An Energy Efficient and DPA Attack Resilient NCFET-Based S-Box Design for Secure and Lightweight SLIM Ciphers
Abstract
1. Introduction
2. Background on IoT Security Challenges and Potential of NCFETs
2.1. Internet of Things (IoT) Security Challenges
2.1.1. Side Channel Attacks and Lightweight Ciphers
2.1.2. Potential of NCFETs for Secure Lightweight Ciphers and Energy Efficiency
3. NCFET Device Structure and Model Description
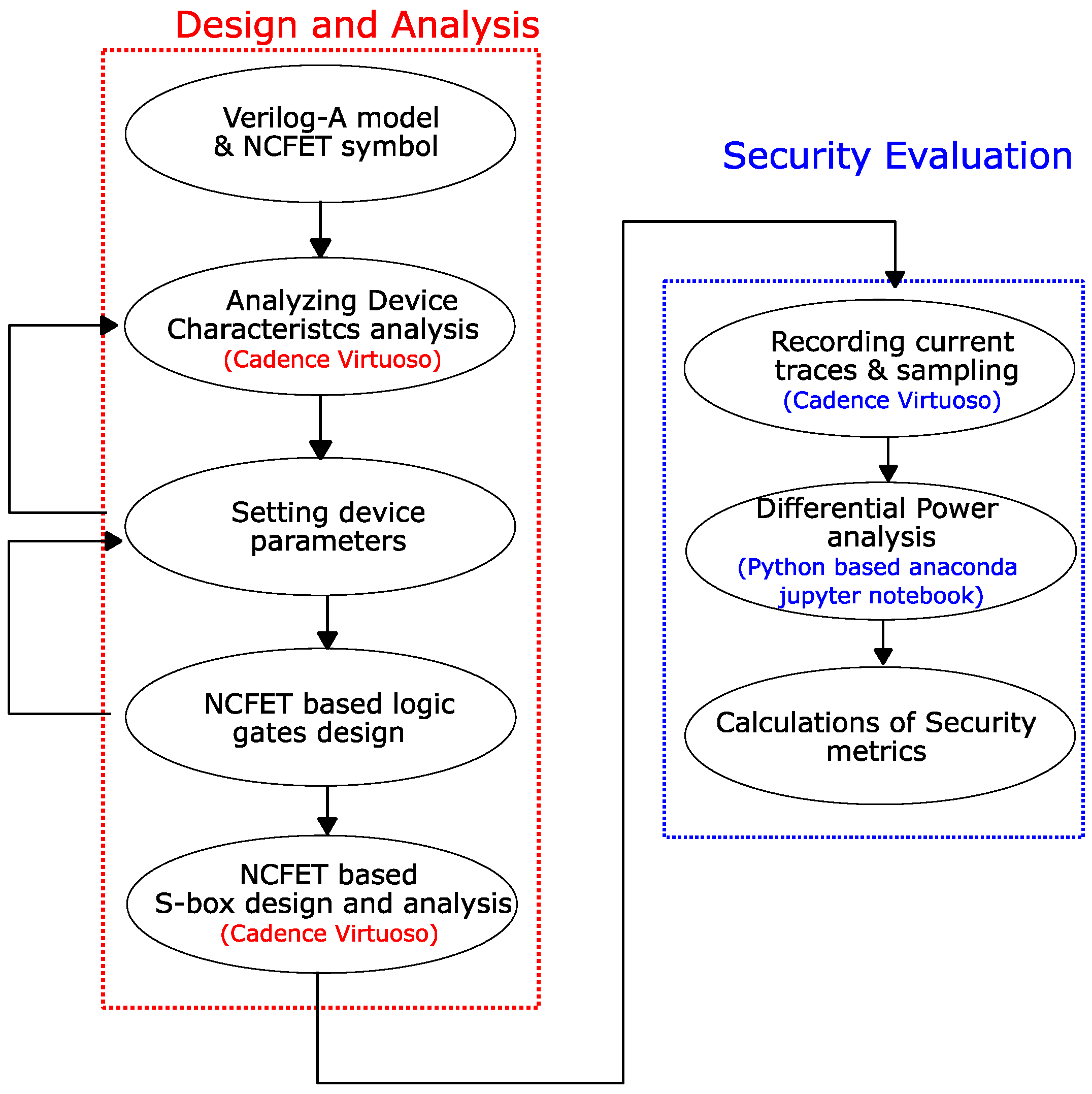
4. Experimental Setup for the NCFET-Based S-Box Design and Security Evaluation Methodology
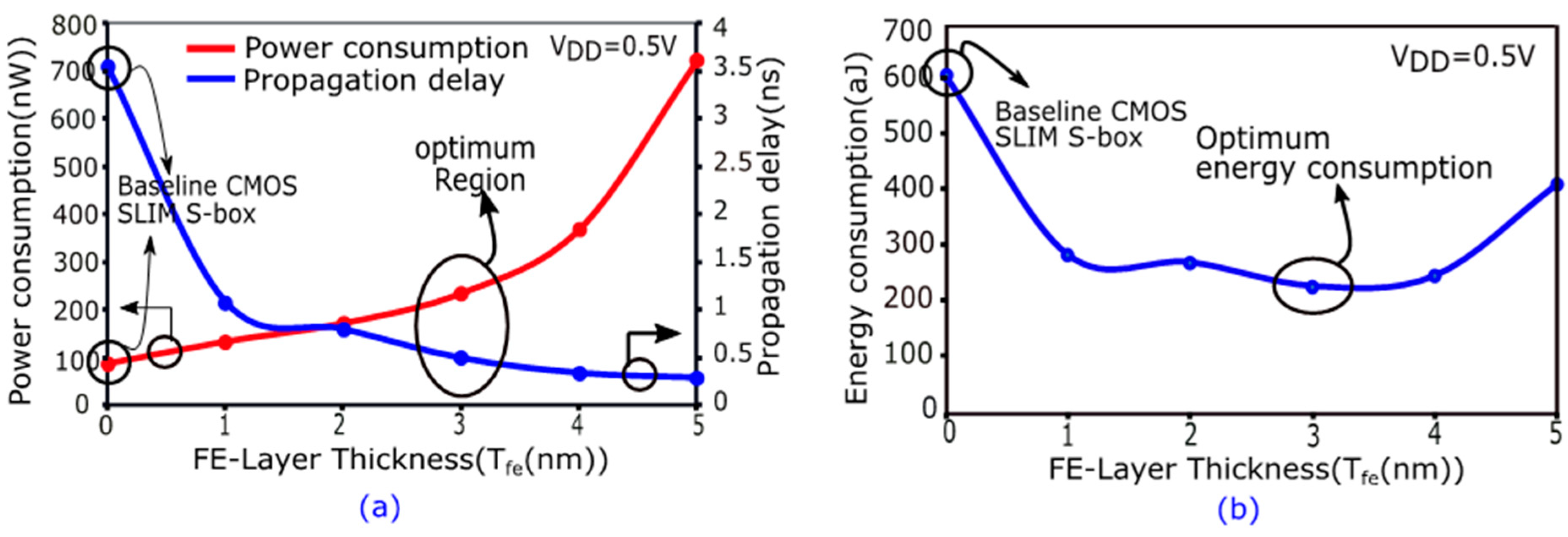
5. Design of an NCFET-Based S-Box for a Lightweight SLIM Block Cipher for Energy Efficiency
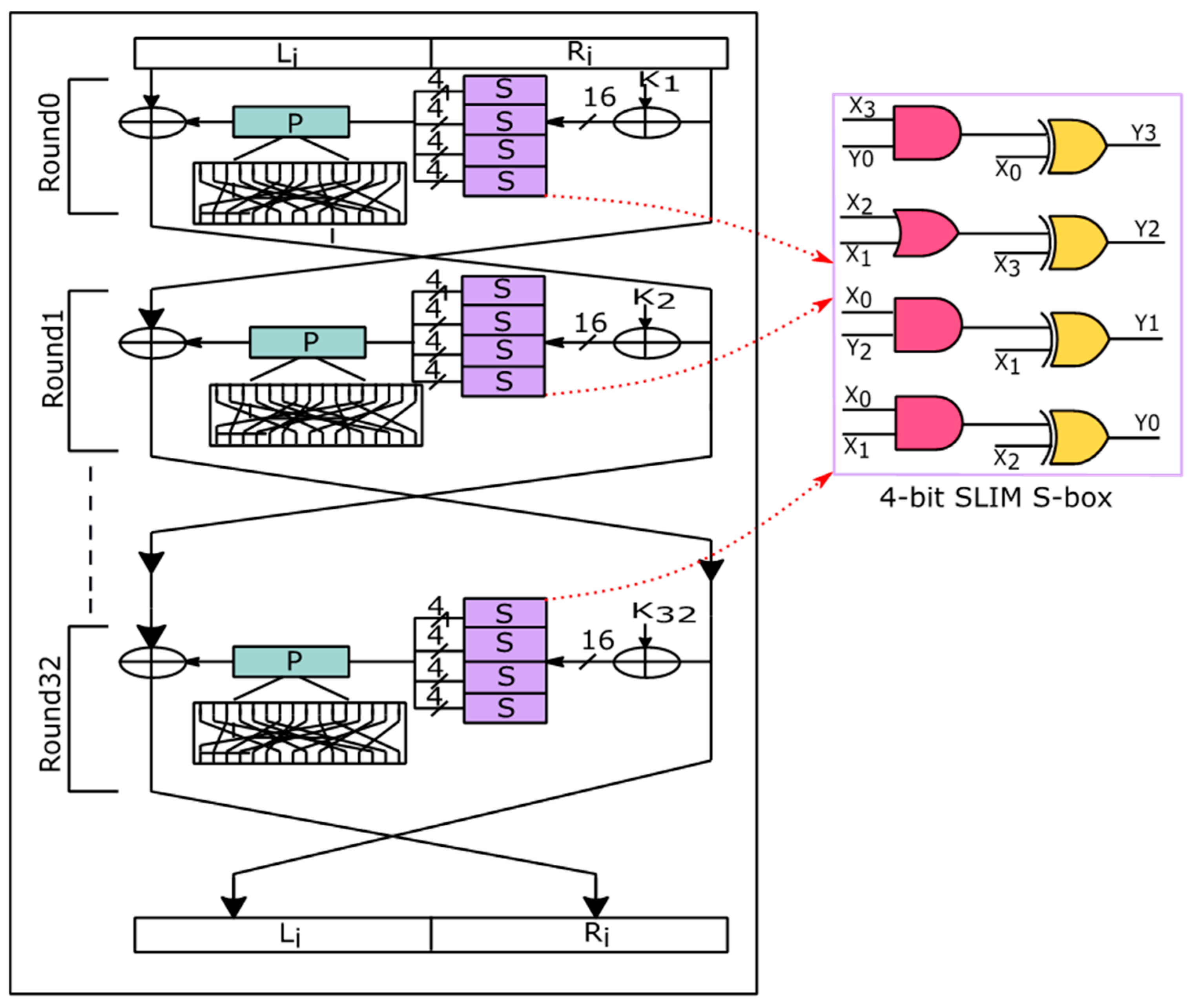
5.1. Structure of the SLIM Lightweight Block Cipher
5.2. The NCFET-Based SLIM S-Box Design
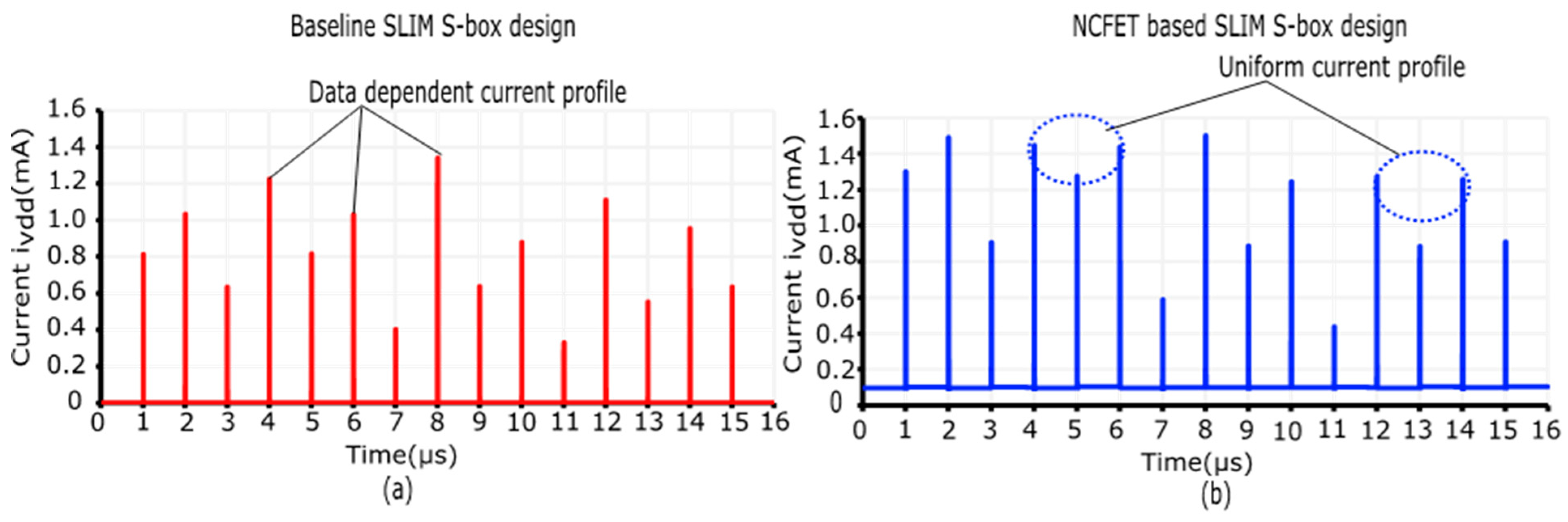
6. Security Assessment of the NCFET-Based S-Box for the Ultra-Lightweight SLIM Cipher Against DPA Attacks and Performance Benchmarking
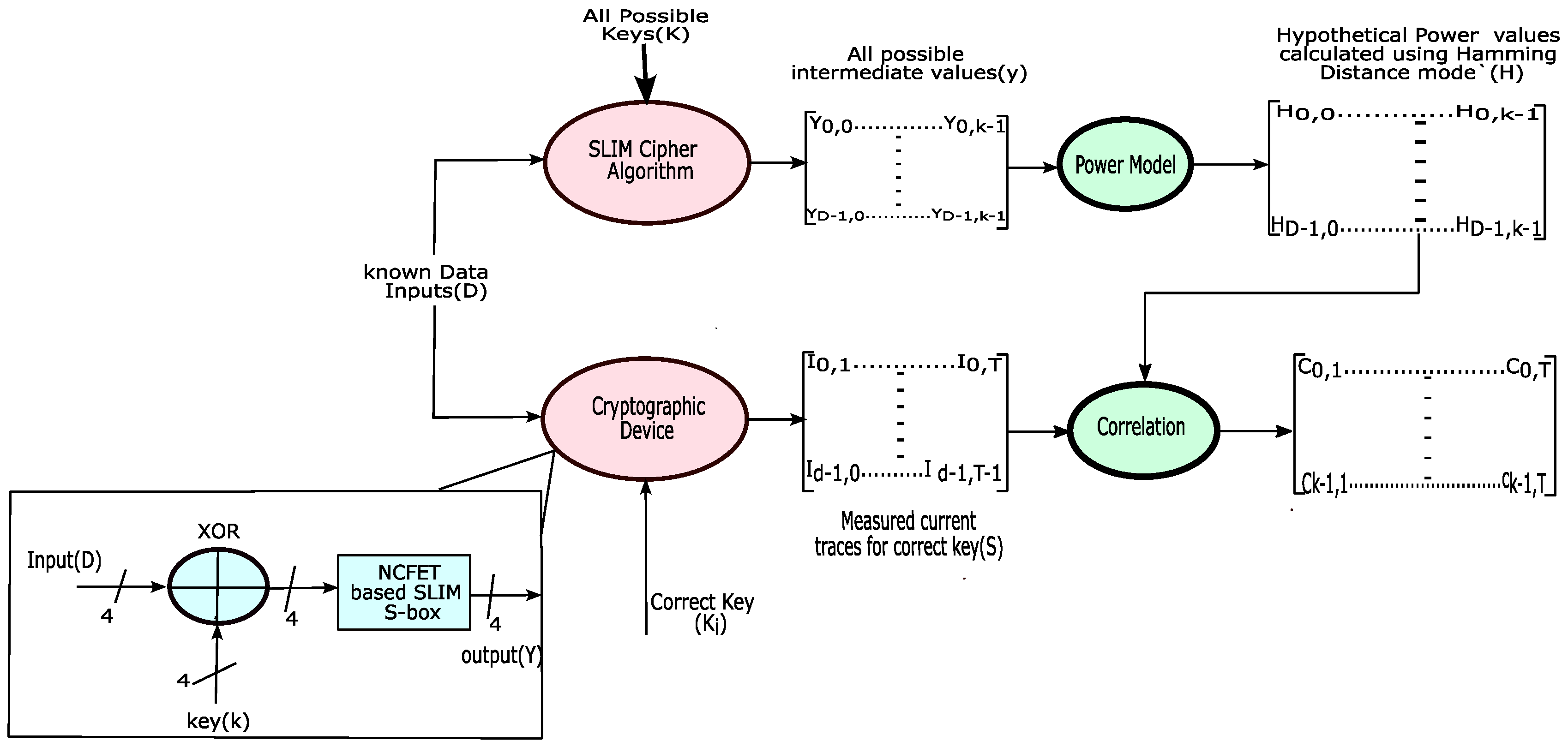
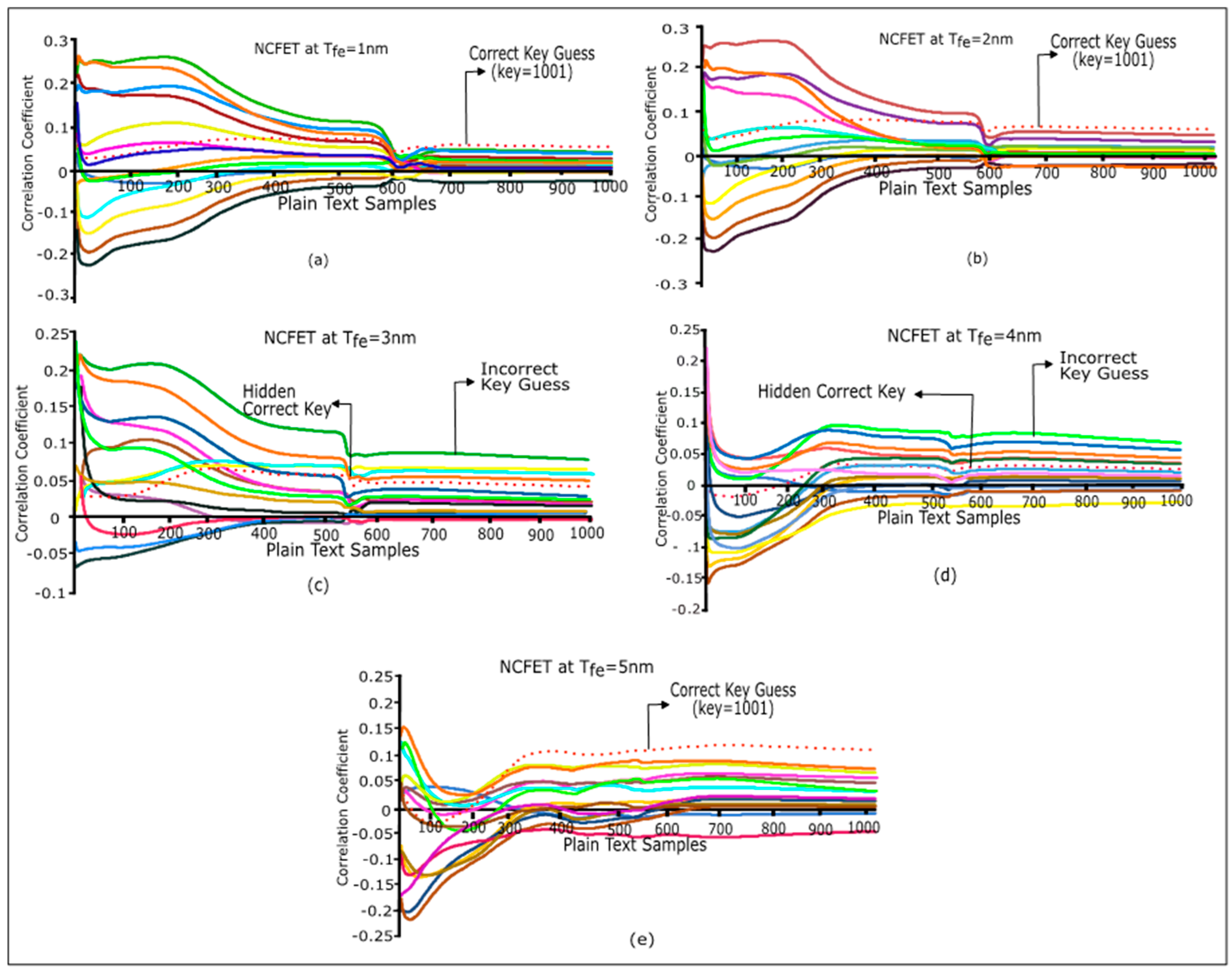
6.1. DPA Attack Methodology on an NCFET-Based S-Box for an Ultra-Lightweight SLIM Cipher
- The S-box is first designed in the Cadence Virtuoso environment, followed by the recording of the current traces (iVdd) using random inputs (D) and a fixed key (Ki).
- The current traces are recorded at a sampling rate of T (T samples per trace) and organized into a matrix S with dimensions of D × T.
- Next, the S-box algorithm will be implemented using Python 3 to calculate the output values with inputs D (the same inputs as in the previous step) and all potential keys K.
- The output values are mapped to hypothetical power consumption values through the Hamming Distance (HD) model and organized in a matrix H with dimensions D × K. The Hamming Distance between two consecutive output values is determined using Equation (7).HD = Hamming weight (Yi−1⊕Y)
- Finally, every column of the H matrix is correlated with all the columns of the current trace matrix S.
6.2. Performance Benchmarking of the Proposed Ultra-Lightweight NCFET-Based SLIM S-Box Design
