CNN-Based Network Intrusion Detection against Denial-of-Service Attacks
Abstract
1. Introduction
2. Related Works
2.1. IDS Datasets
2.2. Trends of IDS Studies
2.3. Trends of IDS Studies Based on Machine Learning and Deep Learning
3. Designing IDS Model Based on CNN
3.1. DoS Datasets
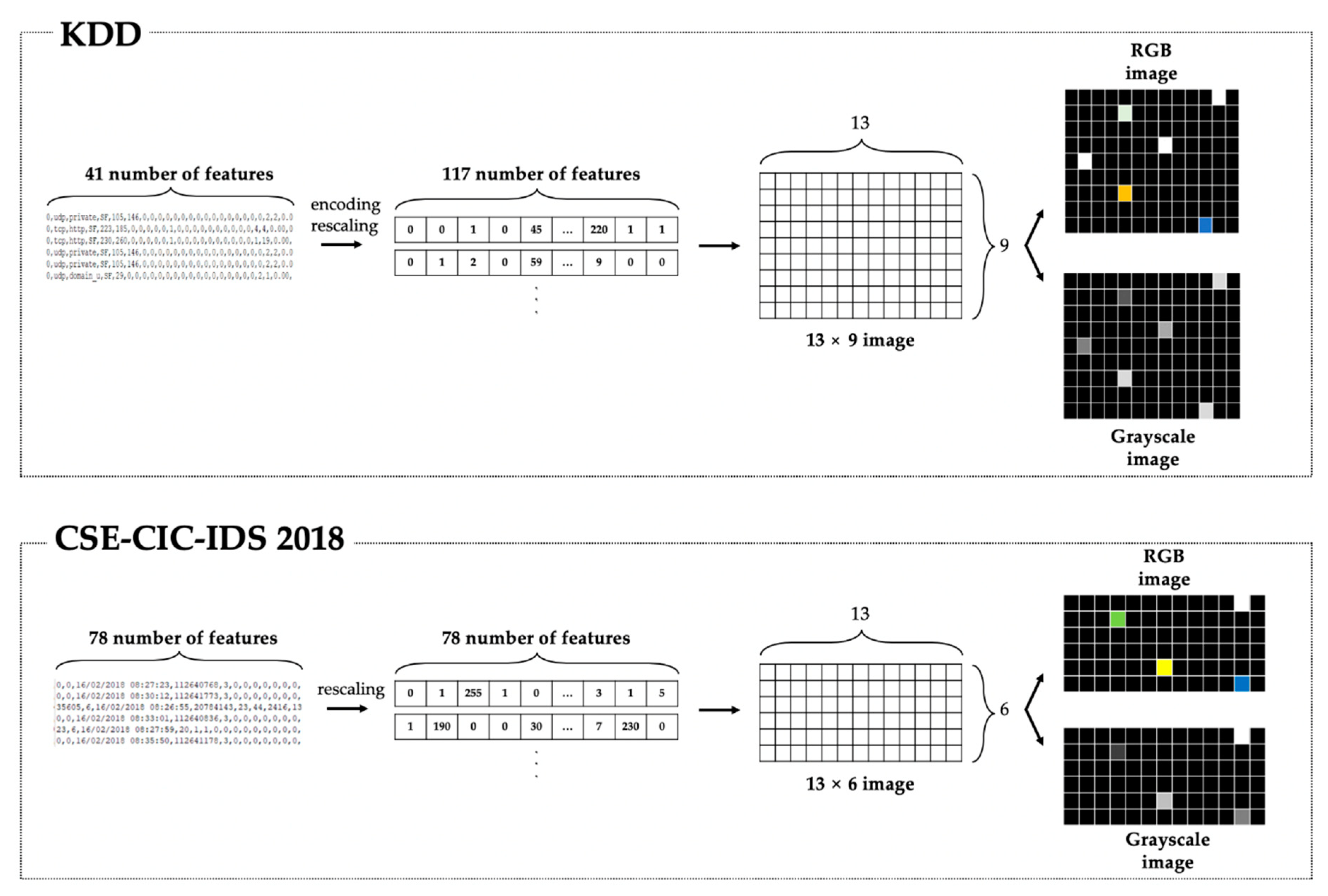
