Secure and Efficient WBAN Authentication Protocols for Intra-BAN Tier
Abstract
:1. Introduction
2. Related Works
2.1. Overview of The System Model
- The first tier is “Intra-BAN“ The communication in this tier is between sensor nodes and a controller node. Sensors monitor and collect the patient’s data, which are then transmitted via a public channel to the controller node/local server/mobile device.
- The second tier is “Inter-BAN“. The communication in this tier is between a controller node/mobile device and a remote medical server. The controller node gathers data from sensor nodes and then sends them to the medical server via a public channel. The medical server stores the data in the database for later analysis.
- The third tier is “Beyond-BAN“. The communication in this tier is between a medical server and a medical service provider (i.e., a doctor). The medical server can be over the cloud, and the doctor can access the server’s data.

2.2. Requirements of Authentication Schemes in WBAN
- Emergency and periodic authentication protocols: The emergency authentication occurs when a sensor detects an emergency in the patient’s body, and it needs to initiate the authentication request for sending the emergency report securely. Periodic authentication occurs when the controller node requests to collect the patient’s data from a sensor node at a specific time, and the controller initiates the periodic authentication request to the sensor node for transmitting the data securely.
- Replay attack: An attacker can obtain messages when transmissions occur via unsecured channels. However, the attacker is unable to perform a replay attack if the message contains a timestamp.
- Session key disclosure attack: If an attacker tries to obtain the session key, the attacker cannot obtain secret values using messages sent via a public channel. Thus, the session key cannot be calculated by the attacker.
- Impersonation attack: An attacker cannot produce an authentication message to impersonate the legitimate entity.
- Controller node/mobile device stolen attack: If an attacker obtains a legitimate patient’s mobile device, the attacker is unable to extract any information stored on it and is unable to generate a legitimate message.
- Off-line guessing attack: An attacker has the ability to guess either identity or a password, but not both at the same time.
- Perfect forward/backward secrecy: Future keys will not be attacked, and previous keys will not be misused (future/past key secrecy).
- Known session-specific temporary information attack: In case an attacker gets the secret values that are created randomly through the session, the session key cannot be calculated.
- Anonymity and unlinkability: This refers to an attacker being unable to obtain the identity of a legitimate entity through message eavesdropping and being unable to trace a legitimate entity using messages sent during previous sessions.
- Desynchronization attack: The solution should prevent the risk of a desynchronization attack that blocks communication between two parties and render them unable to proceed with authentication.
- Secure password change: This refers to an attacker being unable to arbitrarily change the password of a legitimate mobile device because the identity and password of the legitimate entity are unknown to the attacker.
- Performance: Authentication protocols must be cost-effective in terms of computation and communication.
2.3. Adversary Model
- The attacker has total control over all messages sent through unsecured channels. Thus, the attacker has the ability to eavesdrop, manipulate, insert, and remove messages [9].
- An attacker can steal a patient’s mobile device/controller and access the data stored on it [10].
- An attacker could guess either a patient’s identity (IDi) or password (PWi), but not both at the same time [2].
- An attacker can perform desynchronization, man-in-the-middle (MITM) attacks, impersonation attacks, replay attacks, and other possible attacks over public channels [11].
- An attacker is unable to compromise the trusted authority’s private key [12].
2.4. The Existing Authentication Schemes in WBAN
3. Problem Statement and Proposed Scheme
- How can we achieve secure and efficient WBAN authentication protocols for the intra-BAN tier?
3.1. Initialization Phase
- TA chooses an additive group G1 of prime order q and a generator P of the group G1.
- TA selects a secure hash function h:{0,1} → Zq.
- TA generates a secret random number STA ∈ Zq* as its private key and calculates its public key PKTA = STA * P where STA * P denotes the scalar multiplication operation of the point P in G1.
- TA publishes the system’s parameters (G1, PKTA, P, q, h) and keeps STA as a private key.
3.2. Registration Phase
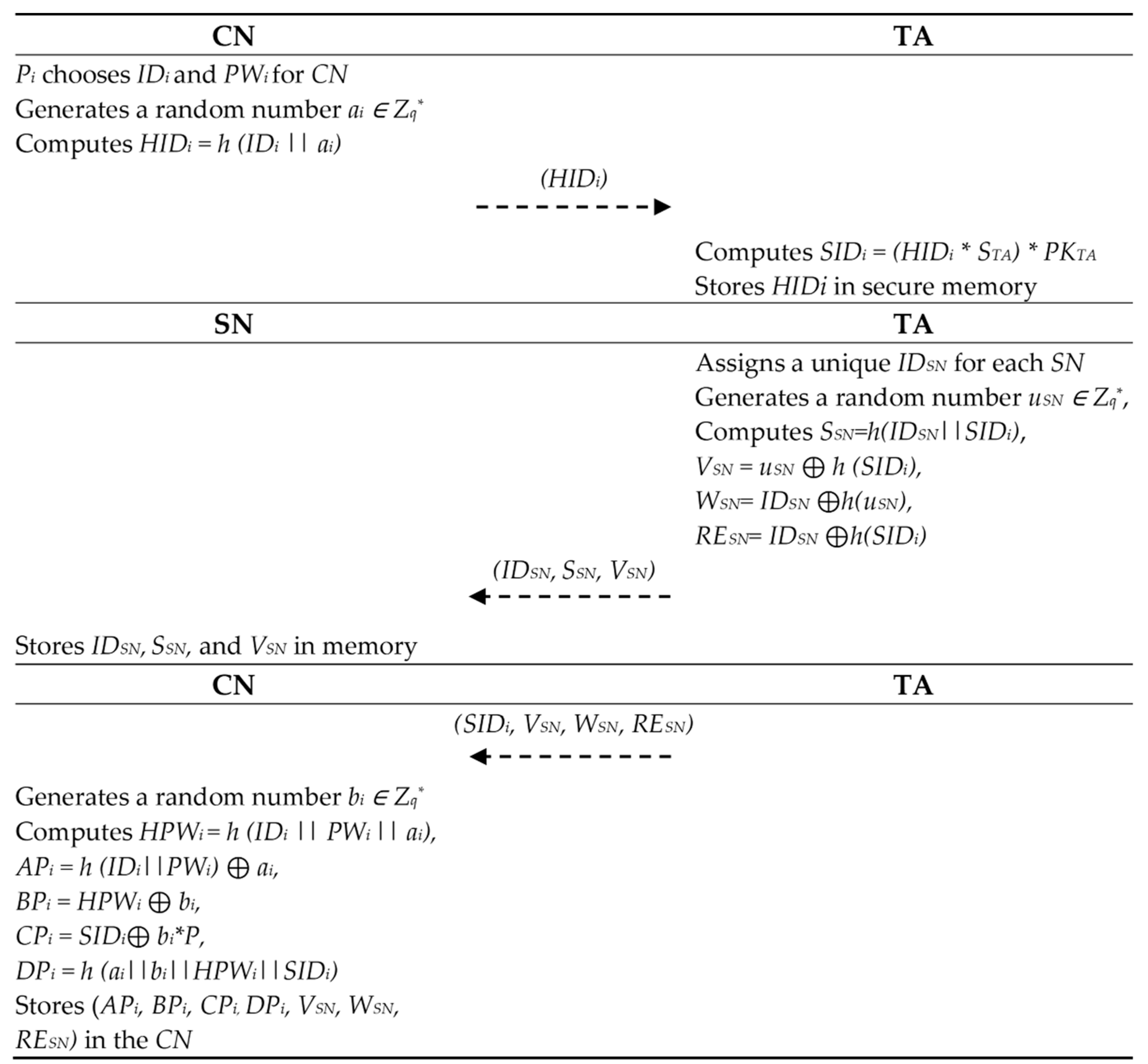
- Pi chooses IDi and PWi and then creates a number ai ∈ Zq*. Pi calculates HIDi = h (IDi || ai) and sends (HIDi) to TA securely. TA calculates SIDi = (HIDi * STA) * PKTA and then stores HIDi in secure memory.
