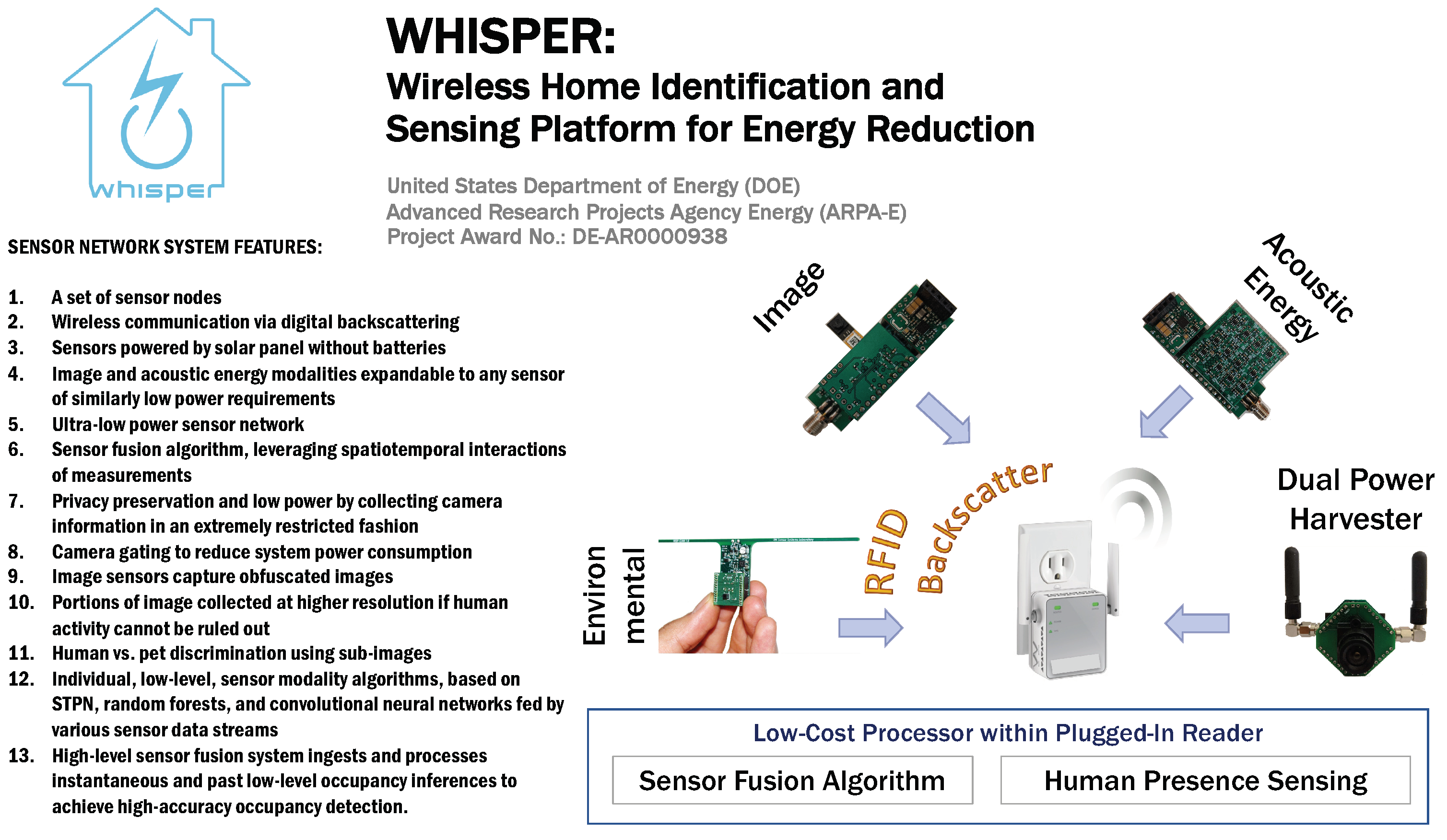
WHISPER: Wireless Home Identification and Sensing Platform for Energy Reduction
Abstract
:1. Introduction
1.1. Motivation
1.2. Design Focus
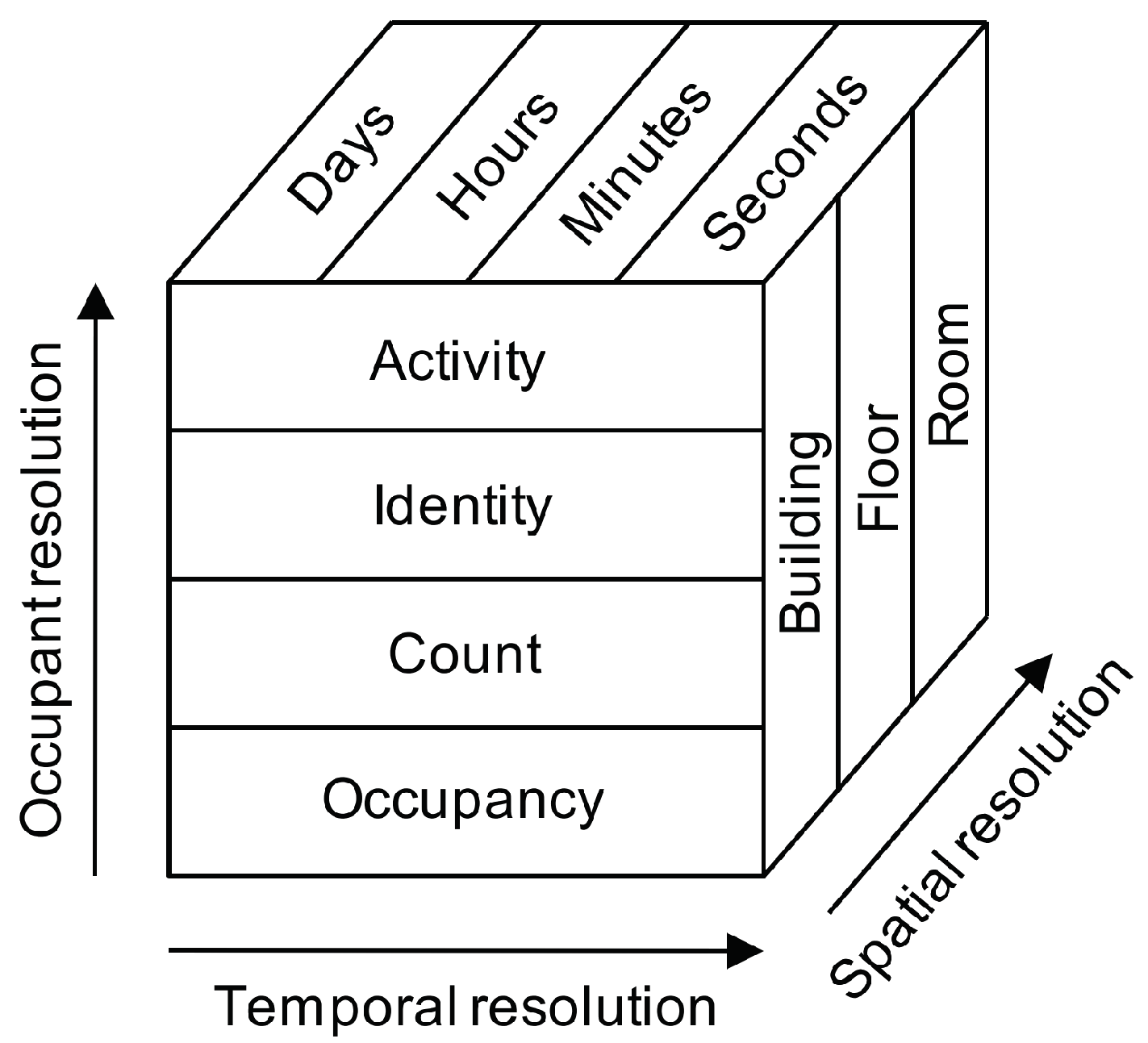
1.3. Background on Occupancy Detection in Buildings
1.3.1. Traditional Methods of Detection
1.3.2. Image Detection
1.3.3. Other Detection Methods
1.3.4. Residential Occupancy Detection
2. Materials and Methods
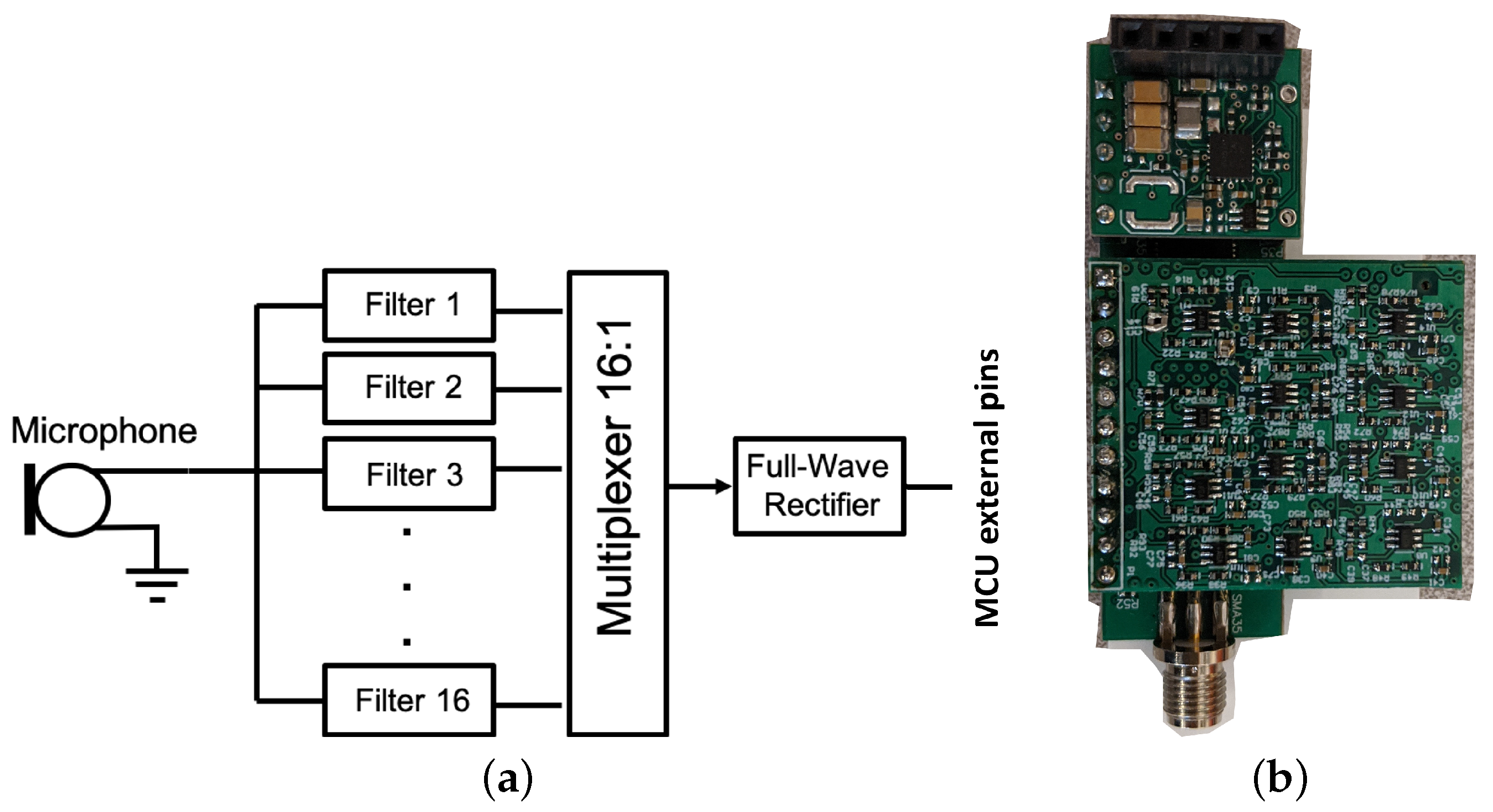
2.1. Sensor Hardware Development
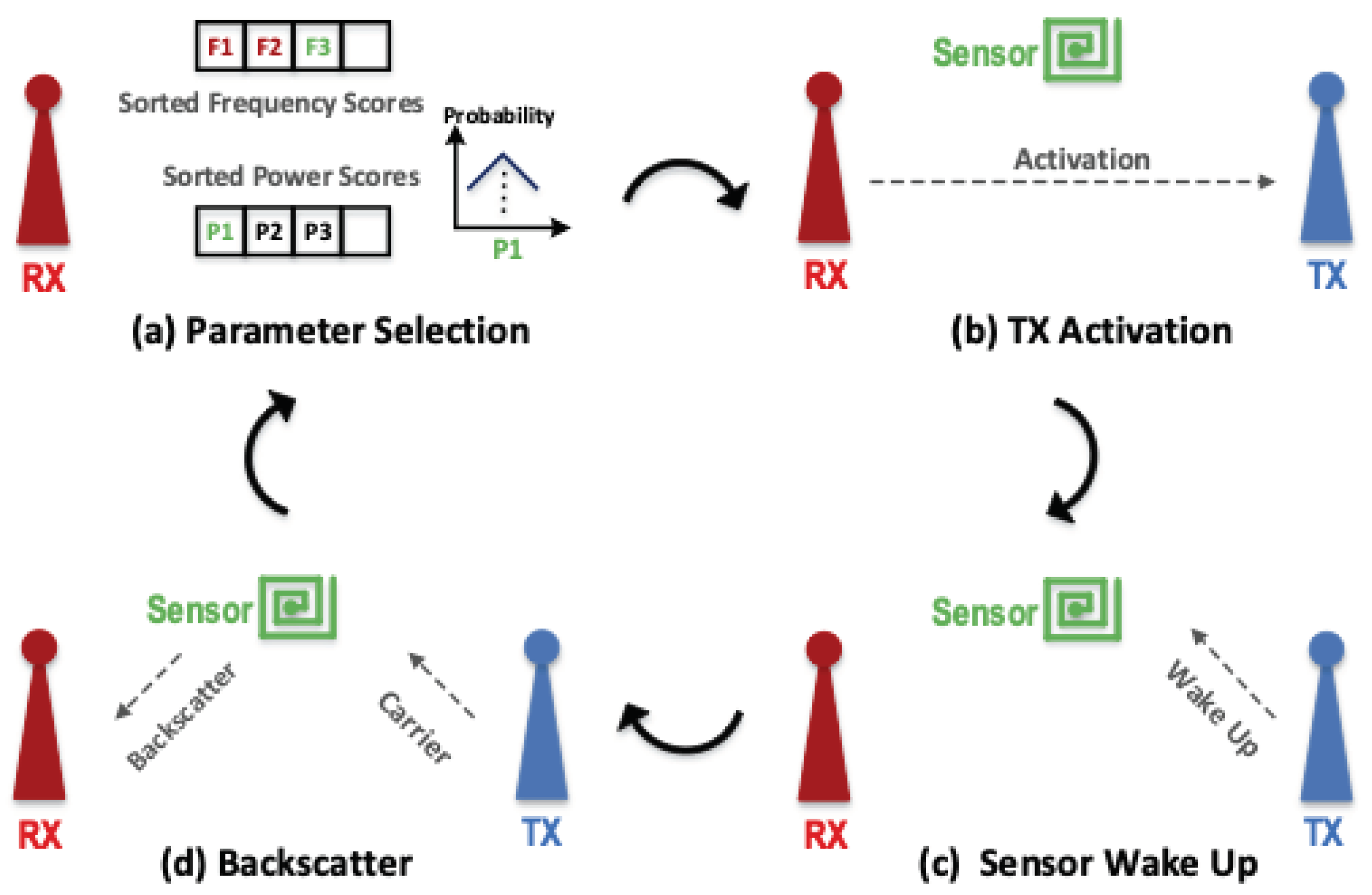
2.1.1. Backscatter Communication
2.1.2. Communication Network Design
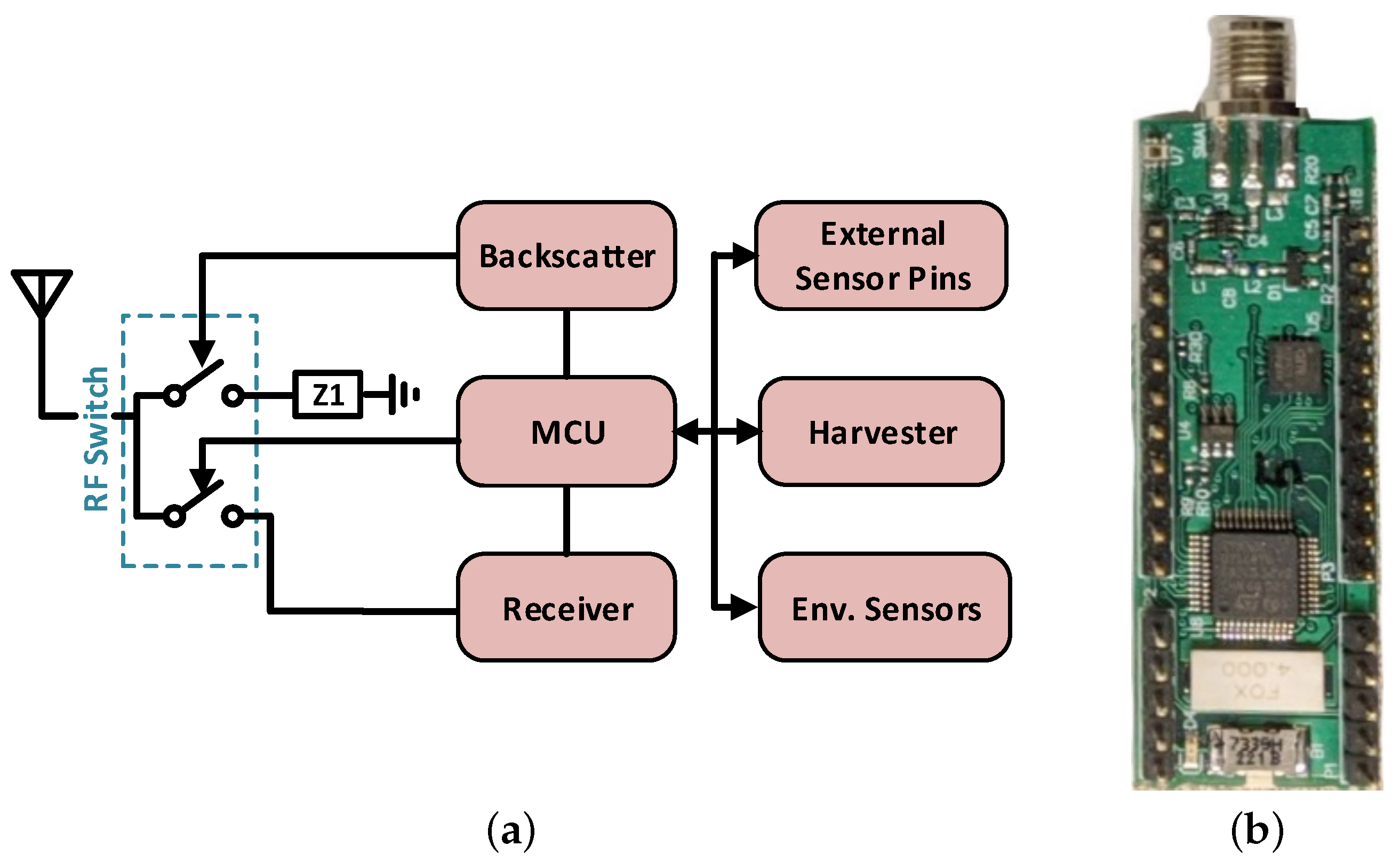
2.1.3. Sensor Node Design
2.2. Inference Algorithms
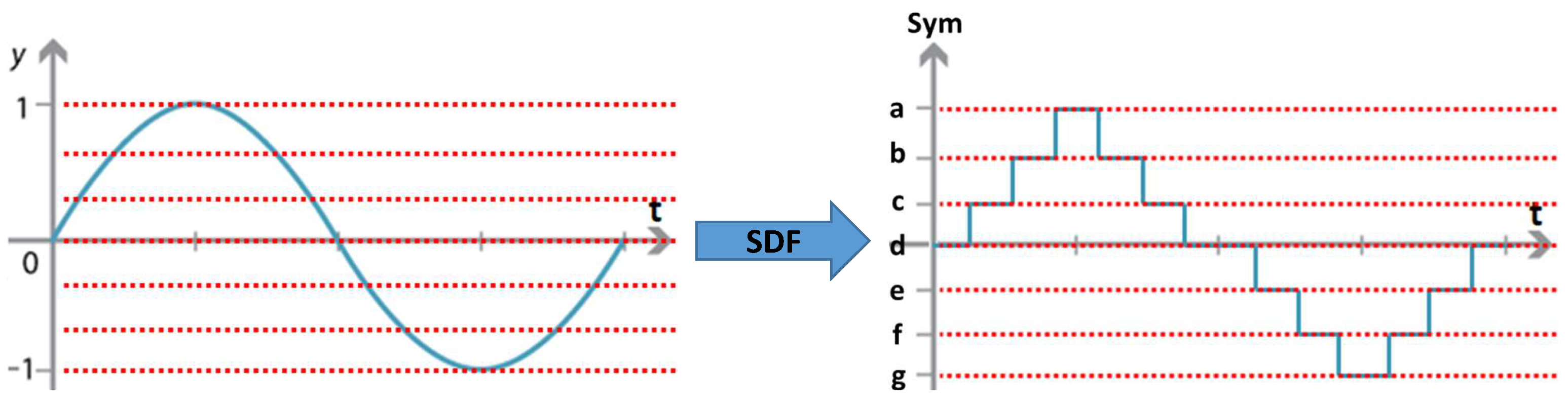
2.2.1. Modality Level Inferences
Environmental Data
Image Data
Acoustic Energy Data
2.3. Sensor Fusion Algorithm
2.3.1. Model Framework
- = Intercept (model offset);
- = Autoregressive coefficients;
- = Exogenous modality-related coefficients;
- = Exogenous time-related coefficients;
- = Probability of occupation given by audio inference;
- = Probability of occupation given by image inference;
- = Probability of occupation given by temperature inference;
- = Probability of occupation given by relative humidity inference;
- = Probability of occupation given by illuminance inference;
- = Probability of occupation given by inference;
- = Binary weekend–weekday flag (with 0 meaning day is in {Saturday, Sunday});
- = ;
- = ;
- M = Total length of history considered in hours;
- K = Number of time-steps per hour;
- = Occupancy prediction (whole-house) at the current time-step, t;
- = Average of predicted whole-house occupancy m hours in the past.
