Maritime Opportunistic Network Routing Strategies for Assessing Link Connectivity Based on Deep Learning
Abstract
1. Introduction
- Intelligent prediction of link state can effectively determine the risk of link breakage, thus assisting routing decisions and improving communication efficiency [11];
- In link prediction, more attention is paid to the link connectivity status in the ship characterization dataset (a ship characterization dataset consists of the communication data from multiple ships at a given moment in time) rather than the time series, in order to cope with the highly variable nature of the links in the maritime opportunistic network;
- Determining the forwarding priority of a node based on its attributes can avoid the repeated transmission of messages and reduce the waste of network resources. This can also avoid the situation in which the current node has no available neighboring nodes to forward packets to the destination within the shortest path, and can only be broadcasted all the time by certain nodes with high-priority messages, resulting in invalid routes, which provides a longer period of communication in the ocean;
- The special feature of opportunistic networks is the random movement of nodes, and, in this paper, we take into account the movement posture of nodes when evaluating them. This leads to a higher probability of forwarding a message to a node that is more convergent in its motion posture or to other nodes that are closer to the target node.
2. Comprehensive Attribute Evaluation of Nodes
2.1. Encounter Probability of Historical Values of Nodes
2.2. Acquired Resource Availability of Nodes
2.3. Kinematic Posture of Nodes
3. Routing Algorithms
4. Intelligent Prediction of Link States
4.1. Effective Additive Attention (EAA)
4.2. Convolutional Neural Networks (CNN)s
4.3. CNN–EAA
5. Simulation Results and Performance Analysis
5.1. Simulation Environment Parameters
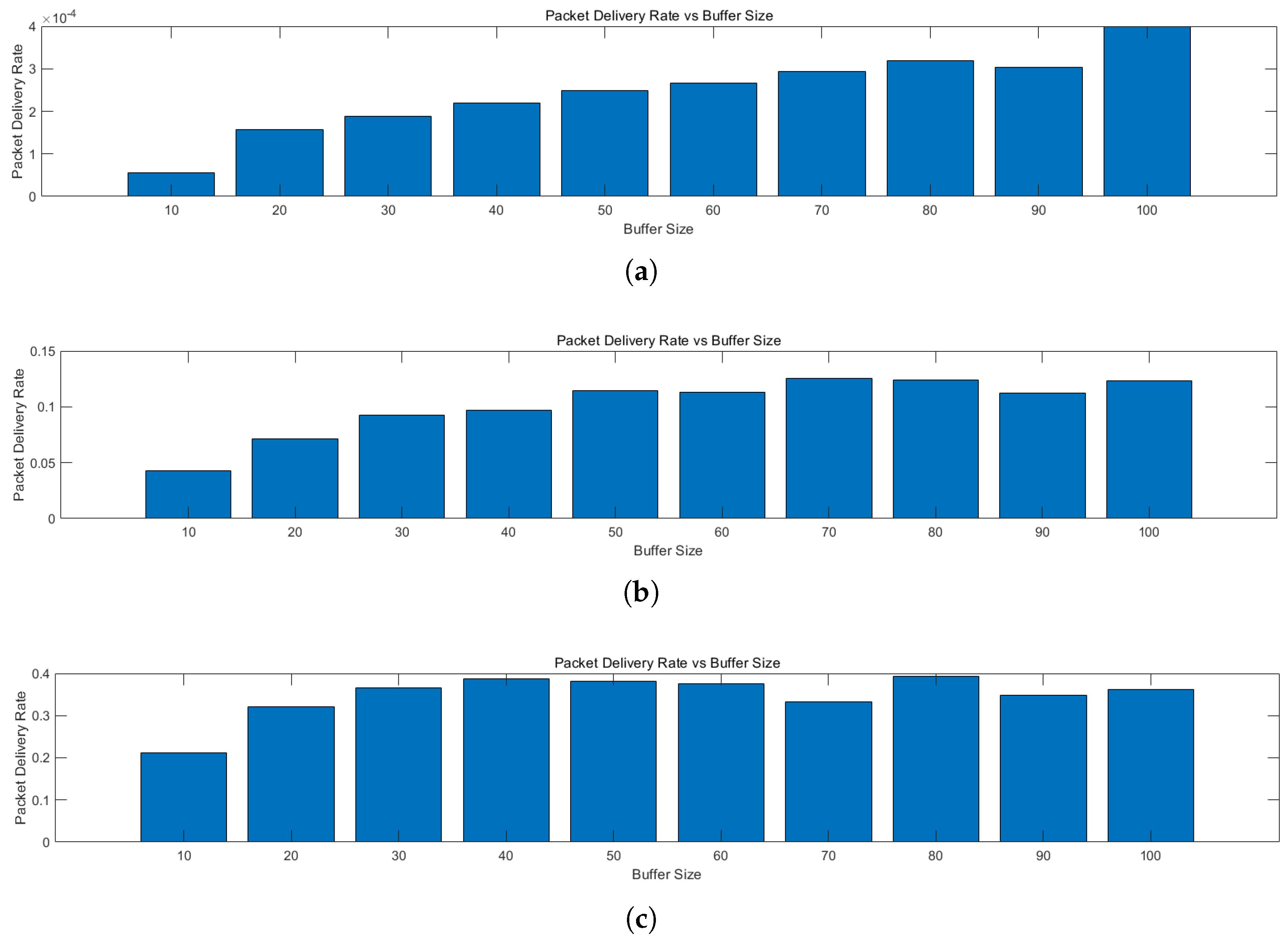