- TA assigns a unique IDSN for each SN and then creates a number uSN ∈ Zq*. TA calculates SSN = h(IDSN || SIDi), VSN = uSN ⊕ h(SIDi), WSN = IDSN ⊕ h(uSN), and RESN = IDSN ⊕ h(SIDi). TA sends (IDSN, SSN, VSN) to the SN securely to store them in the SN’s memory.
- TA sends (SIDi, VSN, WSN, RESN) to the CN securely. The CN generates a random number bi ∈ Zq* and then calculates HPWi = h(IDi PWi || ai), APi = h(IDi || PWi) ⊕ ai, BPi = HPWi ⊕ bi, CPi = SIDi ⊕ bi * P, and DPi = h(ai || bi || HPWi || SIDi). The CN stores (APi, BPi, CPi, DPi, VSN, WSN, RESN) in its memory.
3.3. Authentication Protocol-I
- SN creates a secret number xSN ∈ Zq* and a current timestamp T1. The SN computes XSN = h(SSN) ⊕ xSN and LSN1 = h(IDSN || xSN || SSN || VSN || T1). Afterwards, the SN transmits the message (VSN, LSN1, XSN, T1) to the CN via an unsecured channel.
- When (VSN, LSN1, XSN, T1) is received, Pi enters IDi and PWi to the CN. Then, the CN computes ai = APi ⊕ h(IDi || PWi), HPWi = h(IDi || PWi || ai), bi = HPWi ⊕ BPi, and SIDi = CPi ⊕ bi * P. Next, the CN checks to see if DPi ≟ h(ai || bi || HPWi || SIDi). If so, Pi is logged into the CN successfully.
- The CN checks the validity of the timestamp, i.e., if |T1 − T1*| < ΔT, where T1* denotes the time of message receipt and ΔT denotes the longest possible transmission delay, then the CN retrieves WSN of VSN from its memory and then computes uSN = VSN ⊕ h(SIDi), IDSN = WSN ⊕ h(uSN), SSN = h(IDSN || SIDi), xSN = h(SSN) ⊕ XSN, and LSN1* = h(IDSN || xSN || SSN || VSN || T1). The CN checks whether LSN1* ≟ LSN1. If so, then the SN is authenticated. Next, the CN creates a secret random number uSN+ ∈ Zq* and the current timestamp T2. Afterwards, the CN computes VSN+ = uSN+ ⊕ h(SIDi), WSN+ = IDSN ⊕ h(uSN+), Ui = h(SSN) ⊕ uSN+, SK-I = h(IDSN || SSN || xSN || uSN+ || VSN), and C = VSN+ ⊕ uSN+. The CN replaces (VSN, WSN) with (VSN, WSN, VSN+, WSN+) and then computes Li1 = h(SSN || SK-I || IDSN || VSN+ || T2). The CN transmits the message (Ui, Li1, C, T2) to the SN through an unsecured channel.
