A Time-Based Dynamic Operation Model for Webpage Steganography Methods
Abstract
1. Introduction
- We proposed a time-based dynamic operation model (TDOM) that improves the performance of existing webpage steganography methods in terms of hiding capacity and undetectability.
- We designed two time-based dynamic operation algorithms TDOA-C and TDOA-U, which improve the hiding capacity of existing methods and TDOA-U for improving the undetectability of existing methods, respectively.
- We conducted comparative experiments and numerical analysis to validate our model and show the performance of our proposed algorithms. For this, we implemented two webpage steganography methods with our TDOM (CCL with TDOA-C and COA with TDOA-C) and tested them in the web environment; CCL stands for Changing the Cases of Letters in tags and attributes and COA stands for Changing the Order of Attributes.
- In addition to the above contributions, we hope that this study can provide useful information about webpage steganography techniques and their dynamic operations, which can be used in cyberattacks or cybercrimes, raise an alarm to security engineers and researchers, and, thus, attract them to research defense mechanisms and techniques against them. Meanwhile, we note that our study can be used in positive use cases because the steganography-based covert communication can be used to avoid unauthorized and illegal eavesdroppers.
2. Background and Related Works
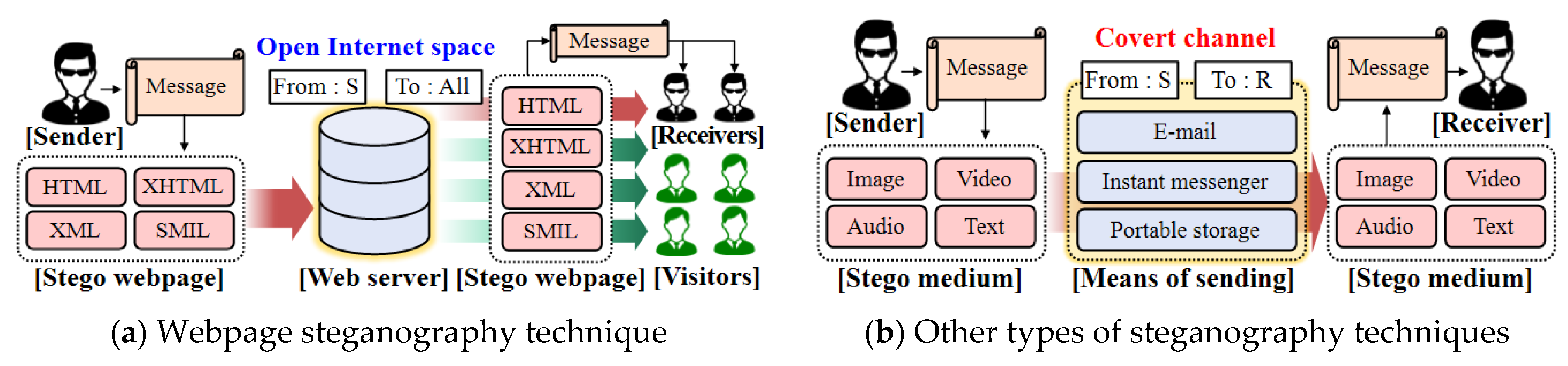
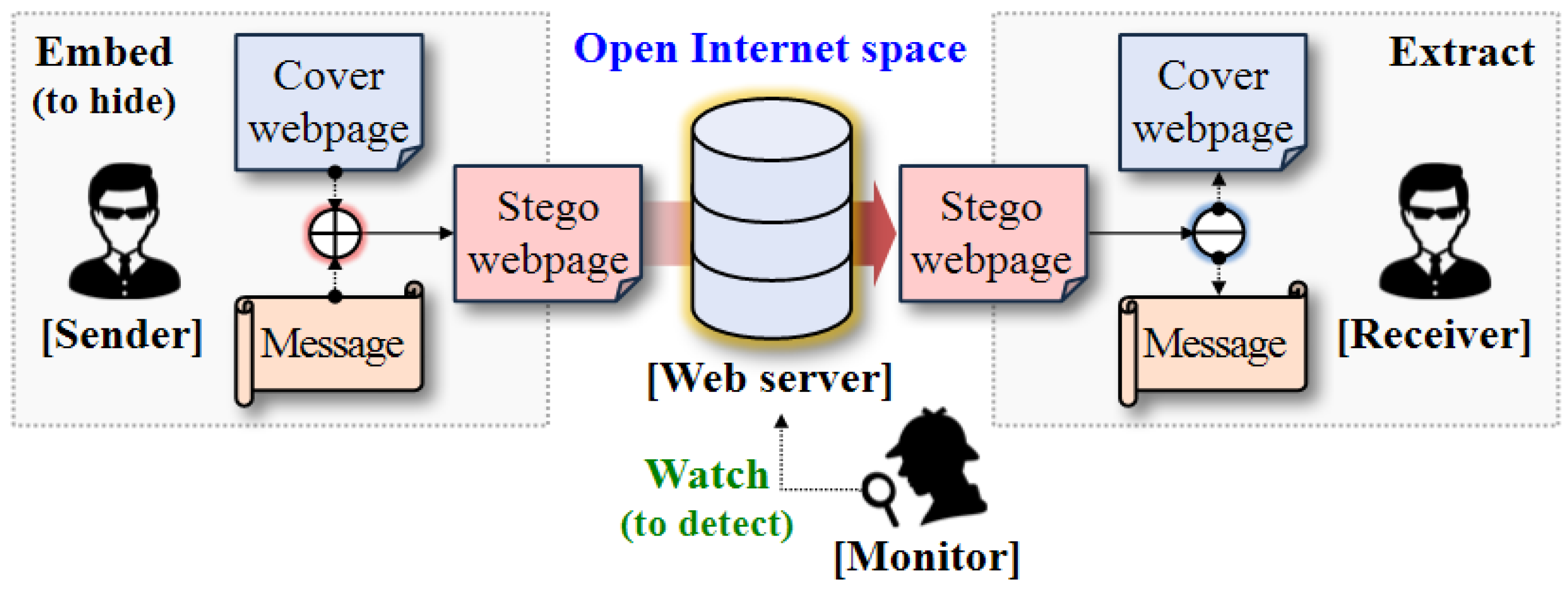
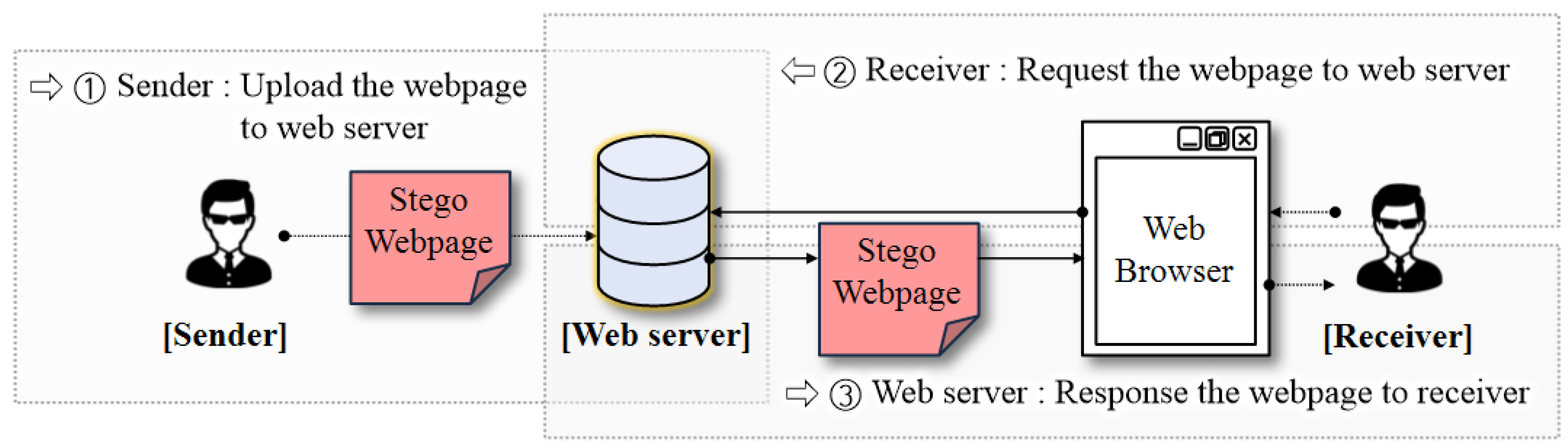
2.1. Webpage Steganography-Based Covert Communication Model
- Hiding capacity: The amount of information that can be embedded in a cover webpage, and this depends on the embedding algorithm of the webpage steganography method and a cover webpage.
- Undetectability: This refers to a degree that the embedded hidden message is not detected by a monitor (passive warden).
- Robustness: This refers to a degree that the embedded hidden message is not destroyed by a monitor (active warden).
2.2. Three Representative Webpage Steganography Approaches and Previous Studies
2.2.1. Adding Invisible Tags or Characters
- Reference [12] proposed a method of inserting extra spaces and tabs into an HTML file.
- References [13,14] proposed a method of using various characters such as   or   that are displayed as blank spaces in the web browser. In addition to this method, References [15,16,17] applied cryptography techniques for improving undetectability, Reference [15] used AES (Advanced Encryption Standard), Reference [16] used Caesar cipher, and Reference [17] used RSA (Rivest Shamir Adleman), respectively.
