Abstract
With the increasing emphasis on safeguarding maritime sovereignty and developing marine resources, the security of underwater acoustic communication has risen to a new level of importance. Given the complex environmental challenges faced by underwater acoustic channels, this paper proposes an NTRU-based key encapsulation scheme designed to ensure secure and reliable underwater data transmission, while maintaining privacy and integrity. In the public–private key pair generation phase, a ring sampling technique is employed to generate a compact NTRU trapdoor, which not only guarantees security but also effectively reduces the communication overhead. During the encapsulation phase, underwater acoustic channel characteristics during communication are introduced as temporary identity information to ensure the confidentiality and reliability of the key encapsulation mechanism. Furthermore, the traditional key encapsulation mechanism is extended by integrating a digital signature process, where the encapsulated ciphertext is signed. The use of digital signature technology verifies the authenticity and integrity of the transmitted data, ensuring that communication data remain secure and unaltered in complex underwater acoustic environments. Finally, we conduct a rigorous correctness analysis and security proofs, demonstrating that the proposed scheme achieves chosen ciphertext security, while meeting the demands of low bandwidth and limited computational capacity in underwater acoustic communication.
1. Introduction
With the growing global demand for maritime sovereignty protection and the exploitation of underwater resources, underwater acoustic communication technology has become a critical means of ocean information transmission and monitoring [1,2]. However, underwater acoustic communication faces numerous challenges, such as low bandwidth, high latency, frequency-selective fading, and the highly dynamic and complex channel environment, making the assurance of data transmission security and integrity a pressing issue [3]. In harsh underwater acoustic environments, traditional encryption mechanisms struggle to ensure the security of communication [4,5]. They have a high computational overhead, while lacking an efficient key encapsulation mechanism and being unable to resist quantum attacks. To address the security challenges of underwater acoustic communication, numerous studies have focused on two key aspects: encryption algorithms, and key management mechanisms [6,7]. Symmetric encryption algorithms, such as the Advanced Encryption Standard (AES), are widely adopted for their efficiency; however, their security relies heavily on key distribution and management, making them vulnerable to eavesdropping and man-in-the-middle attacks [8]. While symmetric encryption algorithms, such as AES, are widely adopted for their efficiency, their security depends on key distribution and management, making them vulnerable to eavesdropping and man-in-the-middle attacks; in contrast, asymmetric cryptographic algorithms, such as Rivest–Shamir–Adleman (RSA) and elliptic curve cryptography (ECC), offer higher security, but their computational complexity makes them unsuitable for resource-constrained underwater acoustic communication environments [9,10]. Meenakshi et al. [11] improved ECC and optimized it for underwater environments, significantly reducing the computational overhead. However, performance bottlenecks still exist under high-noise conditions and low signal-to-noise ratios, and this method is unable to resist quantum attacks.
Recently, post-quantum cryptography has garnered widespread attention for its ability to resist quantum computing attacks. Among these, lattice-based cryptography has emerged as a research hotspot due to its high level of security and efficiency [12,13,14]. F. Nisha et al. [15] discussed the advantages and disadvantages of NTRU encryption, NTRU signature, ring–lizard, and Kyber algorithms, providing an in-depth analysis of their performance in various application scenarios. Use of the NTRU encryption scheme helps reduce computational and storage overhead. The NTRU public key encryption scheme proposed by Jonghyun et al. [16], with its smaller key size and faster computational performance, has been proven suitable for resource-constrained communication scenarios.In 2023, Piljoo et al. [17] proposed a lightweight polynomial multiplication accelerator based on NTRU, which significantly reduced the overhead associated with key generation and transmission. Eros et al. [18] further validated the security and computational efficiency of NTRU in embedded devices, demonstrating its suitability for dynamic environments. In [19], Alexandr et al. proposed a code-based key encapsulation scheme, achieving significant progress in resisting quantum attacks. In [20], Joohee et al. proposed a post-quantum key encapsulation scheme for IoT devices, which ensures security, while reducing the time consumption for key encapsulation and decryption. Therefore, post-quantum key encapsulation schemes can help optimize computational efficiency and reduce overhead, making them suitable for resource-constrained underwater communication.
In recent years, physical layer security techniques have been proposed as an effective approach to counter eavesdropping attacks. By leveraging the random characteristics of underwater acoustic channels, such as channel state information (CSI), as a source of randomness for key generation, these techniques inherently provide information-theoretic security [21,22]. Pan et al. [23] proposed a lightweight key agreement method, which demonstrated strong robustness in complex underwater environments. Yicong et al. [24] proposed an accurate and efficient key generation method, which encapsulates the CSI with a confusion matrix using circular convolution, thereby enhancing communication accuracy and efficiency. However, such schemes lack integration with post-quantum cryptographic mechanisms and are therefore unable to resist quantum attack threats.
However, designing a key encapsulation method based on NTRU and applying it to underwater acoustic communication still faces the following challenges: (1) how to reduce the communication overhead to accommodate the bandwidth limitations of underwater acoustic channels; and (2) how to integrate underwater channel characteristics to enhance the dynamism and security of key encapsulation.
To address the aforementioned issues, this paper proposes an NTRU-based key encapsulation scheme for underwater acoustic communication. By integrating underwater channel characteristics into a post-quantum cryptographic framework, the scheme aims to achieve efficient and secure key management and data transmission. The following are the main contributions of this paper:
- (a).