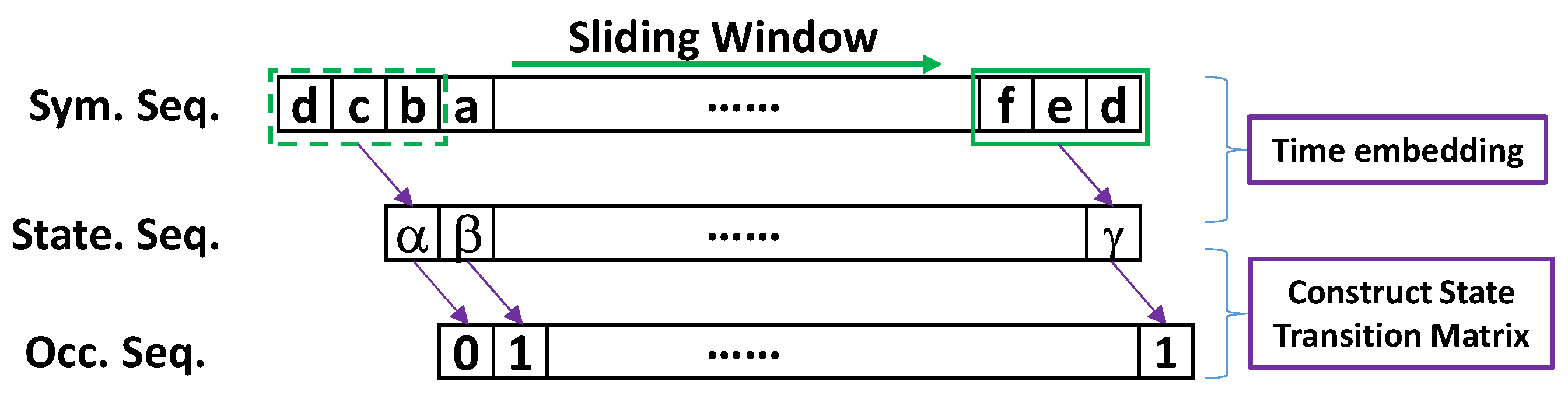
2.3.2. Algorithm Development
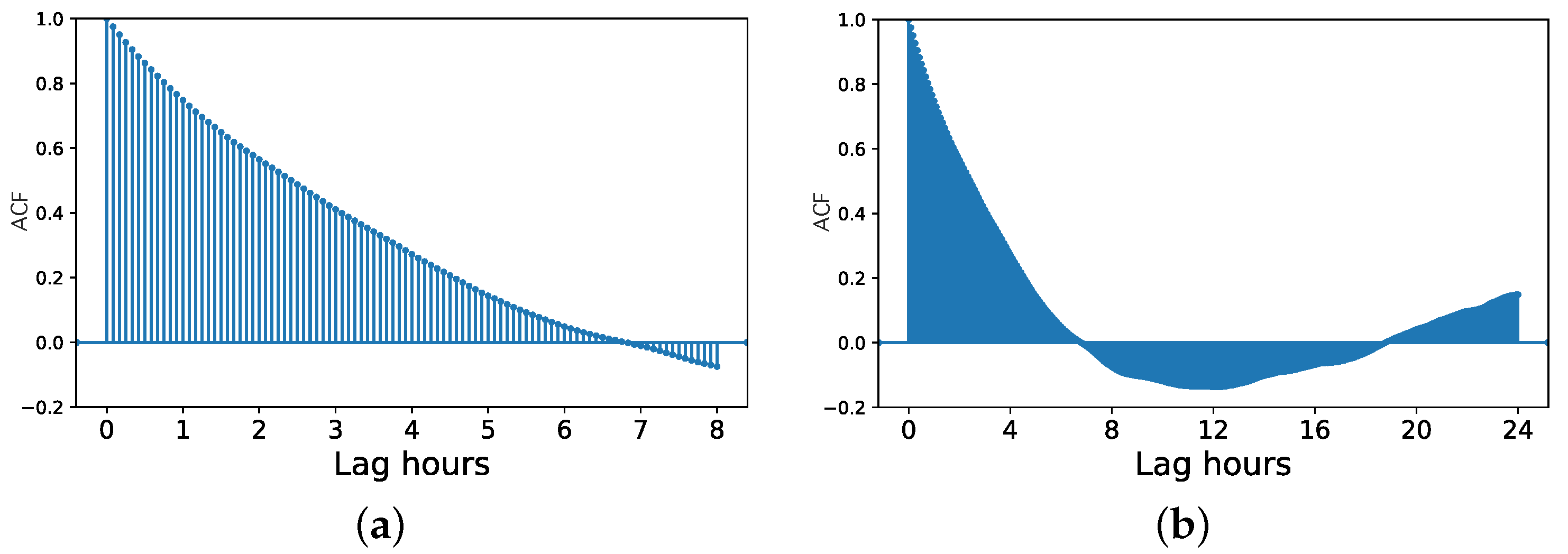
2.3.3. Lag Values
2.3.4. Regularization
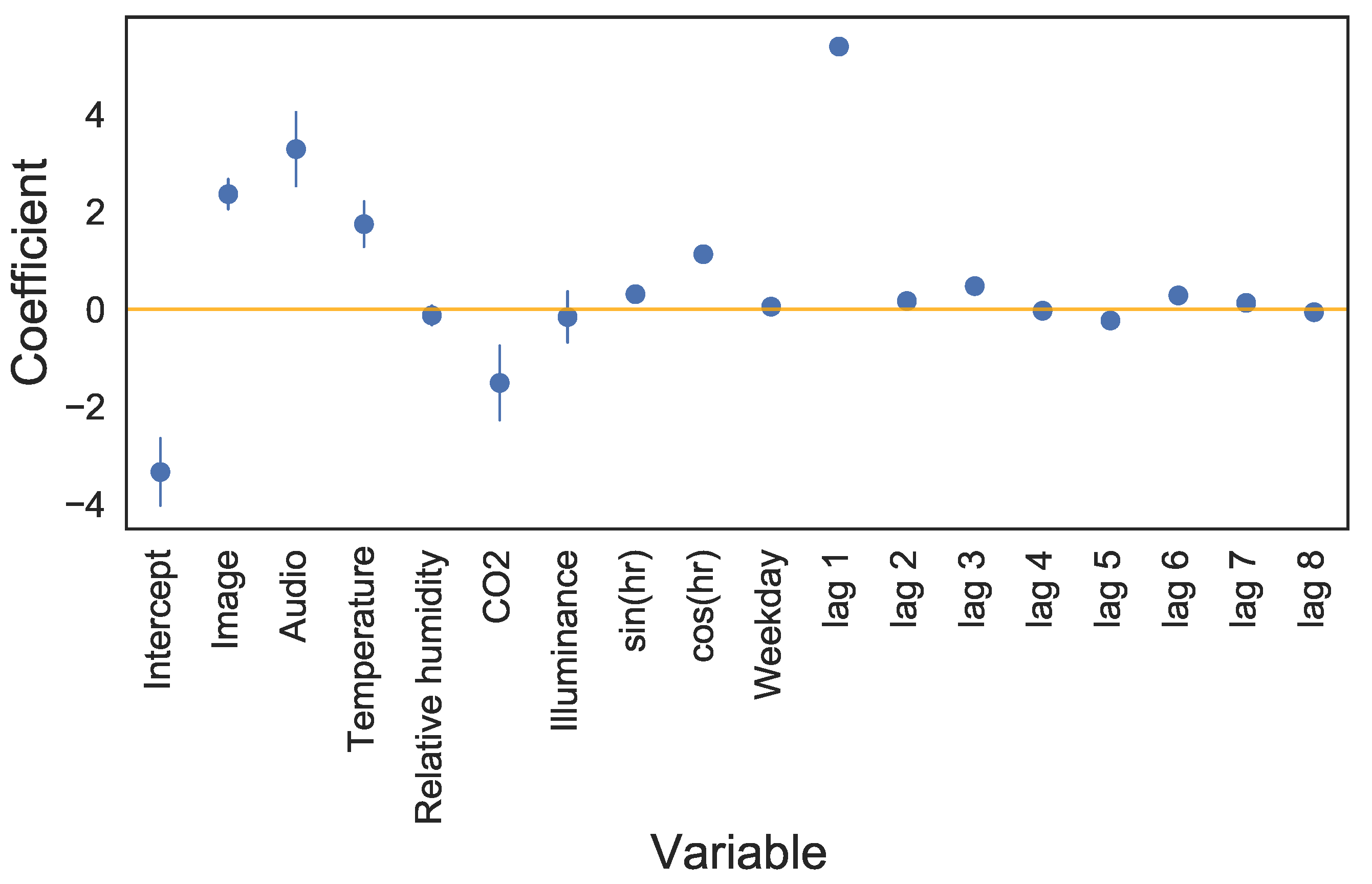
2.3.5. Model Coefficients
2.3.6. Interpretation of Model Coefficients
3. Results
3.1. WHISPER System Hardware Evaluation
3.1.1. Power Consumption
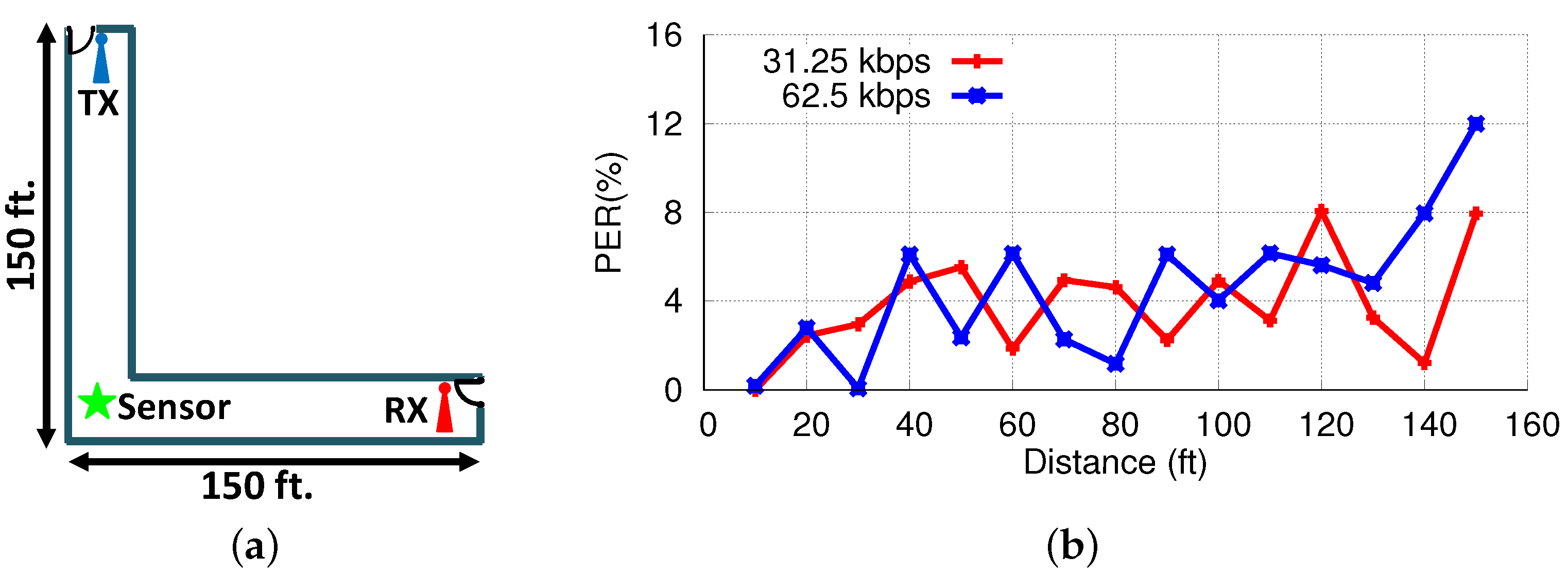
3.1.2. Line-of-Sight Communication Range
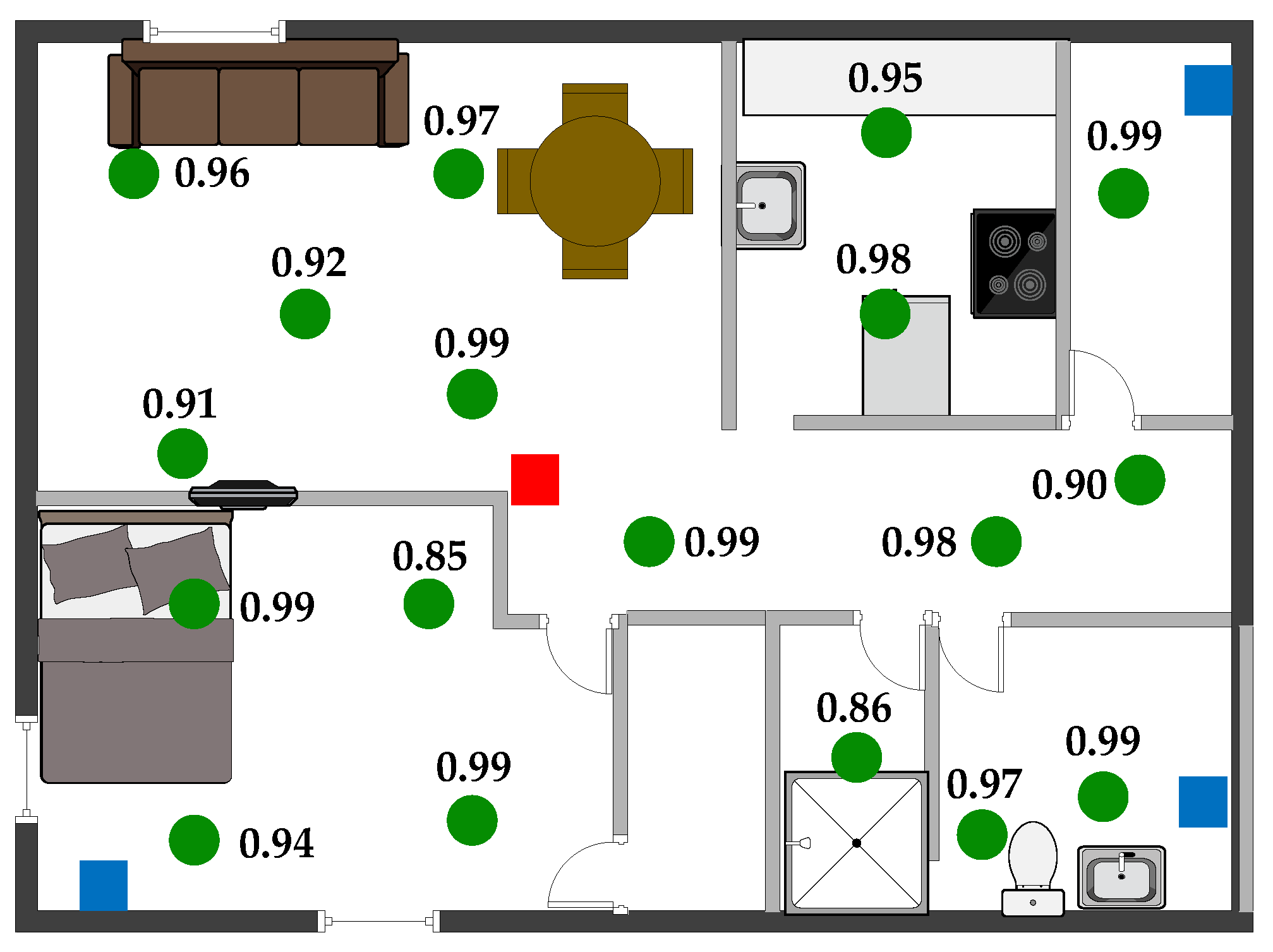
3.1.3. Coverage
3.2. WHISPER System Evaluation
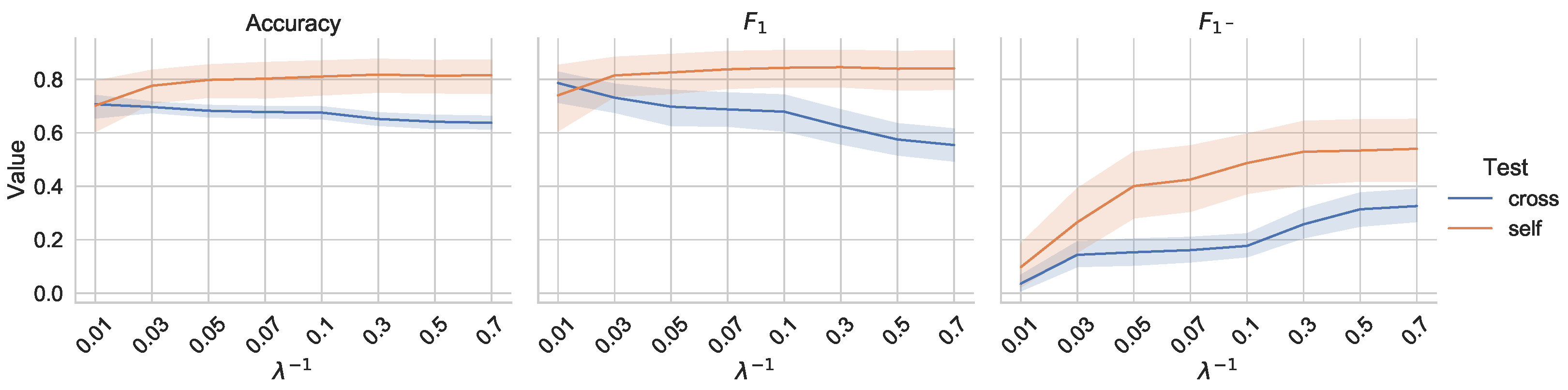
3.3. Sensor Fusion Performance
Comparison to Baselines
3.4. Energy Savings Potential
4. Discussion
4.1. System Extension
4.1.1. Additional Sensor Modalities
4.1.2. Occupancy Counting
4.2. Non-Energy Benefits
4.2.1. Health Care
4.2.2. Security
4.2.3. Indoor Environmental Quality
4.3. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sippel, S.; Meinshausen, N.; Fischer, E.M.; Székely, E.; Knutti, R. Climate change now detectable from any single day of weather at global scale. Nat. Clim. Chang. 2020, 10, 35–41. [Google Scholar] [CrossRef]
- Hoegh-Guldberg, O.; Jacob, D.; Taylor, M.; Bolaños, T.G.; Bindi, M.; Brown, S.; Camilloni, I.A.; Diedhiou, A.; Djalante, R.; Ebi, K.; et al. The human imperative of stabilizing global climate change at 1.5 °C. Science 2019, 365, eaaw6974. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- IPCC. Climate Change and Land: An IPCC Special Report on Climate Change, Desertification, Land Degradation, Sustainable Land Management, Food Security, and Greenhouse Gas Fluxes in Terrestrial Ecosystems; IPCC: Geneva, Switzerland, 2019; pp. 1–864. [Google Scholar]
- Berry, C.; Lawson, G.; Woodward, M. Highlights from the 2015 RECS: Energy Consumption, Expenditures, and End-Use Modeling; Technical Report; U.S. Energy Information Administration: Washington, DC, USA, 2018.
