An NTRU-Based Key Encapsulation Scheme for Underwater Acoustic Communication
Abstract
1. Introduction
- (a).
- In the key generation phase, a compact NTRU trapdoor is generated using ring sampling techniques and used as the private key.
- (b).
- Based on this, underwater acoustic channel characteristics are integrated as temporary identity information to generate the encapsulated key.
- (c).
- The traditional key encapsulation mechanism is extended by incorporating a digital signature phase.
- (d).
- Under the random oracle model, the proposed scheme was proven to achieve security against chosen ciphertext attacks, while significantly reducing the communication bandwidth requirements, making it suitable for complex underwater acoustic communication environments.
2. Preliminaries
2.1. Lattices
2.2. Gaussian Functions and Distributions on Lattices
2.3. Key Encapsulation Mechanism
2.4. Digital Signature
2.5. Hardness Assumption
3. Trapdoor Generation Algorithm on NTRU Lattices
3.1. TrapGen
| Algorithm 1 () |
| Input: |
| Output: |
|
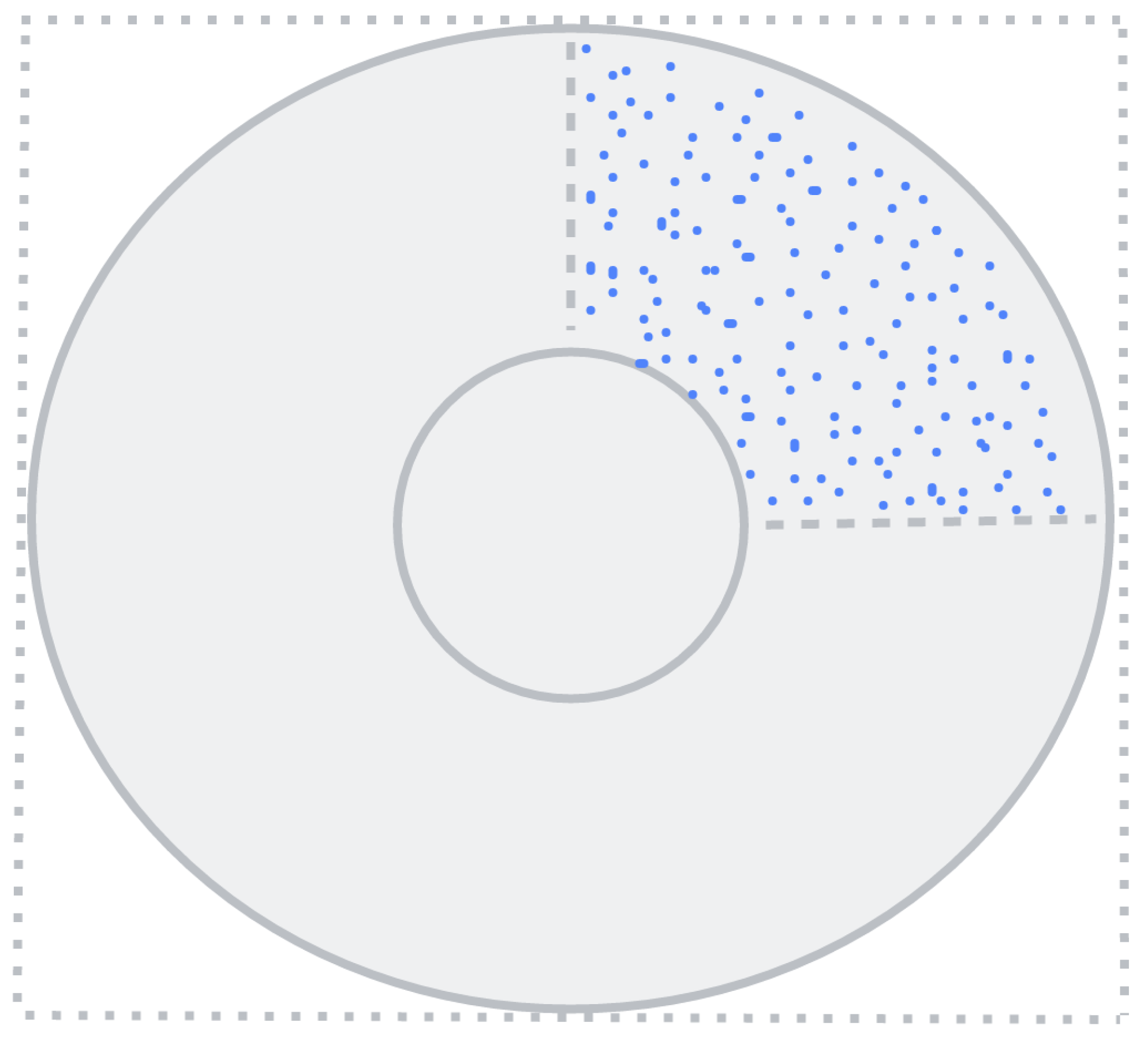
3.2. Annular NTRU Trapdoor Generation
| Algorithm 2 Ring Trapdoor Generation Algorithm |
| Input: Ring order n, modulus q, target quality coefficient and ring region , where . |
| Output: |
|
4. Syntax and Model
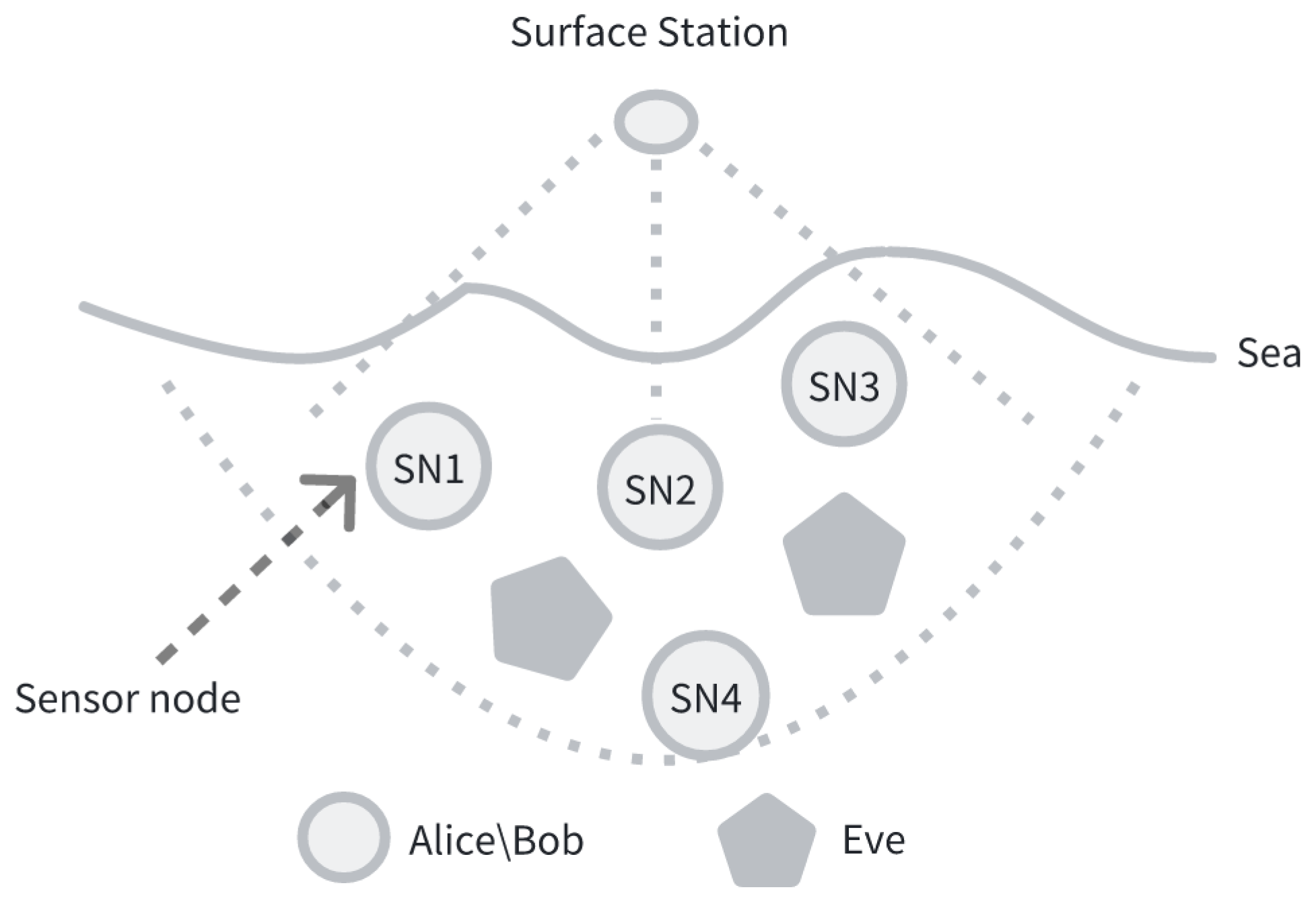
4.1. Underwater Acoustic Channel Model
4.2. Scheme Definition
4.3. Security Model
4.4. Construction of the Scheme in This Paper
4.5. Correctness Analysis
5. Security Proof
5.1. Existential Unforgeability
5.2. Confidentiality
5.3. Summary
6. Comparison and Conclusions
6.1. Comparison
6.2. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Li, Z.; Chitre, M.; Stojanovic, M. Underwater acoustic communications. Nat. Rev. Electr. Eng. 2024, 1–13. [Google Scholar] [CrossRef]
- Yang, J.; Wang, J.; Qiao, G.; Liu, S.; Ma, L.; He, P. Review of underwater acoustic communication and network technology. J. Electron. Inf. Technol. 2024, 46, 1–21. [Google Scholar]