- When the SN received (Ui, Li1, C, T2), the SN checks the validity of the timestamps. If |T2 − T2*| < ΔT, where T2* denotes the time of message receipt, then the SN computes uSN+ = Ui ⊕ h(SSN), SK-I = h(IDSN || SSN || xSN || uSN+ || VSN), and VSN+ = C ⊕ uSN+. The SN checks to see if Li1 ≟ h(SSN || SK-I || IDSN || VSN+ || T2). If so, it replaces (VSN) with (VSN+) in its memory, and the session key is established between the SN and CN.

3.4. Authentication Protocol-II
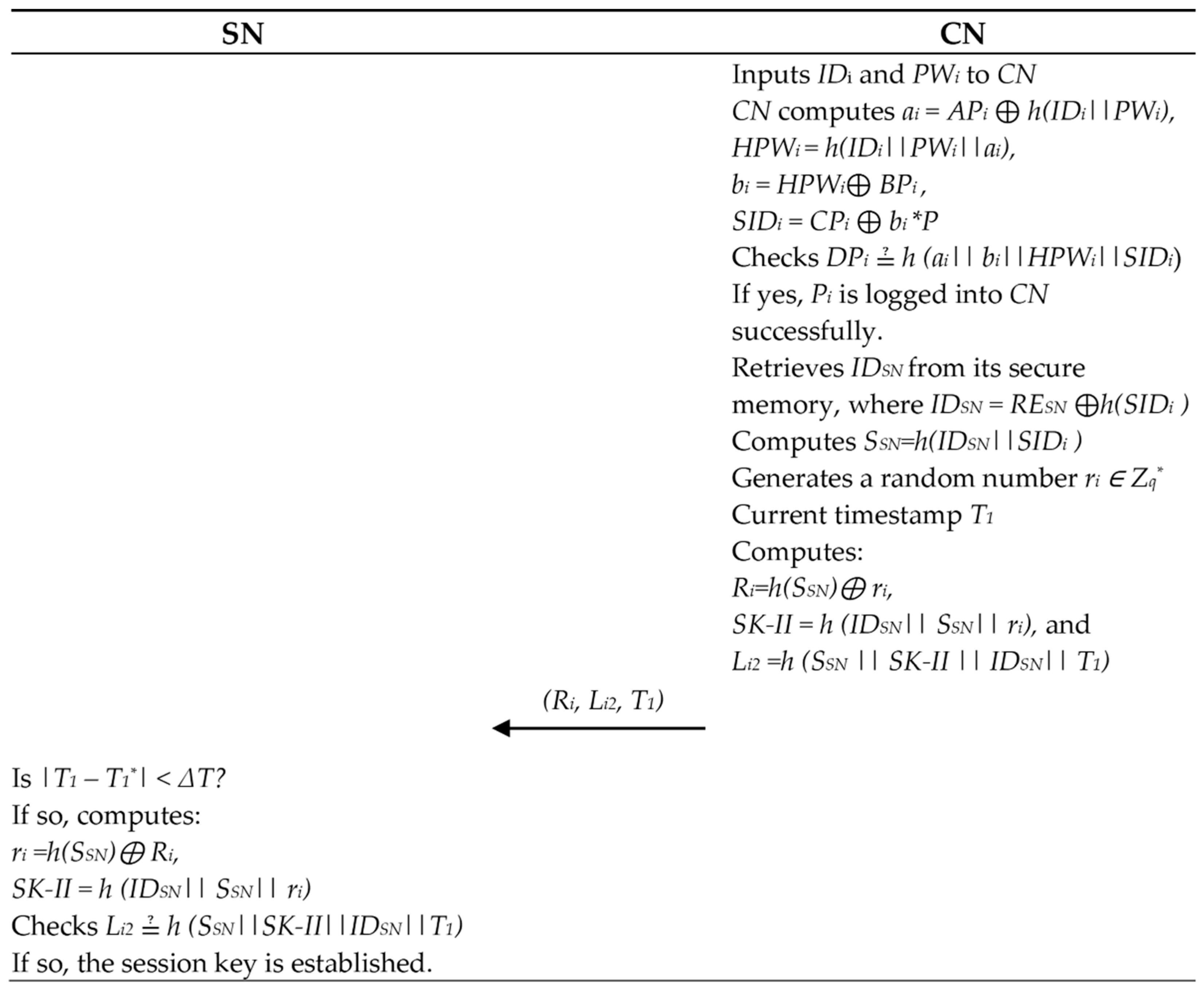
- Pi inputs IDi and PWi to the CN. Then, the CN computes ai = APi ⊕ h(IDi || PWi), HPWi = h(IDi || PWi || ai), bi = HPWi ⊕ BPi, and SIDi = CPi ⊕ bi * P. Next, the CN checks to see if DPi ≟ h(ai || bi || HPWi || SIDi). If so, Pi is logged into the CN successfully.
- The CN retrieves IDSN from its secure memory, where IDSN = RESN ⊕ h(SIDi), and computes SSN = h(IDSN || SIDi). The CN creates a secret number ri ∈ Zq* and current timestamp T1 and then computes Ri = h(SSN) ⊕ ri, SK-II = h(IDSN || SSN || ri), and Li2 = h(SSN || SK-II || IDSN || T1). Afterwards, the CN transmits the message (Ri, Li2, T1) to the SN via a public channel.
- When (Ri, Li2, T1) is received from the CN, the SN checks the validity of the timestamps. If |T1 − T1*| < ΔT, where T1* denotes the time of message receipt, then the SN computes ri = h(SSN) ⊕ Ri and SK-II = h(IDSN || SSN || ri). The SN checks to see if Li2 ≟ h(SSN || SK-II || IDSN || T1). If so, the session key is established between the CN and SN.
3.5. Password Change Protocol
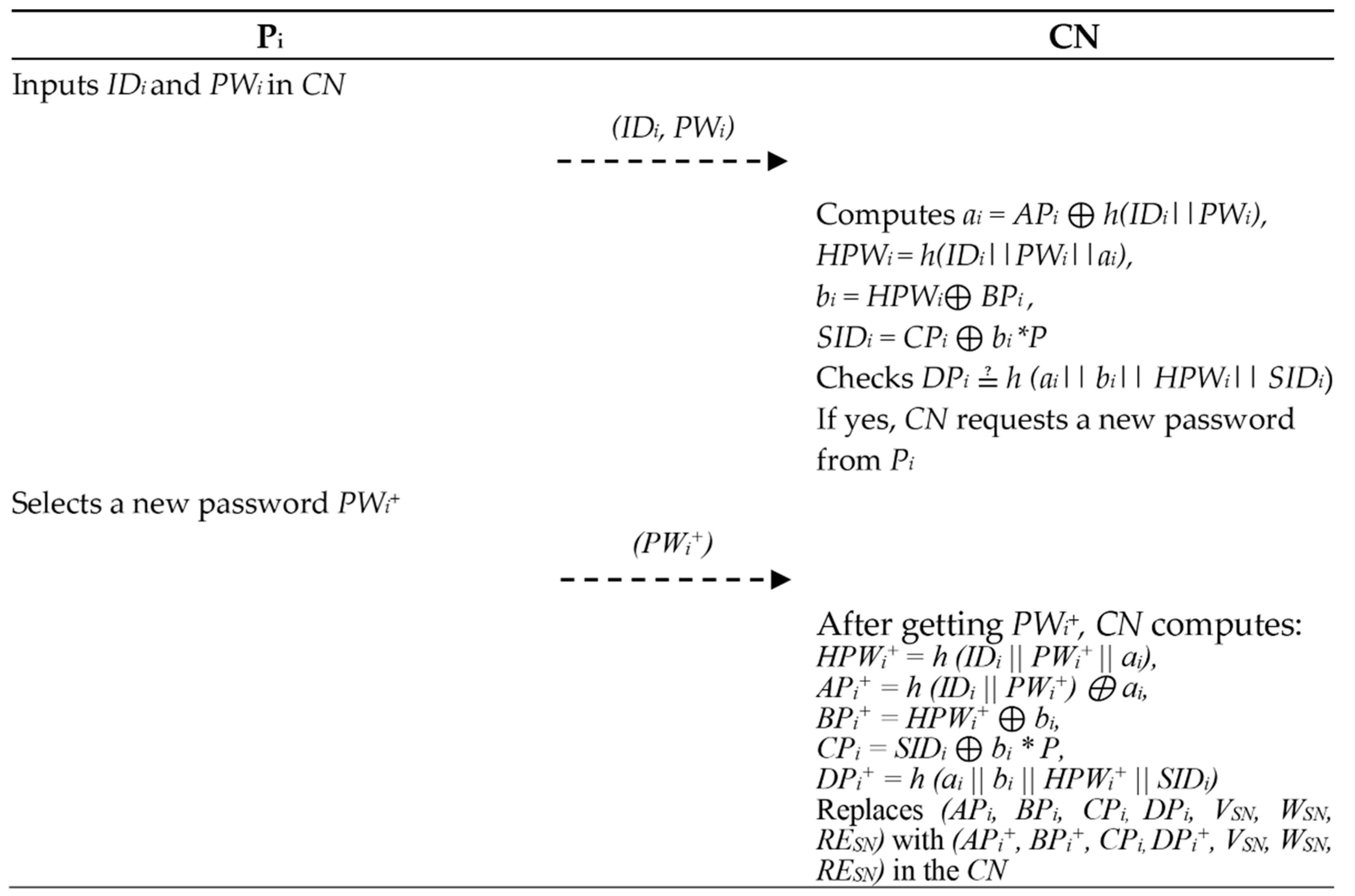
- Pi inputs IDi and PWi in the CN.
