BESTIE: Broadcast Encryption Scheme for Tiny IoT Equipment
Abstract
1. Introduction
1.1. Broadcast Encryption
1.2. BE for Tiny Equipment
- Secure multicast: The research of Reference [3] already justified the usage of BE for secure multicast. To be more specific, an IoT system manager may want to broadcast and distribute secure messages to the devices by using the subset difference of IPv6 address bit string. Current IoT equipment commonly utilize chips that have 4 KB to 128 KB of non-volatile memory (EEPROM or on-chip flash). Some devices tend to use trusted platform module (TPM) chips that can store and manage keys securely, and the TPM key storage also has a size of no more than 16 KB. (ATmega 128 microprocessor has 128 KB flash and 4 KB EEPROM, and Atmel TPM series provide 16 KB of non-volatile key storage [8]).
- Engine control unit (ECU) firmware management: The engine control unit (ECU) of a vehicle is known to have a key storage for its code and data encryption. In time-to-time firmware updates, the system needs to set privileged devices either to guarantee customized firmwares for different vehicles or to revoke the disclosed keys that are often used by other vendors. BE can provide an appropriate environment for the large scale of ECU firmware encryption management. The non-volatile on-chip memory of the ECU usually has a size of no more than 12 KB.
1.3. BESTIE with Short-Key
1.4. Contributions
- Theoretical advance: The proposed BESTIE resolves a challenging problem to reduce the private key size to in the SD-based BE approach, without sacrificing any other efficiency. Moreover, BESTIE is compatible with even CSD, which is more expressive, and is thus more compact than SD.
- Practicality: The BESTIE is applicable to large scale IoT systems ( devices) with a reasonable performance; it requires only 7 KB private key size while the private key size is more than 600 KB in the other existing SD-based approaches.
- Implementation: We implement the proposed protocol on the Intel Edison 500 Mhz IoT device. The implementation result can be directly utilized for various IoT applications, such as secure multicast and ECU firmware updates.
- Security: We prove that the BESTIE is collusion resistant and IND-sID-CPA-secure under the l-Simplified Multi-Exponent Bilinear Diffie-Hellman (l-SMEBDH) assumption (without the random oracle model). We also provide an IND-sID-CCA-secure version of the scheme.
2. Related Work
- Stateful vs. stateless: There are two types of BE schemes, which are stateful schemes [24,26,27] and stateless schemes [1,10,22]. In the stateful BE scheme, the key exchange occurs more than once. On the other hand, the stateless BE scheme allows the key exchange only once in the initial setup. Stateful schemes can be useful in a setting that can allow users to interact after the initial setup. However, in real practice, such as Pay-TV systems or IoT networks, once the devices are deployed, it becomes a big burden to update all keys synchronously.
- Symmetric vs. asymmetric: The BE can be also categorized as a symmetric BE [10,25] and asymmetric BE. In the symmetric BE, only a trusted user who has a symmetric key can encrypt and broadcast the message to the receivers. An asymmetric BE, known as a public key broadcast encryption (PKBE), enables any user to broadcast the encrypted information.
