An Improved Chosen Plaintext Attack on JPEG Encryption
Abstract
1. Introduction
2. Current CPA Scheme
2.1. ACC Encryption in He et al.’s JPEG Encryption Algorithm
2.2. Security Vulnerabilities in He et al.’s ACC Encryption
2.3. The Five Steps of the Current CPA Scheme
2.4. The Overall Process of the Current CPA Scheme
2.5. Current Limitations of the Single Permutation Method
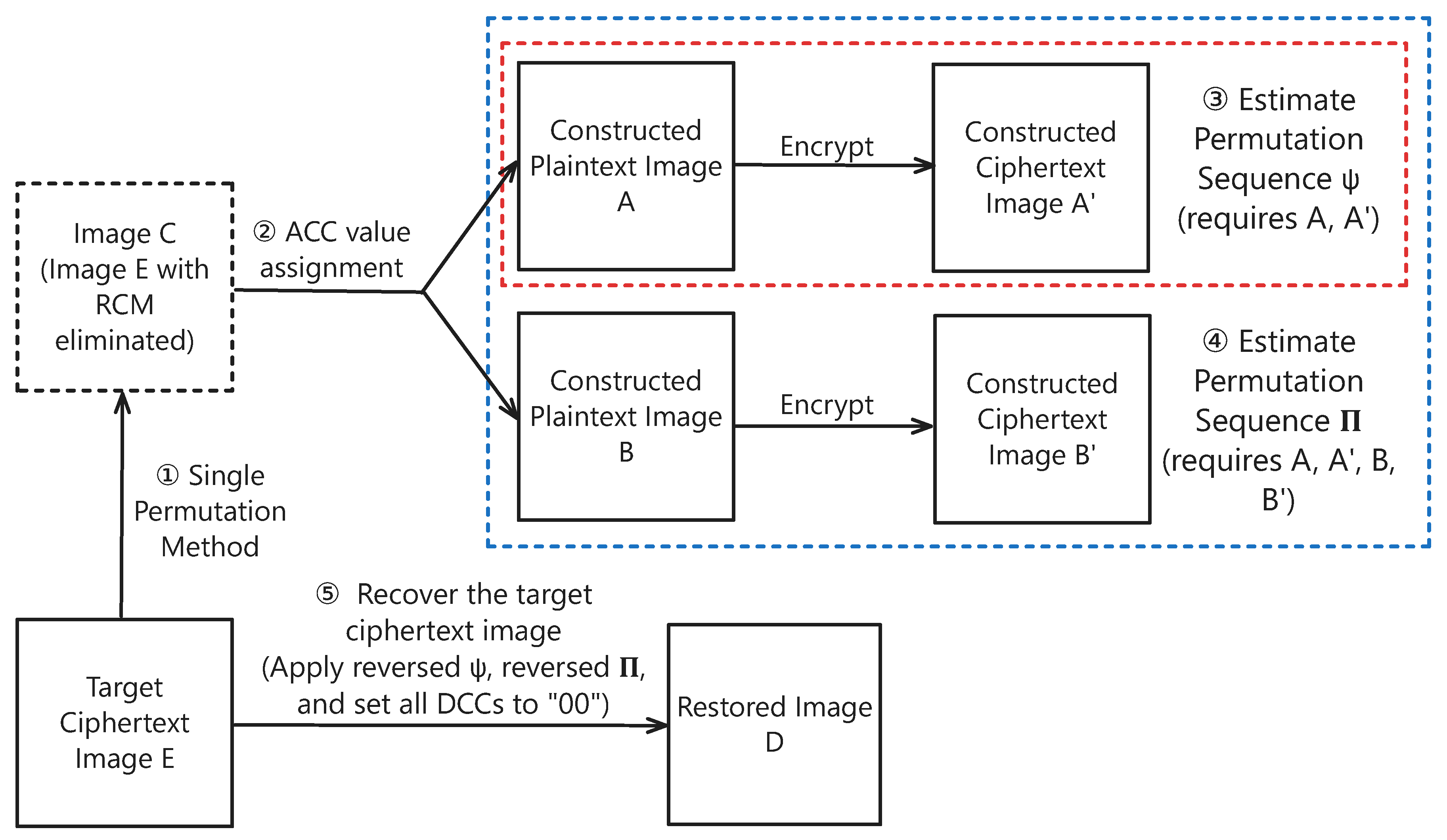
3. Improved CPA Scheme
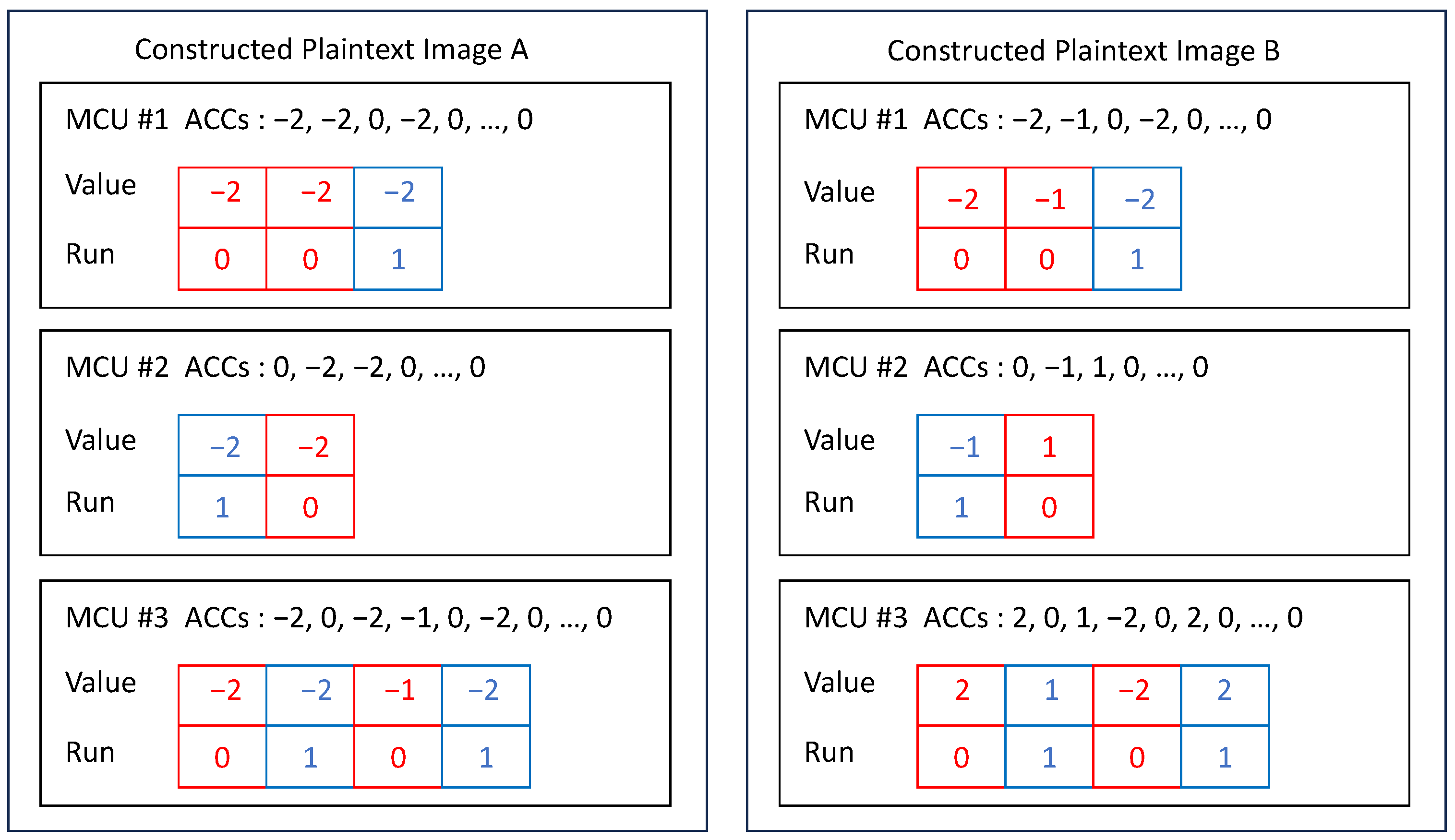
3.1. Plaintext Image Generation Using the Additive Value Method
3.2. The Overall Process of the Improved CPA Scheme
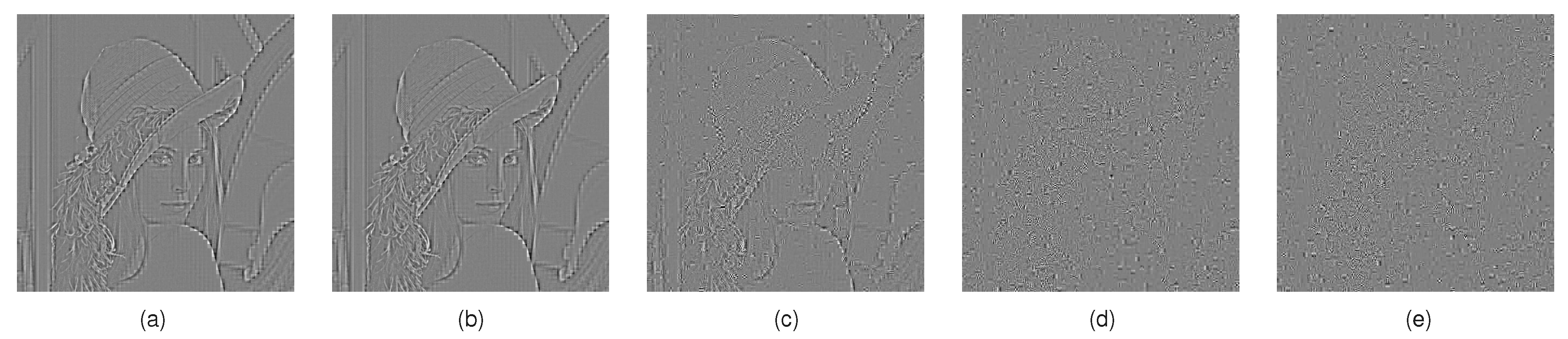
4. Experimental Results and Analysis
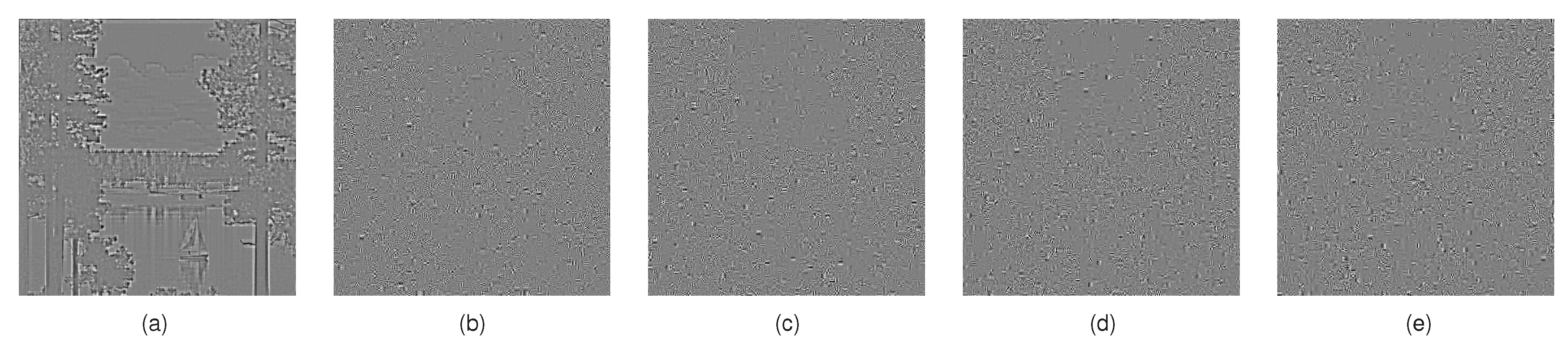
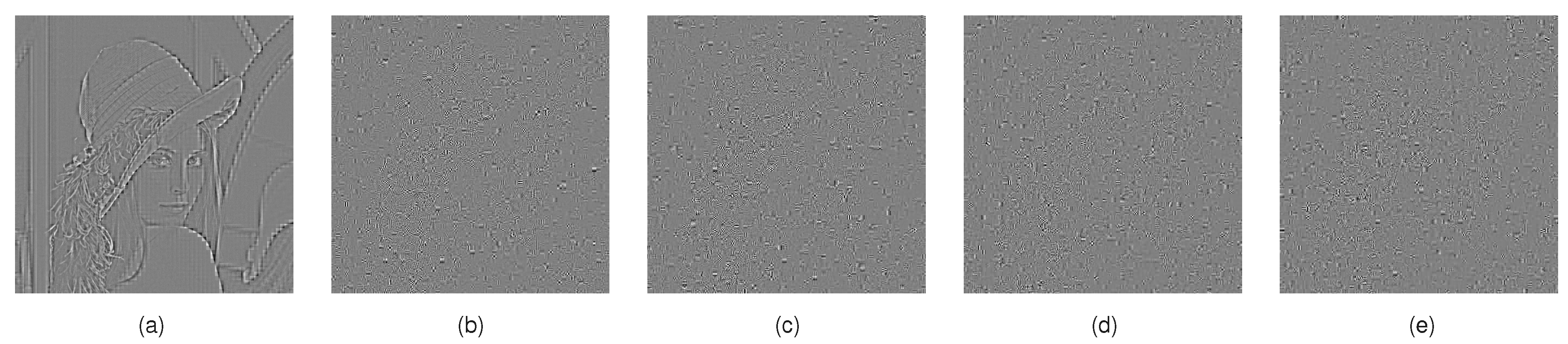
4.1. CPA Effectiveness Using Single-Permutation Method
4.2. CPA Effectiveness Using the Additive Value Method
4.3. Factors Affecting the Effectiveness of the Improved CPA Scheme
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Coppersmith, D. The Data Encryption Standard (DES) and its strength against attacks. IBM J. Res. Dev. 1994, 38, 243–250. [Google Scholar] [CrossRef]
- Wright, M.A. The advanced encryption standard. Netw. Secur. 2001, 2001, 11–13. [Google Scholar] [CrossRef]
- Li, P.; Lo, K. A content-adaptive joint image compression and encryption scheme. IEEE Trans. Multimed. 2018, 20, 1960–1972. [Google Scholar] [CrossRef]
- Li, P.; Lo, K.T. Joint image encryption and compression schemes based on 16 × 16 DCT. J. Vis. Commun. Image Represent. 2019, 58, 12–24. [Google Scholar] [CrossRef]
