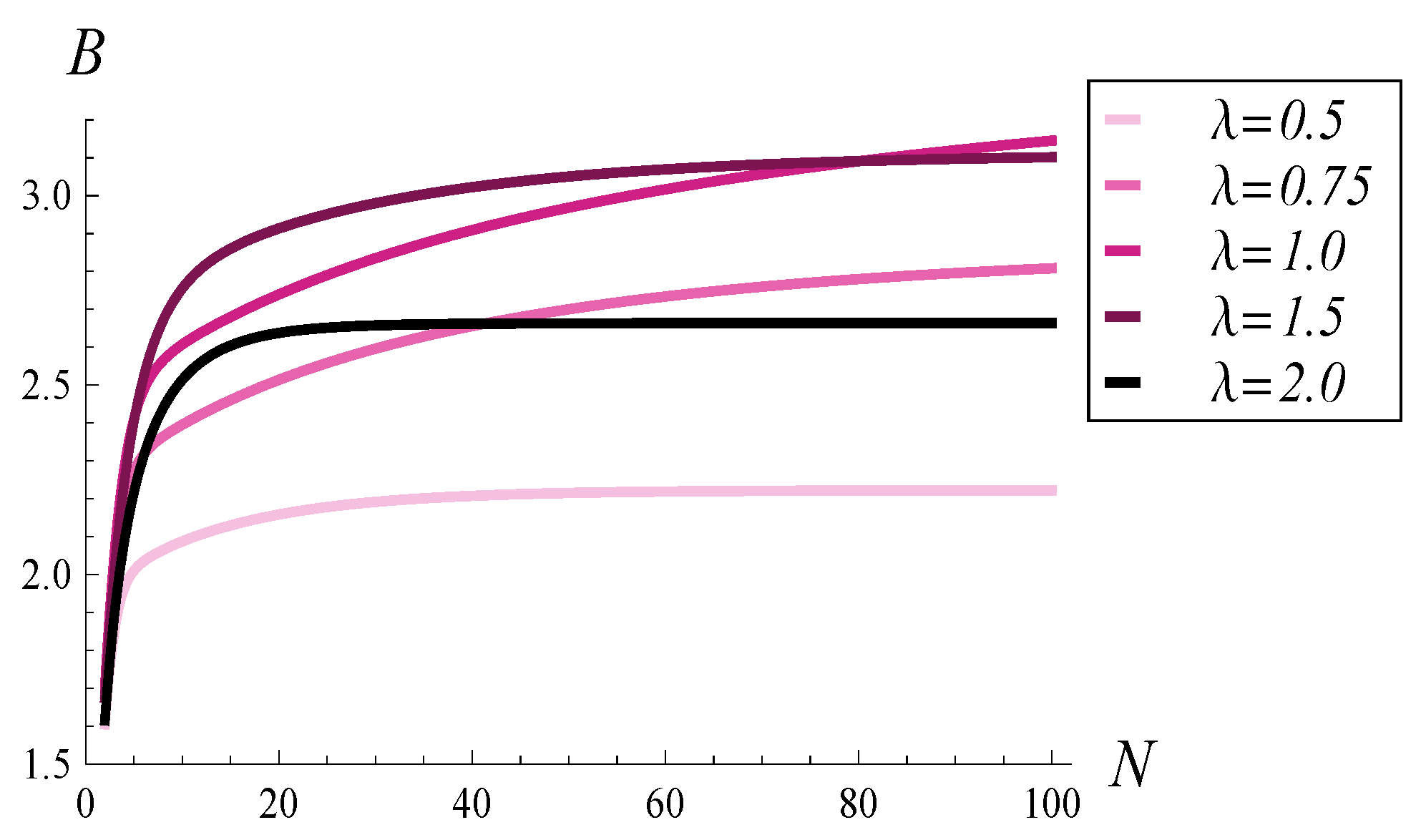1. Introduction
Packet buffers are omnipresent in computer networking, in virtually all types of networks and networking devices, including sensor and actuator networks [
1,
2,
3,
4,
5,
6,
7]. These buffers have several roles to play: they decrease packet loss by capturing traffic bursts, increase the throughput by preventing the output link from experiencing starvation, smooth the packet transmission process, and more. However, what makes the buffers less effective than wanted and expected is the autocorrelation of traffic. In particular, the consecutive packet sizes are often correlated, which arises out of the design of networking protocols.
Packets of correlated sizes, processed by a buffer, have several negative effects on queueing performance. Firstly, the packet transmission times are correlated in the same manner as the packet sizes (see the egress link in
Figure 1), which causes a decline in the throughput of the link. Secondly, the mean buffer occupancy is higher, leading to longer queueing delays. Thirdly, the buffer overflows for more time on average, resulting in greater packet loss (again, see
Figure 1).
All three of these negative effects are well understood and documented in the literature, which will be covered in the next section. There is, however, one more negative consequence of correlated packet sizes that will be studied herein: the aggregation of packet losses in groups, one after another.
Why is this important? When transmitting information of different types, it is often the case that short, isolated gaps are much less damaging than long, continuous gaps, even if the latter occur less frequently. This can be credited to the natural redundancy of information in the transmitted stream, the time-critical nature of the information, redundant coding built into the transmission, or a combination of these factors.
Consider, for illustration, a simple example of a text that is supposed to be transmitted:
Then, consider two unsuccessful transmissions of this text, such that in each of them, four letters are lost (black squares):
We can successfully guess the full message in the first transmission, while, in the second one, it is very difficult or impossible. In both cases, the loss probability is the same, 4/17, but, in the second case, the losses are grouped together. Obviously, the recovery of missing information in the first case occurs due to the natural redundancy of information in the English language. Unfortunately, this redundancy cannot help when the gap is too long.
In sensor and actuator networks, longer gaps can cause problems because of the nature of the transmitted information. For example, if a network is used to monitor temperature, pressure, or chemical solution content, it can be much more damaging when information is missing for a relatively long time–even if rarely—than when it is missing for only short moments—even if more frequently.
The International Telecommunication Union has studied in detail the decline in the quality of packetized voices due to the occurrence of packet losses in series (see the references in the next section). When a video stream is transmitted, it is perhaps less annoying for the viewer if one frame is lost after every nine frames, rather than losing ten frames in a row after ninety frames.