6.2.1. Signal-to-Noise Ratio (SNR)
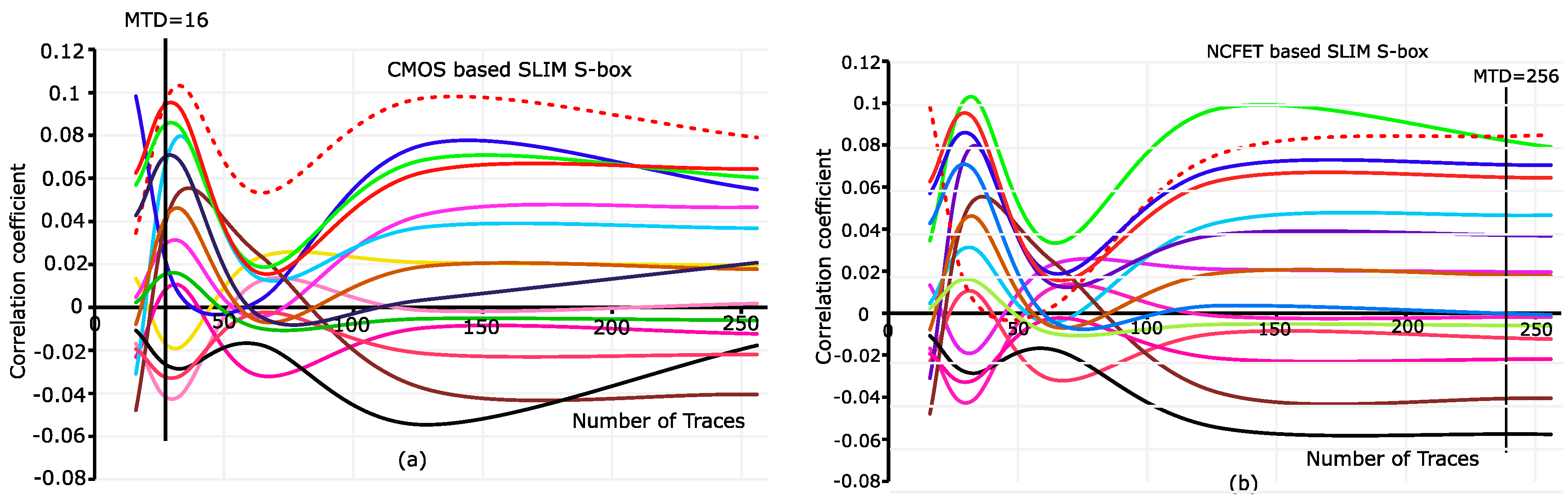
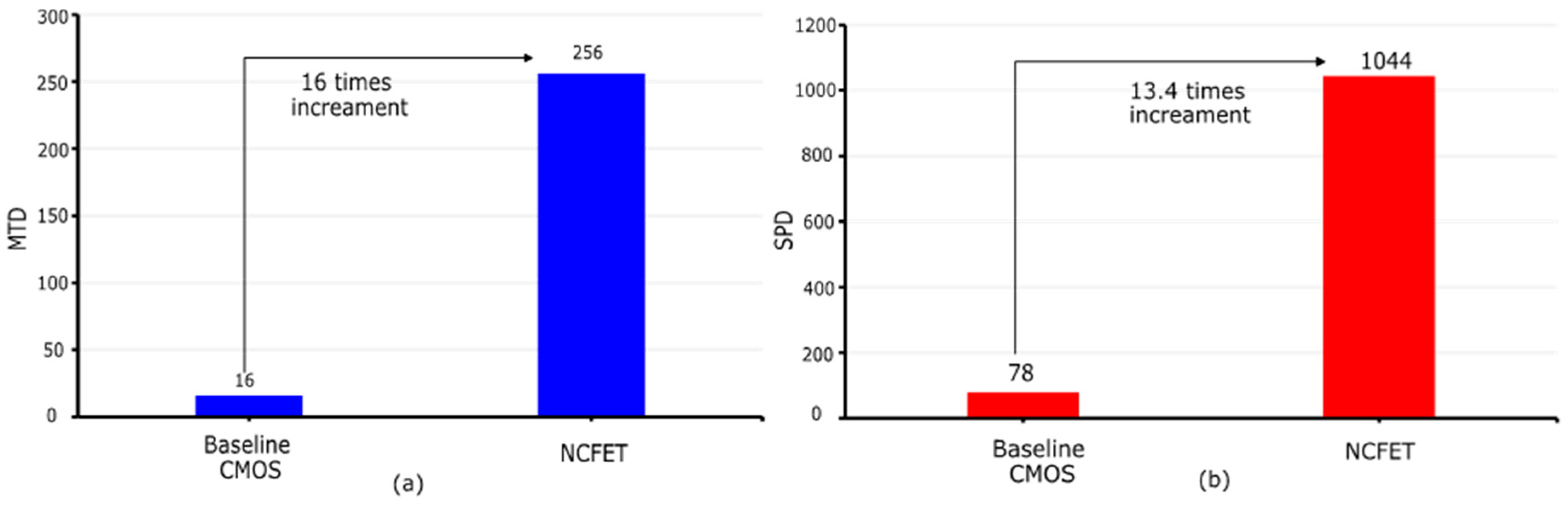
6.2.2. Measurements to Disclosure (MTD)
6.2.3. Security Power Delay (SPD)
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ha, G.; Chen, H.; Jia, C.; Li, M. Threat model and Defense scheme for side-channel attacks in client-side deduplication. Tsinghua Sci. Technol. 2023, 28, 1–12. [Google Scholar] [CrossRef]
- Tiwari, U.; Vollala, S.; Ramasubramanian, N.; Begum, B.S. Efficient hardware realization and high radix implementation of modular multi exponential techniques for public key cryptography. Microelectron. J. 2022, 128, 105548. [Google Scholar] [CrossRef]
- Wang, W.; Han, J.; Cheng, X.; Zeng, X. An energy-efficient crypto-extension design for RISC-V. Microelectron. J. 2021, 115, 105165. [Google Scholar] [CrossRef]
- Japa, A.; Sahoo, S.K.; Vaddi, R.; Majumder, M.K. Emerging tunnel FET and spintronics-based hardware-secure circuit design with ultra-low energy consumption. J. Comput. Electron. 2022, 22, 178–189. [Google Scholar] [CrossRef]
- Mishra, N.; Pandya, S. Internet of Things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- Zaky, A.; Elmitwalli, E.; Hemeda, M.; Ismail, Y.; Salah, K. Ultra low-power encryption/decryption core for lightweight IoT applications. In Proceedings of the ICENCO 2019—2019 15th 2019 15th International Computer Engineering Conference, Cairo, Egypt, 29–30 December 2019; pp. 39–43. [Google Scholar] [CrossRef]
- Yli-Mayry, V.; Ueno, R.; Miura, N.; Nagata, M.; Bhasin, S.; Mathieu, Y.; Graba, T.; Danger, J.L.; Homma, N. Diffusional side-channel leakage from unrolled lightweight block ciphers: A case study of power analysis on prince. IEEE Trans. Inf. Forensics Secur. 2021, 16, 1351–1364. [Google Scholar] [CrossRef]
- Bronchain, O.; Durvaux, F.; Masure, L.; Standaert, F.X. Efficient profiled side-channel analysis of masked implementations, extended. IEEE Trans. Inf. Forensics Secur. 2022, 17, 574–584. [Google Scholar] [CrossRef]
