Safety, Security and Privacy in Machine Learning Based Internet of Things
Abstract
1. Introduction
- A detailed discussion on the attack surfaces, vulnerabilities, and security threats of IoT Systems: we discuss various attack surfaces on IoT devices, i.e., network, physical service, cloud service, application interfaces and web service.
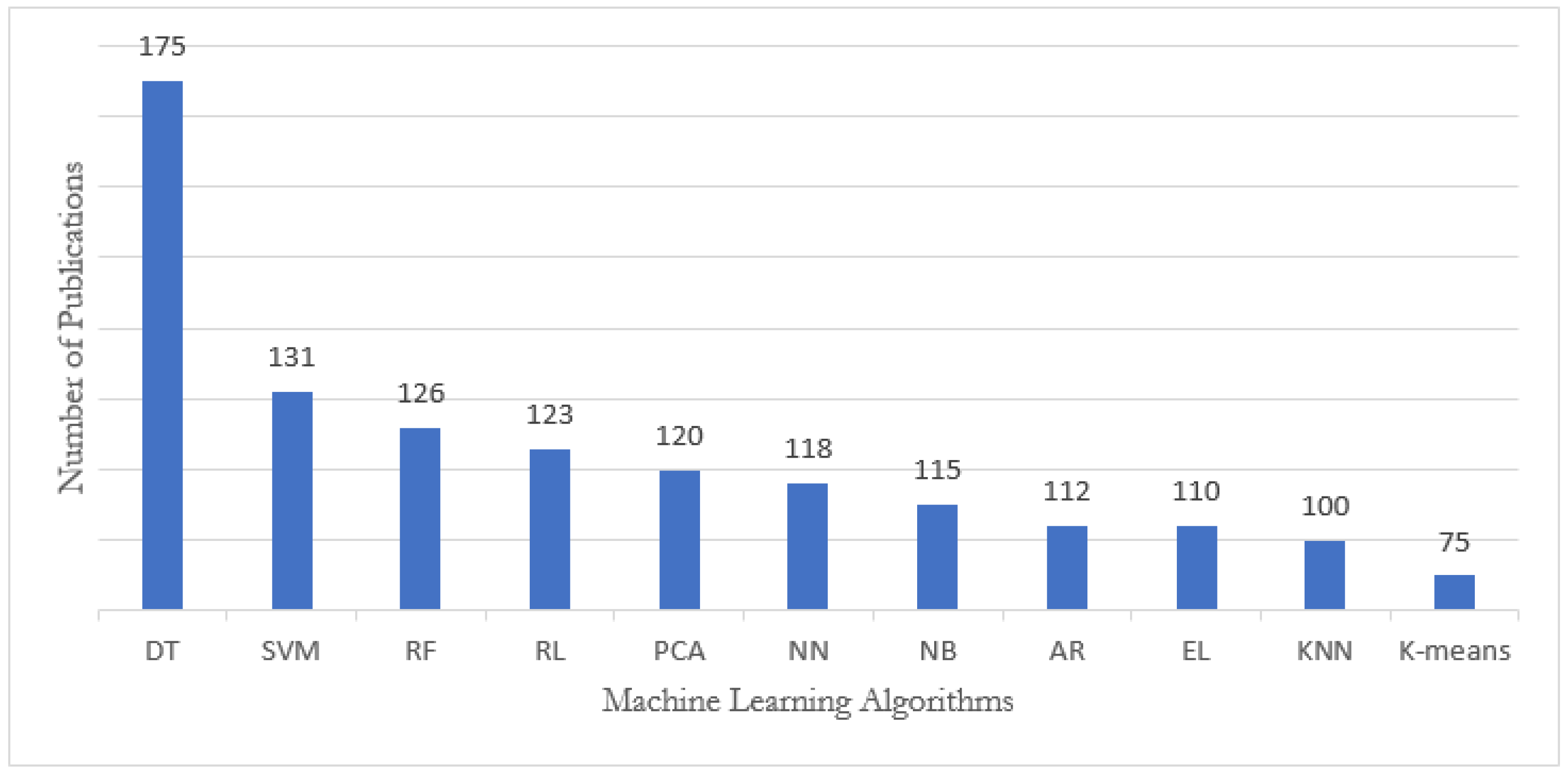
- Detailed discussion and comparison of existing surveys, including an in-depth statistical overview of recently published articles on different ML techniques for IoT security.