- The CN computes ai = APi ⊕ h(IDi || PWi), HPWi = h(IDi || PWi || ai), bi = HPWi ⊕ BPi, and SIDi = CPi ⊕ bi * P. Next, the CN checks to see if DPi ≟ h(ai || bi || HPWi || SIDi). If so, the CN asks Pi for a new password.
- Pi inputs a new password PWi+.
- The CN calculates HPWi+ = h(IDi || PWi+ || ai), APi+ = h(IDi || PWi+) ⊕ ai, BPi+ = HPWi+ ⊕ bi, CPi = SIDi ⊕ bi * P, and DPi+ = h(ai || bi || HPWi+ || SIDi). Finally, the CN replaces (APi, BPi, CPi, DPi, VSN, WSN, RESN) with (APi+, BPi+, CPi, DPi+, VSN, WSN, RESN) in the CN.
4. Security Analysis
4.1. Informal Security Analysis
4.1.1. Emergency and Periodic Authentication Protocols
- There are two proposed authentication protocols: the first protocol is for emergency reports, and the second protocol is for periodic reports. According to protocol-I, when a sensor detects an emergency in the patient’s body, the sensor node initiates the emergency authentication request by sending the message M1 = (VSN, LSN1, XSN, T1) to the CN. An attacker cannot generate a legal LSN1 because it is computed using the secret key SSN. Thus, the CN authenticates the SN by checking LSN1 ≟ h(IDSN || xSN || SSN || VSN || T1). Then, the CN responds to the authentication by sending the message M2 = (Ui, Li1, C, T2) to the SN. An attacker is unable to generate a valid Li1, so the SN authenticates the CN by checking Li1 ≟ h(SSN || SK-I || IDSN || VSN+ || T2). Therefore, the SN and CN can authenticate each other.
- The authentication protocol-Ⅱ occurs when the controller node requests to collect the patient’s data from a sensor node at a specific time. Thus, there is no need to initiate the authentication by the SN, reducing costs and enhancing performance. In this case, the CN requests authentication periodically from the SN, whose identity IDSN is stored in the CN. The CN initiates the authentication by sending the message M1 = (Ri, Li2, T1) to the SN. An attacker cannot generate a legal Li2 because it is computed using the secret key SSN. Thus, the SN authenticates the CN by checking Li2 ≟ h(SSN || SK-II || IDSN || T1). Therefore, the CN and SN can authenticate each other.
4.1.2. Replay and MITM Attacks
4.1.3. Session Key Disclosure Attack
4.1.4. Impersonation Attack
4.1.5. Mobile Device Stolen Attack
4.1.6. Off-Line Guessing Attack
4.1.7. Perfect Forward/Backward Secrecy
4.1.8. Known Session-Specific Temporary Information Attack
4.1.9. Node Anonymity and Untraceability
4.1.10. Desynchronization Attack
4.1.11. Secure Password Change
4.2. BAN Logic Proof
4.2.1. Basic Notation
- P, Q: two principals.
- X1, X2: two statements.
- SK: the session key.
- P|≡ X1: P believes X1, if X1 is true.
- P⊲ X1: P sees X1, i.e., P receives X1 contained within a message, but P does not necessarily believe X1.
- P|∼X1: P once says X1, i.e., P transmits a message including X1. It is unclear if P sent the message lately or a long time ago, but P believes X1 when P sent it.
