Quality of Life, Quality of Experience, and Security Perception in Web of Things: An Overview of Research Opportunities
Abstract
1. Introduction
2. Theoretical Background
2.1. Definitions of QoL, QoE, and Security Perception
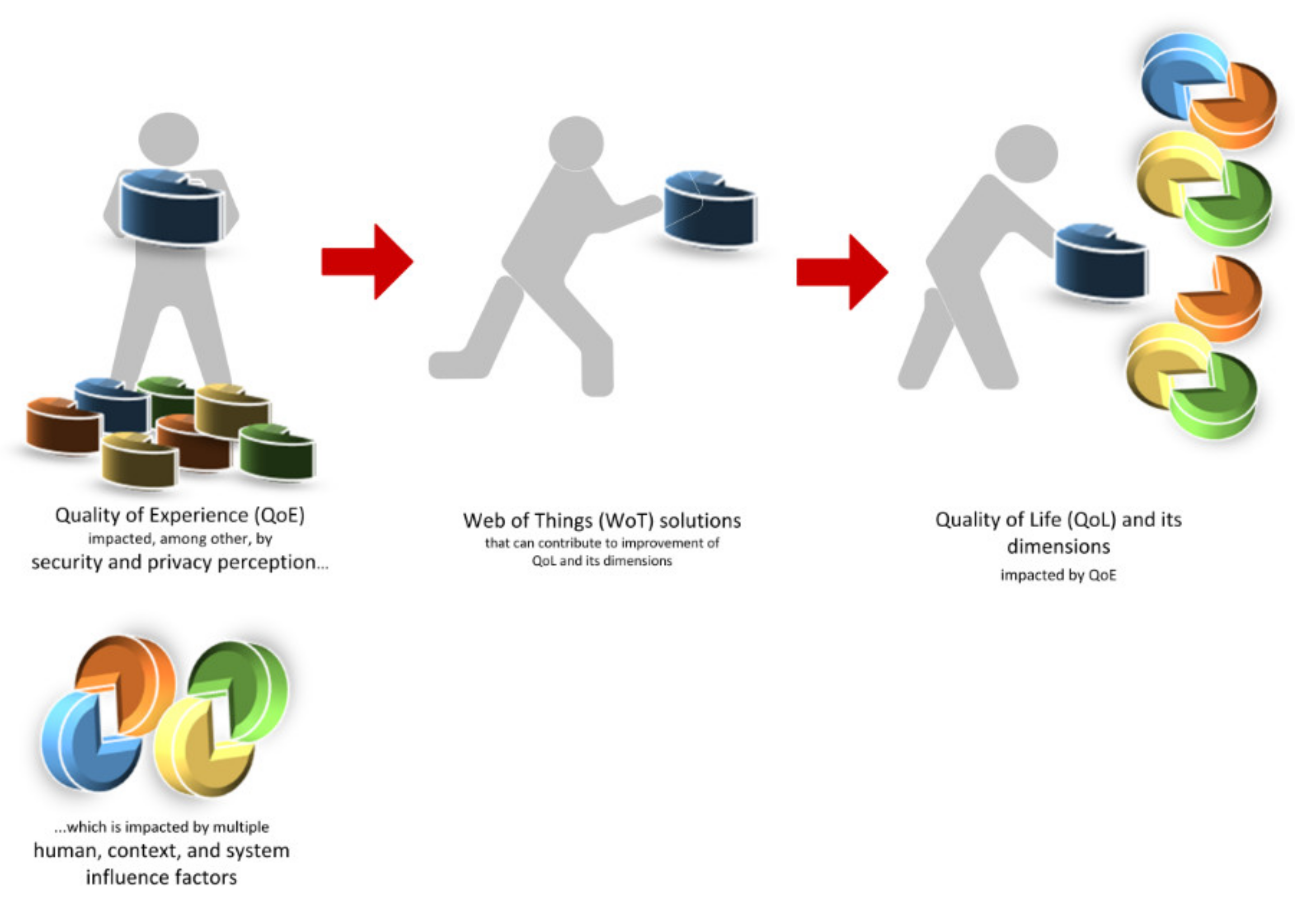
2.2. Dependencies Between QoL, QoE, Security Perception, and Influence Factors
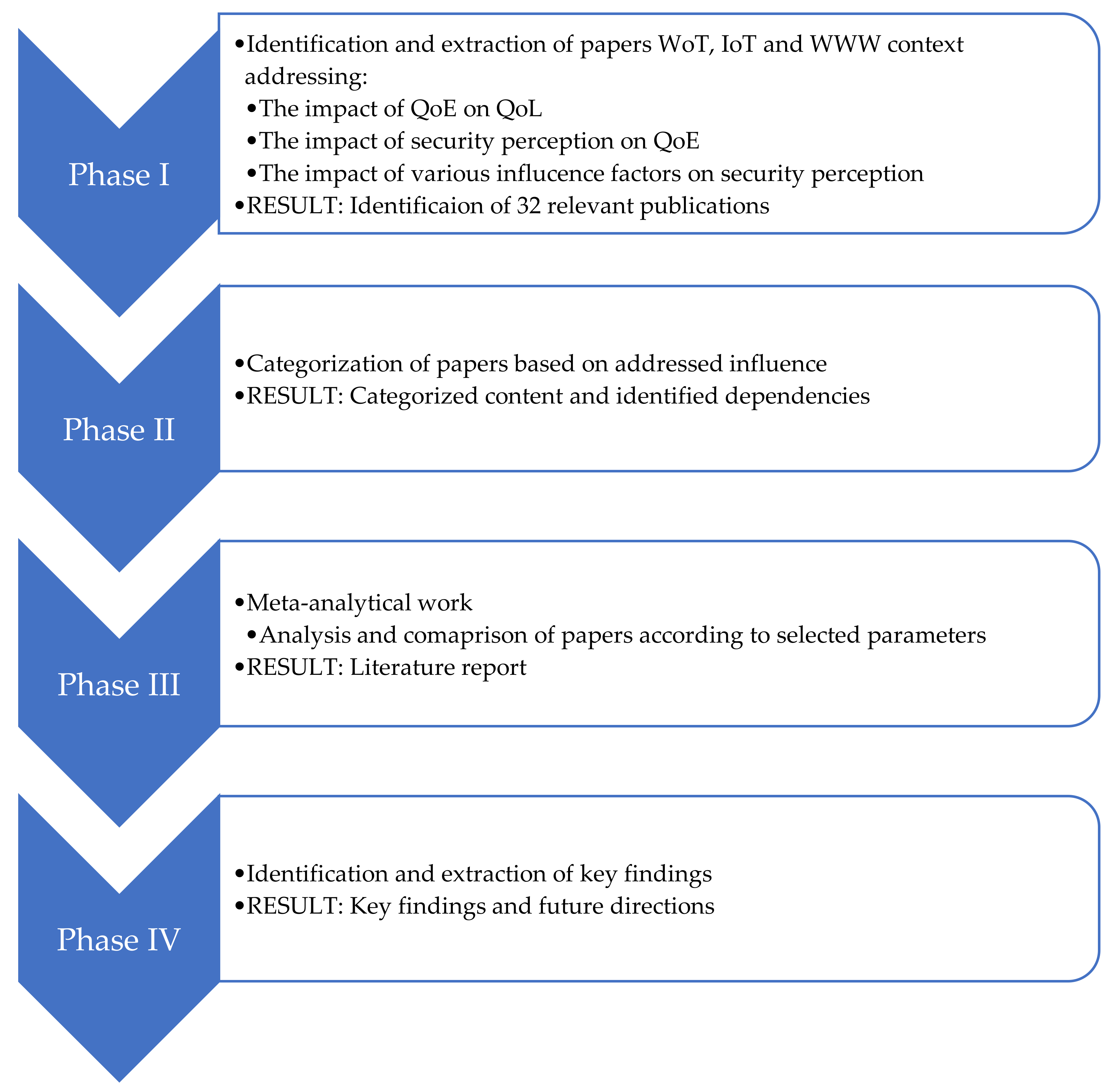
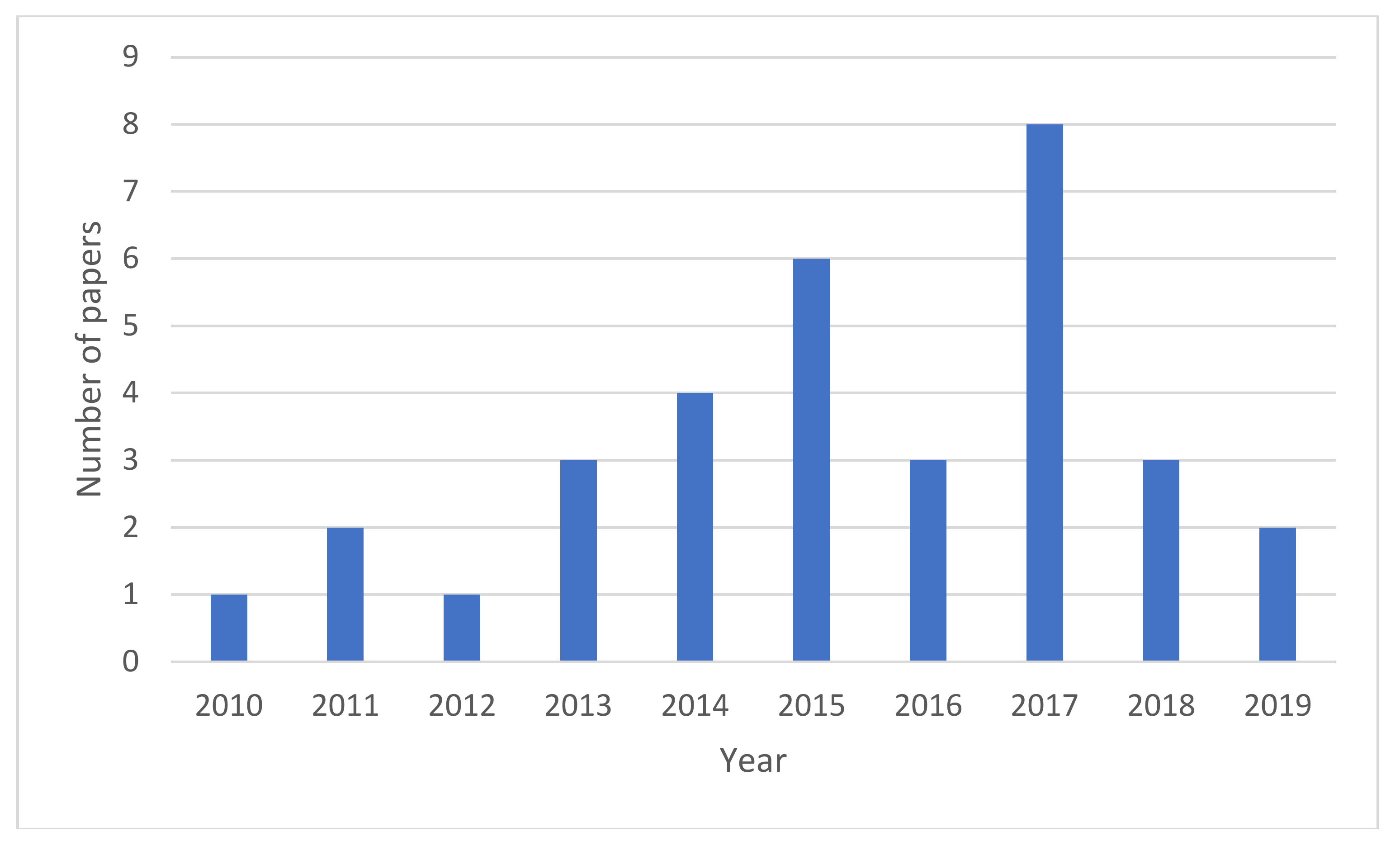
3. Research Methodology
- to gain deeper understanding of the mutual dependencies between QoL, QoE, security perception, as well as influence factors in addressed context through proposed layered framework;
- to organize and synthesize the existing research literature from the field;
- to identify gaps and issues needed to be addressed by the future research activities and suggest novel and open investigation directions in the subject field.
