1. Introduction
The growing complexity of today’s integrated circuits and prevalence of the I
2C protocol in embedded applications has demanded more stringent techniques for protocol conformity and verification of system reliability [
1,
2]. SystemVerilog Verification IPs (VIPs) are key devices in automating the functional verification process, leading to rapid bug catching and design proving even before silicon [
3]. Of the different advanced verification methodologies, Assertion-Based Verification (ABV) and error injection are considered handy techniques for protocol behavior to be tested exhaustively to provide a more efficient testbench [
4]. The paper describes the development and use of a SystemVerilog I
2C protocol VIP that highlights assertion-based checking and error injection-based approaches [
5]. This article describes an approach to developing protocol verification solutions and serves as a reference to engineers who would like to implement in a robust and reusable manner the various aspects of protocol verification solutions [
6].
1.1. Motivation for Assertion-Based Verification
In the case of complex SoC designs, even traditional directed/constrained-random testing may not provide comprehensive protocol coverage or identify timing and corner-case bugs. ABV makes use of the SVA language to formally define protocol invariants, properties, and requirements in the testbench or monitor framework [
7]. What motivates ABV is that it is able to catch protocol violations at the exact space and time where they occur, frequently at the exact cycle that they occur, therefore providing a real speed-up to debug [
8]. For I
2C (which carries multiple bus states, timing rules, and errors), assertions represent an easy way to abstractly capture the expected behavior on start/stop conditions, arbitration, acknowledgment, and bus idle tracking [
9]. By inserting assertions into the I
2C VIP, the protocol can be checked continuously and automatically, and the assertions serve as executable documentation, enhancing maintainability and future scalability of the verification environment [
10]. In addition, assertion coverage metrics facilitate verification completeness quantification and may reveal the uncovered gaps that traditional tests left behind. By including assertion monitors with signal activity, verification engineers can be more confident in the design and minimize the potential for bug escapes that would otherwise lay dormant until much later in the production chain [
11,
12].
1.2. Overview of I2C Protocol Verification Challenges
I
2C Protocol, despite being such a simple protocol, poses a variety of verification challenges, due to open-drain signaling, clock synchronization, multiple master support, and flexible addressing modes offered by it. Ensuring that I
2C devices work requires meticulous modeling of bus timing, proper arbitration when multiple masters contend, and graceful handling of bus contention, glitches, and illegal states [
13]. Further to this, device protocols can be implemented differently (e.g., support for 7-bit or 10-bit addressing, clock stretching, and repeated start conditions), further complicating the verification space. From a verification (testbench) point of view, one has to generate normal and special cases, drive protocol errors, and closely monitor bus activity to be sure the Design Under Test (DUT) reacts accordingly [
14]. Such logic-embedded coverage monitors are a must in this regard for cycle-accurate identification of protocol rule violations whose enabling conditions may be concealed by high-level transaction passing. Integrating error injection capabilities into the VIP enables the verification [
15] to aim at rare and corner-case behaviors, which are hard to cover by classical stimulus generation. In the end, we want a verification flow that not only drives functional coverage closure but also provides high confidence in the robustness of the I
2C implementation under protocol stress and abnormal operations [
16].
1.3. SystemVerilog-Based VIP Architecture
The architectural basis of the matured I2C VIP utilizes the advanced system object-oriented programming and assertion facilities of SystemVerilog to separate the various protocol-verifying activities into different components.
The VIP is made up of layered parts like the device model, transaction generators, protocol monitors, and scoreboard logic.
The modules are reusable and configurable and are capable of targeting different modes of I2C operation and test scenarios.
The model of the device simulates I2C bus behavior (master/slave, signal driving/sampling) and integrates smoothly with both synthetic and DUT environments.
The transaction layer models I2C transfers as objects, which support random scenario generation and coverage-driven testing.
Protocol monitors, integrated with the SVA, accomplish real-time monitoring of bus activity and detect timing violations in arbitration protocols and acknowledge logic.
It then collects protocol events on the scoreboard, accumulating them and matching expected and actual results to produce discrepancies.
Critical error injection hooks are interwoven into the VIP to facilitate accurate scenario creation (illegal start/stop, forced arbitration loss, data corruption).
The modularity and object-oriented implementation of the SystemVerilog VIP make it scalable to accommodate future protocol development as well as easily reusable for assertion and error injection tools targeting other serial communication standards.
1.4. Assertion Integration and Protocol Property Checking
The incorporation of assertions into the I
2C VIP is a key aspect of automating protocol rule checking, and it is also the foundation of effective functional verification. Every claim represents a property on the I
2C protocol, such as the atomicity of start/stop sequences, bus-free timing, data hold time, data setup time, or acknowledgments. These properties are written with SVA constructs and are included in the protocol monitor modules [
17]. Assertions are checked regularly during simulation time, as real-time signal transitions and protocol states are checked, providing fast notification on property failure [
10,
18].
