Abstract
Wireless Sensor Networks (WSNs) are used in many industrial and consumer applications that are increasingly gaining impact in our day to day lives. Still great efforts are needed towards the definition of methodologies for their effective management. One big issue is themonitoring of the network status, which requires the definition of the performance indicators and methodologies and should be accurate and not intrusive at the same time. In this paper, we present a new process for the monitoring of the physical layer in WSNs making use of a completely passive methodology. From data sniffed by external nodes, we first estimate the position of the nodes by applying the Weighted Least Squares (WLS) to the method of indirect observations. The resulting node positions are then used to estimate the status of the communication links using the most appropriate propagation model. We performed a significant number of measurements on the field in both indoor and outdoor environments. From the experiments, we were able to achieve an accurate estimation of the channel links status with an average error lower than 1 dB, which is around 5 dB lower than the error introduced without the application of the proposed method.
1. Introduction
Recent advances in micro-electro-mechanical systems technology, wireless communications and digital electronics have enabled the development of low-cost, low-power, multifunctional sensor nodes that are small in size and communicate untethered in short distances. These tiny sensor nodes, which consist of sensing, data processing and communicating components, leverage the idea of sensor networks based on collaborative effort of a large number of nodes [1]. Hence, the wireless sensors networks (WSNs) are used in many scenarios [2] and for a lot of applications, such as home automation [3], health care [4], remote control [5], industrial control [6], environmental monitoring [7], intelligent transportation systems [8], etc.
WSNs also represent a key component of the Internet of Things (IoT), which is a novel paradigm that is rapidly gaining ground in the scenario of modern wireless telecommunications. The basic idea of this concept is the pervasive presence around us of a variety of things or objects, tags, sensors, actuators, mobile phones, etc., which are able to interact with each other and cooperate with their neighbors to reach common goals [9]. Indeed, sensor networks will also play a crucial role in the IoT because they can cooperate with RFID systems to better track the status of things, i.e., their location, temperature, movements, etc. As such, they can augment the awareness of a certain environment and thus act as a further bridge between the physical and the digital worlds. Today, most of commercial wireless sensor network solutions are based on the IEEE 802.15.4 standard, which defines the physical and MAC layers for low-power, low bit rate communications in wireless personal area networks (WPANs) [10].
If WSNs are sufficiently mature to be used in several applications, as previously discussed, still great efforts are needed towards the definition of methodologies and the design of tools to support their deployment and management. Indeed, deployment of wireless networks in realistic scenarios, often represented by a combination of outdoor and indoor areas, requires the analysis and the modeling of the wireless channels to optimally place the nodes so as to maximize the network lifetime while achieving the WSN application goals (e.g., sensing the status of the environment); it also requires the identification of the best roles of each node (e.g., how many routing nodes to run and which configuration to be set up). After deployment, network management requires methodologies and tools to support the monitoring and troubleshooting during the whole network life. Key to all these activities is the definition of the performance indicators, which should be able to provide a general view of the network status and to easily highlight the major issues, and the techniques to perform the relevant measures, which should be accurate and not intrusive at the same time. On the basis of the availability of the information related to the network channel links, it is possible to improve the network throughput [11], lifetime [12], packet reception rate [13], fault tolerance [14]. Many are the works focused on performance monitoring for WSNs [15,16,17,18,19,20,21,22,23,24,25,26]. In [15], the Rost et al. focus on the in-band monitoring approach so that diagnosis packets are transmitted on the same band used for the WSN communications, whereas, in [20], Cheng et al. propose an out-band monitoring framework so that the diagnosis packets are sent in a separate band with respect to one used by the WSN. In [25], Chen et al. focus on a passive analysis and propose a set of tools to analyse the packets captured by a sniffer.
As it will be clear from the analysis of the state of the art in next section, one of the major problems in the proposed methodologies is their intrusiveness. It is due to the need for the nodes to measure the received signal power and to generate and transmit packets conveying the measurement results to the network. In general, the intrusiveness brings to an increase in both network traffic and signal/data processing. This drawback is extremely undesirable since the nodes are mostly battery-powered and any additional energy consumption could compromise the network lifetime. On the basis of these considerations, in this paper we aim at evaluating the suitability of a passive method for the estimation of the physical layer performance in a wireless sensor network. Herein, by passive we mean that the nodes of the WSN are not involved in the monitoring process, and the measurements are performed by eternal nodes that carry out a series of observations on the wireless channels concerning the transmissions of the network nodes. These observations are then used to estimate the status of the wireless links in the network. The major contributions of this paper are the followings:
- we designed a new process for the monitoring of the physical layer in WSNs making use of a completely passive methodology. From data sniffed by external nodes, we first estimate the position of the nodes in the WSN by applying the Weighted Least Squares (WLS) to the method of indirect observations. The resulting information on the nodes position is then used to estimate the status of the communication links among the network nodes;
- we performed a significant number of measurements on the field to evaluate the accuracy of the proposed approach in both indoor and outdoor environments. In the experiments, the proposed method achieved an accurate estimation of the channel links status so that we could acquire the status of the channel links with an average error lower than 1 dB, which is around 5 dB lower than the error introduced without the application of the proposed method.
The structure of the paper is the following. In Section 2 we review past works related to performance monitoring in WSNs. In Section 3.1 we define the multilateration problem in estimating the position of the nodes in the network and describe the weighted least squares algorithm applied to the method of indirect observations. In Section 4 we present the proposed approach for the passive monitoring of the WSN physical layer and in Section 5 we provide the analysis of the effectiveness of the proposed approach through experiments in realistic scenarios. Final conclusions are drawn in Section 6.
2. State of the Art
In the recent years, many researchers have considered the problem of performance monitoring in WSNs under different requirements and objectives. The main proposed approaches can be classified into the categories of active and passive categories, with some others that are in the middle.
To the first category belongs Memento [15]. It makes use of an in-band monitoring approach since it allows nodes to transmit additional diagnosis packets in the same channel of the data packets. Three broad classes of information are introduced: failure detection to inform the user about failed nodes, symptom alerts to proactively inform the user about symptoms of impending failure or reporting on performance, and ex-post facto inspection to inform the user of the timeline of the events to help infer why a failure or symptom occurred. According to this approach, it is required that each node uses its portion of memory and computing capacity to create the new monitoring messages. Apart from consuming the bandwidth of the network with the new message, the main problem of this approach is the use of the nodes computing and memory capacities. Similarly, Sympathy [16] is an active in-band monitoring tool that has defined some metrics to enable failure detection and an algorithm to find the potential causes. However, due to limited processing power at the nodes and the limited bandwidth of the network, it is very likely that the introduced diagnosis overhead interferes with the operation of the network itself. SNMS [17] is another active in-band monitoring approach. Its innovation is that SNMS generates network traffic only in response to direct human actions and not during the steady state. With respect to the previous ones, it then limits the usage of the network capacity and node computational capacities; however, it still needs a considerable amount of nodes memory. Compared with the predecessors in-band monitoring algorithms, DiMo [18] performs some processing locally at the nodes involved in the measurements so that they only report to the sink if a node is potentially failed. This greatly reduces the transmission overhead and energy consumption.
In the middle between the active and passive categories, there are some hybrid methods that make use of the two types of approaches. In the active approach, a tag is introduced on all packets and a sniffer is used to capture the traffic and analyze the tags. In the passive approach, an out-of-band infrastructure is used for the monitoring, where no additional packets are generated but the computing capacity of the nodes is used for the analysis of the packets. DiF [26] is a Diagnosis Framework for WSN that introduces packet tags. The purpose of the framework is to minimize the effort spent on developing diagnosis tools for variety of WSN, to speed up development of WSN, and to simplify diagnosis and verification of network deployment. It is a very effective method, but it is very complex to be implemented for large networks. In [19] the researchers propose DSN: a non-permanent, wireless cable replacement. It makes use of an out-band monitoring approach and does not disturb the target WSN more than the traditional cable-based approach. The DSN nodes are attached to WSN target devices via a programming and debugging cable and form an autonomous network. DSN nodes provide two radios. The first radio (DSN radio) is used to form a wireless network among the deployment support nodes, while the second radio (WSN radio) is used to overhear the traffic of the sensor network. SNIF [24] is a general framework for passive inspection of multi-hop sensor networks to detect problems related to individual nodes, wireless links, paths and global problems. To overhear the traffic of multi-hop networks, multiple radios are needed, forming a distributed network sniffer. SNIF uses a wireless network of DSN. This approach works indeed very well in small size networks. However, as soon as the network size increases, this approach has the problem of scalability.
Differently from the previously described algorithms, passive diagnosis plants sniffers around the network to overhear the packets exchanged between nodes. The exchanged packets are then merged together to form an overview of the network operations. This approach removes the above limitations of active/hybrid inspection: no instrumentation of sensor nodes is required and sensor network resources are not used. The family of passive monitoring can be split into two subcategories: on-line and off-line. The first performs a real time communication among passive nodes (sniffers) and diagnosis servers using an out-of-band approach with either wired or wireless connections. An event log is generated, which may be retrieved in off-line mode for further diagnosis. The methods of the second subcategory are cheaper and have higher scalability and flexibility, because they do not need any infrastructure for real-time communication among the passive nodes. JIGSAW [20] is an on-line monitoring framework based on a monitoring infrastructure that overlays a wireless network. The monitors in turn feed a centralized system that uses this data to produce a precisely synchronized global picture of all physical, link-layer, network-layer and transport-layer activity. This method can be used for large networks, but it needs wired links among the monitors, making it neither scalable nor flexible. SNDS [23] is another on-line distributed monitoring and protocol analysis system for complex WSNs. It is based on passive sniffers co-deployed with the target WSN, which are inter-connected via Ethernet cables. Sniffers are mainly used to monitor a particular channel and to transmit the data to the service program. SNDS solves the problem of intrusiveness using the sniffers, but the sniffer infrastructure is cabled (Ethernet) so for large WSN this is a main problem. To the off-line subcategory belong EMSTAR [21] and LiveNet [25]. EMSTAR generates an event log that can be evaluated off-line towards fault isolation, fault tolerance, system visibility, in-field debugging, and resource sharing across multiple applications. LiveNet [25] is a set of tools and analysis methods for reconstructing the complex behavior of a deployed sensor network in passive mode. It is based on the use of multiple passive packet sniffers co-located with the network, which collect packet traces that are merged to form a global picture of the network operations.
Although a passive monitoring infrastructure can be expensive due to the need for additional components, we believe that in many cases it is the only way to effectively monitor the network. Our approach is similar to that of LiveNet, since we also propose a completely passive monitoring system that relies on sniffers to capture the network packets and on a post-processing module to analyze off-line the performance. Within this general approach, we propose a novel mechanism that allows for estimating the physical link status other than the network layer status without any collaboration of the WSN nodes. This is an additional feature in this category of methods that improves their potentialities.
3. Estimation of Node Position Using Indirect Observations
In this section, we review the basic theory that is exploited in the proposed algorithm described in Section 4. In the first subsection, we summarize the multilateration problem, and in the second subsection, we describe the Weighted Least Squares (WLS) applied to the method of indirect observations.
3.1. Multilateration Problem
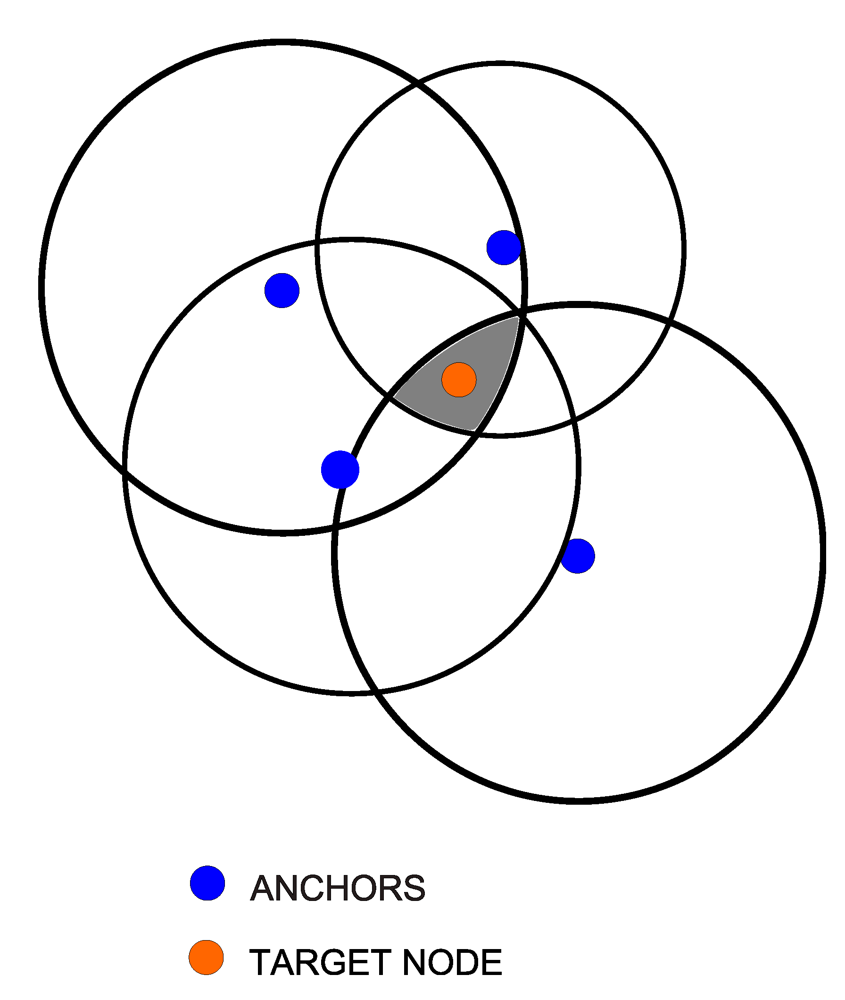
The lateration problem consists in determining the position of a node (i.e., the target node) in the space based on its distance from other nodes with known positions (i.e., the anchors) [27]. To address the lateration problem in a plane, three anchors are needed usually. Using the anchor positions and the distances, the target node position has to be at the intersection of three circles centered at the anchors. A common issue is that distance measurements are often imperfect and the intersection of these circles does not, in general, result in a single point. To overcome these imperfections, distance measurements from more than three anchors can be used (the higher the number of measurements the better), resulting in a multilateration problem [28,29,30,31]. Figure 1 shows a representative scenario with four anchors, where the distance measurements brought to the grey area represent the intersection of the circles as well as the area within which the target node is expected to be located.