4. Literature Analysis and Comparison
4.1. Impact of QoE on QoL
4.2. Impact of Security Perception on QoE
4.3. Influence Factors Affecting Security Perception
4.3.1. Impact of System Factors on Security Perception
4.3.2. Impact of Human Factors on Security Perception
4.3.3. Impact of Context Factors on Security Perception
4.4. Summary of the Literature Report
5. Key Findings and Research Opportunities
6. Summary and Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A
| Ref. | QoL Dimension | WWW/IoT/WoT | Application | Users | Environment | Research Method | Model/Framework | Type of Impact |
|---|---|---|---|---|---|---|---|---|
| [27] | Overall Experience of Life | WWW | Mobile Web Browsing | ALL | REAL | Regression modelling | YES | HIGH |
| [28] | Overall Experience of Life | WWW | Mobile Web Browsing | ALL | REAL | Regression modelling | YES | HIGH |
| [30] | Overall Experience of Life | WWW | Multimedia | ALL | REAL AND LAB | Formula-based QoE estimation methods, and collecting KPIs for most popular services | YES | HIGH |
| [31] | Overall Experience of Life | WWW | Mobile products | ALL | REAL | Data collection and triggering context analysis | YES | HIGH |
| [33] | Overall Experience of Life | WWW | Cellular Networks | ALL | REAL | Intuitive and accurate machine-learning models for capturing complex relationship between different network parameters | YES | HIGH |
| [88] | Overall Experience of Life | IoT | IoT Multimedia | ALL | REAL | Framework for the evaluation and management of the QoE provided by multimedia | YES | HIGH |
| [89] | Overall Experience of Life | IoT | Multimedia | ALL | REAL | QoE optimization using Data Fusion | YES | HIGH |
| [90] | Overall Experience of Life | IoT | Social IoT | ELDERLY | REAL | SIoT to leverage the degree of nteraction among things | YES | HIGH |
Appendix B
| Ref. | QoE | Security Perception | WWW/ IoT/ WoT | Application | Users | Environment | Research Method | Model/Framework | Type of Impact |
|---|---|---|---|---|---|---|---|---|---|
| [39] | QoE | Security and privacy | WoT | Web applications, healthcare, RFID | ALL | REAL | A case study based on some recent studies from WoT framework | YES | HIGH |
Appendix C
| Ref. | Security Perception | Type of Influence Factor | Influence Factor | WWW/IoT/ WoT | Users | Environment | Research Method | Model/Framework | Type of Impact |
|---|---|---|---|---|---|---|---|---|---|
| [49] | Privacy | CIF | User, User profile, state of device, environment information | IoT | ALL | BOTH | Context-aware system using through device-oriented modeling for the IoT | YES | HIGH |
| [71] | Trust | HIF | Realiability, Look&Feel, Availabilty, privacy, security, 3rd party seal, risk, reputatin | WWW | ALL | REAL | Survey | YES | HIGH |
| [77] | Trust | HIF | Social influence related factors, Product related factors, Security related factors | IoT | ALL | REAL | Statistical analysis | YES | HIGH |
| [78] | Security | HIF | Gender, basic need, scepticism, safety and security, care for community | IoT | ALL | REAL | A qualitative research methodology employing interviews and thematic analysis | YES | HIGH |
| [79] | Security/ privacy | CIF | Data acquisition, Distribution | IoT | ALL | REAL | Context-aware computing | YES | HIGH |
| [80] | Trust | CIF | Information gathering, Transaction, Reward and punish, Entity selection, Learning | IoT | ALL | LAB | Design | YES | HIGH |
| [83] | Security | CIF | Data acquisition, Integration, Interoperability | IoT/ WoT | ALL | REAL | Proof-of-concept DaaS | YES | HIGH |
| [84] | Security/privacy | CIF | Environment, User, Temporal | WoT | ALL | REAL | Design | YES | HIGH |
| [85] | Security/privacy | CIF | Location, Social component, Used application | WoT | ALL | REAL | Modelling | YES | MEDIUM |
| [87] | Trust | CIF | Location, Identity, Time, Activity | WoT | ALL | BOTH | Design | YES | MEDIUM |
Appendix D
| Reference | Access Control | IPSEC | Authorization | SSL/TLS | VPN | Encryption | Identity Management | Non-Repudiation | Identification | Buffer Overflow | Access Decision Facility | SmartOrBAC (Organization-Based Access Control) | Authentication |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [39] | x | x | x | x | x | ||||||||
| [72] | x | x | x | x | x | x | x | ||||||
| [73] | x | x | |||||||||||
| [74] | x | x |
Appendix E
Appendix F
| Reference | Location | Identity | When (Time) | What (Activity) | Why | Information Gathering | Transaction | Reward and Punish | Learning | Entity Selection | Social Component | Used Application |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [49] | x | x | ||||||||||
| [79] | x | x | x | x | x | |||||||
| [80] | x | x | x | x | x | |||||||
| [84] | x | x | x | |||||||||
| [85] | x | x | x | |||||||||
| [87] | x | x | x | x |
References
- Juniper Research. The number of connected devices by 2021: Impressive growth ahead, December 2016. Available online: https://www.juniperresearch.com/press/press-releases/%E2%80%98internet-of-things%E2%80%99-connected-devices-triple-2021 (accessed on 11 April 2020).