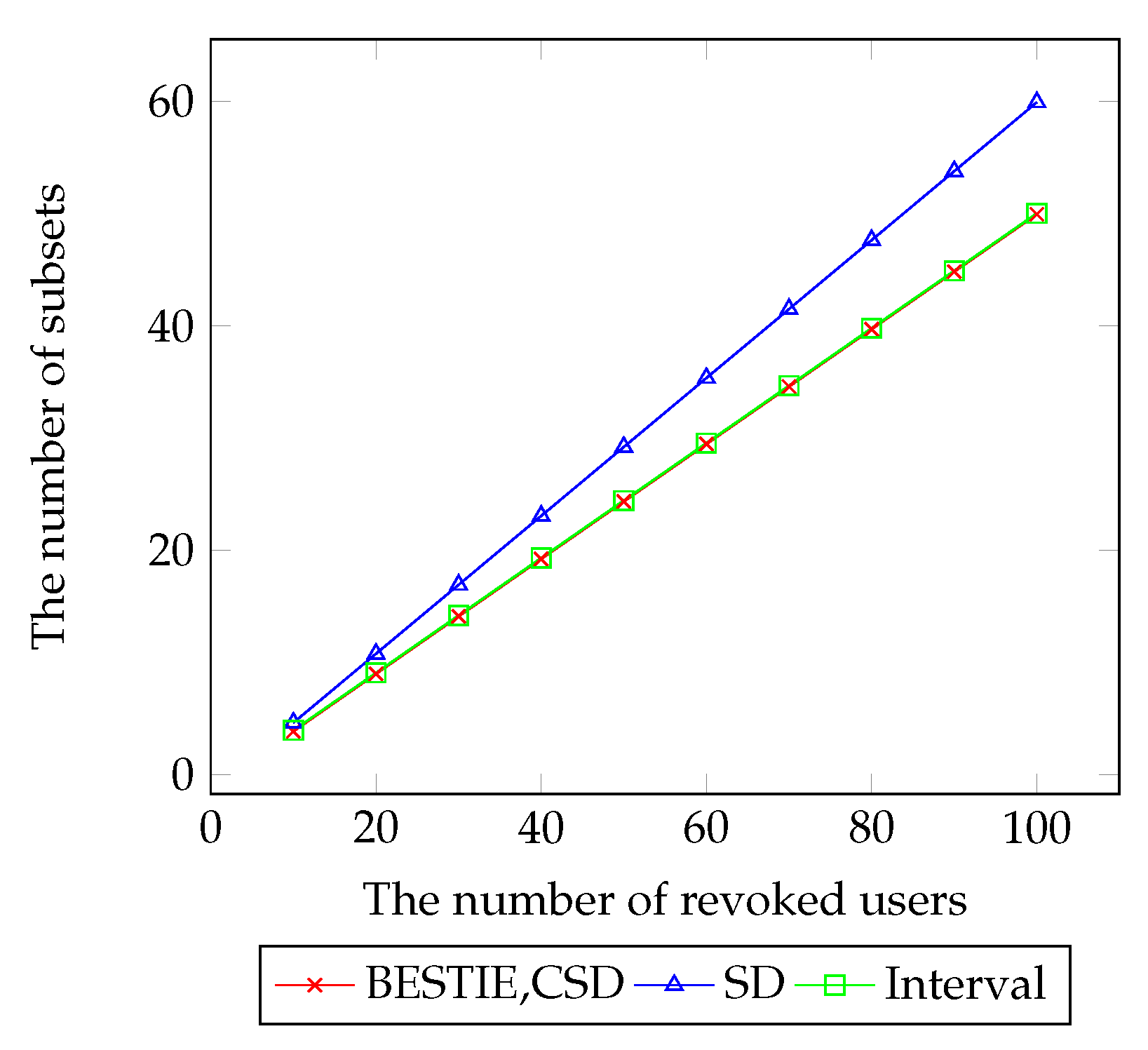
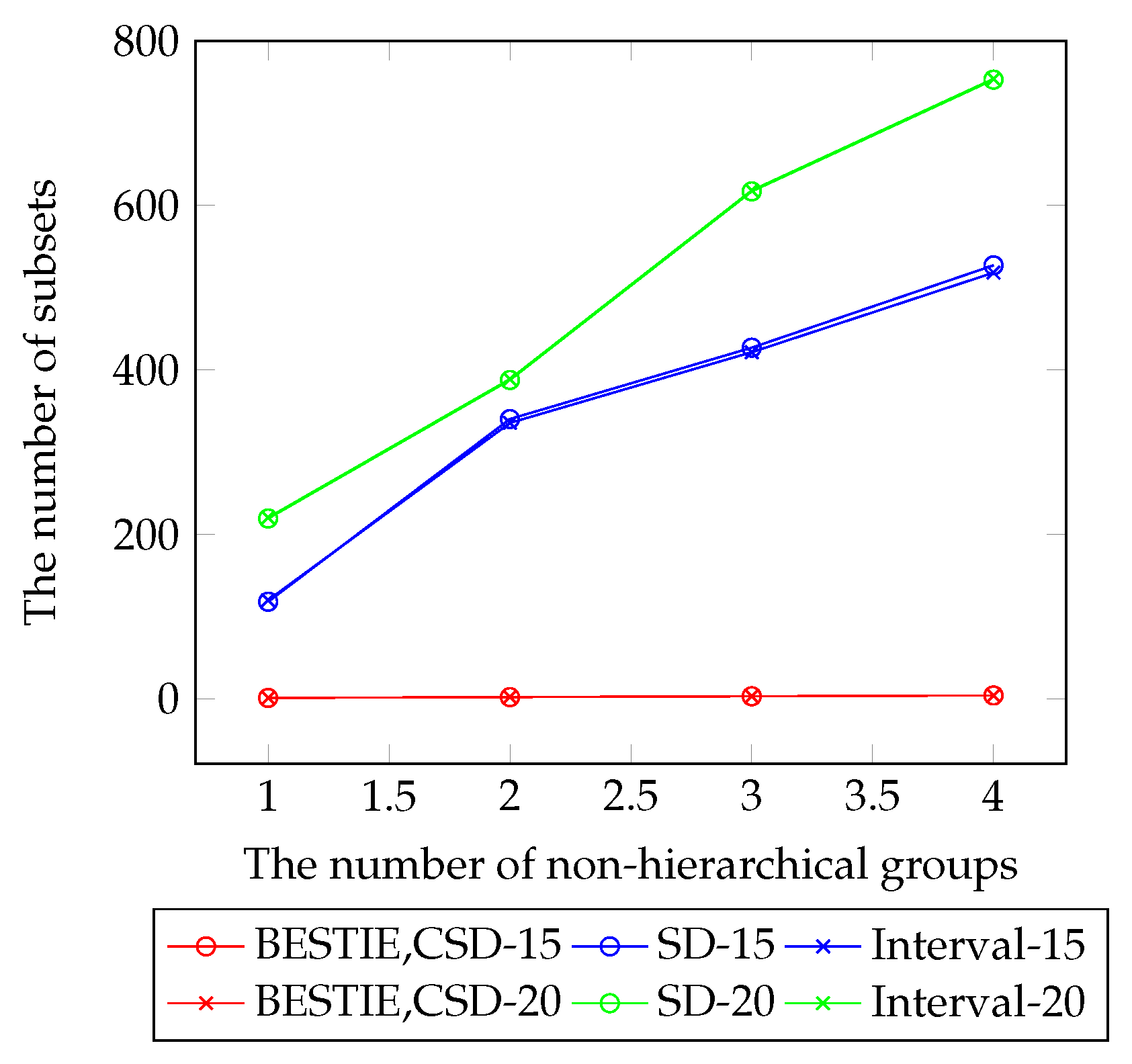
- lHeader size: The main objective of the BE research was to reduce the header size, which decides the transmission overhead. Since the header size relies on the number of subsets, there were many works that proposed subset construction/representation methods [2,10,11,22]. The most common representations were the complete subtree (CS) [11], the subset difference (SD) [11], and the interval encryption [2]. The CS method covers users with root nodes of subtrees. The SD method covers users with a subtraction of two subtrees. The interval encryption covers users with ranges of privileged users. Recently, the work of Reference [3] proposed a combinatorial subset difference (CSD), which covers users with a subtraction of two non-hierarchical bit-labels. The SD scheme has a header size of , the interval scheme has a header size of , and the CSD scheme has a header size of , each for the worst cases when r is the number of revoked users.
- Key size: Some works have focused on reducing the PK/SK size of BE, although there usually is a trade-off between the size and the encryption/decryption time. The work of Reference [6] has succeeded on reducing the SK size to the order of in the subset difference. The interval scheme also obtained an order of for the SK size. Until now, even a symmetric key BE (which is limited, but more generally efficient) has a boundary of for the size of SK.
2.1. SD-Based BE
2.2. Attribute-Based Encryption
3. Preliminaries
3.1. Public Key Broadcast Encryption
- takes user’s ID bit-length l and session key length as inputs. It outputs public parameters and a master key .
