1. Introduction
An SDS contains a high level of software that enables electrical components to be highly controllable, secure, and self-healing [
1]. This software communicates with the control system, protection system, information technology components, operational technology components, advanced metering infrastructure, supervisory control and data acquisition (SCADA) components, measurement devices, distributed generation, and main electrical components. As the distribution system contains a lot of software, the probability of being exposed to hacking is high. CAs are one of the most important challenges that modern smart distribution systems face [
2].
There are three directions in research related to CAs in SDSs. The first direction is concerned with how CAs affect SDSs. CAs can affect electrical components and protocol devices. The electrical components include generators, electric vehicles, transmission lines, transformers, and automatic controlled switches [
3,
4,
5,
6,
7]. The protocol components include advanced metering systems, server infrastructure, routers, SCADA systems, wireless communication signals, and Internet of Things (IoT) technologies. Cyber-attacks in such systems often involve injecting false data to generate incorrect commands [
8,
9,
10,
11].
The second direction of research discusses the impact of CAs on SDSs, which can lead to the complete or partial shutdown of electricity distribution. Smart distribution systems are designed to optimize power delivery. A CA could disable optimization algorithms, leading to inefficient load balancing and overloading certain parts of the grid, while others remain partly loaded, with potential to cause local failures. Attackers could gain remote access to an SDS to manipulate equipment settings, disable monitoring, or make unauthorized changes. This could result in malfunctioning, the destruction of equipment, or the theft of data [
12,
13,
14,
15].
The third direction discusses how to block a chain of CAs in an SDS. Advanced firewalls are used to monitor and filter network traffic, protecting the grid from unauthorized access and potential threats. Systems are set up to detect and stop harmful or suspicious activity on a network. Segmenting the network into smaller, isolated parts can prevent the harm from spreading. For example, separating operational technology (OT) networks from information technology (IT) networks can localize the attacked area. Strong encryption is used to protect data transition between smart meters, substations, control centers, and other devices. This ensures that sensitive data cannot be intercepted or altered by attackers. The regular back-up of system configurations, critical data, and software is performed [
16,
17,
18,
19,
20].
The current paper presents, for the first time, a new research direction toward the supply recovery of the OOSL following a CA hitting an SDS. To the authors’ knowledge, this may be the first work that addresses the supply recovery of the OOSL of an SDS exposed to a CA hitting the ACS, because the related research in the literature is limited.
In 2015, the power distribution network of Western Ukraine was cyber-attacked, causing 225 thousand households to be out of service for two hours [
21]. In 2016, the power distribution network of Kyiv was attacked by hackers, leaving end-users without ES for six hours [
22]. In 2014, a CA hacked South Korean power generation networks to interrupt the ES of 50 thousand end-users for 3 h [
23]. In 2017, a CA was directed against Saudi Arabian power transmission systems, causing a supply interruption for 12 h [
24]. In 2003, a blackout occurred in the United States and Canada due to large CAs causing a delusional fault in the utility systems, so the protection systems took incorrect actions [
25].
The occurrence of CAs in SDSs hinders the self-healing of SDSs. The supply recovery of the OOSL following a CA is the responsibility of the recovery algorithm [
26]. The difference between a fault and a CA imposed on an SDS is that a fault causes a faulty load and OOSL but the CA leaves only the OOSL [
26].