- Mattern, F.; Floerkemeier, C. From the Internet of Computers to the Internet of Things. In Computer Vision; Springer Science and Business Media LLC: New York, NY, USA, 2010; Volume 6462, pp. 242–259. [Google Scholar]
- Guinard, D. A web of Things Application Architecture: Integrating the Real-World into the Web. Ph.D. Thesis, ETH Zurich, Zurich, Switzerland, 2011. [Google Scholar]
- Heuer, J.; Hund, J.; Pfaff, O. Toward the Web of Things: Applying Web Technologies to the Physical World. Computer 2015, 48, 34–42. [Google Scholar] [CrossRef]
- Guinard, D.; Trifa, V. Building the Web of Things; Manning Publications: New York, NY, USA, 2016. [Google Scholar]
- Guinard, D.; Trifa, V.; Mattern, F.; Wilde, E. From the Internet of Things to the Web of Things: Resource-oriented Architecture and Best Practices. In Architecting the Internet of Things; Springer Science and Business Media LLC: New York, NY, USA, 2011; pp. 97–129. [Google Scholar]
- Guinard, D.; Trifa, V. Towards the Web of Things: Web mashups for Embedded Devices. In Proceedings of the WWW (International World Wide Web Conferences), Workshop on Mashups, Enterprise Mashups and Lightweight Composition on the Web (MEM 2009), Madrid, Spain, 20–24 April 2019; Volume 15, p. 8. [Google Scholar]
- Sheng, Q.Z.; Qin, Y.; Yao, L.; Benatallah, B. Managing the Web of Things; Elsevier Inc.: Amsterdam, The Netherlands, 2017. [Google Scholar]
- Trifa, M.V. Building Blocks for a Participatory Web of Things: Devices, Infrastructures, and Programming Frameworks. Ph.D. Thesis, ETH Zurich, Zurich, Switzerland, 2011. [Google Scholar]
- Guinard, D.; Trifa, V.; Pham, T.; Liechti, O. Towards physical mashups in the Web of Things. In Proceedings of the 2009 Sixth International Conference on Networked Sensing Systems (INSS), Pittsburgh, PA, USA, 17–19 June 2009; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2009; pp. 1–4. [Google Scholar]
- El Jaouhari, S. A Secure Design of WoT Services for Smart Cities. Ph.D. Thesis, Comue Universite Bretagne Loire, Ecole Nationale Superieure Mines-Telecom Atlantique, Rennes, France, 2019. [Google Scholar]
- Spirito, M.A.; Delgao, M.T. Internet of Things application scenarios, pilots and innovation. In Building the Hyperconnected Society: IoT Research and Innovation Value Chains, Ecosystems and Markets, 1st ed.; Vermesan, O., Friess, P., Eds.; River Publishers: Aalborg, Denmark, 2015; pp. 119–144. [Google Scholar]
- Ferrera, E.; Pastrone, C.; Brun, P.E.; Besombes, R.D.; Loupos, K.; Kouloumpis, G.; O’Sullivan, P.; Papageorgiou, A.; Katsoulakos, P.; Karakostas, B.; et al. IoT European security and privacy projects: Integration, architectures and interoperability. In Next Generation Internet of Things: Distributed Intelligence at the Edge and Human Machine-to-Machine Cooperation, 1st ed.; Vermesan, O., Bacquet, J., Eds.; River Publishers: Aalborg, Denmark, 2018; pp. 207–294. [Google Scholar]
- Baldini, G.; Peirce, T.; Botterman, M.; Talacchini, M.C.; Pereira, A.; Handte, M.; Rotondi, D.; Vermesa, O.; Baddii, A.; Copigneaux, B.; et al. Internet of Things: IoT Governance, Privacy and Security Issues, 1st ed.; IERC–European Research Cluster on the Internet of Things: Valencia, Spain, 2015. [Google Scholar]
- Ahmad, A.; Baldini, G.; Cousin, P.; Garcia, S.N.M.; Skarmeta, A.; Fourneret, E.; Legeard, B. Large scale IoT security testing, benchmarking and certification. In Cognitive Hyperconnected Digital Transformation: Internet of Things Intelligence Evolution, 1st ed.; Vermesan, O., Bacquet, J., Eds.; River Publishers: Aalborg, Denmark, 2017; pp. 189–220. [Google Scholar]
- Husic, J.B.; Baraković, S.; Dinarević, E.C. Smart Ageing: Are We Succeeding? In Proceedings of the World Congress on Medical Physics and Biomedical Engineering 2006, Seoul, Korea, 27 August–1 September 2019; Springer Science and Business Media LLC: New York, NY, USA, 2019; pp. 387–393. [Google Scholar]
- WHOQOL Group. The World Health Organization quality of life assessment (WHOQOL): Position paper from the World Health Organization. Soc. Sci. Med. 1995, 41, 1403–1409. [Google Scholar] [CrossRef]
- Power, M. The Whoqol Group Development of the World Health Organization WHOQOL-BREF Quality of Life Assessment. Psychol. Med. 1998, 28, 551–558. [Google Scholar] [CrossRef] [PubMed]
- Eurostat. Available online: https://ec/eusopa.eu/eurostat/documents/8131721/8131772/TF3-Final-report-Quality-of-Life.pdf (accessed on 19 September 2019).