- In the key generation phase, a compact NTRU trapdoor is generated using ring sampling techniques and used as the private key.
- (b).
- Based on this, underwater acoustic channel characteristics are integrated as temporary identity information to generate the encapsulated key.
- (c).
- The traditional key encapsulation mechanism is extended by incorporating a digital signature phase.
- (d).
- Under the random oracle model, the proposed scheme was proven to achieve security against chosen ciphertext attacks, while significantly reducing the communication bandwidth requirements, making it suitable for complex underwater acoustic communication environments.
The organization of this paper is as follows: Section 2 provides a brief introduction to NTRU, KEM (key encapsulation mechanism), digital signatures, and related concepts. Section 3 describes the conventional NTRU trapdoor generation algorithm and the ring sampling algorithm adopted in this paper. Section 4 introduces the model of the underwater acoustic channel and presents the proposed NTRU-based key encapsulation scheme for underwater communication. Section 5 provides a security proof under the random oracle model and compares the proposed scheme with other advanced methods. The paper concludes with Section 6, where the primary findings are recapped.
2. Preliminaries
2.1. Lattices
Lattices are a fundamental concept in both mathematics and cryptography. In cryptography, lattices represent a mathematical structure with significant applications. Below are some definitions of lattices:
Definition 1 (Lattices).
In an m-dimensional vector space , represents the set of integers. There is a set of linearly independent vectors (where ), then the lattice is defined as
Vectors form the basis for the lattice , where m is the dimension of the lattice , and n is the rank of the lattice . Before introducing the NTRU lattice, a definition of the anticirculant matrix is first given.
Lemma 1
([25]). Given an n-dimensional lattice Λ, for any , Gaussian parameter , and center , we have If , the minimum value of is at least .
is used to describe the probability at the point x, and represents a bound. Lemma 1 provides both the upper and lower bounds for the function .
Lemma 2.
For any real number and positive integer , there exists
In a Gaussian distribution, as the dimensions m and increase, the probability of drawing a vector whose norm exceeds a certain threshold rapidly becomes very small.
Definition 2 (Anti-circulant matrix).
The N-dimensional anticirculant matrix of is defined as the Toeplitz matrix provided below:
In general, an anti-circulant matrix can be denoted as , which satisfies the following addition and multiplication properties: and .
Definition 3 (NTRU Lattices).
Let be a power of 2, be a positive integer, and . Calculate . The NTRU lattice Λ can be represented as
The lattice is a full-rank lattice in , generated by the matrix . Due to the poor orthogonality of , it cannot be used as the basis for the trapdoor in the key encapsulation scheme of NTRU. Ducas et al. [26] proposed another method for generating short bases , which can generate the same lattice as .
Similarly to the NTRU lattice, we define the -ary lattice.
Definition 4 (-ary lattice).
Let , , and , satisfying . The definition is given as follows:
where is a coset of .
2.2. Gaussian Functions and Distributions on Lattices
Definition 5 (Discrete Gaussian Function).
For any and , the Gaussian function on is defined as
Lemma 3
([27]). For any vector and any positive real number α, if :
Definition 6 (Discrete Gaussian Distribution).
We can define a discrete Gaussian distribution on any lattice , centered at c with the parameter s:
When , it can be simplified as and .
2.3. Key Encapsulation Mechanism
The key encapsulation mechanism consists of three polynomial-time algorithms, denoted as . Let the security parameter be , the key space be , and the ciphertext space be . The following describes the three algorithms:
(1) Key Generation Algorithm ←():
Input the security parameter, and output a pair of public and private keys .
(2) Key Encapsulation Algorithm :
Input the public key , output the temporary encapsulated key and the corresponding ciphertext , where c .
(3) Decapsulation Algorithm :
Input the private key and the ciphertext , output the temporary encapsulated key . Here, can be ⊥, which indicates a decapsulation failure.
Definition 7 (The correctness of KEM).
The probability of key decapsulation failure is defined as
That is, if holds for any security parameter , the encapsulation scheme is considered correct. A scheme is said to satisfy indistinguishability under chosen ciphertext attack (IND-CCA) security if, for any polynomial-time adversary A, the attacker’s advantage satisfies
2.4. Digital Signature
The digital signature scheme comprises three distinct algorithms, denoted as . Let be the message space, be the signature space, and be the security parameter. Below are the definitions of the three algorithms:
(1) Key Generation Algorithm ←():
Given the security parameter , the algorithm outputs a public and private key pair .
(2) Signature Algorithm s = :
Input the message m, where , and the private key ; output the signature s, where .
(3) Verification Algorithm :
Given the public key , the message m, and the signature s, the signature is considered valid if ; otherwise, it is deemed invalid.
Definition 8 (Unforgeability of Digital Signatures).
For a digital signature scheme for any polynomial-time adversary , there exists a non-negligible function such that the following condition is satisfied:
One might conclude that the digital signature scheme exhibits robust resistance to adaptive chosen-message attacks.
Definition 9 (The confidentiality of digital signatures).
In the context of anonymous identity-based cryptography under the multi-user adaptive chosen ciphertext attack (MU-IND-CCA) security model, if no adversary can win the MU-IND-CCA game with a non-negligible advantage in polynomial time, then the digital signature scheme possesses strong secrecy.
