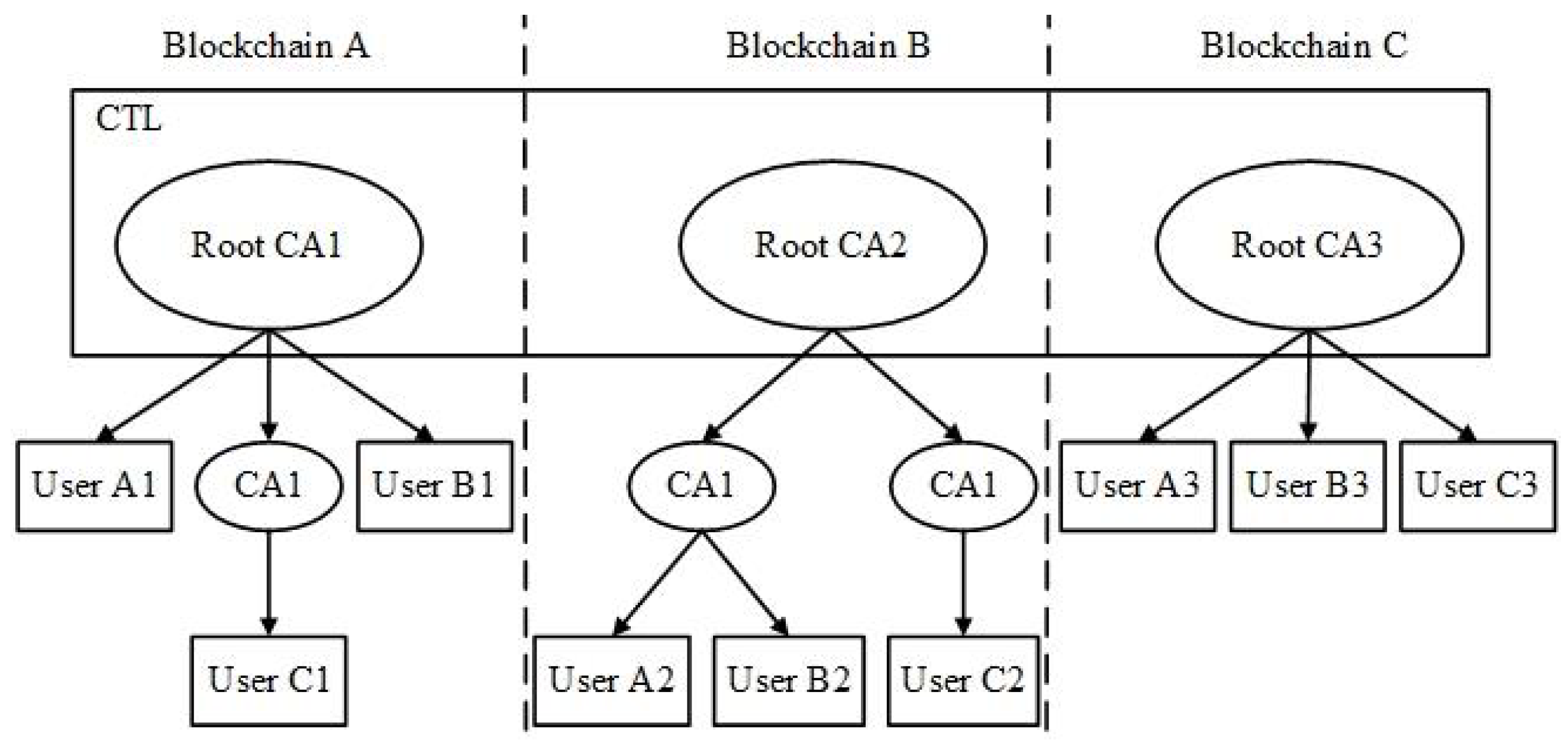
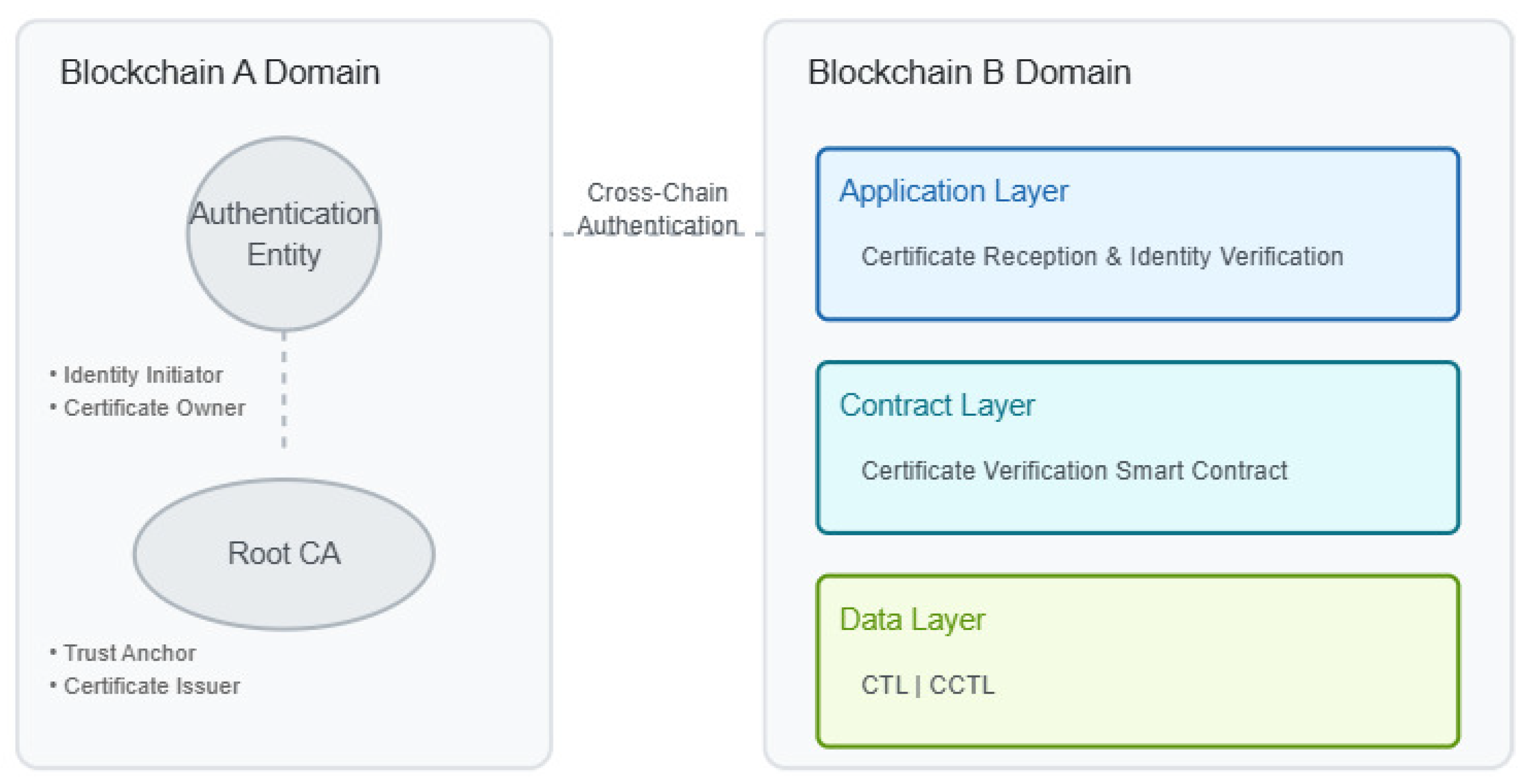
5.1. Cross-Chain Communication Scheme
An essential structure is required for the cross-chain communication system to supervise smart contract interactions among different chains. The CB-SCL (Cross-chain Smart Contract List) embraces a comprehensive data structure with three fundamental components. The essential contract information, embedded in the metadata of smart contracts, consists of vital contract details such as addresses, version control systems, chain identifiers, and deployment durations. Additional assets like access control parameters, controlling inter-chain interactions, are incorporated. The functional specifications segment comprises comprehensive API documentation, input–output parameter frameworks, and operational protocols that bridge various chains, ensuring consistent interaction patterns and the organizational control zone defines access permissions for cross-chain, tailored policies for each channel, and requirements for audit trails, ensuring the network’s operational dependability.
In the blockchain, the data on the chain is operated by smart contracts, so data cross-chain often needs calling smart contracts across the chain. The cross-chain interaction scheme is designed based on the cross-chain authentication method. After successful cross-chain authentication, the smart contract is called to operate cross-chain data, then the results are encrypted and returned.
In the process of cross-chain interaction, the processing of data is handed over to the smart contract, and the call to the smart contract needs to know the specific contract address and related data. Before the cross-chain smart contract is invoked, the shared control of the publicly available smart contract and its related data is carried out by the data chain itself. After invoking the smart contract across the chain, the operator and the specific operation content of the stored data realize the comprehensive traceability of the data operation.
