Cyber Attacks on Precision Time Protocol Networks—A Case Study
Abstract
:1. Introduction
- Prong A (integrated security mechanism) specifies an authentication type-length-value (TLV) to protect PTP messages using a symmetric key. More details of implementing Prong A on power profile using PTP daemon (PTPd) can be found in [11];
- Prong B (PTP external transport security mechanisms) describes external security extensions, i.e., Media Access Control Security (MACsec) and IP Security (IPsec) that can be used to protect the PTP messages;
- Prong C (architecture guidance) describes various redundancy approaches, i.e., redundant time system, redundant grandmaster, and redundant paths;
- Prong D (monitoring and management guidance) describes a monitoring system to observe the PTP slave behavior.
2. The Precision Time Protocol and Security Concerns
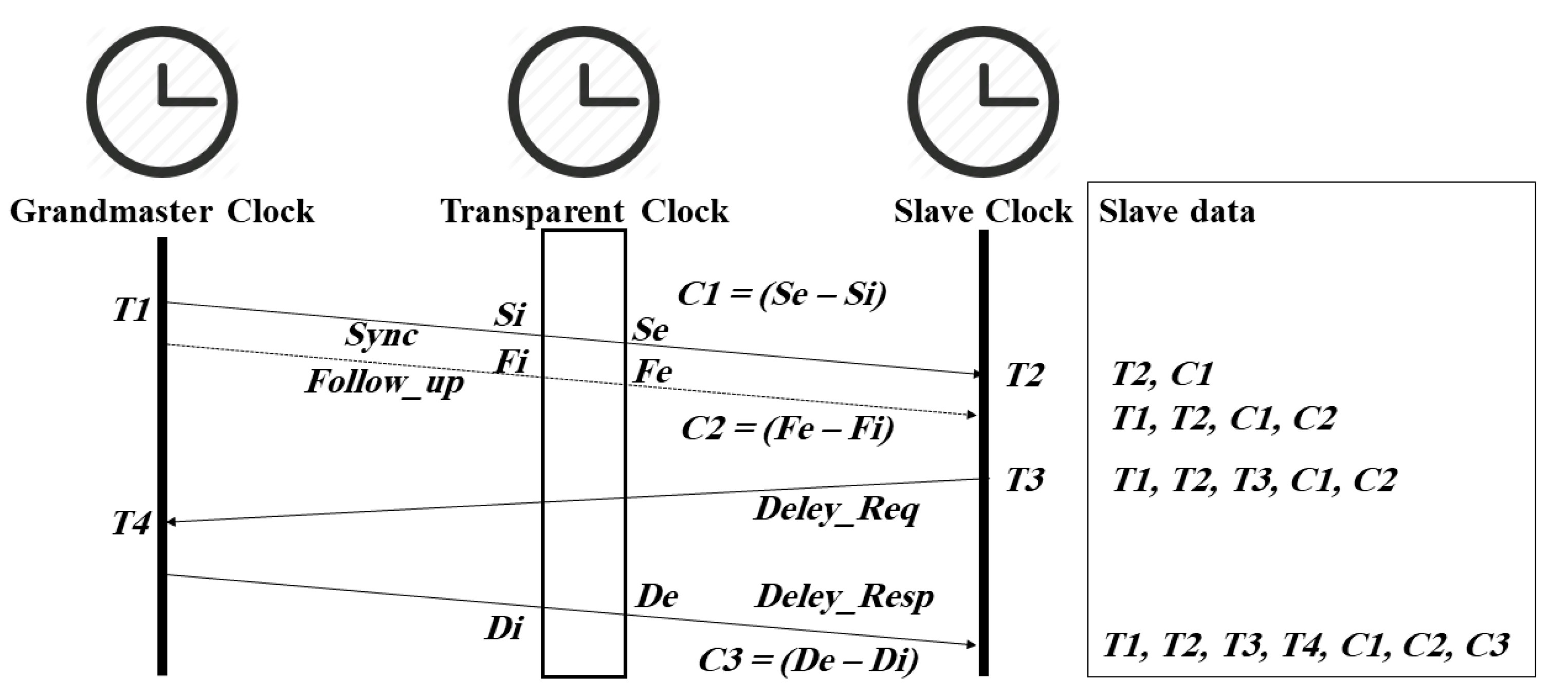
2.1. PTP Overview
2.2. Existing PTP Software Daemons
2.2.1. PTP Daemon (PTPd)—Version 2.3.2
2.2.2. Linuxptp (PTP4l) Version (2.0)
delayAsymmetry + C2)))/2
2.3. Slave Clock Adjustment
- Disable/enable PTP clock adjustment: if the clock adjustment is disabled, the clock will be in free-running mode. If enabled, both daemons use the time offset to calculate the frequency offset between the slave and its master, and gradually adjust the local clock tick duration to improve the local slave clock accuracy. Furthermore, PTPd updates the slave time by adding a small percentage of time to the slave clock depending on the calculated offset.