- takes user’s l-bit , master key , and public key as inputs. It outputs a private key set .
- takes a subset S, and a public key and a message M as inputs. It outputs a broadcast ciphertext for the subset S.
- takes a subset S, a user id , private key for user , and a header as inputs. If , then it outputs message M.
3.2. Security Model
- Init:
- Algorithm outputs a set of users to attack.
- Setup:
- The challenger performs to obtain a public key and a master key .
- KeyGen:
- The challenger runs to obtain private keys , ⋯, . then provides with the public key and all private keys for .
- Phase 1:
- (optional for CCA) Attacker adaptively issues decryption queries where a decryption query consists of the triple with and . responds with .
- Challenge:
- For the challenge, algorithm outputs two messages and . picks , encrypts the message by running to obtain , and gives to the attacker .
- Phase 2:
- (optional for CCA) Attacker continues to adaptively issue decryption queries , ⋯, where a decryption query consists of with and . The only constraint is that . responds as in query phase 1.
- Guess:
- Attacker produces its guess for and wins the game if .
- Init:
- Algorithm outputs a set of users to attack.
- Setup:
- The challenger executes to obtain a public key and a master key .
- KeyGen:
- The challenger runs to obtain private keys , ⋯, . gives all private keys for where .
- Phase 1:
- (optional for CCA) Attacker adaptively issues decryption queries where a decryption query consists of the triple with and . responds with .
- Challenge:
- For the challenge, algorithm outputs two messages and . picks , encrypts the message by running to obtain for , and gives all to the attacker .
- Phase 2:
- (optional for CCA) Attacker continues to adaptively issue decryption queries , ⋯, where a decryption query consists of with and . The only constraint is that . responds as in query phase 1.
- Guess:
- Attacker provides its guess for and wins the game if .
3.3. Bilinear Groups
- , and are (multiplicative) cyclic groups of prime order p.
- and are generators of and , respectively.
- denotes a bilinear map.
- Bilinear: for all , and , we have
- Non-degenerate: .
3.4. Computational Complexity Assumptions
3.5. Combinatorial Subset Difference
4. Proposed Broadcast Encryption Scheme
4.1. Main Idea
4.2. Construction
- Setup():
- This algorithm first generates the bilinear groups , of prime order p of bit size . It selects random elements and . It selects a random exponent . It chooses random group elements , . It outputs a master key and a public key as
- KeyGen():
- This algorithm takes as input , the master key , and the public key . It chooses random exponents and and outputs a private key as
- Encrypt():
- This algorithm takes S = (,) = (, ) as input labels, the public key , and a message as inputs. It selects a random exponent and outputs a ciphertext by implicitly including as
- Decrypt():
- This algorithm takes a subset , a user’s , a private key , and a ciphertext for S as inputs. Let and . Let d denote the number of bits, which, in , are different from or .
4.3. Complexity Analysis
4.4. Security Proof
- Init:
- The game begins with outputting a subset to attack where , .
- Setup:
- To generate the public key, algorithm chooses random exponents , , , and sets , for and , and . Let .
- KeyGen:
- To generate a private key for user , algorithm considers the following three cases.
- (i)
- :Algorithm chooses random exponents and and sets where .Algorithm can easily compute ,since =.Algorithm computes as follows:Algorithm computes , , , and z as follows:
- (ii)
- and :Algorithm selects random exponents and u and sets . It sets .Algorithm can compute , since .Algorithm computes as follows:Algorithm computes , , , and z as follows:Note that if .If then since .
- (iii)
- and :Algorithm does not require the , since .
- Challenge:
- Algorithm submits challenge labels and two messages , . If , then Algorithm aborts the simulation since it failed to guess the challenge labels. Otherwise, flips a random coin internally. implicitly sets and creates a challenge ciphertext as
- Guess:
- Finally, outputs a guess . Algorithm concludes its own game by producing a guess as follows. If then outputs 1 meaning . Otherwise, it outputs 0 meaning that T is random in .