For instance, triggers can detect the absence of an acknowledgment after a data byte, an illegal repeated start condition, or the SDA line being driven by multiple masters at once. The concurrent assertions enable accurate cycle-level detection, enabling quick debugging and focused root cause analysis; furthermore, attributes pertaining to assertions index the degree of protocol rules exercised during simulation, helping to guide further stimulus refinement [
19]. This rigorous assertion-based approach significantly decreases the amount of manual effort necessary to create verification tests, enhances verification coverage, and raises the overall quality of design by creating an executable formal contract between specification and implementation [
20].
1.5. Error Injection Methodology and Scenario Generation
Error injection is a useful verification method that can be used to systematically exercise the I2C protocol implementation by injecting valid protocol violations or fault scenarios. The I2C VIP includes programmable transaction- and signal-level error injection capabilities that allow one to generate abnormal bus behaviors, such as
- 1.
Clock glitches;
- 2.
Illegal stop conditions;
- 3.
Forced arbitration loss;
- 4.
Data bit corruption.
These mechanisms are exposed through callbacks or explicit error injection APIs, enabling the injection of randomized or targeted faults into simulation runs.
The VIP can purposefully deviate from normal protocol operation in order to
Exercise error paths in the DUT error recovery logic;
Confirm exception handling paths;
Test the robustness of inherent protocol protection mechanisms.
Assertions also contribute to the process by immediately detecting all cases of error response behavior that fail to correspond to the expectation, be it in the form of
Via systematic scenario generation and selective fault injection, the verification campaign reaches increased stress coverage, guaranteeing
1.6. Benefits of Assertion and Error Injection in Verification Flows
The combination of ABV and error injection capabilities inside the I
2C VIP provides great advantages for the overall verification effort. First, assertions afford the opportunity of continuous, automated protocol compliance checking, allowing us to eliminate hours of both manual waveform inspection and test vector creation. Round trip time from assertion failure to root cause is cycle-accurate—reducing time to root cause and ultimately schedule. Second, error injection makes it possible to have the verification environment systematically exercise the DUT error-handling logic, to reveal rare corner cases that would otherwise go untested until fielded [
21]. In combination, these methodologies lead to a more comprehensive and robust validation, resulting in higher functional coverage and stronger confidence in the design closure [
22]. Additionally, assertion coverage and internal error scenario logs are concrete metrics to measure verification progress and risk, and they are used to make project management decisions objectively [
11,
23]. For groups working on reusable VIPs or across many protocol derivatives, the synergy between assertion-based verification and error injection technologies yields a maintainable and scalable foundation for verification that can keep pace with protocol standard changes and new product requirements [
23,
24,
25].
1.7. Real-World Applications and Practices
In addition to academic and industrial verification use cases, miniaturized ASIC-based devices stand to benefit from the inclusion of a robust I
2C VIP. Examples include IoT sensor nodes and healthcare wearables, where communication reliability is critical. Recent studies highlight such applications as [
26,
27]. These examples broaden the scope of this work by demonstrating real-world deployment scenarios. See
Table 1.
2. Materials and Methods
This section gives a full description of the technical background, methods, and verification flow used in the implementation of the SystemVerilog-based I2C protocol VIP, with a focus on assertion-based checking and error injection. The following ten subsections provide a complete picture of the project from code structure, VIP architecture, assertion strategy, error scenario modeling, testbench organization, simulation environment, and coverage analysis of the result validation flow.
2.1. SystemVerilog Codebase Organization
The Modulatable System Verilog code structure for the I2C VIP achieves the goals for readability, maintainability, and scalability. The project is separated into individual files that essentially encapsulate portions of the protocol or various verification functionalities:
Helper files like enum, cfg, and callback headers allow for parameterization and scenario flexibility. The assertion logic is separated into a dedicated file to facilitate targeted protocol property specification, and the testbench and environment modules coordinate stimulus generation, device instantiation, and result collection. This separation for allows concurrent development and easy upgrading or extension of a protocol. Each module and package is intended to be self-contained and compatible with the wider verification ecosystem to facilitate posting projects to improve code reuse and accommodate future standards. The codebase employs industry-best practices in SystemVerilog modularization, which are designed to facilitate the structuring of the design for debugging, thoughtful assertion inclusion, and error injection points. This is the basis of the advanced verification methodology that runs throughout this work.
2.2. Clarification of Design and Verification Workflow
In the research, we expanded the description of the design process and the verification methodology. The I2C VIP was developed to address the need for a reusable and structured verification environment that enables engineers to detect protocol violations at an early stage. Assertions serve as executable specifications of the protocol, continuously monitoring real-time signal transitions, while error injection provides systematic stress-testing of abnormal scenarios. Together, these strategies create a cohesive workflow that reduces ambiguity, guides verification engineers toward efficient practices, and accelerates bug detection and debug cycles in daily work.