- Delgado-Lozano, I.M.; Tena-Sanchez, E.; Nunez, J.; Acosta, A.J. Design and analysis of secure emerging crypto-hardware using HyperFET devices. IEEE Trans. Emerg. Top. Comput. 2020, 9, 787–796. [Google Scholar] [CrossRef]
- Padmini, C.; Ravindra, J.V.R. Design of leakage resilient and DPA attack immune architecture of S BOX. In Proceedings of the 2021 6th International Conference on Communication and Electronics Systems, ICCES 2021, Coimbatre, India, 8–10 July 2021; pp. 936–944. [Google Scholar] [CrossRef]
- Masoumi, M. Novel hybrid CMOS/Memristor implementation of the AES algorithm robust against differential power analysis attack. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 1314–1318. [Google Scholar] [CrossRef]
- Arya, N.; Soni, T.; Pattanaik, M.; Sharma, G.K. Area and energy efficient approximate square rooters for error resilient applications. In Proceedings of the 2020 33rd International Conference on VLSI Design and 2020 19th International Conference on Embedded Systems, Bangalore, India, 4–8 January 2020; pp. 90–95. [Google Scholar] [CrossRef]
- Liu, Y.; Qian, K.; Wang, K.; He, L. Effective scaling of blockchain beyond consensus innovations and moore’s law: Challenges and opportunities. IEEE Syst. J. 2022, 16, 1424–1435. [Google Scholar] [CrossRef]
- Japa, A.; Majumder, M.K.; Sahoo, S.K.; Vaddi, R. Low area overhead DPA countermeasure exploiting tunnel transistor-based random number generator. IET Circuits Devices Syst. 2020, 14, 640–647. [Google Scholar] [CrossRef]
- Kumar, S.D.; Thapliyal, H. Exploration of non-volatile MTJ/CMOS circuits for DPA-resistant embedded hardware. IEEE Trans. Magn. 2019, 55, 1–8. [Google Scholar] [CrossRef]
- Amrouch, H.; Van Santen, V.M.; Pahwa, G.; Chauhan, Y.; Henkel, J. NCFET to rescue technology scaling: Opportunities and challenges. In Proceedings of the 2020 25th Asia and South Pacific Design Automation Conference (ASP-DAC), Beijing, China, 13–16 January 2020; pp. 637–644. [Google Scholar] [CrossRef]