5. CCA-Secure Broadcast Encryption
5.1. General ID Scheme
5.2. CCA-Secure Scheme
- Verify if is valid against under the key . If invalid, output ⊥.
- Otherwise, encode to , execute( and output the message M.
5.3. Complexity Analysis
5.4. Security Proof
- for
- for and .
- Perform to check the signature against with verification key . If the signature is invalid, then returns ⊥.
- If , then a forge event happens, and algorithm outputs a random bit and aborts the simulation.
- Otherwise, decrypts the header using the second type of secret keys.
6. Experiment
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Naor, M.; Pinkas, B. Efficient trace and revoke schemes. In Financial Cryptography; Springer: Berlin/Heidelberg, Germany, 2001; pp. 1–20. [Google Scholar]
- Lin, H.; Cao, Z.; Liang, X.; Zhou, M.; Zhu, H.; Xing, D. How to construct interval encryption from binary tree encryption. In Proceedings of the International Conference on Applied Cryptography and Network Security, Beijing, China, 2–25 June 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 19–34. [Google Scholar]
- Lee, J.; Lee, S.; Kim, J.; Oh, H. Combinatorial Subset Difference—IoT-Friendly Subset Representation and Broadcast Encryption. Sensors 2020, 20, 3140. [Google Scholar] [CrossRef] [PubMed]
- Dodis, Y.; Fazio, N. Public Key Broadcast Encryption for Stateless Receivers. In ACM Workshop on Digital Rights Management; Feigenbaum, J., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2696, pp. 61–80. [Google Scholar]
- Boneh, D.; Gentry, C.; Waters, B. Collusion Resistant Broadcast Encryption with Short Ciphertexts and Private Keys. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Shoup, V., Ed.; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2005; Volume 3621, pp. 258–275. [Google Scholar]
- Lee, K.; Koo, W.K.; Lee, D.H.; Park, J.H. Public-key revocation and tracing schemes with subset difference methods revisited. In European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2014; pp. 1–18. [Google Scholar]
- Fukami, A.; Ghose, S.; Luo, Y.; Cai, Y.; Mutlu, O. Improving the reliability of chip-off forensic analysis of NAND flash memory devices. Digit. Investig. 2017, 20, S1–S11. [Google Scholar] [CrossRef]
- Zhang, H.; Qin, Z.; Yang, Q. Design and Implementation of the TPM chip J3210. In Proceedings of the 2008 Third Asia-Pacific Trusted Infrastructure Technologies Conference, Hubei, China, 14–17 October 2008; pp. 72–78. [Google Scholar]
- Su, Y.; Holleman, J.; Otis, B.P. A digital 1.6 pJ/bit chip identification circuit using process variations. IEEE J. Solid State Circuits 2008, 43, 69–77. [Google Scholar] [CrossRef]
- Goodrich, M.T.; Sun, J.Z.; Tamassia, R. Efficient Tree-Based Revocation in Groups of Low-State Devices. In Advances in Cryptology—CRYPTO 2004; Franklin, M.K., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3152, pp. 511–527. [Google Scholar]
- Naor, D.; Naor, M.; Lotspiech, J. Revocation and Tracing Schemes for Stateless Receivers. In Advances in Cryptology—CRYPTO 2001; Kilian, J., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; Volume 2139, pp. 41–62. [Google Scholar]
- Naor, M.; Pinkas, B. Efficient trace and revoke schemes. Int. J. Inf. Secur. 2010, 9, 411–424. [Google Scholar] [CrossRef]
- Boneh, D.; Waters, B. A fully collusion resistant broadcast, trace, and revoke system. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; ACM: New York, NY, USA, 2006; pp. 211–220. [Google Scholar]
- Delerablée, C. Identity-based broadcast encryption with constant size ciphertexts and private keys. In Advances in Cryptology—ASIACRYPT 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 200–215. [Google Scholar]