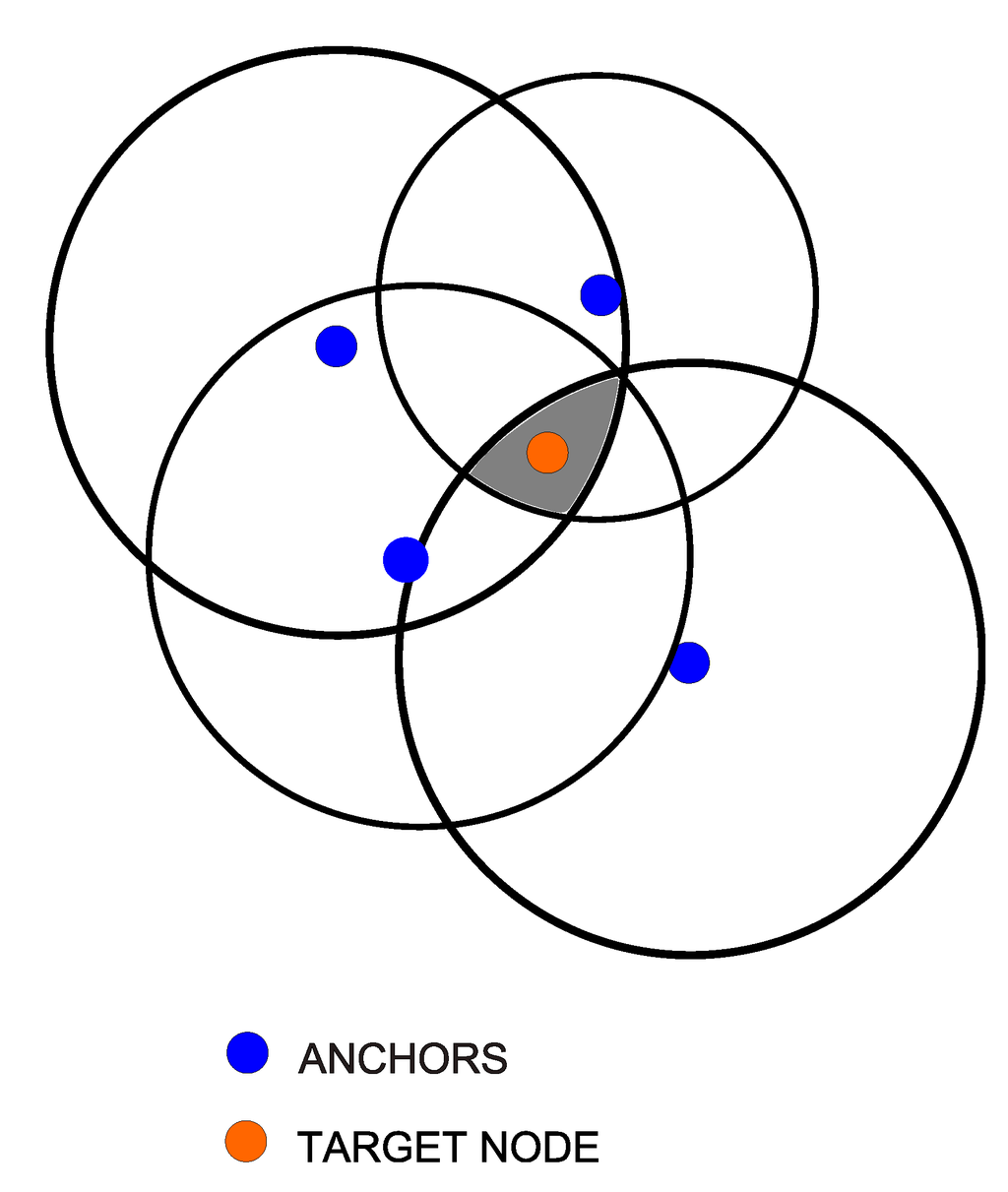
Figure 1.
Example of a multilateration problem. The grey area is obtained as the intersection of the three circles centered at the anchors and is where the target node is expected to be located.
Figure 1.
Example of a multilateration problem. The grey area is obtained as the intersection of the three circles centered at the anchors and is where the target node is expected to be located.
The multilateration problem can then be written as follow
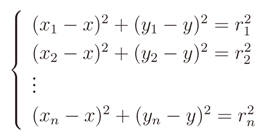 where n is the number of anchors, vector p = (x, y) is the position of the target node, vectors ai = (xi, yi) are the position of anchor i, and ri is the distance measured from anchor i to the target node. This system can be written with the following matrix equation
where n is the number of anchors, vector p = (x, y) is the position of the target node, vectors ai = (xi, yi) are the position of anchor i, and ri is the distance measured from anchor i to the target node. This system can be written with the following matrix equation
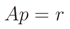
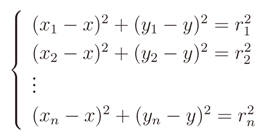
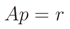
The resulting system is not linear, but it is possible to linearize it by subtracting the i-th equation from all the other n - 1. The new system is the following
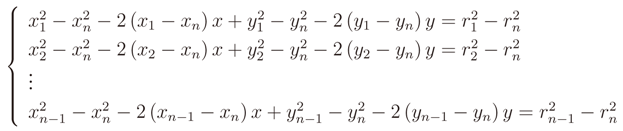
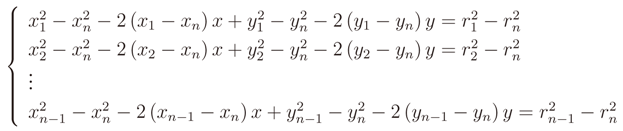
Then it is possible to finally write the following matrix equation
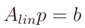
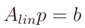
This problem is over-determined so that to find the solution the Ordinary Least Squares (OLS) can be used [32]. In the ideal case where all measures are perfect, all circles intersect at a single point, but in the real case the measures are affected by error and the circles intersect at more than one point. These points identify an area of solution (grey area in Figure 1). By the OLS, we obtain the solution that minimizes the sum of the squared distance. The precision of this solution is given by the residual
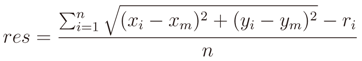 where pm = (xm, ym) is the resulting estimated target node position.
where pm = (xm, ym) is the resulting estimated target node position.
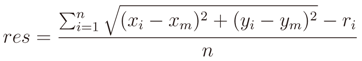
3.2. WLS Applied to the Method of Indirect Observations
The WLS applied to the method of indirect observations is usually adopted in topography science to correct the estimation of positions of nodes in the space [33,34]. The scope is not to find a direct solution in terms of coordinates (x, y), but to estimate corrections δx, δy to compensate an initial estimate (xm, ym) of the target node position. The adopted approach is that of minimizing the probability to obtain the resulting residual by moving the estimated position of δx, δy. The method can be iterated until (δx, δy) are negligible, so that the method converges to a solution. Such a minimization results in the application of the WLS to indirect observations, represented by the measured distances between the anchors and the target node. These are assumed to be indirect, since at every iteration, new distances that represent the indirect observations at each application of the WLS are computed [35,36]. In the WLS algorithm, the weighting matrix is used so that more importance is given to the more reliable observations. Additionally, these weights are updated through an iterative procedure to increase the overall accuracy.
Typically the problem is oversized, because there are a lot of observations available, and the matrix A in Equation (2) is (n × s) with the number of equations (called observations) greater than the number of unknown values (n > s; in the planar case that we are considering, is s = 2). There is the need to start with an initial location estimation (xm, ym), which is obtained by making use of the OLS as explained in the previous subsection. The major difference between the WLS and the OLS methods is that the first uses a weighting matrix to give much importance to the more reliable observations for the benefit of the overall accuracy. On the contrary, the OLS method does not use any weight and all the observations are given with the same importance. Let 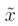 represent the obtained solution and
represent the obtained solution and 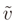 be the residual vector (the set of measures are affected by errors). We can write the following matrix equation
be the residual vector (the set of measures are affected by errors). We can write the following matrix equation
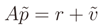
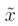 represent the obtained solution and
represent the obtained solution and 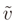 be the residual vector (the set of measures are affected by errors). We can write the following matrix equation
be the residual vector (the set of measures are affected by errors). We can write the following matrix equation
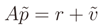
Then the model has n observations and n + s unknown values: s for vector 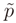 and n for residual vector
and n for residual vector 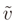 . Hence, the system is oversized and the possible solutions are ∞n.
. Hence, the system is oversized and the possible solutions are ∞n.
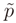 and n for residual vector
and n for residual vector 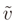 . Hence, the system is oversized and the possible solutions are ∞n.
. Hence, the system is oversized and the possible solutions are ∞n.We now assume that the errors are uncorrelated with each other and with the independent variables and have equal variance. It means that we assume the independence of observations, which is justified by the use of the same device (or devices with the same characteristics to measure the distances from anchors to the target node). We also assume that the residual is governed by the following probability density function
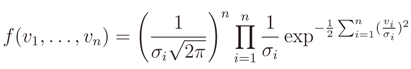
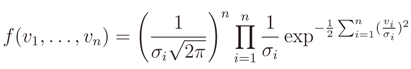
We then change the approach in finding the solution to Equation (2) so that we aim at minimizing the probability in Equation (7), which results in minimizing the following
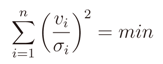
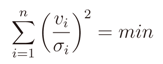
It is possible to insert a constant σ0
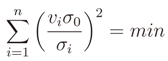
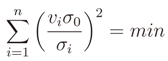
which brings to the application of the WLS where the weights are
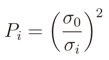
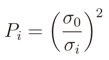
and where the final matrix system is


At this point, it is frequent to encounter the problem of equations that are not linear, which is an issue for the application of the WLS. This problem is also present in the case studied by this article. To address this problem, we linearize the functions in matrix Ap around 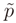 where it is derivable, and we substitute the function by its linearization at this point. We now skip all the next mathematical passages and we give the final solution. Let A∂ represent the partial derivates of Ap in dx and dy computed at
where it is derivable, and we substitute the function by its linearization at this point. We now skip all the next mathematical passages and we give the final solution. Let A∂ represent the partial derivates of Ap in dx and dy computed at 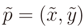 . After the linearization we obtain the bound problem
. After the linearization we obtain the bound problem
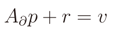
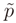 where it is derivable, and we substitute the function by its linearization at this point. We now skip all the next mathematical passages and we give the final solution. Let A∂ represent the partial derivates of Ap in dx and dy computed at
where it is derivable, and we substitute the function by its linearization at this point. We now skip all the next mathematical passages and we give the final solution. Let A∂ represent the partial derivates of Ap in dx and dy computed at 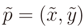 . After the linearization we obtain the bound problem
. After the linearization we obtain the bound problem
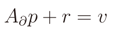
So, by Equations (11) and (12), we can build the system that, once resolved, represents the final solution
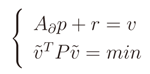
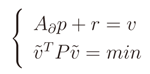
The final solution obtained after the resolution of system in Equation (13) is then the following
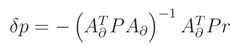
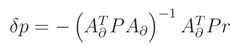
Essentially, with this method, it is possible to spread the error of the measures, to minimize the residual generated by the solution, so that the method provides a more accurate solution with respect to the initial OLS estimation [37]. It is also possible to estimate the precision of the solution. Indeed, for the law of variance propagation, the variance of δp can be easily computed from the square matrix H = (AT∂ P A∂)−1: the values in the diagonal hii correspond to the variance of δp multiplied by a factor scale σ20.
Note that at any iteration we need to estimate the new variances of residuals σi, which are obtained from the vector of residuals of the previous iterations. The value σ02 at each step is instead computed by the maximum likelihood criterion
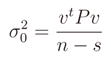
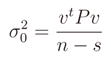
The described method can be iterated until vector δp is lower than a given threshold (which is set according to the desired target application).
4. Proposed Method for Physical Layer Performance Estimation
As already mentioned in the introduction, in this paper we aim at evaluating the suitability of a passive method for the estimation of the physical layer performance in a wireless sensor network. Herein, by passive we mean that the nodes of a network that are already installed and active in a given environment are not involved in the monitoring process. Instead, the measurements are performed by the sniffer nodes that carry out a series of observation on the wireless channels concerning the network nodes transmissions. Then, from these measurements, estimations on the wireless links status among the operating nodes are performed.
The rationale behind the proposed method is that the WSN nodes are mostly battery-powered and any additional activity, such as receiving signal power measurements needed in an active scenario, could compromise the network performance and lifetime. These nodes would not only need to make the measurements of the power but also perform some operations (to compute the average values for instance) and send the relevant data to a sink with additional energy consumption. Furthermore, in the current WSN market, the node prices are kept as low as possible by limiting the computational and memory capabilities, which prevents implementing most of the monitoring tasks in the nodes themselves using the available hardware.
4.1. Reference Scenario
We consider the scenario of an operating WSN of which we are interested in estimating the channel status. We assume that we cannot perform any measurement at these nodes and that the positions of these nodes are unknown; for this reason these are called blind nodes. Such a set of nodes is defined as the set B = {1, ...,Bk, ...,BNB}. The nodes are operating and are connected in a mesh structure according to the specific communication technologies adopted. We may or may not know the graph of the connections among the nodes, but this is not an issue for our problem.
Our objective is to estimate the power of the transmission signal of node Bk as seen by node Bj, which we call BTjk. To this we make use of anchor nodes with known position. The set of anchor nodes is defined as the set A = {1, ...,Ai, ...,ANA}. These are the sniffers used in our measurements. Indeed, we may have only one sniffer that changes its position over time and makes several measurement sessions or many sniffers that make measurements in parallel. Note that each sniffer Ai performs measurements of the signal coming from every blind node. The signal transmission measurements performed by the anchors are represented by TAik. For every i, we expect to have a measure for any blind node k, with k = 1, ...,NB; however, due to the distance and the presence of occluding objects, some of these measures can be set to zero, meaning that the anchor has not been able to detect any signal from blind node k. The measurement TAik is usually obtained as the average power measured for a set of packets received during the sniffing time, and its accuracy clearly depends on the length of the observation time and the transmission frequency of blind node k. Specifically, herein without loss of generality, we refer to the RSSI (Received Signal Strength Indication) measures.
A key part in the proposed approach is the estimation of the distances between the blind nodes and between the blind nodes and the anchor nodes. In line with the notation used for the signal power, we refer to these two entities as DBik and DAik, respectively.