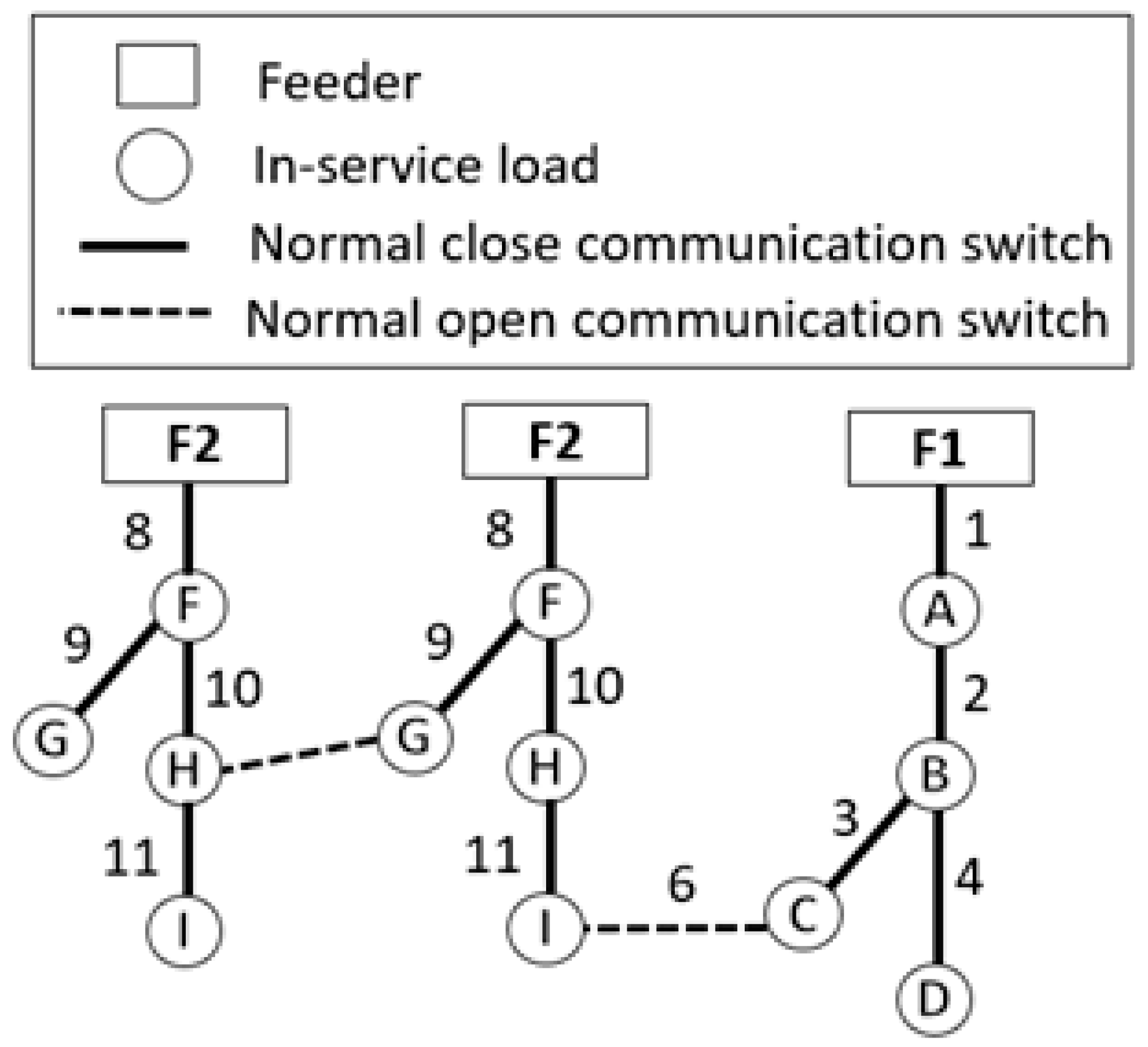
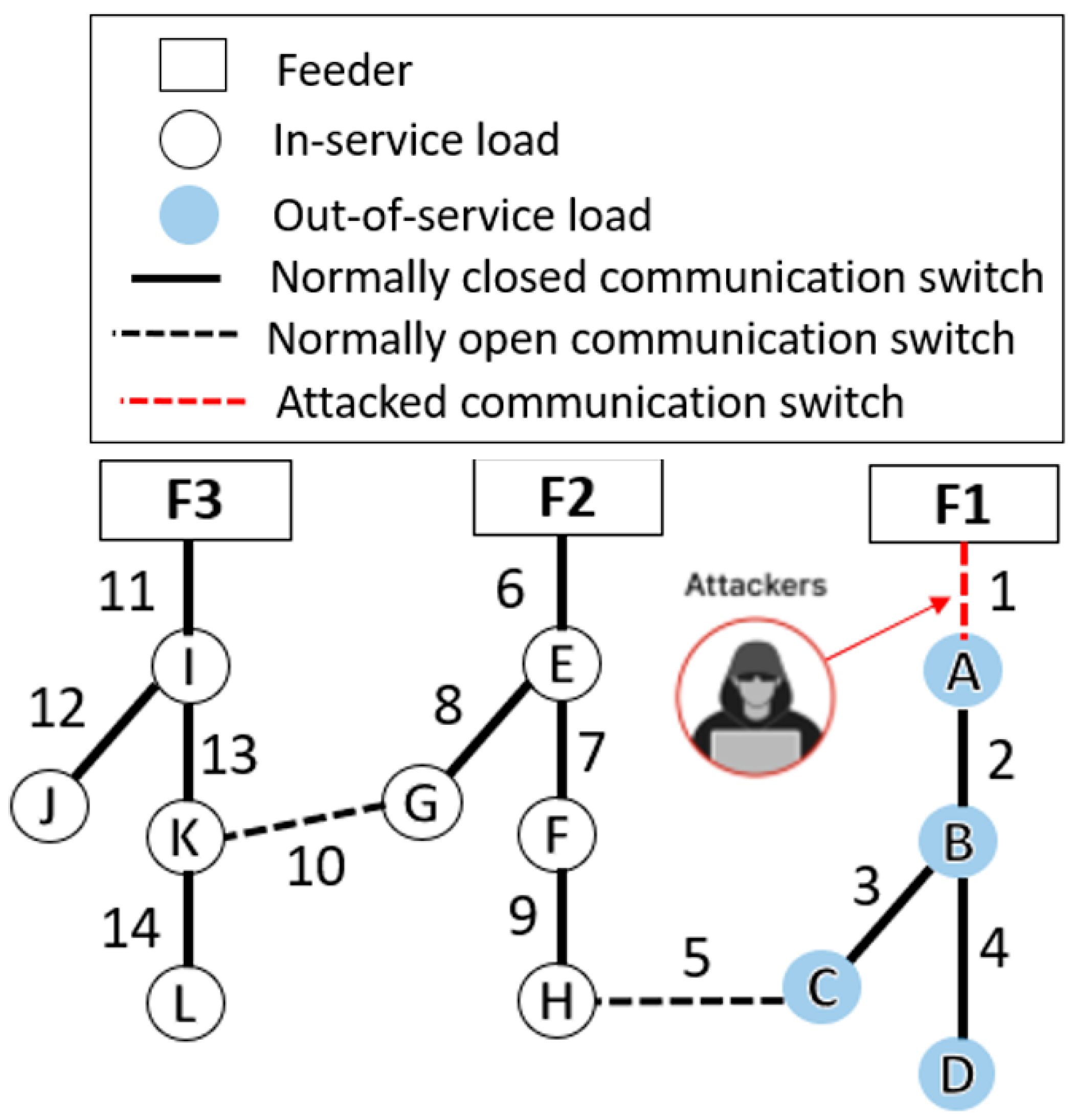
Figure 1 shows a 15-bus SDS with three electric supply feeders. A CA hits the SDS at ACS No. 1, causing the downstream loads from A through D to be OOSLs; see
Figure 2. The objective of the proposed algorithm is to restore the ES for the OOSL without breaking the EL.
The proposed algorithm ultimately prevents hackers from achieving their goal to turn off the electrical distribution systems. The proposed algorithm adds to the software of the smart grid in rendering it more automated, secure, and self-healing. The proposed algorithm increases the resilience of distribution networks in exposure to cyber-wars, such as the one that occurred in 2025 when Pakistani hackers launched a CA to target Indian power systems. The proposed algorithm can be implemented in the control centers or intelligent electronic devices of the smart distribution system or in the resilience modules in the energy management system.
The reliability and resilience of a 39-bus and IEEE 30-bus system was enhanced by 22% [
27] after experiencing a CA by enabling the system to recover from the threat. The number of maintenance personnel was increased after the occurrence of a CA to recover the ES for the OOSL [
28]. The ability of the SDS to withstand a CA was enhanced by using a large number of electric vehicles as distributed generators to feed the OOSL after the occurrence of a CA [
29]. A part of the outage area was restored after experiencing a CA by adding DG resources to support the smart distribution system against CAs [
30]. An optimized algorithm based on mixed-integer linear programming was proposed to handle load interruptions following a CA. This algorithm was based on the philosophy of first fail first repair [
31].