- Reference [18] suggested a method that inserts elements only containing tags without contents (attributes and values). For example, texts between <b> with </b> are bolded, but, if there are no texts between tags, there will be no change in the web browser even though those elements are added.
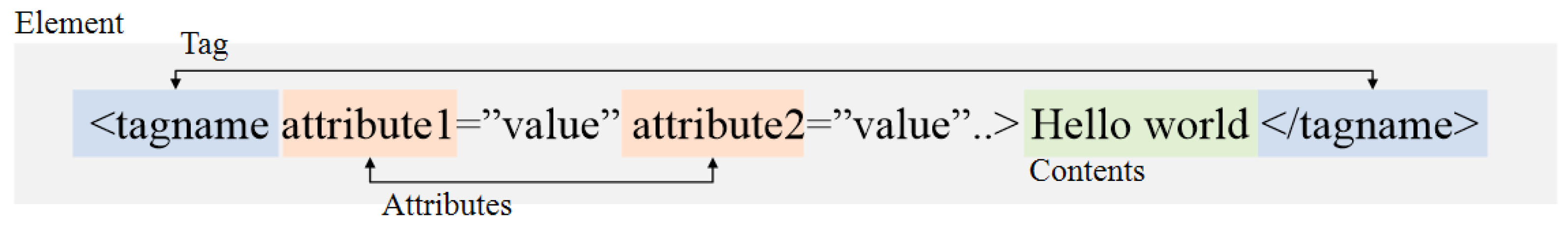
2.2.2. Changing the Case of Letters in Tags and Attributes (CCL Approach)
2.2.3. Changing the Order of Attributes (COA Approach)
- Reference [30] tried to improve the security of this approach by applying cryptography techniques.
- Reference [31] proposed a method that hides 0 or 1 by using whether the attribute belongs to a specific tag. Thus, 1 is hidden when two attributes belong to the same tag. Otherwise, 0 is hidden.
- Reference [36] is a webpage steganography tool, but some HTML tags or attributes newly added after 2006 are not included in their tool.
2.3. Limitations of Previous Studies
- Hiding Capacity (or Capacity): Assuming that, given a webpage, the steganography method and the maximum hiding capacity of a stego webpage is m bits, the total amount of a secret message that the sender can deliver to the receiver is limited to the constant value m bits because the stego webpage does not change and, thus, the receiver will always obtain the same m-bit secret message regardless of request times to the stego webpage.
- Undetectability: Assuming that there is a perfect monitoring and detection tool, the static stego webpage will be captured by the tool at the time when the tool accesses the stego webpage since the stego webpage does not change and, thus, is constantly exposed to any web client.
3. Proposed Model and Algorithms
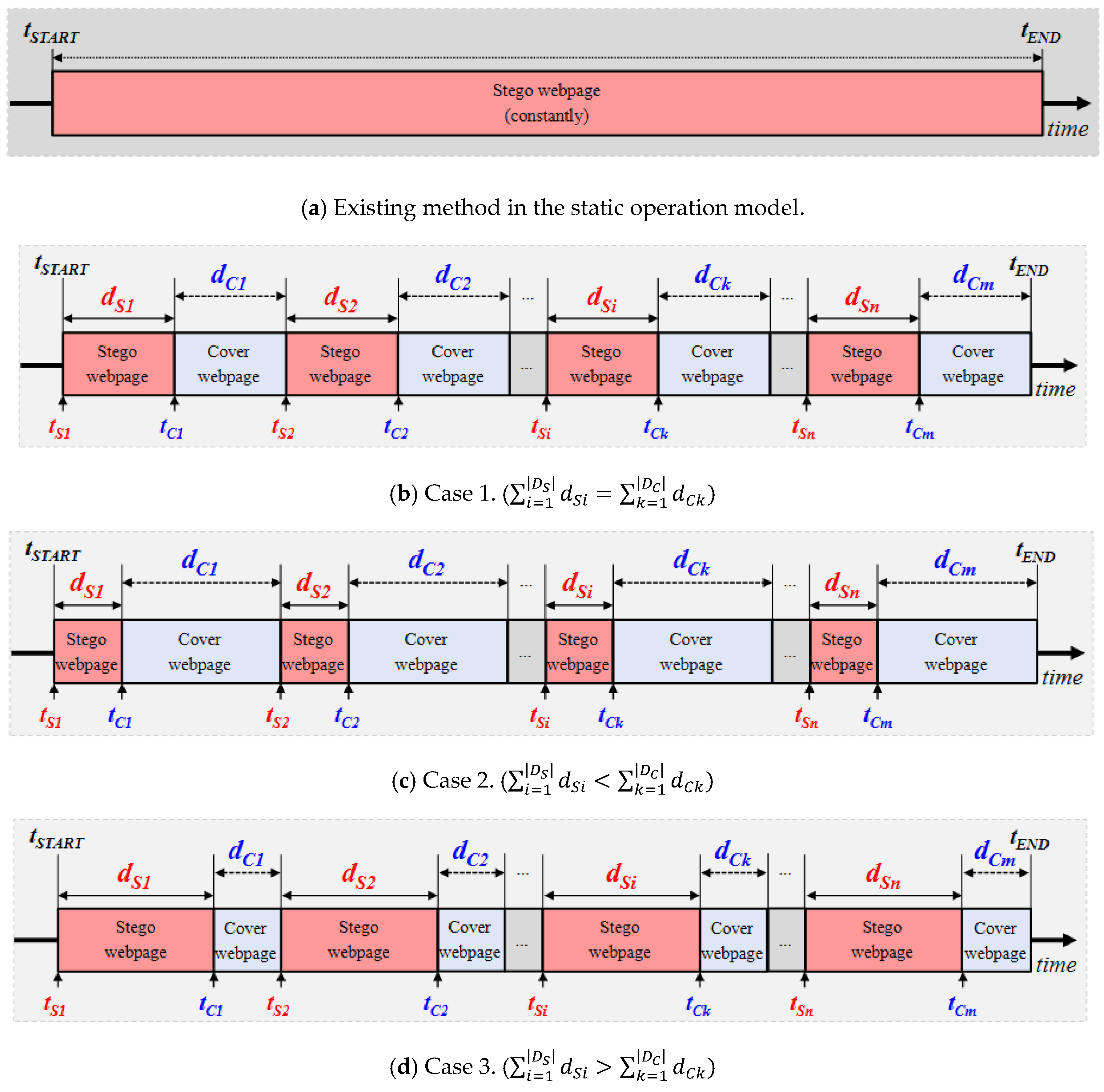
3.1. Our Approach: Time-Based Dynamic Operation Model (TDOM)
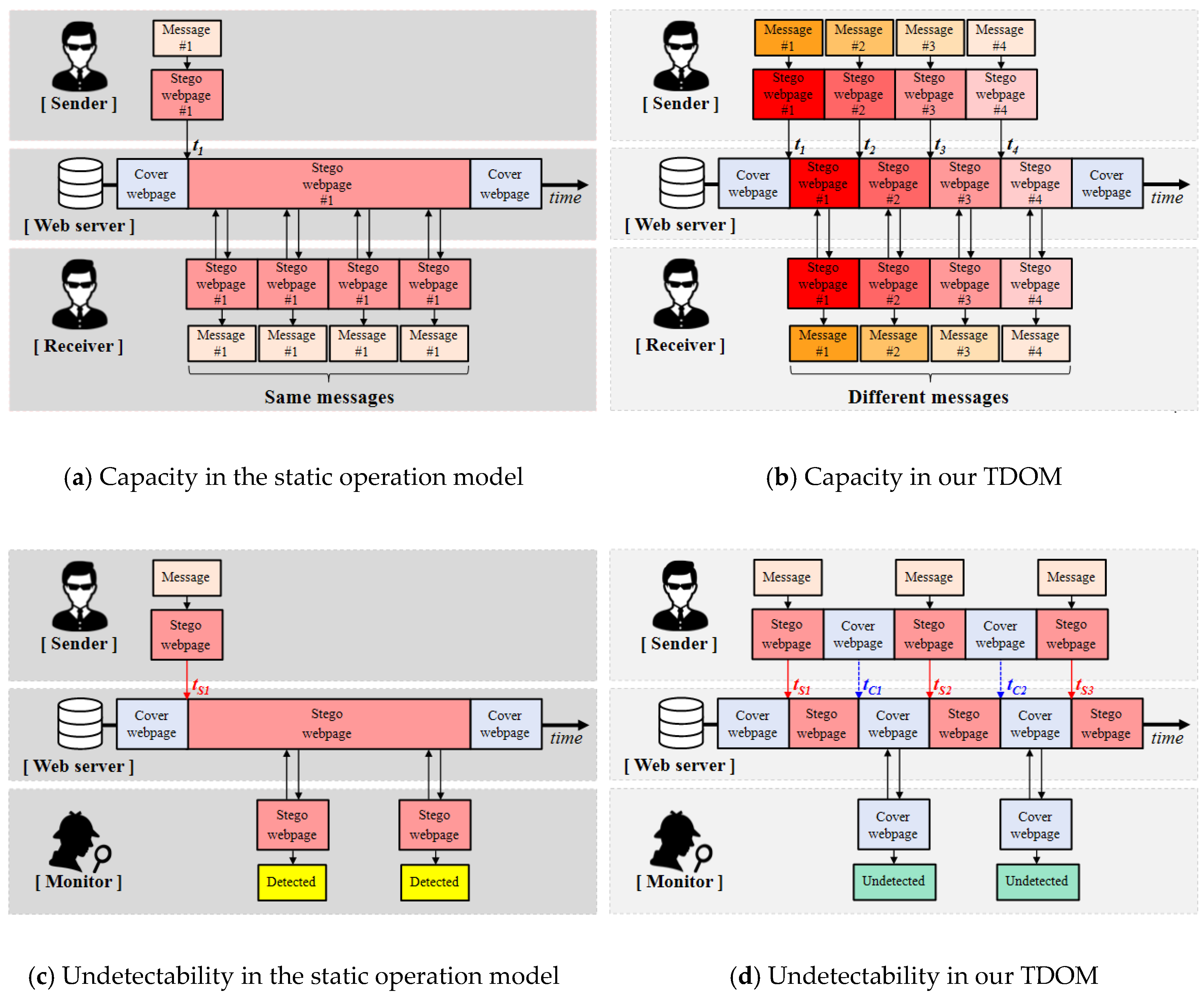
- For higher hiding capacity (or larger amount of secret message delivery): Given the same time slot ( − ), as shown in Figure 6a, a webpage steganography method delivers only one message (#1) in the static operation model. Meanwhile, as shown in Figure 6b, it can deliver four messages (#1–#4) in our TDOM since four different stego webpages are uploaded in turn in the time slot.