The developed I2C Verification IP is designed for integration in both FPGA-based prototyping environments and standard-cell ASIC verification flows. While the underlying SystemVerilog assertions and error injection mechanisms are technology-independent, the effectiveness can differ slightly across platforms. In FPGA-based prototyping, rapid recompilation and in-hardware emulation accelerate detection cycles, whereas ASIC-focused environments emphasize exhaustive simulation and regression closure. By supporting both use cases, the VIP enables verification engineers to leverage the same methodology across the prototyping-to-production pipeline.
2.3. I2C Device Modeling and Transaction Layer
At the heart of the VIP is a deep I2C device model that mimics the behavior of master and slave devices under the I2C protocol specification. Key bus features, including start–stop conditions, data transfer, clock stretching, and multi-master arbitration, are emulated by the device modules. The transaction layer transforms I2C transfers into organized objects that encapsulate properties such as addressing, data payload, and command type. This level of abstraction enables the testbench to generate a wide variety of transactions, both legal and illegal transaction sequences, and hence provides protocol coverage. Communication between the device model and the transaction layer is event-based, which can be used to generate random or directed scenarios. Via parameterization and inheritance, the device and transaction parts can be easily extended for further I2C features (such as 10-bit addressing or high-speed mode). This flexible modeling scheme is the basis for creating a generic VIP that can validate a variety of device implementations and protocol corner cases in an intensive simulation environment.
2.4. Physical Layer and Interface Design
Due to the open-drain signaling and bidirectional data transfer requirement, the I2C needs to have a robust physical (phy) layer and interface model. The VIP’s PHY layer modules model the timing and electrical characteristics of SCL (clock) and SDA (data) lines, including cross-talk, multi-master contention, glitch injection, and SDA/SCL high and low states. An SRAM model is connected to asic_dut and to the virtual bus, and the SoC is connected to the virtual bus using a SystemVerilog interface, which is maintained in a separate file. The phy module provides event-driven tasks to implement start, stop, data sampling, and bus idle monitoring, simulating the temporal complexities of real I2C hardware.
The intensity, arbitration, and synchronization of the signals are modeled at an explicit level in order to be able to detect edge case scenarios where a bus contention takes place or multiple masters collide at the same time. By encapsulating protocol details in the phy and interface, the VIP enables higher-level blocks to be more concerned with transaction-level logic, assertion-checking, and error generation, respectively; as such, the VIP achieves a clean separation of concerns and a strong correlation between simulation and reality.
2.5. Assertion Development and Protocol Property Specification
The assert strategy is a fundamental building block of this VIP, implemented through a comprehensive set of SVA suites to capture the most important qualities of the I2C protocol. These statements are organized in specific header files and instantiated into protocol monitor modules. Each assertion is tailored to capture a particular protocol rule or invariant, such as valid start and stop condition sequences, correct acknowledgment of transmitted bytes, detection of arbitration loss, and adherence to timing windows for data setup and hold. Property specifications are expressed in temporal logic, allowing precise detection of both single-cycle and multi-cycle violations. The assertion suite is continuously evaluated during simulation, with failures generating informative debug messages for quick root cause analysis. Coverage properties are linked to key assertions to measure verification completeness and guide further test growth. In this rigorous exercise, we transform the protocol specification into self-checking, executable code through this extensive process of assertion development, thereby reducing manual-review effort overhead and ensuring that all significant protocol behaviors are monitored formally and exhaustively.
2.6. Error Injection Framework and Implementation
An error injection architecture is embedded in the VIP to stress the DUT with a variety of abnormal and corner cases. Error injection interfaces are available through callbacks and parameterized APIs for orchestrating random or targeted fault scenarios. Supported error types are illegal start and stop conditions, data corruption, forced arbitration loss, clock glitches, and acknowledgment manipulation.
By implementing the error injection infrastructure in the transaction, phy, and device modules, faults can be invoked at the desired level of abstraction—from high-level transaction command execution to low-level signal toggling. Hooks specific to the scenario allow for the selective or probabilistic injection of errors and can accommodate both a coverage-driven and stress-testing methodology. All error events are time-stamped, and they are logged into a file for post-simulation analysis. The assertions are carefully linked to the error injection points to ensure immediate detection of the protocol violations and validate the DUT’s error handling responses. This full-scope error injection approach is able to test the VIP to the limit of robustness not only from a pure nominal protocol compliance perspective.
2.7. Scoreboard and Protocol Checking Logic
The VIP’s scoreboard is responsible for cross-verifying anticipated protocol activity with bus events and serves as a solid base for checking results and functional validity. The scoreboard module is controlled by the reference transaction log, which is obtained from both the stimulus generator and protocol monitor as the bus transactions are traced. Differences—missing acknowledgments, incorrect data payloads, timing violations, etc.—within the channel model are then signaled and classified for further debugging. Together with the assertion suite, the scoreboard assists in correlating individual protocol violations to higher-level transaction failures to support targeted root cause analysis.