- Lu, J.; Sookoor, T.; Srinivasan, V.; Gao, G.; Holben, B.; Stankovic, J.; Field, E.; Whitehouse, K. The Smart Thermostat: Using Occupancy Sensors to Save Energy in Homes. In Proceedings of the 8th ACM Conference on Embedded Networked Sensor Systems; SenSys ’10; Association for Computing Machinery: New York, NY, USA, 2010; pp. 211–224. [Google Scholar] [CrossRef]
- Gao, G.; Whitehouse, K. The Self-Programming Thermostat: Optimizing Setback Schedules Based on Home Occupancy Patterns. In Proceedings of the First ACM Workshop on Embedded Sensing Systems for Energy-Efficiency in Buildings; BuildSys ’09; Association for Computing Machinery: New York, NY, USA, 2009; pp. 67–72. [Google Scholar] [CrossRef]
- Soltanaghaei, E.; Whitehouse, K. WalkSense: Classifying Home Occupancy States Using Walkway Sensing. In Proceedings of the 3rd ACM International Conference on Systems for Energy-Efficient Built Environments; BuildSys ’16; Association for Computing Machinery: New York, NY, USA, 2016; pp. 167–176. [Google Scholar] [CrossRef] [Green Version]
- Pritoni, M.; Meier, A.K.; Aragon, C.; Perry, D.; Peffer, T. Energy efficiency and the misuse of programmable thermostats: The effectiveness of crowdsourcing for understanding household behavior. Energy Res. Soc. Sci. 2015, 8, 190–197. [Google Scholar] [CrossRef] [Green Version]
- Peffer, T.; Pritoni, M.; Meier, A.; Aragon, C.; Perry, D. How people use thermostats in homes: A review. Build. Environ. 2011, 46, 2529–2541. [Google Scholar] [CrossRef] [Green Version]
- Meier, A. How people actually use thermostats. In Proceedings of the American Council for an Energy-Efficient Economy Conference, ACEEE (2010), Sacramento, CA, USA, 14–17 November 2010. [Google Scholar]
- Ayan, O.; Turkay, B. Smart Thermostats for Home Automation Systems and Energy Savings from Smart Thermostats. In Proceedings of the 2018 6th International Conference on Control Engineering Information Technology (CEIT), Istanbul, Turkey, 25–27 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Stopps, H.; Touchie, M.F. Reduction of HVAC system runtime due to occupancy-controlled smart thermostats in contemporary multi-unit residential building suites. IOP Conf. Ser. Mater. Sci. Eng. 2019, 609, 062013. [Google Scholar] [CrossRef] [Green Version]
- Miu, L.M.; Mazur, C.M.; van Dam, K.H.; Lambert, R.S.; Hawkes, A.; Shah, N. Going smart, staying confused: Perceptions and use of smart thermostats in British homes. Energy Res. Soc. Sci. 2019, 57, 101228. [Google Scholar] [CrossRef]
- Pritoni, M.; Woolley, J.M.; Modera, M.P. Do occupancy-responsive learning thermostats save energy? A field study in university residence halls. Energy Build. 2016, 127, 469–478. [Google Scholar] [CrossRef]
- Bustamante, S.; Castro, P.; Laso, A.; Manana, M.; Arroyo, A. Smart thermostats: An experimental facility to test their capabilities and savings potential. Sustainability 2017, 9, 1462. [Google Scholar] [CrossRef] [Green Version]
- Wang, J.; Garifi, K.; Baker, K.; Zuo, W.; Zhang, Y.; Huang, S.; Vrabie, D. Optimal Renewable Resource Allocation and Load Scheduling of Resilient Communities. Energies 2020, 13, 5683. [Google Scholar] [CrossRef]
- Garifi, K.; Baker, K.; Touri, B.; Christensen, D. Stochastic Model Predictive Control for Demand Response in a Home Energy Management System. In Proceedings of the 2018 IEEE Power Energy Society General Meeting (PESGM), Portland, OR, USA, 5–9 August 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Roth, A.; Reyna, J. Grid-Interactive Efficient Buildings Technical Report Series: Whole-Building Controls, Sensors, Modeling, and Analytics; Technical Report; USDOE Office of Energy Efficiency and Renewable Energy (EERE); Energy Efficiency Office and National Renewable Energy Laboratory (NREL): Washington, DC, USA, 2019. [Google Scholar] [CrossRef]
- Blonsky, M.; Nagarajan, A.; Ghosh, S.; McKenna, K.; Veda, S.; Kroposki, B. Potential Impacts of Transportation and Building Electrification on the Grid: A Review of Electrification Projections and Their Effects on Grid Infrastructure, Operation, and Planning. Curr. Sustain. Energy Rep. 2019, 6, 169–176. [Google Scholar] [CrossRef]
- U.S. Energy Information Administration. Monthly Energy Review. Available online: https://www.eia.gov/totalenergy/data/monthly/archive/00352104.pdf (accessed on 2 December 2021).
- Turley, C.; Jacoby, M.; Pavlak, G.; Henze, G. Development and evaluation of occupancy-aware HVAC control for residential building energy efficiency and occupant comfort. Energies 2020, 13, 5396. [Google Scholar] [CrossRef]
- Melfi, R.; Rosenblum, B.; Nordman, B.; Christensen, K.; Nordman, B.; Meier, A. Measuring Building Occupancy Using Existing Network Infrastructure. In Proceedings of the 2011 International Green Computing Conference and Workshops, Orlando, FL, USA, 25–28 July 2011; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Labeodan, T.; Zeiler, W.; Boxem, G.; Zhao, Y. Occupancy measurement in commercial office buildings for demand-driven control applications—A survey and detection system evaluation. Energy Build. 2015, 93, 303–314. [Google Scholar] [CrossRef] [Green Version]
- Stolshek, J.D.; Koehring, P.A. Ultrasonic Technology Provides for Control of Lighting. IEEE Trans. Ind. Appl. 1984, IA-20, 1564–1572. [Google Scholar] [CrossRef]
- Yang, D.; Xu, B.; Rao, K.; Sheng, W. Passive infrared (PIR)-based indoor position tracking for smart homes using accessibility maps and a-star algorithm. Sensors 2018, 18, 332. [Google Scholar] [CrossRef] [Green Version]
- Caicedo, D.; Pandharipande, A. Ultrasonic arrays for localized presence sensing. IEEE Sens. J. 2012, 12, 849–858. [Google Scholar] [CrossRef]
- Guo, X.; Tiller, D.K.; Henze, G.P.; Waters, C.E. The performance of occupancy-based lighting control systems: A review. Light. Res. Technol. 2010, 42, 415–431. [Google Scholar] [CrossRef]
- Shen, W.; Newsham, G.; Gunay, B. Leveraging existing occupancy-related data for optimal control of commercial office buildings: A review. Adv. Eng. Inform. 2017, 33, 230–242. [Google Scholar] [CrossRef] [Green Version]
- Hobson, B.W.; Lowcay, D.; Gunay, H.B.; Ashouri, A.; Newsham, G.R. Opportunistic occupancy-count estimation using sensor fusion: A case study. Build. Environ. 2019, 159, 106154. [Google Scholar] [CrossRef]
- Dodier, R.H.; Henze, G.P.; Tiller, D.K.; Guo, X. Building occupancy detection through sensor belief networks. Energy Build. 2006, 38, 1033–1043. [Google Scholar] [CrossRef]
- Haq, M.A.U.; Hassan, M.Y.; Abdullah, H.; Rahman, H.A.; Abdullah, M.P.; Hussin, F.; Said, D.M. A review on lighting control technologies in commercial buildings, their performance and affecting factors. Renew. Sustain. Energy Rev. 2014, 33, 268–279. [Google Scholar] [CrossRef]
- Liu, X.; Ghosh, P.; Ulutan, O.; Manjunath, B.S.; Chan, K.; Govindan, R. Caesar: Cross-camera complex activity recognition. In Proceedings of the 17th Conference on Embedded Networked Sensor Systems, SenSys 2019, New York, NY, USA, 10–13 November 2019; pp. 232–244. [Google Scholar] [CrossRef]
- Tsakanikas, V.; Dagiuklas, T. Video surveillance systems-current status and future trends. Comput. Electr. Eng. 2018, 70, 736–753. [Google Scholar] [CrossRef]
- Dalal, N.; Triggs, B.; Schmid, C.; Dalal, N.; Triggs, B.; Schmid, C.; Detection, H.; Oriented, U. Human Detection using Oriented Histograms of Flow and Appearance. In Proceedings of the European Conference on Computer Vision (ECCV ’06), Graz, Austria, 7–13 May 2006; pp. 428–441. [Google Scholar]
- Howard, B.; Acha, S.; Shah, N.; Polak, J. Implicit Sensing of Building Occupancy Count with Information and Communication Technology Data Sets. Build. Environ. 2019, 157, 297–308. [Google Scholar] [CrossRef]
- Sun, K.; Zhao, Q.; Zou, J. A review of building occupancy measurement systems. Energy Build. 2020, 216, 109965. [Google Scholar] [CrossRef]
- Caleb Sangogboye, F.; Jia, R.; Hong, T.; Spanos, C.; Baun Kjærgaard, M. A framework for privacy-preserving data publishing with enhanced utility for cyber-physical systems. ACM Trans. Sens. Netw. 2018, 14, 1–22. [Google Scholar] [CrossRef] [Green Version]
- Beymer, D. Person counting using stereo. In Proceedings of the Workshop on Human Motion, Austin, TX, USA, 7–8 December 2000; pp. 127–133. [Google Scholar] [CrossRef]
- Yang, C.E.; Shen, Y.T.; Liao, S.H. Integration of Real-time Facial Recognition and Visualization in BIM. In Proceedings of the 2020 IEEE Eurasia Conference on IOT, Communication and Engineering (ECICE), Yunlin, Taiwan, 23–25 October 2020; pp. 243–245. [Google Scholar] [CrossRef]
- Wang, X.; Tague, P. Non-Invasive User Tracking via Passive Sensing: Privacy Risks of Time-Series Occupancy Measurement. In Proceedings of the 2014 Workshop on Artificial Intelligent and Security Workshop; AISec ’14; Association for Computing Machinery: New York, NY, USA, 2014; pp. 113–124. [Google Scholar] [CrossRef]
- Ahmad, J.; Larijani, H.; Emmanuel, R.; Mannion, M.; Javed, A. Occupancy detection in non-residential buildings—A survey and novel privacy preserved occupancy monitoring solution. Appl. Comput. Inform. 2018, 1–9. [Google Scholar] [CrossRef]
- Schwee, J.H.; Sangogboye, F.C.; Kjærgaard, M.B. Evaluating Practical Privacy Attacks for Building Data Anonymized by Standard Methods. In Proceedings of the 2nd InternationalWorkshop on Security and Privacy for the Internet-of-Things (IoTSec), London, UK, 15 November 2019; pp. 11–14. [Google Scholar]
- Jia, R.; Dong, R.; Sastry, S.S.; Spanos, C.J. Privacy-enhanced architecture for occupancy-based HVAC Control. In Proceedings of the 8th International Conference on Cyber-Physical Systems, Pittsburgh, PA, USA, 18–21 April 2017; pp. 177–186. [Google Scholar] [CrossRef] [Green Version]
- Pappachan, P.; Degeling, M.; Yus, R.; Das, A.; Bhagavatula, S.; Melicher, W.; Naeini, P.E.; Zhang, S.; Bauer, L.; Kobsa, A.; et al. Towards Privacy-Aware Smart Buildings: Capturing, Communicating, and Enforcing Privacy Policies and Preferences. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems Workshops (ICDCSW), Atlanta, GA, USA, 5–8 June 2017; pp. 193–198. [Google Scholar] [CrossRef]
- Raij, A.; Ghosh, A.; Kumar, S.; Srivastava, M. Privacy risks emerging from the adoption of innocuous wearable sensors in the mobile environment. In Proceedings of the ACM CHI Conference on Human Factors in Computing System, Vancouver, BC, Canada, 7–12 May 2011; pp. 11–20. [Google Scholar] [CrossRef]