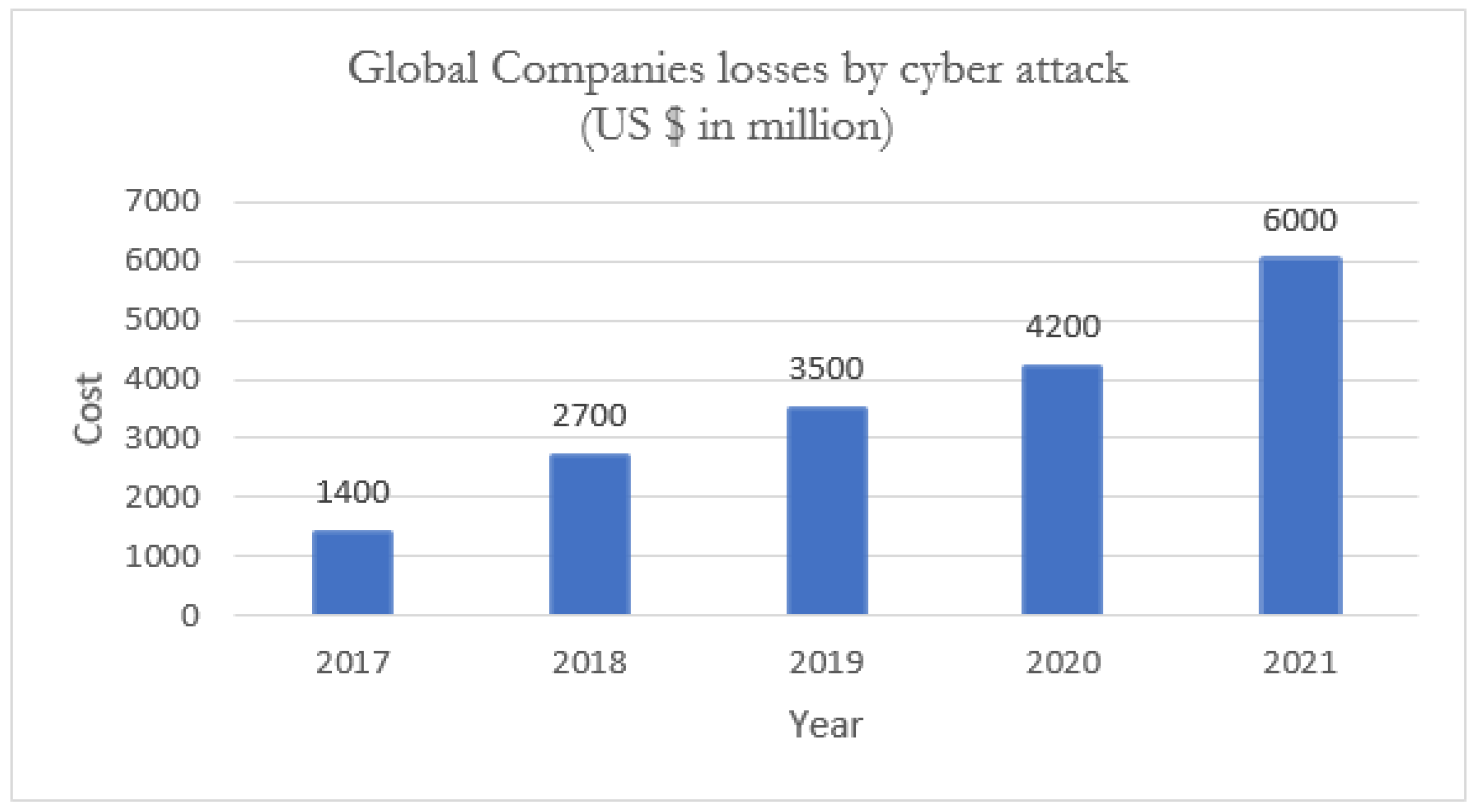
- Incorporation of recent surveys on financial losses by breaches in the security of IoT systems, including the trend in the number of IoT devices in future.
- Presentation of the latest research challenges and future directions for IoT security based on ML.