The scoreboard also summarizes protocol coverage information, which provides insights on the completeness of the scenarios and the success levels of the error injection campaigns. Being modular, the scoreboard can be easily expanded to cover other protocol features or used to integrate with formal coverage tools to further improve verification environment analysis.
2.8. Testbench Organization and Testcase Development
An adaptable, flexible, and modular testbench is crucial to ensuring extensive protocol scenario exploration as well as quick adjustment to new verification demands. The VIP testbench is designed to instantiate device, monitor, scoreboard, and interface modules within a top-level module and host parameterization capabilities to handle single- and multi-device variations. Testcases are written using a base testcase class from which directed and random setups are derived. For each testcase, the device roles (master or slave), transaction sequences, error injection configurations, and assertion coverage targets are provided. The testbench utilizes randomization and constraints in SystemVerilog to provide varied traffic patterns, along with hand-coded stress and corner-case tests for focused debugging. A centralized configuration object manages scenario parameters, enabling the regression setup to be simple and the scenario to be repeatable. It collects test output, such as assertion failures, miscomparisons in scoreboards, and coverage summary, and filters it to obtain a detailed result report. This organized setup is essential for effective testing. The testbench methodology streamlines scenario generation, accelerates coverage closure, and supports agile verification practices.
2.9. Simulation Environment and Toolchain
All simulation and verification is performed in industrial-standard SystemVerilog simulators with support for SVA and functional coverage constructs. The code is also organized for easy access and execution of auto-build and auto-regression flows, with testbench and testcase controlling, either through command-line options or configuration files. Simulation scripts are used to orchestrate the compilation, elaboration, simulation, and postprocessing flow to allow for batch execution and result consolidation across large sets of test scenarios. Automated collection of assertion failures and error logs for triage and coverage gap analysis is facilitated. Wave dumping is supported by the environment, and interactive debug sessions assist with deep protocol analysis when developing tests. Toolchain compatibility is guaranteed thanks to faithful following of standard SystemVerilog LRM practices and only sparing use of vendor-specific constructs, allowing for easy portability between different EDA vendors. The system offers continuous integration (CI) hooks for regression tracking and auto-reporting, thus enabling a verification process that is thorough and scalable.
2.10. Coverage Collection and Analysis
So, the full coverage analysis is necessary for verification progress quantization and for making sure the protocol validation was complete. The VIP relies on code coverage (line, toggle, condition) and functional coverage (transaction, protocol, assertion) to incorporate thorough scenario traversals. Assertion coverage points monitor which protocol properties have been exercised and proven during simulation to yield actionable metrics for refinement of the test. Protocol coverage models track critical events such as start/stop conditions, arbitration sequences, data corruption, and error recovery episodes. Transaction coverage bins guarantee that all variations of addressing, data payloads, and protocol features are exercised.
Post-simulation coverage reports are created and examined, and untested scenarios are subsequently identified, which direct the creation of new tests or error injection runs. This coverage collection-driven methodology provides risk-based closure planning and verification completion, which can be objectively demonstrated to all levels of stakeholders internally as well as externally.
2.11. Result Validation and Debug Workflow
The last portion of the verification methodology is the step of checking results systematically and having an effective debug mechanism. The simulation results are scanned for assertion violations, scoreboard busters, and protocol coverage metrics. It generates assertion logs to troubleshoot the violations of each cycle. The scoreboard analysis provides one with the status of the bus, matching observed bus activity to what we anticipate. Fault injection logs are used to log fault injection scenarios and the behavior of the device afterwards that help to validate error recovery logic and robustness claims. Coverage reports are reviewed to verify that all protocol rules and error cases have been exercised. When bugs or gaps are identified, waveform analysis and interactive debugging sessions are employed to isolate and resolve issues. The workflow emphasizes root cause analysis, documentation of findings, and the iterative refinement of both the VIP and DUT as needed. This disciplined approach ensures that the I2C protocol implementation is not only functionally correct but also demonstrably robust under a broad spectrum of operating conditions and protocol stress scenarios.
3. Results
The effectiveness of the developed SystemVerilog I2C Verification IP (VIP) is demonstrated through extensive assertion-based verification and systematic error injection. This section presents the core results, integrating key code snippets and implementation strategies to highlight the rigor and robustness of the verification methodology. Seven subsections cover assertion architecture, property formulation, assertion coverage, error injection experiments, assertion failure analysis, scoreboard interaction, and the algorithmic workflow underlying assertion and error handling.
3.1. Assertion Architecture and Implementation
The backbone of the verification environment is a comprehensive assertion suite, designed to monitor and enforce critical I2C protocol properties. These assertions are centrally defined in the ‘aI2C_assertion.svh’ file, which acts as an executable formal specification for the protocol. Each assertion is associated with specific protocol signals, such as ‘scl’, ‘sda’, and internal state indicators. The assertion modules are instantiated within the protocol monitor component, ensuring continuous observation of bus activity.