- Maximum clock frequency adjustment: this is an upper threshold for the maximal permissible (positive or negative) frequency correction as calculated above.
- Disable/enable clock reset: if disabled, local clock adjustments per synchronization cycle are limited to the above value. If enabled, the daemon resets the clock when synchronization starts and/or when a calculated offset is larger than a configurable threshold. Resetting the clock makes the slave time the same as the master time in one synchronization step. Further on, PTP4l will also adjust the slave clock frequency before doing a clock reset.
2.4. PTP Security Concerns
2.4.1. Summary of PTP Attack Strategies
- Systematically modify PTP message content, i.e., timestamps T1, T4, C1, C2 and/or C3, in transit via a man-in-the-middle (MitM) attacker located in an intermediate node, such as a router, switch, or transparent clock. For example, Figure 3 shows the manipulation of the correctionField segment (that contains the transparent clock residence time) of PTP messages;
- Selectively delay PTP message propagation by a MitM to induce an asymmetric uplink/downlink delay;
- Directly manipulate the time reference by compromising the grandmaster clock, or by introducing a Byzantine master clock. The latter requires an ordinary clock to become a rogue master (a clock that pretends to be the best in the network) by circulating announce messages with overrated clock attributes such as the PriorityOne field with the aim to manipulate the BMCA [12]. Once the device becomes the grandmaster, it propagates inaccurate timestamps and desynchronize attached slaves, and ultimately desynchronize the entire network.
2.4.2. Summary of Existing PTP Security Measures
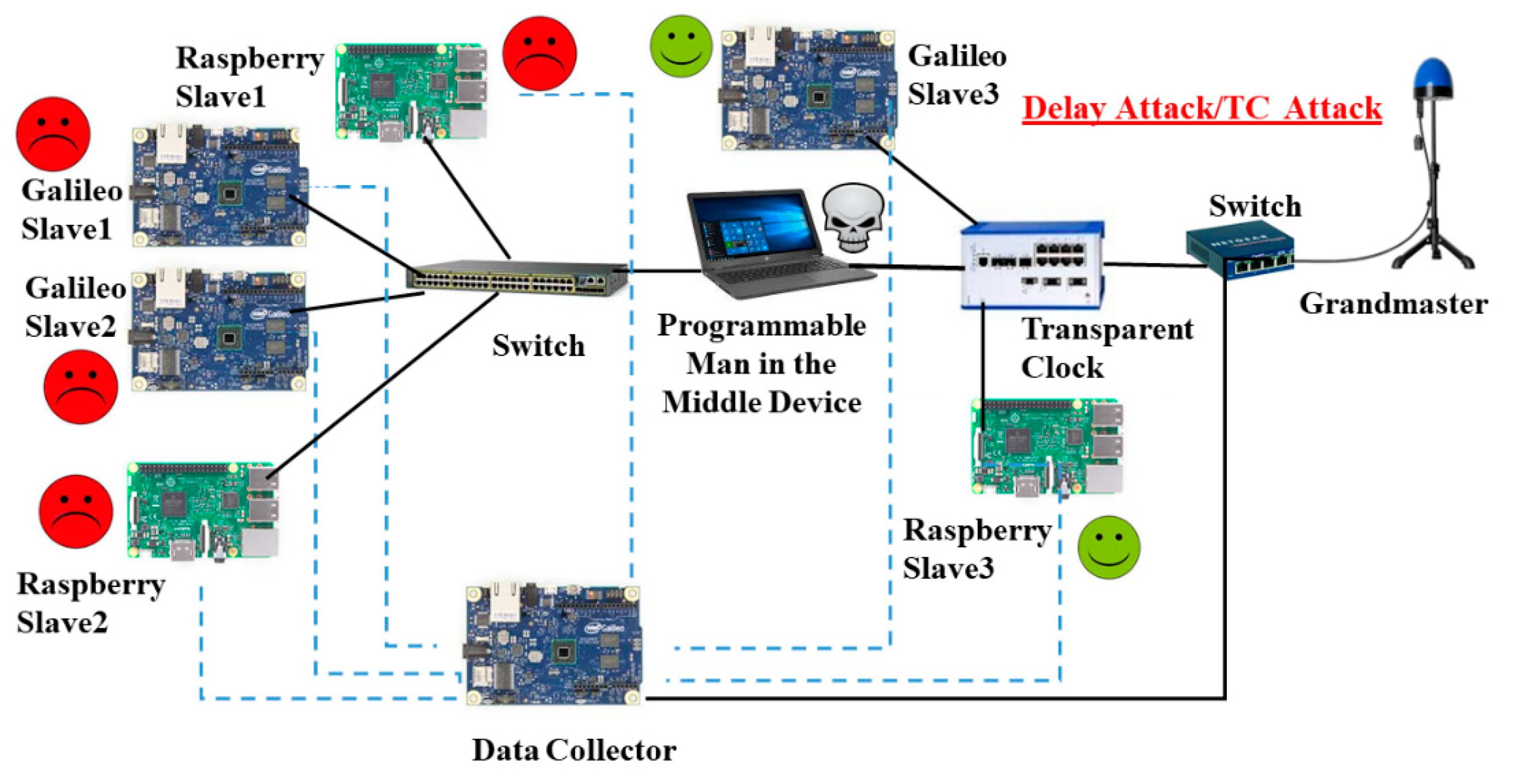
3. Testbed and MITM Device
4. Experimental Results
4.1. Attack 1: Packet Propagation Attack