- P|⇒ X1: P controls X1, and P should trust X1.
- #(X1): X1 is fresh, i.e., X1 has never been sent before.
- (X1) K: X1 is combined with K.
- P Q: P and Q have the same key K.
- : if P is true, then Q is also true.
4.2.2. Inference Rules
4.2.3. Protocol-I Goals
- G1: SN | ≡ (SN CN)
- G2: SN | ≡ CN | ≡ (SN CN)
- G3: CN | ≡ (SN CN)
- G4: CN | ≡ SN | ≡ (SN CN)
4.2.4. Protocol-I Assumptions
- A1: CN | ≡ #(T1)
- A2: SN | ≡ #(T2)
- A3: SN | ≡ CN ⇒ (SN CN)
- A4: CN | ≡ SN ⇒ (SN CN)
- A5: SN | ≡ SN CN
- A6: CN| ≡ SN CN
4.2.5. Protocol Idealized Forms
- Msg1:
- Msg2:
4.2.6. Protocol-I Formal Analysis
4.2.7. Protocol-II Goals
- G1: | ≡ (
- G2: | ≡ | ≡ (
- G3: | ≡ (
- G4: | ≡ | ≡ (
4.2.8. Protocol-II Assumptions
- A1: | ≡ #(T1)
- A2: | ≡ ⇒ ( )
- A3: | ≡ ⇒ ( )
- A4: | ≡
- A5: | ≡ | ≡ ()
4.2.9. Protocol-II Idealized Forms
- Msg1:
- Msg2:
4.2.10. Protocol-II Formal Analysis
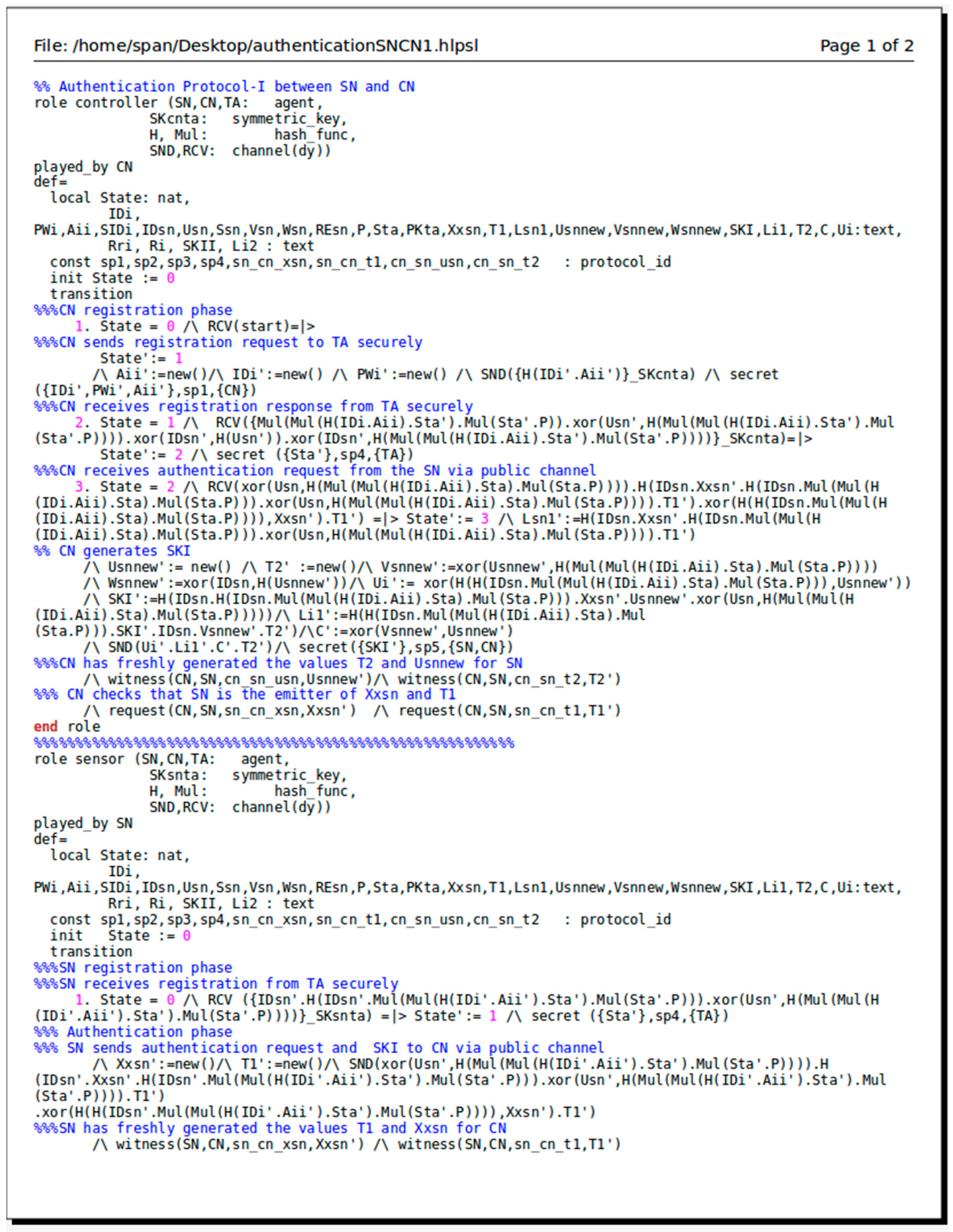
4.3. AVISPA Simulation Tool
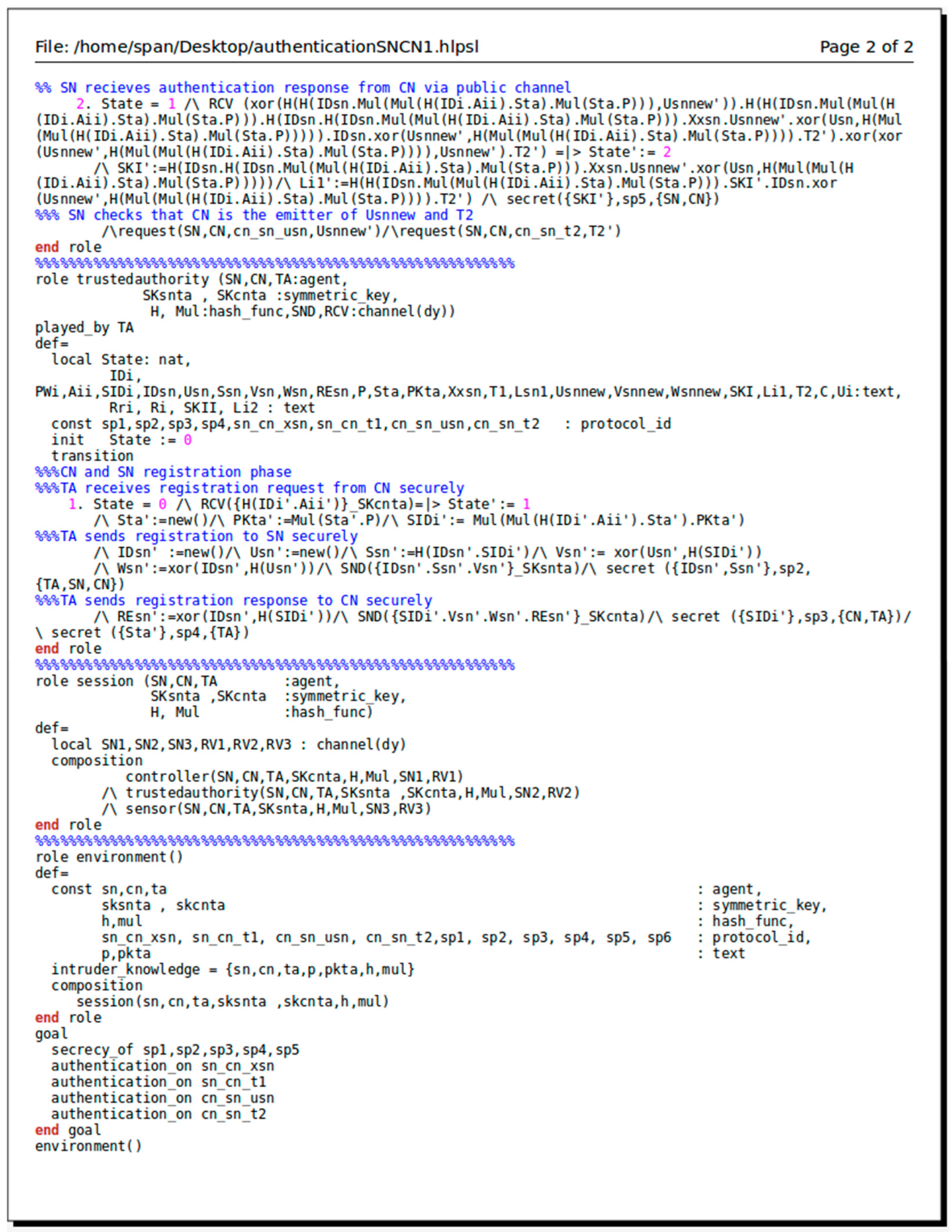
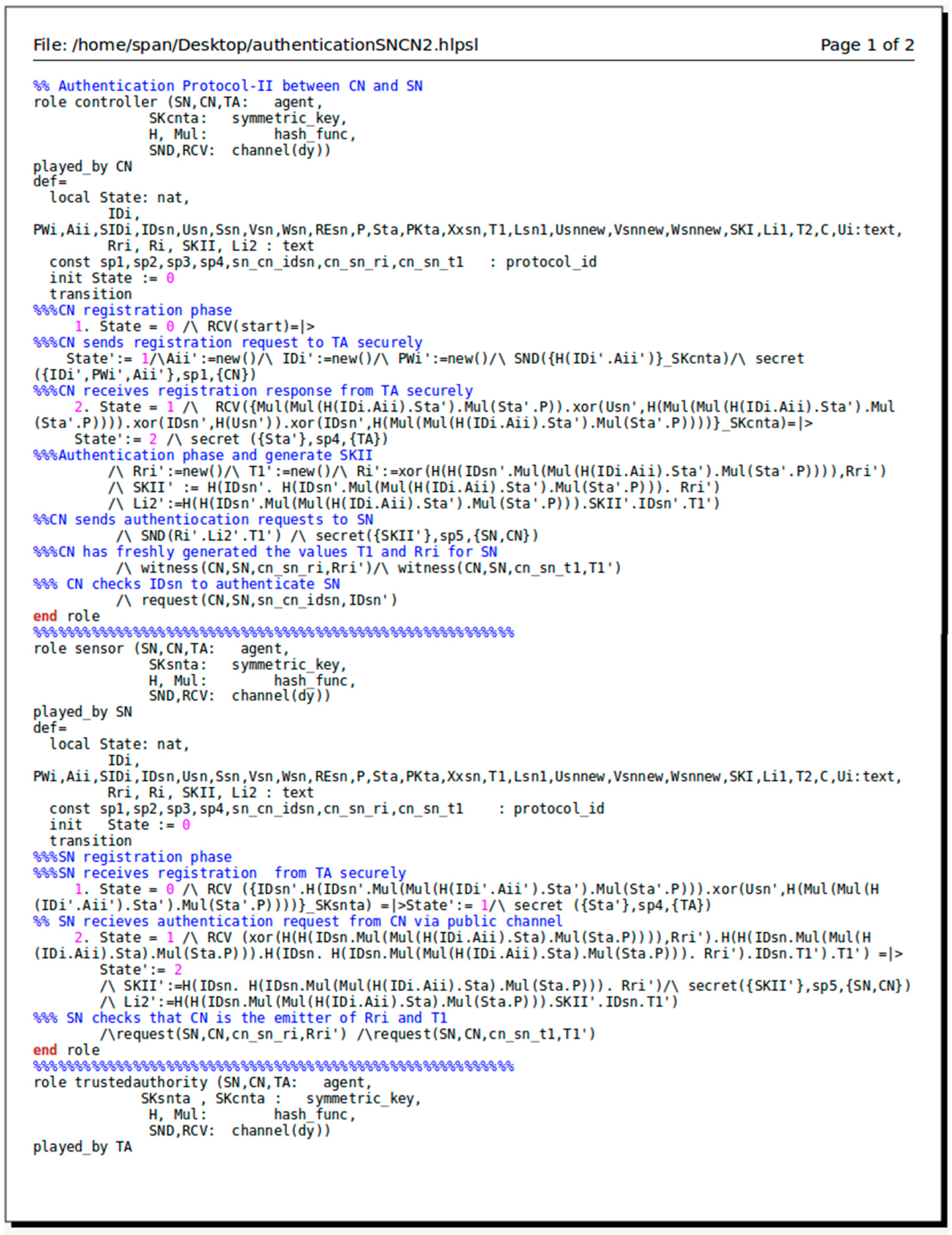

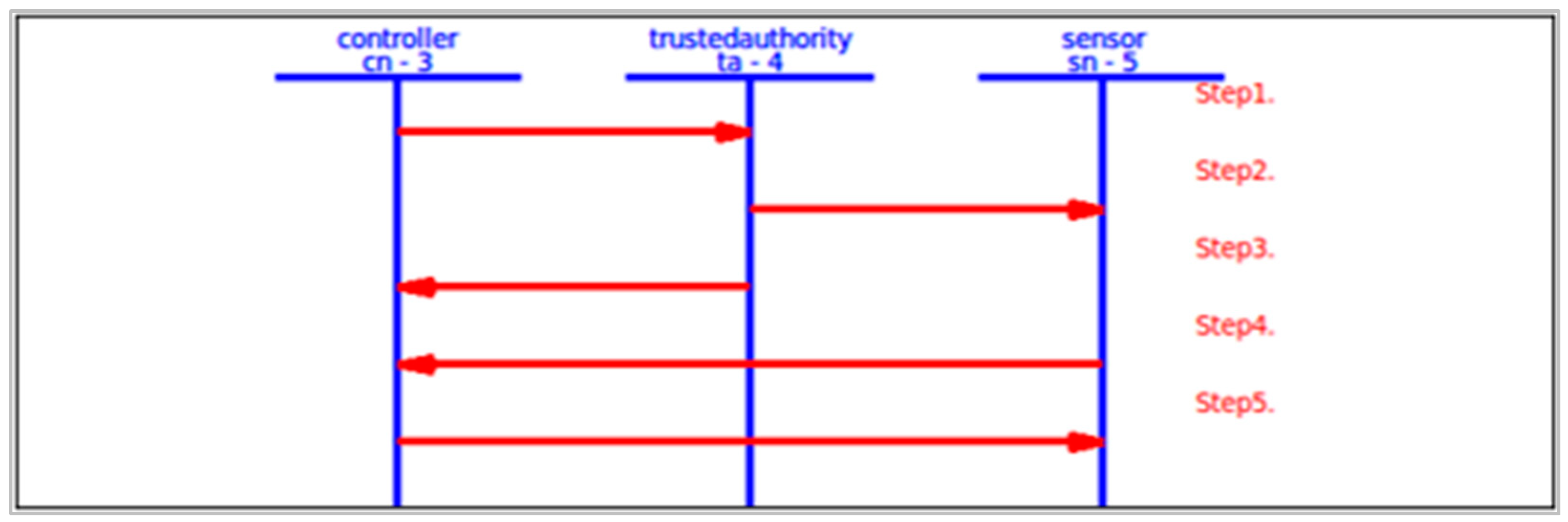
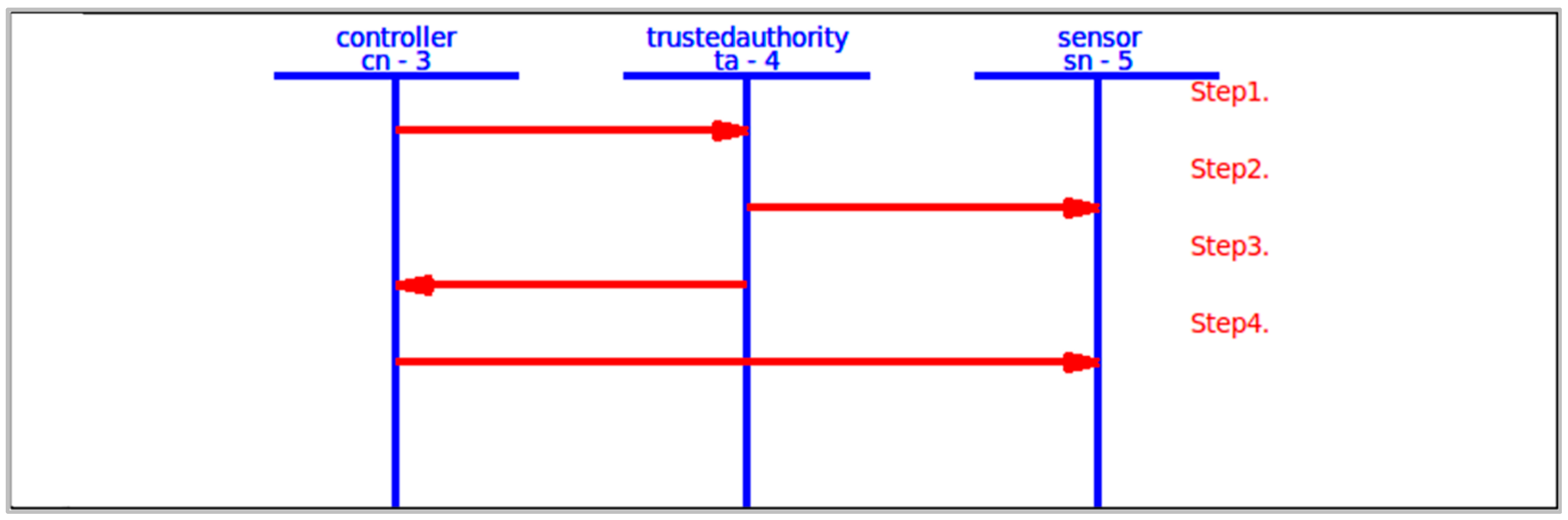


5. Performance Analysis
5.1. Computation Costs
5.2. Communication Costs
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Hsu, C.L.; Le, T.V.; Hsieh, M.C.; Tsai, K.Y.; Lu, C.F.; Lin, T.W. Three-Factor UCSSO Scheme with Fast Authentication and Privacy Protection for Telecare Medicine Information Systems. IEEE Access 2020, 8, 196553–196566. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Kim, M.; Yu, S.; Das, A.K.; Park, Y. Design of Secure Authentication Protocol for Cloud-Assisted Telecare Medical Information System Using Blockchain. IEEE Access 2020, 8, 192177–192191. [Google Scholar] [CrossRef]
- Ryu, J.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y.; Park, Y. Secure ECC-Based Three-Factor Mutual Authentication Protocol for Telecare Medical Information System. IEEE Access 2022, 10, 11511–11526. [Google Scholar] [CrossRef]
- Poongodi, T.; Rathee, A.; Indrakumari, R.; Suresh, P. IoT Sensing Capabilities: Sensor Deployment and Node Discovery, Wearable Sensors, Wireless Body Area Network (WBAN), Data Acquisition. Intell. Syst. Ref. Libr. 2020, 174, 127–151. [Google Scholar] [CrossRef]
- Taleb, H.; Nasser, A.; Andrieux, G.; Charara, N.; Motta Cruz, E. Wireless Technologies, Medical Applications and Future Challenges in WBAN: A Survey. Wirel. Netw. 2021, 27, 5271–5295. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. Smart Mutual Authentication Protocol for Cloud Based Medical Healthcare Systems Using Internet of Medical Things. IEEE J. Sel. Areas Commun. 2021, 39, 346–360. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Vasilakos, A.V. Authenticated Key Management Protocol for Cloud-Assisted Body Area Sensor Networks. J. Netw. Comput. Appl. 2018, 123, 112–126. [Google Scholar] [CrossRef]