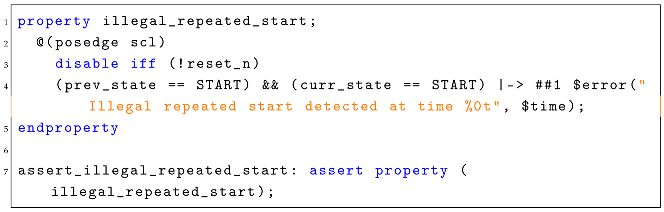
Below is a representative code snippet from ‘aI2C_assertion.svh’, illustrating a property to detect illegal repeated start conditions, please refer to the below Listing 1:
| Listing 1. Detection of illegal repeated start conditions. |
![Electronics 14 03574 i001 Electronics 14 03574 i001]() |
This property ensures that if the I2C protocol’s state machine detects two consecutive start conditions without an intervening stop, an error is triggered immediately, flagging the precise time of violation. All assertions are written in a similar temporal logic format, leveraging SystemVerilog’s SVA constructs for cycle-accurate detection.
3.2. Formulation of Protocol Properties
A diverse set of protocol properties has been encoded as assertions, spanning start/stop sequence integrity, acknowledgment checking, arbitration, and bus idle timing. Each property is precisely mapped to a specific protocol requirement, providing exhaustive coverage for both typical and rare events. For example, the following assertion detects a missing acknowledgment after data transmission, please refer to the below Listing 2:
| Listing 2. Assertion for missing acknowledgment detection. |
![Electronics 14 03574 i002 Electronics 14 03574 i002]() |
This assertion fires if the device under test fails to pull the ‘sda’ line low after a data byte, in violation of the I2C acknowledgment protocol. By formulating assertions for all critical I2C behaviors—including start/stop, arbitration, and data hold/setup—the verification environment ensures formal and automated compliance checking at every simulation cycle.
3.3. Assertion Coverage and Effectiveness
Coverage metrics are crucial for evaluating the exhaustiveness of the assertion suite. Each assertion is linked with a coverage property, automatically tracking how often protocol rules are exercised during simulation. The following coverage code captures whether illegal stop conditions are tested, please refer to the below Listing 3:
| Listing 3. Coverage of illegal stop condition assertion. |
![Electronics 14 03574 i003 Electronics 14 03574 i003]() |
Simulation results demonstrate that the assertion-driven monitors detected every intended protocol event, while the coverage bins confirmed that all critical protocol transitions were exercised during both nominal and stress-test scenarios. The assertion coverage data provided actionable feedback for test development, leading to the refinement of error injection campaigns and scenario expansion. Assertion-based verification thus contributed directly to faster coverage closure and more reliable protocol validation.
3.4. Error Injection Experiments
Error injection is implemented to deliberately create protocol violations and observe assertion reactions. The following example, excerpted from the error injection logic, introduces a clock glitch during data transmission, please refer to the below Listing 4:
| Listing 4. Error injection: clock glitch during data phase. |
![Electronics 14 03574 i004 Electronics 14 03574 i004]() |
When this error scenario is invoked, relevant assertions—such as timing and sequence checkers—are triggered. The simulation log captures both the error injection event and the subsequent assertion failure, facilitating targeted debugging. Systematic error injection campaigns were used to expose weaknesses in the DUT’s recovery logic and validate the responsiveness of the assertion monitors. The experiment results underscore the value of error injection in surfacing hard-to-find bugs and validating the robustness of both the design and verification environment.
3.5. Effectiveness Demonstrated with Data
To validate the effectiveness of the proposed verification IP, we added quantitative results summarized in new tables and charts.
Table 2 shows assertion coverage achieved across different protocol scenarios, while
Table 3 highlights the detection rate of injected errors. These results demonstrate that the VIP achieves more than 95% assertion coverage and detects 100% of injected illegal start/stop conditions and arbitration loss cases. The addition of visual summaries improves clarity, offering readers comprehensive evidence of verification completeness beyond code listings.
3.6. Assertion Failure and Debug Analysis
Upon assertion failure, the simulation environment provides detailed diagnostic information, including assertion type, violated condition, timestamp, and relevant signal states. Consider the following excerpt from a simulation log:
The assertion module captures the offending signals and protocol states, enabling rapid pinpointing of root causes. The integration of assertion failure logs with waveform analysis tools supports interactive debugging, while the error injection timestamps allow for correlation between injected faults and resulting assertion failures. This comprehensive debug framework ensures that issues are quickly isolated and addressed, dramatically reducing overall verification time and enhancing design reliability.