3.2. Creating the Attack Images
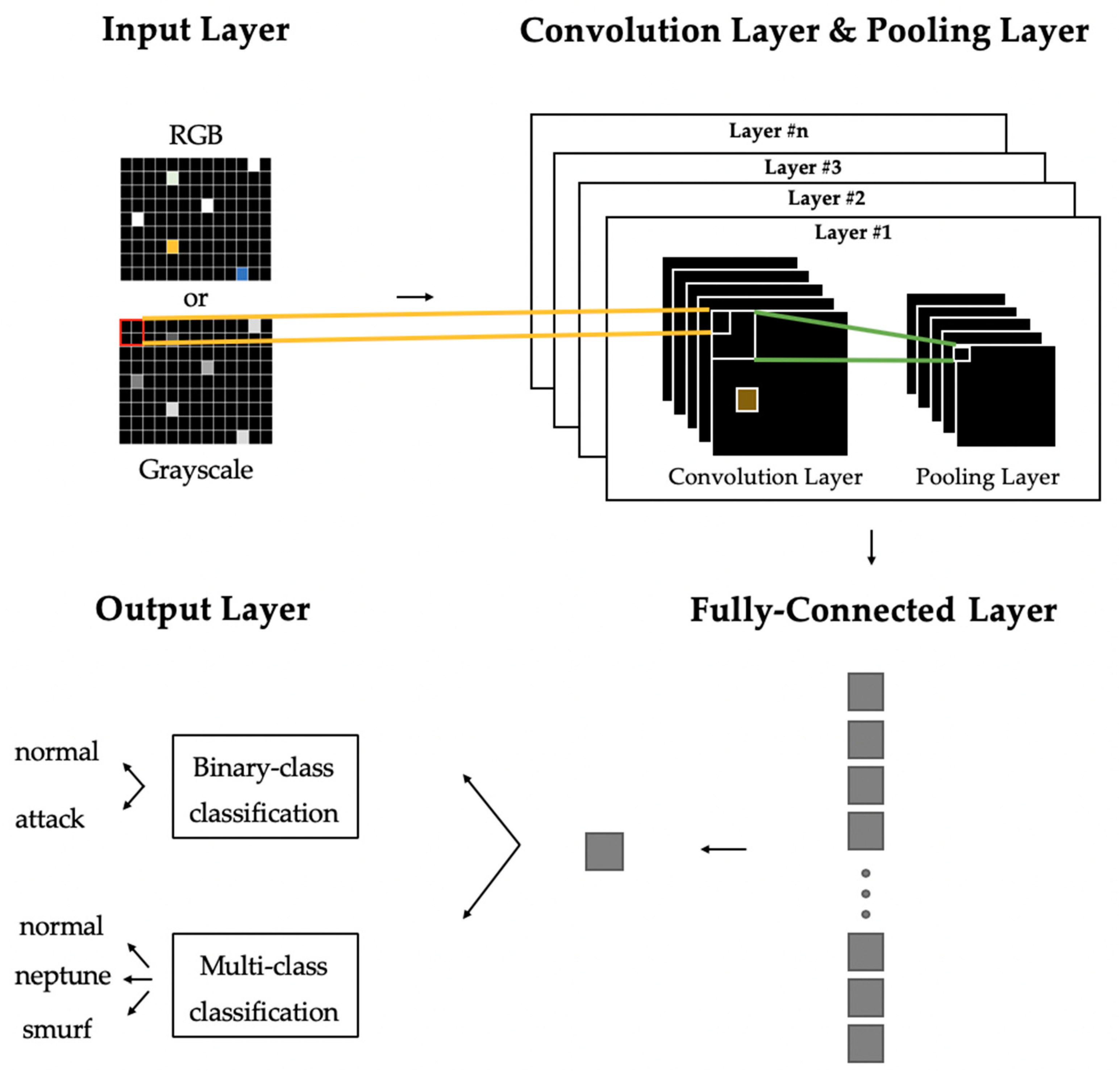
3.3. Designing CNN Model
4. Experimental Evaluation
4.1. Scenario
4.2. Evaluation of Binary Classification
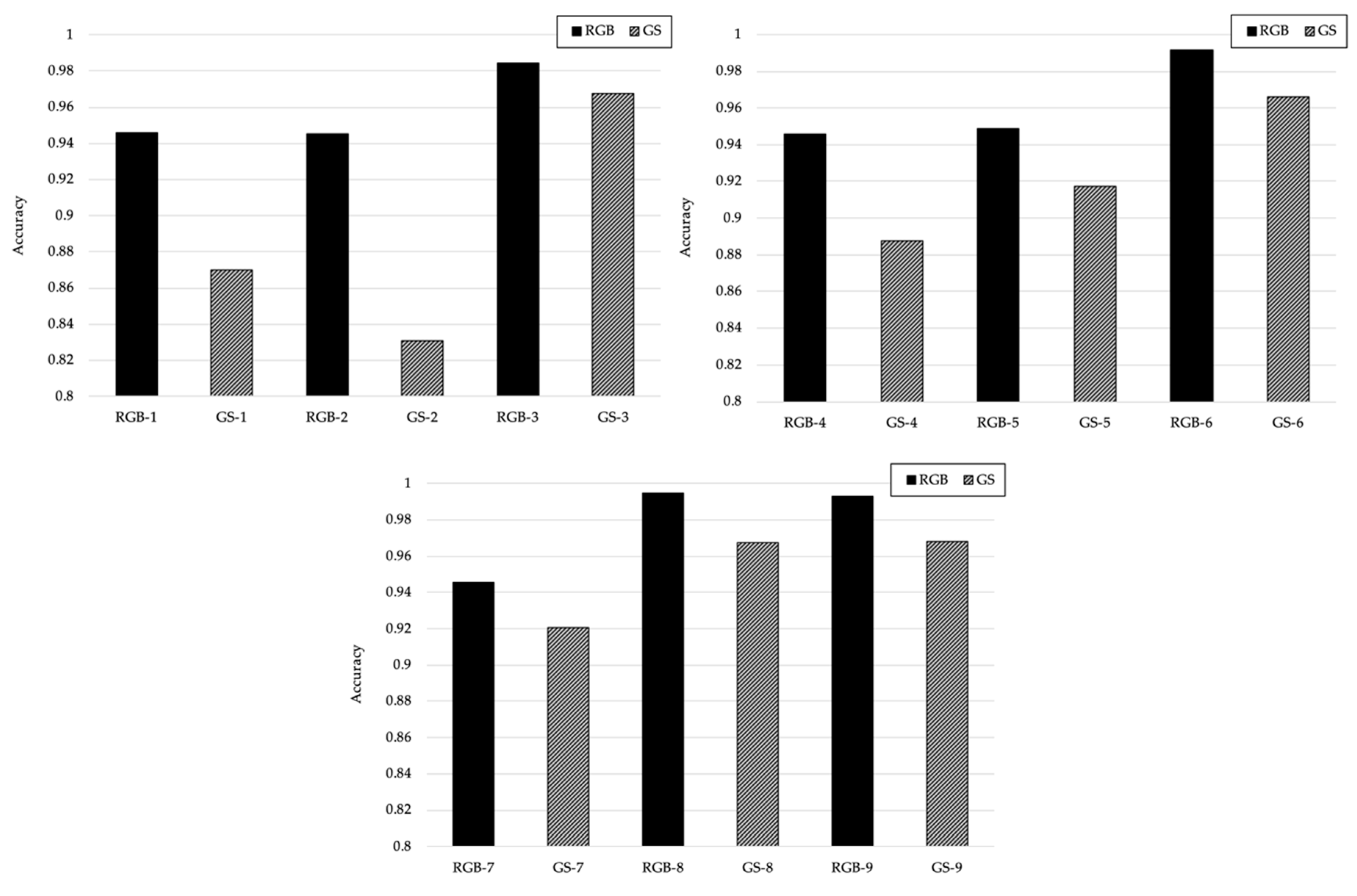
4.2.1. RGB Vs Grayscale
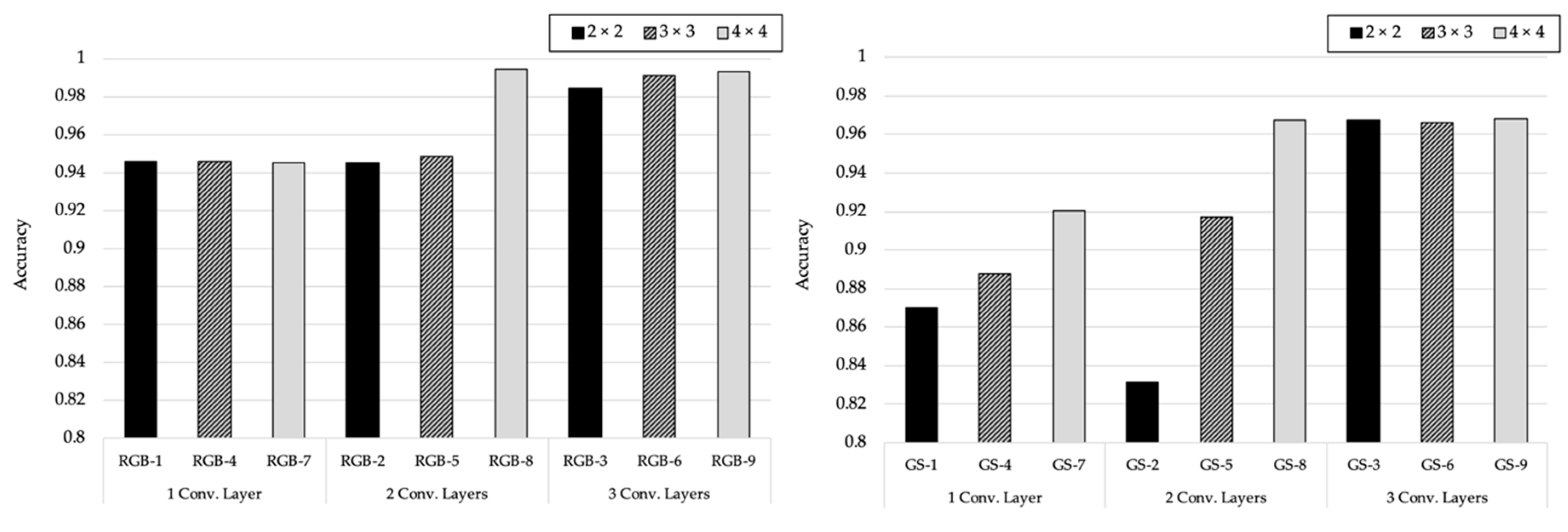
4.2.2. Number of Convolutional Layer
4.2.3. Kernel Size
4.3. Analysis of the Accuracy in Multiclass Classification
4.3.1. RGB Vs Grayscale
4.3.2. Number of Convolutional Layers
4.3.3. Kernel Size
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- KDD. KDD CUP. Available online: https://kdd.ics.uci.edu/databases/kddcup99/task.html (accessed on 17 March 2020).
