. 2025, 9, 1–11. [Google Scholar] [CrossRef]
- Kim, T.; Vecchietti, L.F.; Choi, K.; Lee, S.; Har, D. Machine learning for advanced wireless sensor networks: A review. IEEE Sens. J. 2021, 21, 12379–12397. [Google Scholar] [CrossRef]
- Kumar, V.; Kandpal, D.C.; Jain, M.; Gangopadhyay, R.; Debnath, S. K-mean clustering based cooperative spectrum sensing in generalized κ-μ fading channels. In Proceedings of the 2016 Twenty Second National Conference on Communication, Guwahati, India, 4–6 March 2016; pp. 1–5. [Google Scholar]
- Sutton, R.S.; Barto, A.G. Reinforcement Learning: An Introduction; Smith, R.R., Ed.; MIT Press: Peterborough, NH, USA, 2018. [Google Scholar]
- Bouneffouf, D.; Rish, I.; Aggarwal, C. Survey on Applications of Multi-Armed and Contextual Bandits. In Proceedings of the 2020 IEEE Congress on Evolutionary Computation (CEC), Glasgow, UK, 19–24 July 2020; pp. 1–8. [Google Scholar]
- Li, F.; Yu, D.; Yang, H.; Yu, J.; Karl, H.; Cheng, X. Multi-Armed- Bandit-Based spectrum scheduling algorithms in wireless networks: A survey. IEEE Wirel. Commun. 2020, 27, 24–30. [Google Scholar] [CrossRef]
- Maghsudi, S.; Hossain, E. Multi-armed bandits with application to 5G small cells. IEEE Wirel. Commun. 2016, 23, 64–73. [Google Scholar] [CrossRef]
- Barrachina-Muñoz, S.; Chiumento, A.; Bellalta, B. Multi-armed bandits for spectrum allocation in multi-agent channel bonding WLANs. IEEE Access 2021, 9, 133472–133490. [Google Scholar] [CrossRef]
- Puterman, M.L. Markov Decision Processes: Discrete Stochastic Dynamic Programming; Wiley: Hoboken, NJ, USA, 2014. [Google Scholar]
- Sharma, N.; Mastronarde, N.; Chakareski, J. Accelerated structure-aware reinforcement learning for delay-sensitive energy harvesting wireless sensors. IEEE Trans. Signal Process. 2020, 68, 1409–1424. [Google Scholar] [CrossRef]
- Wu, K.; Jiang, H.; Tellambura, C. Sensing, probing, and transmitting policy for energy harvesting cognitive radio with two-stage after-state reinforcement learning. IEEE Trans. Veh. Technol. 2019, 68, 1616–1630. [Google Scholar] [CrossRef]
- Seijen, H.V.; Mahmood, A.R.; Pilarski, P.M.; Machado, M.C.; Sutton, R.S. True online temporal-difference learning. J. Mach. Learn. Res. 2016, 17, 5057–5096. [Google Scholar]
- Brunton, S.L.; Kutz, J.N. Data-Driven Science and Engineering: Machine Learning, Dynamical Systems, and Control; Cambridge University Press: Cambridge, UK, 2022. [Google Scholar]
- Mu, X.; Zhao, X.; Liang, H. Power allocation based on reinforcement learning for MIMO system with energy harvesting. IEEE Trans. Veh. Technol. 2020, 69, 7622–7633. [Google Scholar] [CrossRef]
- Jiang, H.; He, H.; Liu, L.; Yi, Y. Q-learning for non-cooperative channel access game of cognitive radio networks. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018. [Google Scholar]
- Mammeri, Z. Reinforcement learning based routing in networks: Review and classification of approaches. IEEE Access 2019, 7, 55916–55950. [Google Scholar] [CrossRef]
- Abu Alsheikh, M.; Hoang, D.T.; Niyato, D.; Tan, H.-P.; Lin, S. Markov decision processes with applications in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 1239–1267. [Google Scholar] [CrossRef]