In general, there are many networking scenarios where a structure of losses like this:
is better than a structure of losses like this:
while it is hard to think of an example where the reverse is true.
The best parameter to express the clustering of loss is the burst ratio,
B. It is defined as the mean number of sequential losses,
, to the theoretical mean number of sequential losses,
, that occur in a Bernoulli process, i.e., when all losses happen independently of each other. By definition, we have
If the packet loss probability is
L, then it is easy to establish that
. Thus, we get
Parameter B has a very nice, intuitive explanation. When , the losses must have a statistical inclination to cluster together. The larger B, the more pronounced this inclination. Naturally, may occur only when the losses are strongly dependent on each other and when the chance that a packet is lost given that the previous one was also lost is higher than L. When , the losses must have a statistical inclination to be isolated. Again, the smaller B, the more pronounced this inclination. When , the occurrence of losses is random and independent, with clustering characteristics typical of a Bernoulli process. It is simple to confirm that for the two examples above of 17 transmitted packets with four losses, the burst ratios are 0.76 and 3.06, respectively. The very high in the latter case indicates a very strong clustering inclination.
In this study, we will calculate the burst ratio, assuming the model of a buffer with correlated packet sizes. To the best of the authors’ knowledge, such a formula has not been derived before. Then, we will examine the effect of packet size correlation, buffer size, and traffic intensity on the value of B. To derive B, we will also establish the sequential loss distribution in both transient and stationary cases. These not only constitute intermediate steps for computing the burst ratio but are also interesting as standalone characteristics.
In networking, correlated packet sizes are synonymous with correlated service (transmission) times. Therefore, in the rest of this paper, the term “correlated packet sizes” will be used interchangeably with the term “correlated service times.” To model this phenomenon, the Markovian Service Process (MSP) will be employed herein. MSP combines analytical tractability with great modeling flexibility. Specifically, it enables the modeling of arbitrary distributions of service times (packet sizes) as well as arbitrary correlations between service times.
In detail, the contributions made by this study are
a formula for the sequential loss distribution in the first and k-th buffer overflow periods (Theorems 1 and 2, respectively);
a formula for the sequential loss distribution in the stationary overflow period (Theorem 3);
a formula for the burst ratio (Theorem 4);
numerical results illustrating the impact of packet size correlation, buffer size, and traffic intensity on the burst ratio.
This study proceeds as follows. In
Section 2, previous work related to the burst ratio and buffers with MSP service is reviewed. In the next section, the model of the buffer and the packet transmission process is presented in detail. Then, in
Section 4 and
Section 5, three intermediate formulas needed for the burst ratio are given. In particular,
Section 4 presents a formula for the sequential loss distribution in the first overflow period.
Section 5 provides formulas for the sequential loss distribution in the
k-th overflow period and the stationary case.
The central result of this paper, the formula for
B, is given in
Section 6.
Section 7 discusses computational aspects of all the previously derived formulas.
Section 8 is devoted to numerical examples. First, the impact of buffer size and traffic intensity on
B is demonstrated for both positive and negative correlations of service times. Second, the effect of correlation strength is examined for the two types of correlation and compared with the uncorrelated case. Third, two examples of concrete engineering problems related to loss clustering and the burst ratio are presented and solved. Fourth, theoretical results are compared with simulation results at the end of
Section 8. Finally,
Section 9 presents concluding remarks, discusses the limitations of this study, and proposes directions for future research.
2. Related Work
To the best of the authors’ knowledge, the results of this paper are new. No previously published study has addressed the burst ratio or loss clustering at a buffer with correlated packet sizes.
Early approaches to modeling packet loss were based on abstract stochastic processes, decoupled from the actual causes of loss. These included two-state Markov chains [
8],
k-state Markov chains [
9], and the Gilbert–Elliott model [
10]. Later, the loss process was modeled using the actual, common cause of packet loss, namely, buffer overflows [
11].
The burst ratio was originally introduced in [
12]. It was initially studied for a two-state Markov loss model in [
12,
13,
14]. Specifically, the formula for
B in one loss channel was derived in [
12]. In [
13,
14], the burst ratio was established for multiple concatenated channels, where the model of each channel was founded upon a two-state Markov chain. The International Telecommunication Union studied the decline of packetized voice quality related to
B in [
15,
16]. In [
15], provisional planning values were provided for codec performance under extreme burst ratio values above 4 (see Tables I.4–5 of [
15]). In [
16], a formula expressing voice transmission impairment based on
B was proposed (see Formulas (7–29) of [
16]). More recently, the burst ratio was calculated using a buffer overflow model of losses [
17]. The study demonstrated that the buffering mechanism itself can be a source of high burst ratio values. This is relatively easy to understand: when the buffer is overflowed, it may remain so for some period of time. During this overflow period, all arriving packets are dropped consecutively, thus increasing the burst ratio. The buffer overflow period itself has also been studied as a distinct characteristic, independent of the burst ratio (see, e.g., [
18]).
It must be emphasized that up to now, studies related to the burst ratio have not incorporated correlations of packet sizes (service times). As we will see in
Section 8, this correlation has a significant impact on
B.
The correlation of service times, as incorporated in this work, is modeled using the Markovian Service Process (MSP) [
19]. This stochastic process has been used to derive various performance characteristics of buffering mechanisms [
20,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31]. These studies differed in several respects: the assumed buffer size (finite in [
20,
21,
22,
28,
29,
31] versus infinite in [
23,
24,
25,
26,
27,
30]); the performance characteristics analyzed (e.g., buffer occupancy, waiting time, loss probability, sojourn time, busy period, idle period, buffer throughput); the analytical approach (e.g., the root method in [
24]); and the treatment of batch arrivals or services.
However, none of these studies on buffers with MSP service addressed the burst ratio parameter.
Finally, note that this study deals with the FIFO policy with tail dropping, which is the simplest and most commonly used policy. Since the burst ratio strongly depends on the packet discarding policy, the results of this paper are not applicable to any of the active management policies, e.g., [
32,
33,
34,
35,
36].
3. Buffer Model
We assume a FIFO buffer with a capacity of N packets, including the one currently being transmitted, if applicable. If, on a packet arrival, the buffer is full—i.e., it already stores N packets—the new packet is discarded. Packets are served (transmitted) from the buffer’s head. Since the packet sizes are correlated, the transmission times are correlated in the same manner, which is modeled by the Markovian Service Process (MSP).