- Özgür, A.; Erdem, H. A review of KDD99 dataset usage in intrusion detection and machine learning between 2010 and 2015. Peer. J. Preprints 2016, 4, e1954v1. [Google Scholar]
- Paliwal, S.; Gupta, R. Denial-of-service, probing & remote to user (R2L) attack detection using genetic algorithm. Int. J. Comput. Appl. 2012, 60, 57–62. [Google Scholar]
- Shiravi, A.; Shiravi, H.; Tavallaee, M.; Ghorbani, A.A. Toward developing a systematic approach to generate benchmark datasets for intrusion detection. Comput. Secur. 2012, 31, 357–374. [Google Scholar] [CrossRef]
- Anwar, S.; Mohamad Zain, J.; Zolkipli, M.; Inayat, Z.; Khan, S.; Anthony, B., Jr.; Chang, V. From intrusion detection to an intrusion response system: Fundamentals, requirements, and future directions. Algorithms 2017, 10, 39. [Google Scholar] [CrossRef]
- Jing-Xin, W.; Zhi-Ying, W.; Kui, D. A network intrusion detection system based on the artificial neural networks. In Proceedings of the 3rd international conference on Information security, Shanghai, China, 14–16 November 2004; pp. 166–170. [Google Scholar]
- Manso, P.; Moura, J.; Serrao, C. SDN-Based Intrusion Detection System for Early Detection and Mitigation of DDoS Attacks. Information 2019, 10, 106. [Google Scholar] [CrossRef]
- Karim, I.; Vien, Q.T.; Le, T.; Mapp, G. A comparative experimental design and performance analysis of snort-based intrusion detection system in practical computer networks. Computers 2017, 6, 6. [Google Scholar] [CrossRef]
- Xu, R.; Cheng, J.; Wang, F.; Tang, X.; Xu, J. A DRDoS Detection and Defense Method Based on Deep Forest in the Big Data Environment. Symmetry 2019, 11, 78. [Google Scholar] [CrossRef]
- Ramotsoela, D.; Abu-Mahfouz, A.; Hancke, G. A survey of anomaly detection in industrial wireless sensor networks with critical water system infrastructure as a case study. Sensors 2018, 18, 2491. [Google Scholar] [CrossRef]
- Zhang, Z.; Li, J.; Manikopoulos, C.N.; Jorgenson, J.; Ucles, J. HIDE: A hierarchical network intrusion detection system using statistical preprocessing and neural network classification. In Proceedings of the IEEE Workshop on Information Assurance and Security, West Point, NY, USA, 5–6 June 2001; pp. 85–90. [Google Scholar]
- Koc, L.; Mazzuchi, T.A.; Sarkani, S. A network intrusion detection system based on a Hidden Naïve Bayes multiclass classifier. Expert Syst. Appl. 2012, 39, 13492–13500. [Google Scholar] [CrossRef]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. Threat analysis of IoT networks using artificial neural network intrusion detection system. In Proceedings of the 2016 International Symposium on Networks, Computers and Communications (ISNCC), Hammamet, Tunisia, 11–13 May 2016; pp. 1–6. [Google Scholar]
- Chung, Y.Y.; Wahid, N. A hybrid network intrusion detection system using simplified swarm optimization (SSO). Appl. Soft Comput. 2012, 12, 3014–3022. [Google Scholar] [CrossRef]
- Aydin, M.A.; Zaim, A.H.; Ceylan, K.G. A hybrid intrusion detection system design for computer network security. Comput. Electr. Eng. 2009, 35, 517–526. [Google Scholar] [CrossRef]
- Al-Jarrah, O.; Arafat, A. Network Intrusion Detection System using attack behavior classification. In Proceedings of the 2014 5th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 1–3 April 2014; pp. 1–6. [Google Scholar]
- Karthick, R.R.; Hattiwale, V.P.; Ravindran, B. Adaptive network intrusion detection system using a hybrid approach. In Proceedings of the 2012 Fourth International Conference on Communication Systems and Networks (COMSNETS 2012), Bangalore, India, 3–7 January 2012; pp. 1–7. [Google Scholar]
- Wahab, O.A.; Bentahar, J.; Otrok, H.; Mourad, A. Resource-Aware Detection and Defense System Against Multi-Type Attacks in the Cloud: Repeated Bayesian Stackelberg Game. IEEE Trans. Dependable Secure Comput. 2019. [Google Scholar] [CrossRef]
- Wahab, O.A.; Bentahar, J.; Otrok, H.; Mourad, A. Optimal load distribution for the detection of VM-based DDoS attacks in the cloud. IEEE Trans. Dependable Secure Comput. 2017. [Google Scholar] [CrossRef]