Lemma 4
([28]). Forking Lemma. Suppose A is a probabilistic polynomial-time Turing machine that can generate a valid signature σ for a given message m and a random oracle output h with a non-negligible probability. If A is run again with the same random seed but a different random oracle, it will, with non-negligible probability, produce a second valid forgery for the same message m, corresponding to a different random oracle output , where .
2.5. Hardness Assumption
The following section introduces the related hard problems concerning the lattices and NTRU lattices involved in the proposed scheme.
Definition 10 (The R-SISq,m,β problem).
Given a random vector and a real number , the problem is to find a non-zero vector such that and where .
Definition 11 (The problem on the NTRU lattice).
Given a prime q, a real number β, and two small polynomials , let , where . The SIS problem on the NTRU lattice is to find a vector that satisfies the following two conditions: 1. , 2. .
Definition 12 (The NTRU One-Wayness Assumption).
NTRU one-way hardness refers to the difficulty of computing given the public key h and the ciphertext c.
3. Trapdoor Generation Algorithm on NTRU Lattices
3.1. TrapGen
Given a security parameter , a prime , and a Gaussian parameter , there exists a probabilistic polynomial-time (PPT) algorithm that takes as input and outputs an NTRU lattice with a trapdoor basis and a polynomial , satisfying . Let represent all invertible elements modulo q in the polynomial ring , and let denote the n-dimensional discrete Gaussian distribution with parameter . For the set D, denote as selecting f uniformly at random from D. The specific steps of the algorithm are as follows: Algorithm 1 [29].
| Algorithm 1 () |
| Input: |
| Output: |
|
3.2. Annular NTRU Trapdoor Generation
Common trapdoor generation algorithms (for example, Algorithm 1) typically obtain the desired quality polynomial pair by repeatedly sampling until a random polynomial pair has been generated. Although this method appears to be straightforward, it has shortcomings in terms of efficiency and security. In our approach, to adapt to the underwater acoustic communication environment, we propose a ring-based uniform sampling method based on a hybrid sampler, suitable for generating trapdoor bases .
Our approach embeds a quality target into the hybrid sampler and directly performs uniform sampling from quality targets that meet the conditions. Figure 1 shows the ring uniform sampling. The specific implementation is as follows: Algorithm 2.
| Algorithm 2 Ring Trapdoor Generation Algorithm |
| Input: Ring order n, modulus q, target quality coefficient and ring region , where . |
| Output: |
|
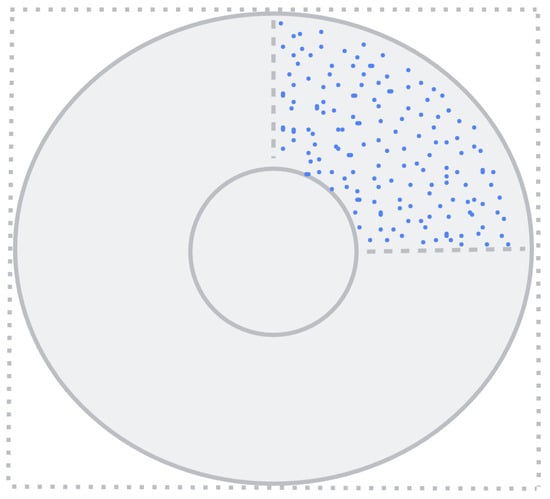
Figure 1.
Sampled uniformly in .
The process from , to is omitted after Step 7 in Algorithm 2, as it is the same as in Algorithm 1. Since the polynomials and generated using the inverse Fourier transform typically do not have integer coefficients and thus do not meet the requirements of the NTRU trapdoor, this paper effectively addresses this issue by applying a coefficient-by-coefficient rounding method [30] which maximally preserves the original properties of the polynomials.
4. Syntax and Model
4.1. Underwater Acoustic Channel Model
The over-the-air (OTA) model is commonly used to describe the process of transmitting and aggregating information through wireless channels, particularly in mobile communication and sensor networks. This model is also applicable to underwater acoustic communication. However, due to factors such as signal attenuation, propagation speed variations, and noise in the underwater environment, the characteristics of underwater acoustic communication differ from those of aerial channels. Therefore, in this paper, we reference relevant literature [31,32] and propose improvements and adaptations to the existing underwater acoustic channel model based on prior research. The following is a detailed introduction to the underwater acoustic channel model adopted in this study.
It is assumed that Alice and Bob, the two parties participating in the underwater acoustic communication, are both legitimate, while the third-party attacker (Eve) is the adversary. In the proposed NTRU-based underwater acoustic communication key encapsulation scheme, Alice is responsible for generating the temporary key, performing the key encapsulation, signing the encapsulated ciphertext, and finally transmitting the data to Bob via the underwater acoustic channel. Bob is responsible for verifying the signature and performing the decapsulation operation to ensure that the received data are legitimate and have not been tampered with. The communication model is shown in Figure 2.