- Peng, Y.; Fu, C.; Cao, G.; Song, W.; Chen, J.; Sham, C.W. JPEG-compatible Joint Image Compression and Encryption Algorithm with File Size Preservation. ACM Trans. Multimed. Comput. Commun. Appl. 2024, 20, 1–20. [Google Scholar] [CrossRef]
- Cheng, H.; Xiaobo, L. On the application of image decomposition to image compression and encryption. In Proceedings of the IFIP TC6/TC11 International Conference on Communications and Multimedia Security II, Essen, Germany, 23–24 September 1996; pp. 116–127. [Google Scholar] [CrossRef]
- Massoudi, A.; Lefebvre, F.; De Vleeschouwer, C.; Macq, B.; Quisquater, J.J. Overview on selective encryption of image and video: Challenges and perspectives. EURASIP J. Inf. Secur. 2008, 2008, 179290. [Google Scholar] [CrossRef]
- Puech, W.; Rodrigues, J. Crypto-compression of medical images by selective encryption of DCT. In Proceedings of the 13th European Signal Processing Conference, Antalya, Turkey, 4–8 September 2005; pp. 1–4. [Google Scholar]
- Pinto, M.; Puech, W.; Subsol, G. Protection of JPEG compressed E-comics by selective encryption. In Proceedings of the 20th IEEE International Conference on Image Processing (ICIP 2013), Melbourne, VIC, Australia, 15–18 September 2013; pp. 4588–4592. [Google Scholar] [CrossRef]
- Lian, S. Efficient image or video encryption based on spatiotemporal chaos system. Chaos Solitons Fractals 2009, 40, 2509–2519. [Google Scholar] [CrossRef]
- Khan, N.A.; Altaf, M.; Khan, F.A. Selective encryption of JPEG images with chaotic based novel S-box. Multimed. Tools Appl. 2021, 80, 9639–9656. [Google Scholar] [CrossRef]
