Design and Power Management of a Secured Wireless Sensor System for Salton Sea Environmental Monitoring
Abstract
1. Introduction
Related Work
2. Materials and Methods
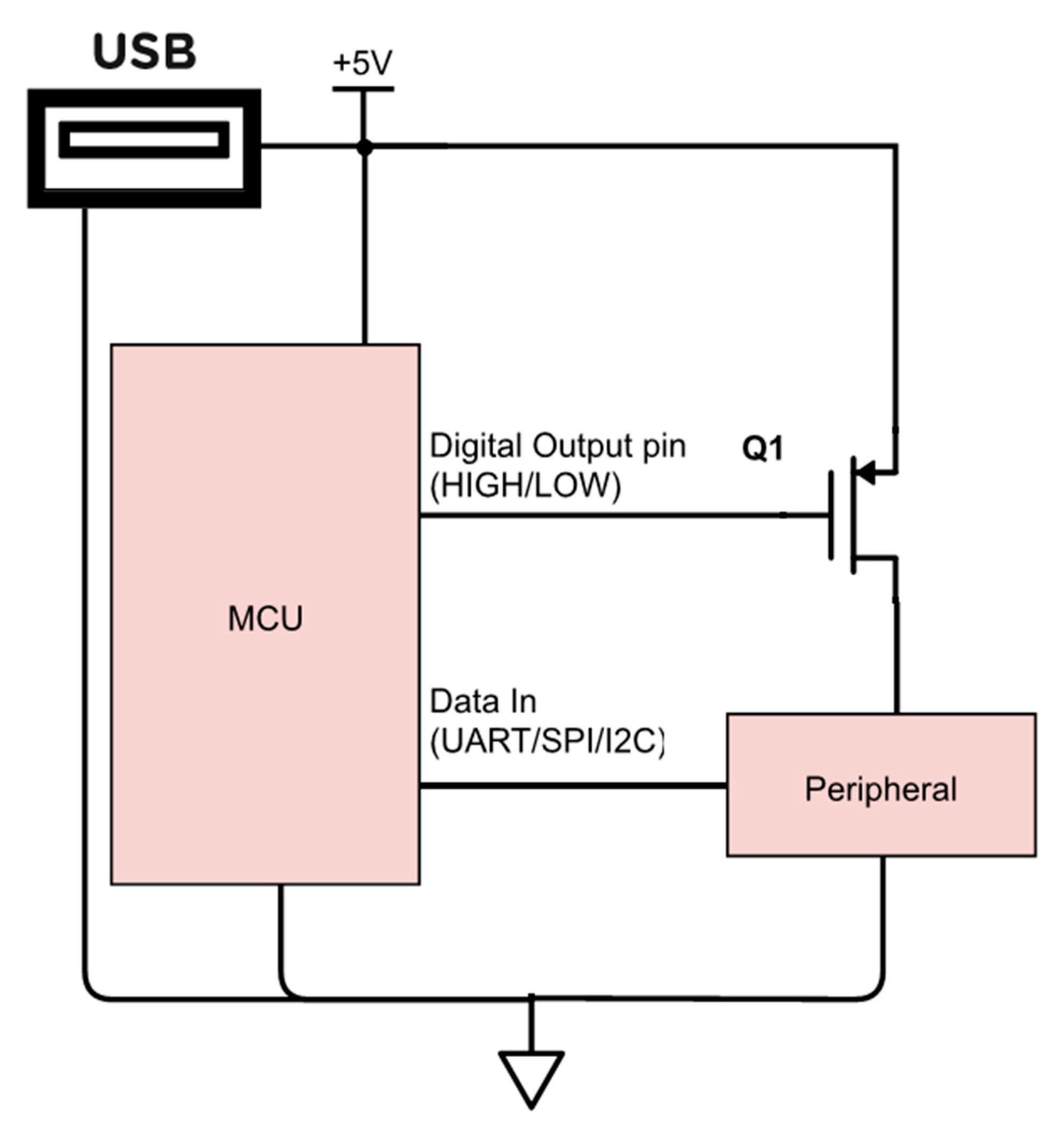
2.1. Hardware
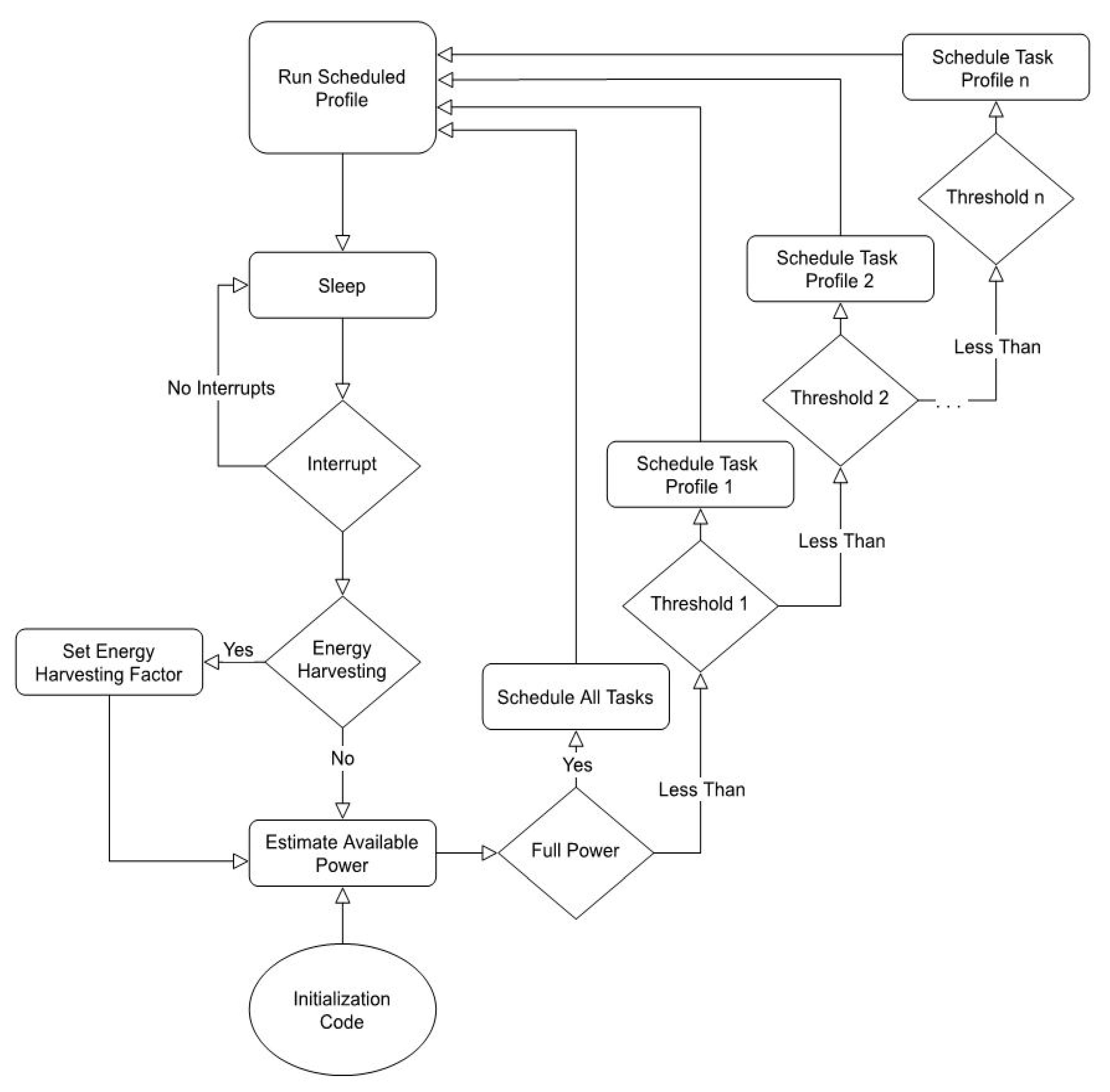
2.2. Software