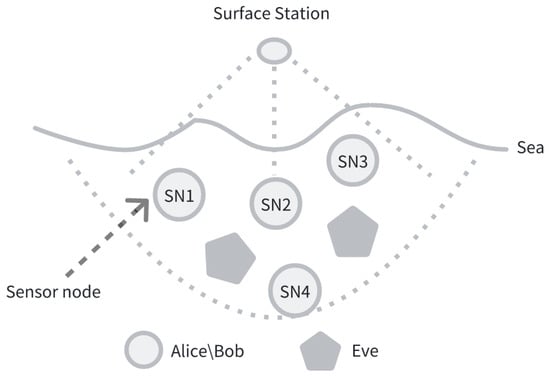
Figure 2.
The Communication Model.
The underwater acoustic channel is a complex, random, spatiotemporal, and frequency-varying channel, and its transmission quality is severely affected by multipath and Doppler effects. Due to the complexity of the shallow water environment, underwater acoustic signals undergo refraction and reflection when interacting with the seabed, sea surface, or marine organisms during transmission. As a result, the underwater acoustic signals sent by Alice do not reach Bob simultaneously, leading to multipath effects.
Let be the number of paths, be the delay of the p-th path, be the channel gain of the p-th path, and be the noise in the channel. The multipath channel can be represented as
where is the transmitted signal and is the received signal.
In underwater communication, the relative positions of Alice and Bob are typically in a state of relative motion, so the impact of the Doppler effect must be considered. Furthermore, as the underwater acoustic signals travel along different paths to the receiver, the incident angles will vary, resulting in different Doppler factors for each path. By substituting into the above equation, the multipath channel with Doppler effect can be expressed as
where is the Doppler factor.
In the proposed scheme of this paper, a joint channel model is developed for the underwater acoustic channel, which can be expressed as
Based on this, a two-dimensional Gaussian distribution is constructed, where the mean and covariance matrices represent the distribution characteristics of the multipath delay and Doppler shift, respectively. The joint distribution can be expressed as
For simplicity, we assume that the received signal undergoes a Fourier transform to obtain its frequency domain representation . Based on the joint distribution , a channel compensation matrix is constructed, where the complex compensation factor for each path can be expressed as . By calculation, the joint compensation for multipath and Doppler can be obtained as follows
In the key encapsulation process, applying the joint compensation of the complex compensation factors to the ciphertext helps improve the integrity and security of transmission over the underwater acoustic channel under the influence of multipath and Doppler effects. In our scheme, the unique characteristics of the underwater acoustic channel are leveraged to enhance the security of the encapsulation.
4.2. Scheme Definition
In this section, we will describe a key encapsulation scheme suitable for underwater acoustic secure communication.
Our scheme involves 6-tuples of algorithms: Setup, Key-Gen, Key-Encaps, Sign, Verify, and Key-Decaps.
Setup. Alice takes the security parameter as input and selects the appropriate parameters required for the system.
Key-Gen. Alice runs the trapdoor generation algorithm to output the public and private key pair.
Key-Encaps. Alice uses the private key to perform the encapsulation operation, taking into account the characteristics of the underwater acoustic channel, and outputs the encapsulated key K and ciphertext .
Sign. Alice generates a signature private key based on the characteristics of the underwater acoustic channel, signs the encapsulated ciphertext , and sends the signature and the ciphertext to Bob.
Verify. Bob uses the public key to verify the received signature .
Key-Decaps. Bob uses the private key to decapsulate the ciphertext after the signature verification is successful, and outputs the message m and the encapsulated key K.
4.3. Security Model
This section outlines the security model for our scheme, focusing primarily on two key dimensions.
Existential Unforgeability: Ensure that in the complex underwater acoustic communication environment, the legitimate receiver receives the signed ciphertext as authentic and complete, thereby ensuring that the decapsulated key K is correct and error-free.
Confidentiality: Ensure that no one, other than the legitimate recipient, can extract any meaningful information from the ciphertext and thereby break the encapsulated key K.
4.4. Construction of the Scheme in This Paper
The NTRU-based underwater acoustic communication key encapsulation scheme proposed in this paper is introduced below, denoted as UA-NTRU.
(1) Setup. Given a security parameter . Let the polynomial ring be , where n is the degree of the polynomial and q is the modulus. Choose a positive integer p such that . Let the plaintext space be , the key encapsulation space be , and the Gaussian parameter , . Let be a hash function.
(2) Key-Gen. Run Algorithm 2 to obtain , where . And obtain . The private key is , and the public key is .
(3) Key-Encaps. This step is divided into two parts: generating the encapsulated key K and the encapsulated ciphertext by combining the characteristics of the underwater acoustic channel. Alice first dynamically obtains the channel characteristics from the underwater acoustic sensor. For the sake of simplicity, it is assumed that the obtained channel characteristics are normalized and then combined into a feature vector . Use a hash function to map H to the polynomial ring: T = H.
Input message , public key . Randomly select , Compute the encapsulated key , . Randomly select , and compute , , Here, , ⌊⌉ represents the rounding function. Considering the computational efficiency of the nodes in the underwater acoustic environment, we perform the following operation on , . Where .
Output the ciphertext , and the encapsulated key is K.
(4) Sign. In this stage, the generated ciphertext is signed to produce the signature . The signing process, combined with underwater acoustic communication, follows the same procedure as described above. Run the Gaussian sampling algorithm to obtain . Where and satisfy Output the signature private key . Select polynomials . Compute . For , compute . Output the signature .