- For higher undetectability: Given the same time slot ( − ), as shown in Figure 6c, a stego webpage keeps exposed to users, and, thus, if a powerful monitor (detection system) visits the stego webpage, the monitor can detect the existence of the stego webpage. Meanwhile, as shown in Figure 6d, when the stego webpage is deactivated and replaced with the original webpage two times, the chance that the monitor detects the stego webpage will definitely decrease accordingly.
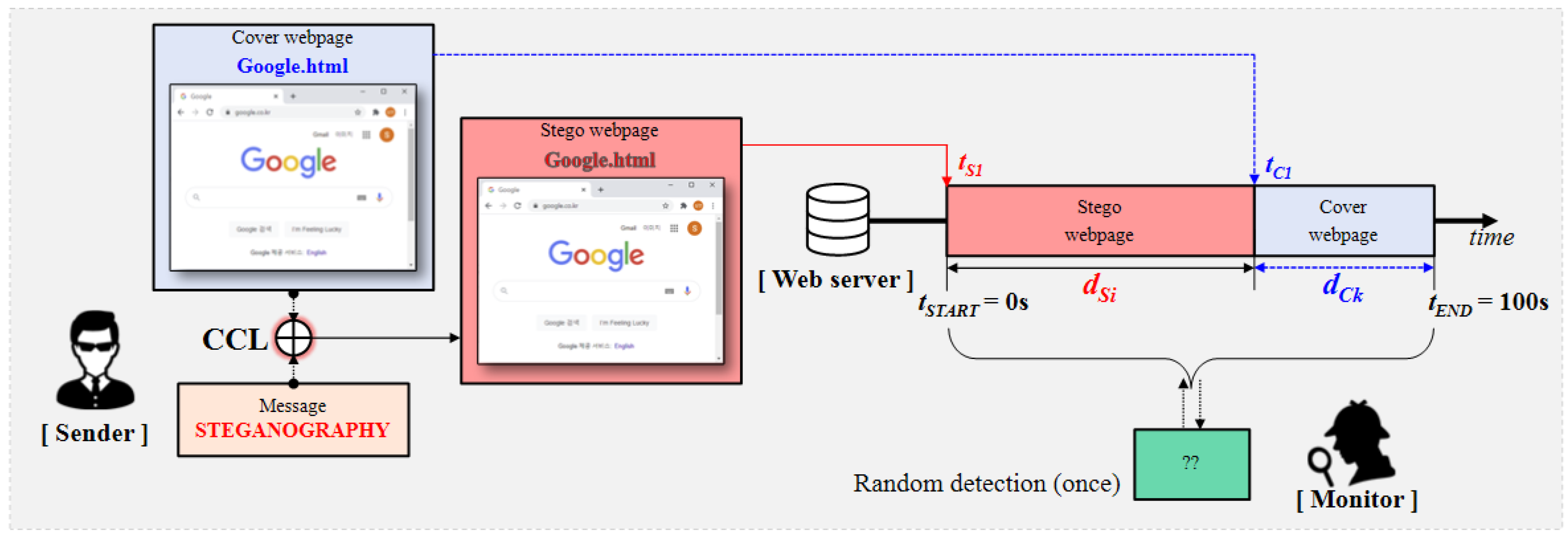
3.2. Time-based Dynamic Operation Algorithm for Hiding Capacity (TDOA-C)
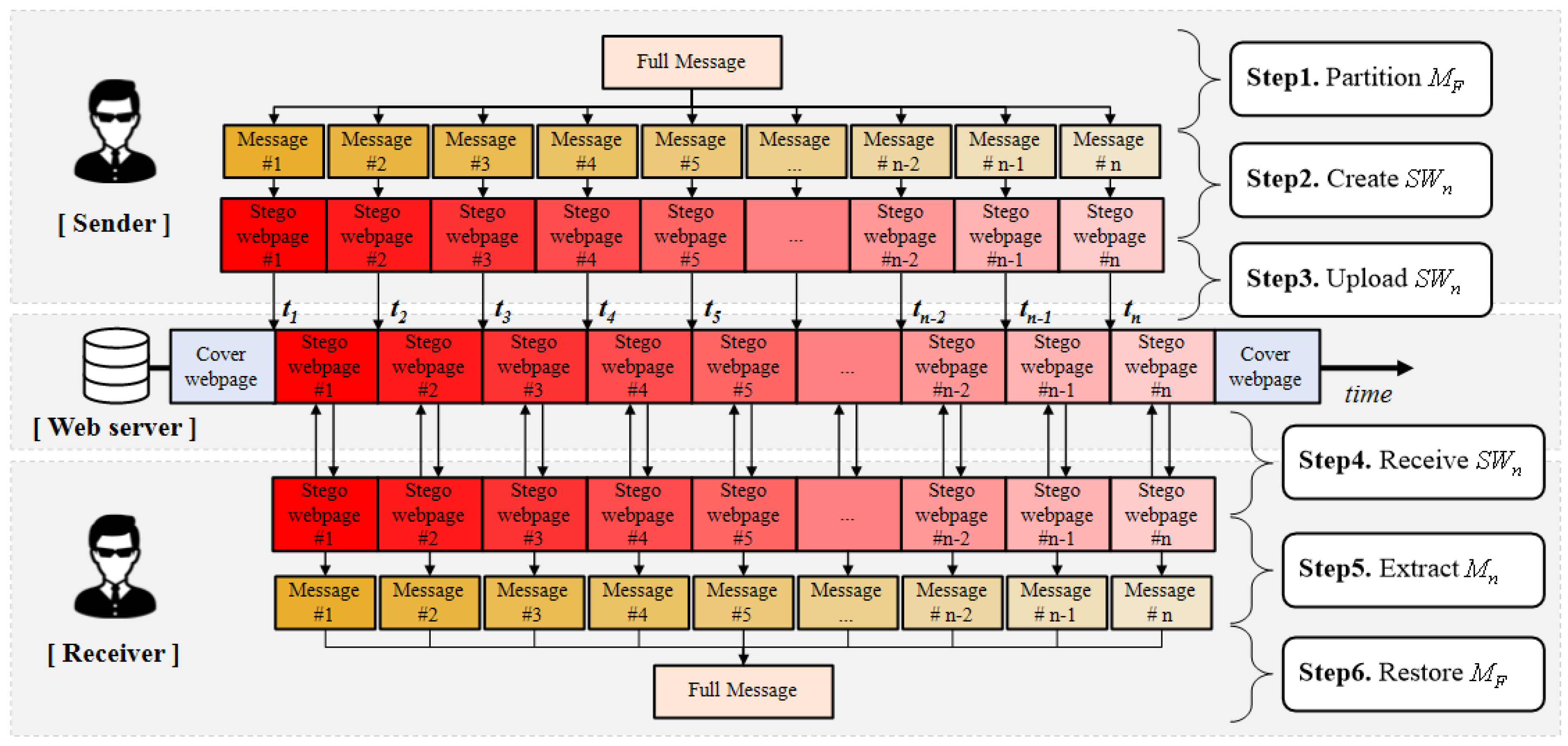
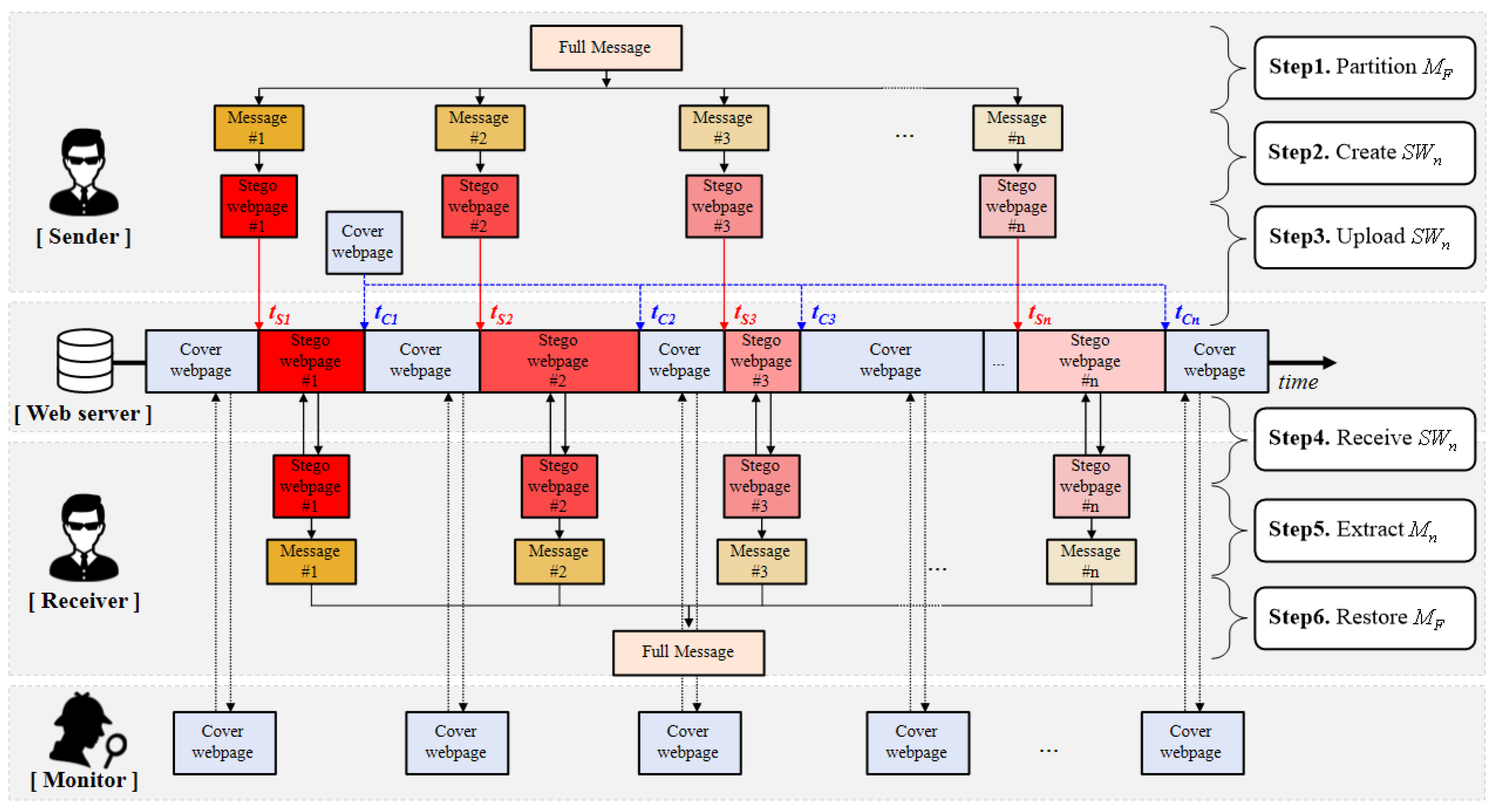
- Step 1. partitions into smaller messages , , …, .
- Step 2. creates stego webpages , , …, by using , , and , , …, .
- Step 3. uploads , , …, to the web server, in turn, at a certain time which is agreed with . For this step, the sender and receiver exchange such information by using another covert channel or in person.
- Step 4. receives each stego webpage, in turn, by accessing the URL where the cover webpage is located at the time period agreed with .
- Step 5. extracts the partitioned secret messages , , …, from received stego webpages.
- Step 6. restores the complete secret message by combining , , …, .
| Algorithm 1 TDOA-C (Time-Based Dynamic Operation Algorithm for Hiding Capacity) | |||
| Definition | |||
| Message | : a full secret message to send to | ||