The cross-chain interaction is secured through multiple layers of smart contract security controls. These include re-entrancy protection, strict access control, and comprehensive input validation, ensuring the integrity and safety of cross-chain operations while maintaining system efficiency.
Before initiating a cross-chain request, the data requester should know the requested data and the corresponding contract address. Therefore, a Cross-chain Smart Contract List (CB-SCL) should be maintained in the cross-chain organization. The data in the list should include the address of the smart contract, the functional description of the contract, the description of the relevant data, the channel, and the parameters attached instructions. This list can also ensure that the source chain can obtain the latest accessing interface in time. After the cross-chain calling smart contract is completed, the smart contract is used to store the requester’s signature, request information, and return results in the channel to which the contract belongs and the identity information in the identity authentication process will also be retained. The organization in the same channel accesses the request data according to the endorsement strategy of the channel to achieve access control of cross-chain operations. The interaction process of each layer in Chain B is shown in
Figure 5.
Chain B as the receiver of the request calls the smart contract through the application layer to operate cross-chain requests. There are four operations in the contract layer in the Figure Contract execution refers to the invocation of the contract in the cross-chain request. The invoked contract does not hold a clear direction and does not depend on certain data. The cross-chain request only calls the contract execution algorithm. In addition, Chain B also needs to run signature verification, data result encryption, and operation records at the contract layer, which are Signature Verification Smart Contract (SVSC), Data Encryption Smart Contract (DESC), and Operation Record Smart Contract (ORSC).