- Tyuichi, M.; Takahisa, S.; Takuki, K. A WoT Gateway with Legacy Devices Virtualization. In Proceedings of the Second W3C Workshop on the Web of Things; Munich, Germnay, 3–5 June 2019.
- Global Web Index. Available online: https://thenextweb.com/tech/2019/01/31/study-shows-were-spending-an-insane-amount-of-time-online/ (accessed on 19 September 2019).
- Le Callet, P.; Möller, S.; Perkis, A. Qualinet White Paper on Definitions of Quality of Experience. Eur. Netw. Qual. Exp. Multimed. Syst. Serv. (COST Action IC 1003) 2012, 3, 1–25. [Google Scholar]
- Wac, K.; Fiordelli, M.; Gustarini, M.; Rivas, H. Quality of Life Technologies: Experiences from the Field and Key Challenges. IEEE Internet Comput. 2015, 19, 28–35. [Google Scholar] [CrossRef]
- Husic, J.B.; Baraković, S.; Cero, E.; Slamnik, N.; Oćuz, M.; Dedović, A.; Zupčić, O. Quality of experience for unified communications: A survey. Int. J. Netw. Manag. 2019. [Google Scholar] [CrossRef]
- Bandara, W.; Mikson, S.; Fieli, E. A Systematic, Tool-supported Method for Conducting Literature Reviews in Information Systems. In Proceedings of the 19th European Conference on Information Systems (ECIS), Helsinki, Finland, 9–11 June 2013. [Google Scholar]
- Levy, Y.; Ellis, T.J. A Systems Approach to Conduct an Effective Literature Review in Support of Information Systems Research. Informing Sci. Int. J. Emerg. Transdiscipl. 2006, 9, 181–212. [Google Scholar] [CrossRef]
- Baraković, S.; Skorin-Kapov, L. Multidimensional modelling of quality of experience for mobile Web browsing. Comput. Hum. Behav. 2015, 50, 314–332. [Google Scholar] [CrossRef]
- Baraković, S.; Skorin-Kapov, L. Modelling the relationship between design/performance factors and perceptual features contributing to Quality of Experience for mobile Web browsing. Comput. Hum. Behav. 2017, 74, 311–329. [Google Scholar] [CrossRef]
- Baraković, S.; Skorin-Kapov, L. Survey of research on Quality of Experience modelling for web browsing. Qual. User Exp. 2017, 2, 6. [Google Scholar] [CrossRef][Green Version]
- Tsolkas, D.; Liotou, E.; Passas, N.; Merakos, L. A survey on parametric QoE estimation for popular services. J. Netw. Comput. Appl. 2017, 77, 1–17. [Google Scholar] [CrossRef]
- Korhonen, P.; Tainio, R.; Wallenius, J. Value efficiency analysis of academic research. Eur. J. Oper. Res. 2001, 130, 121–132. [Google Scholar] [CrossRef]
- Liu, X.H.; Shan, M.Y.; Zhang, R.L.; Zhang, L.H. Green vehicle routing optimization based on carbon emission and multi objective hybrid quantum immune algorithm. Math. Probl. Eng. 2018, 2018. [Google Scholar] [CrossRef]
- Balachandran, A.; Aggarwal, V.; Halepovic, E.; Pang, J.; Seshan, S.; Venkataraman, S.; Yan, H. Modeling web quality-of-experience on cellular networks. In Proceedings of the the 20th Annual International Conference, Maui, HI, USA, 11–13 September 2014; Association for Computing Machinery (ACM): New York, NY, USA, 2014; pp. 213–224. [Google Scholar]
- Bellavista, P.; Giannelli, C.; Lanzone, S.; Riberto, G.; Stefanelli, C.; Tortonesi, M. A Middleware Solution for Wireless IoT Applications in Sparse Smart Cities. Sensors 2017, 17, 2525. [Google Scholar] [CrossRef]
- Krejcar, O.; Maresova, P.; Selamat, A.; Melero, F.J.; Barakovic, S.; Husic, J.B.; Herrera-Viedma, E.; Frischer, R.; Kuča, K. Smart Furniture as a Component of a Smart City—Definition Based on Key Technologies Specification. IEEE Access 2019, 7, 94822–94839. [Google Scholar] [CrossRef]
- Galinina, O.; Andreev, S.; Komarov, M.; Maltseva, S. Leveraging heterogeneous device connectivity in a converged 5G-IoT ecosystem. Comput. Netw. 2017, 128, 123–132. [Google Scholar] [CrossRef]
- Mora, H.; Pont, M.T.S.; Gil, D.; Johnsson, M. Collaborative Working Architecture for IoT-Based Applications†. Sensors 2018, 18, 1676. [Google Scholar] [CrossRef]
- Poncela, J.; Vlacheas, P.; Giaffreda, R.; De, S.; Vecchio, M.; Nechifor, S.; Barco, R.; Aguayo-Torres, M.C.; Stavroulaki, V.; Moessner, K.; et al. Smart Cities via Data Aggregation. Wirel. Pers. Commun. 2014, 76, 149–168. [Google Scholar] [CrossRef]
- Catuogno, L.; Turchi, S. The Dark Side of the Interconnection: Security and Privacy in the Web of Things. In Proceedings of the 2015 9th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Blumenau, Brazil, 8–10 July 2015; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2015; pp. 205–212. [Google Scholar]