| a set of partitioned messages | |||
| : the number of partitioned messages | |||
| Webpage | : cover webpage | ||
| a set of stego webpages | |||
| Time | a set of times that agree with | ||
| : the start and end time of covert communication between and | |||
| : current time | |||
| Function | : embeds the secret message into . returns | ||
| : extracts the embedded secret message from . returns | |||
| : partitions into smaller messages returns | |||
| : restores the by combining . returns | |||
| Sender | Receiver | ||
| Input:, , , , , , | Input:, , , , | ||
| Output:, | Output:, , | ||
| Functions:, | Functions:, | ||
| 1: begin | 1: begin | ||
| 2: #Step1 | 2: while | ||
| 3: for from to do #Step2 | 3: for from to do #Step4 | ||
| 4: ) | 4: while True #infinitely repeat | ||
| 5: #add an element into set | 5: if == then | ||
| 6: while | 6: request to a webserver | ||
| 7: for from to do #Step3 | 7: from a webserver | ||
| 8: while True #infinitely repeat | 8: break | ||
| 9: if then | 9: for from to do #Step5 | ||
| 10: upload to webserver | 10: ) | ||
| 11: break | 11: #add into set | ||
| 12: end | 12: #Step6 | ||
| 13: end | |||
3.3. Time-based Dynamic Operation Algorithm for Undetectability (TDOA-U)
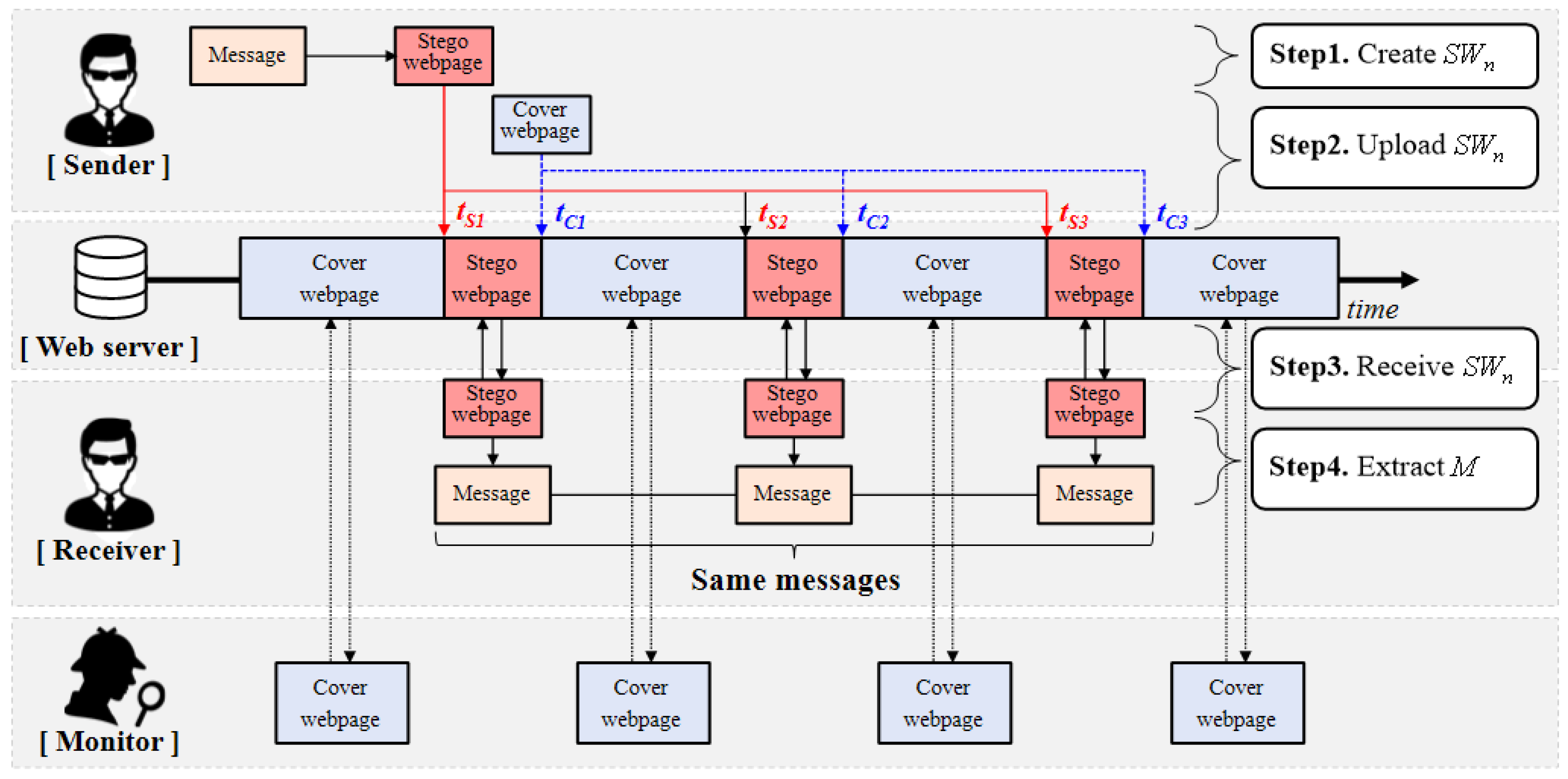
- Step 1. The sender creates stego webpages , , …, by embedding a secret message into a cover webpage . We assume that n stego webpages have the same secret message.