- Chen, H.; Meng, C.; Shan, Z.; Fu, Z.; Bhargava, B.K. A Novel Low-Rate Denial of Service Attack Detection Approach in ZigBee Wireless Sensor Network by Combining Hilbert-Huang Transformation and Trust Evaluation; IEEE Access: Piscataway, NJ, USA, 2019; Volume 7, pp. 32853–32866. [Google Scholar]
- Chang, R.I.; Lai, L.B.; Su, W.D.; Wang, J.C.; Kouh, J.S. Intrusion detection by backpropagation neural networks with sample-query and attribute-query. Int. J. Comput. Intell. Res. 2007, 3, 6–10. [Google Scholar] [CrossRef]
- Staudemeyer, R.C.; Omlin, C.W. Extracting salient features for network intrusion detection using machine learning methods. S. Afr. Comput. J. 2014. [Google Scholar] [CrossRef]
- Sabhnani, M.; Serpen, G. Application of Machine Learning Algorithms to KDD Intrusion Detection Dataset within Misuse Detection Context. In Proceedings of the International Conference on Machine Learning; Models, Technologies and Applications, Las Vegas, NV, USA, 23–26 June 2003; pp. 209–215. [Google Scholar]
- Mulay, S.A.; Devale, P.R.; Garje, G.V. Intrusion detection system using support vector machine and decision tree. Int. J. Comput. Appl. 2010, 3, 40–43. [Google Scholar] [CrossRef]
- Al Mehedi Hasan, M.; Nasser, M.; Pal, B. On the KDD’99 dataset: Support vector machine based intrusion detection system (ids) with different kernels. Int. J. Electron. Commun. Comput. Eng. 2013, 4, 1164–1170. [Google Scholar]
- Yao, J.T.; Zhao, S.; Fan, L. An enhanced support vector machine model for intrusion detection. In Proceedings of the International Conference on Rough Sets and Knowledge Technology, Chongqing, China, 24–26 July 2006; pp. 538–543. [Google Scholar]
- Dong-Hoon, K.; Kim, J.-J.; Insoo, S. Studies on Intrusion Detection based on ML using KDD99CUP. In Proceedings of the Symposium of the Korean Institute of communications and Information Sciences, Jeju Island, Korea, 16–18 October 2019; pp. 861–862. [Google Scholar]
- Yin, C.; Zhu, Y.; Fei, J.; He, X. A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks; IEEE: Piscataway, NJ, USA, 2017; pp. 21954–21961. [Google Scholar]
- Sheikhan, M.; Jadidi, Z.; Farrokhi, A. Intrusion detection using reduced-size RNN based on feature grouping. Neural Comput. Appl. 2012, 21, 1185–1190. [Google Scholar] [CrossRef]
- Bontemps, L.; Cao, V.L.; Mcdermott, J.; Le-Khac, N.A. Collective anomaly detection based on long short-term memory recurrent neural networks. In Proceedings of the International Conference on Future Data and Security Engineering, Can Tho City, Vietnam, 23–25 November 2016; pp. 141–152. [Google Scholar]
- Khan, R.U.; Zhang, X.; Alazab, M.; Kumar, R. An Improved Convolutional Neural Network Model for Intrusion Detection in Networks. In Proceedings of the 2019 Cybersecurity and Cyberforensics Conference (CCC), Melbourne, Australia, 8–9 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 74–77. [Google Scholar]
- Li, Z.; Qin, Z.; Huang, K.; Yang, X.; Ye, S. Intrusion detection using convolutional neural networks for representation learning. In Proceedings of the International Conference on Neural Information Processing, Guangzhou, China, 14–18 November 2017; pp. 858–866. [Google Scholar]
- Upadhyay, R.; Pantiukhin, D. Application of convolutional neural network to intrusion type recognition. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics, Udupi, India, 13–16 September 2017. [Google Scholar]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Otawa, ON, Canada, 8–10 July 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 1–6. [Google Scholar]
- Gao, J.; Chai, S.; Zhang, B.; Xia, Y. Research on Network Intrusion Detection Based on Incremental Extreme Learning Machine and Adaptive Principal Component Analysis. Energies 2019, 12, 1223. [Google Scholar] [CrossRef]
- Chu, W.L.; Lin, C.J.; Chang, K.N. Detection and Classification of Advanced Persistent Threats and Attacks Using the Support Vector Machine. Appl. Sci. 2019, 9, 4579. [Google Scholar] [CrossRef]
- Fares, A.H.; Sharawy, M.I.; Zayed, H. Intrusion detection: Supervised machine learning. J. Comput. Sci. Eng. 2011, 5, 305–313. [Google Scholar] [CrossRef][Green Version]