4.1.1. Delayed Packet Transmission (Compromised Switch)
frequency + (T4 − C3 − (T1 + C1 + delayAsymmetry + C2)))/2
delay) − C3 − T1 + C1 + delayAsymmetry + C2)))/2
- Introduce an asymmetric delay in the path between the slaves and their master, resulting in a slave clock drift approximately half the maximum asymmetric delay (e.g., Figure 8 and Figure 9 show how the slaves drift by 10 ms as a result of a 20 ms asymmetric delay). Here smaller increments result in a small adjustment in the clock frequency and less apparent fluctuations of a slave clock offset.
- Introduce a consecutive large delay in the uplink and downlink path between the master and its slaves that makes a slave clock always slew with the maximum frequency. Here, the value of the slave clock drift is variable and subject to the PTP daemon type and the filtering mechanism that is applied. Such an attack causes an increased slave clock offset over time, which makes the attack easy to be detectable.
4.1.2. CorrectionField Manipulation (Compromised TC)
C3 − (T1 + C1 + delayAsymmetry +C2 + Err)))/2
+ Err) − (T1 + C1 + delayAsymmetry + C2)))/2
(C3 + Err) − (T1 + C1 + delayAsymmetry + C2+ Err)))/2
- In the case of PTPd, introduce an asymmetric/symmetric incremental correctionField offset in the path between the slaves and their master. Here smaller increments result in a small adjustment in the clock frequency and less apparent fluctuations of a slave clock offset and delay value. PTPd is not only vulnerable to both symmetric and asymmetric TC attacks, but its delay values are not correctly reported, making the daemon blind for these attacks.
- In the case of PTP4l, introduce an incremental asymmetric correctionField offset in the path between the slaves and their master. Here the small increment will not affect the offset values, but the delay values will decrease over time, therefore providing an indicator for this attack.