- Step 2. uploads , , …, to the web server, in turn, at and replace them with at in which both and are agreed in advance between and . For this step, the sender and receiver need to exchange such information by using another covert channel or in person. In addition, each will be replaced with again when a small amount of time passes to avoid the monitor. Therefore, the accurate time synchronization between and is very important so that this step can succeed. Moreover, to successfully get even in the presence of a possible time difference between and due to the unexpected network or processing delay, the receiver may need to access the web address of multiple times. Meanwhile, we do not delve into designing a sophisticated time synchronization and guaranteed delivery method for and in this study but, instead, we want to leave it for our future research.
- Step 3. receives each stego webpage, in turn, by accessing the URL where the cover webpage is located at the time period agreed with .
- Step 4. can extract the secret message from received stego webpages , , …, which means that can obtain at any time between and .
| Algorithm 2 TDOA-U (Time-based Dynamic Operation Algorithm for Undetectability) | |||
| Definition | |||
| Message | : a secret message to send to | ||
| : the number of stego webpage to send to | |||
| Webpage | : cover webpage | ||
| a set of stego webpages | |||
| Time | a set of times, which upload to the web server | ||
| : a set of times, which upload to the web server | |||
| : the start and end time of covert communication between and | |||
| : current time | |||
| Function | : embeds the secret message into . returns | ||
| : extracts the embedded secret message from . returns | |||
| : restores the by combining . returns | |||
| Sender | Receiver | ||
| Input:, , , , , , , | Input:, , , , | ||
| Output: | Output:, | ||
| Function: | Functions: | ||
| 1: begin | 1: begin | ||
| 2: for from to do #Step1 | 2: while | ||
| 3: ) | 3: for from to do #Step3 | ||
| 4: #add an element into set | 4: while True #infinitely repeat | ||
| 5: while | 5: if then | ||
| 6: for from to do #Step2 | 6: request to webserver | ||
| 7: while True #infinitely repeat | 7: from webserver | ||
| 8: if then | 8: break | ||
| 9: upload to webserver | 9: choice from to #Step4 | ||
| 10: else if then | 10: ) | ||
| 11: upload to webserver | 11: end | ||
| 12: break | |||
| 13: end | |||
3.4. The Hybrid Model of Combining TDOA-C and TDOA-U
4. Experimental Results
- Experiment 1: Validating TDOA-C has a higher hiding capacity (or a larger amount of secret message delivery) than the existing static model.
- Experiment 2: Validating TDOA-U has a higher undetectability than the existing static model.
4.1. Experiment 1: Validation of TDOA-C
4.1.1. Experiment 1. Part 1: Implementation of TDOA-C in the Web Environment
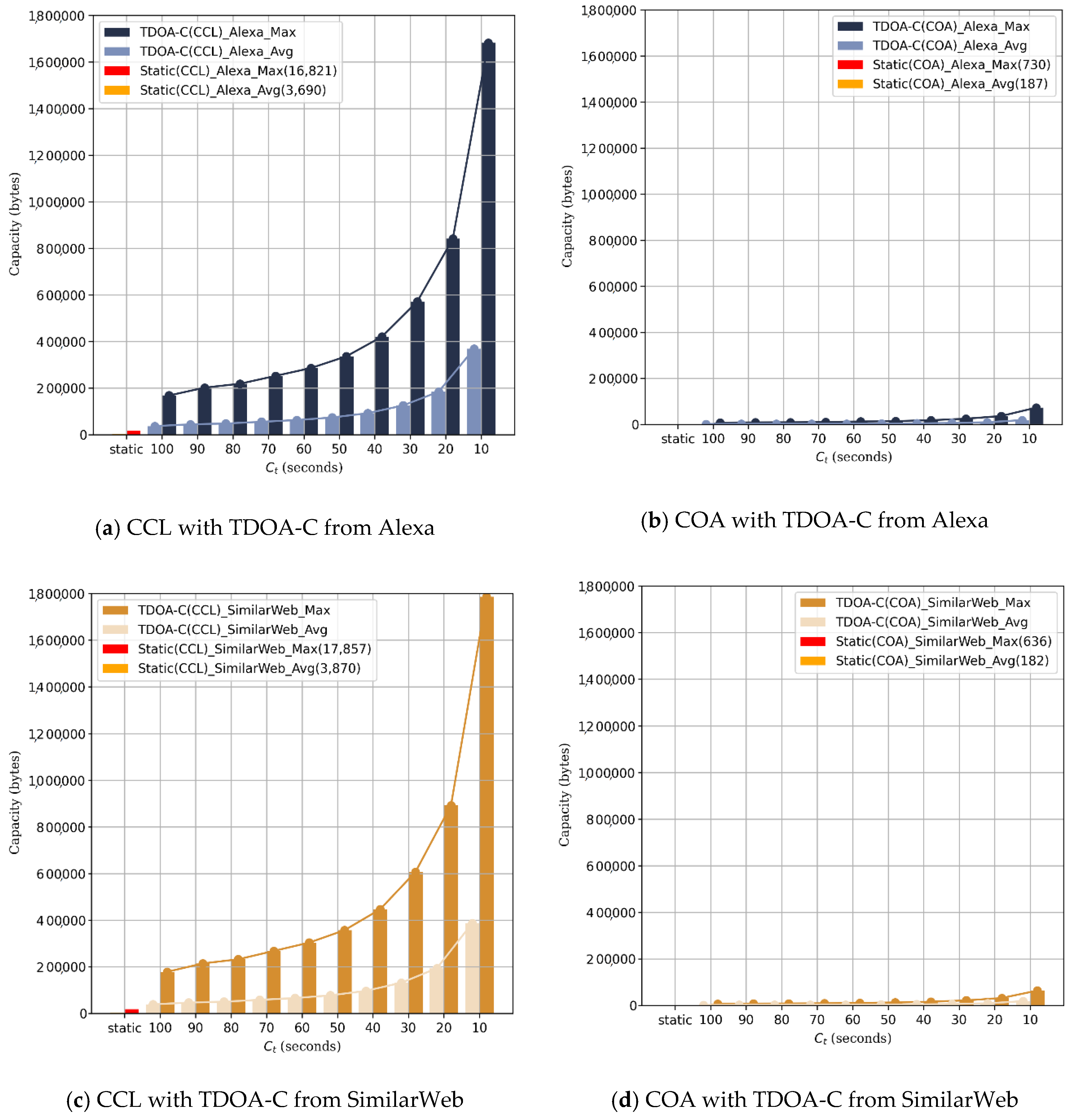
4.1.2. Experiment 1. Part 2: Comparative Numerical Analysis
4.2. Experiment 2: Validation of TDOA-U
5. Conclusions and Future Works
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Johnson, N.F.; Jajodia, S. Exploring steganography: Seeing the unseen. Computer 1998, 31, 26–34. [Google Scholar] [CrossRef]
- Bender, W.; Gruhl, D.; Morimoto, N.; Lu, A. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Steganography: A Close View of the Traditional Attack Technique that Has Created Chaos in the Cybersecurity World. Available online: https://cyware.com/news/steganography-a-close-view-of-the-traditional-attack-technique-that-has-created-chaos-in-the-cybersecurity-world-d412d190 (accessed on 2 December 2020).
- Steganography Anchors Pinpoint Attacks on Industrial Targets. Available online: https://threatpost.com/steganography-pinpoint-attacks-industrial-targets/156151/ (accessed on 2 December 2020).
- Steganography in Attacks on Industrial Enterprises. Available online: https://ics-cert.kaspersky.com/reports/2020/06/17/steganography-in-attacks-on-industrial-enterprises/ (accessed on 2 December 2020).
- Sui, X.G.; Luo, H. A new steganography method based on hypertext. In Proceedings of the 2004 Asia-Pacific Radio Science Conference, Qingdao, China, 24–27 August 2004; IEEE: New York, NY, USA, 2004; pp. 181–184. [Google Scholar]
- Platinum Is Back. Available online: https://securelist.com/platinum-is-back/91135/ (accessed on 2 December 2020).