(5) Verify. Input the signature , ciphertext , and channel characteristics F. The verifier outputs “1” if and only if , where it must satisfy .
(6) Key-Decaps. After step 4, verification is passed, Bob uses the private key to perform the decryption operation on the ciphertext . Compute and . Compute . If the parsed result is , the encapsulation is successful, and output the encapsulated key K; otherwise, output ⊥.
4.5. Correctness Analysis
Let us first consider the correctness of the digital signature in our scheme. In the step Verify, it can be seen that
Therefore, we have , which satisfies the first condition for the correctness of the signature. Based on Lemmas 1–3 and the rejection sampling technique [33], it can be concluded that and with a probability of at least . Therefore, it can be satisfied that with overwhelming probability satisfies . In conclusion, it can be deduced that the digital signature scheme in our proposal satisfies correctness.
After ensuring the correctness of Steps 3–4, the verification process of the underwater acoustic communication-based key encapsulation scheme in this paper is as follows: Through , Bob can compute to recover the original message m. In our scheme, for any and the encapsulated key . Satisfy . To ensure that the key K can be correctly decapsulated, assume that the noise follows a zero-mean Gaussian distribution with a variance of , where is the norm of Bob’s private key. The following correctness condition can be derived: . It is important to note that bit loss may lead to decryption errors. However, when , this does not significantly affect the correct decapsulation of the scheme.
5. Security Proof
5.1. Existential Unforgeability
This section demonstrates that the proposed NTRU-based key encapsulation scheme for underwater acoustic communication achieves unforgeability within the random oracle framework.
Theorem 1.
Assuming that the small integer solution (R-SIS) problem on rings is hard, the NTRU-based underwater acoustic communication key encapsulation scheme proposed in this paper satisfies unforgeability in the random oracle model.
Proof.
If there exists a PPT adversary that can forge a signature in Step 3 of the scheme with a non-negligible probability , then we can construct a challenger that, by interacting with , can solve the R-SIS problem with the same non-negligible probability. The game simulation between the adversary and the challenger is as follows:
(1) The challenger takes the security parameter as input and randomly selects two hash functions and . Then, sends the system’s master private key , the master public key h, and the public parameters to the adversary .
(2) The adversary can adaptively make the following queries to the challenger in polynomial time, assuming that does not make duplicate queries.
query: maintains a list , initially empty. When the adversary sends the channel characteristic F for the query, first searches the list . If is found, returns to the adversary . Otherwise, uniformly randomly selects polynomials , computes , and stores it in . Finally, sends to the adversary .
query: When the adversary sends the channel characteristic F to the oracle for a key extraction query, searches in and sends the corresponding to the adversary .
Signature query: To obtain a signature for the ciphertext CT, the adversary sends for a signature query. Upon receiving the query, first looks up the corresponding in , then randomly selects polynomials and a polynomial . Let . Next, for , computes , obtaining the signature . Finally, stores at the corresponding position in , and sends the signature sig to the adversary .
query: When the adversary sends for an query, searches in for and sends the corresponding polynomial u to the adversary .
The adversary outputs a forged signature for with a non-negligible probability.
According to Lemma 4, outputs a new forged signature for with non-negligible probability, such that , where , so we have . According to Lemmas 1 and 2, we have , which holds with overwhelming probability. Similarly, .
Based on the preimage minimum distance property of the trapdoor function on the NTRU lattice, it is highly probable that there exists a new signing key , where the new signature differs from only in the i-th coefficient, and satisfies . If , then we have Therefore, if , it follows that . Similarly, if , the same reasoning holds, and we omit the detailed description here. Based on the above considerations, it can be concluded that holds with at least probability.
So, if it satisfies , is called the solution of the SIS problem on the NTRU lattice in this paper.
Certificate completed. □
5.2. Confidentiality
The following will prove that our proposed NTRU-based key encapsulation scheme for underwater acoustic communication is IND-CCA secure, based on the NTRU hardness assumption.
Before that, let us first discuss the indistinguishability under chosen plaintext attack (IND-CPA) security of the UA-NTRU scheme.
Theorem 2.
For every probabilistic polynomial-time adversary , one can construct a probabilistic polynomial-time adversary with a runtime similar to , such that
where is a classical adversary, and the hash function is modeled as a classical random oracle.
where is a quantum adversary, the hash function is modeled as a quantum random oracle, and denotes the depth of ’s queries to .
Proof.
Suppose there exists a probabilistic polynomial-time adversary that can win the game , with the output satisfying . We can then construct a probabilistic polynomial-time adversary that solves the NTRU one-way hardness problem. Specifically, receives the public key h and the challenge ciphertext from running in the game . The goal of adversary is to output a pair such that . Adversary takes h and as input and runs the adversary . Adversary outputs a pair , which is then used by as its output. If adversary successfully simulates the game , this means that the pair output by satisfies , i.e., adversary wins the game . Thus, it follows that adversary can successfully solve the NTRU one-way function problem with the pair as output. Conversely, if the pair output by adversary does not satisfy , then adversary , using this pair as its output, will not be able to successfully solve the NTRU one-way function problem. In conclusion, the advantage of adversary winning the game is equal to the advantage of adversary in solving the NTRU one-way function problem, i.e.,
Theorem 3.