- Packet Delivery Ratio: the ratio between the total number of packets delivered to the destination and the total number of packets sent from the source node, reflecting the impact of routing on network performance;
- Average Transmission Delay: the average value of the time taken by a packet to reach the destination node from the source node, which is affected by the frequency of encounters between nodes, packet storage waiting time, etc., and reflects the timeliness of the routing policy in delivering messages [24];
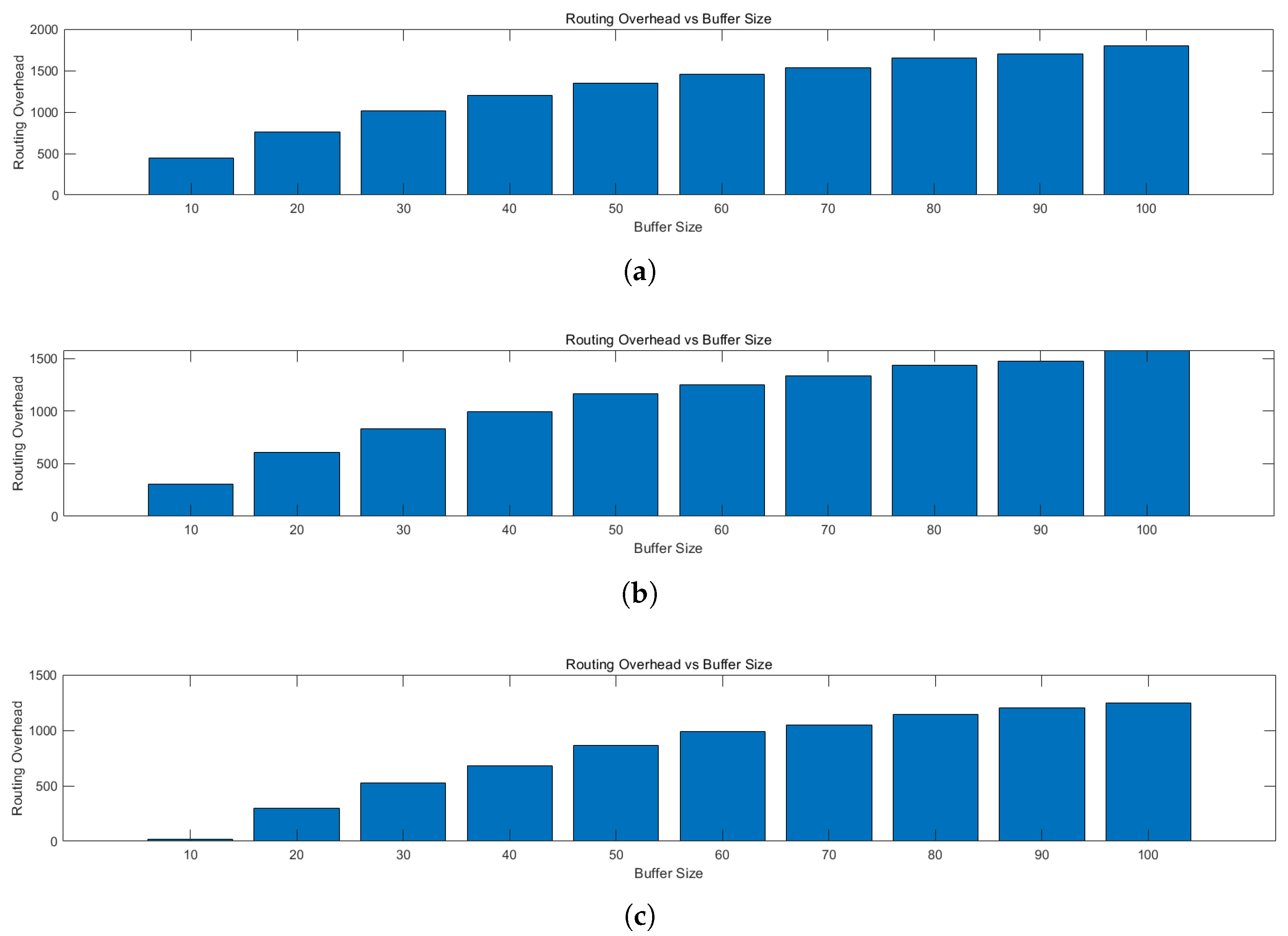
- Routing Overhead: Routing overhead is usually related to the number of packet forwards and network bandwidth consumption, and is used to measure the resource usage efficiency and scalability of the routing policy.
5.2. Comparative Analysis of Routing Performance with Different Buffers
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Trifunovic, S.; Kouyoumdjieva, S.T.; Distl, B.; Pajevic, L.; Karlsson, G.; Plattner, B. A decade of research in opportunistic networks: Challenges, relevance, and future directions. IEEE Commun. Mag. 2017, 55, 168–173. [Google Scholar] [CrossRef]
- Dede, J.; Förster, A.; Hernández-Orallo, E.; Herrera-Tapia, J.; Kuladinithi, K.; Kuppusamy, V.; Manzoni, P.; bin Muslim, A.; Udugama, A.; Vatandas, Z. Simulating opportunistic networks: Survey and future directions. IEEE Commun. Surv. Tutor. 2017, 20, 1547–1573. [Google Scholar] [CrossRef]
- Wei, T.; Feng, W.; Chen, Y.; Wang, C.X.; Ge, N.; Lu, J. Hybrid satellite-terrestrial communication networks for the maritime Internet of Things: Key technologies, opportunities, and challenges. IEEE Internet Things J. 2021, 8, 8910–8934. [Google Scholar] [CrossRef]
- Kidston, D.; Kunz, T. Challenges and opportunities in managing maritime networks. IEEE Commun. Mag. 2008, 46, 162–168. [Google Scholar] [CrossRef]
- Alajeely, M.; Doss, R.; Ahmad, A. Routing protocols in opportunistic networks—A survey. IETE Tech. Rev. 2018, 35, 369–387. [Google Scholar] [CrossRef]
- Chakchouk, N. A survey on opportunistic routing in wireless communication networks. IEEE Commun. Surv. Tutor. 2015, 17, 2214–2241. [Google Scholar] [CrossRef]