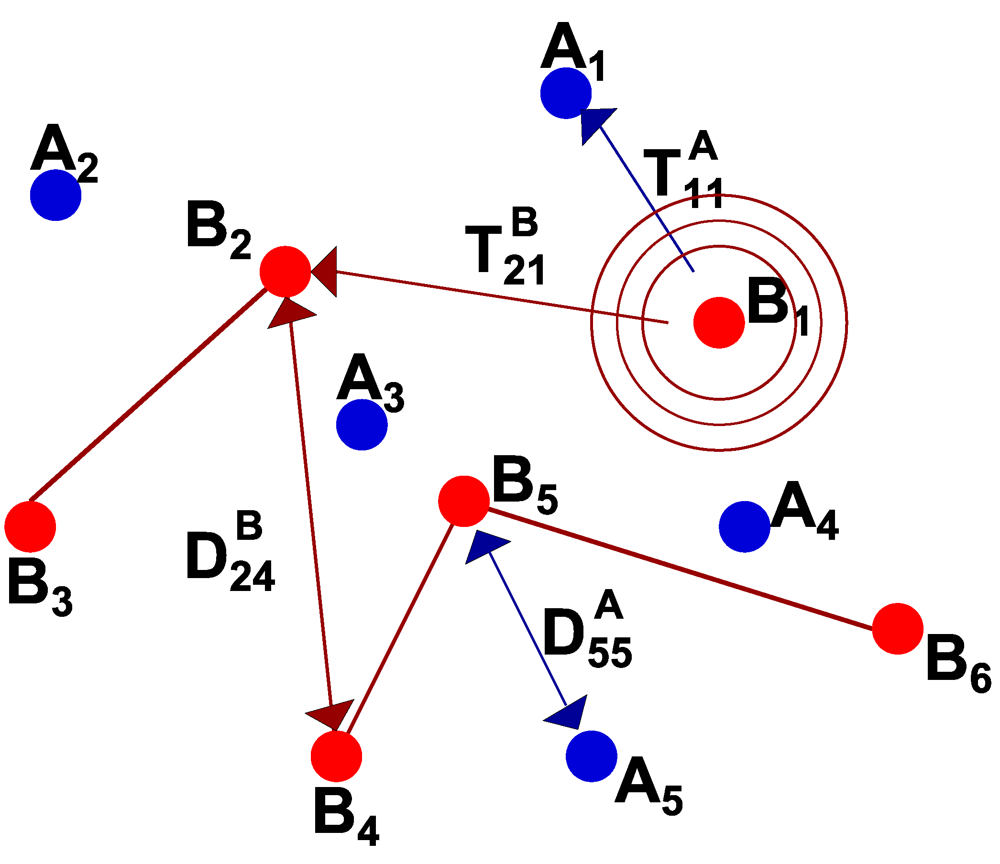
Figure 2 shows an exemplary scenario where the number of anchor and blind nodes is 5 and 6, respectively. In this figure, we represent the power and distance only for some couples of nodes for the sake of clarity, and the same applies to all other figures.
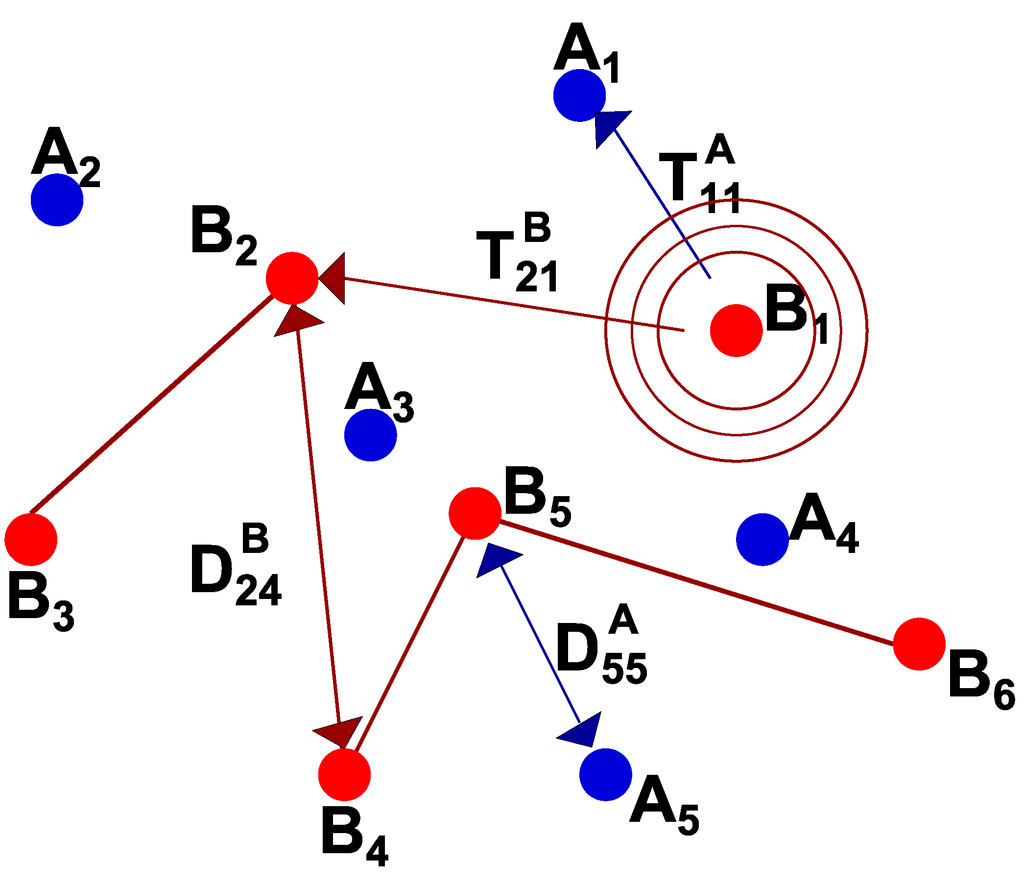
Figure 2.
Reference scenario with 5 anchors and 6 blind nodes.
Figure 2.
Reference scenario with 5 anchors and 6 blind nodes.
4.2. Proposed Power Estimation Algorithm
The method we propose herein is straightforward and is based on estimating the position of blind nodes from the measurements performed by the anchors and using these estimates to infer the channel power for the entire network links. We use the passive device to store the packets exchanged on the network. We analyze the MAC layer to evaluate the RSSI field, which is shown in Figure 3. The RSSI represents information about the power of the signal received by the end-device. Hence, knowing the environment and the model that describes the propagation of the signal, we can easily extract information about the geometric relationships among the blind nodes and the anchors. We use this information to resolve an OLS problem and obtain an initial estimation of blind node positions. This step is necessary to have the input to apply the algorithm proposed in Section 3.2. Now we compute all the coefficients and linearize the function, with the objective to write the bound problem, which is described in Equation (13). Making use of the solution Equation (14), we obtain the estimation of the corrections to be applied to the initial position of each blind node. We are now able to perform an iteration of the method using the new position (the initial position obtained by algorithm OLS with the computed corrections) as the new input. The criterion is iterated until the correction is smaller than a threshold selected a priori in accordance to the desired accuracy. When the algorithm terminates for every blind node, we obtain all the position estimations for the devices. Hence, we easily evaluate the relative distance among the blind nodes, and in accordance to the environment, we apply the appropriate propagation model to estimate the transmission power among all the blind nodes. For more details, see Figure 4.
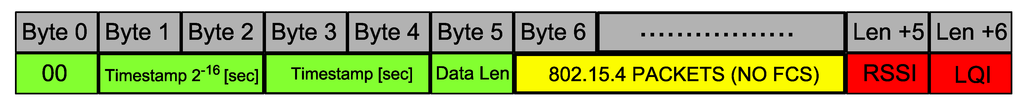
Figure 3.
IEEE 802.15.4 packet.
Figure 3.
IEEE 802.15.4 packet.
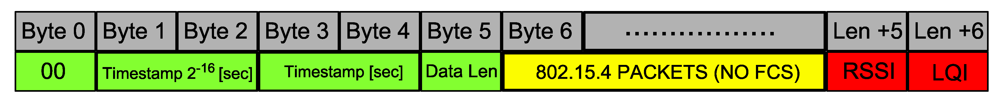
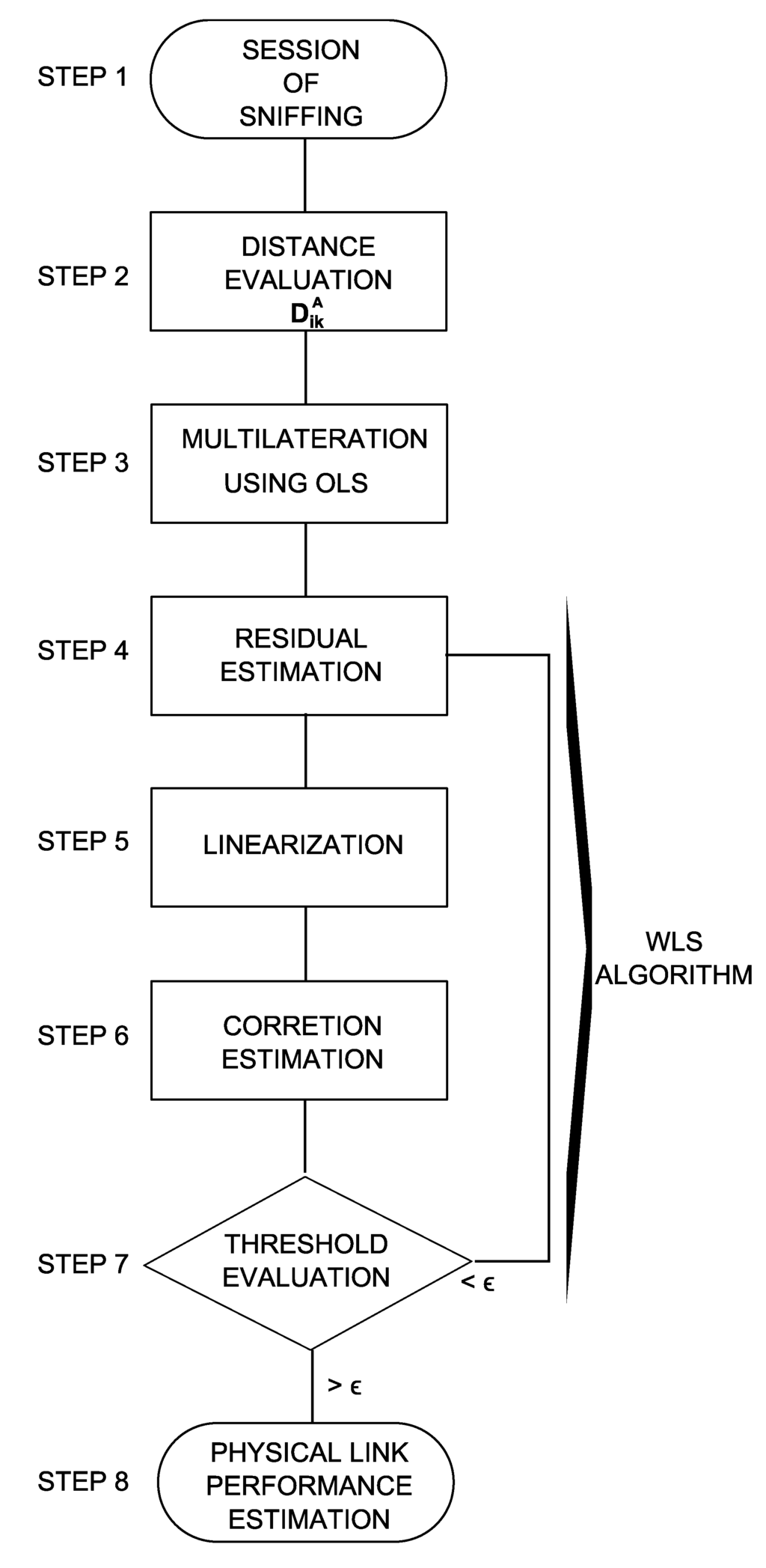
Figure 4.
Flow diagram for the proposed algorithm.
Figure 4.
Flow diagram for the proposed algorithm.
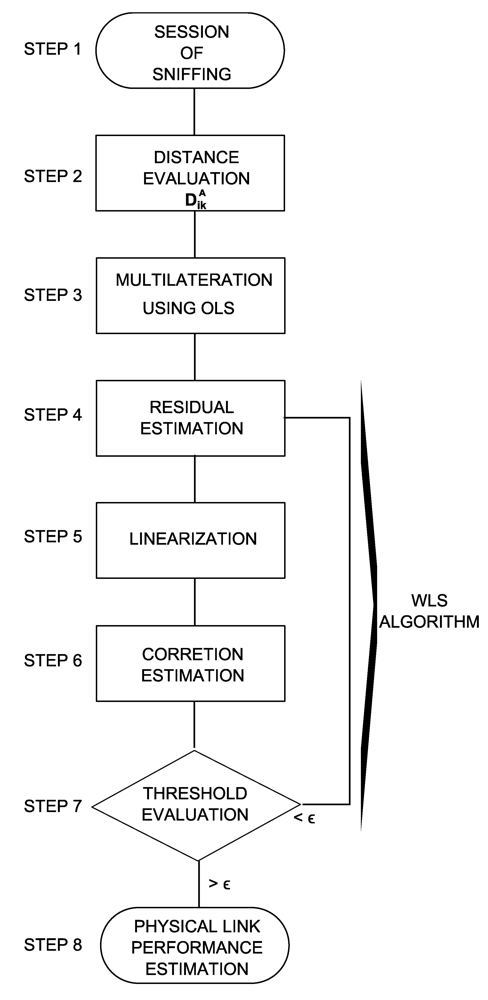
- Step 1: each anchor i measures and stores the received signal for the packets transmitted during a timeframe T and related to Sik packets per blind node k. From these measures the anchors compute the received signal power TAik.
- Step 2: on the basis of information about the ambient environment, each anchor makes use of a channel model for each of the blind nodes k, namely FAik, to estimate the distances DAik.
- Step 3: for any k, we set a vector r = DAik, for k= 1, ...,NB. We then write the system Equation (3) and apply the OLS method described in Section 3.1 to obtain the estimation of the position of each blind node. These estimations are then referred to as
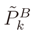 .
. - Step 4: for any k, we also compute the estimated residual by applying Equation (5). From this step on, we enter an interactive WLS algorithm applied to the indirect observations described in Section 3.2.
- Step 5: we compute the coefficients of matrix A∂, which represents the partial derivates of Ap in dx and dy. This is performed by a linearization of each function in the system Ap by a Taylor expansion around the point estimate in Step 3. The general equation for the linearization of a multivariable function f(X) at a point Q is: f(X) ≈ f(Q) + ▽ f|Q(X− Q)
- Step 6: we then apply Equation (14) to obtain the estimation of the correction to be applied to the initial position of each blind node k at each iteration s: δPkB,s. We compute again the new estimated position:
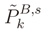 .