4.2. Attack 2: Time Reference Attack (Compromised TC or GM)
((T4 ± Err) − C3 − ((T1 ± Err) + C1 + delayAsymmetry + C2)))/2
5. Proposed Attack Detection System
6. Summary and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- IEEE Standard for a Precision Clock Synchronization Protocol for Networked Measurement and Control Systems; IEEE Std 1588–2008 (Revision of IEEE Std 1588–2002); IEEE: Piscataway, NJ, USA, 2008; pp. 1–269. [CrossRef]
- Estrela, P.V.; Neusüß, S.; Owczarek, W. Using a multi-source NTP watchdog to increase the robustness of PTPv2 in financial industry networks. In Proceedings of the 2014 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control, and Communication (ISPCS), Austin, TX, USA, 21–26 September 2014; pp. 87–92. [Google Scholar]
- Mizrahi, T. Time synchronization security using IPsec and MACsec. In Proceedings of the International IEEE Symposium on Precision Clock Synchronization for Measurement Control and Communication, Munich, Germany, 12–16 September 2011; pp. 38–43. [Google Scholar]
- Baize, E. Developing Secure Products in the Age of Advanced Persistent Threats. IEEE Secur. Priv. 2012, 10, 88–92. [Google Scholar] [CrossRef]
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Chen, T.; Abu-Nimeh, S. Lessons from stuxnet. Computer 2011, 44, 91–93. [Google Scholar] [CrossRef]
- Alghamdi, W.; Schukat, M. Advanced methodologies to deter internal attacks in PTP time synchronization networks. In Proceedings of the 28th Irish Signals and Systems Conference (ISSC), Killarney, Ireland, 20–21 June 2017; pp. 1–6. [Google Scholar]
- Itkin, E.; Wool, A. A Security Analysis and Revised Security Extension for the Precision Time Protocol. IEEE Trans. Dependable Secur. Comput. 2020, 17, 22–34. [Google Scholar] [CrossRef] [Green Version]
- IEEE Standard for a Precision Clock Synchronization Protocol for Networked Measurement and Control Systems; IEEE Std 1588–2019 (Revision ofIEEE Std 1588–2008); IEEE: Piscataway, NJ, USA, 2020; pp. 1–499.
- Shereen, E.; Bitard, F.; Dán, G.; Sel, T.; Fries, S. Next Steps in Security for Time Synchronization: Experiences from implementing IEEE 1588 v2.1. In Proceedings of the 2019 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control, and Communication (ISPCS), Portland, OR, USA, 22–27 September 2019; pp. 1–6. [Google Scholar]
- Maftei, D.; Bartos, R.; Noseworthy, B.; Carlin, T. Implementing proposed IEEE 1588 integrated security mechanism. In Proceedings of the 2018 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control, and Communication (ISPCS), Geneva, Switzerland, 30 September–5 October 2018; pp. 1–6. [Google Scholar]
- Alghamdi, W.; Schukat, M. Advanced Persistent Threats to Precision Time Protocol Networks: A Vulnerability Analysis. Cybersecur. under review.
- Moussa, B.; Kassouf, M.; Hadjidj, R.; Debbabi, M.; Assi, C. An Extension to the Precision Time Protocol (PTP) to Enable the Detection of Cyber Attacks. IEEE Trans. Ind. Inform. 2019, 1. [Google Scholar] [CrossRef]
- Han, M.; Crossley, P. Vulnerability of IEEE 1588 under Time Synchronization Attacks. In Proceedings of the 2019 IEEE Power & Energy Society General Meeting (PESGM), Atlanta, GA, USA, 4–8 August 2019; pp. 1–5. [Google Scholar]
- Neyer, J.; Gassner, L.; Marinescu, C. Redundant Schemes or How to Counter the Delay Attack on Time Synchronization Protocols. In Proceedings of the 2019 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control, and Communication (ISPCS), Portland, OR, USA, 22–27 September 2019; pp. 1–6. [Google Scholar]
- Garner, G.M. IEEE 1588 Version 2. ISPCS Ann. Arbor 2008, 8, 1–89. [Google Scholar]
- List of PTP Implementations. Available online: https://en.wikipedia.org/wiki/List_of_PTP_implementations (accessed on 17 April 2020).
- The Linux PTP Project. Available online: http://linuxptp.sourceforge.net/ (accessed on 18 April 2020).
- Kempen, A.; Kreuzer, S.; Neville, G.; Owczarek, W. Precision Time Protocol Daemon. Available online: https://manpages.debian.org/testing/ptpd/ptpd.8.en.html (accessed on 18 April 2020).
- GitHub. PTPd. Available online: https://github.com/ptpd (accessed on 5 May 2020).
- Correll, K.; Barendt, N.; Branicky, M. Design Considerations for Software Only Implementations of the IEEE 1588 Precision Time Protocol. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.480.8451&rep=rep1&type=pdf (accessed on 25 August 2020).
- GitHub. linuxptp. Available online: https://github.com/openil/linuxptp (accessed on 25 August 2020).