The CB-SCL operates through three methodically designed layers. This structure ensures effective contract administration and secure implementation. Initially, the registering interface introduces a unique protocol for registering new smart contracts, necessitating verification by multiple parties from entities and ensuring automatic version control and compatibility affirmation. The intermediary access control tier governs access rights for organizations via channel-dependent endorsement tactics, verifying smart contract requests against pre-established organizational authorizations. The execution tier orchestrates contract activities across various chains, guaranteeing adherence to consensus regulations while preserving extensive transaction logs within each organizational pathway.
5.1.1. Signature Verification Smart Contract
SVSC is responsible for the signature verification. It is necessary to obtain the list of trusted communication certificates on the chain to perform the signature verification algorithm through the certificate information. If the verification is not successful, the message will be directly returned. The data requester first operates cross-chain certificate authentication and then requests data across the chain. The specific process is shown in Algorithm 2.
| Algorithm 2 Signature Verification Smart Contract |
- Input:
request metadata ciphertext:m, signature pair: r&s, user identifier: userId - Output:
Signature Verification - 1:
cert, err:= contractapi.GetState(userId) - 2:
if err != nil then - 3:
//if the certificate is not found - 4:
return result(“the certificate has expired, re-certify”) - 5:
end if - 6:
PK = cert.PubKey //get the user’s public key from the certificate - 7:
result = ecdsa.Verify(PK, r, s) //signature verification - 8:
return result //return the verification result
|
The Signature Verification Smart Contract (Algorithm 2) extends the security framework by implementing cryptographic signature validation for cross-chain communications. The contract operates on three critical inputs: request metadata (m), signature components (), and a user identifier (). It initiates the verification process by retrieving the previously stored certificate from the blockchain state, incorporating certificate expiration verification as an integral security measure. The core functionality leverages the ECDSA (Elliptic Curve Digital Signature Algorithm) for cryptographic validation, utilizing the public key extracted from the retrieved certificate to verify the signature’s authenticity against the provided data. This implementation ensures the integrity and authenticity of cross-chain communications while maintaining atomic operation consistency throughout the verification process, thereby establishing a secure foundation for trusted cross-chain interactions in consortium blockchain networks.
Signature verification is used in the contract using an ECDSA-based verification algorithm. The parameter set has been obtained during the process of parsing the certificate and can also be requested from the user’s root CA. After the signature verification is passed, the information of the contract and the parameters of the calling contract are written to the request, so the smart contract can be called by parsing the request information. As the smart contract runs automatically, the execution result of the contract is accurate, and the application layer is carried on the node provided by Chain A, so the correctness of the execution result of the contract can be guaranteed.
5.1.2. Data Encryption Smart Contract
After the execution of the contract, DESC encrypts the data using the requester’s public key encryption. Similar to SVSC, DESC also needs to use the trusted communication certificate list on the chain to store the certificate information so that it can execute the encryption algorithm. The specific DESC process is shown in Algorithm 3.
| Algorithm 3 Data Encryption Smart Contract |
- Input:
Contract Execution Result Plaintext: m, user identifier: userId - Output:
Plaintext Pair - 1:
cert, err = contractapi.GetState(userId) - 2:
if err != nil then - 3:
// if the certificate is not found - 4:
return result(“the certificate has expired, re-certify”) - 5:
return result(“the certificate resolution has failed”) - 6:
end if - 7:
hashText = sha256(plainText) - 8:
PK = cert.Pub //get the user’s public key - 9:
result = Encrypt(Reader, PK, m) //encryption - 10:
return result //return the ciphertext
|
Algorithm 3 implements a cryptographic framework for secure cross-chain data transmission within consortium blockchain architectures. This smart contract performs a systematic sequence of certificate validation, cryptographic processing, and secure transmission operations. The implementation incorporates multiple security layers: certificate-based authentication for establishing cryptographic foundations, expiration verification to prevent deprecated credential usage, SHA-256 hash generation for maintaining data integrity, and asymmetric encryption using recipient public keys extracted from validated certificates. This security-by-design approach effectively ensures that only intended recipients with corresponding private keys can decrypt transmitted data, thus providing a computationally efficient yet robust security foundation for cross-chain data exchange in distributed trust environments.
The data encryption uses the ECC algorithm. The parameter set is obtained in the process of parsing the certificate and can also be requested from the user’s root CA.
5.1.3. Operation Record Smart Contract
One of the characteristics of blockchain is traceability, which can not only query historical data but also trace the historical operators of data. In cross-chain interaction, operating data only through smart contracts will cause a failure to track cross-chain data operators. Therefore, after the cross-chain calls the smart contract, it is necessary to store the data operator and the operation content to achieve all-around data traceability. After the smart contract is executed, Chain B calls ORSC to store the requester’s signature, request information, and return results, while retaining the identity authentication information at the same time. The organization in the channel accesses the requested data according to the endorsement strategy to achieve access control for cross-chain operations. ORSC stores results, requests, and identity information, and the encryption contract invoked results back to the requester. The ORSC contract is mounted on the anchor node and the access rights of the cross-chain operation record are limited to its channel, which ensures that the organization in different channels cannot detect the operation record. The cross-chain operation record is stored in the current channel, due to the characteristics of data isolation among channels, other chains cannot obtain the cross-chain operation data in the own channel, so the privacy of the cross-chain operation is guaranteed.