- Li, P.; Meng, J.; Sun, Z. A new JPEG encryption scheme using adaptive block size. In Advances in Intelligent Information Hiding and Multimedia Signal Processing: Proceeding of the 16th International Conference on IIHMSP in Conjunction with the 13th International Conference on FITAT, Ho Chi Minh City, Vietnam, 5–7 November 2020; Springer: Singapore, 2021; Volume 211, pp. 140–147. [Google Scholar] [CrossRef]
- Li, S.; Zhang, Y. Quantized DCT coefficient category address encryption for JPEG image. KSII Trans. Internet Inf. Syst. 2016, 10, 1790–1806. [Google Scholar]
- Auer, S.; Bliem, A.; Engel, D.; Uhl, A.; Unterweger, A. Bitstream-based JPEG encryption in real-time. Int. J. Digit. Crime Forensics 2013, 5, 1–14. [Google Scholar] [CrossRef]
- Puteaux, P.; Yriarte, F.; Puech, W. A secret JPEG image sharing method over GF(2M) galois fields. IEEE Trans. Circuits Syst. Video Technol. 2022, 33, 3030–3042. [Google Scholar] [CrossRef]
- Yuan, Y.; He, H.; Yang, Y.; Mao, N.; Chen, F.; Ali, M. JPEG image encryption with grouping coefficients based on entropy coding. J. Vis. Commun. Image Represent. 2023, 97, 103975. [Google Scholar] [CrossRef]
- Li, P.; Lo, K.T. Survey on JPEG compatible joint image compression and encryption algorithms. IET Signal Process. 2020, 14, 475–488. [Google Scholar] [CrossRef]
- Li, C. When an attacker meets a cipher-image in 2018: A year in review. J. Inf. Secur. Appl. 2019, 48, 102361. [Google Scholar] [CrossRef]
- He, J.; Huang, S.; Tang, S.; Huang, J. JPEG image encryption with improved format compatibility and file size preservation. IEEE Trans. Multimed. 2018, 20, 2645–2658. [Google Scholar] [CrossRef]