- Usman, A.U.; Okereke, O.U.; Omizegba, E.E. Macrocell pathloss prediction using artificial intelligence techniques. Int. J. Electr. 2013, 101, 500–515. [Google Scholar] [CrossRef]
- Meireles, M.R.G.; Almeida, P.E.M.; Simoes, M.G. A comprehensive review for industrial applicability of artificial neural networks. IEEE Trans. Ind. Electron. 2003, 50, 585–601. [Google Scholar] [CrossRef]
- Bottou, L.; Cortes, C.; Denker, J.S.; Drucker, H.; Guyon, I.; Jackel, L.D.; LeCun, Y.; Muller, U.; Sackinger, E.; Simard, P.; et al. Comparison of classifier methods: A case study in handwritten digit recognition. In Proceedings of the 12th IAPR International Conference on Pattern Recognition, Jerusalem, Israel, 9–13 October 1994; Volume 77–82, p. 3. [Google Scholar]
- Lv, M.; Zhou, G.; He, M.; Chen, A.; Zhang, W.; Hu, Y. Maize Leaf Disease Identification Based on Feature Enhancement and DMS-Robust Alexnet. IEEE Access 2020, 8, 57952–57966. [Google Scholar] [CrossRef]
- Alippi, C.; Disabato, S.; Roveri, M. Moving Convolutional Neural Networks to Embedded Systems: The AlexNet and VGG-16 Case. In Proceedings of the 2018 17th ACM/IEEE Conference on Information Processing in Sensor Networks, Porto, Portugal, 11–13 April 2018; pp. 212–223. [Google Scholar]
- Alom, M.Z.; Taha, T.M.; Yakopcic, C.; Westberg, S.; Sidike, P.; Nasrin, M.S.; Hasan, M.; Van Essen, B.C.; Awwal, A.A.S.; Asari, V.K. A state-of-the-art survey on deep learning theory and architectures. Electronics 2019, 8, 292. [Google Scholar] [CrossRef]
- Jordan, M.I. Serial order: A parallel distributed processing approach. Adv. Psychol. Elsevier 1997, 121, 471–495. [Google Scholar]
- Balwani, N.; Patel, D.K.; Soni, B.; Lopez-Benıtez, M. Long short-term memory based spectrum sensing scheme for cognitive radio. In Proceedings of the IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019. [Google Scholar]
- Xie, J.; Fang, J.; Liu, C.; Yang, L. Unsupervised deep spectrum sensing: A variational Auto-Encoder based approach. IEEE Trans. Veh. Technol. 2020, 69, 5307–5329. [Google Scholar] [CrossRef]
- Cheng, Q.; Shi, Z.; Nguyen, D.N.; Dutkiewicz, E. Sensing OFDM signal: A deep learning approach. IEEE Trans. Commun. 2019, 67, 7785–7798. [Google Scholar] [CrossRef]
- Raj, V.; Dias, I.; Tholeti, T.; Kalyani, S. Spectrum access in cognitive radio using a two-stage reinforcement learning approach. IEEE J. Sel. Top. Sig. Process. 2018, 12, 20–34. [Google Scholar] [CrossRef]
- Vakili, S.; Liu, K.; Zhao, Q. Deterministic sequencing of exploration and exploitation for multi-armed bandit problems. IEEE J. Sel. Top. Sig. Process. 2013, 7, 759–767. [Google Scholar] [CrossRef]
- Zhu, J.; Song, Y.; Jiang, D.; Song, H. A new deep-Q-learning-based transmission scheduling mechanism for the cognitive Internet of things. IEEE Internet Things J. 2018, 5, 2375–2385. [Google Scholar] [CrossRef]
- Mnih, V.; Kavukcuoglu, K.; Silver, D.; Rusu, A.A.; Veness, J.; Bellemare, M.G.; Graves, A.; Riedmiller, M.; Fidjeland, A.K.; Ostrovski, G. Human-level control through deep reinforcement learning. Nature 2015, 518, 529–533. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Reddi, V.J. Deep reinforcement learning for cyber security. IEEE Trans. Neural Netw. Learn. Syst. 2021, 34, 3779–3795. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhang, D.; Qiu, R.C. Deep reinforcement learning for power system applications: An overview. CSEE J. Power Energy Syst. 2019, 6, 213–225. [Google Scholar]