5.1.4. Smart Contract Execution Optimization
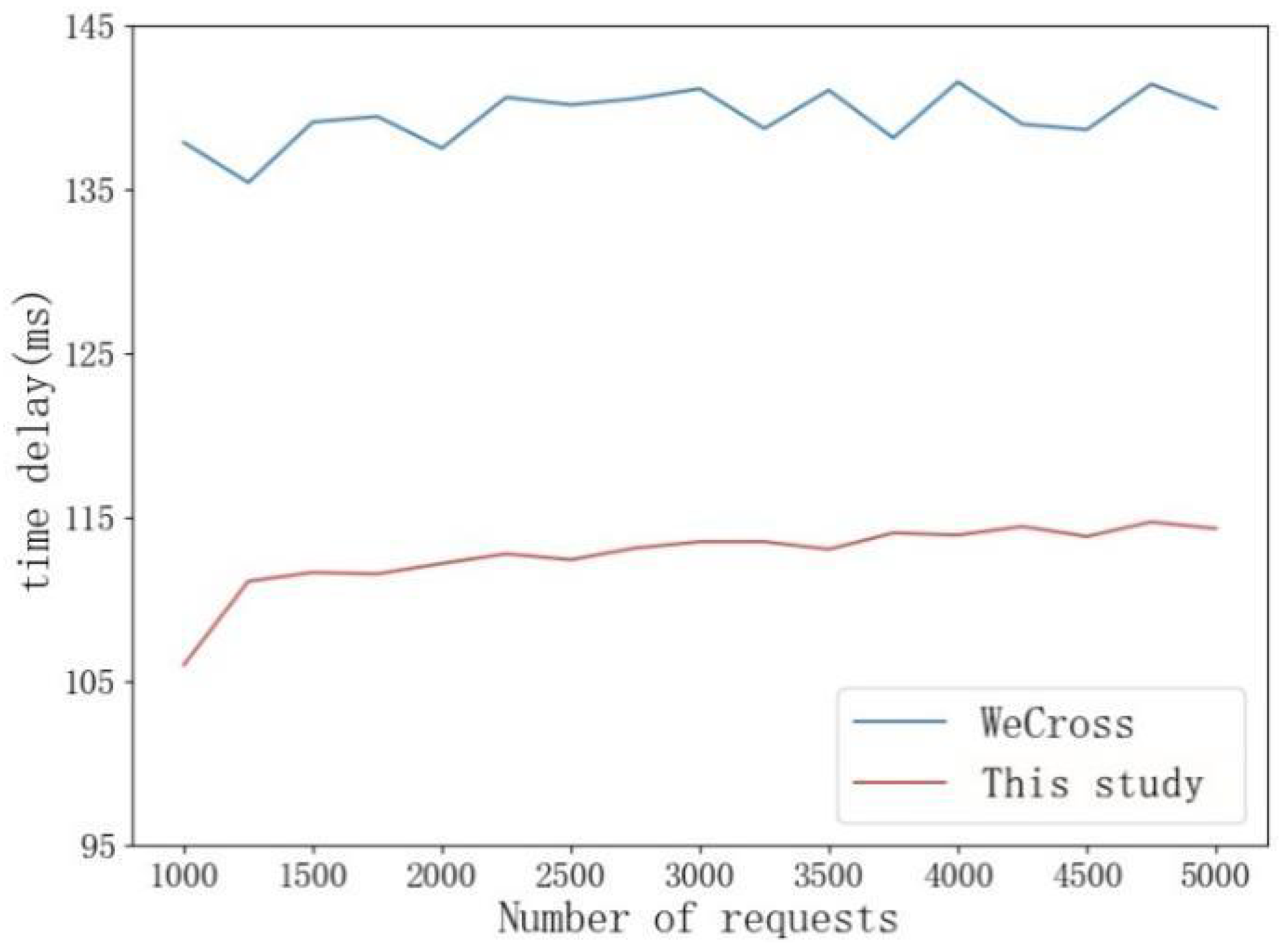
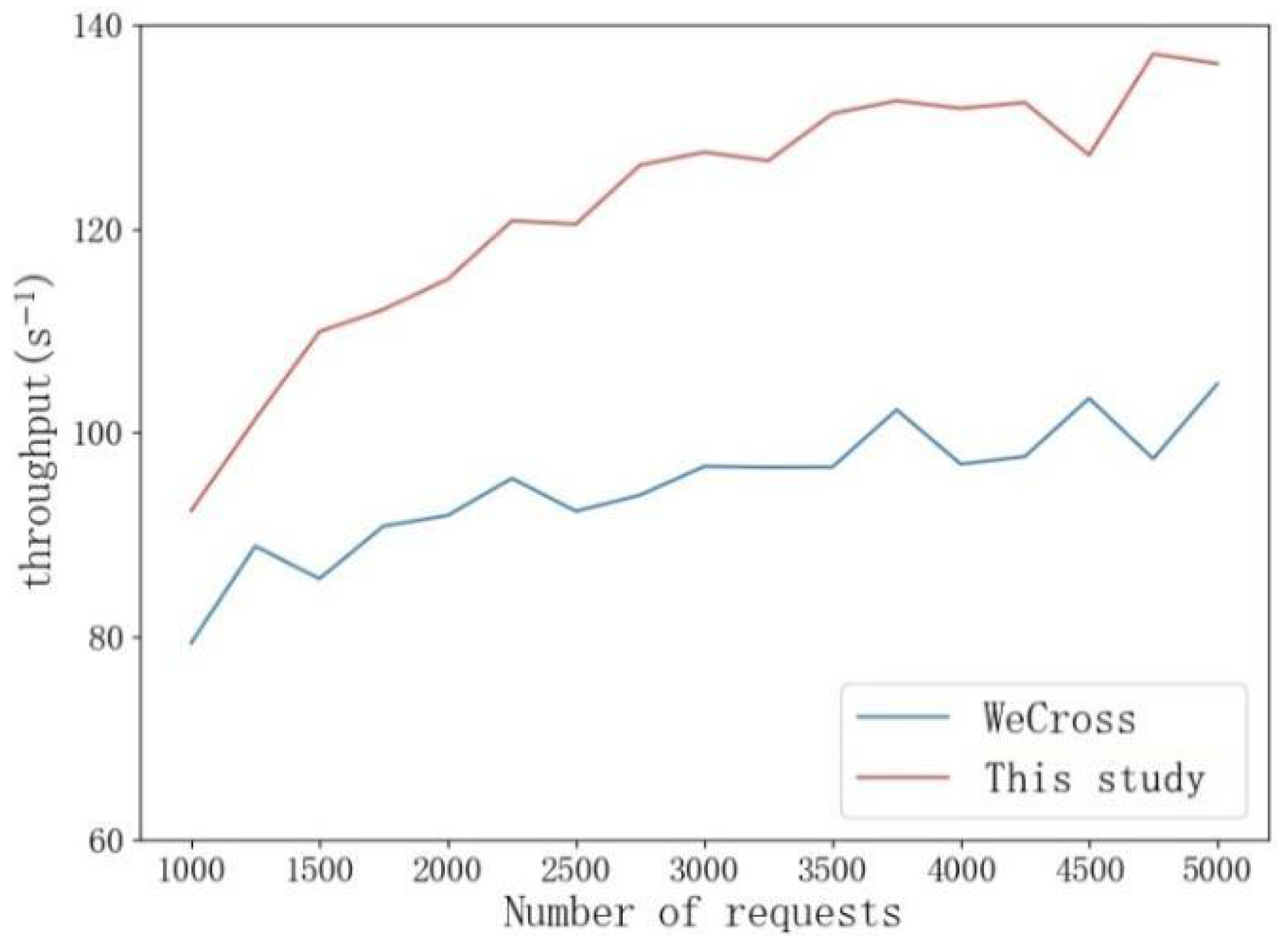
The research suggests an all-encompassing framework for optimizing smart contract execution that effectively manages the efficiency of contract execution in cross-chain situations. The framework, built on the current tri-level smart contract framework (CVSC, DESC, ORSC), enhances the system’s security and dependability by intensifying the process of contract implementation and deepening its efficiency. In Certificate Verification Smart Contracts (CVSC), the framework streamlines the verification procedure by thoroughly integrating it with the CCTL system. It employs CCTL and LRU, a fixed-length storage solution, to significantly diminish the frequency of verification and greatly advance certificate verification procedures. When it comes to Data Encryption Smart Contracts (DESCs), they enhance encryption strategies and processing processes, thereby ensuring data security and efficiency. This optimization plays a crucial role in transferring information across multiple-chain trust domains, directly influencing the system’s throughput and delay. At the operational record smart contract (ORSC) stage, an effective audit trail is attained by refining the blockchain status update process, guaranteeing full traceability in cross-chain activities while preserving high-chain performance in simultaneous scenarios.
5.1.5. Cross-Chain Component Specifications
The suggested inter-chain architecture introduces an advanced, multi-part structure greatly improving the reliability and effectiveness of inter-blockchain communication. The CVSC, a pivotal component of the trust verification process, integrates sophisticated protocols for parameter validation and refined algorithms for chain validation of certificates. Its incorporation features an intelligent caching layer for authenticated certificates, markedly cutting down computational expenses while upholding strict security protocols.
The innovative design of cross-chain anchor nodes is noteworthy, featuring a weighted round-robin algorithm for load balancing along with constant health observation. They sustain dynamically proportioned connection pools and execute a priority-driven request queue control, optimizing the usage of resources and ensuring system robustness under differing load scenarios. The systems’ failure detection and recovery systems ensure strong consistency and operational effectiveness.