- Cardona-López, M.A.; Chimal-Eguía, J.C.; Silva-García, V.M.; Flores-Carapia, R. Statistical Analysis of the Negative–Positive Transformation in Image Encryption. Mathematics 2024, 12, 908. [Google Scholar] [CrossRef]
- Chen, J.; Chen, L.; Zhou, Y. Universal chosen-ciphertext attack for a family of image encryption schemes. IEEE Trans. Multimed. 2021, 23, 2372–2385. [Google Scholar] [CrossRef]
- He, H.; Yuan, Y.; Ye, Y.; Tai, H.M.; Chen, F. Chosen Plaintext Attack on JPEG Image Encryption with Adaptive Key and Run Consistency. J. Vis. Commun. Image Represent. 2023, 90, 103733. [Google Scholar] [CrossRef]
- Yuan, Y.; He, H.; Chen, F. On the security of encrypted JPEG image with adaptive key generated by invariant characteristic. In Digital Forensics and Watermarking: 20th International Workshop, IWDW 2021, Beijing, China, 20–22 November 2021; Springer: Cham, Switzerland, 2022; Volume 13180, pp. 58–71. [Google Scholar] [CrossRef]
- Benrhouma, O.; Hermassi, H.; El-Latif, A.A.A.; Belghith, S. Cryptanalysis of a video encryption method based on mixing and permutation operations in the DCT domain. Signal Image Video Process. 2015, 9, 1281–1286. [Google Scholar] [CrossRef]
- Lee, M.K.; Jang, E.S. Cryptanalysis of start code-based encryption method for HEVC. IEEE Access Pract. Innov. Open Solut. 2021, 9, 92568–92577. [Google Scholar] [CrossRef]