- Ning, Z.; Xie, L. A survey on multi-agent reinforcement learning and its applications. J. Autom. Intel. 2024, 3, 73–91. [Google Scholar] [CrossRef]
- Canese, L.; Cardarilli, G.C.; Di Nunzio, L.; Fazzolari, R.; Giardino, D.; Re, M.; Spanò, S. Multi-Agent Reinforcement Learning: A Review of Challenges and Applications. Appl. Sci. 2021, 11, 4948. [Google Scholar] [CrossRef]
- Tavares, C.H.A.; Marinello, J.C.; Proenca, M.L.; Abaw, T. Machine learning-based models for spectrum sensing in cooperative radio networks. IET Commun. 2020, 14, 3102–3109. [Google Scholar] [CrossRef]
- Solanki, S.; Dehalwar, V.; Choudhary, J.; Kolhe, M.L.; Ogura, K. Spectrum sensing in cognitive radio using CNN-RNN and transfer learning. IEEE Access 2022, 10, 113482–113492. [Google Scholar] [CrossRef]
- Kumar, A.; Gaur, N.; Chakravarty, S.; Alsharif, M.H.; Uthansakul, P.; Uthansakul, M. Analysis of spectrum sensing using deep learning algorithms: CNNs and RNNs. Ain Shams Eng. J. 2024, 15, 102505. [Google Scholar] [CrossRef]
- Ajayi, O.O.; Badrudeen, A.A.; Oyedeji, A.I. Deep learning based spectrum sensing technique for smarter cognitive radio networks. J. Inven. Eng. Technol. 2021, 1, 64–77. [Google Scholar]
- Mishra, Y.; Chanudhary, V.S. Deep learning approach for cooperative sensing under congested cognitive IoT network. J. Integr. Sci. Technol. 2024, 12, 1–8. [Google Scholar] [CrossRef]
- Patel, D.K.; Lopez-Benitez, M.; Soni, B.; Garcia-Fernandez, A.-F. Artificial neural network design for improved spectrum sensing in cognitive radio. Wirel. Netw. 2020, 26, 6155–6174. [Google Scholar] [CrossRef]
- Samala, S.; Mishra, S.; Singh, S.S. Machine learning based cooperative spectrum sensing in a generalized α-κ-β fading channels. J. Sci. Ind. Res. 2023, 82, 219–225. [Google Scholar]
- Olatunji, S.A.; Fajemilehin, T.O.; Opadiji, J.F. Reduction of computational time for cooperative sensing using reinforcement learning algorithm. Afr. J. Comput. ICT 2019, 12, 90–108. [Google Scholar]
- Raghavendra, L.R.; Manjunatha, R.C. Optimizing spectrum sensing in cognitive radio using Bayesian-optimized random forest. Int. J. Intell. Eng. Syst. 2023, 16, 505–518. [Google Scholar]
- Gao, A.; Du, C.; Ng, S.X.; Liang, W. A cooperative spectrum sensing with multi-agent reinforcement learning approach in cognitive radio networks. IEEE Commun. Lett. 2021, 25, 2604–2608. [Google Scholar] [CrossRef]
- Tan, T.; Jing, X. Cooperative spectrum sensing based on Convolutional Neural Networks. Appl. Sci. 2021, 11, 4440. [Google Scholar] [CrossRef]
- Kumar, A.; Gaur, N.; Nanthaamornphong, A. Hybrid spectrum using Neural network-based MF and ED for enhanced detection in Rayleigh channel. J. Electr. Comput. Eng. 2025, 2025, 9506922. [Google Scholar] [CrossRef]
- Prasad, K.V.V.; Rao, P.T. Learning based cooperative spectrum sensing for primary user detection in cognitive radio networks. ICTACT J. Commun. Technol. 2020, 11, 3. [Google Scholar] [CrossRef]
- Li, Z.; Wu, W.; Liu, X.; Qi, P. Improved cooperative spectrum sensing model based on machine learning for cognitive radio networks. IET Commun. 2018, 12, 2485–2492. [Google Scholar] [CrossRef]