5.2. Cross-Chain Model Based on Cross-Chain Anchor Nodes
5.2.1. Multi-Level Certificate Management System
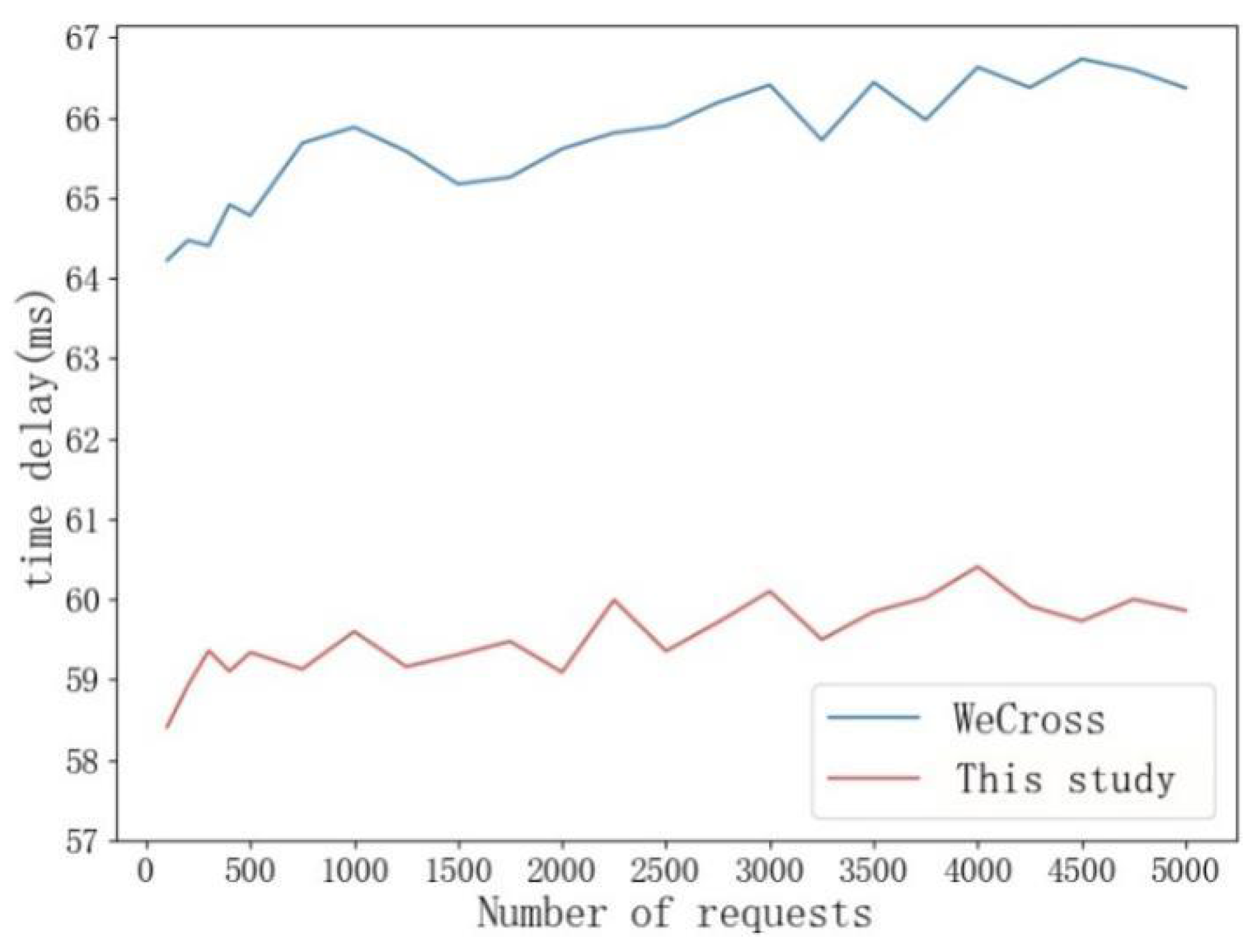
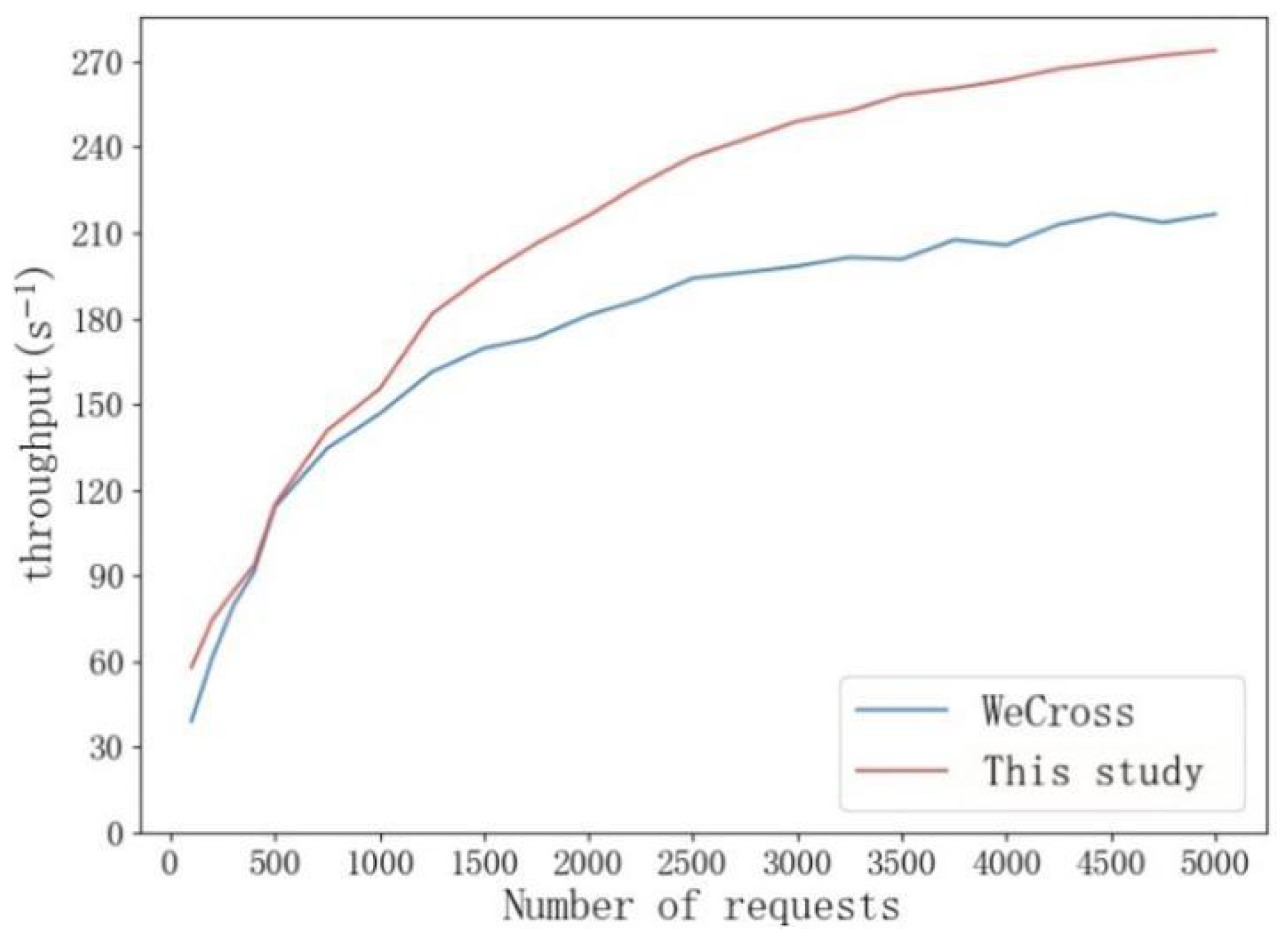
In order to deal with the computational overhead in large-scale cross-chain authentication scenarios, an enhanced certificate management system is proposed in this paper. The system uses an innovative CCTL framework to optimize the certificate management process by combining dynamic caching and efficient storage methods. In terms of architecture design, the system implements a composite storage structure, which combines high-speed memory cache with blockchain persistent storage to deal with frequently accessed certificate data and low active certificate data, respectively. This architecture not only ensures fast access to commonly used certificates but also guarantees a complete audit record through blockchain storage. In order to further improve the processing efficiency, batch processing technology is introduced to support parallel signature verification and authentication task processing. At the level of network transmission, the system adopts advanced certificate compression technology, including selective field transmission and dynamic compression ratio adjustment based on network conditions, which effectively reduces the network load. Experimental data show that the management system can significantly reduce authentication latency in typical cross-chain scenarios while maintaining complete record accuracy. By introducing these optimization mechanisms, the system significantly improves the efficiency and scalability of certificate management while maintaining high security, and provides strong technical support for large-scale cross-chain interaction.
This architecture enhances the foundational distributed trust model and addresses the performance constraints in cross-chain verification via technological advancements. The experiment indicates the system’s efficacy in managing substantial concurrent requests and offers a dependable technical route for establishing a proficient alliance chain cross-chain system.
5.2.2. Cross-Chain Model Implementation
Before discussing the specific implementation of cross-chain anchor nodes, it is essential to understand how cross-chain organizations maintain and utilize the CB-SCL through a sophisticated distributed consensus mechanism. Each participating organization contributes to multiple critical processes, actively engaging in validating new contract registrations, maintaining contract metadata integrity, and enforcing access control policies within their respective channels. This collaborative framework enables participating organizations to maintain synchronized copies of the CB-SCL while participating in periodic audits of contract operations. The CB-SCL thus serves as a critical bridge between organizational boundaries, facilitating secure and controlled cross-chain interactions while preserving the autonomy of individual chains.