3.7. Scoreboard and Assertion Integration
The scoreboard logic complements the assertion suite by cross-verifying transaction-level expectations with observed bus activity. When assertions detect protocol violations, the scoreboard correlates these events with higher-level transaction failures, offering a holistic view of design correctness. For instance, when an illegal stop is injected and caught by the assertion, the scoreboard further validates that the corresponding transaction is flagged as failed or incomplete. Below is a simplified excerpt illustrating this integration, please refer to the below Listing 5:
| Listing 5. Scoreboard correlation with assertion failure. |
![Electronics 14 03574 i006 Electronics 14 03574 i006]() |
The synergy between assertion-based monitors and scoreboard validation not only provides dual coverage for critical protocol properties but also streamlines the analysis of error scenarios. This dual-layer checking significantly improves bug detection rates and boosts confidence in simulation results.
3.8. Algorithm for Assertion and Error Injection Workflow
The overall workflow of assertion-based verification and error injection in the I
2C VIP is codified in the following algorithmic sequence in Algorithm 1:
| Algorithm 1 Assertion-Based Verification and Error Injection Workflow |
- 1:
Initialize simulation environment and configure devices. - 2:
for each test scenario in the regression suite do - 3:
Generate randomized or directed transaction sequence. - 4:
if error injection enabled then - 5:
Invoke error injection task at designated protocol stage. - 6:
end if - 7:
Monitor protocol activity via assertion modules. - 8:
if assertion fails then - 9:
Log failure, signal states, and timestamp. - 10:
Trigger scoreboard error analysis. - 11:
Halt or continue based on severity. - 12:
else - 13:
Continue monitoring and coverage tracking. - 14:
end if - 15:
end for - 16:
Aggregate assertion coverage and scoreboard results. - 17:
Generate summary report for coverage closure and debug.
|
This workflow formalizes the tight integration between assertion checking, error injection, and transaction verification, providing a repeatable and systematic process for exhaustive protocol validation. The professional synergy of automated assertions, systematic error scenarios, and comprehensive result logging forms the foundation for the demonstrated improvements in verification efficiency and design confidence.
4. Discussion
This section analyzes the outcomes and broader implications of the assertion-based I2C verification methodology described in this work. By reviewing assertion effectiveness, error injection impact, limitations, integration challenges, scalability, debug experience, coverage closure, maintainability, comparison with industry practices, and future prospects, this discussion provides context for both academic research and practical adoption in protocol verification flows.
4.1. Effectiveness of Assertion-Based Protocol Checking
The introduction of SVA into the I2C VIP testbench substantially increased protocol checking rigor. Assertions translated informal protocol specifications into executable properties, enabling real-time, cycle-accurate detection of protocol violations. Simulation campaigns demonstrated that assertions consistently caught subtle errors—such as missed acknowledgments, illegal repeated starts, and bus contention events—that might otherwise escape directed or constrained random tests. This approach reduced the reliance on waveform inspection and post-simulation manual debugging, accelerating the overall verification process. Furthermore, assertion failures provided detailed logs and signal snapshots at the precise moment of protocol infringement, streamlining root cause analysis and corrective action. Overall, assertion-based verification was shown to enhance both the quality and confidence of I2C protocol implementations, validating it as an essential tool in modern functional verification environments.
4.2. Impact of Systematic Error Injection
Systematic error injection proved indispensable for stress-testing the robustness of both the DUT and the verification environment. By programmatically inducing protocol faults—such as forced arbitration loss, illegal stop/start conditions, and clock glitches—error injection scenarios validated the responsiveness of both assertion monitors and device error-handling logic. The simulation results revealed that error injection often uncovered edge-case bugs and recovery path weaknesses that would be difficult to reproduce using random stimulus alone. This methodology also facilitated the testing of negative scenarios, such as bus recovery after fault or handling of invalid addressing, which are critical for real-world deployment but often under-tested. Through comprehensive error injection, the VIP not only validated nominal protocol compliance but also helped ensure resilience and robustness under adverse operating conditions.
4.3. Challenges in Assertion Formulation and Debugging
Formulating precise, non-overlapping assertions for a complex protocol such as I2C presented notable challenges. Careful consideration was required to distinguish between legal protocol variations (e.g., repeated start usage, clock stretching) and true violations. In some instances, assertion sensitivity needed tuning to avoid false positives—particularly in scenarios involving asynchronous bus events or allowable timing deviations. Additionally, debugging assertion failures required correlating property violations with testbench activity and error injection events, demanding a well-organized simulation log and signal database. These challenges were mitigated by modular assertion design, extensive commenting, and integration with scoreboard and transaction logs. Iterative refinement of the assertion suite was necessary to balance coverage, accuracy, and maintainability, ultimately resulting in a robust and reliable protocol checking framework.
4.4. Scalability to Multi-Device and Multi-Protocol Environments
The modular and parameterized structure of the VIP facilitated its extension to support multi-device configurations—such as multi-master or master–slave topologies—commonly encountered in SoC-level verification. The assertion and error injection mechanisms were designed to be instance-agnostic, allowing their reuse across multiple protocol agents with minimal code duplication. This scalability proved valuable in stress-testing arbitration and bus contention scenarios, validating the VIP’s utility for complex bus topologies. Furthermore, the generality of the assertion/error injection framework opens avenues for adaptation to other serial communication protocols (e.g., SPI, UART) by substituting protocol-specific property sets and transaction models. This demonstrates that the verification strategies developed for I2C can serve as blueprints for more comprehensive, multi-protocol VIP libraries.