- Ning, W.; Huang, X.; Yang, K.; Wu, F.; Leng, S. Reinforcement learning enabled cooperative spectrum sensing in cognitive radio networks. J. Commun. Netw. 2020, 22, 1. [Google Scholar] [CrossRef]
- Saber, M.; ElRharras, A.; Saadane, R.; Chehri, A.; Hakem, N.; Kharraz, H.A. Spectrum sensing for smart embedded devices in cognitive networks using machine learning algorithms. Procedia Comput. Sci. 2020, 176, 2404–2413. [Google Scholar] [CrossRef]
- Zhang, Y.; Luo, Z. A deep-learning based method for spectrum sensing with multiple feature combination. Electronics 2024, 13, 2795. [Google Scholar] [CrossRef]
- Subekti, A.; Pardede, H.F.; Sustika, R.; Suyoto. Spectrum sensing for cognitive radio using deep Autoencoder neural network. In Proceedings of the 2018 International Conference on Radar, Antenna, Microwave, Electronics, and Telecommunications (ICRAMET), Serpong, Indonesia, 1–2 November 2018; pp. 81–85. [Google Scholar]
- Subray, S.; Tsschmben, S.; Gifford, K. Towards enhancing spectrum sensing: Signal classification using Autoencoder. IEEE Access 2021, 9, 82288–82299. [Google Scholar] [CrossRef]
- Li, Y.; Song, H.; Ren, X.; Zhang, Z.; Cheng, S.; Jing, X. Spectrum Sensing Meets ISAC: An Spectrum Detection Scheme for ISAC Services Based on Improved Denoising Auto-Encoder and CNN. Appl. Sci. 2025, 15, 3381. [Google Scholar] [CrossRef]
- Mourougayare, K.; Amgothu, B.; Bhagat, S.; Srikanth, S. A robust multistage spectrum sensing model for cognitive radio applications. AEU Int. J. Electron. Commun. 2019, 110, 152876. [Google Scholar] [CrossRef]
- Kockaya, K.; Develi, I. Spectrum sensing in cognitive radio network: Threshold optimization and analysis. EURASIP J. Wirel. Commun. Netw. 2020, 255, 1–20. [Google Scholar] [CrossRef]
- Fernando, X.; Lazaroui, G. Spectrum sensing, clustering algorithms, and energy harvesting technology for cognitive-radio based Internet-of-Things network. Sensors 2023, 23, 7792. [Google Scholar] [CrossRef] [PubMed]
- Song, Z.; Wang, X.; Liu, Y.; Zhang, Z. Joint spectrum resource allocation in NOMA-based cognitive radio network with SWIPT. IEEE Access 2019, 7, 89594–89603. [Google Scholar] [CrossRef]
- Obite, I.; Usman, A.D.; Okafor, E. An overview of deep reinforcement learning for spectrum sensing in cognitive radio networks. Dig. Sign. Process. 2021, 113, 103014. [Google Scholar] [CrossRef]
- Teodara, S.; George, D.-M.; Sherali, Z.; Silviu, F. Energy harvesting techniques for internet of things (IoT). IEEE Access 2021, 9, 39530–39549. [Google Scholar] [CrossRef]
- Fakharian, M.M. A high gain wideband circularly polarized rectenna with wide ranges of input power and output power. Int. J. Electron. 2021, 109, 83–99. [Google Scholar] [CrossRef]
- Erinosho, T.C.; Adekola, S.A.; Amusa, K.A. Design of practical rectennas for RF energy harvesting. In Proceedings of the 2019 Photonics & Electromagnetics Research Symposium (PIERS), Moscow, Russia, 17–20 June 2019; pp. 1149–1156. [Google Scholar]
- Manesh, M.R.; Kaabouch, N. Security threats and countermeasures of MAC layer in cognitive radio networks. Ad Hoc Netw. 2018, 70, 85–102. [Google Scholar] [CrossRef]