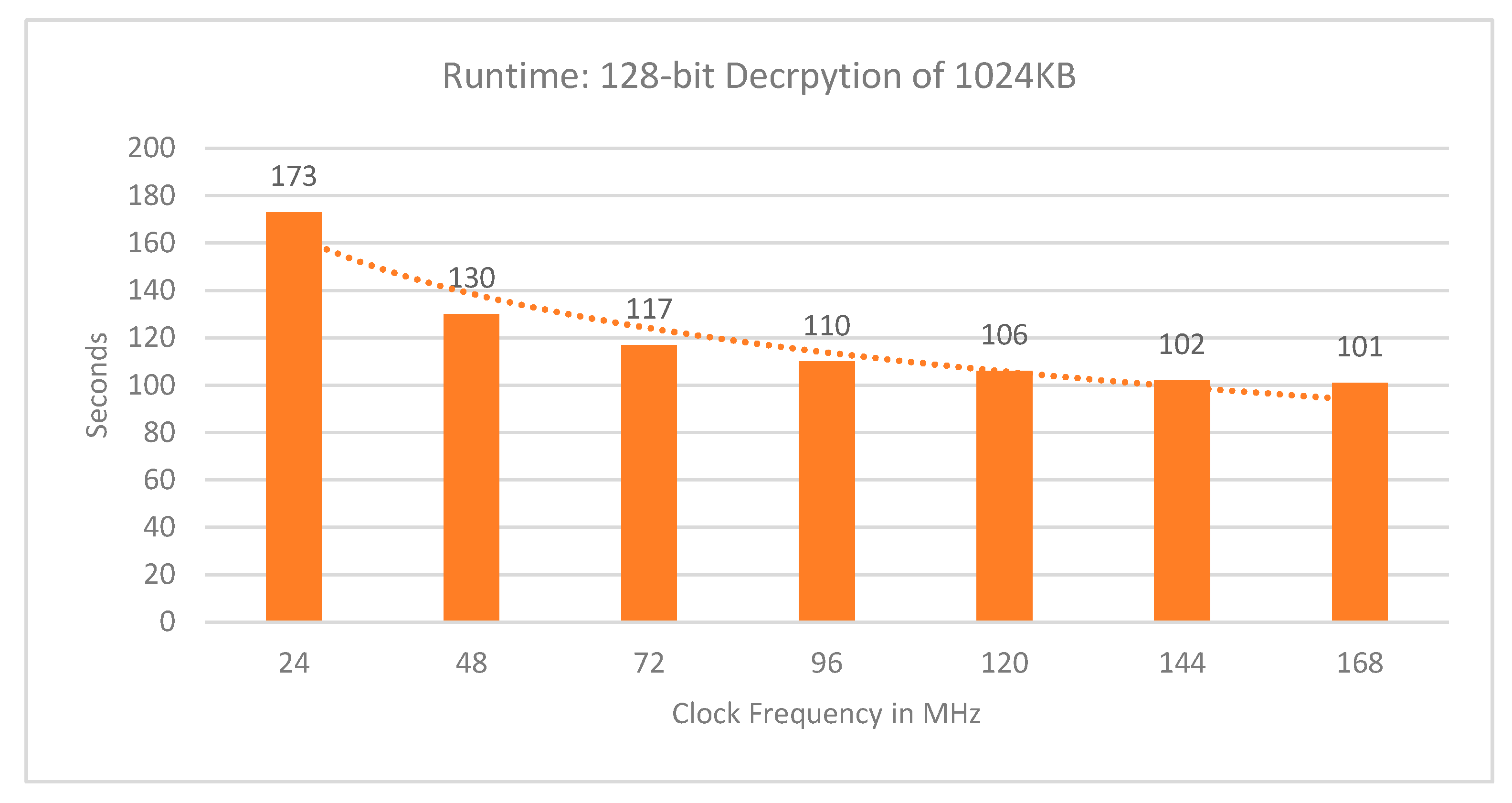
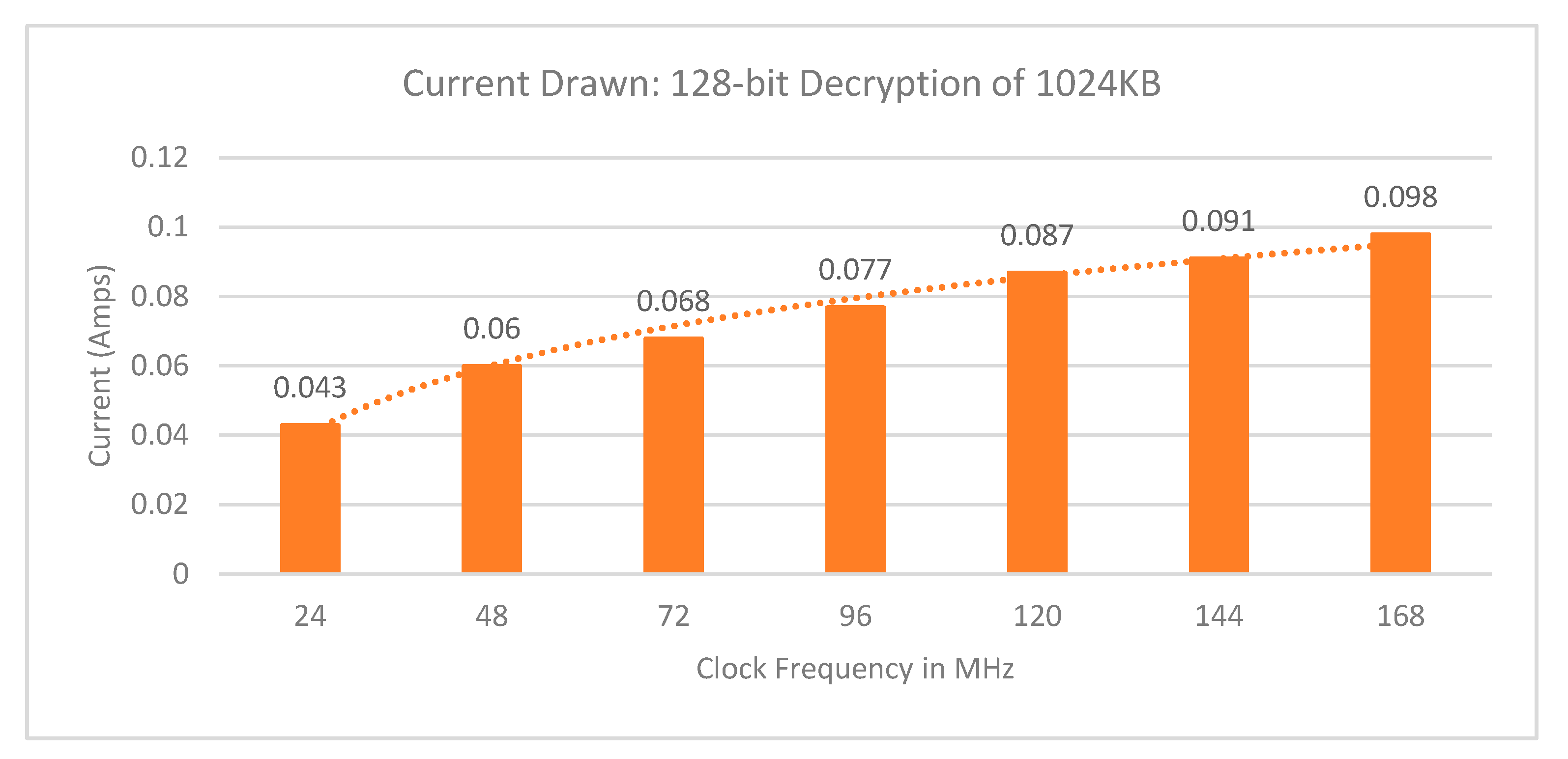
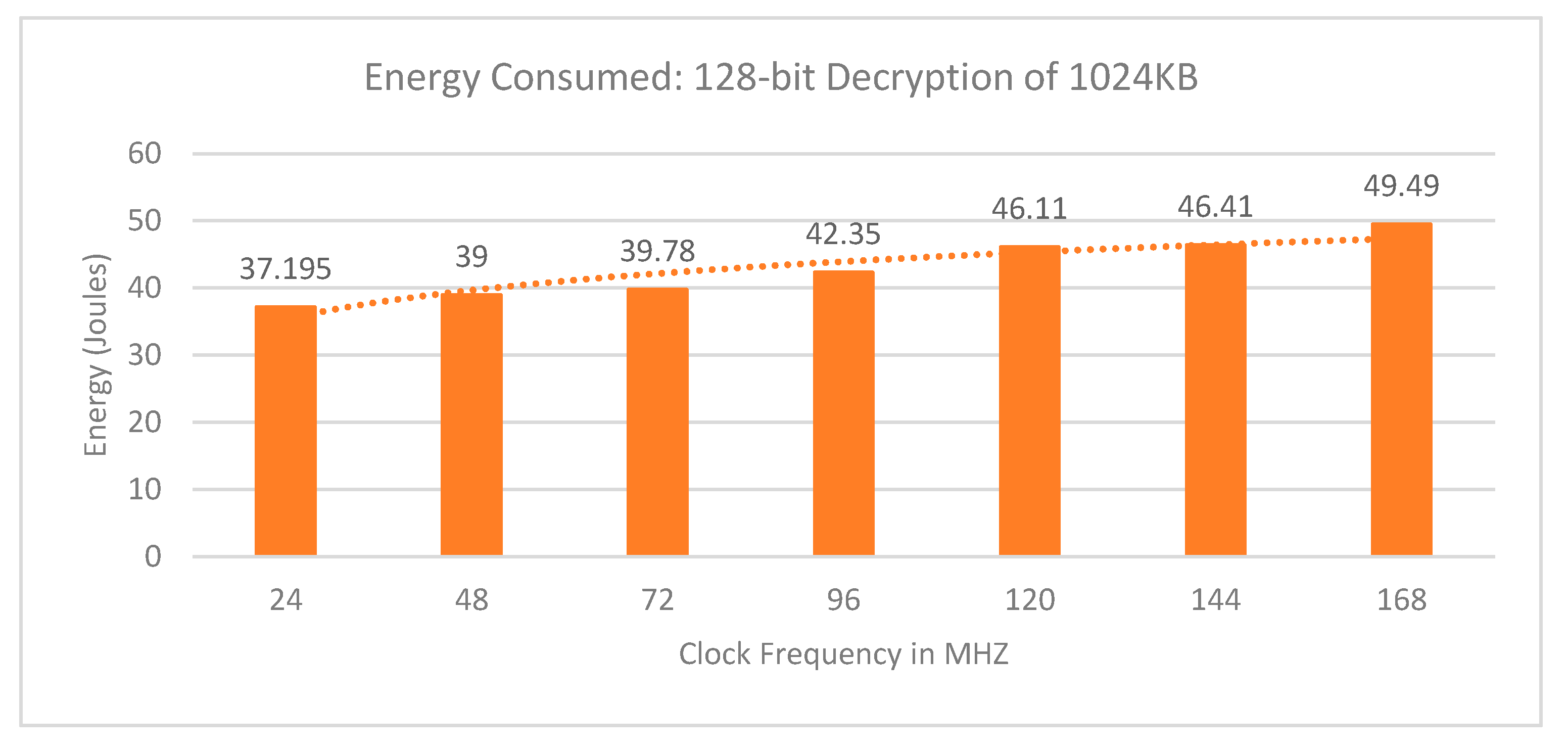
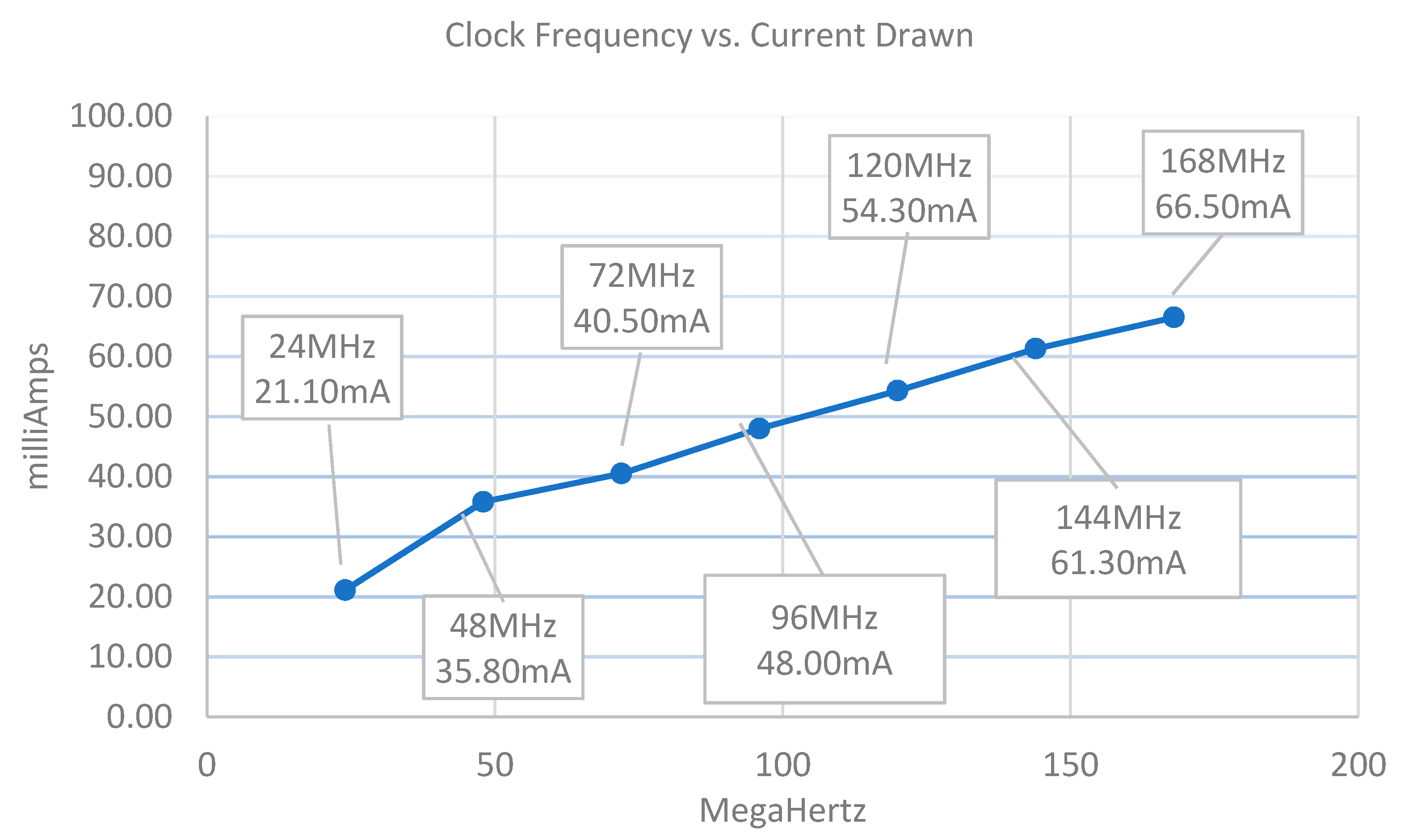
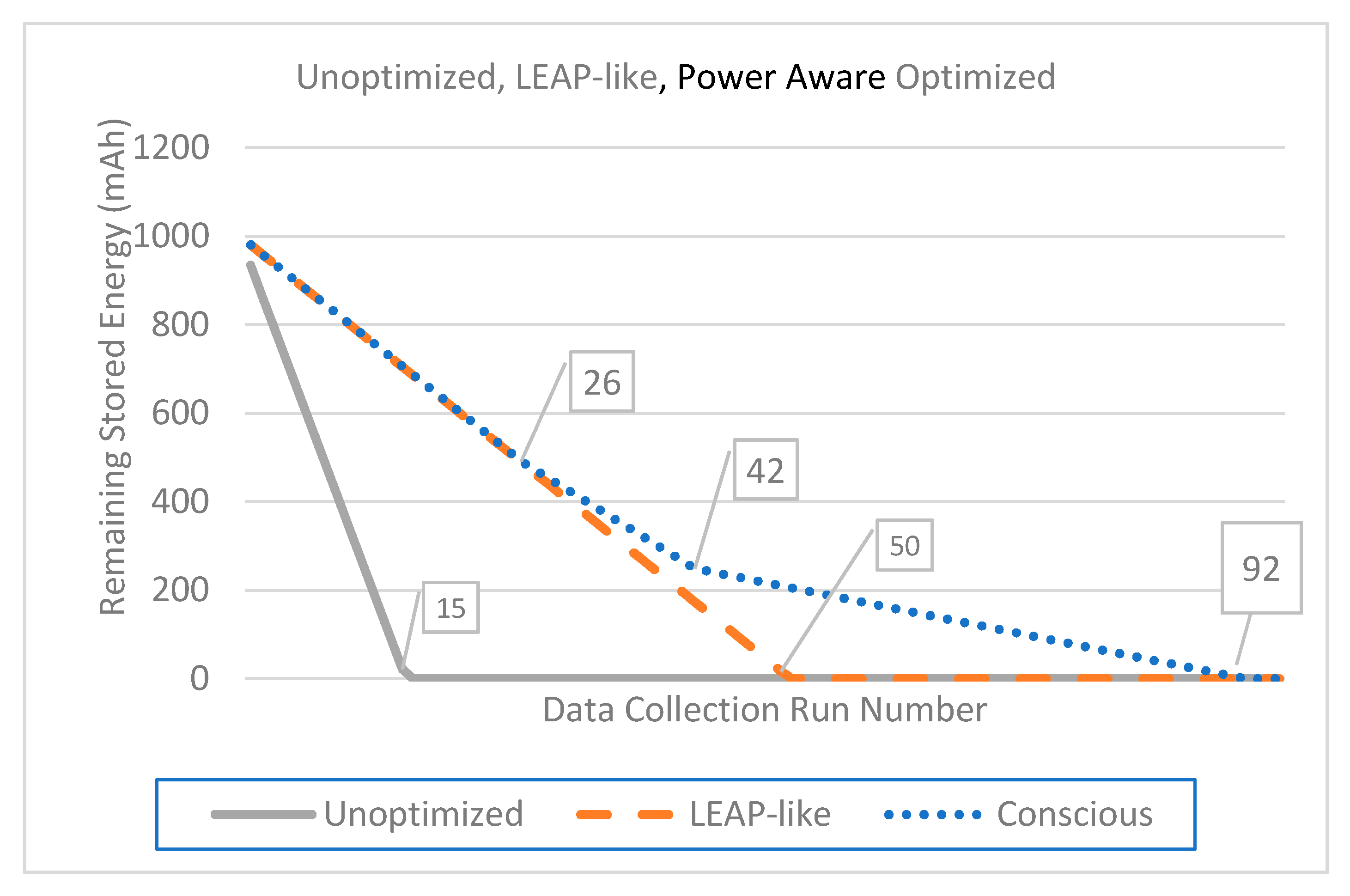
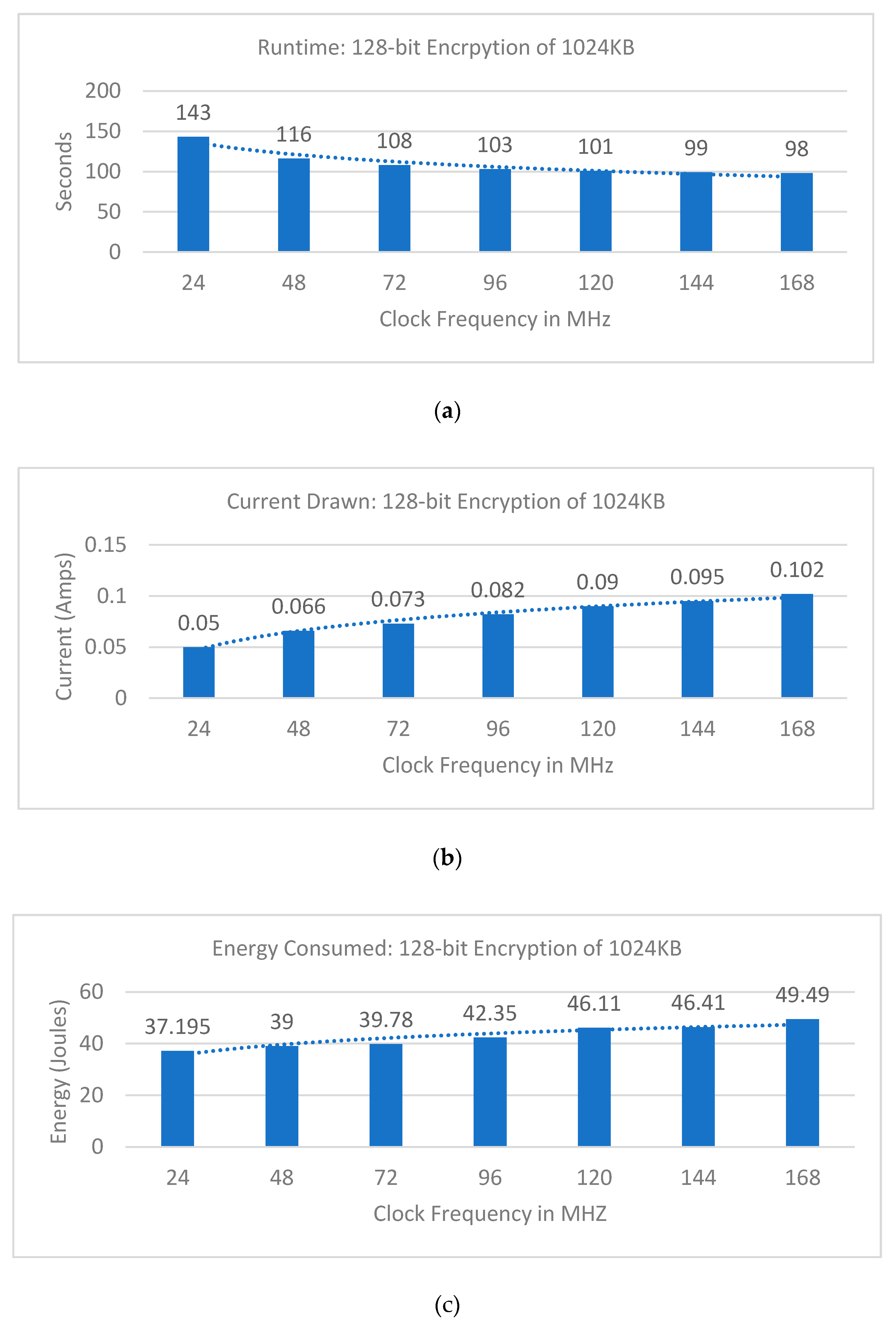
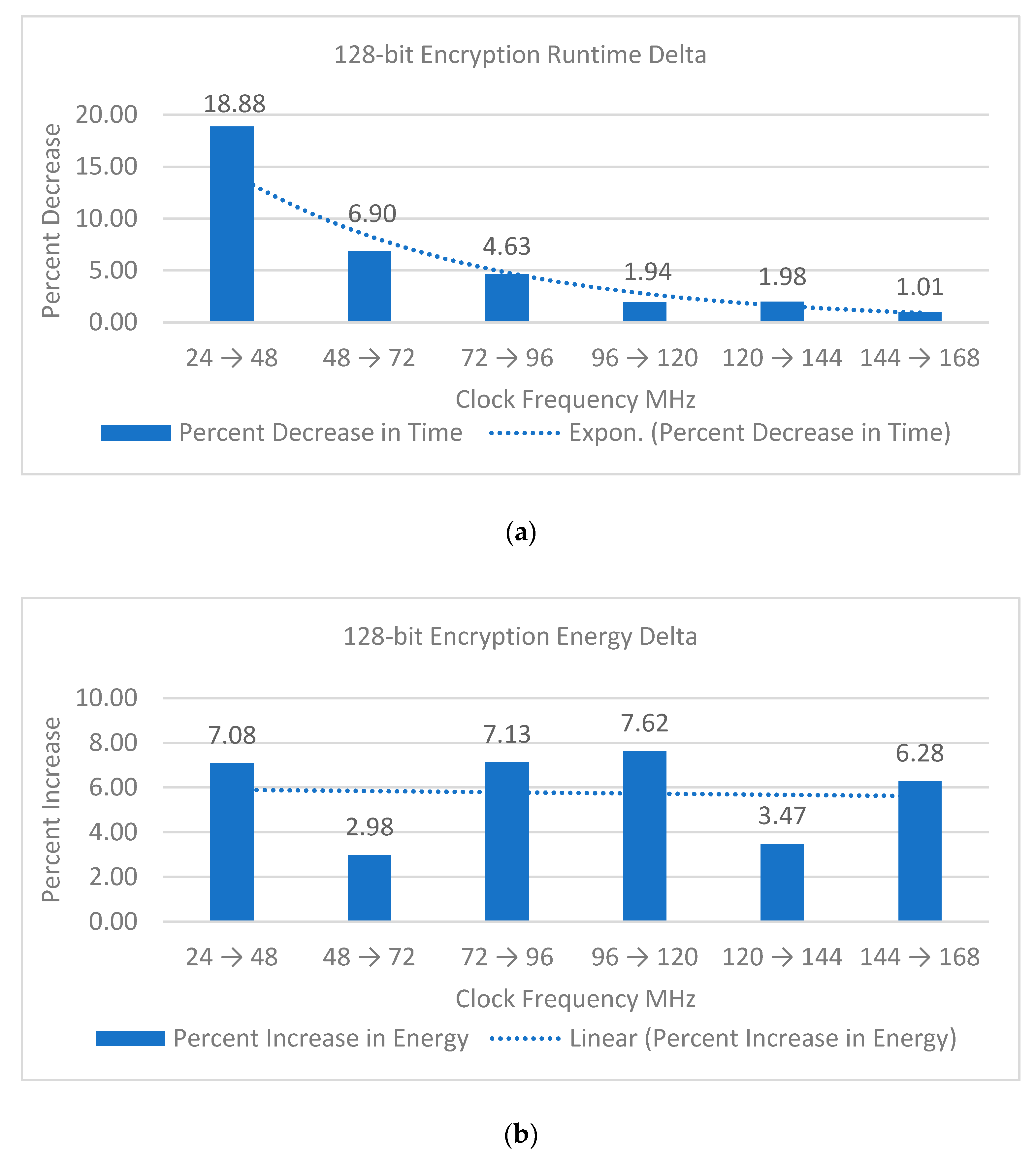