If the adversary can break the IND-CCA security of the UA-NTRU scheme, then there exists an adversary that can break the IND-CPA security of UA-NTRU, such that
where is the number of queries to the random oracle, is the number of queries to the decapsulation algorithm and challenge queries, γ is the length of the private key, and is the entropy of . In summary, based on the NTRU hardness assumption, the NTRU-based key encapsulation scheme for underwater acoustic communication proposed in this paper is IND-CCA secure.
Certificate completed. □
5.3. Summary
In the context of underwater communication, for instance, when two underwater sensing devices need to exchange critical data (such as detection signals, positioning information, etc.), existential unforgeability ensures that these data cannot be impersonated or altered by intermediary attackers, thereby preventing erroneous decisions and potential security risks. At the same time, confidentiality ensures that the transmitted data are accessible only to authorized users, effectively protecting the privacy and sensitive information in underwater communication. The scheme proposed in this paper, through rigorous security proofs, is able to fully satisfy the aforementioned security requirements.
6. Comparison and Conclusions
6.1. Comparison
The key encapsulation mechanism is a crucial component in encryption protocols. Common examples include those based on the RSA public-key encryption algorithm [34] and the Diffie–Hellman [35] key exchange protocol. These mechanisms were designed based on the integer factorization problem and the discrete logarithm problem, respectively. With the rapid development of quantum computers, their powerful parallel computing capabilities pose significant security challenges to traditional key encapsulation mechanisms. This paper proposes an NTRU-based key encapsulation scheme for underwater acoustic communication, leveraging the algebraic structure of NTRU, which can achieve quantum-resistant security in underwater acoustic communication. The scheme offers advantages such as small storage space, low computational cost, and fulfillment of IND-CCA security. To reduce the storage space in underwater acoustic communication, this scheme uses the trapdoor basis obtained through ring sampling as the system’s private key. Water acoustic channel characteristics are incorporated into the key encapsulation process to provide authenticity to the scheme. Additionally, a short-length digital signature is introduced, ensuring the integrity of data transmission in the underwater acoustic environment, without compromising the overall computational efficiency.
In Table 1, we present a comparison of the security strengths of different schemes. In this paper, the proposed scheme incorporates underwater acoustic channel characteristics during the key encapsulation process, effectively introducing identity information, which enables the scheme to resist forgery attacks such as message replay and information reorganization. In contrast, Refs. [36,37] do not introduce relevant identity information and, therefore, cannot defend against message replay attacks. Additionally, the proposed scheme ensures unforgeability and CCA security due to the integration of a digital signature mechanism in the NTRU-based key encapsulation scheme. Ref. [36], based on the ring learning with errors (R-LWE) problem, does not satisfy CCA security and lacks unforgeability. Although Ref. [37] is also an NTRU-based key encapsulation scheme that satisfies CCA security, it lacks unforgeability.

Table 1.
Comparison of security strength.
As shown in Table 2, the private key generated by the ring sampling algorithm in this paper requires less storage space compared to [37]. Additionally, the storage space for the ciphertext is also smaller than that in [37], and the storage space for the added signature is also relatively small. Compared with [36], the proposed scheme has a slightly larger storage space for various aspects. However, Ref. [36] does not have quantum-resistant capabilities. Considering the complexity of the underwater acoustic communication environment and the need to ensure communication security, the proposed scheme is more suitable for underwater acoustic communication.

Table 2.
Comparison of storage space (unit:KB).
Table 3 presents a comparison of the time overheads between the proposed scheme and those in [36,37]. Although the proposed scheme includes an additional signature step, its time overhead is similar to that of [37] and far superior to that of [36]. Without significantly increasing the overhead, our scheme offers better security, making it well-suited for challenging underwater acoustic communication environments.

Table 3.
Comparison of time overheads (unit: s).
6.2. Conclusions
In this paper, we proposed an NTRU-based key encapsulation scheme for underwater acoustic communication. The scheme leverages a trapdoor basis generated by the ring sampling algorithm as the private key, while incorporating the characteristics of underwater acoustic channels into the key encapsulation process. Additionally, by introducing a signature step, the scheme overcomes the limitations of traditional key encapsulation mechanisms. Experimental results showed that our scheme ensures IND-CCA security, while offering reduced storage requirements and improved computational efficiency. However, in extreme underwater acoustic environments with high noise and low signal-to-noise ratios, the current scheme may still face performance bottlenecks, particularly in terms of the computational overhead during key generation and encapsulation. Future work will focus on improving the operational efficiency of the key encapsulation algorithm to meet the computational constraints of underwater communication systems. Furthermore, we will explore how to adapt the scheme for different underwater communication scenarios, to enhance its flexibility and robustness. Given the potential threats posed by quantum computing, strengthening the post-quantum resilience of the scheme and integrating it with other cryptographic mechanisms will be a key direction for future research.
Author Contributions
Conceptualization, P.H. and M.X.; Methodology, P.H. and M.X.; Writing—original draft preparation, P.H.; Writing—review and editing, P.H. and M.X.; Supervision, M.X.; Funding Acquisition, M.X. All authors have read and agreed to the published version of the manuscript.