- Fihri, W.F.; Arjoune, Y.; El Ghazi, H.; Kaabouch, N.; Abou El Majd, B. A particle swarm optimization based algorithm for primary user emulation attack detection. In Proceedings of the 2018 IEEE 8th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 8–10 January 2018; pp. 823–827. [Google Scholar]
- Arjoune, Y.; Mrabet, Z.E.; Kaabouch, N. Multi-Attributes, Utility-Based, Channel Quality Ranking Mechanism for Cognitive Radio Networks. Appl. Sci. 2018, 8, 628. [Google Scholar] [CrossRef]
- Alican, D.; Cemal, Y. Enhancing apple plant leaf disease detection performance with transfer learning methods. Sak. Univ. J. Comput. Inf. Sci. 2025, 9, 592–605. [Google Scholar]




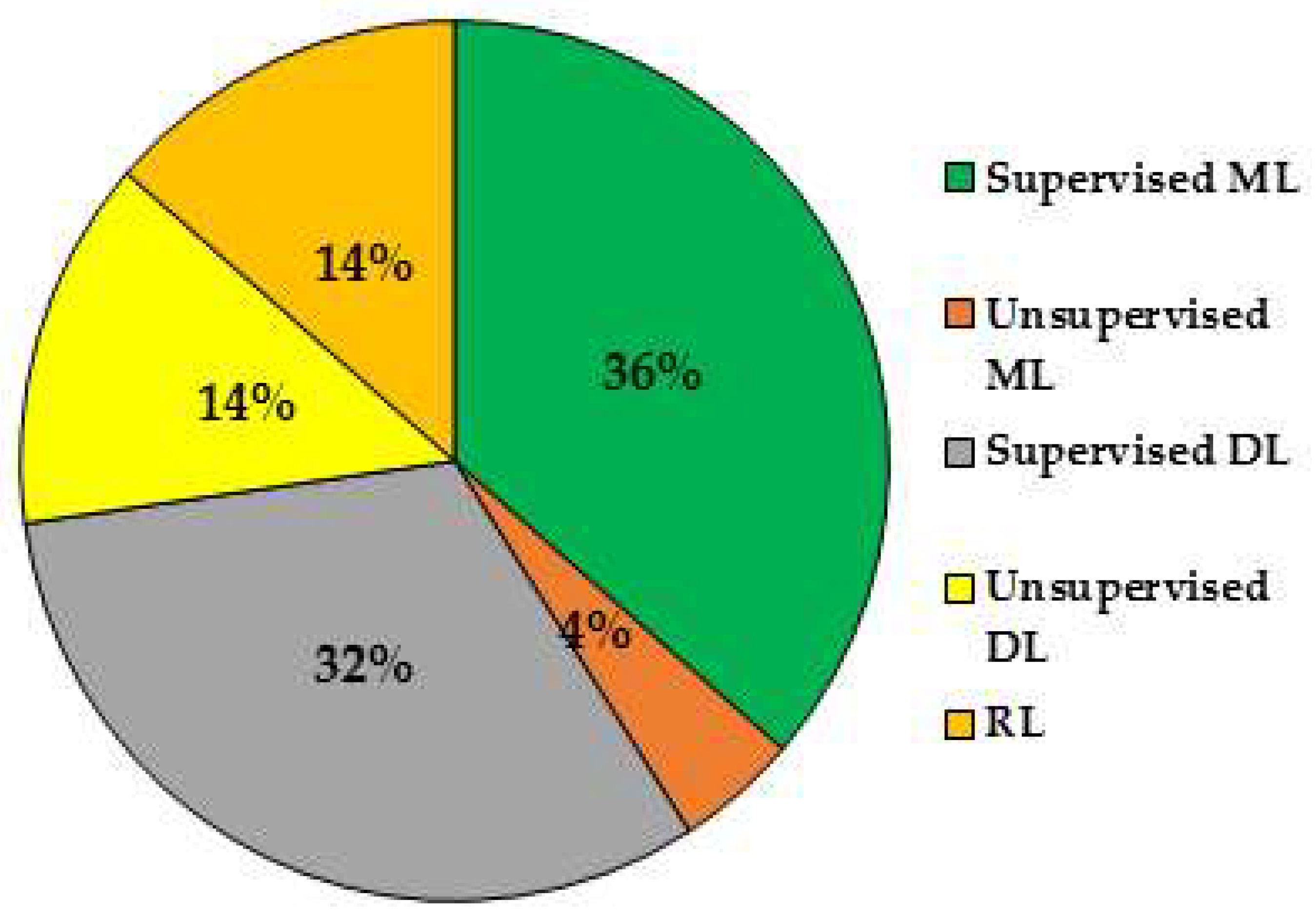
| Reference | Type of the Article | SS Methods Adopted | Contribution/Findings | Remarks/Limitations |
|---|---|---|---|---|
| [18] | Research | Statistical method | The authors introduce a statistical covariance technique for SS, which is shown to outperform ED and CFD schemes. | The performance of the proposed technique degrades at low value of the threshold. |
| [19] | Research | Genetic algorithm | Genetic algorithm is proposed to optimize the sensing time and to reduce the probability of mis-detection. | It requires knowledge of the PU and channel condition, which may not be available prior to the design of the IoT network. |
| [20] | Research | CFD | The authors show that the probability of detecting the PU in a radio network is high if MIMO antennas are used. | The work fails to account for the imperfection in the wireless channel and does not demonstrate the application of the proposed technique in a real-world scenario. |
| [21] | Research | Pietra–Ricci index detection | A novel Pietra–Ricci index detector (statistical model) is utilized to detect the presence of the PU. The proposed technique is shown to exhibit less computational complexity when compared with CFD. | Goodness of fit test, which is critical for evaluating the performance of a statistical model is not considered by the authors. |
| [22] | Research | Multi-user antenna design system | The authors propose multi-user antenna system to detect the presence of the PU in a noisy region, where ED and CFD consider such conditions as signifying the absence of the PU signal. | The proposed technique falters at high-noise regimes of the wireless channel. |
| [23] | Research | PSO | The authors propose PSO to show that detection threshold, swarm size, and the number of iterations impact on spectrum detection and spectral efficiency of the wireless network. | The authors fail to validate the proposed technique by comparing its performance with the state-of-the-art techniques. |
| [24] | Research | Linear combination scheme | Proposes linear combination scheme for SS in slow, block, and fast-fading environments. The superiority of the proposed model to conventional linear combination schemes is demonstrated. | Mobility of wireless channel, which is synonymous with real-life applications is overlooked by the authors for ease of analysis. |
| [25] | Research | Soft combination scheme | The authors propose soft combination scheme to reduce the time required for detecting the vacant spectrum in the noisy conditions of the wireless channel. The superiority of the proposed technique to ED is demonstrated. | The performance of the proposed scheme degrades at high SNR values. |