The originality and novelty of this paper are represented as follows:
- (i).
A novel algorithm is proposed for the first time to recover the ES for the OOSL after the occurrence of a CA on an ACS in the SDS, regardless of whether the CA occurs on a single or multiple ACSs.
- (ii).
The proposed algorithm takes into consideration the EL regarding (a) the maximum feeder current, (b) the voltage limits of each node, (c) the load priority, (d) the radiality maintenance of the SDS, and (d) the instruction sequence of the ACS, as well as minimizing their number and (f) achieving the minimum total system power loss.
- (iii).
The proposed algorithm shows better performance irrespective of the (a) number of OOSLs, (b) system size, (c) operation with or without DGs, and (d) number of simultaneous CAs.
- (iv).
The proposed algorithm shows better performance according to (a) the time of electric service recovery, (b) the ability to achieve self-healing, and (c) testing under single and simultaneous CAs.
The rest of the paper is organized as follows.
Section 2 addressees the proposed algorithm.
Section 3 contains the results obtained on applying the proposed algorithm to a 70-bus SDS with four electric supply feeders exposed to CAs.
Section 4 contains the conclusions.
2. Proposed Algorithm
The novelty and originality of the proposed algorithm is based on achieving the self-healing goal after the occurrence of a single or simultaneous CAs hitting the ACS in the SDS, without breaking seven ELs. In this context, the goal of the proposed recovery algorithm is to guarantee the continuity of the ES to the OOSL following exposure to a CA as early as possible, without breaking the ELs, which are as follows.
Electric limitation 1 (EL1): This limitation is concerned with the maximum branch current and node voltage limits. It is forbidden to transfer loads in the maneuvering process to a branch if it becomes overloaded or the voltage limit is exceeded. The overloading causes an outage for all loads connected to the overloaded branch, without recovering the OOSL.
Electric limitation 2 (EL2): The proposed algorithm should guarantee that the system is radial after the maneuvering process (MP).
Electric limitation 3 (EL3): The proposed algorithm should take into consideration the load priority. For this reason, the recovery algorithm should first recover the OOSL with the highest priority index before those with lower priority.
Electric limitation 4 (EL4): The proposed algorithm should minimize the total system power loss by performing system reconfiguration.
Electric limitation 5 (EL5): The proposed algorithm should minimize the number of commanded ACSs when recovering the OOSL.
Electric limitation 6 (EL6): The proposed algorithm should take into consideration the sequence of the commanded ACSs.
Electric limitation 7 (EL7): The proposed algorithm should restore the OOSL upon the occurrence of simultaneous CAs. Multiple cyber-attacks can simultaneously target the same number of automatic communication switches. This means that each cyber-attack is responsible for changing the state of a single switch from closed to open, thereby disconnecting all downstream loads from the power supply. In other words, each CA hits only one automatic switch.
The proposed algorithm is based on three sequential steps as follows.
Step 1: This step is responsible for defining the data of the SDS to serve the proposed algorithm, regardless of the system size of the SDS, with/without DGs. This points to two advantages of the proposed algorithm: (a) independence from the system size and (b) independence from the DGs. It is worth mentioning that the proposed algorithm is independent of the complexity of the CAs because the implementation of the proposed algorithm occurs after the CA. The data should be defined for the proposed algorithm in matrix form, as shown in
Figure 3. This matrix consists of three rows, and the number of columns is equal to the number of ACSs in the SDS. Each column consists of the switch connecting the upstream node and the downstream node. The switch is defined by its name and its status, e.g., C represents a closed status and O represents an open status.
Figure 3 provides a representation of the 15-bus SDS that is shown in
Figure 1 in matrix form, serving as data input for the proposed algorithm. For example, the first column represents a normally closed switch, No. 1, linking upstream node F1 to downstream node A. The second column represents a normally closed switch, No. 2, linking upstream node A to downstream node B.