An MSP is parameterized by two square matrices, and , such that has negative elements only on the diagonal, while has all entries non-negative. Furthermore, must have each row summing to zero so that it can serve as the infinitesimal generator of a Markov chain with service states set as .
Once an MSP is parameterized, its evolution can be described as follows. If, at time t, the buffer is non-empty, the service state evolves as a Markov chain with infinitesimal generator L. Moreover, if , then at , the service state may change to k with probability , in which case, the ongoing packet service continues. Alternatively, it may change to k with probability , in which case, the ongoing packet service is completed.
During any idle period, remains unchanged and equal to the last service state prior to the buffer becoming empty.
The mean packet service rate,
, can be calculated by means of the relation
where
stands for the stationary vector for infinitesimal generator
L and
Packet arrivals follow the Poisson process of rate
. The traffic intensity
is, therefore,
where
is given in (
3).
We denote the buffer occupancy at time t by , including the packet being transmitted, if applicable.
Finally, the correlation coefficient of two consecutive service times,
, is
(see, e.g., [
37]).
4. First Series of Losses
Naturally, a few packets are lost sequentially only within a single buffer overflow period. The overflow period ends when at least one free position becomes available in the buffer. Thus, the next arriving packet will be accepted, terminating the loss sequence.
In order to derive
B using (
2), we first need to compute
, which is the mean number of sequential losses in the stationary regime. Before this can be accomplished, however, we must establish the distribution of the count of losses in the first and, more generally, the
k-th overflow period.
Therefore, the overall plan of the work requires the derivation of the following:
Sequential loss distribution in the first overflow period.
Sequential loss distribution in the k-th overflow period, .
Sequential loss distribution in the stationary overflow period.
Burst ratio, B.
Each of these tasks depends on the preceding one and must be carried out in the specified order. Task 1 is described in this section, Tasks 2 and 3 in
Section 5, and the final task in
Section 6. The characteristics obtained in Tasks 1–3 not only serve as intermediate steps toward Task 4 but are also valuable as standalone performance metrics.
Lastly, note that to compute
B from (
2), we need not only
but also the loss probability
L. This has already been computed at this stage and will be recalled in
Section 7.
We now begin with the first task. Naturally, the sequential loss distribution during the first overflow period depends on the initial conditions, specifically, the initial service state and buffer occupancy. Let be the probability that there are l packet losses during the first overflow period, given that and .
Assume first that the buffer is initially almost full, with one free position, i.e.,
. We can assemble the following equation expressing
:
Before we can explain (
6), we need to present definitions of functions
,
, and
which are present there. First,
denotes the probability of
m packet services finished in
and the service state being
j at
t, given that
and
. Second,
denotes the probability of
m packet services finished in
and having the service state
j at the end of the
m-th service, given that
and
. Third,
stands for the probability of the first service ending at
and the service state being
j just after that, given that
.
Equation (
6) can be detailed as follows. We have conditions for the time of the first arrival,
t, which yields an integral involving the exponential density
. This integral is then split into three parts, corresponding to three distinct scenarios:
No service completions by time t, which occurs with probability : In this case, the arrival at time t triggers the start of the first overflow period. The packets lost after time t form the first series of losses. Clearly, the probability that this series has length l is .
m services completed by time t, where : In this case, no overflow occurs by time t and, just after t, the buffer occupancy is . Thus, counting from t, the new probability that there will be l losses during the first overflow period is then .
services completed by time t: In this scenario, the service state stops at state j when the last service is completed. The buffer occupancy is zero just before t and becomes 1 at time t due to the arriving packet. Thus, counting from t, the new probability that there will be l losses during the first overflow period is .
Assume now the initial buffer occupancy
n of
. In this case, the equation for
is constructed as follows:
Equation (
7) can be justified just like Equation (
6), except for the first term of (
6), which is absent in (
7). The first term of (
6) accounts for an overflow event occurring at time
t. However, when starting with the buffer occupancy of no more than
packets, an overflow upon the first arrival is not possible. Therefore, no corresponding term appears in (
7).
Finally, if the buffer is vacant at the beginning, it must first reach a state where it contains exactly one packet before any overflow can occur. Moreover, the service state remains unchanged until the first arrival takes place. These considerations yield
Denoting
we obtain the following from (
6):
while obtaining the following from (
7):
Vectors and matrices are applied as follows:
Equation (
12) yields
while (
13) gives
Similarly, (
8) in this notation has the form
Exploiting Formula (7) of [
38], from (
19), we have
where
stands for the
matrix of 0 s and
is a vector of length
M. The substitution
in (
21) produces the following relation between
and
:
Hence, (
21) can be rewritten with the help of (
24) and (
25) as follows:
where
Then, combining (
18) with (
26), we get
leading to
which we know to be also equal to
, according to (
20).
This completes the derivations of for every n, which can be compiled as follows.
Theorem 1. Sequential loss distribution in the first overflow period iswhere n is the initial buffer occupancy, while , , , and are defined in (27), (9), (10), and (11), respectively. Moreover, is given in (29). In
Section 8, it will be shown how numerical values of
,
, and
can be obtained while
is a function of these three. Hence, Theorem 1 allows the distribution to be obtained effectively.
5. Subsequent and Stationary Series of Losses
We now derive the sequential loss distribution in the k-th overflow period, where . To do this, we must first establish the distribution of the service state at the end of the first overflow period.
Let denote the probability of the service state being j at the end of the first overflow period, given that and .
Assume first that the buffer initially contains
packets. We can assemble the following equation for
:
This equation is established in the same way as (
6) (see the explanation below (
6)). If the buffer initially has
packets, then we have
which is justified like (
7). Then, we have
(see the explanation below (
Section 8)). Denoting
System (
31)–(
33) is equivalent to
It is noticeable that system (
37)–(
39) has exactly the same composition as system (
18)–(
20). Hence, it can be solved likewise. Consequently, we obtain
which is an analog of (
30), and
which is an analog of (
29).
Now, consider a sequence , , …, where is the initial service state, i.e., , and for is the service state just after the k-th overflow period. The sequence forms a Markov chain, since the distribution of depends only on and not on , , etc.
Clearly, the transition
is governed by the transition matrix
, as given in either (
40) or (
41), depending on whether
or
, respectively. The transition
for
is always governed by the transition matrix
given in (
40) since, immediately after an overflow period, the buffer always contains
packets.