- Alzahrani, B.A.; Irshad, A.; Albeshri, A.; Alsubhi, K.; Shafiq, M. An Improved Lightweight Authentication Protocol for Wireless Body Area Networks. IEEE Access 2020, 8, 190855–190872. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, Q.; Li, Z.; Lu, X.; Gan, Y. A Lightweight and Secure Anonymous User Authentication Protocol for Wireless Body Area Networks. Secur. Commun. Netw. 2021, 2021, 4939589. [Google Scholar] [CrossRef]
- Yu, S.J.; Lee, J.Y.; Park, Y.H.; Park, Y.H.; Lee, S.W.; Chung, B.H. A Secure and Efficient Three-Factor Authentication Protocol in Global Mobility Networks. Appl. Sci. 2020, 10, 3565. [Google Scholar] [CrossRef]
- Yang, X.; Yi, X.; Nepal, S.; Khalil, I.; Huang, X.; Shen, J. Efficient and Anonymous Authentication for Healthcare Service with Cloud Based WBANs. IEEE Trans. Serv. Comput. 2021, 1. [Google Scholar] [CrossRef]
- Ali, Z.; Ghani, A.; Khan, I.; Ashraf, S.; Hafizul, S.K. A Robust Authentication and Access Control Protocol for Securing Wireless Healthcare Sensor Networks. J. Inf. Secur. Appl. 2020, 52, 102502. [Google Scholar] [CrossRef]
- Shen, J.; Chang, S.; Shen, J.; Liu, Q.; Sun, X. A Lightweight Multi-Layer Authentication Protocol for Wireless Body Area Networks. Futur. Gener. Comput. Syst. 2018, 78, 956–963. [Google Scholar] [CrossRef]
- Liu, X.; Jin, C.; Li, F. An Improved Two-Layer Authentication Scheme for Wireless Body Area Networks. J. Med. Syst. 2018, 42, 1–14. [Google Scholar] [CrossRef]
- Ding, Y.; Xu, H.; Zhao, M.; Liang, H.; Wang, Y. Group Authentication and Key Distribution for Sensors in Wireless Body Area Network. Int. J. Distrib. Sens. Netw. 2021, 17, 15501477211044338. [Google Scholar] [CrossRef]
- Ur Rehman, Z.; Altaf, S.; Iqbal, S. An Efficient Lightweight Key Agreement and Authentication Scheme for WBAN. IEEE Access 2020, 8, 175385–175397. [Google Scholar] [CrossRef]
- Chen, C.M.; Xiang, B.; Wu, T.Y.; Wang, K.H. An Anonymous Mutual Authenticated Key Agreement Scheme for Wearable Sensors in Wireless Body Area Networks. Appl. Sci. 2018, 8, 1074. [Google Scholar] [CrossRef] [Green Version]
- Wan, T.; Wang, L.; Liao, W.; Yue, S. A Lightweight Continuous Authentication Scheme for Medical Wireless Body Area Networks. Peer-to-Peer Netw. Appl. 2021, 14, 3473–3487. [Google Scholar] [CrossRef]
- Rehman, Z.U.; Altaf, S.; Ahmad, S.; Huda, S.; Al-Shayea, A.M.; Iqbal, S. An Efficient, Hybrid Authentication Using Ecg and Lightweight Cryptographic Scheme for Wban. IEEE Access 2021, 9, 133809–133819. [Google Scholar] [CrossRef]
- Li, X.; Ibrahim, M.H.; Kumari, S.; Kumar, R. Secure and Efficient Anonymous Authentication Scheme for Three-Tier Mobile Healthcare Systems with Wearable Sensors. Telecommun. Syst. 2018, 67, 323–348. [Google Scholar] [CrossRef]
- Abiramy, N.V.; Sudha, S.V. A secure and lightweight authentication protocol for multiple layers in wireless body area network. Smart Intell. Comput. Appl. 2019, 104, 287–296. [Google Scholar] [CrossRef]