- Wang, Z.; Liu, X.; Yang, Y.; Peng, M. Complementary Coded Identical Code Cyclic Shift Multiple Access Under Asynchronous Frequency-Selective Fading Channels. IEEE Trans. Veh. Technol. 2023, 72, 13269–13280. [Google Scholar] [CrossRef]
- Javadpour, A.; Ja’fari, F.; Taleb, T.; Zhao, Y.; Bin, Y.; Benzaïd, C. Encryption as a service for IoT: Opportunities, challenges and solutions. IEEE Internet Things J. 2023, 11, 7525–7558. [Google Scholar] [CrossRef]
- Shohrab, S. Dynamic Data Encryption with Polarized Feedback. Ph.D. Thesis, Dublin Business School, Dublin, Ireland, 2023. [Google Scholar]
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Park, J.H. Advanced lightweight encryption algorithms for IoT devices: Survey, challenges and solutions. J. Ambient. Intell. Humaniz. Comput. 2024, 15, 1625–1642. [Google Scholar] [CrossRef]
- Tomović, S.; Krivokapić, B.; Nađ, Đ.; Radusinović, I. BEKMP: A Blockchain-Enabled Key Management Protocol for Underwater Acoustic Sensor Networks. IEEE Access 2024, 12, 74108–74125. [Google Scholar] [CrossRef]
- Sood, R.; Kaur, H. A literature review on rsa, des and aes encryption algorithms. In Emerging Trends in Engineering and Management; SCRS: Delhi, India, 2023; pp. 57–63. [Google Scholar]
- Dalal, Y.M.; Supreeth, S.; Amuthabala, K.; Satheesha, T.Y.; Asha, P.N.; Somanath, S. Optimizing Security: A Comparative Analysis of RSA, ECC, and DH Algorithms. In Proceedings of the 2024 IEEE North Karnataka Subsection Flagship International Conference (NKCon), Bagalkote, India, 21–22 September 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Zhao, J. DES-Co-RSA: A Hybrid Encryption Algorithm Based on DES and RSA. In Proceedings of the 2023 IEEE 3rd International Conference on Power, Electronics and Computer Applications (ICPECA), Shenyang, China, 29–31 January 2023; pp. 846–850. [Google Scholar] [CrossRef]