Funding
Covert Secret Key Agreement Scheme Based on the Underwater Acoustic Dynamic Hypergraph. This work was supported by the National Natural Science Foundation of China under Grant 62172269.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Li, Z.; Chitre, M.; Stojanovic, M. Underwater acoustic communications. Nat. Rev. Electr. Eng. 2024, 1–13. [Google Scholar] [CrossRef]
- Yang, J.; Wang, J.; Qiao, G.; Liu, S.; Ma, L.; He, P. Review of underwater acoustic communication and network technology. J. Electron. Inf. Technol. 2024, 46, 1–21. [Google Scholar]
- Wang, Z.; Liu, X.; Yang, Y.; Peng, M. Complementary Coded Identical Code Cyclic Shift Multiple Access Under Asynchronous Frequency-Selective Fading Channels. IEEE Trans. Veh. Technol. 2023, 72, 13269–13280. [Google Scholar] [CrossRef]
- Javadpour, A.; Ja’fari, F.; Taleb, T.; Zhao, Y.; Bin, Y.; Benzaïd, C. Encryption as a service for IoT: Opportunities, challenges and solutions. IEEE Internet Things J. 2023, 11, 7525–7558. [Google Scholar] [CrossRef]
- Shohrab, S. Dynamic Data Encryption with Polarized Feedback. Ph.D. Thesis, Dublin Business School, Dublin, Ireland, 2023. [Google Scholar]
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Park, J.H. Advanced lightweight encryption algorithms for IoT devices: Survey, challenges and solutions. J. Ambient. Intell. Humaniz. Comput. 2024, 15, 1625–1642. [Google Scholar] [CrossRef]
- Tomović, S.; Krivokapić, B.; Nađ, Đ.; Radusinović, I. BEKMP: A Blockchain-Enabled Key Management Protocol for Underwater Acoustic Sensor Networks. IEEE Access 2024, 12, 74108–74125. [Google Scholar] [CrossRef]
- Sood, R.; Kaur, H. A literature review on rsa, des and aes encryption algorithms. In Emerging Trends in Engineering and Management; SCRS: Delhi, India, 2023; pp. 57–63. [Google Scholar]
- Dalal, Y.M.; Supreeth, S.; Amuthabala, K.; Satheesha, T.Y.; Asha, P.N.; Somanath, S. Optimizing Security: A Comparative Analysis of RSA, ECC, and DH Algorithms. In Proceedings of the 2024 IEEE North Karnataka Subsection Flagship International Conference (NKCon), Bagalkote, India, 21–22 September 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Zhao, J. DES-Co-RSA: A Hybrid Encryption Algorithm Based on DES and RSA. In Proceedings of the 2023 IEEE 3rd International Conference on Power, Electronics and Computer Applications (ICPECA), Shenyang, China, 29–31 January 2023; pp. 846–850. [Google Scholar] [CrossRef]
- Gupta, M.; Gera, P.; Mishra, B. A Lightweight Certificateless Signcryption Scheme based on HCC for securing Underwater Wireless Sensor Networks (UWSNs). In Proceedings of the 2023 16th International Conference on Security of Information and Networks (SIN), Jaipur, India, 20–21 November 2023; pp. 1–8. [Google Scholar] [CrossRef]
- Mujdei, C.; Wouters, L.; Karmakar, A.; Beckers, A.; Bermudo Mera, J.M.; Verbauwhede, I. Side-channel analysis of lattice-based post-quantum cryptography: Exploiting polynomial multiplication. ACM Trans. Embed. Comput. Syst. 2024, 23, 27. [Google Scholar] [CrossRef]
- Canto, A.C.; Sarker, A.; Kaur, J.; Kermani, M.M.; Azarderakhsh, R. Error detection schemes assessed on FPGA for multipliers in lattice-based key encapsulation mechanisms in post-quantum cryptography. IEEE Trans. Emerg. Top. Comput. 2022, 11, 791–797. [Google Scholar] [CrossRef]
- Kumar, M.; Pattnaik, P. Post quantum cryptography (pqc)-an overview. In Proceedings of the 2020 IEEE High Performance Extreme Computing Conference (HPEC), Waltham, MA, USA, 22–24 September 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–9. [Google Scholar]
- Nisha, F.; Lenin, J.; Saravanan, S.; Rohit, V.R.; Selvam, P.D.; Rajmohan, M. Lattice-Based Cryptography and NTRU: Quantum-Resistant Encryption Algorithms. In Proceedings of the 2024 International Conference on Emerging Systems and Intelligent Computing (ESIC), Bhubaneswar, India, 9–10 February 2024; pp. 509–514. [Google Scholar] [CrossRef]
- Kim, J.; Park, J.H. NTRU+ PKE: Efficient Public-Key Encryption Schemes from the NTRU Problem. Cryptol. ePrint Arch. 2024. Available online: https://eprint.iacr.org/2024/1282 (accessed on 16 January 2025).