- NASPI Time Synchronization Task Force. Time Synchronization in the Electric Power System; Technical Report; North American Synchrophasor Initiative: Washington, DC, USA, 2017. [Google Scholar]
- Ullmann, M.; Vögeler, M. Delay attacks—Implication on NTP and PTP time synchronization. In Proceedings of the 2009 International Symposium on Precision Clock Synchronization for Measurement, Control and Communication, Brescia, Italy, 12–16 October 2009; pp. 1–6. [Google Scholar]
- Moussa, B.; Debbabi, M.; Assi, C. A Detection and Mitigation Model for PTP Delay Attack in an IEC 61850 Substation. IEEE Trans. Smart Grid 2018, 9, 3954–3965. [Google Scholar] [CrossRef]
- Mizrahi, T. Security Requirements of Time Protocols in Packet Switched Networks; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2014. [Google Scholar]
- Narula, L.; Humphreys, T.E. Requirements for Secure Clock Synchronization. IEEE J. Sel. Top. Signal Process. 2018, 12, 749–762. [Google Scholar] [CrossRef]
- Koskiahde, T.; Kujala, J. PTP monitoring in redundant network. In Proceedings of the 2016 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control, and Communication (ISPCS), Stockholm, Sweden, 4–9 September 2016; pp. 1–5. [Google Scholar]
- Dalmas, M.; Rachadel, H.; Silvano, G.; Dutra, C. Improving PTP robustness to the byzantine failure. In Proceedings of the 2015 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control, and Communication (ISPCS), Beijing, China, 11–16 October 2015; pp. 111–114. [Google Scholar]
- Shpiner, A.; Revah, Y.; Mizrahi, T. Multi-path Time Protocols. In Proceedings of the 2013 IEEE International Symposium on Precision Clock Synchronization for Measurement, Control and Communication (ISPCS), Lemgo, Germany, 22–27 September 2013; pp. 1–6. [Google Scholar]
- IEEE Draft Standard for a Precision Clock Synchronization Protocol for Networked Measurement and Control Systems; IEEE: Piscataway, NJ, USA, 2019; pp. 1–535.
- Girela-López, F.; López-Jiménez, J.; Jiménez-López, M.; Rodríguez, R.; Ros, E.; Díaz, J. IEEE 1588 high accuracy default profile: Applications and challenges. IEEE Access 2020, 8, 45211–45220. [Google Scholar] [CrossRef]
- Shannon, J.; Melvin, H.; Ruzzelli, A.G. Dynamic flooding time synchronisation protocol for WSNs. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 365–371. [Google Scholar]
- ITU. G.8275.2: Precision Time Protocol Telecom Profile for Time/Phase Synchronization with Partial Timing Support from the Network. Available online: https://www.itu.int/rec/T-REC-G.8275.2-202003-I/en (accessed on 21 June 2020).
- ST 2059-2:2015—SMPTE Standard—SMPTE Profile for Use of IEEE-1588 Precision Time Protocol in Professional Broadcast Applications; ST 2059-2:2015; The Society of Motion Picture and Television Engineers (SMPTE): White Plains, NY, USA, 2015; pp. 1–19. ISBN 9781614828648.






























| Configuration | Clock Characteristics after 20 min | |||
|---|---|---|---|---|
| Offset | Mean Path Delay | |||
| Average (µs) | Standard Deviation (µs) | Average (µs) | Standard Deviation (µs) | |
| Galileo without MitM | −0.066 | 15 | 424 | 3 |
| Galileo with MitM | −0.031 | 30 | 537 | 6 |
| Raspberry without MitM | 0.125 | 8 | 169 | 1 |
| Raspberry with MitM | 0.065 | 14 | 280 | 2 |
| Attack Type | Typical Attacker Location |
|---|---|
| Delayed packet transmission | Switch |
| correctionField manipulation | TC |
| GM timestamp manipulation | TC |
| Byzantine attack | GM |
| Parameter | Setting | Comment |
|---|---|---|
| Delay mechanism | End-to-End | The ordinary switches used do not support peer delay mechanism |
| Operation Mode | Two-Step | Slave NIC does not support HW timestamping |