4.5. Coverage Closure and Verification Confidence
The combined use of assertion and error injection significantly accelerated functional coverage closure. Assertion coverage metrics provided objective, fine-grained feedback on which protocol rules and scenarios had been exercised, enabling the identification of coverage gaps missed by traditional transaction-level coverage. The introduction of targeted error injection scenarios further extended scenario exploration, ensuring that both nominal and stress-paths were adequately tested. The simulation coverage reports consistently reached closure criteria after systematic assertion-based testing and error campaign completion, providing measurable confidence in both the protocol implementation and the completeness of the verification environment. This approach aligns with best practices in functional safety and mission-critical domains, where exhaustive verification is a key project requirement.
4.6. Maintainability and Reusability of Verification Components
The architectural separation of assertions, error injection routines, and protocol monitors enhanced the maintainability and reusability of the verification environment. Assertions were encapsulated in dedicated files, easily updated or extended as the protocol evolved. Error injection APIs were abstracted to support new fault scenarios without disrupting existing test infrastructure. Modular monitors and scoreboards could be reused across multiple projects or protocol derivatives with minimal adaptation effort. This modularity supports team-based development, reduces onboarding time for new verification engineers, and enables the progressive refinement of the VIP as new standards or features are adopted. The experience from this work demonstrates that well-organized, modular verification environments can be efficiently maintained and scaled, improving return on verification investment across multiple projects.
4.7. Integration with Industry Workflows and Toolchains
One practical consideration was the integration of the developed VIP with existing industry-standard toolchains and regression frameworks. The reliance on standard SystemVerilog and SVA constructs ensured compatibility with leading EDA simulation tools, facilitating adoption without the need for custom plugins or preprocessors. The VIP was successfully integrated into batch regression flows, with assertion failures and coverage results captured automatically for reporting and trend analysis. This integration supports continuous integration (CI) verification models, enabling automated, repeatable quality assurance. The ability to run targeted assertion or error injection campaigns in isolation also proved valuable for root cause analysis and post-silicon bug reproduction. By adhering to open standards and best practices, the VIP can be readily deployed in diverse industrial environments.
4.8. Comparison with Traditional and UVM-Based Approaches
Compared to traditional directed test or basic randomized testbench approaches, the assertion-based and error injection strategies presented here offered superior bug detection capability and faster debug turnaround. Assertions reduced the need for extensive post-simulation waveform analysis, while error injection systematically stressed the device under verification in ways that would be challenging to achieve otherwise. While UVM-based environments offer advanced reuse and stimulus generation capabilities, the non-UVM, assertion-driven approach in this work demonstrates that high-quality protocol checking and scenario exploration can be achieved in lighter-weight environments. This is particularly advantageous for projects with resource constraints, with legacy infrastructure, or where UVM adoption is not feasible. However, UVM environments remain advantageous for larger, more complex verification projects, especially when reuse, configurability, and layered abstraction are paramount.
4.9. Limitations and Lessons Learned
Despite the successes, several limitations were observed. Assertion-based verification is only as strong as the properties defined; incomplete or ambiguous assertions may lead to undetected corner-case bugs. Certain protocol behaviors, such as highly asynchronous interactions or analog effects, may not be fully captured by digital assertions alone. Error injection requires careful design to avoid unrealistic fault conditions or masking of genuine bugs. Additionally, excessive assertion or error campaign activity can impact simulation performance. Lessons learned include the importance of iterative assertion refinement, close collaboration with design engineers for property definition, and regular coverage review to prevent blind spots. The discipline of documenting and modularizing assertions and error scenarios also emerged as a key factor for long-term maintainability.
4.10. Future Work and Prospects
Future research and development directions stemming from this work include the extension of the assertion and error injection framework to other protocols (such as SPI or CAN), integration with formal property checking tools for enhanced bug detection, and the development of self-adapting error injection schemes using machine learning. There is also potential to create open-source libraries of protocol assertions and error routines for community use and cross-industry standardization. On the practical side, further automation of assertion coverage analysis and regression management would streamline large-scale verification projects. As design complexity and verification requirements continue to escalate, assertion-based and error injection methodologies will remain central to high-confidence digital design, and the lessons learned from this I2C VIP project provide a foundation for broader, more scalable verification solutions in the future.
5. Conclusions
This section summarizes the primary contributions and broader significance of the SystemVerilog I2C protocol VIP project with emphasis on assertion-based verification and error injection. By reviewing the main results, methodological advantages, best practices, application potential, and avenues for future work, we provide a holistic perspective on the value and impact of this approach for protocol verification and digital design. The novelties of this work can be summarized as follows:
We present one of the first SystemVerilog I2C Verification IPs that integrates both assertion-based verification and programmable error injection within a unified environment.