- Niyaz, Q.; Sun, W.; Javaid, A.; Alam, M. A deep learning approach for network intrusion detection system. In Proceedings of the 9th EAI International Conference on Bio-inspired Information and Communications Technologies (formerly BIONETICS), New York, NY, USA, 3–5 December 2015; pp. 21–26. [Google Scholar]
- Tang, T.A.; Mhamdi, L.; McLernon, D.; Zaidi, S.A.R.; Ghogho, M. Deep learning approach for network intrusion detection in software defined networking. In Proceedings of the 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 26–29 October 2016; pp. 258–263. [Google Scholar]
- Ingre, B.; Yadav, A. Performance analysis of NSL-KDD dataset using ANN. In Proceedings of the 2015 International Conference on Signal Processing and Communication Engineering Systems, Vijayawada, India, 2–3 January 2015; pp. 92–96. [Google Scholar]
- Erol, S.E.; Benzer, R. An Application of Artificial Neural Network Based Intrusion Detection System. In Proceedings of the 5th International Management Information Systems Conference, Ankara, Turkey, 24–26 October 2018. [Google Scholar]
- Ibrahim, L.M. Anomaly network intrusion detection system based on distributed time-delay neural network (DTDNN). J. Eng. Sci. Technol. 2010, 5, 457–471. [Google Scholar]
- Tan, X.; Su, S.; Huang, Z.; Guo, X.; Zuo, Z.; Sun, X.; Li, L. Wireless Sensor Networks Intrusion Detection Based on SMOTE and the Random Forest Algorithm. Sensors 2019, 19, 203. [Google Scholar] [CrossRef]
- Farnaaz, N.; Jabbar, M.A. Random forest modeling for network intrusion detection system. Procedia Comput. Sci. 2016, 89, 213–217. [Google Scholar] [CrossRef]
- Ye, K. Key Feature Recognition Algorithm of Network Intrusion Signal Based on Neural Network and Support Vector Machine. Symmetry 2019, 11, 380. [Google Scholar] [CrossRef]
- Ali, M.H.; Al Mohammed, B.A.D.; Ismail, A.; Zolkipli, M.F. A New Intrusion Detection System Based on Fast Learning Network and Particle Swarm Optimization; IEEE Access: Piscataway, NJ, USA, 2018; pp. 20255–20261. [Google Scholar]
- Yang, A.; Zhuansun, Y.; Liu, C.; Li, J.; Zhang, C. Design of Intrusion Detection System for Internet of Things Based on Improved BP Neural Network; IEEE Access: Piscataway, NJ, USA, 2019; pp. 106043–106052. [Google Scholar]
- Seo, J.H. A study on the performance evaluation of unbalanced intrusion detection dataset classification based on machine learning. J. Korean Inst. Intell. Syst. 2017, 27, 466–474. [Google Scholar] [CrossRef]
- Amma, B.N.G.; Selvakumar, S. Deep Radial Intelligence with Cumulative Incarnation approach for detecting Denial of Service attacks. Neurocomputing 2019, 340, 294–308. [Google Scholar]
- Koay, A.; Chen, A.; Welch, I.; Seah, W.K. A new multi classifier system using entropy-based features in DDoS attack detection. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 162–167. [Google Scholar]
- Idhammad, M.; Afdel, K.; Belouch, M. Semi-supervised machine learning approach for DDoS detection. Appl. Intell. 2018, 48, 3193–3208. [Google Scholar] [CrossRef]
- Yassin, W.; Udzir, N.I.; Muda, Z.; Sulaiman, M.N. Anomaly-based intrusion detection through k-means clustering and naives bayes classification. In Proceedings of the 4th International Conference on Computing and Applied Informatics, Kuching, Sarawak, Malaysia, 28–30 August 2013; pp. 298–303. [Google Scholar]
- Soheily-Khah, S.; Marteau, P.F.; Béchet, N. Intrusion detection in network systems through hybrid supervised and unsupervised machine learning process: A case study on the iscx dataset. In Proceedings of the 2018 1st International Conference on Data Intelligence and Security (ICDIS), Island, TX, USA, 8–10 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 219–226. [Google Scholar]
- Faker, O.; Dogdu, E. Intrusion detection using big data and deep learning techniques. In Proceedings of the 2019 ACM Southeast Conference, Kennesaw, GA, USA, 18–20 April 2019; pp. 86–93. [Google Scholar]
- Zhang, X.; Chen, J.; Zhou, Y.; Han, L.; Lin, J. A Multiple-Layer Representation Learning Model for Network-Based Attack Detection; IEEE Access: Piscataway, NJ, USA, 2019; pp. 91992–92008. [Google Scholar]
- Zhou, Q.; Pezaros, D. Evaluation of Machine Learning Classifiers for Zero-Day Intrusion Detection-An Analysis on CIC-AWS-2018 dataset. arXiv 2019, arXiv:1905.03685. [Google Scholar]