. - Step 7: for any blind node k we go back for another iteration if δPkB,s< ε, where ε is a threshold set as the stop criterion. Otherwise we go ahead with the next step.
- Step 8: from the estimated position of the blinds nodes and making use of the most appropriate channel model FBjk (this is selected again on the basis of the ambient environment), the transmission power of node k seen by the blind node j is computed.
5. Experiments
In this section, we firstly illustrate the setup and present the selection of the propagation models, which are key to the proposed method performance. We then present and analyze the results.
5.1. Setup
The effectiveness of the proposed methodology has been tested in three indoor scenarios: a conference room, an office room and a small flat, with some details provided in Table 1. The tools used for the experiments are as follows:
- Development kit case provided by Telit Wireless Solutions. This kit is made of five ZigBee radio boards that are based on the Texas Instruments CC2530 System on Chip with the Embedded Telit Z-One ZigBee-PRO Stack. The antennas are external dipoles characterized by an omnidirectional pattern. Four modules are used to create the network under analysis whereas the fifth works as the sniffer, for which a specific firmware has been developed to correctly capture all the packets on air.
- The software used to inspect the packet content is Wireshark. To analyze the performance of the network from the Wireshark output and to conduct network discovery and commissioning, a specific tool has been developed by Telit Wireless Solution in collaboration with our lab and named SRManager Tool. In this experiment, this tool has been used to collect the RSSI values observed from the different nodes in the network.

Table 1.
Environment of the experiments scenarios.
| Scenario | Size | Description | Link type |
|---|---|---|---|
| Conference room | 6.3 m × 5.4 m | The room includes 12 desks with around 40 chairs. The room was empty when making the measurements. | LOS |
| Office room | 4.5 m × 9.5 m | The room includes 5 desks, 5 personal computers, and 4 people were working when making the measurements. | LOS |
| Small flat | around 85 m2 | The flat has 5 rooms (kitchen, living room, corridor and 2 bedrooms) with typical furniture | LOS/NLOS |
During the experiments we used the standard ZigBee channel number 14 in the 2.4 GHz ISM frequency band. For each scenario, the blind nodes (NB = 4) have been placed randomly and then switched on; then, the sniffer has been moved again randomly in ten positions (NA = 10) to perform the required sniffing session. The network nodes are identified by their network 16-bit address: 00-00, 95-4C, 1E-57, 28-1F. For each position, the sniffer captures the first 1,000 packets generated by each active node and exchanged in the PAN network. We firstly performed the campaign of RSSI measures by the sniffer; secondly, we applied the model of indoor propagation to estimate the distances; and thirdly, we used the approach discussed in Section 4 to estimate the physical link performance. Figure 5, Figure 6 and Figure 7 show the locations of both the blind nodes and the sniffer for the three scenarios. Note that in these figures, the origin of the Euclidean space has been set to the first anchor position.
Through the serial port, the sniffer was connected to a laptop running Wireshark together with the SRManager Tool. For each position, the sniffer captured around 1000 packets from which we extracted the RSSI values from the IEEE 802.15.4 packets. This value is a measure of the power of the received signal as measured by the receiving device. In our scenarios, the receiver is the sniffer and the transmitters are the blind nodes building the PAN. For each packet with the same source node address, we extracted the RSSI and computed the arithmetic average of all the resulting values. Indeed, these measurements are affected by the peaks caused by a multipath fading, since in the indoor scenario a small variation of the environment can significantly affect the signal strength. This process is replicated for each anchor position. Finally, we obtained ten sets of observations, each containing information about the average RSSI value between the anchor node and the blind nodes. Table 2 shows the average RSSI values for the three scenarios.
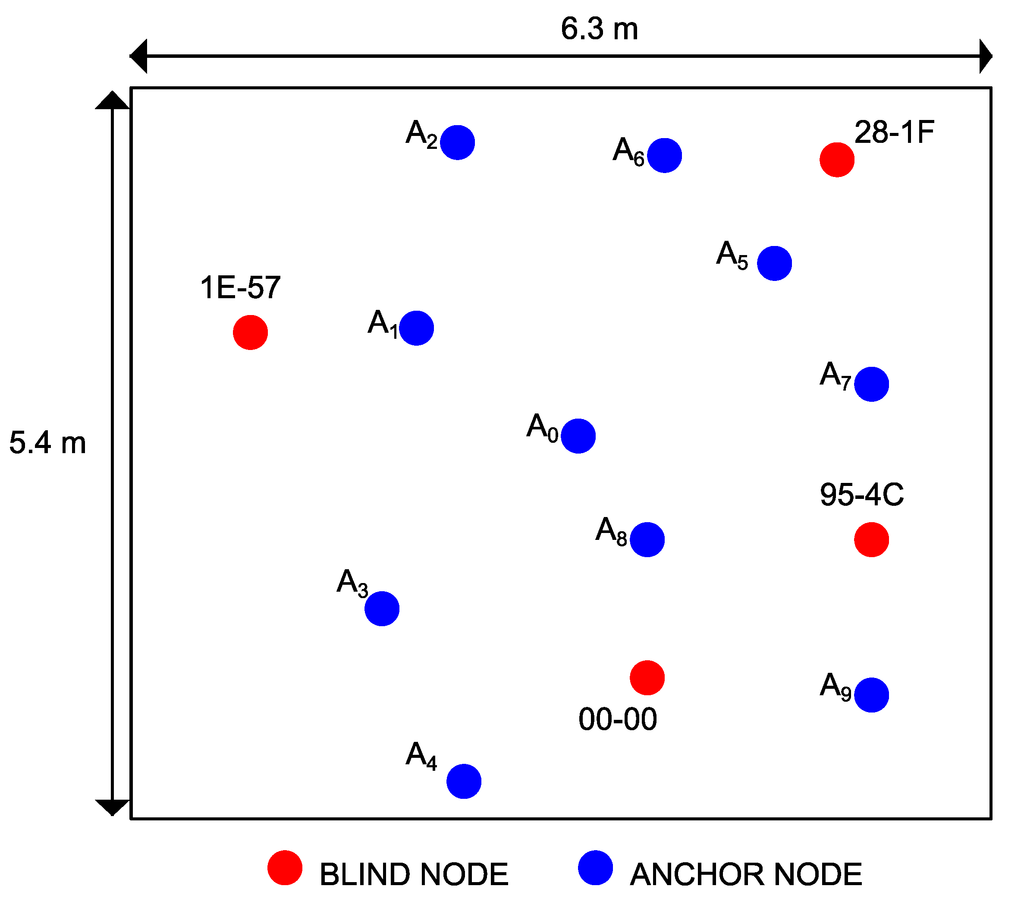
Figure 5.
Position of the blind nodes and anchors for the conference room experiments.
Figure 5.
Position of the blind nodes and anchors for the conference room experiments.
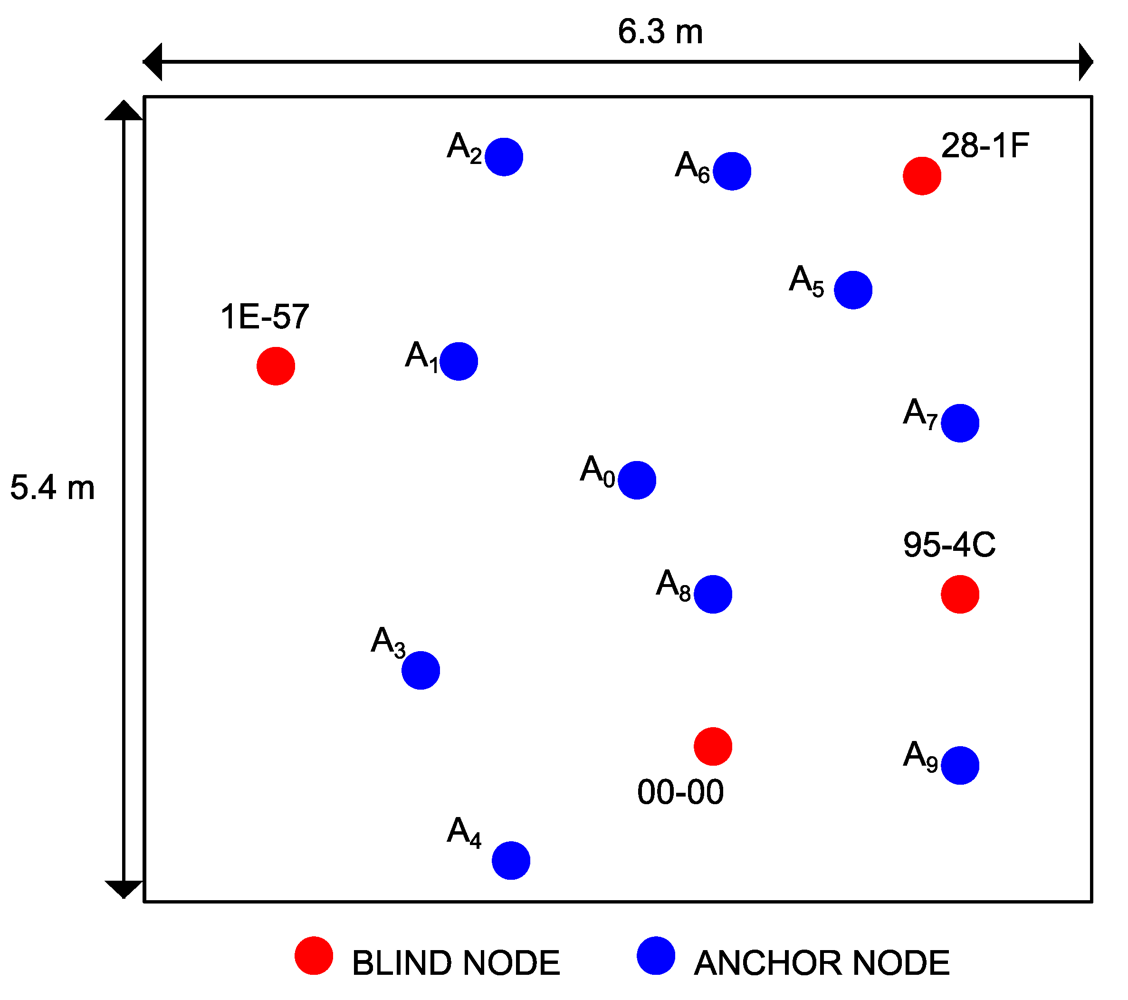
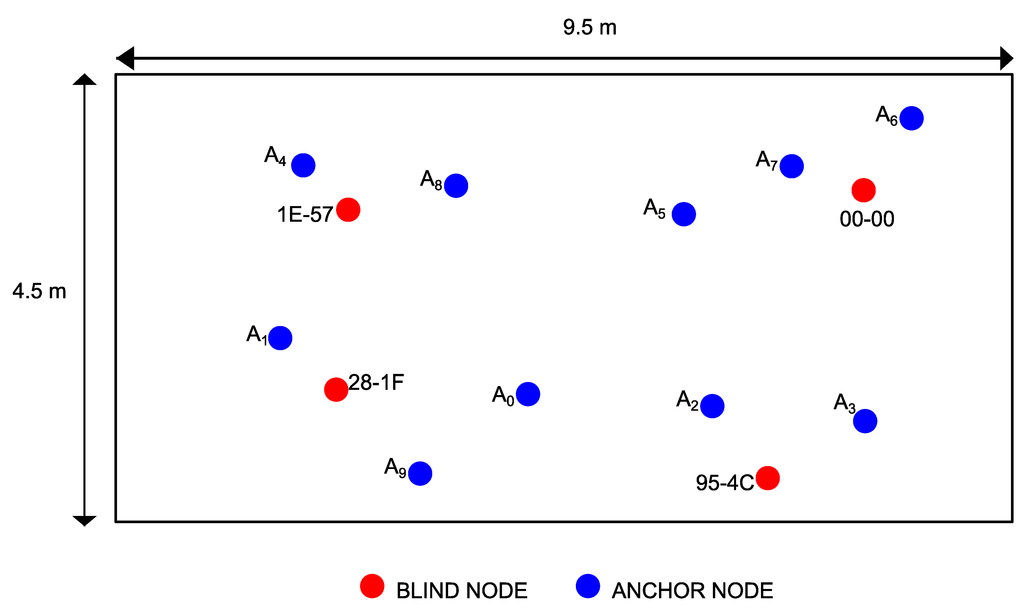
Figure 6.
Position of the blind nodes and anchors for the office.
Figure 6.
Position of the blind nodes and anchors for the office.
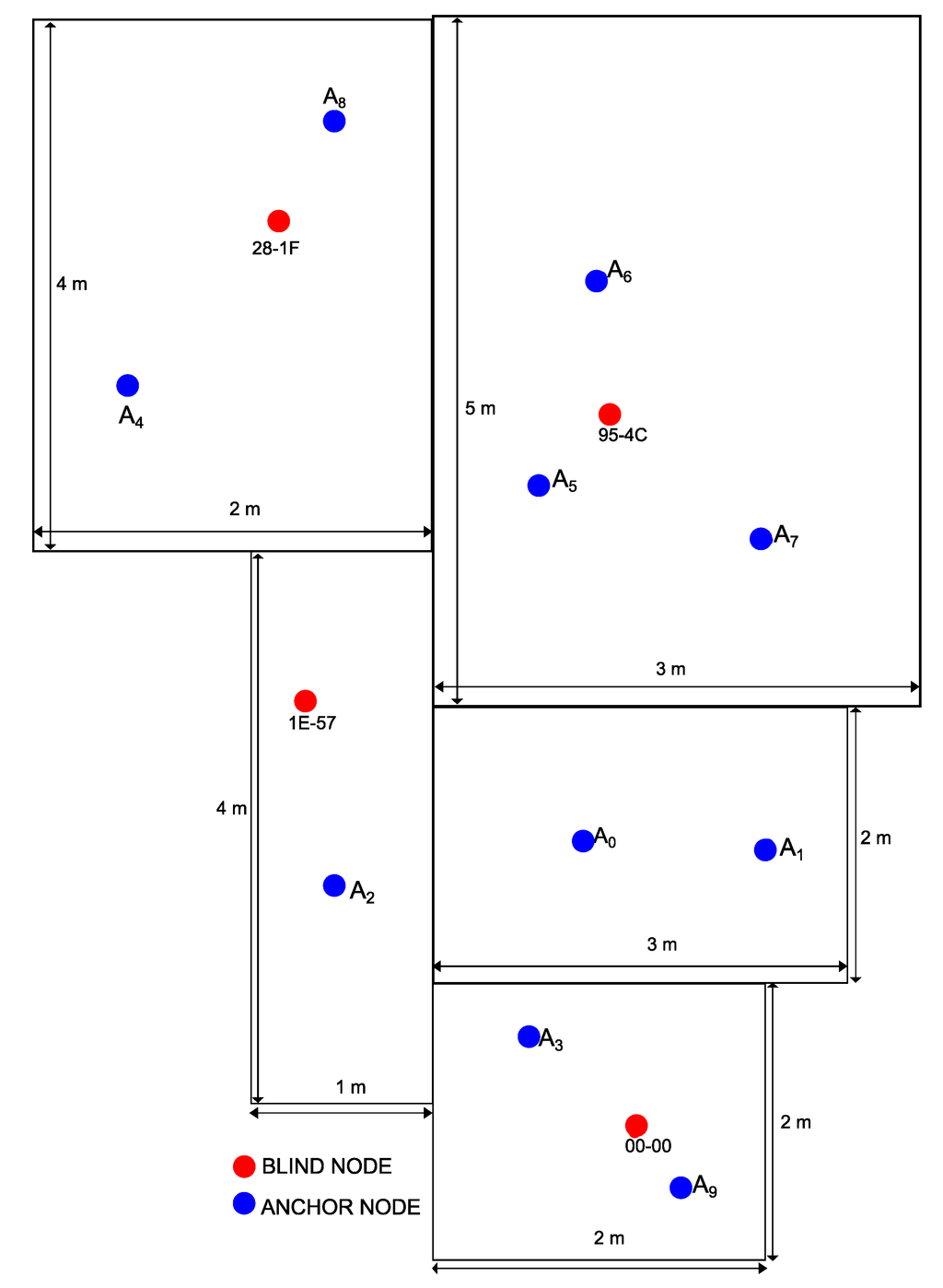
Figure 7.