- Bheemana, R.C.; Japa, A.; Yellampalli, S.; Vaddi, R. Steep switching NCFET based logic for future energy efficient electronics. In Proceedings of the 2021 IEEE International Symposium on Smart Electronic Systems (iSES), Jaipur, India, 18–22 December 2021; pp. 327–330. [Google Scholar] [CrossRef]
- Tu, L.; Wang, X.; Wang, J.; Meng, X.; Chu, J. Ferroelectric negative capacitance field effect transistor. Adv. Electron. Mater. 2018, 4, 1800231. [Google Scholar] [CrossRef]
- Fan, C.C.; Cheng, C.H.; Chen, Y.R.; Liu, C.; Chang, C.Y. Energy-efficient HfAlOx NCFET: Using gate strain and defect passivation to realize nearly hysteresis-free sub-25mV/dec switch with ultralow leakage. In Proceedings of the 2017 IEEE International Electron Devices Meeting (IEDM), San Francisco, CA, USA, 2–6 December 2018; pp. 23.2.1–23.2.4. [Google Scholar] [CrossRef]
- Jo, J.; Shin, C. Experimental observation of voltage amplification using negative capacitance for sub-60 mV/decade CMOS devices. Curr. Appl. Phys. 2015, 15, 352–355. [Google Scholar] [CrossRef]
- Jooq, M.K.Q.; Moaiyeri, M.H.; Tamersit, K. Ultra-compact ternary logic gates based on negative capacitance carbon nanotube FETs. IEEE Trans. Circuits Syst. II Express Briefs 2021, 68, 2162–2166. [Google Scholar] [CrossRef]
- Wang, H.; Yang, M.; Huang, Q.; Zhu, K.; Zhao, Y.; Liang, Z.; Chen, C.; Wang, Z.; Zhong, Y.; Zhang, X.; et al. New insights into the physical origin of negative capacitance and hysteresis in NCFETs. In Proceedings of the 2018 IEEE International Electron Devices Meeting (IEDM), San Francisco, CA, USA, 1–5 December 2019; p. 31. [Google Scholar] [CrossRef]
- Salamin, S.; Rapp, M.; Pathania, A.; Maity, A.; Henkel, J.; Mitra, T.; Amrouch, H. Power-efficient heterogeneous many-core design with NCFET technology. IEEE Trans. Comput. 2021, 70, 1484–1497. [Google Scholar] [CrossRef]
- Lee, C.H.; Hsu, Y.T.; Liu, T.T.; Chiueh, T.D. Design of an 45nm NCFET based compute-in-SRAM for energy-efficient machine learning applications. In Proceedings of the 2020 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS), Ha Long, Vietnam, 8–10 December 2020; pp. 193–196. [Google Scholar] [CrossRef]