Consequently, the transition of the service state from the time origin to the end of the
k-th overflow period for
is covered by the matrix
Let
be the probability that there are
l packet losses during the
k-th overflow period, given that
,
, and denote
To obtain
,
, we consider the fact that at end of the
th overflow period, the buffer occupancy is
, while the service state can be obtained using transition matrix
These considerations can be recapped as follows.
Theorem 2. Sequential loss distribution in the k-th overflow period, , is:where n is the initial buffer occupancy, is given in (40) and (41), while in (30). Denote now:
Namely,
denotes the stationary probability that there are
l packet losses during an overflow period. Clearly, the initial buffer occupancy of 0 used in (
45) is irrelevant—any value can be used without affecting
.
As
, the Markov chain
reaches its stationary distribution. In other words, the distribution of the service state at the end of an overflow period will be given by the vector
p, which is a stationary distribution vector of the matrix
. It can be found by solving the well-known system
From this, we get the final result of this section.
Theorem 3. Sequential loss distribution in the stationary overflow period iswhere p stands for the stationary vector for matrix , given in (40), while is obtained in (30). 6. Burst Ratio
We are now prepared to obtain the burst ratio by means of Formula (
2).
Note first that , defined as the mean number of sequential losses, cannot be computed directly as the mean of the distribution given in Theorem 3. This is because in some overflow periods, no loss may happen at all. Certainly, every series of losses occurs within a particular overflow period, but not every overflow period results in a series of losses.
To account for this, we may calculate the probability of no packet losses in a stationary overflow period. According to Theorem 3, this probability is
. Therefore, the probability of forming a proper sequence—i.e., with non-zero losses—within a stationary overflow period is
. Thus, we have
By gathering the above formula together with all previous results, we obtain the final theorem.
Theorem 4. The burst ratio of losses at a buffer with correlated MSP service iswhereL is the packet loss probability; p stands for the stationary vector for matrix :while , , , , and E are given in (27), (9), (10), (11), and (35), respectively. Effective numerical calculation of B therefore requires computing , , , E, and L (note that is a function of and ). In the next section, we will show how all these characteristics can be computed efficiently.
7. Computational Aspects
A formula for the loss probability in the model of interest, needed in (
48), is found in [
31], page 11. Namely, it holds
where
Therefore,
L can be calculated numerically using a very small
s in (
51), e.g.,
, but calculations of
and
are required first.
can be determined using the uniformization technique (see, e.g., [
37], p. 66, for details), while
can be determined using Formulas (40)–(42) of [
31]. Applying all of these, we obtain
where
I is the identity matrix, and
Having
and
, we can compute not only
L, using (
51), but also
and
, following the obvious relations:
Therefore, what remains is to calculate
and
E. A formula for
E is well known:
(see [
37], p. 68), whereas
can be determined using the uniformization technique once more. Specifically, we have
8. Examples
8.1. Impact of Traffic Intensity and Buffer Size
We will first use a moderately strong positive correlation of packet sizes (service times), with a correlation coefficient of 0.4. The following MSP matrices produce such a correlation:
The service rate for matrices (
69) and (
70) is normalized to 1 packet per time unit. The arrival rate is varied from
to
packets per time unit, representing a range from very light to very heavy traffic. A summary of all system settings described in this subsection is shown in
Table 1.
In
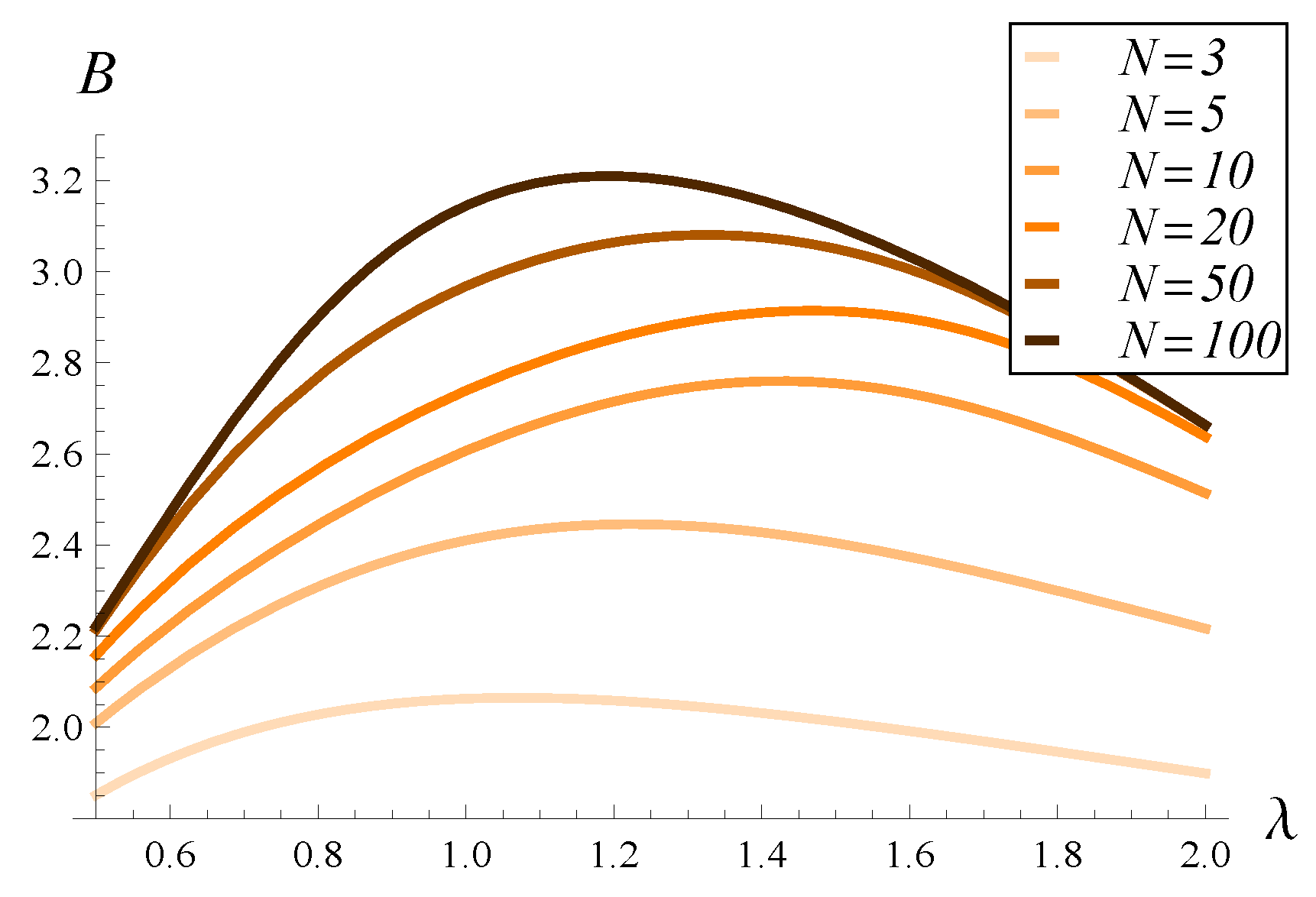
Figure 2, the effect of traffic intensity on the burst ratio is presented for six buffer sizes:
, 5, 10, 20, 50, and 100 packets.