Position of the blind nodes and anchors for the flat.
Figure 7.
Position of the blind nodes and anchors for the flat.

Table 2.
Average values of the RSSI measurements for the three scenarios.
| ANCHOR | 00-00 | 28-1F | 95-4C | 1E-57 |
|---|---|---|---|---|
| Conference room | ||||
| A1 | 30.03 | 26.92 | 28.00 | 36.00 |
| A2 | 23.99 | 10.13 | 22.00 | 40.00 |
| A3 | 27.03 | 28.00 | 8.95 | 33.99 |
| A4 | 27.92 | 21.95 | 22.88 | 30.00 |
| A5 | 31.97 | 7.52 | 26.75 | 24.02 |
| A6 | 24.95 | 34.00 | 30.00 | 11.90 |
| A7 | 20.97 | 31.01 | 24.00 | 28.84 |
| A8 | 25.68 | 30.15 | 36.00 | 13.65 |
| A9 | 35.00 | 20.28 | 16.77 | 24.00 |
| A10 | 28.00 | 20.96 | 36.83 | 17.97 |
| Office room | ||||
| A1 | 24.10 | 7.63 | 34.00 | 24.35 |
| A2 | 25.62 | 42.00 | 12.50 | 33.36 |
| A3 | 29.21 | 6.20 | 39.98 | 20.31 |
| A4 | 29.27 | 14.54 | 38.00 | 25.21 |
| A5 | 23.01 | 30.00 | 20.55 | 36.45 |
| A6 | 13.60 | 30.00 | 10.85 | 43.07 |
| A7 | 27.09 | 23.03 | 21.96 | 29.59 |
| A8 | 41.96 | 15.30 | 19.63 | 21.87 |
| A9 | 33.81 | 26.26 | 21.44 | 21.96 |
| A10 | 9.60 | 34.49 | 23.53 | 28.02 |
| Flat | ||||
| A1 | 13.17 | 5.01 | 23.00 | 20.28 |
| A2 | 21.98 | -0.54 | 18.00 | 25.00 |
| A3 | 16.00 | 16.92 | 36.00 | 16.00 |
| A4 | 28.10 | 12.00 | 4.73 | 9.29 |
| A5 | -8.48 | 29.08 | 22.51 | 9.97 |
| A6 | 4.91 | 6.86 | 22.00 | 35.02 |
| A7 | 7.57 | 18.98 | -0.90 | 27.50 |
| A8 | 10.15 | 5.96 | 7.33 | 32.00 |
| A9 | -1.17 | 36.00 | 13.17 | 15.00 |
| A10 | 39.74 | -5.29 | 13.90 | 16.33 |
5.2. Propagation Models
A key aspect in the proposed method is the selection of the most appropriate propagation model. It is used to estimate the distance from the measured power and to again estimate the power from the estimated distance. Specifically, in our experiments the power is measured in terms of RSSI (Received Signal Strength Indication). The indoor-radio channel differs from the outdoor channel because the indoor channel has shorter distances to cover, higher path-loss variability, and greater variance in the received signal power. Several models have been proposed in the literature to estimate the path loss in the indoor environment. In our experiments, we have used the one-slope and multi-wall models [38,39,46]. These are the most important and frequently employed path loss models for the estimation of the average received power levels in indoor propagation scenarios, since they provide a good trade-off between simplicity and precision. For the one-slope model, the path loss in dB is given by
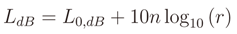
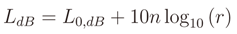
where L0,dB is the path loss at distance of 1 m, n is the attenuation coefficient and r is the distance. L0,dB should be estimated in a free space and it is not affected by the environment. It only depends on physical properties of link (distance and frequency) and can be estimated a priori by the following Friis free-space equation (in dB)
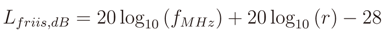
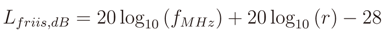
For the 2.4 GHz and for the distance of 1 m the Equation (17) has a value of 40.2 dB.
As for the coefficient n, it is environment dependent and in literature there are several studies that provide an estimation of this value. In our experiments, we have selected the value of n = 4.2 in accordance with the study in [40,41,42]. This model has been used for the conference and office environment.
For the flat scenario, due to the presence of walls we have used the multi-wall model given by the following expression
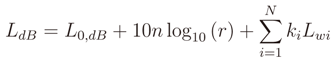
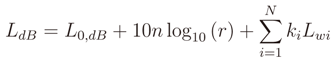
where the integer N is the number of wall types, ki denotes the number of wall of type i, and Lwi the signal loss for wall type i. There are different Lwi values in relationship to the material and thickness of the walls, but in our work all walls have same characteristic. So the difference among the wall is only their position in the path. In our experiments, in accordance with the work in [43], we used the calibration method proposed in [44] to estimate the Lwi values for our flat environment. Whether the wall is the first or the second in the path changes the value of Lwi. After the calibration, we obtained these values: Lw1 = 8.21 and Lw2 = 7.12.
The described models are then used to extract the distance from the collected RSSI measures, but before this, a conversion is needed since these measures do not represent exactly the received power, which is instead given by the following expression
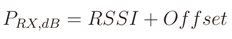
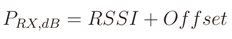
For the used CC2530 chipset, Offset = – 73. Then, knowing the transmission power PTX,dB (for the Telit ZE51 module, the transmission power is PTX,dB = 4 dBm [45]), we can compute the distance from the following expression
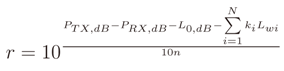
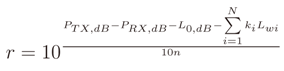
Obviously, if there are no walls in the path, in Equation (20), the value of 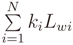 is zero.
is zero.
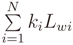 is zero.
is zero.5.3. Analysis of Results
After performing the sessions of measures and the post-processing of the RSSI values, we obtain a set of distances between the anchors and the PAN active nodes (blind nodes). These are then used to compute the distances among the PAN nodes and estimate the RSSI values of the network channel links. Table 3 presents the actual values of these distances for each scenario. Since the relative distances are now known, we can compute the link budget for these links using the relative equation with the appropriate propagation model so that we obtain the path loss from Equations (16) and (18). The chip producer provides an absolute non-calibrated accuracy range equal to ± 4 dB for the hardware CC2530 used in our experiments. On the basis of this accuracy, we can compute the range of RSSI values for each link starting from the actual values. These actual RSSI ranges are shown in Table 4. The key results are also presented through bar graphics in Figure 8 and Figure 9. The first shows the percentage of distance error, before and after the application of proposed method, for all scenarios. The second shows the percentage of RSSI error, again before and after the application of proposed method, for all scenarios.

Table 3.
Actual distances among the nodes for the three scenarios.
| Node tx | Node rx | Conference room | Office | Flat |
|---|---|---|---|---|
| 00-00 | 28-1F | 3.52 m | 3.14 m | 7.11 m |
| -00 | 95-4C | 2.20 m | 2.08 m | 5.36 m |
| -00 | 1E-57 | 3.21 m | 2.85 m | 3.87 m |
| -4C | 28-1F | 2.52 m | 1.78 m | 3.38 m |
| -1F | 1E-57 | 3.59 m | 1.11 m | 3.36 m |
| -4C | 1E-57 | 4.46 m | 2.31 m | 3.78 m |

Table 4.
Error on the distance and RSSI estimations obtained using 10 anchors.
| Node | Multilateration—Error | Proposed method-Error | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| TX | RX | RSSI | distance | RSSI | distance | RSSI | ||||
| [dB] | a.v.[m] | [%] | a.v.[dB] | [%] | a.v.[m] | [%] | a.v.[dB] | [%] | ||
| Conference room | ||||||||||
| 00-00 | 28-1F | 10 ÷ 18 | 0.25 | 7.6% | 0 | 0% | 0.33 | 10.3% | 0 | 0% |
| 00-00 | 95-4C | 18 ÷ 26 | 0.96 | 77.4% | 2 | 7.7% | 0.73 | 49.6% | 0 | 0% |
| 00-00 | 1E-57 | 12 ÷ 20 | 0.98 | 43.9% | 0 | 0% | 0.96 | 42.7% | 0 | 0% |
| 95-4C | 28-1F | 16 ÷ 24 | 0.06 | 0.7% | 0 | 0% | 0.62 | 19.7% | 0 | 0% |
| 28-1F | 1E-57 | 9 ÷ 17 | 0.04 | 1.1% | 0 | 0% | 0.33 | 10.1% | 0 | 0% |
| 95-4C | 1E-57 | 6 ÷ 14 | 1.33 | 42.5% | 0 | 0% | 0.89 | 24.9% | 0 | 0% |
| mean | 0.60 | 28.9% | 0.33 | 1.3% | 0.64 | 26.2% | 0 | 0% | ||
| variance | 0.55 | 30.9% | 0.56 | 0.1% | 0.27 | 16.6% | 0 | 0% | ||
| Office | ||||||||||
| 00-00 | 28-1F | 12 ÷ 20 | 2.52 | 44.5% | 7 | 35 % | 0.01 | 0.3% | 0 | 0% |
| 00-00 | 95-4C | 19 ÷ 27 | 2.32 | 52.7% | 10 | 37 % | 0.25 | 13.7% | 0 | 0% |
| 00-00 | 1E-57 | 14 ÷ 22 | 0.98 | 25.6% | 1 | 4.5 % | 0.57 | 25% | 0 | 0% |
| 95-4C | 28-1F | 22 ÷ 30 | 2.51 | 58.5% | 12 | 40 % | 1.3 | 42.2% | 6 | 20% |
| 28-1F | 1E-57 | 31 ÷ 39 | 1.10 | 49.8% | 9 | 23 % | 0.02 | 1.8% | 0 | 0% |
| 95-4C | 1E-57 | 18 ÷ 26 | 0.10 | 4.1% | 0 | 0 % | 0.02 | 0.9% | 0 | 0% |
| mean | 1.58 | 39.2% | 6.5 | 68.2% | 0.36 | 14.0% | 1 | 3.3% | ||
| variance | 1.01 | 20.5% | 24.3 | 59.7% | 0.51 | 16.9% | 6 | 0.5% | ||
| Flat | ||||||||||
| 00-00 | 28-1F** | –18 ÷ –10 | 0.63 | 8.1% | 2 | 20% | 0.7 | 8.9% | 0 | 0% |
| 00-00 | 95-4C** | –12 ÷ –4 | 0.51 | 8.7% | 1 | 25% | 1.31 | 19.7% | 0 | 0% |
| 00-00 | 1E-57** | –6 ÷ 2 | 1.76 | 31.3% | 8 | 400% | 0.7 | 15.3% | 0 | 0% |
| 95-4C | 28-1F* | 2 ÷ 10 | 1.68 | 33.2% | 7 | 70% | 0.23 | 6.4% | 0 | 0% |
| 28-1F | 1E-57* | 1 ÷ 9 | 1.39 | 27.7% | 9 | 100% | 0.41 | 10.2% | 0 | 0% |
| 95-4C | 1E-57** | -6 ÷2 | 1.56 | 29.2% | 10 | 50% | 1.39 | 26.9% | 2 | 100% |
| mean | 1.25 | 23.0% | 6.17 | 170.5% | 0.79 | 14.6% | 0.33 | 16.7% | ||
| variance | 0.55 | 11.5% | 14.16 | 418% | 0.47 | 7.7% | 0.67 | 13.2% | ||
* Path with one wall; ** Path with two walls.
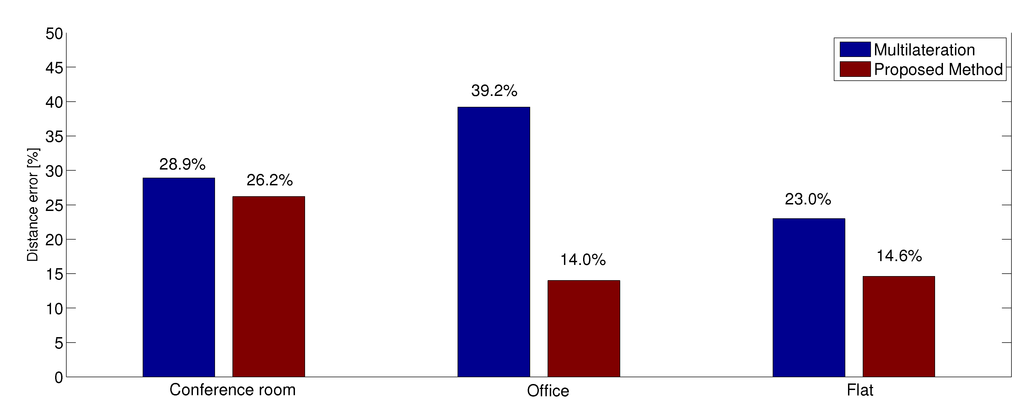
Figure 8.
Distance estimation error in percentage using 10 anchors.
Figure 8.
Distance estimation error in percentage using 10 anchors.