- Preishuber, M.; Hütter, T.; Katzenbeisser, S.; Uhl, A. Depreciating motivation and empirical security analysis of chaos-based image and video encryption. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2137–2150. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Feng, B.; Lü, J.; Hao, F. Cryptanalysis of a chaotic image encryption algorithm based on information entropy. IEEE Access Pract. Innov. Open Solut. 2018, 6, 75834–75842. [Google Scholar] [CrossRef]
- Feng, W.; He, Y. Cryptanalysis and improvement of the hyper-chaotic image encryption scheme based on DNA encoding and scrambling. IEEE Photonics J. 2018, 10, 1–15. [Google Scholar] [CrossRef]
- Xiang, T.; Guo, S.; Li, X. Perceptual visual security index based on edge and texture similarities. IEEE Trans. Inf. Forensics Secur. 2016, 11, 951–963. [Google Scholar] [CrossRef]
- Wu, Y.; Zhou, Y.; Saveriades, G.; Agaian, S.; Noonan, J.P.; Natarajan, P. Local shannon entropy measure with statistical tests for image randomness. Inf. Sci. 2013, 222, 323–342. [Google Scholar] [CrossRef]
- Chuman, T.; Kiya, H. Security evaluation for block scrambling-based image encryption including JPEG distortion against jigsaw puzzle solver attacks. IEICE Trans. 2018, 101-A, 2405–2408. [Google Scholar] [CrossRef]
- Özkaynak, F. Brief review on application of nonlinear dynamics in image encryption. Nonlinear Dyn. 2018, 92, 305–313. [Google Scholar] [CrossRef]
- Mitchell, J. Digital Compression and Coding of Continuous-Tone Still Images: Requirements and Guidelines; ITU-T Recommendation T.81; International Telecommunication Union: Geneva, Switzerland, 1992; Available online: https://www.itu.int/rec/T-REC-T.81-199209-I/en (accessed on 28 May 2025).