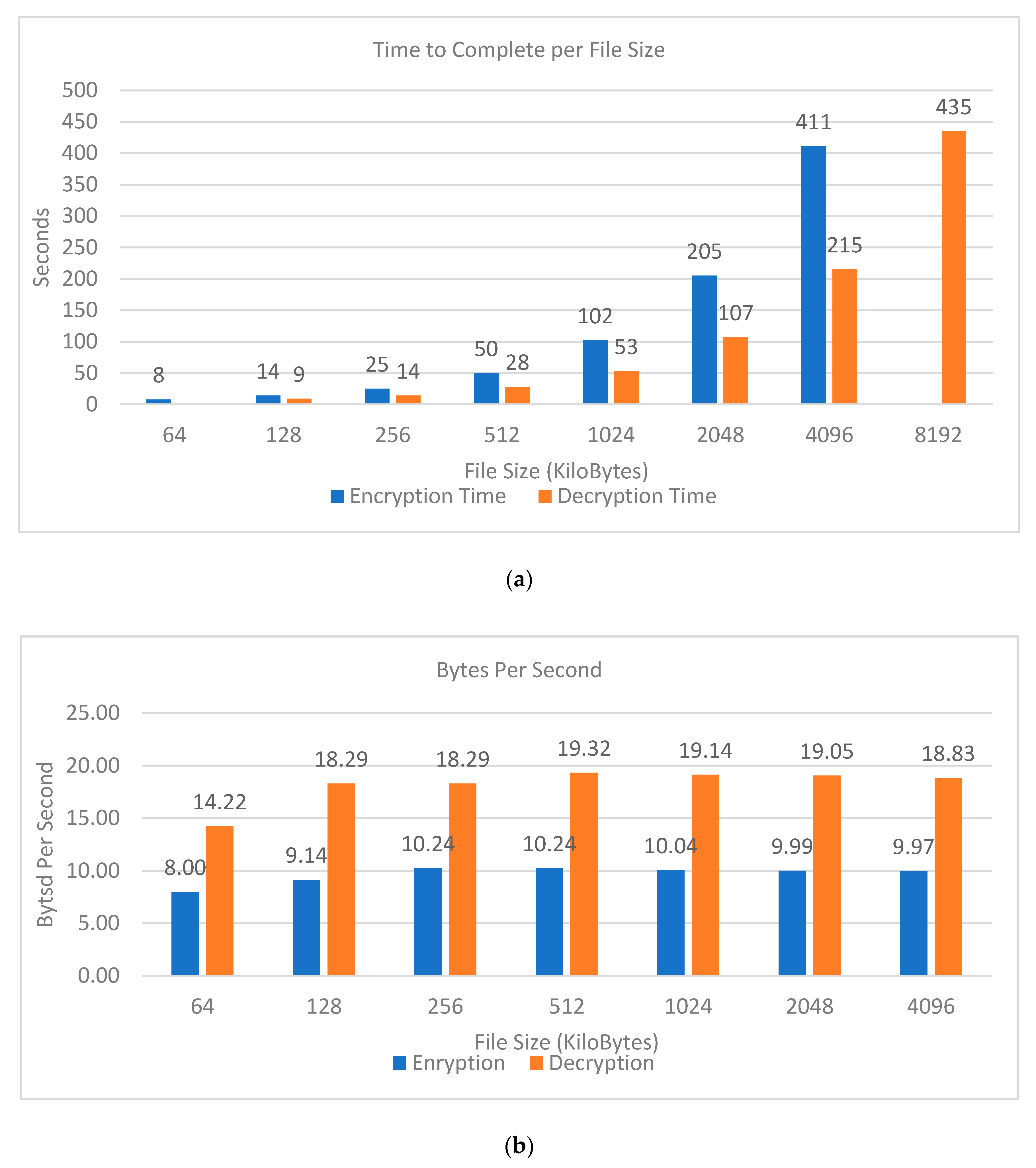
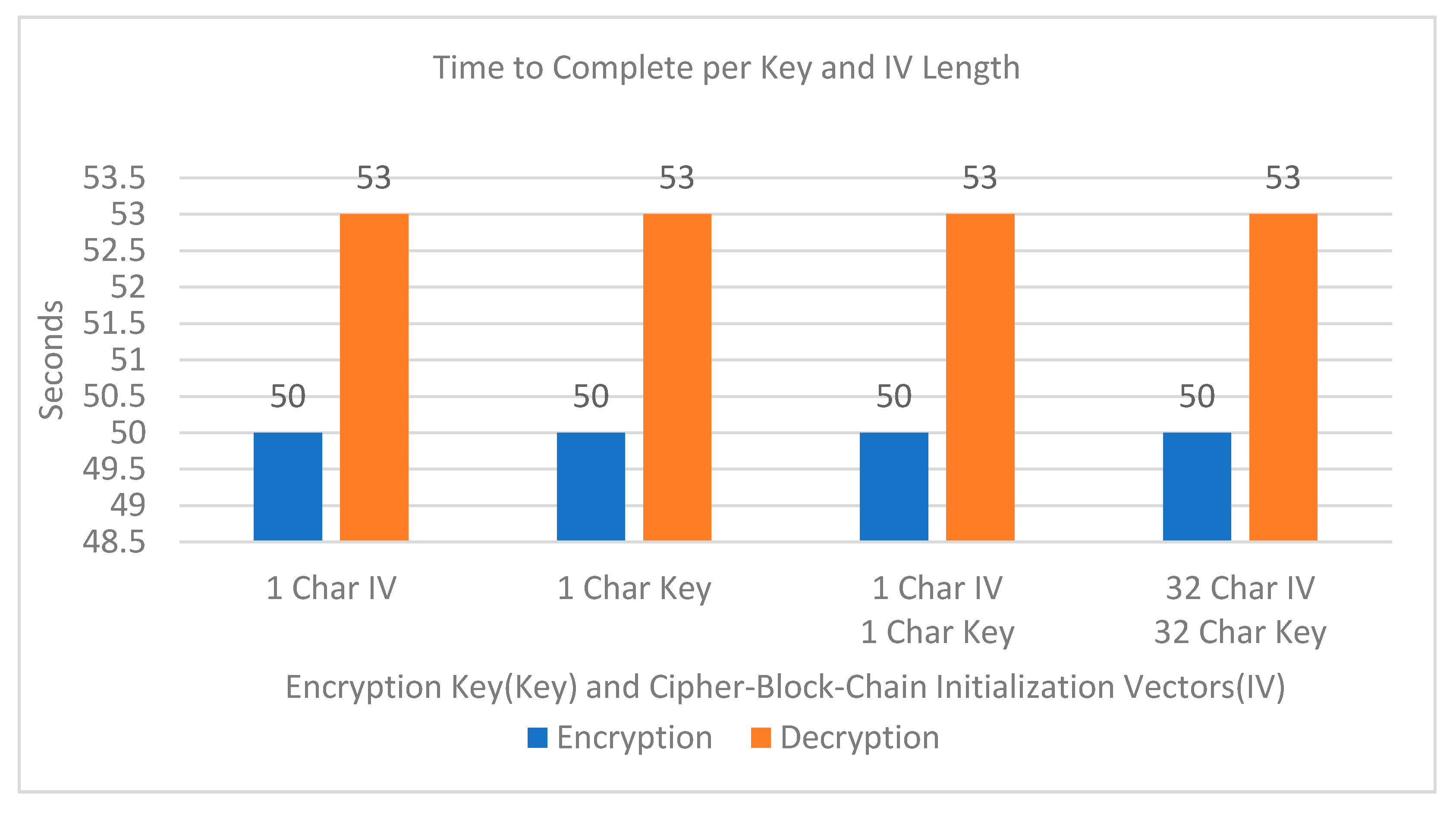
3. Results
3.1. Theoretical Application
3.2. Security
4. Discussion
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A


References
- State of California Department of Water Resources, California Natural Resources Agency, California Department of Fish and Wildlife, Salton Sea Management Program Phase 1: 10-Year Plan. Available online: http://www.socalwaterdialogue.org/calendar/papers/2017/June/3_SaltonSeaManagementProgram.pdf (accessed on 21 March 2020).
- Frie, A.L.; Dingle, J.H.; Ying, S.C.; Bahreini, R. The effect of a receding saline Lake (the Salton Sea) on airborne particulate matter composition. Environ. Sci. Technol. 2017, 51, 8283–8292. [Google Scholar] [CrossRef] [PubMed]
- Bradley, T.; Yanega, G. The Ecological Future of the Salton Sea. Available online: https://pacinst.org/publication/ecology-and-future-salton-sea/ (accessed on 21 March 2020).
- Lawrence, D.K. Toxic Blowing Dust and Mounting Social Harms: Understanding Slow Violence at the Salton Sea as a State-Corporate Crime and Environmental Injustice. Northern Arizona University M.S. thesis 2019. [Google Scholar]
- Randy. Home > Blog > The Wandering Minds > How Hot Is Salton Sea? Available online: https://www.saltonseawalk.com/how-hot-is-salton-sea/ (accessed on 21 March 2020).