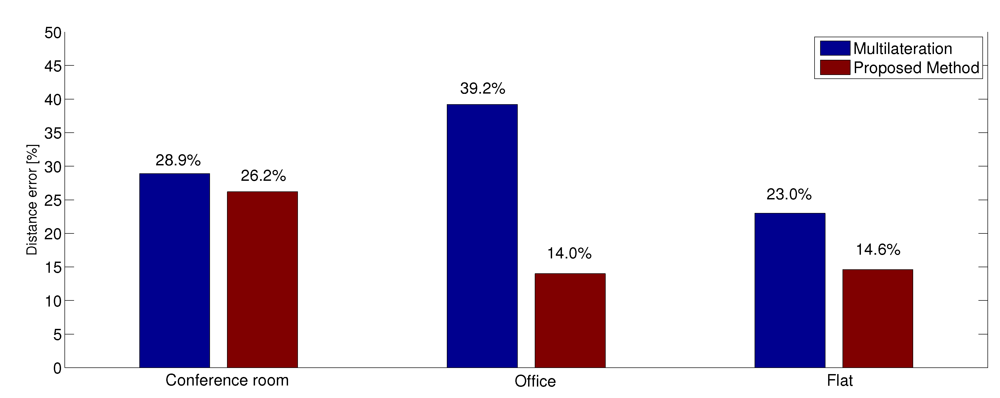
As discussed in Section 3.1, we applied the multilateration algorithm using to ten anchors measurements to achieve the first estimation of blind nodes positions, from which we then computed the relative distance among them. Then we computed the link budget from these relative distances by applying the appropriate propagation models to the path loss. We first analyze the results obtained with the multilteration algorithm using only the OLS, which are shown in the “ multilateration” columns of Table 4. Other than the absolute values (referred to as “ a.v.”), the table presents the error in percentage. It can be noted that the errors in the conference room are smaller than in other scenarios. This result is due to the presence of more obstacles in both the office and the flat. This is a cause of stronger multipath fading that affects the measurements. It is also possible to note another problem when looking at the path loss logarithmic progress in Figure 10. For short distances, a small variation in the distance value corresponds to small variations in the path loss, whereas the same variation at greater distances corresponds to larger variations in terms of path loss. Accordingly, the absolute value of the error has to be considered together with the distance it is related to. This problem is more evident in large environments than in smaller ones, as can be clearly seen in Table 4.
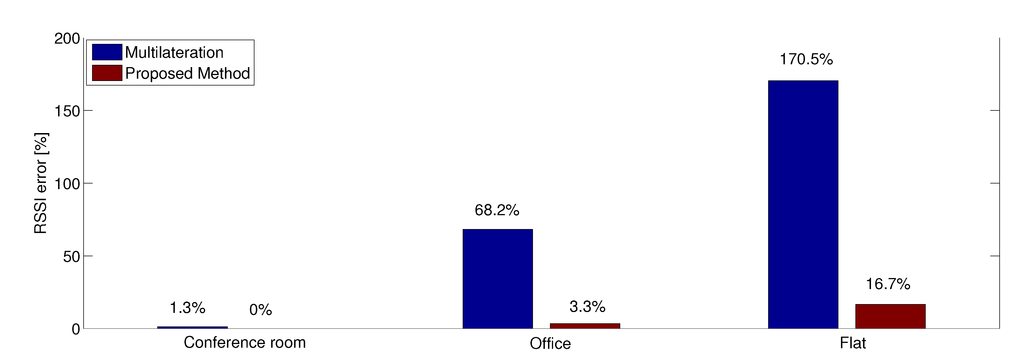
Figure 9.
RSSI estimation error in percentage using 10 anchors.
Figure 9.
RSSI estimation error in percentage using 10 anchors.
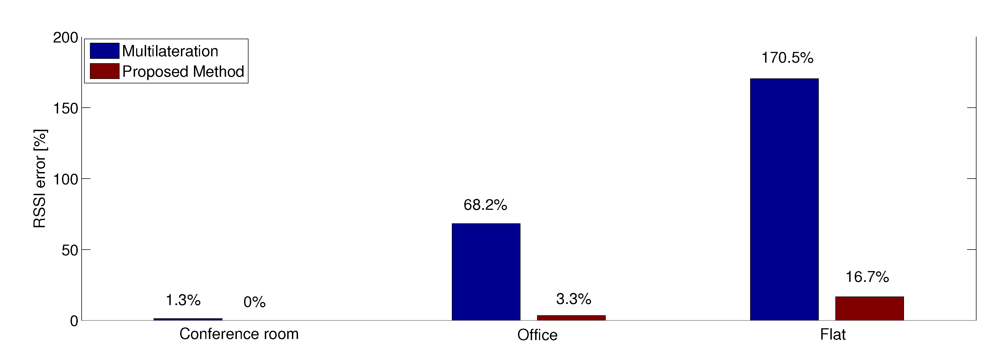
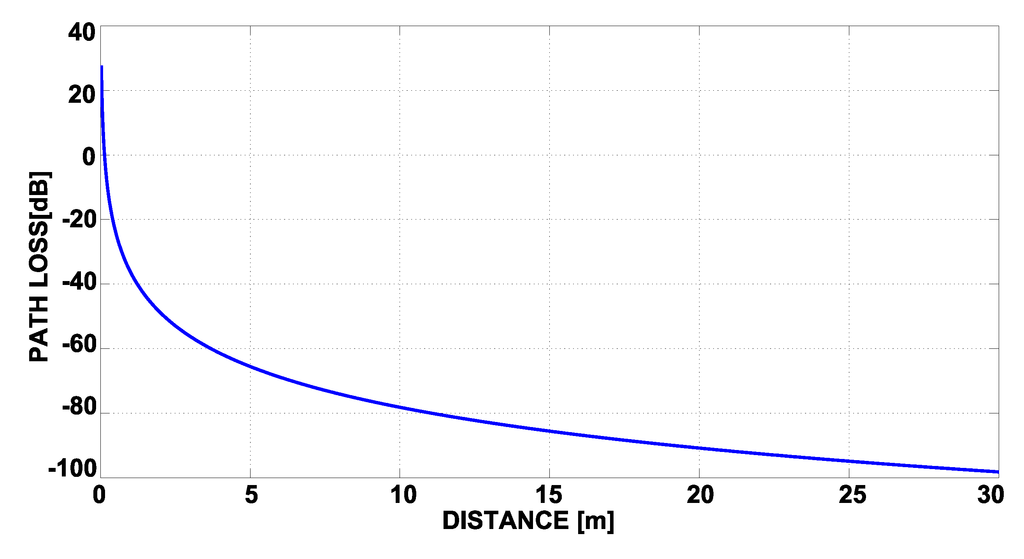
Figure 10.
Path Loss progress.
Figure 10.
Path Loss progress.
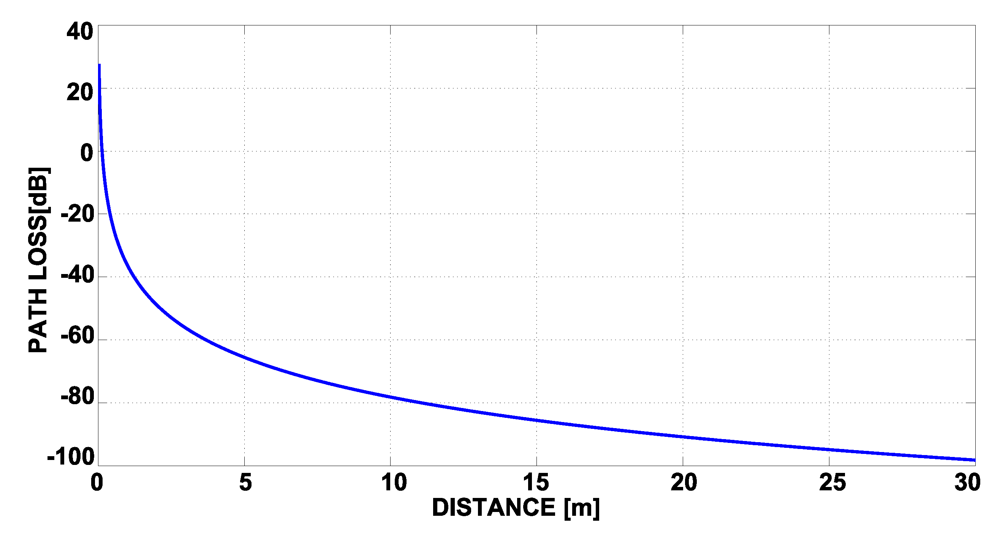
The estimation of physical layer performance is clearly improved with the application of the indirect observations (“ proposed method” columns in Table 4). This method achieves significant improvements also in the scenarios characterized by the problem of large environments discussed before, allowing for compensating multipath fading effects due to the presence of more consecutive obstacles. As show in Table 4, it allows for reducing the RSSI estimation error from the results obtained with the application of the multilateration algorithm of 1.33 dB for the conference room scenario, 5.5 dB for the office room scenario and 5.85 dB for the flat scenario. The more complex is the scenario, the higher are the benefits of applying the proposed algorithm. With respect to the distance estimation, the RSSI evaluation presents lower errors. This is due to the fact that the RSSI and the node distance are linked by a logarithmic relationship, as discussed in Section 5.2. Accordingly, a big error in terms of distance does not correspond to a big error in terms of RSSI if we analyze the relationship where the curve of path loss has a little slope.
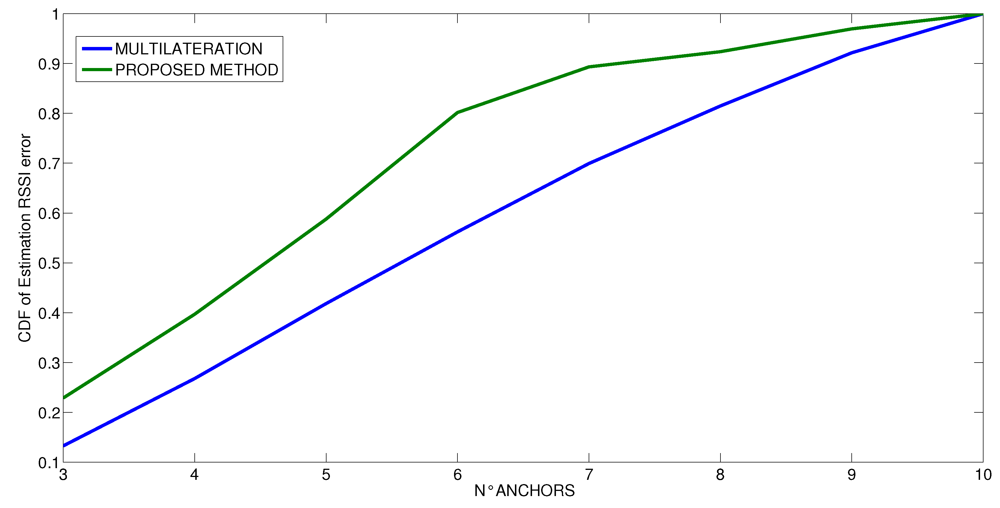
We also performed some runs that vary the number of anchors in the estimation of the distances. The results are shown in Figure 11, Figure 12 and Figure 13, where the vertical axis shows the CDF (Cumulative Density Function) of the RSSI estimated error value and the horizontal axis shows the number of anchors used in the estimation process. At first, we have performed the experiments by using the entire set of ten anchors, and then we iteratively removed one anchor in sequence, estimating again each time the RSSI value. These experiments are intended to analyze what is the needed number of anchors to achieve a given error. This is important to either limit the time spent to perform the measurements when only one real anchor is used at different positions or to reduce the number of different anchors used in parallel. In any case, the minimum number of anchor measurements is clearly three. Looking at the curves, we see at first that the behavior is different for the three scenarios. In the first scenario, which is the simplest one, as soon as the minimum number of anchors has been exceeded (three), the probability of the estimation is not affected by error. Indeed, it increases linearly until 7 anchors are used, then the value is stable until 9 anchors are used and then it increases rapidly with 10 anchors. In contrast, in the other two scenarios, the number of anchors is very important, and the estimation would benefit from using more than only ten anchors. In any case, it is possible to note that the probability that the estimation process is not affected by error increases according to logarithm mode and the probability to have some errors decreases after the application of indirect observations for any number of anchors. The improvement of the proposed method is more visible when the number of anchors is low. In all scenarios, the proposed method increases the probability that the RSSI estimation is not affected by error; indeed, in all the considered cases, the CDF of the proposed method is shifted upwards with respect to the CDF of the multilateration method. On average, thanks to the proposed method, the probability to have a correct RSSI estimation is improved by 15%.
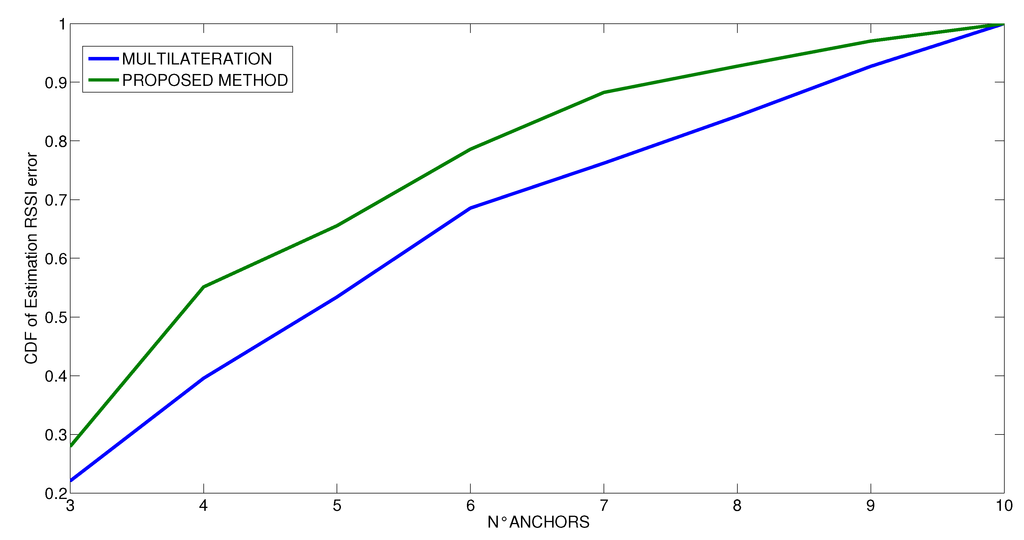
Figure 11.
Cumulative Distribution Function of the RSSI estimation error at varying number of anchors for the office scenario.
Figure 11.
Cumulative Distribution Function of the RSSI estimation error at varying number of anchors for the office scenario.