- Chauhan, N.; Bagga, N.; Banchhor, S.; Datta, A.; Dasgupta, S.; Bulusu, A. Negative-to-positive differential resistance transition in ferroelectric FET: Physical insight and utilization in analog circuits. IEEE Trans. Ultrason. Ferroelectrics Freq. Control 2022, 69, 430–437. [Google Scholar] [CrossRef]
- Liang, Y.; Zhu, Z.; Li, X.; Gupta, S.K.; Datta, S.; Narayanan, V. Utilization of negative-capacitance FETs to boost analog circuit performances. IEEE Trans. Very Large Scale Integr. Syst. 2019, 27, 2855–2860. [Google Scholar] [CrossRef]
- Bheemana, R.C.; Japa, A.; Yellampalli, S.S.; Vaddi, R. Negative capacitance FETs for energy efficient and hardware secure logic designs. Microelectron. J. 2022, 119, 105320. [Google Scholar] [CrossRef]
- Japa, A.; Majumder, M.K.; Sahoo, S.K.; Vaddi, R.; Kaushik, B.K. Hardware security exploiting post-CMOS devices: Fundamental device characteristics, state-of-the-art countermeasures, challenges and roadmap. IEEE Circ. Syst. Mag. 2021, 21, 4–30. [Google Scholar] [CrossRef]
- Birudu, V.; Yellampalli, S.S.; Vaddi, R. A negative capacitance FET based energy efficient 6T SRAM computing-in-memory (CiM) cell design for deep neural networks. Microelectron. J. 2023, 139, 105867. [Google Scholar] [CrossRef]
- Keerthi, G.; Semwal, S.; Kranti, A. Analytical modeling of negative capacitance transistor based ultra-low power Schmitt trigger. Solid-State Electron. 2023, 207, 108700. [Google Scholar] [CrossRef]
- Choudhuri, B.; Mummaneni, K. A new pocket-doped NCFET for low power applications: Impact of ferroelectric and oxide thickness on its performance. Micro Nanostruct. 2022, 169, 207360. [Google Scholar]
- Hassan, R.; Qamar, F.; Hasan, M.K.; Ha, A.; Aman, M.; Ahmed, A.S. Internet of Things and its applications: A comprehensive survey. Symmetry 2020, 12, 1674. [Google Scholar] [CrossRef]
- Dash, S.P. The impact of IoT in healthcare: Global review. J. Indian Inst. Sci. 2020, 100, 773–785. [Google Scholar] [CrossRef]
- Demestichas, K.; Peppes, N.; Alexakis, T. Survey on security threats in agricultural IoT and smart farming. Sensors 2020, 20, 6458. [Google Scholar] [CrossRef]