- Mahendran, V.; Murthy, C.S.R. Buffer dimensioning of DTN replication-based routing nodes. IEEE Commun. Lett. 2012, 17, 123–126. [Google Scholar] [CrossRef]
- Ge, L.; Jiang, S.; Wang, X.; Xu, Y.; Feng, R.; Zheng, Z. Link availability prediction based on machine learning for opportunistic networks in oceans. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2022, 105, 598–602. [Google Scholar] [CrossRef]
- Ji, M.; Cui, X.; Li, J.; Xu, T.; Li, S.; Liu, J. A routing algorithm based on network connectivity assessment for maritime opportunistic networks. Procedia Comput. Sci. 2021, 187, 200–205. [Google Scholar] [CrossRef]
- Bazzi, A.; Bomfin, R.; Mezzavilla, M.; Rangan, S.; Rappaport, T.; Chafii, M. Upper Mid-Band Spectrum for 6G: Vision, Opportunity and Challenges. arXiv 2025, arXiv:2502.17914. [Google Scholar]
- Kumar, A.; Singh, S.S.; Singh, K.; Biswas, B. Link prediction techniques, applications, and performance: A survey. Phys. A Stat. Mech. Its Appl. 2020, 553, 124289. [Google Scholar] [CrossRef]
- Ge, L.; Jiang, S. An efficient routing scheme based on node attributes for opportunistic networks in oceans. Entropy 2022, 24, 607. [Google Scholar] [CrossRef] [PubMed]
- Dalal, R.; Khari, M.; Anzola, J.P.; García-Díaz, V. Proliferation of opportunistic routing: A systematic review. IEEE Access 2021, 10, 5855–5883. [Google Scholar] [CrossRef]
- Zhang, S.; Zhou, Q.; Wu, X. Fast dynamic routing based on weighted kernel density estimation. In Proceedings of the International Symposium on Artificial Intelligence and Robotics, Paris, France, 21–22 August 2018; pp. 301–309. [Google Scholar]
- Shaker, A.; Maaz, M.; Rasheed, H.; Khan, S.; Yang, M.H.; Khan, F.S. Swiftformer: Efficient additive attention for transformer-based real-time mobile vision applications. In Proceedings of the IEEE/CVF International Conference on Computer Vision, Paris, France, 2–3 October 2023; pp. 17425–17436. [Google Scholar]