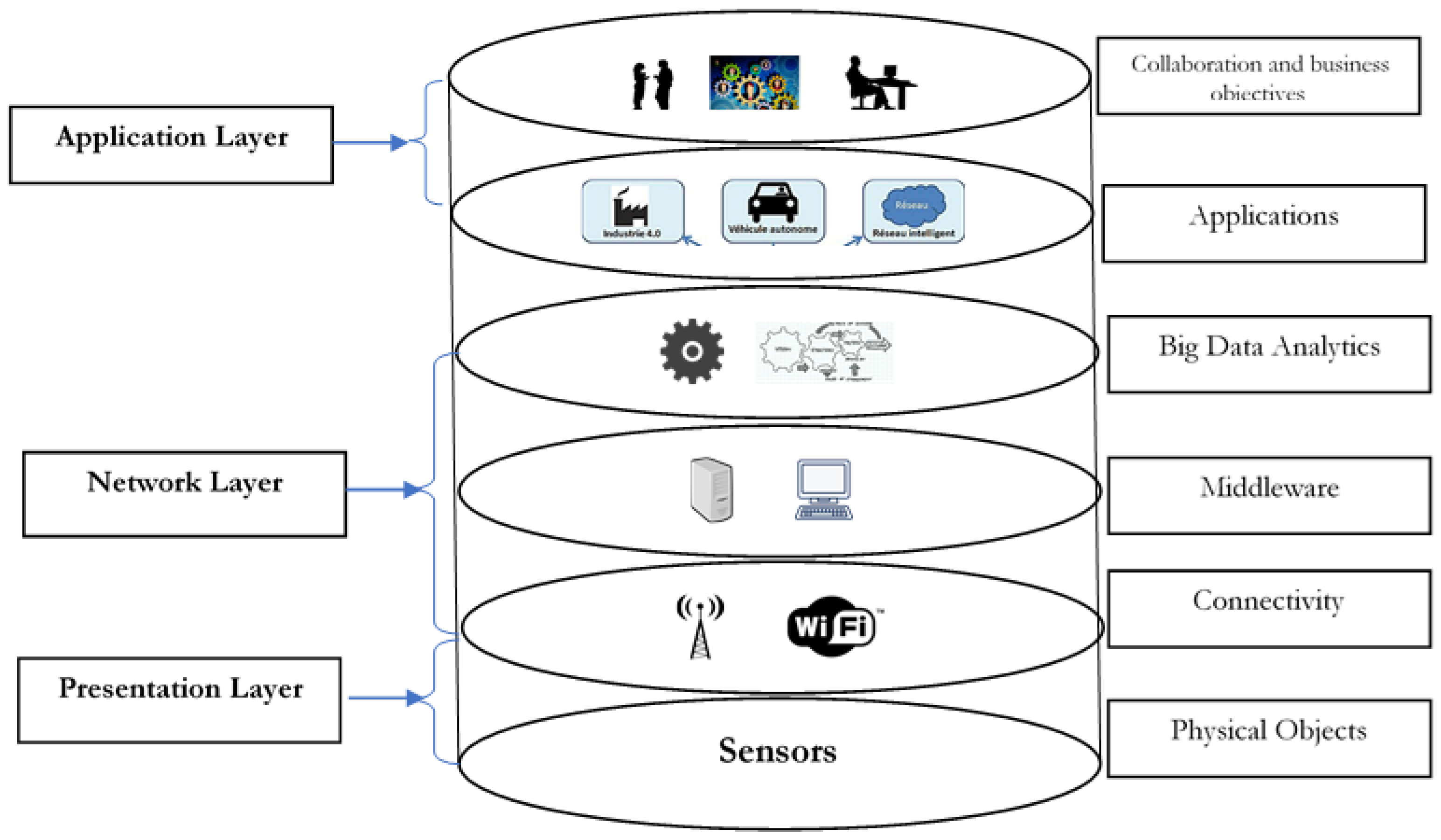
2. An Overview of IoT System
- The presentation or physical layer consists of all the physical objects that are responsible for sensing and collecting information from its surrounding environment. The sensors in this layer identify smart objects in the environment.
- The network layer consists of connectivity devices and is responsible for connecting and communicating with smart objects, servers, and network devices. Features of this layer are used for communicating and processing the sensor data.
- The application layer describes the various collaboration, deployments, and applications of IoTs such as smart objects for homes, transport, cities, agriculture and farming, etc. This layer classifies the application’s services to a user.