- Rahim, M.A.; Rahman, M.A.; Rahman, M.M.; Asyhari, A.T.; Bhuiyan, M.Z.A.; Ramasamy, D. Evolution of IoT-enabled connectivity and applications in automotive industry: A review. Veh. Commun. 2021, 27, 100285. [Google Scholar] [CrossRef]
- Suryadevara, N.K.; Biswal, G.R. Smart plugs: Paradigms and applications in the smart city-and-smart grid. Energies 2019, 12, 1957. [Google Scholar] [CrossRef]
- Ngo, Q.-D.; Nguyen, H.-T.; Nguyen, L.-C.; Nguyen, D.-H. A survey of IoT malware and detection methods based on static features. ICT Express 2020, 6, 280–286. [Google Scholar] [CrossRef]
- Khalifa, O.O.; Islam, M.R.; Khan, S.; Shebani, M.S. Communications cryptography. In Proceedings of the 2004 RF and Microwave Conference, Selangor, Malaysia, 5–6 October 2004. [Google Scholar]
- Thakor, V.A.; Razzaque, M.A.; Khandaker, M.R.A. Lightweight Cryptography Algorithms for Resource-Constrained IoT Devices: A Review, Comparison and Research Opportunities. IEEE Access 2021, 9, 28177–28193. [Google Scholar] [CrossRef]
- Aziz, S.; Shoukat, I.A.; Iftikhar, M.; Murtaza, M.; Alenezi, A.M.; Lee, C.-C.; Taj, I. Next-Generation Block Ciphers: Achieving Superior Memory Efficiency and Cryptographic Robustness for IoT Devices. Cryptography 2024, 8, 47. [Google Scholar] [CrossRef]
- Diehl, W.; Abdulgadir, A.; Kaps, J.P.; Gaj, K. Comparing the cost of protecting selected lightweight block ciphers against differential power analysis in low-cost FPGAs. Computers 2018, 7, 28. [Google Scholar] [CrossRef]
- Bheemana, R.C.; Japa, A.; Yellampalli, S.S.; Vaddi, R. Negative capacitance FET based energy efficient and DPA attack resilient ultra-light weight block cipher design. Microelectron. J. 2023, 133, 105711. [Google Scholar] [CrossRef]
- Kaushal, S. Introduction to Newly Adopted NCFET and Ferroelectrics for Low-Power Application. In Advanced Ultra Low-Power Semiconductor Devices: Design and Applications; Wiley: Hoboken, NJ, USA,, 2023; pp. 207–234. [Google Scholar] [CrossRef]
- Japa, A.; Majumder, M.K.; Sahoo, S.K.; Vaddi, R. Tunnel FET-based ultralow-power and hardware-secure circuit design considering p-i-n forward leakage. Int. J. Circuit Theory Appl. 2020, 48, 524–538. [Google Scholar] [CrossRef]