- Li, Y.; Yuan, G.; Wen, Y.; Hu, J.; Evangelidis, G.; Tulyakov, S.; Wang, Y.; Ren, J. Efficientformer: Vision transformers at mobilenet speed. Adv. Neural Inf. Process. Syst. 2022, 35, 12934–12949. [Google Scholar]
- Maaz, M.; Shaker, A.; Cholakkal, H.; Khan, S.; Zamir, S.W.; Anwer, R.M.; Shahbaz Khan, F. Edgenext: Efficiently amalgamated cnn-transformer architecture for mobile vision applications. In Proceedings of the European Conference on Computer Vision, Tel Aviv, Israel, 23–27 October 2022; pp. 3–20. [Google Scholar]
- Ye, S.; Zhijun, F.; Yongbin, G. Multi-model fusion of coronary cta segmentation based on attention mechanism. J. Front. Comput. Sci. Technol. 2020, 14, 1602. [Google Scholar]
- Zhao, L.; Zhang, Z. A improved pooling method for convolutional neural networks. Sci. Rep. 2024, 14, 1589. [Google Scholar] [CrossRef] [PubMed]
- Xie, H.; Jiang, S. Maritime Opportunity Network Link Evaluation Method Based on Convolutional Neural Network and Additive Attention Mechanism. Mob. Commun. 2025; in press. [Google Scholar]
- Zhang, Y.; Peng, C. A Hybrid Model based on Deep Learning and Cross-attention for Short-term Wind Power Prediction. In Proceedings of the 2022 5th International Conference on Renewable Energy and Power Engineering (REPE), Beijing, China, 28–30 September 2022; pp. 351–355. [Google Scholar]
- Derakhshanfard, N.; Sabaei, M.; Rahmani, A.M. Sharing spray and wait routing algorithm in opportunistic networks. Wirel. Netw. 2016, 22, 2403–2414. [Google Scholar] [CrossRef]
- Liao, Z.; Liu, L.; Chen, Y. A novel link prediction method for opportunistic networks based on random walk and a deep belief network. IEEE Access 2020, 8, 16236–16247. [Google Scholar] [CrossRef]
- Huang, T.K.; Lee, C.K.; Chen, L.J. Prophet+: An adaptive prophet-based routing protocol for opportunistic network. In Proceedings of the 2010 24th IEEE International Conference on Advanced Information Networking and Applications, Perth, Australia, 20–23 April 2010; pp. 112–119. [Google Scholar]
- Ge, L.; Jiang, S. An efficient opportunistic routing based on prediction for nautical wireless ad hoc networks. J. Mar. Sci. Eng. 2022, 10, 789. [Google Scholar] [CrossRef]