- Choi, P.; Kim, D.K. Lightweight Polynomial Multiplication Accelerator for NTRU Using Shared SRAM. IEEE Trans. Circuits Syst. II Express Briefs 2023, 70, 4574–4578. [Google Scholar] [CrossRef]
- Camacho-Ruiz, E.; Martínez-Rodríguez, M.C.; Sánchez-Solano, S.; Brox, P. Accelerating the Development of NTRU Algorithm on Embedded Systems. In Proceedings of the 2020 XXXV Conference on Design of Circuits and Integrated Systems (DCIS), Segovia, Spain, 18–20 November 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Kuznetsov, A.; Lutsenko, M.; Kiian, N.; Makushenko, T.; Kuznetsova, T. Code-based key encapsulation mechanisms for post-quantum standardization. In Proceedings of the 2018 IEEE 9th International Conference on Dependable Systems, Services and Technologies (DESSERT), Kyiv, UKraine, 24–27 May 2018; pp. 276–281. [Google Scholar] [CrossRef]
- Lee, J.; Kim, D.; Lee, H.; Lee, Y.; Cheon, J.H. RLizard: Post-Quantum Key Encapsulation Mechanism for IoT Devices. IEEE Access 2019, 7, 2080–2091. [Google Scholar] [CrossRef]
- Bhatti, D.S.; Choi, H.; Lee, H.N. Beyond Traditional Security: A Review on Information-Theoretic Secret Key Generation at Wireless Physical Layer. Authorea Prepr. 2024. [Google Scholar] [CrossRef]
- Wu, L.; Wang, H.; Liu, K.; Zhao, L.; Xia, Y. Privacy and security trade-off in cyber-physical systems: An information theory-based framework. Int. J. Robust Nonlinear Control 2024, 34, 5110–5125. [Google Scholar] [CrossRef]
- Pan, P.; Su, Y.; Fan, R.; Yang, S. A Secret Key Generation Scheme Exploiting Spatiotemporal Acoustic Channel Characteristics for Underwater Sensor Networks. IEEE Sensors J. 2024, 24, 31188–31200. [Google Scholar] [CrossRef]
- Du, Y.; Liu, H.; Shao, Z.; Ren, Y.; Li, S.; Dai, H.; Yu, J. Secure and Controllable Secret Key Generation Through CSI Obfuscation Matrix Encapsulation. IEEE Trans. Mob. Comput. 2024, 23, 12313–12329. [Google Scholar] [CrossRef]
- Micciancio, D.; Regev, O. Lattice-based cryptography. In Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2009; pp. 147–191. [Google Scholar]
- Ducas, L.; Lyubashevsky, V.; Prest, T. Efficient identity-based encryption over NTRU lattices. In Proceedings of the Advances in Cryptology—ASIACRYPT 2014: 20th International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, 7–11 December 2014; Proceedings, Part II 20. Springer: Berlin/Heidelberg, Germany, 2014; pp. 22–41. [Google Scholar]
- Lyubashevsky, V. Lattice signatures without trapdoors. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 738–755. [Google Scholar]
- Komlo, C. A Note on Various Forking Lemmas. 2023. Available online: https://www.chelseakomlo.com/assets/content/notes/Forking-Lemma-Variants.pdf (accessed on 24 April 2023).
- Yu, H.; Hui, W. Certificateless ring signature from NTRU lattice for electronic voting. J. Inf. Secur. Appl. 2023, 75, 103496. [Google Scholar] [CrossRef]
- Watson, A.B. DCT quantization matrices visually optimized for individual images. In Proceedings of the Human Vision, Visual Processing, and Digital Display IV, San Jose, CA, USA, 31 January–5 February 1993; SPIE: Bellingham, WA, USA, 1993; Volume 1913, pp. 202–216. [Google Scholar]
- Xu, C.; Zhang, C.; Huang, Y.; Niyato, D. Random Aggregate Beamforming for Over-the-Air Federated Learning in Large-Scale Networks. IEEE Internet Things J. 2024, 11, 34325–34336. [Google Scholar] [CrossRef]
- Tang, M.; Cai, S.; Lau, V.K.N. Radix-Partition-Based Over-the-Air Aggregation and Low-Complexity State Estimation for IoT Systems Over Wireless Fading Channels. IEEE Trans. Signal Process. 2022, 70, 1464–1477. [Google Scholar] [CrossRef]
- Liu, T.; Zhao, Y.; Joshi, R.; Khalman, M.; Saleh, M.; Liu, P.J.; Liu, J. Statistical rejection sampling improves preference optimization. arXiv 2023, arXiv:2309.06657. [Google Scholar]
- Ahubele, B.; Oghenekaro, L.U. Secured electronic voting system using RSA Key encapsulation mechanism. Eur. J. Electr. Eng. Comput. Sci. 2022, 6, 81–87. [Google Scholar] [CrossRef]
- Gao, D.; Chen, H.; Chang, C.C. Plaintext aware encryption in the standard model under the linear Diffie-Hellman knowledge assumption. Int. J. Comput. Sci. Eng. 2020, 22, 270–279. [Google Scholar] [CrossRef]
- Pöppelmann, T.; Güneysu, T. Towards practical lattice-based public-key encryption on reconfigurable hardware. In Proceedings of the Selected Areas in Cryptography–SAC 2013: 20th International Conference, Burnaby, BC, Canada, 14–16 August 2013; Revised Selected Papers 20. Springer: Berlin/Heidelberg, Germany, 2014; pp. 68–85. [Google Scholar]
- Zeng, Q.; Li, Q.; Zhao, B.; Jiao, H.; Huang, Y. Hardware design and implementation of post-quantum cryptography Kyber. In Proceedings of the 2022 IEEE High Performance Extreme Computing Conference (HPEC), Waltham, MA, USA, 19–23 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).