3. Safety and Security Threats in IoT
3.1. IoT Attack Surface(s)
3.1.1. Attack Surface at Physical Devices
3.1.2. Attack Surface at Network Service
3.1.3. Attack Surface at Cloud Service
3.1.4. Attack Surface at Web and Application Surface
4. Machine Learning for IoT Security
4.1. Machine Learning (ML) Techniques
4.1.1. Supervised Machine Learning
4.1.2. Unsupervised Learning
4.1.3. Re-Inforcement Learning
4.2. Application of Basic Machine Learning (ML) Techniques
4.3. Supervised Machine Learning
4.3.1. Decision Trees (DTs)
4.3.2. Support Vector Machine
4.3.3. Bayesian Algorithms
4.3.4. K-Nearest Neighbor (KNN)
4.3.5. Random Forest (RF)
4.3.6. Association Rule Algorithms
4.3.7. Ensemble Learning (EL)
4.4. Unsupervised ML
4.4.1. K-Means Clustering (KMC)
4.4.2. Principal Component Analysis
4.5. Emerging Techniques for IoT Safety and Security
4.5.1. Federated Learning (FL)
4.5.2. Generative Adversarial Network (GAN)
5. Research Challenges, and Future Directions
- Data Security and integrity:In machine learning techniques, reliable data for datasets and training data are very important to develop an accurate machine learning technique. A training dataset with low-quality data may interrupt the implementation of a particular learning technique. Thus, authenticated training datasets are crucial in ML techniques to secure the IoT network [74]. Furthermore, it is very easy for any hacker to learn the attack type and device vulnerabilities, and be able to manipulate the dataset used in the ML technique. Hence, it is a significant challenge to ascertain how the date can be secured and to detect different types of attacks and their probability of occurrence in any IoT environment. In other words, data security and integrity is challenging the future research field of IoT security.
- Backup Security Mechanisms:Usually, it is difficult to accurately state and estimate the network attack in an IoT environment in case of a “bad” defense policy in the learning process. Sometimes, this can cause disaster and drastic loss for IoT networks. Backup security mechanisms may also solve this difficulty protecting IoT systems from the exploration of the learning process. More mechanisms need to address this issue by incorporating ML-based security schemes to provide reliable, resilient and secure IoT services by reducing the risks of selecting bad policies.
- Privacy Problems:Privacy is a common issue in IoT environments. In IoT environments, Smart devices, such as sensors and wearable devices, are used to exchange data and information, and the users are not fully aware of where and how their personal information is shared via these devices. IoT smart devices carry the private and personal information of the clients and users, which may be misused. Every IoT device has security protocols to communicate with other devices, i.e., encryption and authentication. Privacy disclosures, leakage, and threats are crucial challenges that make users hesitate to adopt these technologies [75].
- Computational Cost:Many ML-based techniques require a substantial amount of training datasets and a complicated process for feature extraction, creating high computational costs and increasing the complexity of the system. Therefore, it is challenging to find new ML techniques with low communication and computational costs [76].
- Infrastructure Issues:A weak infrastructure always makes it easier for attackers to hack through the software. This is also known as a zero-day attack and is very difficult to determine using traditional security suits and schemes. It is, therefore, essential to build a strong and smart infrastructure to develop a secure IoT system [77]. Safety and Security features must be considered and need to be included in every phase of the IoT system.
6. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- An, P.; Singh, Y.; Selwal, A.; Singh, P.K.; Felseghi, R.A.; Raboaca, M.S. IoVT: Internet of vulnerable things? Threat architecture, attack surfaces, and vulnerabilities in Internet of Things And Its Applications Towards Smart Grids. Energies 2020, 13, 4813. [Google Scholar]