- Cox, I.; Miller, M.; Bloom, J.; Fridrich, J.; Kalker, T. Digital Watermarking and Steganography; Morgan kaufmann: San Francisco, CA, USA, 2007. [Google Scholar]
- Rafat, K.F. Cutting Edge Steganography Using HTML Document-An Appraisal. Int. J. Comput. Sci. Inf. Secur. 2016, 14, 960. [Google Scholar]
- Odeh, A.; Elleithy, K.; Faezipour, M.; Abdelfattah, E. Novel Steganography over HTML Code. In Innovations and Advances in Computing, Informatics, Systems Sciences, Networking and Engineering; Springer: Cham, Switzerland, 2015; pp. 607–611. [Google Scholar]
- Kis, D.; Pataki, N. Source Code-based Steganography. In Proceedings of the 10th International Conference on Applied Informatics, Eger, Hungary, 30 January–1 February 2017; pp. 157–162. [Google Scholar]
- Katzenbeisser, S.; Petitcolas, F.A.P. Digital Watermarking; Artech House: London, UK, 2000; Volume 2. [Google Scholar]
- Lee, I.S.; Tsai, W.H. Secret communication through webpages using special space codes in HTML files. Int. J. Appl. Sci. Eng. 2008, 6, 141–149. [Google Scholar]
- Chou, Y.C.; Huang, C.Y.; Liao, H.C. A reversible data hiding scheme using cartesian product for HTML file. In Proceedings of the 2012 Sixth International Conference on Genetic and Evolutionary Computing, Kitakyushu, Japan, 25–28 August 2012; IEEE: New York, NY, USA, 2012; pp. 153–156. [Google Scholar]
- Imran, S.; Khan, A.; Ahmad, B. Text Steganography Utilizing XML, HTML and XHTML Markup Languages. Int. J. Inf. Technol. Secur. 2017, 9, 99–116. [Google Scholar]
- Tariq, M.A.; Khan, A.T.A.A.; Ahmad, B. Boosting the Capacity of Web based Steganography by Utilizing Html Space Codes: A blind Steganography Approach. IT Ind. 2017, 5, 29–36. [Google Scholar]
- Bajaj, I.; Aggarwal, R.K. RSA Secured Web Based Steganography Employing HTML Space Codes and Compression Technique. In Proceedings of the 2019 International Conference on Intelligent Computing and Control Systems (ICCS), Madurai, India, 15–17 May 2019; IEEE: New York, NY, USA, 2019; pp. 865–868. [Google Scholar]
- Jaiswal, R.J.; Patil, N.N. Implementation of a new technique for web document protection using unicode. In Proceedings of the 2013 International Conference on Information Communication and Embedded Systems (ICICES), Chennai, India, 21–22 February 2013; IEEE: New York, NY, USA, 2013; pp. 69–72. [Google Scholar]
- Zhao, Q.; Lu, H. A PCA-based watermarking scheme for tamper-proof of webpages. Pattern Recognit. 2005, 38, 1321–1323. [Google Scholar] [CrossRef]
- Zhao, Q.; Lu, H. PCA-based webpage watermarking. Pattern Recognit. 2007, 40, 1334–1341. [Google Scholar] [CrossRef]
- Wu, C.C.; Chang, C.C.; Yang, S.R. An efficient fragile watermarking for webpages tamper-proof. In Advances in Web and Network Technologies, and Information Management; Springer: Berlin/Heidelberg, Germany, 2007; pp. 654–663. [Google Scholar]
- Junling, R.; Chengquan, W. A Webpage information hiding algorithm based on tag dictionary. In Proceedings of the 2012 International Conference on Computer Science and Electronics Engineering, Hangzhou, China, 23–25 March 2012; IEEE: New York, NY, USA, 2012; pp. 546–550. [Google Scholar]
- Ghosh, S. StegHTML: A message hiding mechanism in HTML tags; Technical Report: Charlottesville, VA, USA, 10 December 2007. [Google Scholar]
- Shen, D.; Zhao, H. A novel scheme of webpage information hiding based on attributes. In Proceedings of the 2010 IEEE International Conference on Information Theory and Information Security, Austin, TX, USA, 13–18 June 2010; IEEE: New York, NY, USA, 2010; pp. 1147–1150. [Google Scholar]
- Huang, H.; Zhong, S.; Sun, X. An algorithm of webpage information hiding based on attributes permutation. In Proceedings of the 2008 International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Harbin, China, 15–17 August 2008; IEEE: New York, NY, USA, 2008; pp. 257–260. [Google Scholar]