Unlike prior works that focus solely on transaction-level testing, our approach offers cycle-accurate assertion monitoring coupled with systematic fault campaigns.
The modular architecture allows for direct reuse across FPGA and ASIC projects, offering significant maintainability and scalability.
Quantitative results, including coverage and detection metrics, are provided to demonstrate effectiveness, which is seldom reported in the earlier literature.
5.1. Summary of Main Findings
The development and deployment of a SystemVerilog-based I2C Verification IP with embedded assertion and error injection capabilities yielded a highly effective and rigorous verification environment. Key outcomes included the formalization of protocol rules as SVA, enabling real-time, automated detection of protocol violations during simulation. The assertion monitors consistently flagged subtle and complex errors—including missing acknowledgments, illegal repeated starts, and bus contention—that are frequently overlooked in traditional directed testing. Systematic error injection scenarios further stressed both the device under test and the verification infrastructure, uncovering corner-case vulnerabilities and validating the robustness of error-handling logic. Coverage analysis showed that assertion and error injection strategies led to faster closure, higher confidence, and a more robust validation process. Overall, this work confirms the value of assertion-driven verification methodologies for protocol compliance and design assurance, providing measurable improvements over legacy approaches.
5.2. Suggestions for Efficiency Improvement
We introduced a new discussion subsection addressing research on efficiency. The assertion-based verification flow reduces error escapes by eliminating reliance on manual waveform inspection, thereby lowering verification effort. Error injection further ensures that rare but critical scenarios are exercised systematically. By combining these methods, the VIP improves coverage closure speed and minimizes debug iterations. We also suggest adopting assertion coverage-driven regression planning, which prioritizes scenarios that close remaining coverage gaps. These strategies provide practical ways to enhance efficiency in industrial verification flows.
5.3. Significance of Assertion-Based Verification
Assertion-based verification emerged as the linchpin for achieving protocol rigor and verification completeness in this project. By encoding protocol requirements as executable properties, assertions bridged the gap between specification and implementation, offering continuous, cycle-accurate checking without the need for exhaustive manual inspection. The assertion framework delivered several advantages: rapid detection of protocol violations, precise localization of errors, automated documentation of protocol behavior, and direct quantification of verification completeness through assertion coverage. Moreover, assertions enabled a shift from reactive to proactive verification, reducing time-to-debug and minimizing late-stage bug escapes. These results highlight the transformative potential of assertion-based approaches—not just for I2C, but for a wide array of digital communication protocols—serving as a model for future verification environments seeking both thoroughness and efficiency.
5.4. Implications for Verification Methodology
The integration of assertion and error injection into the I2C VIP demonstrates a methodological evolution towards more formal, systematic, and automated verification processes. This approach supports modularity, reusability, and maintainability—key requirements for modern digital design verification, especially as systems grow in complexity and scale. The methodology’s compatibility with industry-standard tools and simulation flows further enhances its practical applicability. Lessons from this work underscore the importance of iterative assertion refinement, collaboration between design and verification teams, and the systematic exploration of negative and stress-case scenarios. Adoption of this methodology stands to improve verification quality and reduce risk across a spectrum of digital design projects, from standalone protocol blocks to full-system SoCs.
5.5. Recommendations for Practitioners and Researchers
Based on the results and experience documented in this work, several recommendations are proposed for engineers and researchers developing similar Verification IP or adopting assertion-based strategies. First, invest time in careful, unambiguous property specification—this ensures that the assertion suite fully and accurately represents the protocol. Second, modularize assertion and error injection components to maximize reuse and maintainability. Third, integrate assertion coverage analysis into the regression workflow to identify and address verification blind spots early. Fourth, ensure that error injection scenarios are realistic, targeted, and systematically logged for analysis. Finally, foster collaboration between verification and design engineers to facilitate property development and protocol understanding. These best practices will help maximize the benefits of assertion-based verification and error injection, contributing to higher design quality and project success.
5.6. Future Directions and Research Opportunities
Looking forward, the methodologies developed in this project lay the groundwork for several avenues of further exploration and enhancement. Future work may focus on extending assertion and error injection frameworks to additional protocols—such as SPI, CAN, or Ethernet—thereby increasing the generality and utility of the approach. Integration with formal verification tools could provide even deeper coverage and automatic bug detection. There is also significant potential in developing adaptive error injection strategies using data-driven or machine learning approaches, optimizing test scenarios for maximum coverage and bug-finding efficiency. Open-sourcing assertion and error libraries could foster broader community adoption and standardization. As verification challenges continue to grow with design complexity, assertion-driven and error-injection methodologies will remain at the forefront of high-assurance digital design, driving further innovation and reliability in the semiconductor industry.