- Koya, A.M.; Deepthi, P.P. Deepthi. Anonymous Hybrid Mutual Authentication and Key Agreement Scheme for Wireless Body Area Network. Comput. Netw. 2018, 140, 138–151. [Google Scholar] [CrossRef]
- Arfaoui, A.; ben Letaifa, A.; Kribeche, A.; Senouci, S.M.; Hamdi, M. Adaptive Anonymous Authentication for Wearable Sensors in Wireless Body Area Networks. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 606–611. [Google Scholar] [CrossRef]
- Morales-Sandoval, M.; De-La-Parra-Aguirre, R.; Galeana-Zapien, H.; Galaviz-Mosqueda, A. A Three-Tier Approach for Lightweight Data Security of Body Area Networks in E-Health Applications. IEEE Access 2021, 9, 146350–146365. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Karuppiah, M.; Nayyar, A. An Efficient Anonymous Authentication and Confidentiality Preservation Schemes for Secure Communications in Wireless Body Area Networks. Wirel. Netw. 2021, 27, 2119–2130. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Alqudaihi, K.S. A Lightweight and Secure Anonymity Preserving Protocol for WBAN. IEEE Access 2020, 8, 178183–178194. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Nikooghadam, M.; Abbasinezhad-Mood, D. Design of a Lightweight and Anonymous Authenticated Key Agreement Protocol for Wireless Body Area Networks. Int. J. Commun. Syst. 2019, 32, e3974. [Google Scholar] [CrossRef]
- Shuai, M.; Xiong, L.; Wang, C.; Yu, N. Lightweight and Privacy-Preserving Authentication Scheme with the Resilience of Desynchronisation Attacks for WBANs. IET Inf. Secur. 2020, 14, 380–390. [Google Scholar] [CrossRef]
- Xu, Z.; Xu, C.; Liang, W.; Xu, J.; Chen, H. And Key Agreement Scheme for Medical Internet of Things. IEEE Access 2019, 7, 53922–53931. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Alqudaihi, K.S. Authentication in Wireless Body Area Network: Taxonomy and Open Challenges. J. Internet Things 2021, 3, 159–182. [Google Scholar] [CrossRef]
- Kilinc, H.H.; Yanik, T. A Survey of SIP Authentication and Key Agreement Schemes. IEEE Commun. Surv. Tutor. 2014, 16, 1005–1023. [Google Scholar] [CrossRef]
- Kim, M.; Yu, S.; Lee, J.; Park, Y.; Park, Y. Design of Secure Protocol for Cloud-Assisted Electronic Health Record System Using Blockchain. Sensors 2020, 20, 2913. [Google Scholar] [CrossRef] [PubMed]
| Notation | Description |
|---|---|
| Pi | i-th patient |
| CN | Controller node of Pi |
| SN | Sensor node-i of Pi |
| TA | Trusted authority |
| IDi, PWi | Identity and password of Pi |
| IDSN | Identity of SN |
| HIDi | Masked identity of Pi |
| SIDi | Secret identity of Pi |
| SSN | Secret key of SN |
| STA, PKTA | Secret key and public key of TA |
| ai, bi, uSN+, ri | CN-generated random numbers |
| xSN | SN-generated random number |
| uSN | TA-generated random number |
| VSN, WSN, VSN+, WSN+ | Data to check message synchronization |