- Hwang, Y.H. IoT Security & Privacy. In Proceedings of the 1st ACM Workshop on Cognitive Radio Architectures for Broadband-CRAB ’13, Singapore, 14–17 April 2015; Association for Computing Machinery (ACM): New York, NY, USA, 2015; p. 1. [Google Scholar]
- Abomhara, M.; Koien, G.M. Security and privacy in the Internet of Things: Current status and open issues. In Proceedings of the 2014 International Conference on Privacy and Security in Mobile Systems (PRISMS), Aalborg, Denmark, 11–14 May 2014; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 014; pp. 1–8. [Google Scholar]
- Sicari, S.; Rizzardi, A.; Grieco, L.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Sadeghi, A.-R.; Wachsmann, C.; Waidner, M. Security and privacy challenges in industrial internet of things. In Proceedings of the 52nd Annual Design Automation Conference on-DAC ’15, San Francisco, CA, USA, 8–12 June 2014; Association for Computing Machinery (ACM): New York, NY, USA, 2015; pp. 1–6. [Google Scholar]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Maple, C. Security and privacy in the internet of things. J. Cyber Policy 2017, 2, 155–184. [Google Scholar] [CrossRef]
- Sivaraman, V.; Gharakheili, H.H.; Fernandes, C.; Clark, N.; Karliychuk, T. Smart IoT Devices in the Home: Security and Privacy Implications. IEEE Technol. Soc. Mag. 2018, 37, 71–79. [Google Scholar] [CrossRef]
- Giraldo, J.; Sarkar, E.; Cardenas, A.A.; Maniatakos, M.; Kantarcioglu, M. Security and Privacy in Cyber-Physical Systems: A Survey of Surveys. IEEE Des. Test 2017, 34, 7–17. [Google Scholar] [CrossRef]
- Mukherjee, M.; Matam, R.; Shu, L.; Maglaras, L.; Ferrag, M.A.; Choudhury, N.; Kumar, V. Security and Privacy in Fog Computing: Challenges. IEEE Access 2017, 5, 19293–19304. [Google Scholar] [CrossRef]
- Yang, K.; Cho, S.-B. A context-aware system in Internet of Things using modular Bayesian networks. Int. J. Distrib. Sens. Netw. 2017, 13. [Google Scholar] [CrossRef]
- Lin, H.; Bergmann, N. IoT Privacy and Security Challenges for Smart Home Environments. Information 2016, 7, 44. [Google Scholar] [CrossRef]
- Stergiou, C.; Psannis, K.; Kim, B.-G.; Gupta, B. Secure integration of IoT and Cloud Computing. Futur. Gener. Comput. Syst. 2018, 78, 964–975. [Google Scholar] [CrossRef]
- Zhou, W.; Jia, Y.; Peng, A.; Zhang, Y.; Liu, P. The Effect of IoT New Features on Security and Privacy: New Threats, Existing Solutions, and Challenges Yet to Be Solved. IEEE Internet Things J. 2019, 6, 1606–1616. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenges. IEEE Internet Things J. 2017, 5, 2483–2495. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Hasan, M.; Islam, M.; Zarif, I.I.; Hashem, M.; Islam, I. Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 2019, 7, 100059. [Google Scholar] [CrossRef]
- Mawgoud, A.A.; Karadawy, A.I.; Tawfik, B.S. A Secure Authentication Technique in Internet of Medical Things through Machine Learning. arXiv 2019, arXiv:1912.12143. [Google Scholar]
- Tabassum, A.; Lebda, W. Security Framework for IoT Devices against Cyber-attacks. In Proceedings of the 6th International Conference on Computer Science, Engineering and Information Technology (CSEIT-2019), Zurich, Switzerland, 23–24 November 2019; Academy and Industry Research Collaboration Center (AIRCC): Zurich, Switzerland, 2019; pp. 249–266. [Google Scholar]
- Ataç, C.; Akleylek, S. A Survey on Security Threats and Solutions in the Age of IoT. Eur. J. Sci. Technol. 2019, 15, 36–42. [Google Scholar] [CrossRef]
- Silaghi, V.D.; Silaghi, M.; Mandiau, R. Privacy of Existence of Secrets: Introducing Steganographic DCOPs and Revisiting DCOP Frameworks. arXiv 2019, arXiv:1902.05943. [Google Scholar]
- Guan, Z.; Zhang, Y.; Wu, L.; Wu, J.; Li, J.; Ma, Y.; Hu, J. APPA: An anonymous and privacy preserving data aggregation scheme for fog-enhanced IoT. J. Netw. Comput. Appl. 2019, 125, 82–92. [Google Scholar] [CrossRef]
- Al-Shukri, H.K.H.; Udayanan. Factors Influencing Online Shopping Intention: A study among shoppers in Oman. Int. J. Acad. Res. Bus. Soc. Sci. 2019, 9, 691–709. [Google Scholar]
- Wu, W.Y.; Ke, C.C. An online shopping behaviour model integrating personality traits, perceived risk, and technology acceptance. Soc. Behav. Personal. Int. J. 2015, 43, 85–97. [Google Scholar] [CrossRef]
- Topaloğlu, C. Consumer motivation and concern factors for online shopping in Turkey. Asian Acad. Manag. J. 2012, 17, 1–19. [Google Scholar]
- Shadkam, M. An empirical study on influence factors of online purchasing. Int. J. Arts Sci. 2012, 5, 479. [Google Scholar]