We observe that all values of
B are very high, ranging from about 1.8 up to 3.2. This indicates that the mean series of packet losses is 2–3 times longer than it would be in the case of independent losses. Such loss clustering may have a significant impact on many applications, as was explained in
Section 1 and will be further illustrated in
Section 8.4.
Intuitively, loss clustering can be explained as follows. The buffering mechanism causes loss clustering because losses can occur only in continuous time intervals, i.e., during buffer overflow periods. During an overflow period, all arriving packets are lost consecutively, forming a sequence of losses. In other words, when a particular packet is lost at time , this means that the buffer is full at and will remain full after for at least some time. Therefore, it is likely that the next packet arriving after will also be lost.
This effect is further strengthened by the correlation of packet sizes. Specifically, the correlation makes it more likely that a sequence of longer-than-average service times occurs. A sequence like this has two possible consequences. First, it quickly increases the buffer occupancy, raising the risk of buffer overflow. Second, if an overflow does occur, the overflow period is exceptionally long because its duration equals an exceptionally long service time.
In summary, the high burst ratio is due to two factors: the buffering mechanism itself (which would increase B even without correlation) and the correlation of packet sizes. The separate influence of these two factors will be demonstrated later.
In
Figure 2, we see the burst ratio changing in a non-monotonic manner with traffic intensity. Specifically, it reaches a maximum at a certain intensity, and the position of this maximum is conditioned by the buffer size. For a very small buffer, the maximum occurs near an intensity of 1 (slightly more than 1). Then, as the buffer grows, it gets closer to 1.5. Then, when the buffer grows even more, the maximum returns to a position near 1 again.
The existence of such a maximum can be understood by considering two extreme cases: and . In the former case, both and are large, but similar, due to the fact that the loss probability is very high (most packets are lost). In the latter case, losses are extremely rare, and both and are small. Somewhere between these two extremes, a maximum can be expected. However, it is difficult to explain intuitively why this maximum occurs at a specific position, e.g., at , for a specific system parameterization. Such a specific position is a consequence of the interplay between various system parameters, each having possibly a different influence on B.
In
Figure 3, the dependence of
B on buffer size is depicted for five traffic intensities: 0.5, 0.75, 1, 1.5, and 2. We observe the burst ratio increasing with buffer size in every case. Furthermore, for both low and high traffic intensities, the burst ratio approaches its maximum relatively quickly. For example, when
, it does not change significantly beyond a buffer size of 40 packets. Similarly, when
, it stabilizes at a buffer size as small as 30 packets. However, when
is close to 1, the burst ratio continues to grow even beyond
.
As is evident in
Figure 2 and
Figure 3, a very small buffer results in a low burst ratio. This can be explained as follows. The burst ratio, as defined in (
1), accounts for the extra clustering tendency, additional to the pure random formation of loss sequences. For this reason, there is a denominator in (
1). When the buffer is very small, the loss probability is high, and there are many losses. Apparently, in this case, the purely random formation of loss sequences prevails, i.e., the value of
B is low because of the high denominator in (
1).
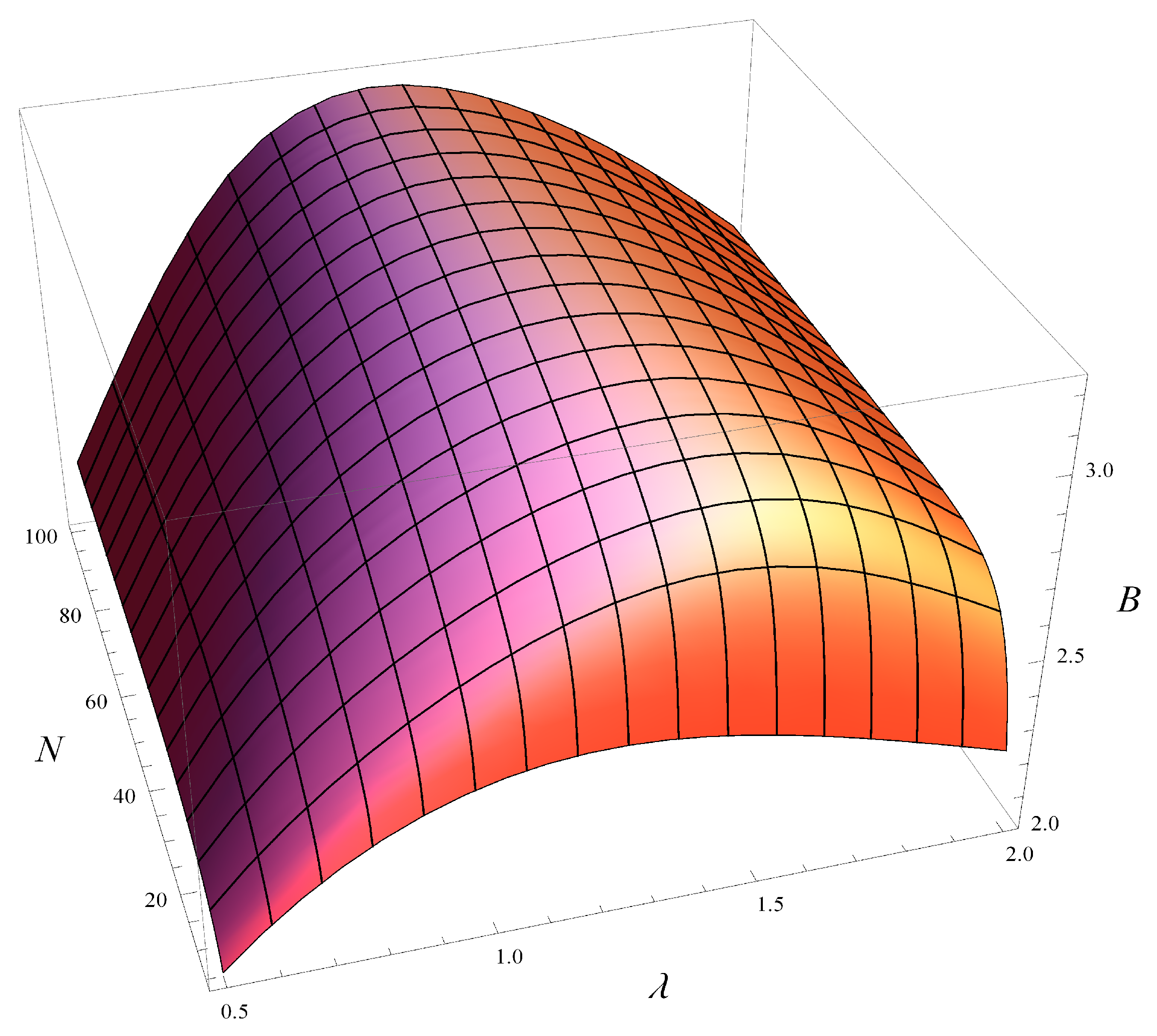
The combined impact of buffer size and traffic intensity on
B is shown in
Figure 4 for
and
. We can observe how the maximum shifts as the buffer size increases.