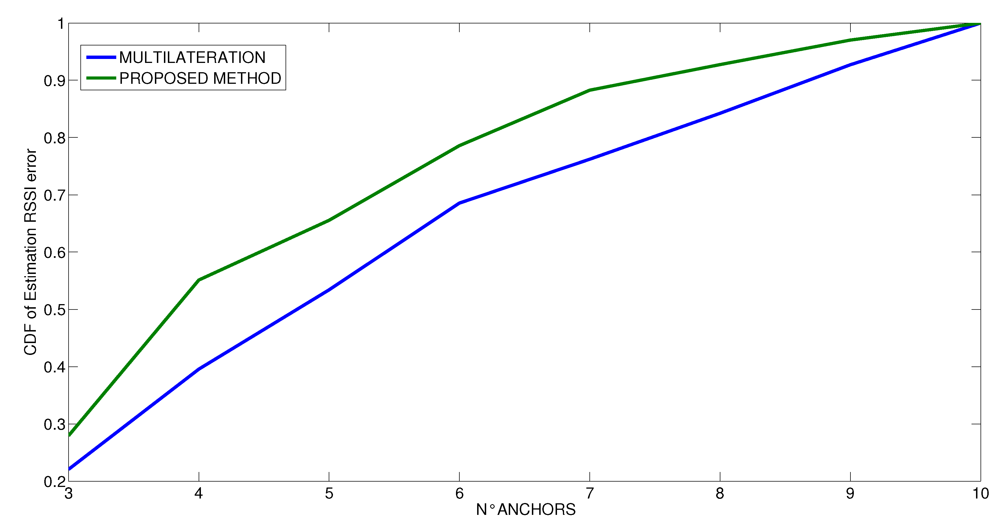
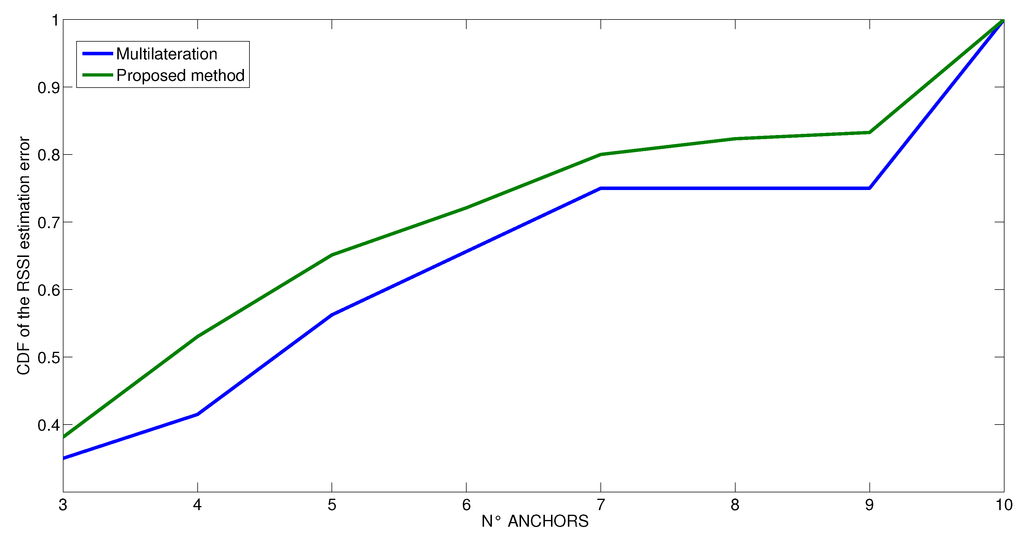
Figure 12.
Cumulative Distribution Function of the RSSI estimation error at varying number of anchors for the conference room scenario.
Figure 12.
Cumulative Distribution Function of the RSSI estimation error at varying number of anchors for the conference room scenario.
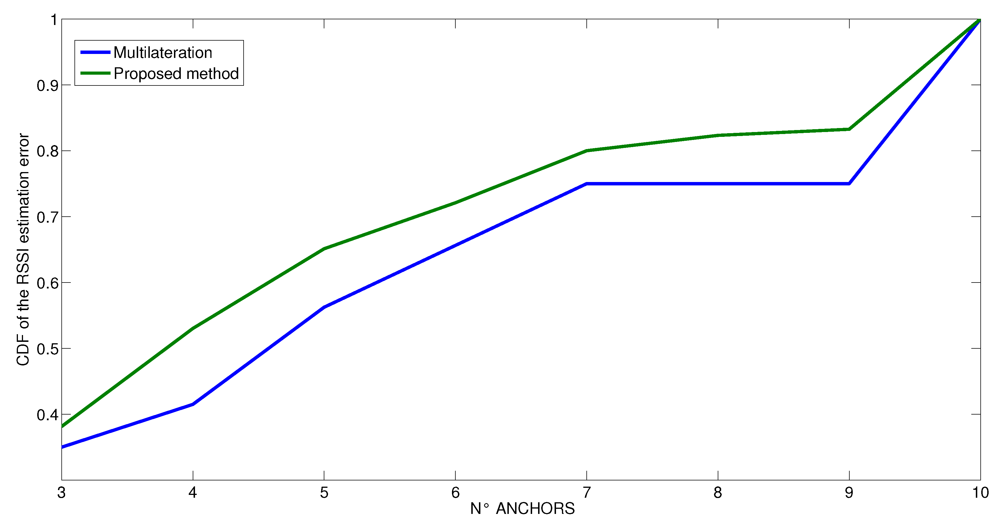
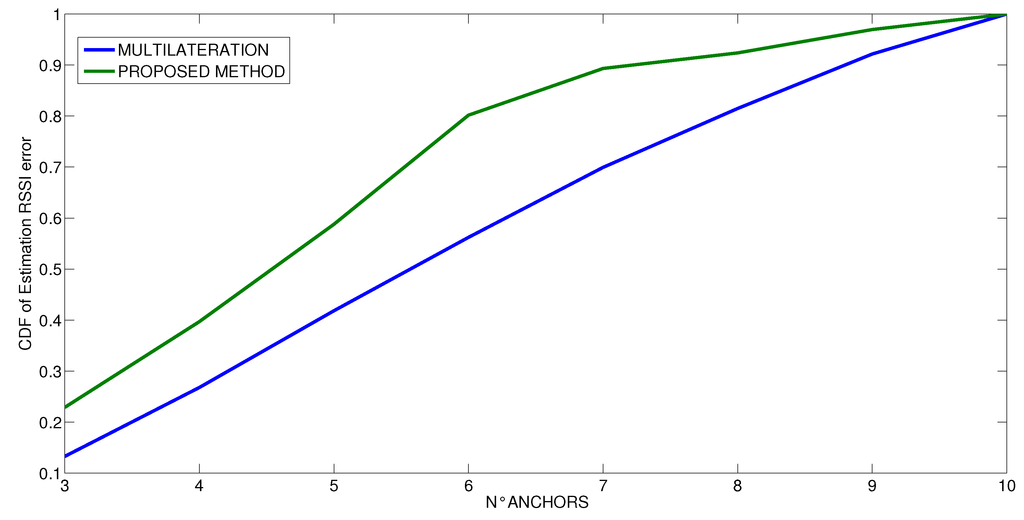
Figure 13.
Cumulative Distribution Function of the RSSI estimation error at varying number of anchors for the flat scenario.
Figure 13.
Cumulative Distribution Function of the RSSI estimation error at varying number of anchors for the flat scenario.
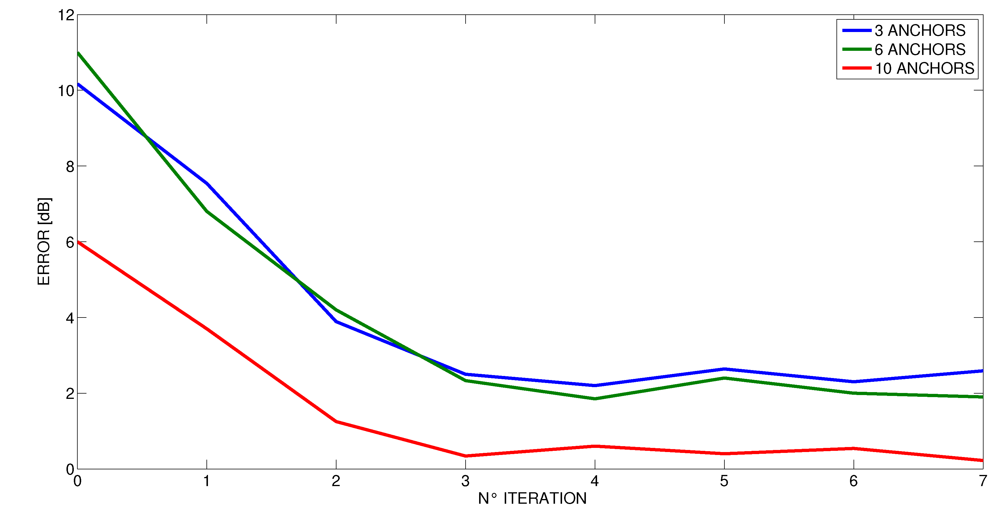
When performing the proposed iterative method, we have empirically observed that after three iteration, the gap (δx, δy) is very small and comparable with the variance of the result σ. Therefore, in our experiments, we stopped the method after having performed just three iterations (the results shown before refer to this setting). However, we wanted to further investigate this phenomenon, and in Figure 14, Figure 15 and Figure 16 we present the average error as the number of iterations in the proposed method increases at different number of anchors. These curves confirm that after three iterations, the method does not benefit from performing more steps for all the cases. Indeed, even the number of anchors does not seem to affect the number of iterations that are needed to achieve a stable result. Accordingly, this number appeared to be a good trade-off between computational costs and accuracy.
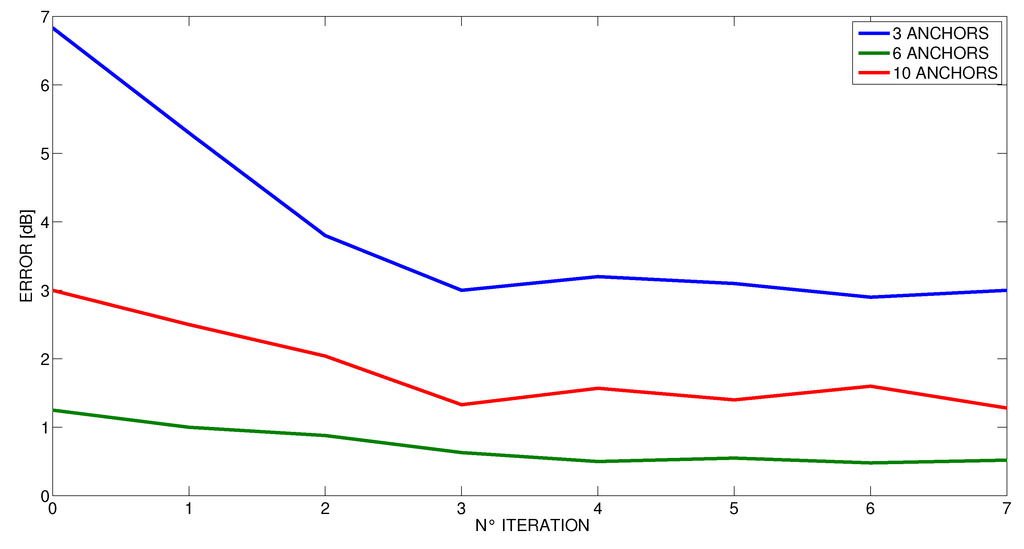
Figure 14.
Decrease of error by method iteration in the conference room.
Figure 14.
Decrease of error by method iteration in the conference room.
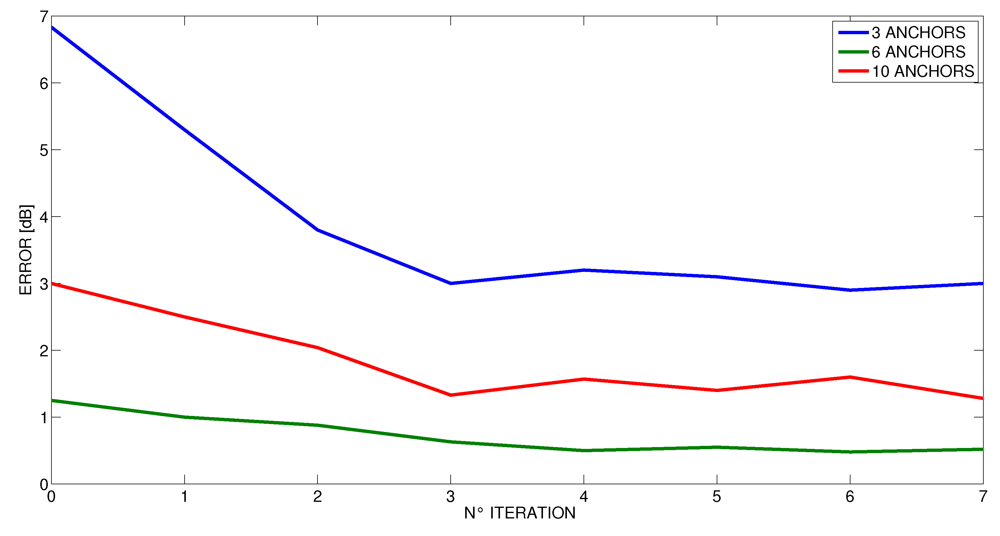
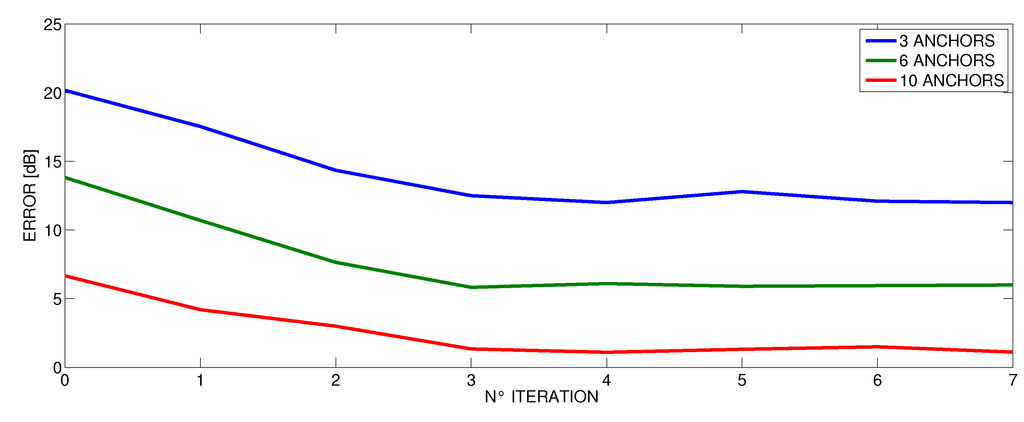
Figure 15.