- Kim, J.; Shin, Y.; Choi, E. An Intrusion Detection Model based on a Convolutional Neural Network. J. Mult. Inform. Syst. 2019, 6, 165–172. [Google Scholar] [CrossRef]
- Chadza, T.; Kyrakopoulos, K.G.; Lambotharan, S. Contemporary Sequential Network Attacks Prediction using Hidden Markov Model. In Proceedings of the 2019 17th International Conference on Privacy, Security and Trust (PST), Fredericton, NB, Canada, 26–28 August 2019; pp. 1–3. [Google Scholar]
- MATLAB. Available online: https://www.mathworks.com/help/matlab/ref/image.html (accessed on 20 January 2020).
- Tensorflow. Available online: https://www.tensorflow.org (accessed on 17 March 2020).
- Simonyan, K.; Zisserman, A. Very deep convolutional networks for large-scale image recognition. arXiv 2014, arXiv:1409.1556. [Google Scholar]





| Classification | Name of Attack | Num. of Samples |
|---|---|---|
| Denial of Service (DoS) | Neptune, smurf, pod, teardrop, land, back, apache2, udpstorm, processtable, mail-bomb | 229,853 |
| User to Root (U2R) | buffer-overflow, load-module, perl, rootkit, xterm, ps, sqlattack | 70 |
| Remote to Local (R2L) | guess-password, ftp-write, imap, phf, multihop, spy, warezclient | 16,347 |
| Probing | port-sweep, ip-sweep, nmap, satan, saint, mscan | 4166 |
| Dataset | Classification | Total |
|---|---|---|
| KDD | Benign | 60,591 |
| Neptune Attack | 58,001 | |
| Smurf Attack | 164,091 | |
| CSE-CIC-IDS 2018 | Benign | 9,108,759 |
| DoS-Hulk Attack | 461,912 | |
| DoS-SlowHTTPTest | 139,890 | |
| DoS-GoldenEye | 41,508 | |
| DoS-Slowloris | 10,990 | |
| DDoS-LOIC-HTTP | 576,191 | |
| DDoS-HOIC | 686,012 |
| No. | Scenario | Num. of Conv. Layer | Kernel Size | Num. of Kernels | ||
|---|---|---|---|---|---|---|
| Conv. Layer1 | Conv. Layer2 | Conv. Layer3 | ||||
| 1 | RGB-1 | 1 | 2 × 2 | 32 | - | - |
| 2 | RGB-2 | 2 | 2 × 2 | 32 | 64 | - |
| 3 | RGB-3 | 3 | 2 × 2 | 32 | 64 | 128 |
| 4 | RGB-4 | 1 | 3 × 3 | 32 | - | - |
| 5 | RGB-5 | 2 | 3 × 3 | 32 | 64 | - |
| 6 | RGB-6 | 3 | 3 × 3 | 32 | 64 | 128 |
| 7 | RGB-7 | 1 | 4 × 4 | 32 | - | - |
| 8 | RGB-8 | 2 | 4 × 4 | 32 | 64 | - |
| 9 | RGB-9 | 3 | 4 × 4 | 32 | 64 | 128 |
| 10 | GS-1 | 1 | 2 × 2 | 32 | - | - |
| 11 | GS-2 | 2 | 2 × 2 | 32 | 64 | - |
| 12 | GS-3 | 3 | 2 × 2 | 32 | 64 | 128 |
| 13 | GS-4 | 1 | 3 × 3 | 32 | - | - |
| 14 | GS-5 | 2 | 3 × 3 | 32 | 64 | - |
| 15 | GS-6 | 3 | 3 × 3 | 32 | 64 | 128 |
| 16 | GS-7 | 1 | 4 × 4 | 32 | - | - |
| 17 | GS-8 | 2 | 4 × 4 | 32 | 64 | - |
| 18 | GS-9 | 3 | 4 × 4 | 32 | 64 | 128 |
| Class | KDD | CSE-CIC-IDS 2018 | ||
|---|---|---|---|---|
| Binary | Multiclass | Binary | Multiclass | |
| 1 | benign | benign | benign | benign |
| 2 | attack | smurf | attack | DoS-Hulk |
| 3 | - | neptune | - | DoS-SlowHTTPTest |
| 4 | - | - | - | DoS-GoldenEye |
| 5 | - | - | - | DoS-Slowloris |
| 6 | - | - | - | DDoS-LOIC-HTTP |
| 7 | - | - | - | DDoS-HOIC |
| RGB Scenarios | TP and TN | FP and FN | Accuracy | GS Scenarios | TP and TN | FP and FN | Accuracy |
|---|---|---|---|---|---|---|---|
| RGB-1 | 282,596 | 87 | 0.999693 | GS-1 | 282,502 | 181 | 0.999359 |
| RGB-2 | 282,607 | 76 | 0.999731 | GS-2 | 282,580 | 103 | 0.999637 |
| RGB-3 | 282,664 | 19 | 0.999932 | GS-3 | 282,620 | 63 | 0.999778 |
| RGB-4 | 282,589 | 94 | 0.999667 | GS-4 | 282,582 | 101 | 0.999642 |
| RGB-5 | 282,642 | 41 | 0.999856 | GS-5 | 282,602 | 81 | 0.999712 |
| RGB-6 | 282,648 | 35 | 0.999875 | GS-6 | 282,623 | 60 | 0.999788 |
| RGB-7 | 282,614 | 69 | 0.999755 | GS-7 | 282,537 | 146 | 0.999484 |
| RGB-8 | 282,661 | 22 | 0.999922 | GS-8 | 282,646 | 37 | 0.999868 |
| RGB-9 | 282,630 | 53 | 0.999814 | GS-9 | 282,590 | 93 | 0.999670 |
| Kernel Size | RGB Scenarios | Num. of Conv. Layer | Accuracy | Kernel Size | GS Scenarios | Num.of Conv. Layer | Accuracy |
|---|---|---|---|---|---|---|---|
| 2 × 2 | RGB-1 | 1 | 0.999693 | 2 × 2 | GS-1 | 1 | 0.999359 |
| RGB-2 | 2 | 0.999731 | GS-2 | 2 | 0.999637 | ||
| RGB-3 | 3 | 0.999932 | GS-3 | 3 | 0.999778 | ||
| 3 × 3 | RGB-4 | 1 | 0.999667 | 3 × 3 | GS-4 | 1 | 0.999642 |
| RGB-5 | 2 | 0.999856 | GS-5 | 2 | 0.999712 | ||
| RGB-6 | 3 | 0.999875 | GS-6 | 3 | 0.999788 | ||
| 4 × 4 | RGB-7 | 1 | 0.999755 | 4 × 4 | GS-7 | 1 | 0.999484 |