- Airehrour, D.; Gutierrez, J.A.; Kumar, S. SecTrust -RPL: A secure trust-aware RPL routing protocol for Internet of Things. Future Gener. Comput. Syst. 2019, 93, 860–876. [Google Scholar] [CrossRef]
- Rikli, N.E.; Alnasser, A. Lightweight trust model for the detection of concealed malicious nodes in sparse wireless ad hoc networks. Int. J. Distrib. Sens. Netw. 2016, 12, 1550147716657246. [Google Scholar] [CrossRef][Green Version]
- Yan, Z.; Zhang, P.; Vasilakos, A.V. A survey on trust management for Internet of Things. J. Netw. Comput. Appl. 2014, 42, 120–134. [Google Scholar] [CrossRef]
- Wu, X.; Li, F. A multi-domain trust management model for supporting RFID applications of IoT. PLoS ONE 2017, 12, e0181124. [Google Scholar] [CrossRef]
- Steinhubl, S.R.; Muse, E.D.; Topol, E.J. The emerging field of mobile health. Sci. Transl. Med. 2015, 7, 283rv3. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context aware computing for the Internet of Things: A survey. IEEE Commun. Surv. Tutor. 2013, 16, 414–454. [Google Scholar] [CrossRef]
- Karlof, C.; Sastry, N.; Wagner, D.A. TinySec: A link layer security architecture for wireless sensor networks. In Proceedings of the ACM 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 162–175. [Google Scholar]
- Hussain, F.J.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine learning in IoT security: Current solutions and future challenges. IEEE Commun. Surv. Tutorials 2020, 22, 1686–1721. [Google Scholar] [CrossRef]
- Liang, F.; Hatcher, W.G.; Liao, W.; Gao, W.; Yu, W. Machine Learning for Security and the Internet of Things: The Good, the Bad, and the Ugly. IEEE Access 2019, 7, 158126–158147. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Tang, F.; Mao, B.; Kato, N.; Akashi, O.; Inoue, T.; Mizutani, K. State-of-the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent network traffic control systems. IEEE Commun. Surv. Tutor. 2017, 19, 2432–2455. [Google Scholar] [CrossRef]
- Modi, C.; Patel, D.R.; Borisaniya, B.; Patel, H.; Patel, A.; Rajarajan, M. A survey of intrusion detection techniques in cloud. J. Netw. Comput. Appl. 2013, 36, 42–57. [Google Scholar] [CrossRef]
- Zhao, K.; Ge, L. A survey on the Internet of Things security. In Proceedings of the IEEE 9th International Conference on Computational Intelligence and Security (CIS), Chengdu, China, 14–15 December 2013; pp. 663–667. [Google Scholar] [CrossRef]
- Bahtiyar, S.; Çaglayan, M.U. Extracting trust information from security system of a service. J. Netw. Comput. Appl. 2012, 35, 480–490. [Google Scholar] [CrossRef]
- Banerjee, A.; Venkatasubramanian, K.K.; Mukherjee, T.; Gupta, S.K.S. Ensuring safety, security, and sustainability of mission-critical cyber-physical systems. Proc. IEEE 2012, 100, 283–299. [Google Scholar] [CrossRef]
- AlTawy, R.; Youssef, A.M. Security tradeoffs in cyber physical systems: A case study survey on implantable medical devices. IEEE Access 2016, 4, 959–979. [Google Scholar] [CrossRef]
- Khan, Z.; Aalsalem, M.Y.; Khan, M.K. Communal acts of IoT consumers: A potential threat to security and privacy. IEEE Trans. Consum. Electron. 2019, 65, 64–72. [Google Scholar] [CrossRef]
- Doshi, R.; Apthorpe, N.; Feamster, N. Machine learning DDoS detection for consumer Internet of Things devices. In Proceedings of the 2018 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 24–24 May 2018. [Google Scholar]
- Abomhara, M. Cyber security and the Internet of Things:Vulnerabilities, threats, intruders and attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Abbas, G.; Mehmood, A.; Lloret, J.; Raza, M.S.; Ibrahim, M. FIPA-based reference architecture for efficient discovery and selection of appropriate cloud service using cloud ontology. Int. J. Commun. Syst. 2020, 33, e4504. [Google Scholar] [CrossRef]
- Subashini, S.; Kavitha, V. A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 2011, 34, 1–11. [Google Scholar] [CrossRef]
- Bhattasali, T.; Chaki, R.; Chaki, N. Secure and trusted cloud of things. In Proceedings of the Annual IEEE India Conference (INDICON), Mumbai, India, 13–15 December 2013; pp. 1–6. [Google Scholar]