- Nicolai, T.; Kenn, H. About the relationship between people and discoverable Bluetooth devices in urban environments. In Proceedings of the Mobility Conference 2007—The 4th Int. Conf. Mobile Technology, Applications and Systems, Mobility 2007, Incorporating the 1st Int. Symp. Computer Human Interaction in Mobile Technology, IS-CHI 2007, Singapore, 10–12 September 2007; pp. 72–78. [Google Scholar] [CrossRef]
- Park, J.Y.; Mbata, E.; Nagy, Z. Good to see you again: Capture and recapture method on mobile devices to estimate occupancy profiles. In Proceedings of the BuildSys 2019—The 6th ACM International Conference on Systems for Energy-Efficient Buildings, Cities, and Transportation, New York, NY, USA, 13–14 November 2019; pp. 145–148. [Google Scholar] [CrossRef]
- Yang, J.; Santamouris, M.; Lee, S.E. Review of occupancy sensing systems and occupancy modeling methodologies for the application in institutional buildings. Energy Build. 2016, 121, 344–349. [Google Scholar] [CrossRef]
- Saha, H.; Florita, A.R.; Henze, G.P.; Sarkar, S. Occupancy sensing in buildings: A review of data analytics approaches. Energy Build. 2019, 188–189, 278–285. [Google Scholar] [CrossRef]
- Huchuk, B.; Sanner, S.; O’Brien, W. Comparison of machine learning models for occupancy prediction in residential buildings using connected thermostat data. Build. Environ. 2019, 160, 106177. [Google Scholar] [CrossRef]
- Page, J.; Robinson, D.; Morel, N.; Scartezzini, J.L. A generalised stochastic model for the simulation of occupant presence. Energy Build. 2008, 40, 83–98. [Google Scholar] [CrossRef]
- Mosiman, C.; Henze, G.; Els, H. Development and Application of Schema Based Occupant-Centric Building Performance Metrics. Energies 2021, 14, 3513. [Google Scholar] [CrossRef]
- van Dronkelaar, C.; Dowson, M.; Burman, E.; Spataru, C.; Mumovic, D. A Review of the Energy Performance Gap and Its Underlying Causes in Non-Domestic Buildings. Front. Mech. Eng. 2016, 1, 17. [Google Scholar] [CrossRef] [Green Version]
- Chen, Z.; Jiang, C.; Xie, L. Building occupancy estimation and detection: A review. Energy Build. 2018, 169, 260–270. [Google Scholar] [CrossRef]
- Arvidsson, S.; Gullstrand, M.; Sirmacek, B.; Riveiro, M. Sensor Fusion and Convolutional Neural Networks for Indoor Occupancy Prediction Using Multiple Low-Cost Low-Resolution Heat Sensor Data. Sensors 2021, 21, 1036. [Google Scholar] [CrossRef] [PubMed]
- Kampezidou, S.I.; Ray, A.T.; Duncan, S.; Balchanos, M.G.; Mavris, D.N. Real-time occupancy detection with physics-informed pattern-recognition machines based on limited CO2 and temperature sensors. Energy Build. 2021, 242, 110863. [Google Scholar] [CrossRef]
- Rueda, L.; Agbossou, K.; Cardenas, A.; Henao, N.; Kelouwani, S. A comprehensive review of approaches to building occupancy detection. Build. Environ. 2020, 180, 106966. [Google Scholar] [CrossRef]
- Khan, A.; Plötz, T.; Nicholson, J.; Mellor, S.; Jackson, D.; Ladha, K.; Ladha, C.; Hand, J.; Clarke, J.; Olivier, P. Occupancy monitoring using environmental & context sensors and a hierarchical analysis framework. In Proceedings of the BuildSys ’14: 1st ACM Conference on Embedded Systems for Energy-Efficient Buildings, Memphis, TN, USA, 5–6 November 2014; pp. 90–99. [Google Scholar] [CrossRef]
- Dong, B.; Lam, K.P. Building energy and comfort management through occupant behaviour pattern detection based on a large-scale environmental sensor network. J. Build. Perform. Simul. 2011, 4, 359–369. [Google Scholar] [CrossRef]
- Google Store. Nest Learning Thermostat. Available online: https://store.google.com/us/product/nest_learning_thermostat_3rd_gen (accessed on 2 December 2020).
- Malinick, T.; Wilairat, N.; Holmes, J.; Perry, L. Destined to Disappoint: Programmable Thermostat Savings are Only as Good as the Assumptions about Their Operating Characteristics. In Proceedings of the 2012 ACEEE Summer Study on Energy Efficiency in Buildings, Pacific Grove, CA, USA, 12–17 August 2012; pp. 162–173. [Google Scholar]
- Yang, R.; Newman, M.W. Learning from a learning thermostat. In Proceedings of the UbiComp: Home Heating, Zurich, Switzerland, 8–12 September 2013; p. 93. [Google Scholar] [CrossRef]
- Hernandez, G.; Arias, O.; Buentello, D.; Jin, Y. Smart Nest Thermostat: A Smart Spy in Your Home. In Black Hat USA; 2014; pp. 1–8. Available online: https://scholar.google.com/scholar?as_q=From+today’s+Intranet+of+things+to+a%0A+future+Internet+of+Things%3A+A+wireless-and+mobility-related+view&as_occt=title&hl=en&as_sdt=0%2C31 (accessed on 2 December 2021).
- Albergotti, R. How Nest, designed to keep intruders out of people’s homes, effectively allowed hackers to get in. The Washington Post, 23 April 2019. [Google Scholar]
- Moody, M.; Hunter, A. Exploiting known vulnerabilities of a smart thermostat. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 50–53. [Google Scholar]
- Gulati, M.; Ram, S.S.; Singh, A. An in depth study into using EMI signatures for appliance identification. In Proceedings of the BuildSys 2014—1st ACM Conference on Embedded Systems for Energy-Efficient Buildings, Memphis, TN, USA, 3–6 November 2014; pp. 70–79. [Google Scholar] [CrossRef] [Green Version]
- Gupta, S.; Reynolds, M.S.; Patel, S.N. ElectriSense. In Proceedings of the 12th ACM International Conference on Ubiquitous Computing—Ubicomp ’10, Copenhagen, Denmark, 26–29 September 2010; p. 139. [Google Scholar] [CrossRef]
- Kleiminger, W.; Beckel, C.; Santini, S. Household Occupancy Monitoring Using Electricity Meters. In Proceedings of the 2015 ACM International Joint Conference on Pervasive and Ubiquitous Computing (UbiComp 2015), Osaka, Japan, 7–11 September 2015. [Google Scholar]
- Talla, V.; Hessar, M.; Kellogg, B.; Najafi, A.; Smith, J.R.; Gollakota, S. LoRa Backscatter: Enabling The Vision of Ubiquitous Connectivity. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2017, 1, 1–24. [Google Scholar] [CrossRef]
- Saffari, A.; Hessar, M.; Naderiparizi, S.; Smith, J.R. Battery-Free Wireless Video Streaming Camera System. In Proceedings of the 2019 IEEE International Conference on RFID (RFID), Pisa, Italy, 25–27 September 2019. [Google Scholar] [CrossRef]
- Liu, V.; Parks, A.; Talla, V.; Gollakota, S.; Wetherall, D.; Smith, J.R. Ambient Backscatter: Wireless Communication out of Thin Air. In Proceedings of the ACM SIGCOMM 2013 Conference on SIGCOMM; SIGCOMM ’13; ACM: New York, NY, USA, 2013; pp. 39–50. [Google Scholar] [CrossRef]
- Sample, A.; Yeager, D.; Powledge, P.; Mamishev, A.; Smith, J. Design of an RFID-Based Battery-Free Programmable Sensing Platform. IEEE Trans. Instrum. Meas. 2008, 57, 2608–2615. [Google Scholar] [CrossRef]
- Hessar, M.; Naderiparizi, S.; Wang, Y.; Saffari, A.; Gollakota, S.; Smith, J.R. Wireless Video Streaming for Ultra-low-power Cameras. In Proceedings of the 16th Annual International Conference on Mobile Systems, Applications, and Services, Munich, Germany, 10–15 June 2018. [Google Scholar] [CrossRef]
- Katanbaf, M.; Saffari, A.; Smith, J.R. Receiver Selectivity Limits on Bistatic Backscatter Range. In Proceedings of the 2020 IEEE International Conference on RFID (RFID), Orlando, FL, USA, 28 September–16 October 2020. [Google Scholar] [CrossRef]
- Katanbaf, M.; Jain, V.; Smith, J.R. Relacks: Reliable Backscatter Communication in Indoor Environments. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2020, 4, 1–24. [Google Scholar] [CrossRef]
- Saffari, A. WideScatter: Toward Wide Area Battery-Free Wireless Sensor Networks. Master’s Thesis, University of Washington, Seattle, WA, USA, 2021. [Google Scholar]
- Tan, S.Y.; Saha, H.; Florita, A.R.; Henze, G.P.; Sarkar, S. A flexible framework for building occupancy detection using spatiotemporal pattern networks. In Proceedings of the 2019 American Control Conference (ACC), Philadelphia, PA, USA, 10–12 July 2019; pp. 5884–5889. [Google Scholar] [CrossRef]
- Sarkar, S.; Mukherjee, K.; Jin, X.; Singh, D.S.; Ray, A. Optimization of symbolic feature extraction for pattern classification. Signal Process. 2012, 92, 625–635. [Google Scholar] [CrossRef]
- Tan, S.Y.; Saha, H.; Jacoby, M.; Henze, G.; Sarkar, S. Granger Causality Based Hierarchical Time Series Clustering for State Estimation. IFAC-PapersOnLine 2020, 53, 524–529. [Google Scholar] [CrossRef]
- Saffari, A.; Tan, S.Y.; Katanbaf, M.; Saha, H.; Smith, J.R.; Sarkar, S. Battery-Free Camera Occupancy Detection System. In Proceedings of the 5th International Workshop on Embedded and Mobile Deep Learning; EMDL’21; Association for Computing Machinery: New York, NY, USA, 2021; pp. 13–18. [Google Scholar] [CrossRef]
- Andrews, J.; Kowsika, M.; Vakil, A.; Li, J. A motion induced passive infrared (PIR) sensor for stationary human occupancy detection. In Proceedings of the 2020 IEEE/ION Position, Location and Navigation Symposium (PLANS), Portland, OR, USA, 20–23 April 2020; pp. 1295–1304. [Google Scholar]
- Leech, C.; Raykov, Y.P.; Ozer, E.; Merrett, G.V. Real-time room occupancy estimation with Bayesian machine learning using a single PIR sensor and microcontroller. In Proceedings of the 2017 IEEE Sensors Applications Symposium (SAS), Glassboro, NJ, USA, 13–15 March 2017; pp. 1–6. [Google Scholar]
- Raykov, Y.P.; Ozer, E.; Dasika, G.; Boukouvalas, A.; Little, M.A. Predicting room occupancy with a single passive infrared (PIR) sensor through behavior extraction. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Heidelberg, Germany, 12–16 September 2016; pp. 1016–1027. [Google Scholar]
- Desai, P.; Modi, N. Problems with PIR Sensors in Smart Lighting+Security Solution and Solutions of Problems. In Smart Trends in Computing and Communications; Zhang, Y.D., Mandal, J.K., So-In, C., Thakur, N.V., Eds.; Springer: Singapore, 2020; pp. 481–486. [Google Scholar]
- Gaetani, I.; Hoes, P.J.; Hensen, J.L. Occupant behavior in building energy simulation: Towards a fit-for-purpose modeling strategy. Energy Build. 2016, 121, 188–204. [Google Scholar] [CrossRef]
- Pedregosa, F.; Varoquaux, G.; Gramfort, A.; Michel, V.; Thirion, B.; Grisel, O.; Blondel, M.; Prettenhofer, P.; Weiss, R.; Dubourg, V.; et al. Scikit-learn: Machine Learning in Python. J. Mach. Learn. Res. 2011, 12, 2825–2830. [Google Scholar]
- Seabold, S.; Perktold, J. statsmodels: Econometric and statistical modeling with python. In Proceedings of the 9th Python in Science Conference, Austin, TX, USA, 28 June–3 July 2010. [Google Scholar]
- Brockwell, P.J.; Davis, R.A. Introduction to Time Series and Forecasting; Springer International Publishing: Berlin/Heidelberg, Germany, 2016. [Google Scholar] [CrossRef]
- ARPA-E. SENSOR: Saving Energy Nationwide in Structures with Occupancy Recognition. Available online: https://arpa-e.energy.gov/?q=arpa-e-programs/sensor (accessed on 5 December 2021).