| RGB-8 | 2 | 0.999922 | GS-8 | 2 | 0.999868 | ||
| RGB-9 | 3 | 0.999813 | GS-9 | 3 | 0.999670 |
| Num. of Conv. Layer | RGB Scenarios | Kernel Size | Accuracy | Num. of Conv. Layer | GS Scenarios | Kernel Size | Accuracy |
|---|---|---|---|---|---|---|---|
| 1 | RGB-1 | 2 × 2 | 0.999693 | 1 | GS-1 | 2 × 2 | 0.999359 |
| RGB-4 | 3 × 3 | 0.999667 | GS-4 | 3 × 3 | 0.999642 | ||
| RGB-7 | 4 × 4 | 0.999755 | GS-7 | 4 × 4 | 0.999484 | ||
| 2 | RGB-2 | 2 × 2 | 0.999731 | 2 | GS-2 | 2 × 2 | 0.999637 |
| RGB-5 | 3 × 3 | 0.999856 | GS-5 | 3 × 3 | 0.999712 | ||
| RGB-8 | 4 × 4 | 0.999922 | GS-8 | 4 × 4 | 0.999868 | ||
| 3 | RGB-3 | 2 × 2 | 0.999932 | 3 | GS-3 | 2 × 2 | 0.999778 |
| RGB-6 | 3 × 3 | 0.999875 | GS-6 | 3 × 3 | 0.999788 | ||
| RGB-9 | 4 × 4 | 0.999813 | GS-9 | 4 × 4 | 0.999670 |
| RGB Scenarios | Accuracy | GS Scenarios | Accuracy |
|---|---|---|---|
| RGB-1 | 0.999691 | GS-1 | 0.999481 |
| RGB-2 | 0.999767 | GS-2 | 0.999611 |
| RGB-3 | 0.999960 | GS-3 | 0.999755 |
| RGB-4 | 0.999719 | GS-4 | 0.999538 |
| RGB-5 | 0.999889 | GS-5 | 0.999825 |
| RGB-6 | 0.999830 | GS-6 | 0.999823 |
| RGB-7 | 0.999566 | GS-7 | 0.999476 |
| RGB-8 | 0.999778 | GS-8 | 0.999835 |
| RGB-9 | 0.999781 | GS-9 | 0.999455 |
| Kernel Size | RGB Scenarios | Num. of Conv. Layer | Accuracy | Kernel Size | GS Scenarios | Num. of Conv. Layer | Accuracy |
|---|---|---|---|---|---|---|---|
| 2 × 2 | RGB-1 | 1 | 0.999691 | 2 × 2 | GS-1 | 1 | 0.999481 |
| RGB-2 | 2 | 0.999767 | GS-2 | 2 | 0.999611 | ||
| RGB-3 | 3 | 0.999960 | GS-3 | 3 | 0.999755 | ||
| 3 × 3 | RGB-4 | 1 | 0.999719 | 3 × 3 | GS-4 | 1 | 0.999538 |
| RGB-5 | 2 | 0.999889 | GS-5 | 2 | 0.999825 | ||
| RGB-6 | 3 | 0.999830 | GS-6 | 3 | 0.999823 | ||
| 4 × 4 | RGB-7 | 1 | 0.999566 | 4 × 4 | GS-7 | 1 | 0.999476 |
| RGB-8 | 2 | 0.999778 | GS-8 | 2 | 0.999835 | ||
| RGB-9 | 3 | 0.999781 | GS-9 | 3 | 0.999455 |
| Num. of Conv. Layer | RGN Scenarios | Kernel Size | Accuracy | Num. of Conv. Layer | GS Scenarios | Kernel Size | Accuracy |
|---|---|---|---|---|---|---|---|
| 1 | RGB-1 | 2 × 2 | 0.999691 | 1 | GS-1 | 2 × 2 | 0.999481 |
| RGB-4 | 3 × 3 | 0.999719 | GS-4 | 3 × 3 | 0.999538 | ||
| RGB-7 | 4 × 4 | 0.999566 | GS-7 | 4 × 4 | 0.999476 | ||
| 2 | RGB-2 | 2 × 2 | 0.999767 | 2 | GS-2 | 2 × 2 | 0.999611 |
| RGB-5 | 3 × 3 | 0.999890 | GS-5 | 3 × 3 | 0.999825 | ||
| RGB-8 | 4 × 4 | 0.999778 | GS-8 | 4 × 4 | 0.999835 | ||
| 3 | RGB-3 | 2 × 2 | 0.999959 | 3 | GS-3 | 2 × 2 | 0.999755 |
| RGB-6 | 3 × 3 | 0.999830 | GS-6 | 3 × 3 | 0.999823 | ||
| RGB-9 | 4 × 4 | 0.999781 | GS-9 | 4 × 4 | 0.999455 |
| Classification | Precision | Recall | F1-Score | |
|---|---|---|---|---|
| binary-class | benign | 0.99 | 1.00 | 0.99 |
| attack | 1.00 | 1.00 | 1.00 | |
| multiclass | Benign | 0.77 | 0.94 | 0.85 |
| Neptune | 0.92 | 0.71 | 0.80 | |
| Smurf | 1.00 | 1.00 | 1.00 | |
| Classification | Precision | Recall | F1-Score | |
|---|---|---|---|---|
| binary-class | benign | 0.8175 | 0.8225 | 0.82 |
| attack | 0.6 | 0.8475 | 0.8475 | |
| multiclass | benign | 0.7275 | 0.77 | 0.735 |
| DoS-Hulk | 0.37 | 0.51 | 0.43 | |
| DoS-SlowHTTPTest | 0.79 | 0.05 | 0.09 | |
| DoS-GoldenEye | 0.91 | 0.99 | 0.95 | |
| DoS-Slowloris | 0.84 | 0.93 | 0.89 | |
| DDoS-LOIC-HTTP | 1 | 0.94 | 0.97 | |
| DDoS-HOIC | 0.44 | 0.52 | 0.47 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, J.; Kim, J.; Kim, H.; Shim, M.; Choi, E. CNN-Based Network Intrusion Detection against Denial-of-Service Attacks. Electronics 2020, 9, 916. https://doi.org/10.3390/electronics9060916
Kim J, Kim J, Kim H, Shim M, Choi E. CNN-Based Network Intrusion Detection against Denial-of-Service Attacks. Electronics. 2020; 9(6):916. https://doi.org/10.3390/electronics9060916
Chicago/Turabian StyleKim, Jiyeon, Jiwon Kim, Hyunjung Kim, Minsun Shim, and Eunjung Choi. 2020. "CNN-Based Network Intrusion Detection against Denial-of-Service Attacks" Electronics 9, no. 6: 916. https://doi.org/10.3390/electronics9060916
APA StyleKim, J., Kim, J., Kim, H., Shim, M., & Choi, E. (2020). CNN-Based Network Intrusion Detection against Denial-of-Service Attacks. Electronics, 9(6), 916. https://doi.org/10.3390/electronics9060916