| [26] | Review | __ | Focusses the discussion on half and full duplex CR as well as SS in a wireless sensor network. CR applications in 5G and beyond network are discussed. Furthermore, the paper discusses challenges that need to be addressed in SS in the latter part of the article. | Discussion on a ML-based solution to SS problems in the CRIoT network is not presented. |
| [27] | Review | ED, CFD, MF, and wave form detection are discussed | Discussion is centered on the utilization of ED, CFD, MF, and waveform detection methods for reducing sensing time in CR networks. | ML-based solution to SS problems is not discussed. |
| This paper | Review | MF, CFD, Pietra–Ricci detection scheme and ML algorithms are discussed | Provides an overview of SS techniques employed in CRIoT networks. The techniques considered are MF, CFD, the Pietra–Ricci detection scheme, and ML algorithms. Proposes MADRL for SS in CRIoT networks. Furthermore, an overview of the studies on the application of ML algorithms is presented. In addition, challenges in implementation and open areas for further exploration are highlighted and discussed. |
| SS Techniques | Strength | Weakness |
|---|---|---|
| ED | Implementation is easy and no prior information about the PU is required. | Exhibits poor performance at low SNR. |
| CFD | Robust to noise, fading, and shadowing. | Computationally intensive and takes longer time to sense vacant spectrum. |
| MF | Demonstrates robust performance at low SNR profile of wireless medium. | Requires information about the PU, which may not be available prior to the design of the IoT network |
| Pietra–Ricci Index detector | Prior information about the PU is not required. | Performance depends on the value of the threshold. Poor choice of the value of the threshold gives false pretense about the PU. |
| Supervised Learning and Unsupervised Learning | Learns features of the PU from a given dataset without requiring either partial or full knowledge of the PU. | Large quantity of datasets is required and the accuracy of spectrum detection depends on selected features. |
| Deep Learning (CNN, MLP, and LSTM) | Demonstrates good performance at low SNR. | High quantity of datasets is needed. High computational complexity is due to large hidden layers involved in training and the manner of processing the data. |
| Reinforcement Learning | Few datasets are required for implementation. Resilient performance at low SNR and it requires less time for sensing vacant spectrum. | High computing power is needed for implementation. |
| Reference | ML Techniques | Class of the ML Techniques | Cognitive Radio Network | Main Findings | Limitations |
|---|---|---|---|---|---|
| [66] | RF, SVM, decision tree, Naïve Bayes, KNN, LR, and ANN | Supervised ML | Cooperative | The authors demonstrate that the performance of RF is superior to SVM, decision tree, Naïve Bayes, KNN, LR, and ANN. | All ML techniques considered as candidates for sensing exhibit high , which is undesirable in SS. |
| [103] | MLP, SVM, and NB | Supervised DL and supervised ML | Cooperative | MLP exhibits better performance in terms of training time and spectrum detection capability. | Attention is not paid to the assessment of the models in the non-stationary condition of the wireless channel, where SU and PU are mobile. The research is limited to the case of a single PU and three SUs. |