- Faruki, P.; Bharmal, A.; Laxmi, V.; Ganmoor, V.; Gaur, M.S.; Conti, M.; Rajarajan, M. Android security: A survey of issues, malware penetration, and defenses. IEEE Commun. Surv. Tutor. 2015, 17, 998–1022. [Google Scholar] [CrossRef]
- Jordan, M.I.; Mitchell, T.M. Machine learning: Trends, perspectives, and prospects. Science 2015, 349, 255–260. [Google Scholar] [CrossRef]
- Mishra, P.; Varadharajan, V.; Tupakula, U.; Pilli, E.S. A detailed investigation and analysis of using machine learning techniques for intrusion detection. IEEE Commun. Surv. Tutor. 2019, 21, 686–728. [Google Scholar] [CrossRef]
- Lugmayr, A.; Danelljan, M.; Timofte, R. Unsupervised learning for real-world super-resolution. In Proceedings of the 2019 IEEE/CVF International Conference on Computer Vision Workshop (ICCVW), Seoul, Korea, 27–28 October 2019; pp. 3408–3416. [Google Scholar]
- Mnih, V.; Kavukcuoglu, K.; Silver, D.; Rusu, A.A.; Veness, J.; Bellemare, M.G.; Graves, A.; Riedmiller, M.; Fidjel, A.K.; Ostrovski, G.; et al. Human-level control through deep reinforcement learning. Nature 2015, 518, 529. [Google Scholar] [CrossRef] [PubMed]
- Quinlan, J.R. Induction of decision trees. Mach. Learn. 1986, 1, 81–106. [Google Scholar] [CrossRef]
- Du, W.; Zhan, Z. Building decision tree classifier on private data. In Proceedings of the IEEE International Conference Privacy Security Data Mining, Syracuse, New York, NY, USA, 14 December 2002; pp. 1–8. [Google Scholar]
- Kotsiantis, S.B. Decision trees: A recent overview. Artif. Intell. Rev. 2013, 39, 261–283. [Google Scholar] [CrossRef]
- Goeschel, K. Reducing false positives in intrusion detection systems using data-mining techniques utilizing support vector machines, decision trees, and Naive Bayes for off-line analysis. In Proceedings of the IEEE SoutheastCon, Norfolk, VI, USA, 30 March–3 April 2016; pp. 1–6. [Google Scholar]
- Alharbi, S.; Rodriguez, P.; Maharaja, R.; Iyer, P.; Subaschandrabose, N.; Ye, Z. Secure the Internet of Things with challenge response authentication in fog computing. In Proceedings of the IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–2. [Google Scholar]
- Kalaivaani, P.T.; Krishnamoorthy, R.; Reddy, A.S.; Chelladurai, A.D.D. Adaptive Multimode Decision Tree Classification Model Using Effective System Analysis in IDS for 5G and IoT Security Issues. In Secure Communication for 5G and IoT Networks; Springer: Cham, Switzerland, 2022; pp. 141–158. [Google Scholar]
- Tajbakhsh, A.; Rahmati, M.; Mirzaei, A. Intrusion detection using fuzzy association rules. Appl. Soft Comput. 2009, 9, 462–469. [Google Scholar] [CrossRef]
- Tong, S.; Koller, D. Support vector machine active learning with applications to text classification. J. Mach. Learn. Res. 2001, 2, 45–66. [Google Scholar]
- Hu, W.; Liao, Y.; Vemuri, V.R. Robust support vector machines for anomaly detection in computer security. In Proceedings of the International Conference on Machine Learning and Applications (ICMLA), Los Angeles, CA, USA, 23–24 June 2003; pp. 168–174. [Google Scholar]
- Liu, Y.; Pi, D. A novel kernel SVM algorithm with game theory for network intrusion detection. KSII Trans. Internet Inf. Syst. 2017, 11, 4043–4060. [Google Scholar]
- Wagner, C.; François, J.; Engel, T. Machine learning approach for IP-flow record anomaly detection. In Proceedings of the International Conference on Research in Networking, Valencia, Spain, 9–13 May 2011; pp. 28–39. [Google Scholar]
- Ham, H.S.; Kim, H.H.; Kim, M.S.; Choi, M.J. Linear SVM-based android malware detection for reliable IoT services. J. Appl. Math. 2014, 2014, 594501. [Google Scholar] [CrossRef]
- Lerman, L.; Bontempi, G.; Markowitch, O. A machine learning approach against a masked AES. J. Cryptograph. Eng. 2015, 5, 123–139. [Google Scholar] [CrossRef]
- D’Agostini, G. A multidimensional unfolding method based on Bayes’ theorem. Nucl. Instrum. Methods Phys. Res. A Accel. Spectr. Detect. Assoc. Equip. 1995, 362, 487–498. [Google Scholar] [CrossRef]
- Panda, M.; Patra, M.R. Network intrusion detection using Naive Bayes. Int. J. Comput. Sci. Netw. Secur. 2007, 7, 258–263. [Google Scholar]
- Mukherjee, S.; Sharma, N. Intrusion detection using Naive Bayes classifier with feature reduction. Procedia Technol. 2012, 4, 119–128. [Google Scholar] [CrossRef]