The cross-chain communication scheme is the core content of the cross-chain interaction scheme. In the specific implementation process, in order to eliminate the security risks brought by third parties, this study proposes a cross-chain model based on cross-chain anchor nodes. The difference between cross-chain anchor nodes and ordinary nodes is that cross-chain anchor nodes need application layer services dedicated to cross-chain. The organization with cross-chain anchor nodes is called a cross-chain organization. There is at least one cross-chain anchor node in the cross-chain organization, and the load balancing server is used to assign cross-chain requests to each anchor node to improve the availability of the system. As a basic member of the channel, the organization can flexibly set the cross-chain access rights of the data using the endorsement strategy within the channel. In addition, the contract calling result is returned by the cross-chain anchor node, and the cross-chain access control is realized by combining the access strategy of the channel.
A cross-chain is an off-chain service component, which has little impact on the underlying structure of the blockchain. Because the organizational structure of the distributed trust model based on the trust list is relatively loose, the main interaction among chains is implemented on the application layer of the blockchain. The cross-chain model is shown in
Figure 6.
In the process of establishing cross-chain communication, Certificate Trust List (CTL) and Routing Address List (RAL) can be maintained through sharing, and cross-chain requests for CTL and RAL can be achieved without authentication. Therefore, as long as the trusted cross-chain organization routing is obtained, the chain CTL can be requested to supplement and maintain its own CTL to achieve trust transfer.
By adding cross-chain anchor nodes to the chain and updating the open nodes and CTLs outside the chain, cross-chain communication can be achieved with other chains. It truly achieves a lightweight and pluggable efficient consortium blockchain cross-chain scheme without a third party. In addition, because the scheme of this study mainly uses smart contracts and application layer services, this scheme can meet the cross-chain requirements between various heterogeneous consortium blockchains.