| [104] | Hybrid CNN-RNN and transfer learning | Supervised DL | Cooperative | Achieves high and low . | The study incurs high computational complexity that may limit its adoption in large-scale networks. |
| [105] | RNN and CNN | Supervised DL | Cooperative | CNN and RNN outperform traditional techniques in terms of , and bit error rate. | The models require large datasets for training and are susceptible to overfitting. |
| [106] | LSTM | Supervised DL | Cooperative | Higher spectrum detection accuracy and robust performance in low SNR regime of the wireless channel are achieved. | Large training datasets are needed, and relatively high detection time is required for implementing the ML technique. |
| [107] | ResNet50 | Supervised DL | Non-cooperative | The rate of detection of PUs in the CRIoT network improves with the reduction in the level of noise in the network. | Optimization of the model to reduce computational time at high SNR values is not reported. |
| [108] | ANN | Supervised ML | Non-cooperative | High detection rate at high SNR and robust performance at low SNR are demonstrated. The model is superior to ED and improved ED. | Single PU and single SU are considered for investigation but a practical wireless communication system has many PUs and SUs. |
| [109] | K-means clustering | Unsupervised ML | Cooperative | Achieves resilient detection performance in the noisy condition of the channel. | Requires large training datasets. |
| [110] | Q-learning | RL | Cooperative | Improves spectrum detection in CR network. | The impact of changes in the network environment on the performance of RL algorithm is not addressed. |
| [111] | RF | Supervised ML | Cooperative | RF exhibits better accuracy than SVM, KNN, GMM, and NB. | The work is limited to the case of a single PU and three SUs. |
| [112] | Actor–critic | RL | Cooperative | Reduces the communication overhead required for SS. | The authors do not evaluate the performance of the learning model in terms of and . The study overlooks real-world challenges and imperfections like small- and large-scale fading as well as noise interference, which may impede practical deployment. |
| [113] | CNN (AlexNet, LeNet, and VGG-16) | Supervised DL | Cooperative | Improves the accuracy of spectrum detection in the CRIoT network. The CNN models exhibit better sensing performance than traditional AND, OR, and voting-based SS schemes. | Large quantity of datasets is needed for its implementation. |
| [114] | ANN | Supervised ML | Cooperative | Utilizes an ANN to improve the performance of ED and MF at low SNRs. Achieves better accuracy in spectrum detection. Furthermore, the proposed ANN+ED and ANN+MF reduce the false alarm rate and BER. It is shown that ANN+MF outperforms ANN+ED, ED, CFD, and SVM, | High computational complexity and large training datasets are needed. The proposed models are susceptible to overfitting and require a vast amount of fine tuning to suit a real network environment. |
| [115] | SVM, KNN, and RL | Supervised ML and RL | Cooperative | Demonstrates the effectiveness of RL for SS. | The study lacks detailed analysis of practical deployment and challenges in the real world. |