- Ng, A.Y.; Jordan, M.I. On discriminative vs. generative classifiers: A comparison of logistic regression and naive Bayes. Adv. Neural Inf. Process. Syst. 2002, 14, 841–848. [Google Scholar]
- Ioannou, C.; Vassiliou, V. Network Attack Classification in IoT Using Support Vector Machines. J. Sens. Actuator Netw. 2021, 10, 58. [Google Scholar] [CrossRef]
- Deng, Z.; Zhu, X.; Cheng, D.; Zong, M.; Zhang, S. Efficient kNN classification algorithm for big data. Neurocomputing 2016, 195, 143–148. [Google Scholar] [CrossRef]
- Su, M.-Y. Real-time anomaly detection systems for denial-of-service attacks by weighted k-nearest-neighbor classifiers. Expert Syst. Appl. 2011, 38, 3492–3498. [Google Scholar] [CrossRef]
- Li, W.; Yi, P.; Wu, Y.; Pan, L.; Li, J. A new intrusion detection system based on KNN classification algorithm in wireless sensor network. J. Elect. Comput. Eng. 2014, 2014, 8. [Google Scholar] [CrossRef]
- Breiman, L. Random forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Domb, M.; Bonchek-Dokow, E.; Leshem, G. Lightweight adaptive Random-Forest for IoT rule generation and execution. J. Inf. Secur. Appl. 2017, 34, 218–224. [Google Scholar] [CrossRef]
- Cutler, D.R.; Edwards, T.C., Jr.; Beard, K.H.; Cutler, A.; Hess, K.T.; Gibson, J.; Lawler, J.J. Random forests for classification in ecology. Ecology 2007, 88, 2783–2792. [Google Scholar] [CrossRef] [PubMed]
- Agrawal, R.; Imieliñski, T.; Swami, A. Mining association rules between sets of items in large databases. In Proceedings of the 1993 ACM SIGMOD International Conference on Management of Data, Washington, DC, USA, 25–28 May 1993; pp. 207–216. [Google Scholar]
- WoŸniak, M.; Graña, M.; Corchado, E. A survey of multiple classifier systems as hybrid systems. Inf. Fusion 2014, 16, 3–17. [Google Scholar] [CrossRef]
- Zhang, C.; Ma, Y. Ensemble Machine Learning: Methods and Applications; Springer: New York, NY, USA, 2012. [Google Scholar]
- Chen, Z.S.; Zhang, X.; Pedrycz, W.; Wang, X.J.; Chin, K.S.; Martínez, L. K-means clustering for the aggregation of HFLTS possibility distributions: N-two-stage algorithmic paradigm. Knowl.-Based Syst. 2021, 227, 107230. [Google Scholar] [CrossRef]
- Hartigan, J.A.; Wong, M.A. Algorithm AS 136: A k-means clustering algorithm. J. Roy. Stat. Soc. C (Appl. Stat.) 1979, 28, 100–108. [Google Scholar] [CrossRef]
- Jain, A.K. Data clustering: 50 years beyond k-means. Pattern Recognit. Lett. 2010, 31, 651–666. [Google Scholar] [CrossRef]
- Münz, G.; Li, S.; Carle, G. Traffic anomaly detection using k-means clustering. In GI/ITG Workshop MMBnet; 2007; pp. 1–8. Available online: https://www.net.in.tum.de/projects/dfg-lupus/files/muenz07k-means.pdf (accessed on 10 June 2022).
- Bosman, H.H.; Iacca, G.; Tejada, A.; Wörtche, H.J.; Liotta, A. Ensembles of incremental learners to detect anomalies in ad hoc sensor networks. Ad Hoc Netw. 2015, 35, 14–36. [Google Scholar] [CrossRef]
- Wold, S.; Esbensen, K.; Geladi, P. Principal component analysis. Chemometr. Intell. Lab. Syst. 1987, 2, 37–52. [Google Scholar] [CrossRef]
- Nobakht, M.; Sivaraman, V.; Boreli, R. A host-based intrusion detection and mitigation framework for smart home IoT using OpenFlow. In Proceedings of the IEEE 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 147–156. [Google Scholar]
- Aminanto, M.E.; Kim, K. Improving detection of Wi-Fi impersonation by fully unsupervised deep learning. In International Workshop on Information Security Applications (WISA); Springer: Cham, Switzerland, 2017; pp. 212–223. [Google Scholar]
- Shi, C.; Liu, J.; Liu, H.; Chen, Y. Smart user authentication through actuation of daily activities leveraging WiFi-enabled IoT. In Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Chennai, India, 10–14 July 2017; p. 5. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Shabtai, A.; Guarnizo, J.D.; Ochoa, M.; Tippenhauer, N.O.; Elovici, Y. ProfilIoT: A machine learning approach for IoT device identification based on network traffic analysis. In Proceedings of the ACM Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017; pp. 506–509. [Google Scholar]