- Reddy, B.S.; Kuppusamy, K.S.; Sivakumar, T. Towards Web page steganography with Attribute Truth Table. In Proceedings of the 2016 3rd International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 22–23 January 2016; IEEE: New York, NY, USA, 2016; pp. 1–5. [Google Scholar]
- Singh, R.K.; Alankar, B. A Novel Approach For Data Hiding In Web Page Steganography Using Encryption With Compression Based Technique. IOSR J. Comput. Eng. 2016, 18, 73–77. [Google Scholar] [CrossRef]
- Yang, Y.J.; Yang, Y.M. An efficient webpage information hiding method based on tag attributes. In Proceedings of the 2010 Seventh International Conference on Fuzzy Systems and Knowledge Discovery, Yantai, China, 10–12 August 2010; IEEE: New York, NY, USA, 2010; pp. 1181–1184. [Google Scholar]
- Yong, X.; Juan, L.; Yilai, Z. A high capacity information hiding method for webpage based on tag. In Proceedings of the 2012 Third International Conference on Digital Manufacturing & Automation, Guilin, China, 31 July–2 August 2012; IEEE: New York, NY, USA, 2012; pp. 62–65. [Google Scholar]
- Garg, M. A novel text steganography technique based on html documents. Int. J. Adv. Sci. Technol. 2011, 35, 129–138. [Google Scholar]
- Mahato, S.; Yadav, D.K.; Khan, D.A. A modified approach to text steganography using HyperText markup language. In Proceedings of the 2013 Third International Conference on Advanced Computing and Communication Technologies (ACCT), Rohtak, India, 6–7 April 2013; IEEE: New York, NY, USA, 2013; pp. 40–44. [Google Scholar]
- Fridrich, J. Applications of data hiding in digital images. In Proceedings of the Fifth International Symposium on Signal Processing and its Applications (IEEE Cat. No. 99EX359), ISSPA’99, Brisbane, QLD, Australia, 22–25 August; IEEE: New York, NY, USA, 1999; Volume 1. [Google Scholar]
- Wbstego. Available online: http://wbstego.wbailer.com/ (accessed on 2 December 2020).
- Invisible Secret. Available online: http://www.invisiblesecrets.com/ (accessed on 2 December 2020).
- Snow. Available online: http://www.darkside.com.au/snow/ (accessed on 2 December 2020).
- Deogol. Available online: https://hord.ca/projects/deogol/ (accessed on 2 December 2020).
- Cho, Y. Intelligent On-Off Web Defacement Attacks and Random Monitoring-Based Detection Algorithms. Electronics 2019, 8, 1338. [Google Scholar] [CrossRef]
- Flask Web Framework. Available online: https://flask.palletsprojects.com/en/1.1.x/ (accessed on 2 December 2020).
- Python url.request Library. Available online: https://docs.python.org/3/library/urllib.request.html (accessed on 2 December 2020).
- UUID_RFC4122. Available online: https://www.ietf.org/rfc/rfc4122.txt (accessed on 2 December 2020).
- Alexa Top 500 Sites on the Web. Available online: https://www.alexa.com/topsites (accessed on 2 December 2020).
- SimilarWeb Top Websites Ranking. Available online: https://www.similarweb.com/top-websites/ (accessed on 2 December 2020).
- Tan, J. Optimal strategy selection approach to moving target defense based on Markov robust game. Comput. Secur. 2019, 85, 63–76. [Google Scholar] [CrossRef]
- Kanellopoulos, A.; Vamvoudakis, K.G. A moving target defense control framework for cyber-physical systems. IEEE Trans. Autom. Control 2019, 65, 1029–1043. [Google Scholar] [CrossRef]
- Yuk, S.; Cho, Y. A New Covert Communication Method based on Webpage Steganography. In Proceedings of the KIISE Korea Software Congress, Pyeongchang, Korea, 18–20 December 2019; Volume 12, pp. 794–796. [Google Scholar]

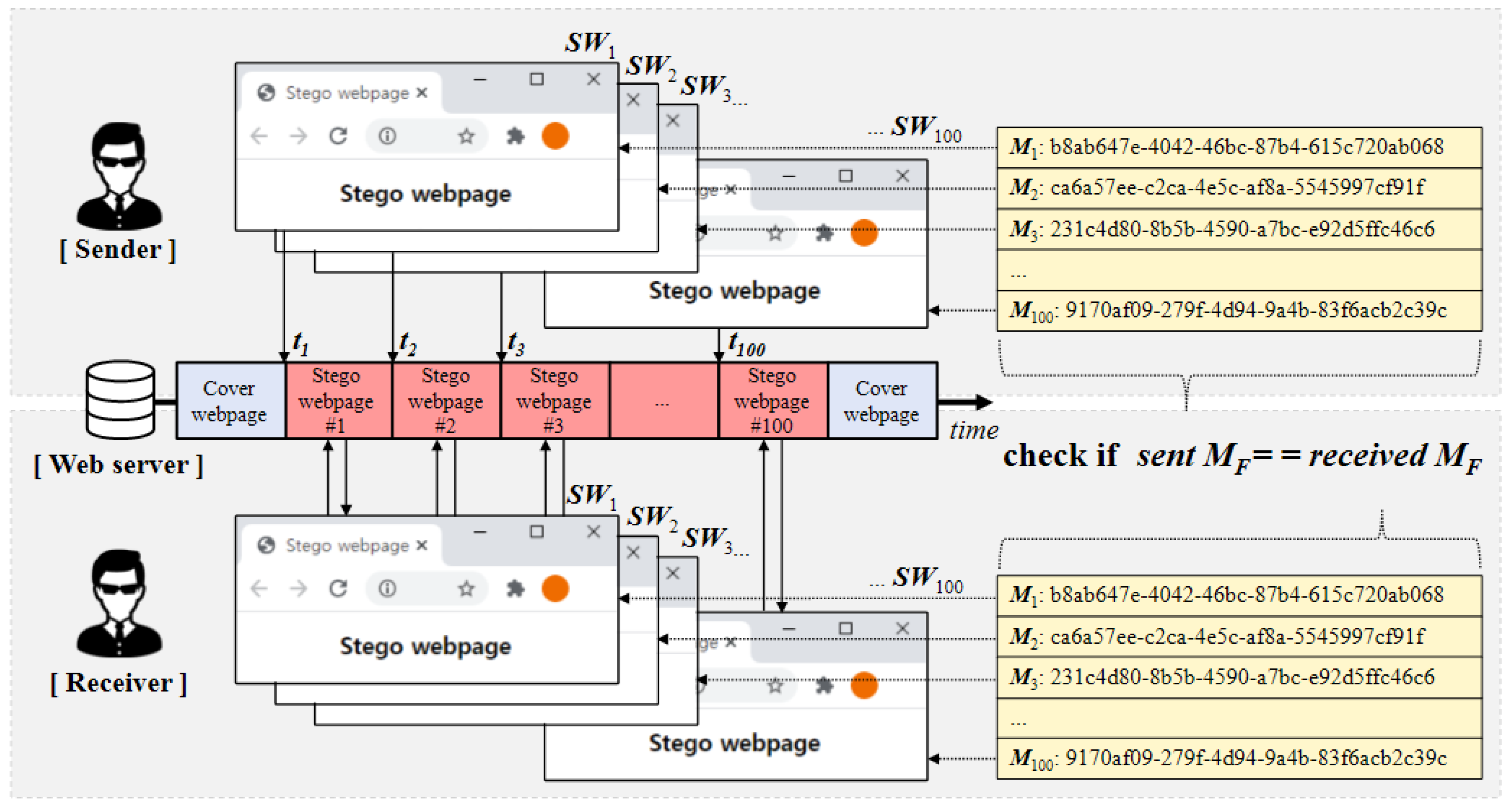
| Secret Messages (UUID 4) | Match Result | ||
|---|---|---|---|
| Sender Side (Embedded) | Receiver Side (Extracted) | ||
| 1 | b8ab647e-4042-46bc-87b4-615c720ab068 | b8ab647e-4042-46bc-87b4-615c720ab068 | matched |
| 2 | ca6a57ee-c2ca-4e5c-af8a-5545997cf91f | ca6a57ee-c2ca-4e5c-af8a-5545997cf91f | matched |
| 3 | 231c4d80-8b5b-4590-a7bc-e92d5ffc46c6 | 231c4d80-8b5b-4590-a7bc-e92d5ffc46c6 | matched |
| 4 | f3325710-e852-4bd2-837d-3d9ab67fbd5c | f3325710-e852-4bd2-837d-3d9ab67fbd5c | matched |