Decrease of error by method iteration in the office.
Figure 15.
Decrease of error by method iteration in the office.
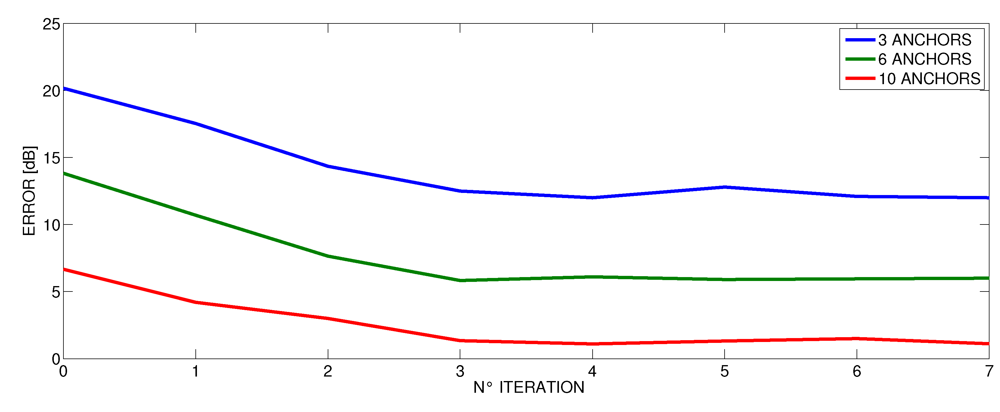
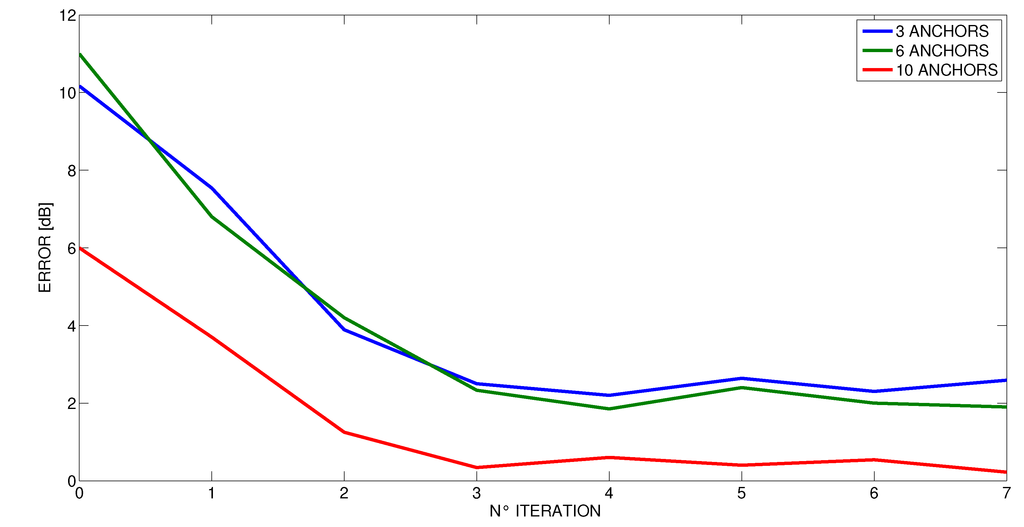
Figure 16.
Decrease of error by method iteration in the flat.
Figure 16.
Decrease of error by method iteration in the flat.
6. Conclusions
In this work, we applied the method of indirect observations to estimate the physical layer performance in the WSNs. The proposed criterion is completely not invasive because it makes use of external sniffers to capture the packet data. From sniffed data, we first compute the information of signal strength (RSSI), and using this information we estimate the position of the nodes in the WSN by applying the WLS to the method of indirect observations. By the resulting information, we estimate the status of all links in the network using the appropriate propagation model. We have conducted real experiments in three different scenarios: an office room, a conference room, and a flat. By applying the proposed method, we have been able to increase the accuracy in the estimation of the RSSI in all the scenarios with respect to the application of the OLS to the multilateration problem. Such an increase is on average 6 dB and reaches as high as 10 dB. The experiments also show that the proposed method allows for estimating the channel link status with an error lower than 2 dB with respect to the calibration accuracy in 75% of measurements and lower than 5 dB in 90% of measurements.
References
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A survey on sensor networks. IEEE Commun. Mag. 2002, 40, 104–112. [Google Scholar]
- Garca-Hernndez, C.F.; Ibargengoytia-Gonzlez, P.H.; Garca-Hernndez, J.; Prez-Daz, J.A. Wireless sensor networks and applications: A survey. Int. J. Comput. Sci. Netw. Secur. 2007, 7, 264–273. [Google Scholar]
- Gill, K.; Yang, S.-H.; Yao, F.; Lu, X. A zigbee-based home automation system. IEEE Trans. Consum. Electron. 2009, 55, 422–430. [Google Scholar] [CrossRef]
- Alemdar, H.; Ersoy, C. Wireless sensor networks for healthcare: A survey. Comput. Netw. 2010, 54, 2688–2710. [Google Scholar]
- Han, J.; Lee, H.; Park, K.-R. Remote-controllable and energy-saving room architecture based on zigbee communication. IEEE Trans. Consum. Electron. 2009, 55, 264–268. [Google Scholar] [CrossRef]
- Lin, S.; Liu, J.; Fang, Y. ZigBee Based Wireless Sensor Networks and its Applications in Industrial. In Proceedings of the IEEE International Conference on Automation and Logistics, Jinan, China, 18–21 August 2007.
- Jiang, P.; Xia, H.; He, Z.; Wang, Z. Design of a water environment monitoring system based on wireless sensor networks. Sensors 2009, 9, 6411–6434. [Google Scholar] [CrossRef]
- Iqbal, R.; Yukimatsu, K. Intelligent transportation systems using short range wireless technologies. J. Trans. Technol. 2011, 1, 132–137. [Google Scholar] [CrossRef]
- The Internet of Things; Giusto, D.; Iera, A.; Morabito, G.; Atzori, L. (Eds.) Springer: Berlin/Heidelberg, Germany, 2010.
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Di Caro, G.A.; Flushing, E.F. Optimal Relay Node Placement for throughput Enhancement in Wireless Sensor Networks. In Proceedings of the 50th FITCE Congress, Palermo, Italy, 31 August–3 September 2011.
- Pilloni, V.; Atzori, L. Deployment of distributed applications in wireless sensor networks. Sensors 2011, 11, 7395–7419. [Google Scholar]
- Navid, P.; Turgay, K. Improving Packet Reception Rate for Mobile Sinks in Wireless Sensor Networks. In Proceedings of the IEEE International Symposium on a World Wireless Mobile Multimedia Networks (WoWMoM) 2012, San Francisco, CA, USA, 25–28 June 2012.
- Han, X.; Cao, X.; Lloyd, E.L.; Shen, C.-C. Fault-tolerant relay node placement in heterogeneous wireless sensor networks. IEEE Trans. Mob. Comput. 2010, 9, 643–656. [Google Scholar] [CrossRef]
- Rost, S.; Balakrishnan, H. Memento: A Health Monitoring System for Wireless Sensor Networks. In Proceedings of Third Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, IEEE SECON, Reston, VA, USA, 25–28 September 2006.
- Nithya, R.; Kevin, C.; Rahul, K.; Lewis, G.; Eddie, K.; Deborah, E. Sympathy for the Sensor Network Debugger. In Proceedings of the SenSys International Conference on Embedded Networked Sensor Systems, San Diego, CA, USA, 2–4 November 2005.
- Tolle, G.; Culler, D. Design of an Application-Cooperative Management System for Wireless Sensor Networks. In Proceedings of the Second European Workshop on Wireless Sensor Networks (EWSN), Istanbul, Turkey, 31 January–2 February 2005.
- Andreas, M.; Mehul, M.; Hu, S.; Simon, K. DiMo: Distributed Node Monitoring in Wireless Sensor Networks. In Proceedings of the MSWiM International Symposium on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Vancouver, BC, Canada, 27–31 October 2008.
- Jan, B.; Matthias, D.; Lennart, M.; Lothar, T. Scalable Topology Control for Deployment-Support Networks. In Proceedings of the 4th International Conference Information Processing in Sensor Networks, Los Angeles, CA, USA, 25–27 April 2005.
- Cheng, Y.; John, B.; Pter, B.; Snoeren, A.C.; Voelker, G.M.; Savage, S. Jigsaw: Solving the Puzzle of Enterprise 802.11 Analysis. In Proceedings of the Special Interest Group on Data Communication (SIGCOMM), Pisa, Italy, 11–15 September 2006.
- Lewis, G.; Nithya, R.; Jeremy, E.; Thanos, S.; Martin, L.; Deborah, E. Emstar: A software environment for developing and deploying heterogeneous sensor-actuator networks. ACM Trans. Sens. Netw. 2007, 3, 1–31. [Google Scholar]
- Rodrigo, F.; Omprakash, G.; Kyle, J.; Philip, L. Four Bit Wireless Link Estimation. In Proceedings of the Sixth Workshop on Hot Topics in Networks (HotNets VI), Atlanta, GA, USA, 14–15 November 2007.
- Kuang, X.; Shen, J. SNDS: A Distributed Monitoring and Protocol Analysis System for Wireless Sensor Network. In Proceedings of the IEEE International Conference on Networks SecurityWireless Communications and Trusted Computing, Wuhan, China, 24–25 April 2010; pp. 422–425.
- Matthias, R.; Kay, R.; Andrea, V. Passive Inspection of Sensor Networks. In Proceedings of IEEE International Conference on Distributed Computing in Sensor Systems, Santa Fe, NM, USA, 18–20 June 2007.
- Chen, B.; Georey, P.; Geo, M.; Matt, W. LiveNet: Using Passive Monitoring to Reconstruct Sensor Network Dynamics. In Proceedings of the IEEE International Conference on Distributed Computing in Sensor Systems, Santorini Island, Greece, 11–14 June 2008; pp. 79–98.
- Dan, Y. DiF: A Diagnosis Framework for Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Computer Communications INFOCOM, San Diego, CA, USA, 15–19 March 2010; pp. 1–5.
- Oliveira, H.A.B.; Nakamura, E.F.; Loureiro, A.A.F. Localization systems for wireless sensor networks. IEEE Wirel. Commun. 2007, 14, 6–12. [Google Scholar]
- Wang, L.; Liu, Y.; Xu, X.; Wang, X. WSN Multilateration Algorithm Based on Landweber Iteration. In Proceedings of the IEEE The Ninth International Conference on Electronic Measurement Instruments ICEMI, Beijing, China, 16–19 August 2009; 1, pp. 250–254.
- Wang, X.; Yuan, S.; Laura, R.; Lang, W. Dynamic localization based on spatial reasoning with RSSI in wireless sensor networks for transport logistics. Sens. Actuat. 2011, 171, 421–428. [Google Scholar] [CrossRef]
- Lakafosis, V.; Tentzeris, M.M. From single to multihop: The status of wireless localization. IEEE Microw. Mag. 2009, 10, 34–41. [Google Scholar]
- Vanheel, F.; Verhaevert, J.; Laermans, E. Ingrid moerman and piet demeester. Automated linear regression tools improve RSSI WSN localization in multipath indoor environment. EURASIP J. Wirel. Commun. Netw. 2011, 38, 1–27. [Google Scholar]
- Goldberger, A.S. Econometric Theory; John Wiley & Sons: New York, NY, USA, 1964. [Google Scholar]
- Shen, Y.; Li, B.; Chen, Y. An iterative solution of weighted total least-squares adjustment. J. Geodesy 2011, 85, 229–238. [Google Scholar] [CrossRef]
- Amiri-Simkooei, A.; Jazaeri, S. Weighted total least squares formulated by standard least squares theory. J. Geodetic Sci. 2012, 2, 1–12. [Google Scholar] [CrossRef]
- Kim, E.; Kim, K. Distance estimation with weighted least squares for mobile beacon-based localization in wireless sensor networks. IEEE Signal Process. Lett. 2010, 17, 559–562. [Google Scholar] [CrossRef]
- Tarr?o, P.; Bernardos, A.M.; Casar, J.R. Weighted least squares techniques for improved received signal strength based localization. Sensors 2011, 11, 8569–8592. [Google Scholar]
- Ampeliotis, D.; Berberidis, K. Linear Least Squares Based Acoustic Source Localization Utilizing Energy Measurements. In Proceedings of the IEEE Sensor Array and Multichannel Signal Processing Workshop, Darmstadt, Germany, 21–23 July 2008; pp. 349–352.
- Homayoun, H. The indoor radio propagation channel. Proc. IEEE 1993, 81, 943–968. [Google Scholar] [CrossRef]
- Fleury, B.H.; Leuthold, P.E. Radiowave propagation in mobile communications: An overview of European research. IEEE Commun. Mag. 1996, 34, 70–81. [Google Scholar]
- Yoo, J.H.; Lee, J.H.; Cho, S.H. A Propagation Model in 2.4GHz ISM Band Using IEEE 802.15.4 Systems. In Proceedings of the Asia-Pacific Conference on Communications, Sabah, Malaysia, 2–5 October 2011; pp. 339–343.
- Yang, T.; Ikeda, M.; Mino, G.; Barolli, L.; Durresi, A.; Xhafa, F. Performance Evaluation of Wireless Sensor Networks for Mobile Sink Considering Consumed Energy Metric. In Proceedings of the International Conference on Advanced Information Networking and Applications, Perth, WA, Australia, 20–23 April 2010; pp. 245–250.
- Zvanovec, S.; Pechac, P.; Klepal, M. Wireless LAN networks design: Site survey or propagation modeling? Radioengineering 2003, 12, 42–49. [Google Scholar]
- Barsocchi, P.; Lenzi, S.; Chessa, S.; Furfari, F. Automatic virtual calibration of range-based indoor localization systems. Wirel. Commun. Mob. Comput. 2011, 12, 1546–1557. [Google Scholar]
- Barsocchi, P.; Lenzi, S.; Chessa, S.; Giunta, G. Virtual Calibration for RSSI-based Indoor Localization with IEEE 802.15.4. In Proceedings of the IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–5.
- Telit ZE51 2.4 module Datasheet. Available online: http://www.telit.com/module/infopool/download.php?id=2350 (accessed on 30 June 2012).
- Sarkar, T.K.; Ji, Z.; Kim, K.; Medouri, A.; Salazar-Palma, M. A survey of various propagation models for mobile communication. IEEE Antennas Propag. Mag. 2003, 45, 51–82. [Google Scholar] [CrossRef]
© 2012 by the authors; licensee MDPI, Basel, Switzerland. This article is an open-access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