| RESN | Data used in protocol-II for IDSN retrieval and SN authentication |
| HPWi, APi, BPi, CPi, DPi | Data used by CN to authenticate Pi |
| Tn | Timestamp n |
| Tn* | The time of message receipt |
| ΔT | The maximum transmission delay |
| XSN | Data used to retrieve xSN in protocol-I |
| LSN1 | Data used by CN to authenticate SN in protocol-I |
| Ui | Data used to retrieve uSN+ in protocol-I |
| C | Data used to retrieve VSN+ in protocol-I |
| Li1 | Data used by SN to authenticate CN in protocol-I |
| Ri | Data used to retrieve ri in protocol-II |
| Li2 | Data used by SN to authenticate CN in protocol-II |
| SK-I | Session key for protocol-I |
| SK-II | Session key for protocol-II |
| q | Large prime number |
| G1 | An additive group of order q |
| P | A generator of the group G1 |
| h | Hash function |
| Zq* | The nonzero positive integers’ modulus q |
| || | Concatenation operation |
| * | Scalar multiplication operation |
| ⊕ | XOR operation |
 | Secure communication channel |
 | Public communication channel |
| Feature | [13] | [14] | [16] | [17] | [18] | [19] | [20] | Proposed |
|---|---|---|---|---|---|---|---|---|
| Emergency and periodic authentication protocols | × | × | × | × | × | × | × | ✓ |
| Replay and MITM attacks | N/A | N/A | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Session key disclosure attack | ✓ | ✓ | N/A | N/A | ✓ | N/A | ✓ | ✓ |
| Impersonation attack | N/A | N/A | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Mobile device stolen attack | × | × | × | × | × | × | × | ✓ |
| Off-line guessing attack | N/A | N/A | N/A | ✓ | N/A | N/A | N/A | ✓ |
| Perfect forward/backward secrecy | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Known session-specific temporary information | N/A | N/A | N/A | N/A | ✓ | N/A | ✓ | ✓ |
| Node anonymity and unlinkability | × | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Desynchronization attacks | × | × | ✓ | ✓ | × | ✓ | ✓ | ✓ |
| Secure password change | × | × | × | × | × | × | × | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almuhaideb, A.M.; Alghamdi, H.A. Secure and Efficient WBAN Authentication Protocols for Intra-BAN Tier. J. Sens. Actuator Netw. 2022, 11, 44. https://doi.org/10.3390/jsan11030044
Almuhaideb AM, Alghamdi HA. Secure and Efficient WBAN Authentication Protocols for Intra-BAN Tier. Journal of Sensor and Actuator Networks. 2022; 11(3):44. https://doi.org/10.3390/jsan11030044
Chicago/Turabian StyleAlmuhaideb, Abdullah M., and Huda A. Alghamdi. 2022. "Secure and Efficient WBAN Authentication Protocols for Intra-BAN Tier" Journal of Sensor and Actuator Networks 11, no. 3: 44. https://doi.org/10.3390/jsan11030044
APA StyleAlmuhaideb, A. M., & Alghamdi, H. A. (2022). Secure and Efficient WBAN Authentication Protocols for Intra-BAN Tier. Journal of Sensor and Actuator Networks, 11(3), 44. https://doi.org/10.3390/jsan11030044