- Boneh, D.; Hamburg, M. Generalized identity based and broadcast encryption schemes. In Advances in Cryptology—ASIACRYPT 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 455–470. [Google Scholar]
- Boneh, D.; Sahai, A.; Waters, B. Fully collusion resistant traitor tracing with short ciphertexts and private keys. In Advances in Cryptology—EUROCRYPT 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 573–592. [Google Scholar]
- Gentry, C.; Waters, B. Adaptive Security in Broadcast Encryption Systems (with Short Ciphertexts). In Advances in Cryptology—EUROCRYPT 2009, Proceedings of the 28th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cologne, Germany, 26–30 April 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 171–188. [Google Scholar] [CrossRef]
- Yao, D.; Fazio, N.; Dodis, Y.; Lysyanskaya, A. ID-based Encryption for Complex Hierarchies with Applications to Forward Security and Broadcast Encryption. In Proceedings of the ACM Conference on Computer and Communications Security, Washington, DC, USA, 25–29 October 2004; ACM: New York, NY, USA, 2004; pp. 354–363. [Google Scholar] [CrossRef]
- Canetti, R.; Halevi, S.; Katz, J. Chosen-Ciphertext Security from Identity-Based Encryption. In Advances in Cryptology—EUROCRYPT 2004, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 207–222. [Google Scholar] [CrossRef]
- Boneh, D.; Boyen, X.; Goh, E. Hierarchical Identity Based Encryption with Constant Size Ciphertext. In Advances in Cryptology—EUROCRYPT 2005, Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3494, pp. 440–456. [Google Scholar] [CrossRef]
- Fiat, A.; Naor, M. Broadcast Encryption. In Advances in Cryptology—CRYPTO’93; Stinson, D.R., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1993; Volume 773, pp. 480–491. [Google Scholar]
- Halevy, D.; Shamir, A. The LSD Broadcast Encryption Scheme. In Advances in Cryptology—CRYPTO 2002; Yung, M., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2002; Volume 2442, pp. 47–60. [Google Scholar]
- Wallner, D.M.; Harder, E.J.; Agee, R.C. Key Management for Multicast: Issues and Architectures. Internet Draft. Available online: https://www.hjp.at/(de,st_b)/doc/rfc/rfc2627.html (accessed on 27 August 2020).
- Canetti, R.; Malkin, T.; Nissim, K. Efficient communication-storage tradeoffs for multicast encryption. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; Springer: Berlin/Heidelberg, Germany, 1999; pp. 459–474. [Google Scholar]
- Cheon, J.H.; Jho, N.; Kim, M.; Yoo, E.S. Skipping, Cascade, and Combined Chain Schemes for Broadcast Encryption. IEEE Trans. Inf. Theory 2008, 54, 5155–5171. [Google Scholar] [CrossRef]
- Canetti, R.; Garay, J.; Itkis, G.; Micciancio, D.; Naor, M.; Pinkas, B. Multicast security: A taxonomy and some efficient constructions. In IEEE INFOCOM’99. Conference on Computer Communications, Proceedings of the Eighteenth Annual Joint Conference of the IEEE Computer and Communications Societies, New York, NY, USA, 21–25 March 1999; IEEE: Piscataway, NJ, USA, 1999; Volume 2, pp. 708–716. [Google Scholar]
- Sherman, A.T.; McGrew, D.A. Key establishment in large dynamic groups using one-way function trees. IEEE Trans. Softw. Eng. 2003, 29, 444–458. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Emura, K.; Miyaji, A.; Nomura, A.; Omote, K.; Soshi, M. A Ciphertext-Policy Attribute-Based Encryption Scheme with Constant Ciphertext Length. In Proceedings of the 5th International Conference on Information Security Practice and Experience, ISPEC, Xi’an, China, 13–15 April 2009; pp. 13–23. [Google Scholar]