- Gupta, M.; Gera, P.; Mishra, B. A Lightweight Certificateless Signcryption Scheme based on HCC for securing Underwater Wireless Sensor Networks (UWSNs). In Proceedings of the 2023 16th International Conference on Security of Information and Networks (SIN), Jaipur, India, 20–21 November 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Mujdei, C.; Wouters, L.; Karmakar, A.; Beckers, A.; Bermudo Mera, J.M.; Verbauwhede, I. Side-channel analysis of lattice-based post-quantum cryptography: Exploiting polynomial multiplication. ACM Trans. Embed. Comput. Syst. 2024, 23, 27. [Google Scholar] [CrossRef]
- Canto, A.C.; Sarker, A.; Kaur, J.; Kermani, M.M.; Azarderakhsh, R. Error detection schemes assessed on FPGA for multipliers in lattice-based key encapsulation mechanisms in post-quantum cryptography. IEEE Trans. Emerg. Top. Comput. 2022, 11, 791–797. [Google Scholar] [CrossRef]
- Kumar, M.; Pattnaik, P. Post quantum cryptography (pqc)-an overview. In Proceedings of the 2020 IEEE High Performance Extreme Computing Conference (HPEC), Waltham, MA, USA, 22–24 September 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–9. [Google Scholar]
- Nisha, F.; Lenin, J.; Saravanan, S.; Rohit, V.R.; Selvam, P.D.; Rajmohan, M. Lattice-Based Cryptography and NTRU: Quantum-Resistant Encryption Algorithms. In Proceedings of the 2024 International Conference on Emerging Systems and Intelligent Computing (ESIC), Bhubaneswar, India, 9–10 February 2024; pp. 509–514. [Google Scholar] [CrossRef]
- Kim, J.; Park, J.H. NTRU+ PKE: Efficient Public-Key Encryption Schemes from the NTRU Problem. Cryptol. ePrint Arch. 2024. Available online: https://eprint.iacr.org/2024/1282 (accessed on 16 January 2025).
- Choi, P.; Kim, D.K. Lightweight Polynomial Multiplication Accelerator for NTRU Using Shared SRAM. IEEE Trans. Circuits Syst. II Express Briefs 2023, 70, 4574–4578. [Google Scholar] [CrossRef]
- Camacho-Ruiz, E.; Martínez-Rodríguez, M.C.; Sánchez-Solano, S.; Brox, P. Accelerating the Development of NTRU Algorithm on Embedded Systems. In Proceedings of the 2020 XXXV Conference on Design of Circuits and Integrated Systems (DCIS), Segovia, Spain, 18–20 November 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Kuznetsov, A.; Lutsenko, M.; Kiian, N.; Makushenko, T.; Kuznetsova, T. Code-based key encapsulation mechanisms for post-quantum standardization. In Proceedings of the 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT), Kyiv, UKraine, 24–27 May 2018; pp. 276–281. [Google Scholar] [CrossRef]