8.2. Impact of Negative Correlation
In the next batch of examples, we apply a correlation of the same magnitude but with the opposite sign. The following MSP matrices yield a negative correlation of −0.4, while preserving the service rate of 1:
A summary of all system settings described in this subsection is shown in
Table 2.
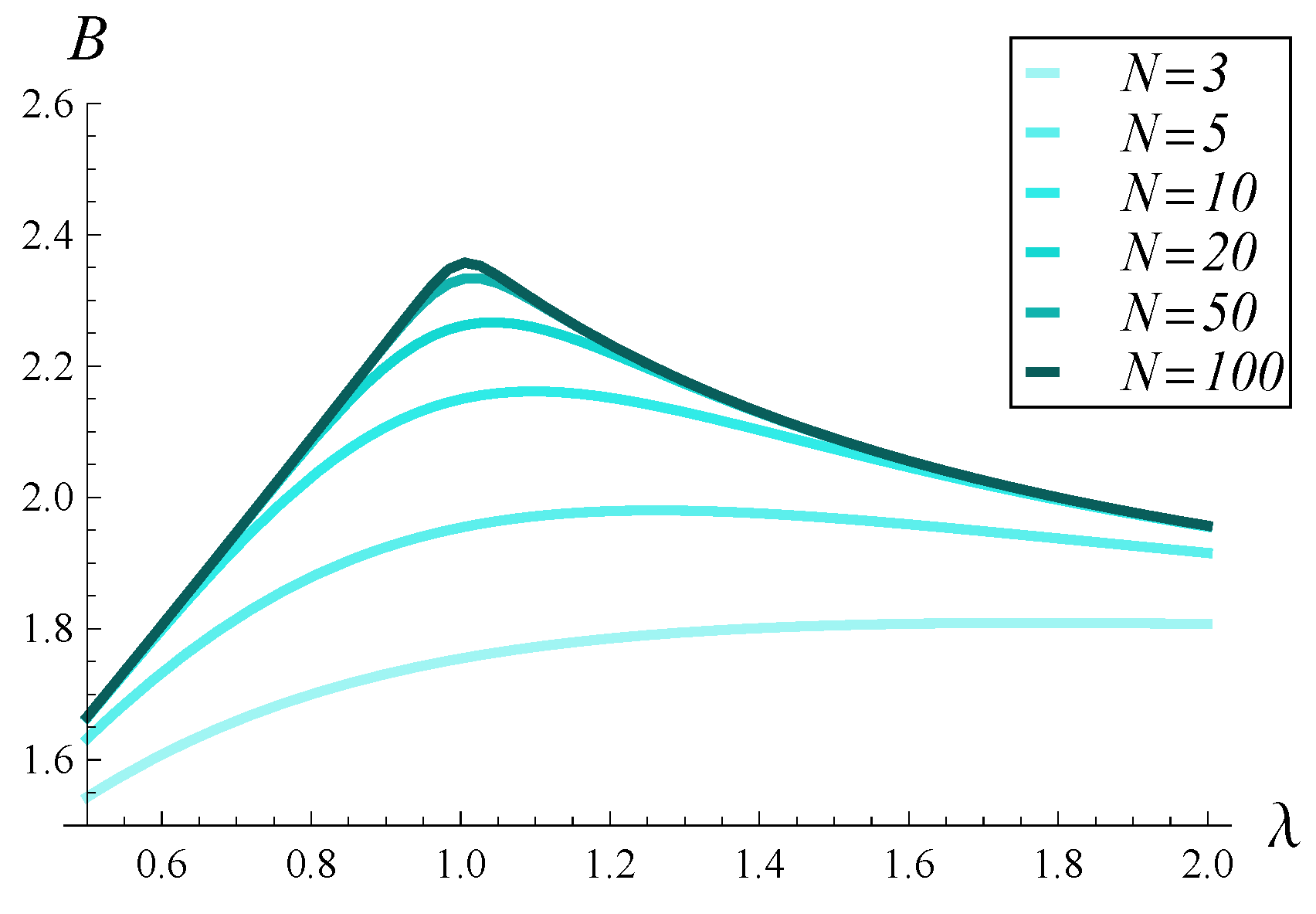
In
Figure 5, the impact of traffic intensity on
B is shown for six buffer sizes:
, 5, 10, 20, 50, and 100 packets.
We observe that in the case of a negative correlation, the burst ratio values remain high—ranging from 1.5 to 2.4—but are noticeably lower than those in
Figure 2. Once again, the burst ratio is a non-monotonic function of traffic intensity; however, in this case, the maximum is consistently located near
for all buffer sizes considered.