- Zhou, Z.; Huang, D. On efficient ciphertext-policy attribute based encryption and broadcast encryption: Extended abstract. In Proceedings of the 17th ACM Conference on Computer and Communications Security, CCS, Chicago, IL, USA, 4–8 October 2010; pp. 753–755. [Google Scholar]
- Attrapadung, N.; Herranz, J.; Laguillaumie, F.; Libert, B.; De Panafieu, E.; Ràfols, C. Attribute-based encryption schemes with constant-size ciphertexts. Theor. Comput. Sci. 2012, 422, 15–38. [Google Scholar] [CrossRef]
- Joux, A. A One Round Protocol for Tripartite Diffie-Hellman. J. Cryptol. 2004, 17, 263–276. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M.K. Identity-Based Encryption from the Weil Pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef]
- Galbraith, S.D.; Paterson, K.G.; Smart, N.P. Pairings for cryptographers. Discret. Appl. Math. 2008, 156, 3113–3121. [Google Scholar] [CrossRef]
- Dubois, R.; Guillevic, A.; Breton, M.S.L. Improved Broadcast Encryption Scheme with Constant-size Ciphertext. In Proceedings of the 5th International Conference on Pairing-Based Cryptography, Beijing, China, 22–24 November 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 196–202. [Google Scholar] [CrossRef]
- Chase, M.; Maller, M.; Meiklejohn, S. Déjà Q All Over Again: Tighter and Broader Reductions of q-Type Assumptions. In Advances in Cryptology—ASIACRYPT 2016, Proceedings of the 22nd International Conference on the Theory and Application of Cryptology and Information Security, Hanoi, Vietnam, 4–8 December 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 655–681. [Google Scholar] [CrossRef]
- Boneh, D.; Canetti, R.; Halevi, S.; Katz, J. Chosen-Ciphertext Security from Identity-Based Encryption. SIAM J. Comput. 2007, 36, 1301–1328. [Google Scholar] [CrossRef]




| BESTIE | LKLP’14 | Lin’10 | DF’02 | NNL’01 | GST’04 | |
|---|---|---|---|---|---|---|
| (Ours) | [6] | [2] | [4] | [11] | [10] | |
| PK Size | N/A | N/A | ||||
| SK Size | ||||||
| CT Size | ||||||
| Enc Time | ||||||
| Dec Time | ||||||
| Enc type | Asymmetric | Asymmetric | Asymmetric | Asymmetric | Symmetric | Symmetric |
| Assumption | One-way func. | One-way func. | ||||
| ROM | No | Yes | No | No | No | No |
| BESTIE | CSD | SD(HIBE) | Interval | ||
|---|---|---|---|---|---|
| (Ours) | [3] | [4,20] | [2] | ||
| PK size | |||||
| 8 bit | 0.66 | 0.66 | 0.20 | 0.39 | |
| 16 bit | 1.29 | 1.29 | 0.35 | 0.70 | |
| 32 bit | 2.54 | 2.54 | 0.66 | 1.33 | |
| 64 bit | 5.04 | 5.04 | 1.29 | 2.58 | |
| 128 bit | 10.04 | 10.04 | 2.54 | 5.08 | |
| SK size | |||||
| 8bit | 0.53 | 3.79 | 10.04 | 2.58 | |
| 16 bit | 1.00 | 15.04 | 80.04 | 10.08 | |
| 32 bit | 1.93 | 60.04 | 640.04 | 40.08 | |
| 64 bit | 3.81 | 240.04 | 5120.04 | 160.08 | |
| 128 bit | 7.56 | 960.04 | 40960.04 | 640.08 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.; Kim, J.; Oh, H. BESTIE: Broadcast Encryption Scheme for Tiny IoT Equipment. Electronics 2020, 9, 1389. https://doi.org/10.3390/electronics9091389
Lee J, Kim J, Oh H. BESTIE: Broadcast Encryption Scheme for Tiny IoT Equipment. Electronics. 2020; 9(9):1389. https://doi.org/10.3390/electronics9091389
Chicago/Turabian StyleLee, Jiwon, Jihye Kim, and Hyunok Oh. 2020. "BESTIE: Broadcast Encryption Scheme for Tiny IoT Equipment" Electronics 9, no. 9: 1389. https://doi.org/10.3390/electronics9091389
APA StyleLee, J., Kim, J., & Oh, H. (2020). BESTIE: Broadcast Encryption Scheme for Tiny IoT Equipment. Electronics, 9(9), 1389. https://doi.org/10.3390/electronics9091389