- Wendt, Z. Introducing the Top 10 Dev Boards of 2018. Available online: https://www.arrow.com/en/research-and-events/videos/the-top-10-development-platforms-dev-kits-2018 (accessed on 4 March 2019).
- Parra, L.; Sendra, S.; García, L.; Lloret, J. Design and deployment of low-cost sensors for monitoring the water quality and fish behavior in aquaculture tanks during the feeding process. Sensors 2018, 18, 750. [Google Scholar] [CrossRef]
- Hu, S. Dynamic monitoring based on wireless sensor networks of IoT. In Proceedings of the 2015 International Conference on Logistics, Informatics and Service Sciences (LISS), Barcelona, Spain, 27–29 July 2015. [Google Scholar]
- Prauzek, M.; Konecny, J.; Borova, M.; Janosova, K.; Hlavica, J.; Musilek, P. Energy Harvesting Sources, Storage Devices and System Topologies for Environmental Wireless Sensor Networks: A Review. Sensors 2018, 18, 2446. [Google Scholar] [CrossRef] [PubMed]
- Prauzek, M.; Krömer, P.; Rodway, J.; Musilek, P. Differential evolution of fuzzy controller for environmentally-powered wireless sensors. Appl. Soft Comput. 2016, 48, 193–206. [Google Scholar] [CrossRef]
- Djajadi, A.; Wijanarko, M. Ambient environmental quality monitoring using IoT sensor network. Internetworking Indones. J. 2016, 8, 41–47. [Google Scholar]
- Engmann, F.; Katsriku, F.A.; Abdulai, J.D.; Adu-Manu, K.S.; Banaseka, F.K. Prolonging the lifetime of wireless sensor networks: A review of current techniques. Wirel. Commun. Mob. Comput. 2018. [CrossRef]
- Rao, B.S.; Rao, K.S.; Ome, N. Internet of Things (IoT) based weather monitoring system. Int. J. Adv. Res. Comput. Commun. Eng. 2016, 5, 312–319. [Google Scholar]
- McIntire, D.; Ho, K.; Yip, B.; Sing, A.; Wu, W.; Kaiser, J.W. The Low Power Energy Aware Processing (LEAP) Embedded Networked Sensor System’. In Proceedings of the 5th International Conference on Information Processing in Sensor Networks, Nashville, TN, USA, 19–21 April 2006. [Google Scholar]
- Ismat, T. Comparative Analysis of AES Algorithms and Implementation of AES in Arduino Dhaka. Available online: http://dspace.bracu.ac.bd/xmlui/handle/10361/4889 (accessed on 21 March 2020).
- Diaz, K.; Teh, Y.K. Power Optimization of Arduino-Based Sensor System for Salton Sea Environmental Monitoring. In Proceedings of the 2019 IEEE 62nd International Midwest Symposium on Circuits and Systems (MWSCAS), Dallas, TX, USA, 4–7 August 2019. [Google Scholar]
- ON Semiconductor. FQP27P06 60 V P-Channel MOSFET. Available online: https://www.onsemi.com/pub/Collateral/FQP27P06-D.PDF (accessed on 21 March 2020).
- GPS Schematic. Available online: http://wiki.seeedstudio.com/Grove-GPS/#version (accessed on 4 March 2020).
- Ultra High Sensitivity and Low Power GPS Receiver Module. Available online: https://www.mouser.com/datasheet/2/744/Seeed_113020003-1217502.pdf (accessed on 21 March 2020).
- Shinyei. Particle Sensor Model PPD42NS. Available online: https://www.shinyei.co.jp/stc/eng/products/optical/ppd42nj.html (accessed on 21 March 2020).
- Matej Sychra, Thinx-Aies-Lib. GitHub Repository. Available online: https://github.com/suculent/thinx-aes-lib/tree/master (accessed on 21 March 2020).
| Condition | E-1612-UB GPS | PPD42NS Dust Sensor |
|---|---|---|
| Direct Connection | 93 mA–103 mA | 134 mA |
| MOS-ON Connect | 93 mA–103 mA | 134 mA |
| Direct Disconnected | 54 mA Integrally regulated | 54 mA |
| MOS-OFF Disconnected | 54 mA | 54 mA |
| Vin = 5 V | E-1612-UB GPS | PPD42NS Dust Sensor |
|---|---|---|
| VDD, NMOS-ON | 4.94 V | 4.84 V |
| VDD, NMOS-OFF | 0.70 V | 0.00 V |
| Specified Voltage Input Range | 3.3 V [18,19] Integrally regulated | 4.5 V–5.5 V [20] |
| Communication | Live | Stopped | Difference |
|---|---|---|---|
| UART | 54 mA | 53 mA | −1 mA |
| SPI | 54 mA | 48 mA | −6 mA |
| I2C | 54 mA | 48 mA | 0 mA |
| Total | 54 mA | 47 mA | −7 mA |
| State | Current Drawn | Difference |
|---|---|---|
| Awake | 54 mA | N/A |
| Sleep | 2 mA | −52 mA |
| Deep Sleep | 0.370 mA | −53.63 mA |
| Hibernate | 0.190 mA | −53.81 mA |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Diaz, K.; Teh, Y.-K. Design and Power Management of a Secured Wireless Sensor System for Salton Sea Environmental Monitoring. Electronics 2020, 9, 544. https://doi.org/10.3390/electronics9040544
Diaz K, Teh Y-K. Design and Power Management of a Secured Wireless Sensor System for Salton Sea Environmental Monitoring. Electronics. 2020; 9(4):544. https://doi.org/10.3390/electronics9040544
Chicago/Turabian StyleDiaz, Kristian, and Ying-Khai Teh. 2020. "Design and Power Management of a Secured Wireless Sensor System for Salton Sea Environmental Monitoring" Electronics 9, no. 4: 544. https://doi.org/10.3390/electronics9040544
APA StyleDiaz, K., & Teh, Y.-K. (2020). Design and Power Management of a Secured Wireless Sensor System for Salton Sea Environmental Monitoring. Electronics, 9(4), 544. https://doi.org/10.3390/electronics9040544