- Lee, J.; Kim, D.; Lee, H.; Lee, Y.; Cheon, J.H. RLizard: Post-Quantum Key Encapsulation Mechanism for IoT Devices. IEEE Access 2019, 7, 2080–2091. [Google Scholar] [CrossRef]
- Bhatti, D.S.; Choi, H.; Lee, H.N. Beyond Traditional Security: A Review on Information-Theoretic Secret Key Generation at Wireless Physical Layer. Authorea Prepr. 2024. [Google Scholar] [CrossRef]
- Wu, L.; Wang, H.; Liu, K.; Zhao, L.; Xia, Y. Privacy and security trade-off in cyber-physical systems: An information theory-based framework. Int. J. Robust Nonlinear Control 2024, 34, 5110–5125. [Google Scholar] [CrossRef]
- Pan, P.; Su, Y.; Fan, R.; Yang, S. A Secret Key Generation Scheme Exploiting Spatiotemporal Acoustic Channel Characteristics for Underwater Sensor Networks. IEEE Sensors J. 2024, 24, 31188–31200. [Google Scholar] [CrossRef]
- Du, Y.; Liu, H.; Shao, Z.; Ren, Y.; Li, S.; Dai, H.; Yu, J. Secure and Controllable Secret Key Generation Through CSI Obfuscation Matrix Encapsulation. IEEE Trans. Mob. Comput. 2024, 23, 12313–12329. [Google Scholar] [CrossRef]
- Micciancio, D.; Regev, O. Lattice-based cryptography. In Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2009; pp. 147–191. [Google Scholar]
- Ducas, L.; Lyubashevsky, V.; Prest, T. Efficient identity-based encryption over NTRU lattices. In Proceedings of the Advances in Cryptology—ASIACRYPT 2014: 20th International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, 7–11 December 2014; Proceedings, Part II 20. Springer: Berlin/Heidelberg, Germany, 2014; pp. 22–41. [Google Scholar]
- Lyubashevsky, V. Lattice signatures without trapdoors. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 738–755. [Google Scholar]
- Komlo, C. A Note on Various Forking Lemmas. 2023. Available online: https://www.chelseakomlo.com/assets/content/notes/Forking-Lemma-Variants.pdf (accessed on 24 April 2023).