| [116] | SVM | Supervised ML | Cooperative | Reduces computational time and improves the accuracy of spectrum detection. Furthermore, the work theoretically demonstrates how to reduce potential harm of redundant and abnormal SUs in an IoT network. | The paper overlooks imperfections like fading and noise interference in the real world. |
| [117] | Q-learning | RL | Cooperative | Reduces computational resources and delay in accessing the vacant PU band. | Noise interference in real-time implementation is not accounted for in the study. |
| [118] | ANN, SVM, decision tree, and KNN | Supervised ML | Experimental | Detects spectral holes of the primary communication in real time application. | Huge number of real signals are needed for training the ML models. The study overlooks the noise effect, shadowing, and multipath fading, which degrade performance in real-time applications. |
| [119] | Hybrid CNN-LSTM | Supervised DL | Cooperative | Improves the accuracy of spectrum detection in low SNR regimes of the wireless channel. | High computational complexity and dependence on large training datasets for implementation. |
| [120] | Deep Autoencoder | Unsupervised DL | __ | Utilizes a deep autoencoder to learn the features of the PUs and determine whether they are active or not. | The research overlooks imperfections associated with the wireless channel. This may derail the adoption of the model for practical applications. |
| [121] | Deep, LSTM, and variational Autoencoders | Unsupervised DL | __ | Demonstrates the superiority of LSTM and deep autoencoders in sensing and distinguishing LTE and Wi-Fi signals. | The research overlooks the impact of wireless channels on signal transmission. The effect of fading, shadowing, and noise are not considered, limiting the implementation of the study in the real world. |
| [122] | Denoising Autoencoder | Unsupervised DL | Cooperative | Proposes a denoising autoencoder for detecting the vacant spectrum in integrated sensors and communication networks. | The study overlooks the mobility or non-stationarity of the wireless channel, critical in real-life applications. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Raji, A.A.; Olwal, T.O. Spectrum Sensing in Cognitive Radio Internet of Things: State-of-the-Art, Applications, Challenges, and Future Prospects. J. Sens. Actuator Netw. 2025, 14, 109. https://doi.org/10.3390/jsan14060109
Raji AA, Olwal TO. Spectrum Sensing in Cognitive Radio Internet of Things: State-of-the-Art, Applications, Challenges, and Future Prospects. Journal of Sensor and Actuator Networks. 2025; 14(6):109. https://doi.org/10.3390/jsan14060109
Chicago/Turabian StyleRaji, Akeem Abimbola, and Thomas O. Olwal. 2025. "Spectrum Sensing in Cognitive Radio Internet of Things: State-of-the-Art, Applications, Challenges, and Future Prospects" Journal of Sensor and Actuator Networks 14, no. 6: 109. https://doi.org/10.3390/jsan14060109
APA StyleRaji, A. A., & Olwal, T. O. (2025). Spectrum Sensing in Cognitive Radio Internet of Things: State-of-the-Art, Applications, Challenges, and Future Prospects. Journal of Sensor and Actuator Networks, 14(6), 109. https://doi.org/10.3390/jsan14060109