In
Figure 6, the impact of buffer size on
B is shown for five traffic intensities: 0.5, 0.75, 1, 1.5, and 2. In every setting, the burst ratio increases with buffer size, but it now stabilizes much more quickly than in the positive correlation setting. Specifically, for all the considered cases, except
, a buffer size as small as 15 packets is sufficient for the burst ratio to reach full saturation. In the case of
, convergence is slower, but still significantly faster than what is observed in
Figure 3.
In
Figure 7, the combined influence of buffer size and traffic intensity on the burst ratio is represented for
and
.
Figure 7 ought to be contrasted with
Figure 4, obtained for a positive correlation of packet sizes.
8.3. Impact of Correlation Strength
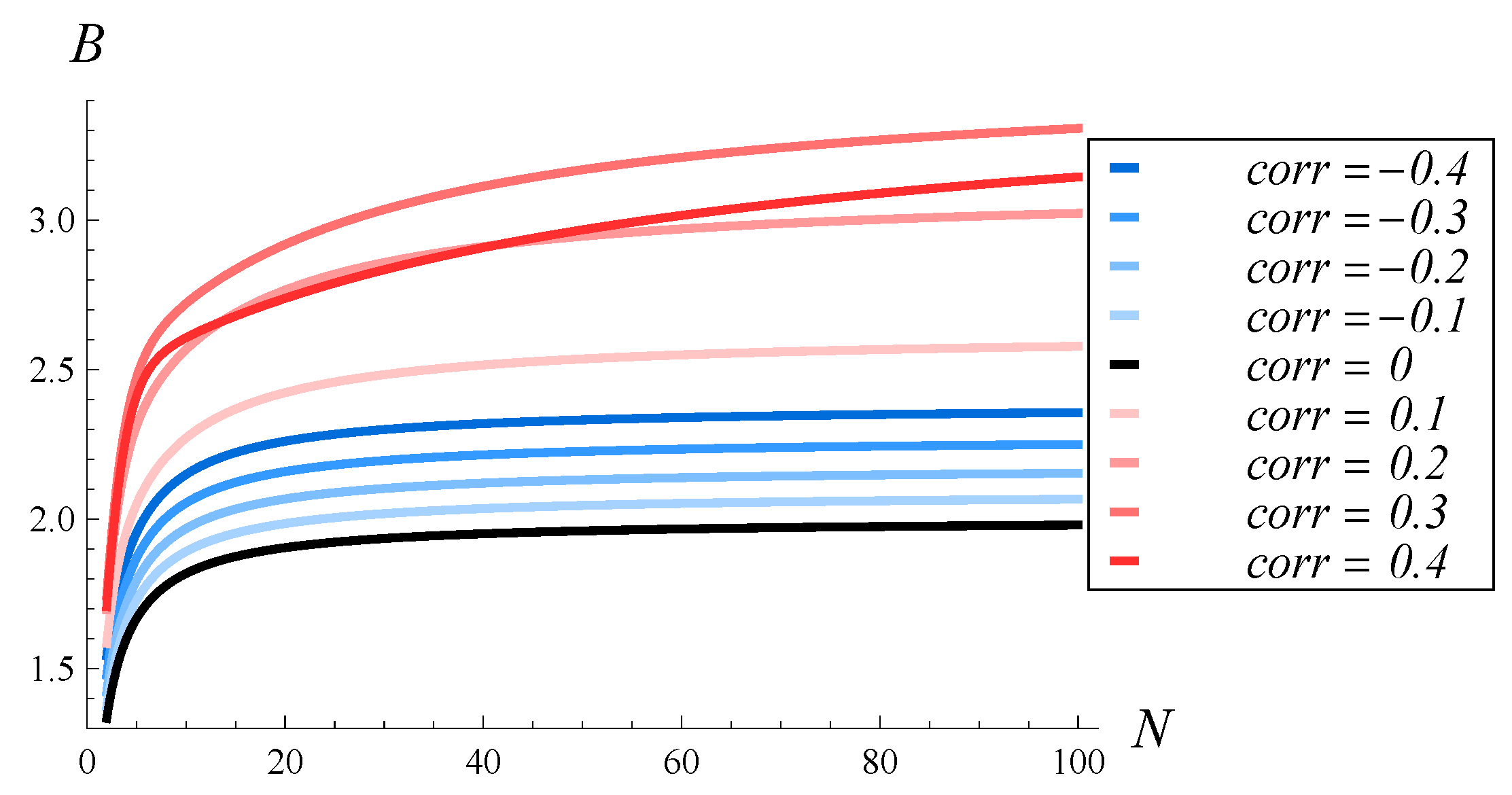
So far, we have considered a fixed correlation of service times. In this subsection, we will examine how correlations of varying strength influence the burst ratio. To accomplish this, we will use nine parameterizations of service times, with correlations of −0.4, −0.3, −0.2, −0.1, 0, 0.1, 0.2, 0.3, and 0.4.
The correlation of −0.4 is obtained using matrices (
71) and (
72). The correlation of −0.3 is obtained using matrices
where
and
are given in (
71) and (
72), respectively. The correlation of −0.2 is procured using matrices
The correlation of −0.1 is obtained using matrices
The correlation of 0 is achieved using i.i.d. service times, exponentially distributed with
. The correlation of 0.1 is obtained using matrices
where
and
are given in (
69) and (
70), respectively. The correlation of 0.2 is accomplished using matrices
The correlation of 0.3 is obtained using matrices
Finally, the correlation of 0.4 is obtained using unaltered matrices (
69) and (
70).
A summary of all system settings described in this subsection is shown in
Table 3.
In
Figure 8, the dependence of
B on traffic intensity is depicted for the nine considered correlations and a fixed buffer size of 100. Similarly, in
Figure 9, the burst ratio versus buffer size is presented for the same nine correlation values, with a fixed traffic intensity of 1.
As we observe in
Figure 8 and
Figure 9, the dependence of
B on the strength and sign of the correlation is complex. First of all, the smallest
B is always achieved for zero correlation. A negative correlation induces a higher
B than no correlation at all—compare the blue lines with the black line in
Figure 8 and
Figure 9. Second, positive correlations result in higher burst ratios than their negative counterparts—compare the red lines with the blue lines in
Figure 8 and
Figure 9. Third, the burst ratio generally increases with the strength of the correlation, whether positive or negative. Namely,
B is higher for
than for
and, similarly, higher for
than for
. However, when the correlation is strong, the burst ratio also depends heavily on
and
N. Therefore, for low
or low
N, a correlation of 0.3 can produce a higher burst ratio than a correlation of 0.4.