- Kwon, D.; Cheema, S.; Shanker, N.; Chatterjee, K.; Liao, Y.H.; Tan, A.J.; Hu, C.; Salahuddin, S. Negative Capacitance FET with 1.8-nm-Thick Zr-Doped HfO2 Oxide. IEEE Electron Device Lett. 2019, 40, 993–996. [Google Scholar] [CrossRef]
- Li, X.; Sampson, J.; Khan, A.; Ma, K.; George, S.; Aziz, A.; Gupta, S.K.; Salahuddin, S.; Chang, M.-F.; Datta, S.; et al. Enabling Energy-Efficient Nonvolatile Computing with Negative Capacitance FET. IEEE Trans. Electron Devices 2017, 64, 3452–3458. [Google Scholar] [CrossRef]
- Radhakrishna, U.; Khan, P.A.; Tech, G.; Berkeley, U.C. Compact Model of Negative Capacitance CMOSs (NCFETs). 2017. Available online: https://nanohub.org/projects/mvsncfet (accessed on 23 October 2024).
- Pahwa, G.; Dutta, T.; Agarwal, A.; Khandelwal, S.; Salahuddin, S.; Hu, C.; Chauhan, Y.S. Analysis and compact modelling of negative capacitance transistor with high ON-current and negative output differential resistance—Part I: Model description. IEEE Trans. Electron. Dev. 2016, 63, 4981–4985. [Google Scholar] [CrossRef]
- Aboushosha, B.; Ramadan, R.A.; Dwivedi, A.D.; El-Sayed, A.; Dessouky, M.M. SLIM: A Lightweight Block Cipher for Internet of Health Things. IEEE Access 2020, 8, 203747–203757. [Google Scholar] [CrossRef]
- Kumar, S.D.; Thapliyal, H.; Mohammad, A. FinSAL: FinFET-Based Secure Adiabatic Logic for Energy-Efficient and DPA Resistant IoT Devices. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2018, 37, 110–122. [Google Scholar] [CrossRef]
- Tiri, K.; Hwang, D.; Hodjat, A.; Lai, B.C.; Yang, S.; Schaumont, P.; Verbauwhede, I. Prototype IC with WDDL and differential routing–DPA resistance assessment. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2005; pp. 354–365. [Google Scholar]
- Tena-Sánchez, E.; Acosta, A.J. Logic minimization and wide fan-in issues in DPL-based cryptocircuits against power analysis attacks. Int. J. Circuit Theory Appl. 2019, 47, 238–253. [Google Scholar]

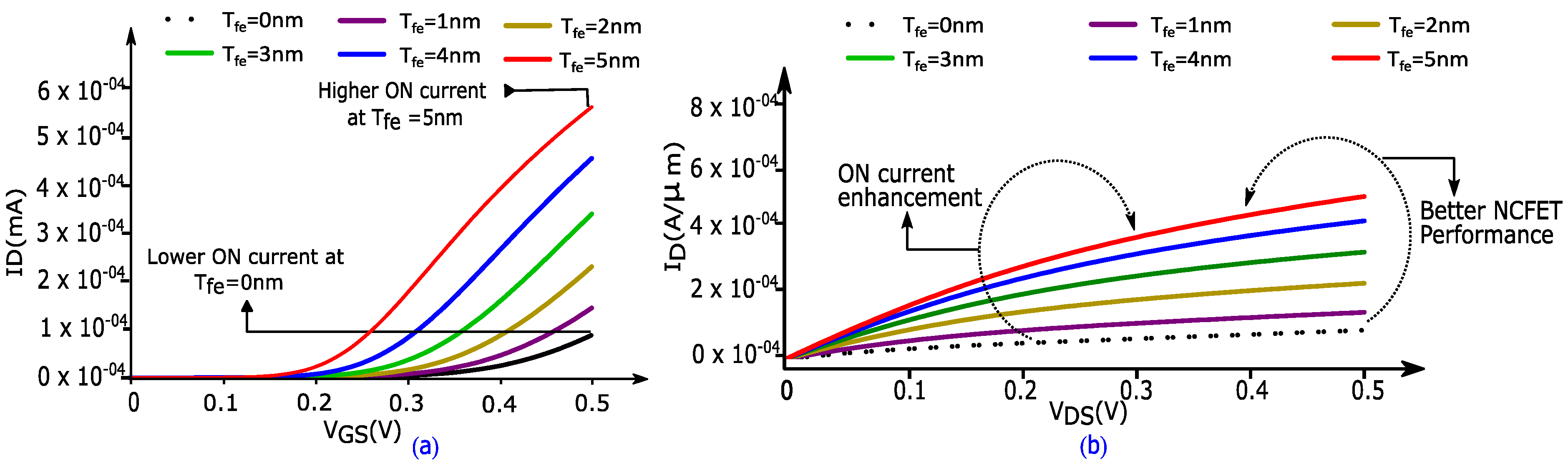
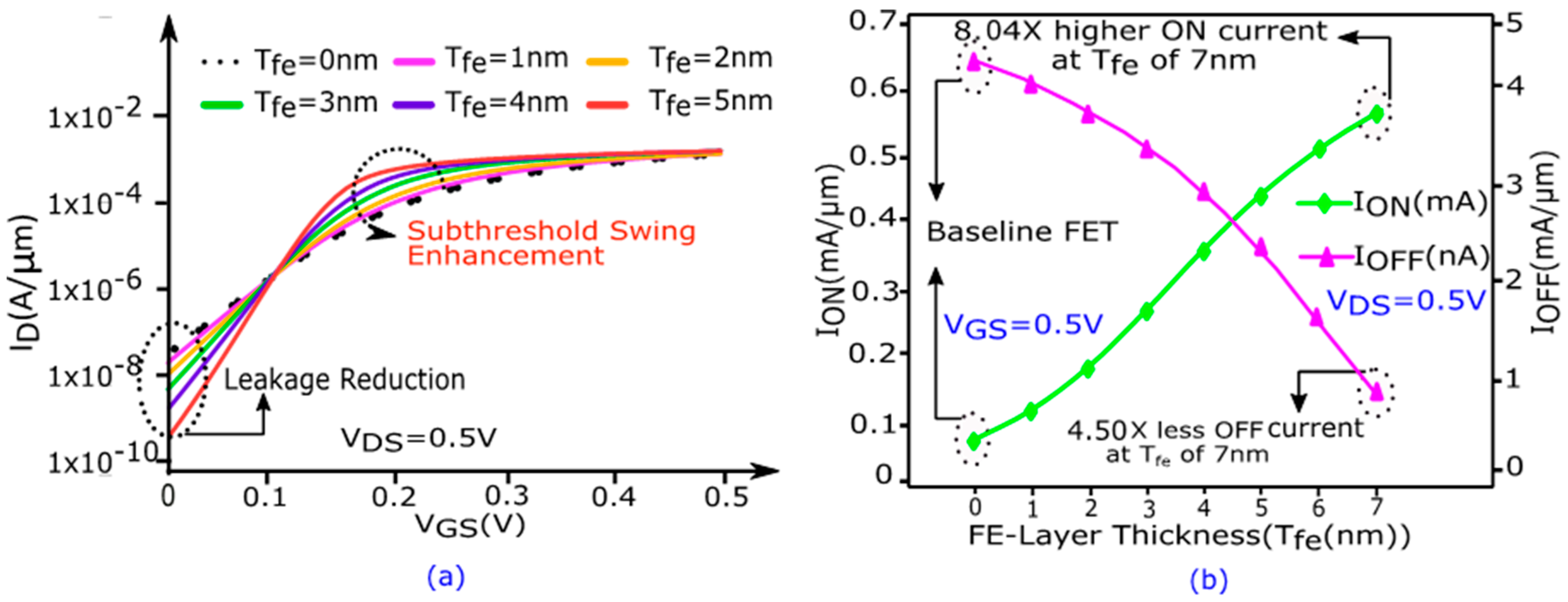