- Lakhotia, A.; Kapoor, A.; Kumar, E. Are metamorphic viruses really invincible. Virus Bull. 2004, 12, 57. [Google Scholar]
- Miettinen, M.; Marchal, S.; Hafeez, I.; Asokan, N.; Sadeghi, A.-R.; Tarkoma, S. IoT sentinel: Automated device-type identification for security enforcement in IoT. In Proceedings of the IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2177–2184. [Google Scholar]
- Smys, S.; Basar, A.; Wang, H. Hybrid intrusion detection system for internet of things (IoT). J. ISMAC 2020, 2, 190–199. [Google Scholar] [CrossRef]
- Li, Q.; Zhang, K.; Cheffena, M.; Shen, X. Channel-based sybil detection in industrial wireless sensor networks: A multi-kernel approach. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Rathore, S.; Park, J.H. Semi-supervised learning based distributed attack detection framework for IoT. Appl. Soft Comput. 2018, 72, 79–89. [Google Scholar] [CrossRef]
- Niknam, S.; Dhillon, H.S.; Reed, J.H. Federated learning for wireless communications: Motivation, opportunities and challenges. arXiv 2019, arXiv:1908.06847. [Google Scholar] [CrossRef]
- Brownlee, J. A gentle introduction to generative adversarial networks (GANS). Tutor. Gan Lin395c Res. Comput. Linguist. 2019, 17. [Google Scholar]
- Ferdowsi, A.; Saad, W. Generative adversarial networks for distributed intrusion detection in the internet of things. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019. [Google Scholar]
- Musonda, C.; Monica, M.K.; Nyirenda, M.; Phiri, J. Security, Privacy and Integrity in Internet of Things—A Review. In Proceedings of the ICTSZ International Conference in ICTs, Lusaka, Zambia, 18 July 2019; pp. 148–152. [Google Scholar]
- Ferrag, M.A.; Shu, L. The performance evaluation of blockchain-based security and privacy systems for the Internet of Things: A tutorial. IEEE Internet Things J. 2021, 8, 17236–17260. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Friha, O.; Yang, X. Cyber Security Intrusion Detection for Agriculture 4.0: Machine Learning-Based Solutions, Datasets, and Future Directions. IEEE/CAA J. Autom. Sin. 2021, 9, 407–436. [Google Scholar] [CrossRef]
- Hussain, M.; Mehmood, A.; Khan, S.; Khan, M.A.; Iqbal, Z. Authentication techniques and methodologies used in wireless body area networks. J. Syst. Archit. 2019, 101, 101655. [Google Scholar] [CrossRef]




| Ref. | Supervised Learning | Unsupervised ML | Threat Detected | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| NB | SVM | DT | KNN | RF | AR | EL | K-Means | PCA | ||
| [60] | - | √ | - | √ | - | - | √ | - | - | False detection attack |
| [62] | - | √ | - | - | - | - | - | - | - | Intrusion detection |
| [63] | - | - | - | - | √ | - | - | - | - | Authorization |
| [64] | - | - | - | - | - | - | - | - | √ | Intrusion detection |
| [65] | - | √ | - | - | - | - | - | - | - | Authentication |
| [66] | - | - | - | - | - | - | √ | - | - | Authorization |
| [67] | - | - | - | √ | - | - | - | - | - | Impersonation attack |
| [68] | - | √ | - | - | - | - | - | √ | - | Data tempering |
| [69] | - | - | - | - | - | - | - | - | √ | Intrusion detection |
| [70] | - | - | - | - | - | - | - | - | - | Intrusion detection |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abbas, G.; Mehmood, A.; Carsten, M.; Epiphaniou, G.; Lloret, J. Safety, Security and Privacy in Machine Learning Based Internet of Things. J. Sens. Actuator Netw. 2022, 11, 38. https://doi.org/10.3390/jsan11030038
Abbas G, Mehmood A, Carsten M, Epiphaniou G, Lloret J. Safety, Security and Privacy in Machine Learning Based Internet of Things. Journal of Sensor and Actuator Networks. 2022; 11(3):38. https://doi.org/10.3390/jsan11030038
Chicago/Turabian StyleAbbas, Ghulam, Amjad Mehmood, Maple Carsten, Gregory Epiphaniou, and Jaime Lloret. 2022. "Safety, Security and Privacy in Machine Learning Based Internet of Things" Journal of Sensor and Actuator Networks 11, no. 3: 38. https://doi.org/10.3390/jsan11030038
APA StyleAbbas, G., Mehmood, A., Carsten, M., Epiphaniou, G., & Lloret, J. (2022). Safety, Security and Privacy in Machine Learning Based Internet of Things. Journal of Sensor and Actuator Networks, 11(3), 38. https://doi.org/10.3390/jsan11030038