- Yu, H.; Hui, W. Certificateless ring signature from NTRU lattice for electronic voting. J. Inf. Secur. Appl. 2023, 75, 103496. [Google Scholar] [CrossRef]
- Watson, A.B. DCT quantization matrices visually optimized for individual images. In Proceedings of the Human Vision, Visual Processing, and Digital Display IV, San Jose, CA, USA, 31 January–5 February 1993; SPIE: Bellingham, WA, USA, 1993; Volume 1913, pp. 202–216. [Google Scholar]
- Xu, C.; Zhang, C.; Huang, Y.; Niyato, D. Random Aggregate Beamforming for Over-the-Air Federated Learning in Large-Scale Networks. IEEE Internet Things J. 2024, 11, 34325–34336. [Google Scholar] [CrossRef]
- Tang, M.; Cai, S.; Lau, V.K.N. Radix-Partition-Based Over-the-Air Aggregation and Low-Complexity State Estimation for IoT Systems Over Wireless Fading Channels. IEEE Trans. Signal Process. 2022, 70, 1464–1477. [Google Scholar] [CrossRef]
- Liu, T.; Zhao, Y.; Joshi, R.; Khalman, M.; Saleh, M.; Liu, P.J.; Liu, J. Statistical rejection sampling improves preference optimization. arXiv 2023, arXiv:2309.06657. [Google Scholar]
- Ahubele, B.; Oghenekaro, L.U. Secured electronic voting system using RSA Key encapsulation mechanism. Eur. J. Electr. Eng. Comput. Sci. 2022, 6, 81–87. [Google Scholar] [CrossRef]
- Gao, D.; Chen, H.; Chang, C.C. Plaintext aware encryption in the standard model under the linear Diffie-Hellman knowledge assumption. Int. J. Comput. Sci. Eng. 2020, 22, 270–279. [Google Scholar] [CrossRef]
- Pöppelmann, T.; Güneysu, T. Towards practical lattice-based public-key encryption on reconfigurable hardware. In Proceedings of the Selected Areas in Cryptography–SAC 2013: 20th International Conference, Burnaby, BC, Canada, 14–16 August 2013; Revised Selected Papers 20. Springer: Berlin/Heidelberg, Germany, 2014; pp. 68–85. [Google Scholar]
- Zeng, Q.; Li, Q.; Zhao, B.; Jiao, H.; Huang, Y. Hardware design and implementation of post-quantum cryptography Kyber. In Proceedings of the 2022 IEEE High Performance Extreme Computing Conference (HPEC), Waltham, MA, USA, 19–23 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
| Scheme | CCA | Replay Attack | Unforgeability |
|---|---|---|---|
| Our scheme | ✓ | ✓ | ✓ |
| Ref. [36] | × | × | × |
| Ref. [37] | ✓ | × | × |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, P.; Xu, M. An NTRU-Based Key Encapsulation Scheme for Underwater Acoustic Communication. Electronics 2025, 14, 405. https://doi.org/10.3390/electronics14030405
He P, Xu M. An NTRU-Based Key Encapsulation Scheme for Underwater Acoustic Communication. Electronics. 2025; 14(3):405. https://doi.org/10.3390/electronics14030405
Chicago/Turabian StyleHe, Peng, and Ming Xu. 2025. "An NTRU-Based Key Encapsulation Scheme for Underwater Acoustic Communication" Electronics 14, no. 3: 405. https://doi.org/10.3390/electronics14030405
APA StyleHe, P., & Xu, M. (2025). An NTRU-Based Key Encapsulation Scheme for Underwater Acoustic Communication. Electronics, 14(3), 405. https://doi.org/10.3390/electronics14030405