- Hsu, C.-L.; Lin, J.C.-C.; Chiang, H.-S. The effects of blogger recommendations on customers’ online shopping intentions. Internet Res. 2013, 23, 69–88. [Google Scholar] [CrossRef]
- Hsu, M.-H.; Chuang, L.-W.; Hsu, C.-S. Understanding online shopping intention: The roles of four types of trust and their antecedents. Internet Res. 2014, 24, 332–352. [Google Scholar] [CrossRef]
- Amin, M.; Rezaei, S.; Abolghasemi, M. User satisfaction with mobile websites: The impact of perceived usefulness (PU), perceived ease of use (PEOU) and trust. Nankai Bus. Rev. Int. 2014, 5, 258–274. [Google Scholar] [CrossRef]
- Seckler, M.; Heinz, S.; Forde, S.; Tuch, A.N.; Opwis, K. Trust and distrust on the web: User experiences and website characteristics. Comput. Hum. Behav. 2015, 45, 39–50. [Google Scholar] [CrossRef]
- Zinner, T.; Hohlfeld, O.; Abboud, O.; Hoßfeld, T. Impact of frame rate and resolution on objective QoE metrics. In Proceedings of the Second International Workshop on Quality of Multimedia Experience (QoMEX), Trondheim, Norway , 21–23 June 2010; 2010; pp. 29–34. [Google Scholar] [CrossRef]
- Jammeh, E.; Mkwawa, I.-H.; Khan, A.; Goudarzi, M.; Sun, L.; Ifeachor, E.C. Quality of experience (QoE) driven adaptation scheme for voice/video over IP. Telecommun. Syst. 2010, 49, 99–111. [Google Scholar] [CrossRef]
- Costante, E.; Hartog, J.D.; Petković, M. On-line trust perception: What really matters. In Proceedings of the 1st Workshop on Socio-Technical Aspects in Security and Trust (STAST), Milan, Italy, 8 September 2011; Volume 59. [Google Scholar] [CrossRef]
- El Jaouhari, S.; Bouabdallah, A.; Bonnin, J.M. Security Issues of the Web of Things. In Managing the Web of Things; Elsevier BV: New York, NY, USA, 2017; pp. 389–424. [Google Scholar]
- Ouaddah, A.; Bouij-Pasquier, I.; Abou, A.; Abdellah, E.; Ouahman, A.A. Security analysis and proposal of new access control model in the Internet of Thing. In Proceedings of the 2015 International Conference on Electrical and Information Technologies (ICEIT), Marrakech, Morocco, 25–27 March 2015; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2015; pp. 30–35. [Google Scholar]
- Skarmeta, A.; Hernandez-Ramos, J.L.; Bernabe, J.B. A required security and privacy framework for smart objects. 2015 ITU Kaleidosc. Trust Inf. Soc. (K-2015) 2015, 1–7. [Google Scholar] [CrossRef]
- Li, L.; Li, S.; Zhao, S. QoS-Aware Scheduling of Services-Oriented Internet of Things. IEEE Trans. Ind. Inform. 2014, 10, 1497–1505. [Google Scholar] [CrossRef]
- Sackl, A.; Casas, P.; Schatz, R.; Janowski, L.; Irmer, R. Quantifying the impact of network bandwidth fluctuations and outages on Web QoE. In Proceedings of the Seventh International Workshop on Quality of Multimedia Experience (QoMEX), Pylos-Nestoras, Greece, 26–29 May 2015; 2015; pp. 1–6. [Google Scholar] [CrossRef]
- AlHogail, A. Improving IoT Technology Adoption through Improving Consumer Trust. Technology 2018, 6, 64. [Google Scholar] [CrossRef]
- Luqman, A.; Van Belle, J.-P. Analysis of human factors to the adoption of Internet of Things-based services in informal settlements in Cape Town. In Proceedings of the 2017 1st International Conference on Next Generation Computing Applications (NextComp), Mauritius, 19–21 March 2015; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2017; pp. 61–67. [Google Scholar]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context Aware Computing for The Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2013, 16, 414–454. [Google Scholar] [CrossRef]
- Ben Saied, Y.; Olivereau, A.; Zeghlache, D.; Laurent, M. Trust management system design for the Internet of Things: A context-aware and multi-service approach. Comput. Secur. 2013, 39, 351–365. [Google Scholar] [CrossRef]
- Dey, A.K.; Abowd, G.; Salber, D. A Conceptual Framework and a Toolkit for Supporting the Rapid Prototyping of Context-Aware Applications. Hum. Comput. Interact. 2001, 16, 97–166. [Google Scholar] [CrossRef]
- Perera, C.; Liu, C.H.; Jayawardena, S.; Chen, M. A Survey on Internet of Things From Industrial Market Perspective. IEEE Access 2015, 2, 1660–1679. [Google Scholar] [CrossRef]
- Lehmann, M.; Biørn-Hansen, A.; Ghinea, G.; Grønli, T.-M.; Younas, M. Data Analysis as a Service: An Infrastructure for Storing and Analyzing the Internet of Things. In Proceedings of the Lecture Notes in Computer Science, Paris, France, 3–5 November 2015; Springer Science and Business Media LLC: New York, NY, USA, 2015; Volume 9228, pp. 161–169. [Google Scholar]