- Panchabikesan, K.; Haghighat, F.; Mankibi, M.E. Data driven occupancy information for energy simulation and energy use assessment in residential buildings. Energy 2021, 218, 119539. [Google Scholar] [CrossRef]
- Elsts, A.; Fafoutis, X.; Woznowski, P.; Tonkin, E.; Oikonomou, G.; Piechocki, R.; Craddock, I. Enabling Healthcare in Smart Homes: The SPHERE IoT Network Infrastructure. IEEE Commun. Mag. 2018, 56, 164–170. [Google Scholar] [CrossRef]
- Ellis, R.J.; Ng, Y.S.; Zhu, S.; Tan, D.M.; Anderson, B.; Schlaug, G.; Wang, Y. A Validated Smartphone-Based Assessment of Gait and Gait Variability in Parkinson’s Disease. PLoS ONE 2015, 10, 1–22. [Google Scholar] [CrossRef] [Green Version]
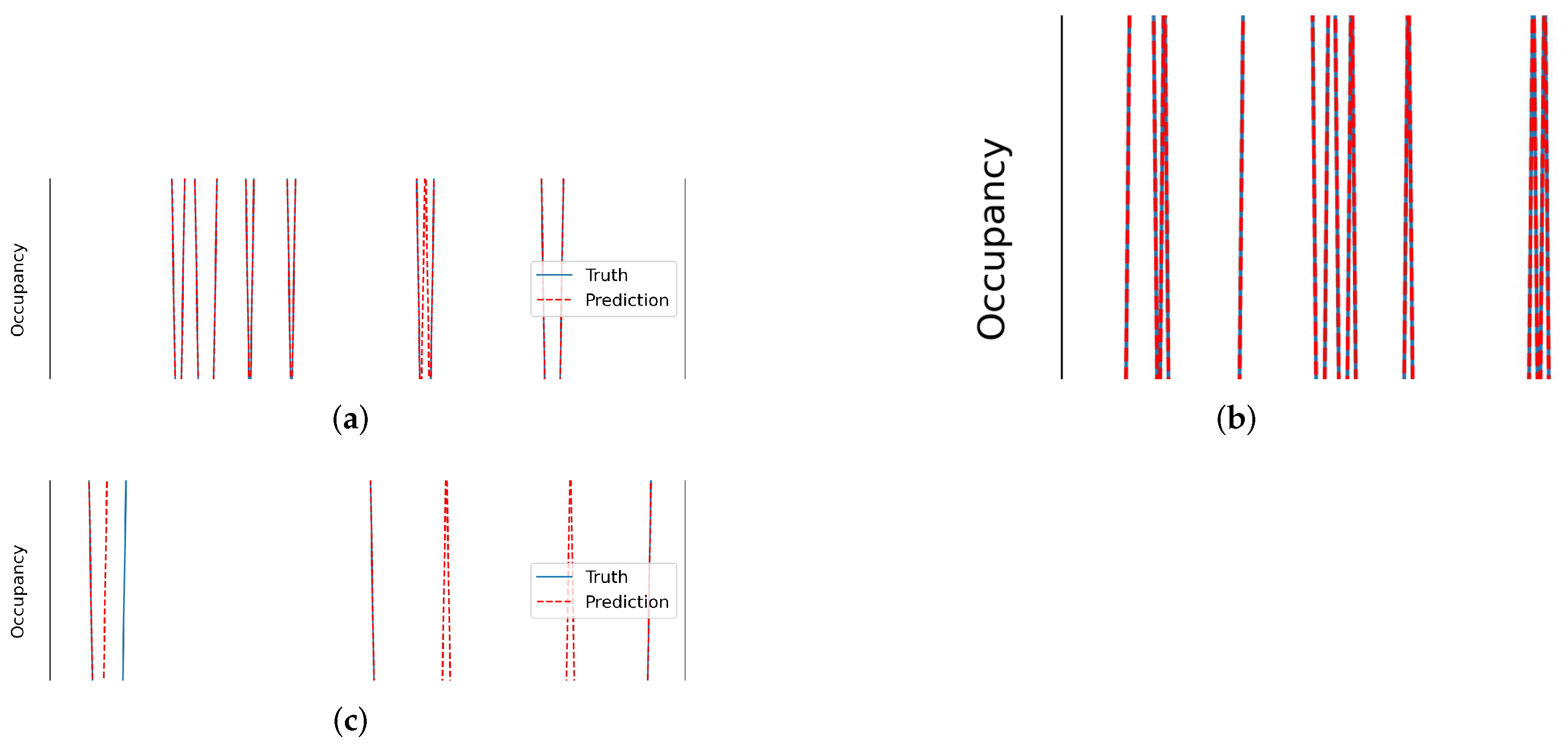
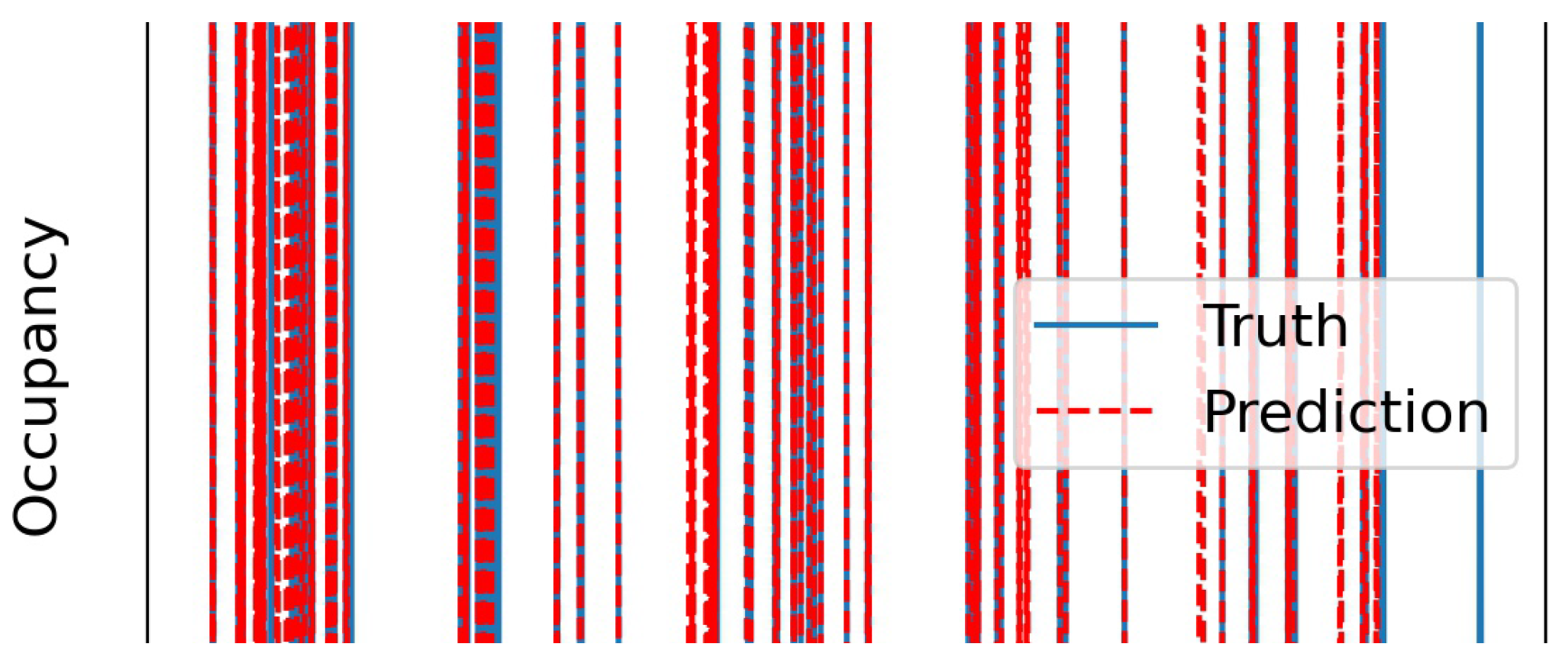
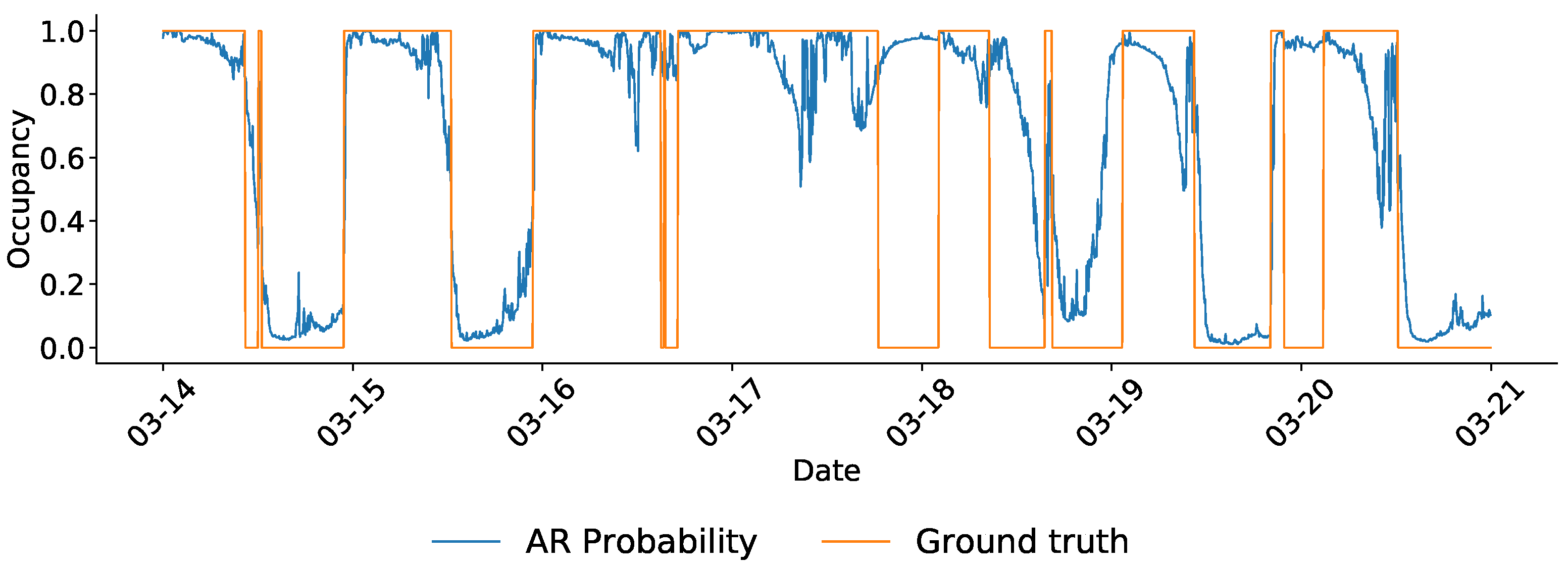
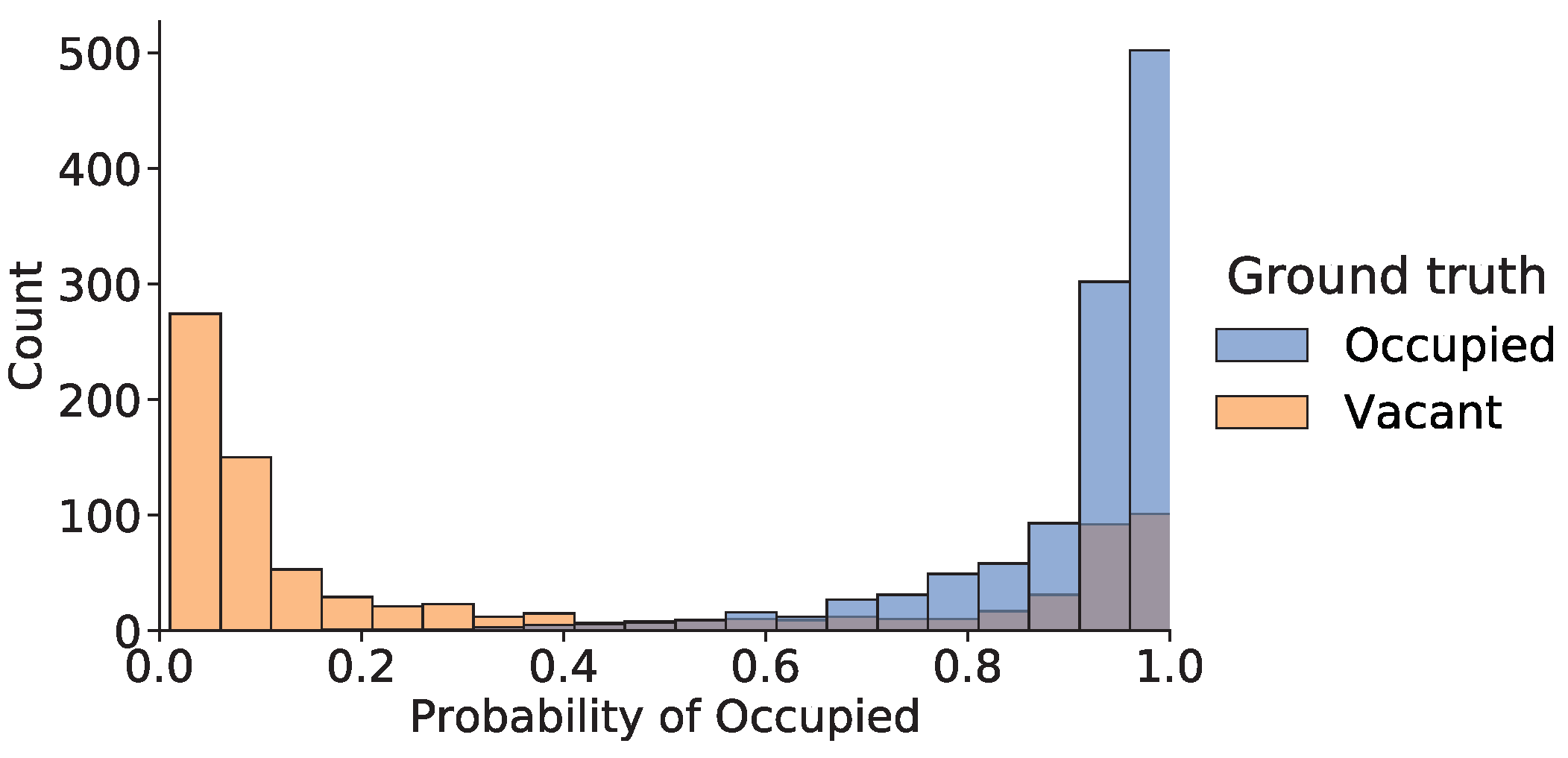
| Variable | Coef. | Std. Error | z | p | [0.025 | 0.975] |
|---|---|---|---|---|---|---|
| Intercept | −4.9298 | 0.169 | −29.100 | 0.000 | −5.262 | −4.598 |
| Audio | 4.3068 | 0.160 | 26.838 | 0.000 | 3.992 | 4.621 |
| Image | 2.5030 | 0.217 | 11.554 | 0.000 | 2.078 | 2.928 |
| CO | −1.0129 | 0.298 | −3.401 | 0.001 | −1.597 | −0.429 |
| Illuminance | 0.7804 | 0.257 | 3.042 | 0.002 | 0.278 | 1.283 |
| Relative humidity | 0.6870 | 0.180 | 3.807 | 0.000 | 0.333 | 1.041 |
| Temperature | 1.5155 | 0.199 | 7.616 | 0.000 | 1.125 | 1.905 |
| sin(hr) | 0.6070 | 0.051 | 11.821 | 0.000 | 0.506 | 0.708 |
| cos(hr) | 1.0737 | 0.057 | 18.762 | 0.000 | 0.962 | 1.186 |
| Weekday | −0.2659 | 0.074 | −3.614 | 0.000 | −0.410 | −0.122 |
| Lag 1 | 5.4175 | 0.108 | 50.070 | 0.000 | 5.205 | 5.630 |
| Lag 2 | 0.3172 | 0.134 | 2.363 | 0.018 | 0.054 | 0.580 |
| Lag 3 | 0.1480 | 0.147 | 1.009 | 0.313 | −0.139 | 0.436 |
| Lag 4 | 0.0314 | 0.125 | 0.251 | 0.802 | −0.214 | 0.277 |
| Lag 5 | 0 | − | − | − | − | − |
| Lag 6 | 0 | − | − | − | − | − |
| Lag 7 | 0 | − | − | − | − | − |
| Lag 8 | 0.0097 | 0.086 | 0.113 | 0.910 | −0.159 | 0.179 |
| Idle Power | Sensing Energy | Comm. Energy | Solar-Powered Update Rate | |
|---|---|---|---|---|
| (W) | (J) | (J) | 2 in Panel | 17 in Panel |
| 25 | 25 | 14 | 1 s | 0.2 s |
| Locations | Accuracy (%) | F-Score |
|---|---|---|