| QFs | Lake | Lena | Boat | Baboon |
|---|---|---|---|---|
| 95 | Inf | Inf | Inf | Inf |
| 90 | Inf | Inf | Inf | Inf |
| 85 | 14.76 | 17.99 | Inf | Inf |
| 80 | 15.12 | 18.24 | 16.46 | Inf |
| 75 | 15.63 | 18.97 | 17.03 | Inf |
| 70 | 15.96 | 19.15 | 17.18 | Inf |
| 65 | 16.09 | 19.16 | 17.19 | 36.13 |
| 60 | 16.32 | 19.42 | 17.59 | Inf |
| QFs | Lake− | Lake+ | Lena− | Lena+ | Boat− | Boat+ | Bab− | Bab+ |
|---|---|---|---|---|---|---|---|---|
| 95 | 4 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 90 | 20 | 0 | 48 | 0 | 2 | 0 | 0 | 0 |
| 85 | 152 | 0 | 287 | 0 | 45 | 0 | 0 | 0 |
| 80 | 384 | 4 | 867 | 2 | 207 | 0 | 6 | 0 |
| 75 | 597 | 34 | 1300 | 25 | 533 | 18 | 6 | 0 |
| 70 | 792 | 98 | 1697 | 162 | 856 | 93 | 20 | 0 |
| 65 | 949 | 189 | 2029 | 387 | 1140 | 187 | 40 | 0 |
| 60 | 1154 | 277 | 2223 | 602 | 1345 | 310 | 73 | 0 |
| QFs | Lake | Lena | Boat | Baboon |
|---|---|---|---|---|
| 95 | Inf | Inf | Inf | Inf |
| 90 | Inf | Inf | Inf | Inf |
| 85 | Inf | Inf | Inf | Inf |
| 80 | 19.02 | 20.92 | Inf | Inf |
| 75 | 15.72 | 19.06 | 17.09 | Inf |
| 70 | 15.93 | 19.15 | 17.16 | Inf |
| 65 | 16.11 | 19.25 | 17.34 | Inf |
| 60 | 16.36 | 19.43 | 17.56 | Inf |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, J.; Gu, K.; Huang, Y.; Li, Y.; Chen, X. An Improved Chosen Plaintext Attack on JPEG Encryption. J. Sens. Actuator Netw. 2025, 14, 72. https://doi.org/10.3390/jsan14040072
He J, Gu K, Huang Y, Li Y, Chen X. An Improved Chosen Plaintext Attack on JPEG Encryption. Journal of Sensor and Actuator Networks. 2025; 14(4):72. https://doi.org/10.3390/jsan14040072
Chicago/Turabian StyleHe, Junhui, Kaitian Gu, Yihan Huang, Yue Li, and Xiang Chen. 2025. "An Improved Chosen Plaintext Attack on JPEG Encryption" Journal of Sensor and Actuator Networks 14, no. 4: 72. https://doi.org/10.3390/jsan14040072
APA StyleHe, J., Gu, K., Huang, Y., Li, Y., & Chen, X. (2025). An Improved Chosen Plaintext Attack on JPEG Encryption. Journal of Sensor and Actuator Networks, 14(4), 72. https://doi.org/10.3390/jsan14040072