| IP protocol | Version 4 | - |
| Log Sync Interval | 0 | The master sends a Sync message every 20 s |
| Log Announce Interval | 1 | The master sends an Announce message each 21 s |
| Announce receipt timeout | 3 | After 3 unsuccessful announce intervals a slave clock will change into free-running mode |
| Log delay request interval | 0 | The slave sends a new Delay_Req message every 20 s |
| Clock Frequency | 512 ppm | Maximum absolute frequency change that can be applied to the clock servo |
| Clock Adjustment | enabled | Slave clock update enabled |
| Clock Reset & Step threshold (PTP4l) | On start-up | Reset the clock only at the beginning of the synchronization |
| Clock Reset & Step threshold (PTPd) | offset >1 s | Reset the clock only if the offset from the master is greater than one second |
| Experiment No | Attack Parameters | |||||||
|---|---|---|---|---|---|---|---|---|
| Delay Increment between Cycles | Interval | Duration of Attack | Delay Type | PTP Daemon | Accumulated Slave Clock Drift | Offset Average | Delay Average | |
| 1 | 5 ms | 1 s | 200 s | Asymmetric | PTP4l | 93 ms | 226 ms | 234 ms |
| PTPd | 101 ms | 164 ms | 74 ms | |||||
| Symmetric | PTP4l | 84 ms | 24 ms | 432 ms | ||||
| PTPd | 61 ms | 51 ms | 187 ms | |||||
| 2 | 10 µs | 1 s | 910 s | Asymmetric | PTP4l | 5 ms | 8.6 µs | 2.8 ms |
| PTPd | 5 ms | 13 µs | 1 ms | |||||
| Symmetric | PTP4l | 0 | 13 µs | 5 ms | ||||
| PTPd | 0 | −3.3 µs | 2.4 ms | |||||
| 3 | 20 ms (once-off increment) | - | 910 s | Asymmetric | PTP4l | 10 ms | 135 µs | 10 ms |
| PTPd | 10 ms | 75 µs | 9 ms | |||||
| Symmetric | PTP4l | 0 | 114 µs | 20 ms | ||||
| PTPd | 0 | 268 µs | 17 ms | |||||
| Experiment No | Attack Parameters | |||||||
|---|---|---|---|---|---|---|---|---|
| Correction Field Timestamp Increment between Cycles | Interval | Duration of Attack | Increment Type | PTP Daemon | Accumulated Slave Clock Drift | Offset Average | Delay Average | |
| 1 | 5 ms | 10 s | 200 s | Asymmetric | PTP4l | −50 ms | −1 ms | −22.8 ms |
| PTPd | −98 ms | −2.2 ms | 116 µs | |||||
| Symmetric | PTP4l | −3 ms | −0.807 µs | −48 ms | ||||
| PTPd | −75 ms | −2.3 ms | 28 µs | |||||
| 2 | 10 µs | 10 s | 910 s | Asymmetric | PTP4l | −230 µs | 6 µs | 388 µs |
| PTPd | −326 µs | −0.802 µs | 163 µs | |||||
| Symmetric | PTP4l | ≈ 0 | −0.077 µs | 108.5 µs | ||||
| PTPd | −500 µs | −0.822 | 114 µs | |||||
| Experiment No | Attack Parameters | |||||||
|---|---|---|---|---|---|---|---|---|
| Grandmaster Timestamp Increment between Cycles | Interval | Duration of Attack | Increment Type | PTP Daemon | Accumulated Slave Clock Drift | Offset Average | Delay Average | |
| 1 | 5 ms | 10 s | 200 s | Symmetric | PTP4l | −92 ms | −3.2 ms | 452 µ |
| PTPd | −101 ms | −2.3 ms | 310 µ | |||||
| 2 | 10 µs | 10 s | 910 s | PTP4l | −910 µ | −0.913 µ | 583 µ | |
| PTPd | −910 µ | −16 µ | 315 µ | |||||
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alghamdi, W.; Schukat, M. Cyber Attacks on Precision Time Protocol Networks—A Case Study. Electronics 2020, 9, 1398. https://doi.org/10.3390/electronics9091398
Alghamdi W, Schukat M. Cyber Attacks on Precision Time Protocol Networks—A Case Study. Electronics. 2020; 9(9):1398. https://doi.org/10.3390/electronics9091398
Chicago/Turabian StyleAlghamdi, Waleed, and Michael Schukat. 2020. "Cyber Attacks on Precision Time Protocol Networks—A Case Study" Electronics 9, no. 9: 1398. https://doi.org/10.3390/electronics9091398
APA StyleAlghamdi, W., & Schukat, M. (2020). Cyber Attacks on Precision Time Protocol Networks—A Case Study. Electronics, 9(9), 1398. https://doi.org/10.3390/electronics9091398