| ShipID | (km/h) | SNR (dB) | Link_Connectivity | |||
|---|---|---|---|---|---|---|
| 1 | 113.1691 | −62.0405 | 236.0666 | 14.12 | 13.16 | 0 |
| 2 | 146.0954 | 84.7322 | 12.8562 | 0.63 | 11.44 | 0 |
| 3 | −134.2308 | 81.7312 | 305.6865 | 5.53 | 22.96 | 1 |
| 4 | 148.8293 | −2.6385 | 336.2375 | 0.92 | 23.85 | 1 |
| 5 | 47.6353 | 54.0007 | 244.3446 | 1.94 | 5.60 | 1 |
| 6 | −144.8721 | −64.0963 | 272.7864 | 16.47 | 14.69 | 1 |
| 7 | −79.7506 | −14.3215 | 267.5276 | 13.89 | 13.36 | 1 |
| 8 | 16.7949 | 75.0855 | 141.2017 | 6.34 | 19.39 | 0 |
| 9 | 164.5252 | 52.1651 | 235.9720 | 19.01 | 21.28 | 1 |
| 10 | 167.3653 | 82.7882 | 61.6272 | 0.68 | 22.64 | 0 |
| Parameters | Values | Description |
|---|---|---|
| Node Deployment Area | 100 m × 100 m | Square monitoring area |
| Transmission Speed | 200 kbps | The speed at which a node transmits a message |
| Message Interval | 10 s | Packet delivery cycle |
| Maximum Message Survival Time | 1000 s | Packet survival time limit to prevent packets from looping indefinitely in the network |
| Nodal Velocity | 0∼20 km/h | Random speed range |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, H.; Jiang, S. Maritime Opportunistic Network Routing Strategies for Assessing Link Connectivity Based on Deep Learning. Electronics 2025, 14, 1187. https://doi.org/10.3390/electronics14061187
Xie H, Jiang S. Maritime Opportunistic Network Routing Strategies for Assessing Link Connectivity Based on Deep Learning. Electronics. 2025; 14(6):1187. https://doi.org/10.3390/electronics14061187
Chicago/Turabian StyleXie, Huilin, and Shengming Jiang. 2025. "Maritime Opportunistic Network Routing Strategies for Assessing Link Connectivity Based on Deep Learning" Electronics 14, no. 6: 1187. https://doi.org/10.3390/electronics14061187
APA StyleXie, H., & Jiang, S. (2025). Maritime Opportunistic Network Routing Strategies for Assessing Link Connectivity Based on Deep Learning. Electronics, 14(6), 1187. https://doi.org/10.3390/electronics14061187