| Symbol | Device Parameters | Values |
|---|---|---|
| Lgdr | Length of the Gate | 4.0 × 10−6 cm |
| W | Transistor Width | 1.0 × 10−6 cm |
| Po | Remnant Polarization | 2.5 × 102 C/cm2 |
| Ec | Coercive Field | 6.5 × 109 V/cm |
| Tfe | Thickness of the FE Layer | 5.0 × 10−11 cm |
| PRIDE S-Box [52] | PRIDE S-Box [52] | PRIDE-Based S-Box with SABL [4] | PRIDE-Based S-Box with SABL [4] | PRESENT-80 S-Box [44] | SLIM S-Box (This Work) | ||
|---|---|---|---|---|---|---|---|
| Technology | FinFET 14 nm | HyperFET 14 nm | TFET 20 nm | FinFET 20 nm | NCFET 40 nm | CMOS 40 nm | NCFET 40 nm |
| VDD (V) | 0.8 | 0.8 | 0.3 | 0.3 | 0.5 | 0.5 | 0.5 |
| Power consumption (µW) | 5.04 | 5.16 | 6.3 | 6.7 | 0.254 | 0.085 | 0.233 |
| Propagation delay (ns) | 0.18 | 0.52 | 2.12 | 6.17 | 0.51 | 3.54 | 0.45 |
| Energy consumption (fJ) | 1.81 | 5.36 | 13.09 | 41.339 | 0.259 | 0.608 | 0.228 |
| SNR | --- | --- | -- | -- | 0.795 | 1.1074 | 0.298 |
| MTD | 76.06 | -- | -- | -- | 64 | 16 | 256 |
| SPD (1015) J−1 | 85.83 | 711.36 | -- | -- | 275 | 78 | 1044 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Penumalli, K.R.; Gonuguntla, V.; Vaddi, R. An Energy Efficient and DPA Attack Resilient NCFET-Based S-Box Design for Secure and Lightweight SLIM Ciphers. Electronics 2025, 14, 1114. https://doi.org/10.3390/electronics14061114
Penumalli KR, Gonuguntla V, Vaddi R. An Energy Efficient and DPA Attack Resilient NCFET-Based S-Box Design for Secure and Lightweight SLIM Ciphers. Electronics. 2025; 14(6):1114. https://doi.org/10.3390/electronics14061114
Chicago/Turabian StylePenumalli, Koteswara Rao, Venkateswarlu Gonuguntla, and Ramesh Vaddi. 2025. "An Energy Efficient and DPA Attack Resilient NCFET-Based S-Box Design for Secure and Lightweight SLIM Ciphers" Electronics 14, no. 6: 1114. https://doi.org/10.3390/electronics14061114
APA StylePenumalli, K. R., Gonuguntla, V., & Vaddi, R. (2025). An Energy Efficient and DPA Attack Resilient NCFET-Based S-Box Design for Secure and Lightweight SLIM Ciphers. Electronics, 14(6), 1114. https://doi.org/10.3390/electronics14061114