Finally, by comparing the red and blue lines with the black one in
Figure 8 and
Figure 9, we can assess the impact of correlation on
B, separated from the impact of the buffering mechanism itself. Specifically, the buffering mechanism alone can cause the burst ratio to rise up to 1.9, even in the absence of a correlation (see the black line in
Figure 8). A negative correlation can increase it further, up to 2.3 (top blue line), while a positive correlation pushes it even higher, up to 3.3 (top red line).
8.4. Concrete Problem Solutions
Now, we can demonstrate how the obtained theoretical results can be used to solve concrete engineering problems.
Assume, for instance, that a sensor node is monitoring a system or device. The monitoring data is transmitted in packets. A critical system error occurs when 10 packets of monitoring data are missing in a row.
Problem 1. Compute the probability that a critical error occurs within a week of system operation. Assume buffer size
,
, and the correlation structure as in (
69), (
70).
Problem 2. What buffer size is needed to make the probability of a critical error occurring less than 0.001?
Problem 1 solution. From (
51), we can obtain the overall packet loss probability for
. We have
Given such a loss probability, one might naively deduce that it is very unlikely to lose 10 packets in a row because
is an extremely small number (on the order of
). As we will see, this conclusion is completely wrong. To find the correct solution, we first compute the burst ratio from Theorem 4. We have
Then, we obtain the average length of the series of losses:
Using Theorem 3, we calculate the probability that an arbitrary series of losses has a length less than 10:
Within a week, the node sends, on average, 302,400 packets with monitoring data, out of which 993 packets are lost. Therefore, we can expect the following number of separate series of losses within a week:
The probability that at least one of these series of losses consists of 10 or more packets is then
As we can see, it is very likely to have a critical system error within a week, with a probability exceeding 0.8.
Problem 2 solution. To solve this problem, we can simply increase
N and repeat all the calculations as long as is necessary, i.e., until the probability of the critical error occurring goes below 0.001. In
Figure 10, we can see the full dependence of the critical error probability on the buffer size, up to
. Specifically, for
, we have
, which completes the solution of the second problem.
Naturally, the solutions to the problems presented above depend on matrices (
69) and (
70), which here constitute only one selected example. What is crucial is that there are well-known methods to fit these matrices precisely to any packet size correlation structure and packet size distribution. These methods are described in detail in
Section 5 of the excellent monograph in [
39]. In
Section 7 of the same monograph, the reader can find recommended software tools to automate the fitting process. Therefore, the problems in this section can be solved for streams of packets with arbitrary size distributions and correlations.
8.5. Verification via Simulations
Theoretical results were also verified through simulations performed in the OMNeT++ network simulator [
40], version 5.6. The simulation granularity was set to
, i.e., the setting
simtime-scale = −9 was used in the OMNeT++ configuration file. The buffer model presented in
Section 3 was implemented manually, without the use of any specialized libraries, except for the general OMNeT++ libraries.
Twelve simulation scenarios were conducted, featuring various combinations of traffic intensity, buffer size, and correlation type. In each scenario, packets were processed by the buffer, and the resulting burst ratio was measured and compared with its theoretical counterpart.
The results are summarized in
Table 4. As we see, there is excellent agreement between the simulated values and their theoretical counterparts in every scenario.
9. Conclusions
We studied the effect of the correlation of packet sizes (service times) on the packet loss clustering, when the losses are caused by overflows of a FIFO buffer. Specifically, we established formulae for the sequential losses distribution in the first, k-th, and stationary overflow periods, using a model that allows for arbitrarily strong correlation (MSP). Based on these results, we derived the final formula for the burst ratio. All computational aspects were addressed, making the formulae fully applicable.
The mathematical results were then exploited in numeric examples, showing the effects of packet size correlation, buffer size, and traffic intensity on the burst ratio. Several noteworthy observations were made. Most importantly, we found that a positive correlation of service times significantly increased the burst ratio compared to the uncorrelated case across all scenarios, regardless of buffer size or traffic intensity. A negative correlation also increased the burst ratio, but to a lesser extent than a positive correlation.
We also observed that the burst ratio varies non-monotonically with traffic intensity, exhibiting a clear maximum. In the case of a positive correlation, the location of this maximum depends on the buffer size. Specifically, for very small buffers, the maximum occurs near a traffic intensity of 1. As the buffer grows, it gets closer to 1.5. Then, when the buffer grows even more, the maximum returns to a position near 1. This effect does not appear in negative or uncorrelated cases, where the maximum consistently occurs near a traffic intensity of 1, regardless of buffer size.
The burst ratio increases monotonically with buffer size, regardless of traffic intensity and correlation type. In most scenarios, it saturates quickly, reaching a maximum value at relatively small buffer sizes, after which, further increases in buffer size have no effect. This convergence is significantly slower, however, in scenarios with a positive service time correlation and a traffic intensity of 1.
In addition to these numeric calculations, we presented two examples of concrete engineering problems related to loss clustering and the burst ratio. The problems were then solved using two main theoretical results of this paper, i.e., Theorems 3 and 4.
The limitations of this study are twofold. Firstly, we considered only one particular buffer policy, namely, the FIFO policy with tail dropping. This policy is commonly used in networking devices of all types, but it is not the only existing approach. For instance, many active buffer management policies have been proposed for various devices and networks. Since the burst ratio strongly depends on the packet discarding policy, the results of this paper are not applicable to any of the active management policies.
The second limitation of this study is related to the fact that, in addition to packet service times, packet interarrival times can also be correlated in real networks. This effect is not taken into account in the model considered here, although it can certainly affect the burst ratio. Therefore, the results of this paper are applicable to traffic with uncorrelated or only weakly correlated interarrival times. For moderate or strong correlations of interarrival times, the model would likely produce significant errors.
These limitations clearly suggest two directions for future research. First, the burst ratio under buffer policies other than FIFO with tail dropping can be investigated. A promising starting point could be a RED-type active buffer management policy. Second, the burst ratio could be studied in a model incorporating both interarrival time correlations and service time correlations. A natural candidate for modeling correlated interarrival times would be the Markovian Arrival Process (MAP), in the addition to the Markovian Service Process (MSP) used here.