| Living Room (LR) | 99.21 | 0.9919 |
| Kitchen (K) | 99.30 | 0.9930 |
| Lab | 95.08 | 0.9509 |
| LR & K (5-days) | 95.76 | 0.9577 |
| Accuracy | F | F | ||||
|---|---|---|---|---|---|---|
| Home | Mean | Std dev. | Mean | Std dev. | Mean | Std dev. |
| H1 | 84% | 0.07 | 0.91 | 0.04 | 0.09 | 0.23 |
| H2 | 83% | 0.07 | 0.85 | 0.06 | 0.80 | 0.09 |
| H3 | 87% | 0.05 | 0.93 | 0.03 | 0.13 | 0.12 |
| H5 | 82% | 0.22 | 0.89 | 0.14 | 0.02 | 0.03 |
| H6 | 56% | 0.19 | 0.64 | 0.19 | 0.42 | 0.15 |
| Mean | 78% | 0.13 | 0.84 | 0.12 | 0.29 | 0.32 |
| Classifier | Accuracy | F | F | TPR | FPR | TNR | FNR |
|---|---|---|---|---|---|---|---|
| ARXLR | 78% | 0.85 | 0.26 | 96% | 76% | 24% | 4% |
| Minority-vote | 51% | 0.46 | 0.46 | 31% | 9% | 91% | 67% |
| Non-probabilistic | 71% | 0.81 | 0.14 | 97% | 91% | 9% | 3% |
| Ground truth | 96% | 0.97 | 0.83 | 97% | 20% | 80% | 3% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jacoby, M.; Tan, S.Y.; Katanbaf, M.; Saffari, A.; Saha, H.; Kapetanovic, Z.; Garland, J.; Florita, A.; Henze, G.; Sarkar, S.; et al. WHISPER: Wireless Home Identification and Sensing Platform for Energy Reduction. J. Sens. Actuator Netw. 2021, 10, 71. https://doi.org/10.3390/jsan10040071
Jacoby M, Tan SY, Katanbaf M, Saffari A, Saha H, Kapetanovic Z, Garland J, Florita A, Henze G, Sarkar S, et al. WHISPER: Wireless Home Identification and Sensing Platform for Energy Reduction. Journal of Sensor and Actuator Networks. 2021; 10(4):71. https://doi.org/10.3390/jsan10040071
Chicago/Turabian StyleJacoby, Margarite, Sin Yong Tan, Mohamad Katanbaf, Ali Saffari, Homagni Saha, Zerina Kapetanovic, Jasmine Garland, Anthony Florita, Gregor Henze, Soumik Sarkar, and et al. 2021. "WHISPER: Wireless Home Identification and Sensing Platform for Energy Reduction" Journal of Sensor and Actuator Networks 10, no. 4: 71. https://doi.org/10.3390/jsan10040071
APA StyleJacoby, M., Tan, S. Y., Katanbaf, M., Saffari, A., Saha, H., Kapetanovic, Z., Garland, J., Florita, A., Henze, G., Sarkar, S., & Smith, J. (2021). WHISPER: Wireless Home Identification and Sensing Platform for Energy Reduction. Journal of Sensor and Actuator Networks, 10(4), 71. https://doi.org/10.3390/jsan10040071