- Bai, G.; Yan, L.; Gu, L.; Guo, Y.; Chen, X. Context-aware usage control for web of things. Secur. Commun. Networks 2012, 7, 2696–2712. [Google Scholar] [CrossRef]
- Terdjimi, M.; Médini, L.; Marissa, M. Towards a Meta-model for Context in the Web of Things. In Proceedings of the Karlsruhe Service Summit Workshop, Karlsruhe, Germany, 25–26 February 2016. [Google Scholar]
- Shafik, W.; Matinkhah, S. Privacy Issues in Social Web of Things. In Proceedings of the 2019 5th International Conference on Web Research (ICWR), Tehran, Iran, 24–25 April 2019; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2019; pp. 208–214. [Google Scholar]
- Javaid, S.; Afzal, H.; Arif, F.; Iltaf, N.; Abbas, H.; Iqbal, M.M.W. CATSWoTS: Context Aware Trustworthy Social Web of Things System. Sensors 2019, 19, 3076. [Google Scholar] [CrossRef] [PubMed]
- Floris, A.; Atzori, L. Managing the Quality of Experience in the Multimedia Internet of Things: A Layered-Based Approach †. Sensors 2016, 16, 2057. [Google Scholar] [CrossRef]
- Huang, X.; Xie, K.; Leng, S.; Yuan, T.; Ma, M. Improving Quality of Experience in multimedia Internet of Things leveraging machine learning on big data. Futur. Gener. Comput. Syst. 2018, 86, 1413–1423. [Google Scholar] [CrossRef]
- Miori, V.; Russo, D. Improving life quality for the elderly through the Social Internet of Things (SIoT). In Proceedings of the Global Internet Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; 2017; pp. 1–6. [Google Scholar] [CrossRef]

| Quality Metrics and Factors | Findings | References | |
|---|---|---|---|
| QoL and its dimensions |
| [27,28,30,31,33,88,89,90] | |
| QoE | Security perception |
| [39] |
| IF | System |
| [39,49,71,72,73,74,77,78,79,80,83,84,85,87] |
| Human |
| [49,71,77,78,79,80,83,84,85,87] | |
| Context |
| [49,71,77,78,79,80,83,84,85,87] | |
| Influence Factor Type | Web of Things | |
|---|---|---|
| Context influence factors | Price Mobility Time of day/week/month/year Type of task Location Environment Economic state Technical and information context Device context Social context Spatial context Data confidentiality Affiliation Access control | User Who (Identity) Where (Location) When (Time) What (Activity, Service, Capability) Why Physical Application Communication System Presentation Execution Tagging |
| Human influence factors | Age Lifestyle User routine Gender Culture Emotional state Prior experience | Mood Physical disabilities Mental state Knowledge Education level Personality Health state Productivity |
| System influence factors | WoT device characteristics Terminal device characteristics Battery lifetime Computational resources Storage capacity Operating system Usability Physical phenomena of wireless/wired channel – variability Wireless/wired channel reliability Wireless/wired capacity Wireless/wired channel variability Handover Brand Security Encryption Access control Risk 3rd party seal Quality Aesthetics/visual representation of elements | Availability Reliability Reputation Delay Ease of use Access Control IPSEC Authorization SSL/TLS VPN Encryption Identity management Non-repudiation Identification Buffer overflow Access Decision Facility SmartOrBAC (organization-based access control) Authentication |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Baraković, S.; Baraković Husić, J.; Maraj, D.; Maraj, A.; Krejcar, O.; Maresova, P.; Melero, F.J. Quality of Life, Quality of Experience, and Security Perception in Web of Things: An Overview of Research Opportunities. Electronics 2020, 9, 700. https://doi.org/10.3390/electronics9040700
Baraković S, Baraković Husić J, Maraj D, Maraj A, Krejcar O, Maresova P, Melero FJ. Quality of Life, Quality of Experience, and Security Perception in Web of Things: An Overview of Research Opportunities. Electronics. 2020; 9(4):700. https://doi.org/10.3390/electronics9040700
Chicago/Turabian StyleBaraković, Sabina, Jasmina Baraković Husić, Dardan Maraj, Arianit Maraj, Ondrej Krejcar, Petra Maresova, and Francisco Jose Melero. 2020. "Quality of Life, Quality of Experience, and Security Perception in Web of Things: An Overview of Research Opportunities" Electronics 9, no. 4: 700. https://doi.org/10.3390/electronics9040700
APA StyleBaraković, S., Baraković Husić, J., Maraj, D., Maraj, A., Krejcar, O., Maresova, P., & Melero, F. J. (2020). Quality of Life, Quality of Experience, and Security Perception in Web of Things: An Overview of Research Opportunities. Electronics, 9(4), 700. https://doi.org/10.3390/electronics9040700