| 5 | 8cf7a48b-72ec-4488-b165-d4c07a82c1fb | 8cf7a48b-72ec-4488-b165-d4c07a82c1fb | matched |
| 10 | 75bf76b3-0bd8-4887-8986-a18e9bad6b18 | 75bf76b3-0bd8-4887-8986-a18e9bad6b18 | matched |
| 50 | 78ccde2a-dbf4-4ddb-b3b9-111de53caaf3 | 78ccde2a-dbf4-4ddb-b3b9-111de53caaf3 | matched |
| 100 | 9170af09-279f-4d94-9a4b-83f6acb2c39c | 9170af09-279f-4d94-9a4b-83f6acb2c39c | matched |
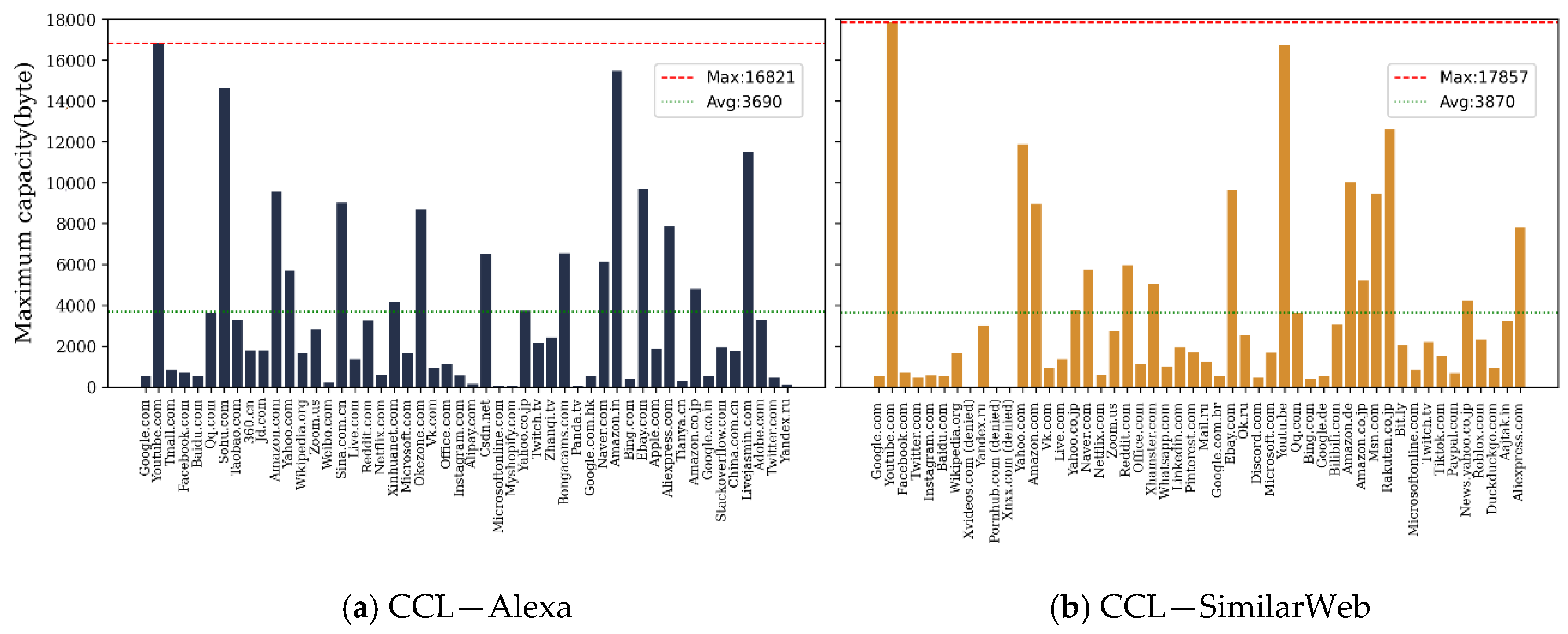
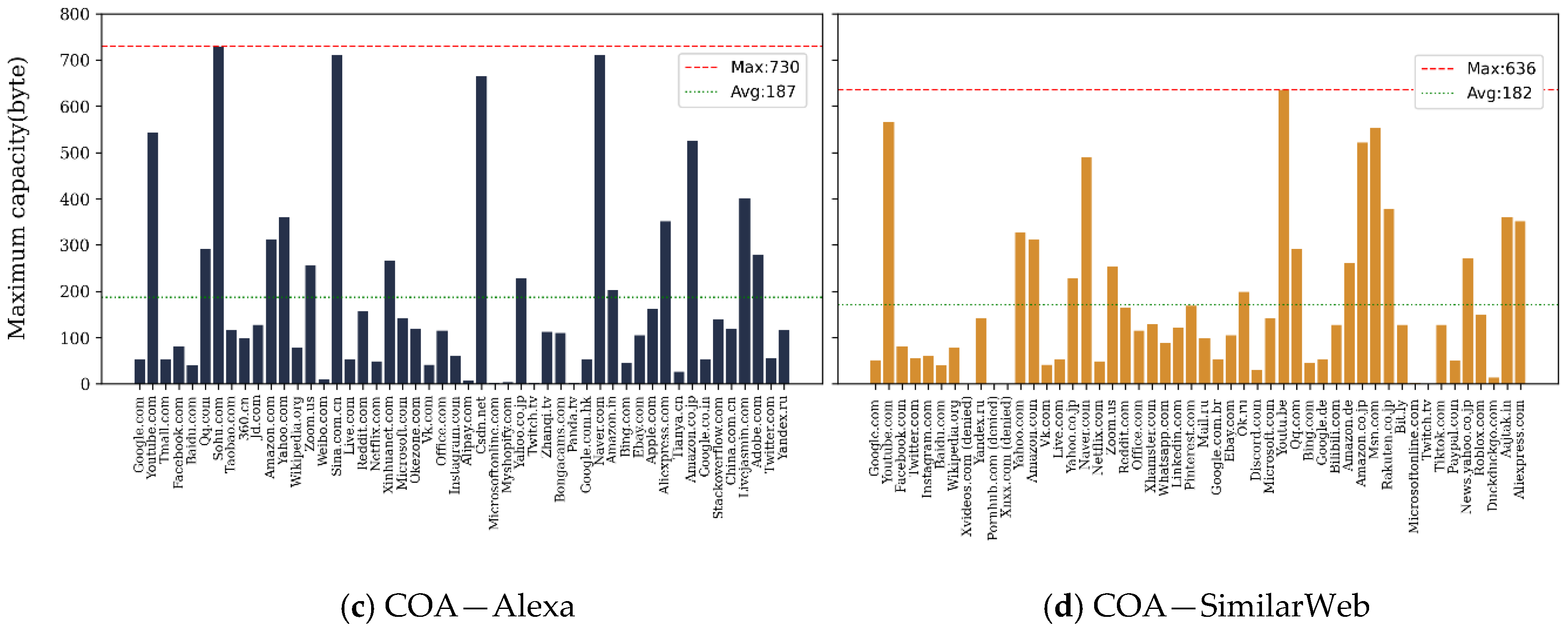
| Hiding Capacity (Bytes) | CCL | COA | ||
|---|---|---|---|---|
| Alexa | SimilarWeb | Alexa | SimilarWeb | |
| Max () | 16,821 | 17,857 | 730 | 636 |
| Average () | 3690 | 3870 | 187 | 182 |
| Standard Deviation () | 4028 | 4303 | 199 | 163 |
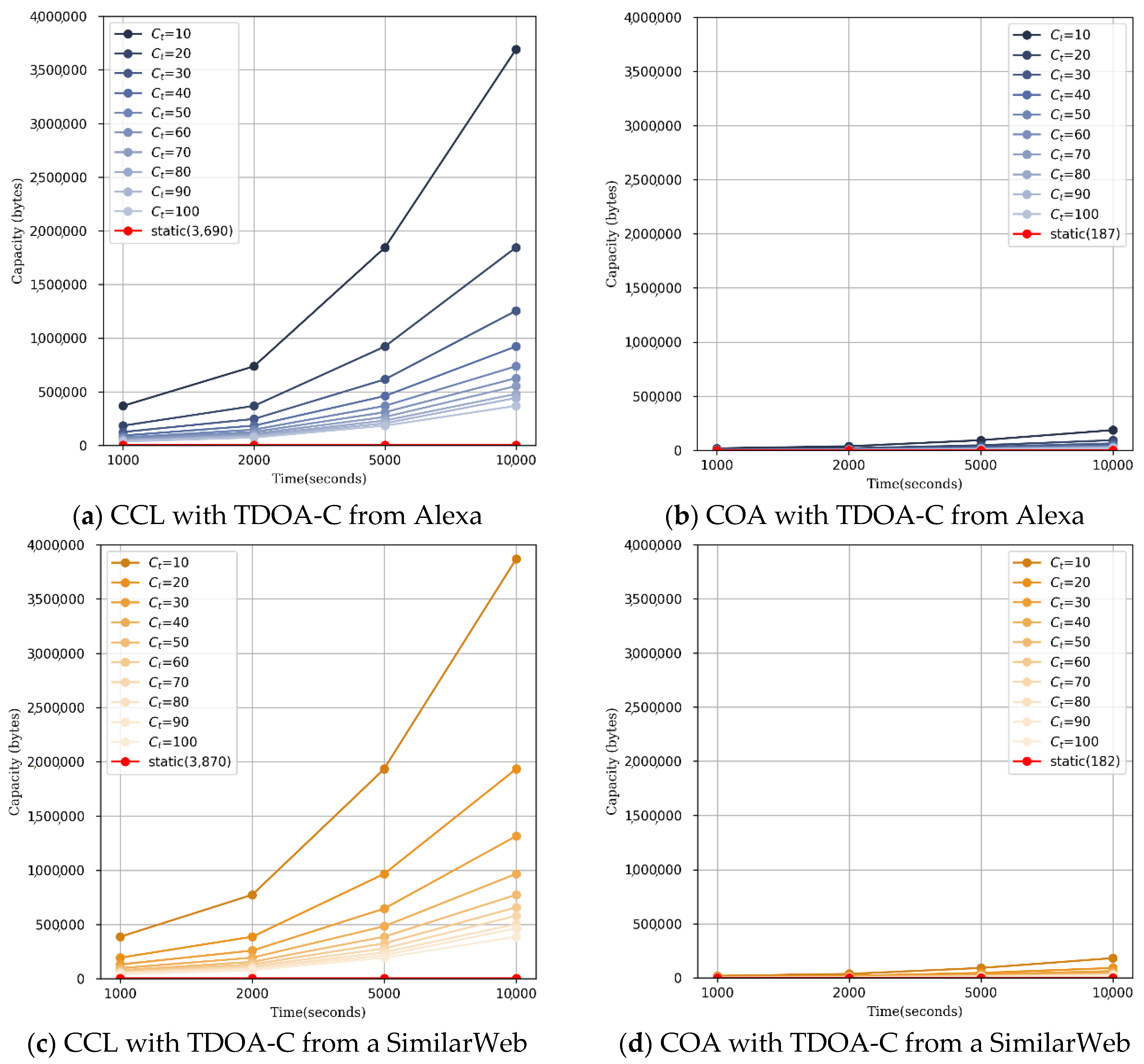
| Existing Static Model | CCL with TDOA-C | ||||||||||||
| 100 | 90 | 80 | 70 | 60 | 50 | 40 | 30 | 20 | 10 | ||||
| 1 | 10 | 12 | 13 | 15 | 17 | 20 | 25 | 34 | 50 | 100 | |||
| Website list | Alexa | Avg | 3690 | 36,900 | 44,280 | 47,970 | 55,350 | 62,730 | 73,800 | 92,250 | 125,460 | 184,500 | 369,000 |
| Max | 16,821 | 168,210 | 201,852 | 218,673 | 252,315 | 285,957 | 336,420 | 420,525 | 571,914 | 841,050 | 1682,100 | ||
| SimilarWeb | Avg | 3870 | 38,700 | 46,440 | 50,310 | 58,050 | 65,790 | 77,400 | 96,750 | 131,580 | 193,500 | 387,000 | |
| Max | 17,857 | 178,570 | 214,284 | 232,141 | 267,855 | 303,569 | 357,140 | 446,425 | 607,138 | 892,850 | 1,785,700 | ||
| Existing Static Model | COA with TDOA-C | ||||||||||||
| 100 | 90 | 80 | 70 | 60 | 50 | 40 | 30 | 20 | 10 | ||||
| 1 | 10 | 12 | 13 | 15 | 17 | 20 | 25 | 34 | 50 | 100 | |||
| Website list | Alexa | Avg | 187 | 1870 | 2244 | 2431 | 2805 | 3179 | 3740 | 4675 | 6358 | 9350 | 18,700 |
| Max | 730 | 7300 | 8760 | 9490 | 10,950 | 12,410 | 14,600 | 18,250 | 24,820 | 36,500 | 73,000 | ||
| SimilarWeb | Avg | 182 | 1820 | 2184 | 2366 | 2730 | 3094 | 3640 | 4550 | 6188 | 9100 | 18,200 | |
| Max | 636 | 6360 | 7632 | 8268 | 9540 | 10,812 | 12,720 | 15,900 | 21,624 | 31,800 | 63,600 | ||
| 10 | 20 | 30 | 40 | 50 | 60 | 70 | 80 | 90 | 100 | ||
|---|---|---|---|---|---|---|---|---|---|---|---|
| 10 | 0.50 | 0.33 | 0.25 | 0.20 | 0.16 | 0.14 | 0.12 | 0.11 | 0.10 | 0.09 | |
| 20 | 0.66 | 0.50 | 0.40 | 0.32 | 0.28 | 0.24 | 0.22 | 0.20 | 0.18 | 0.16 | |
| 30 | 0.75 | 0.60 | 0.49 | 0.42 | 0.36 | 0.33 | 0.30 | 0.27 | 0.24 | 0.21 | |
| 40 | 0.80 | 0.66 | 0.56 | 0.48 | 0.44 | 0.40 | 0.36 | 0.32 | 0.28 | 0.28 | |
| 50 | 0.83 | 0.70 | 0.61 | 0.55 | 0.50 | 0.45 | 0.40 | 0.36 | 0.35 | 0.30 | |
| 60 | 0.85 | 0.74 | 0.66 | 0.60 | 0.54 | 0.48 | 0.44 | 0.42 | 0.37 | 0.36 | |
| 70 | 0.87 | 0.77 | 0.70 | 0.63 | 0.56 | 0.52 | 0.49 | 0.44 | 0.42 | 0.40 | |
| 80 | 0.88 | 0.80 | 0.72 | 0.64 | 0.60 | 0.56 | 0.51 | 0.48 | 0.46 | 0.40 | |
| 90 | 0.90 | 0.81 | 0.73 | 0.68 | 0.63 | 0.58 | 0.54 | 0.52 | 0.46 | 0.45 | |
| 100 | 0.90 | 0.82 | 0.76 | 0.70 | 0.65 | 0.60 | 0.58 | 0.52 | 0.50 | 0.50 | |
| Case | Numerical Analysis | Web Experiment | ||||
|---|---|---|---|---|---|---|
| Set (s) | MU,NA | Number of Detections | ||||
| Case 1. ( | 50 | 50 | 0.5 | 51/100 | 49/100 | 0.49 |
| Case 2. ( | 30 | 70 | 0.7 | 33/100 | 67/100 | 0.67 |
| Case 3. ( | 70 | 30 | 0.3 | 71/100 | 29/100 | 0.29 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yuk, S.; Cho, Y. A Time-Based Dynamic Operation Model for Webpage Steganography Methods. Electronics 2020, 9, 2113. https://doi.org/10.3390/electronics9122113
Yuk S, Cho Y. A Time-Based Dynamic Operation Model for Webpage Steganography Methods. Electronics. 2020; 9(12):2113. https://doi.org/10.3390/electronics9122113
Chicago/Turabian StyleYuk, Simun, and Youngho Cho. 2020. "A Time-Based Dynamic Operation Model for Webpage Steganography Methods" Electronics 9, no. 12: 2113. https://doi.org/10.3390/electronics9122113
APA StyleYuk, S., & Cho, Y. (2020). A Time-Based Dynamic Operation Model for Webpage Steganography Methods. Electronics, 9(12), 2113. https://doi.org/10.3390/electronics9122113