The CB-SCL’s technical deployment utilizes an advanced data structure framework aimed at enhancing contract management and access control checks. Its primary structure revolves around a ContractMetadata framework, which incorporates crucial operational elements. This framework upholds key data fields, including an address identifier for accurate contract positioning, a chain identifier represented as a 32-byte value for distinct chain identification, and a timestamp for version control and timing tracking. This system includes a dynamic authorization mapping mechanism, correlating organizational addresses to boolean access permissions, thus offering detailed control over inter-chain communication. Moreover, it preserves a range of supported procedures represented as 32-byte values, aiding in thorough operation monitoring and validation.
Implementation of the contract registry system involves a mapping framework, linking distinct identifiers with each ContractMetadata instance. This architecture facilitates effective contract retrieval processes while maintaining robust access control verification systems. The registry system streamlines cross-chain operations by fine-tuning data access patterns and organized metadata management protocols, allowing the CB-SCL to handle the intricacies of cross-chain interactions efficiently, all the while adhering to stringent security and autonomy standards.
The architectural design of this system guarantees operational effectiveness and security throughout the network, establishing a solid base for inter-chain interaction and managing contracts. It shows a focus on scalability and security needs, ensuring the adaptability required for various cross-chain situations.
5.3. Mechanism to Prevent Sybil Attacks
In order to better address the security issues of Sybil attacks, we propose solutions to the problem in this subsection.
The segment delineates a multi-layered authorization and reliability evaluation system, established at the core of consortium blockchain rights, aimed at preventing malicious nodes from creating various identities for executing Sybil attacks in inter-chain communications. It integrates organizational entry control, validation of anchor node qualifications, and dynamic trust evaluation to establish a comprehensive defense structure.
To regulate member access to an entity, rigorous entry procedures are applied in the consortium’s blockchain system. An entity,
, must obtain multiple signature validations from existing collectives before joining. With a total of
n organizations, entry into new entities demands a baseline of
m signatures (assuming
), as shown in Equation:
where
is the maximum number of anchor nodes allowed per organization.
Ultimately, a flexible trust assessment method has been set up for anchor nodes: For each node labeled
k, its trust metric
is computed using the formula
where
represents the node’s modified online duration,
the standardized response rate,
the node’s transaction success rate,
,
,
the weight coefficients, and the total of
equals 1.
The update strategy of trust score adopts a dual-track system: (1) Periodic update based on time, triggering the whole network credit reassessment with a fixed block interval (for example, after every 1000 blocks are generated). (2) Event-based triggered update, when there is an obvious anomaly in node behavior (such as continuous failed transactions exceeding the preset threshold), the trust re-calculation is performed immediately. To prevent malicious nodes from manipulating the trust score, all trust updates must be verified by multi-organization consensus, requiring at least m organizations to sign for confirmation (where , n is the total number of organizations), thus ensuring the fairness of the scoring process.
The node’s cross-chain service qualification is determined by its trust score according to Equation:
When a new node joins the alliance chain network, the system adopts the progressive trust establishment mechanism, initially puts the node in the trial state with limited permissions, and assigns the initial trust value of the lowest acceptable threshold . The access process requires the new node to provide an identity certificate signed and endorsed by at least kof existing high-trust nodes (meeting the condition of ), and then the system performs a complete certificate chain verification on the certificate to ensure its consistency with the existing CTL. The new node gradually accumulates trust value through continuous and stable cross-chain service and can obtain formal node qualification only after maintaining good performance for successive mevaluation cycles. In terms of node exit management, the system supports two modes: In the normal exit process, the exiting node actively initiates the certificate revocation request, and the certificate revocation notice is broadcast on the whole network after the network consensus is confirmed. When the node trust score continuously drops below the threshold of or malicious behaviors occur, the system triggers a forced protocol exit. Regardless of the exit method, the updated CTL and Communication Certificates Trust List (CCTL) will be synchronized to all participating chains, and the complete behavior history of the exiting node will be retained on the blockchain for subsequent audit and security analysis. Node states based on trust scores are defined as three levels: Active (), Probation (), and Suspended (). Nodes in different statuses have different configurations of cross-chain permissions: only the Active node can perform all cross-chain operations, the Probation node is limited to low-risk cross-chain read operations, and the Suspended node suspends all cross-chain services. This complete node lifecycle management framework and dynamic trust evaluation mechanism complement each other, and together constitute the infrastructure of the distributed trust model in this paper, providing reliable security for the alliance blockchain cross-chain identity authentication system.
Leveraging the consortium blockchain’s sanctioned status, this framework implements measures at the organizational level and integrates a trust evaluation system for ongoing monitoring at the nodes. The system’s seamless integration of static authorization control with dynamic trust assessment successfully averts Sybil attacks while minimally hindering standard cross-chain activities. Its layered defense approach guarantees that despite an attacker registering numerous identities, sustained good behavior over an extended time is essential for earning system trust, thereby greatly raising the expense and complexity of initiating Sybil attacks.
Additionally, incorporating trust evaluation results into the cross-chain validation process detailed in
Section 2.4 enhances the system’s overall security and is consistent with the distributed trust paradigm proposed in this study, thereby setting a sturdy security groundwork for future cross-chain data exchanges.