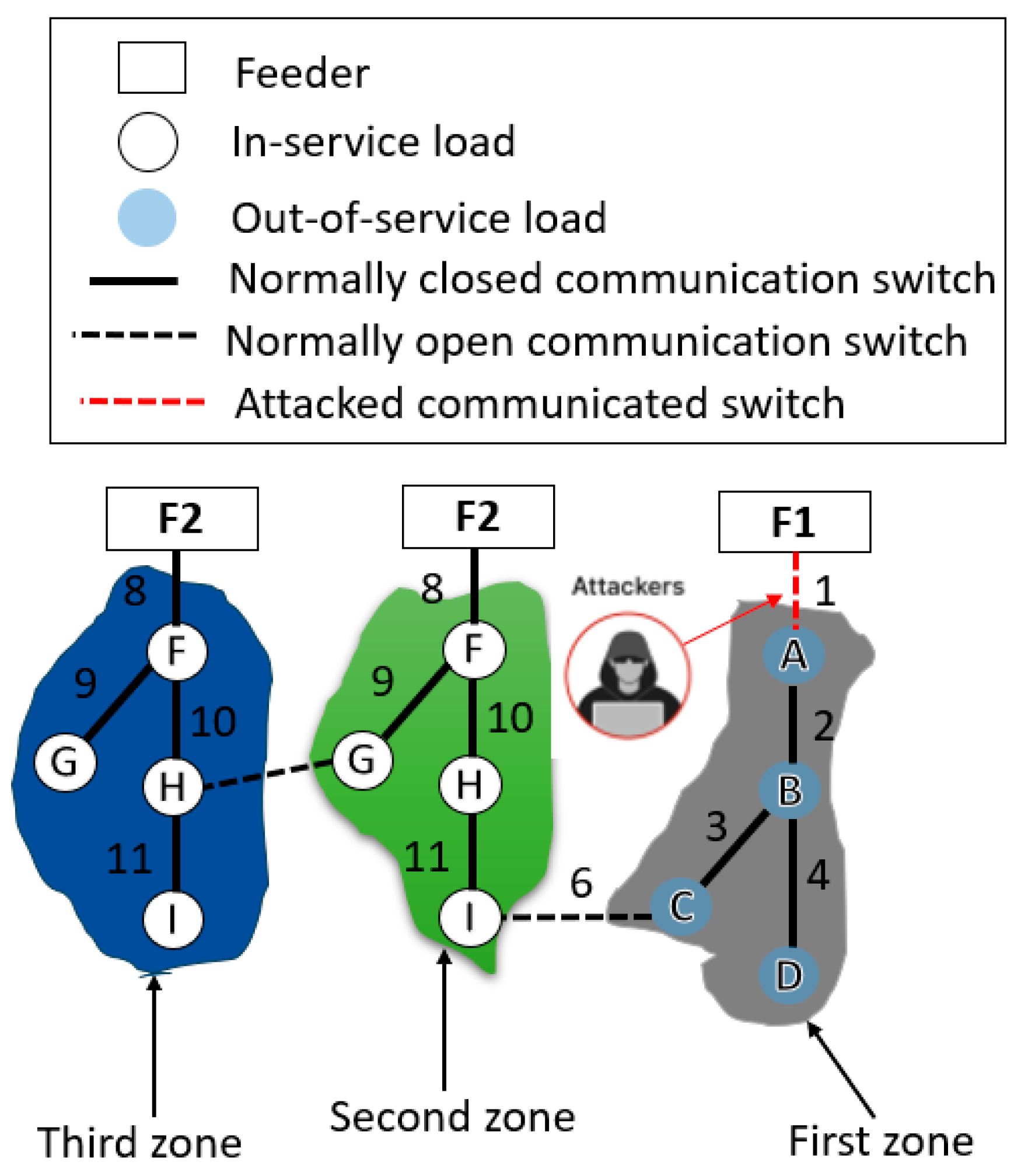
Step 2: This step is responsible for dividing the SDS into three zones after the occurrence of a CA as follows.
Step 2.1: “The attacked zone” includes the OOSL zone, which includes all downstream OOSLs, as sown in
Figure 4.
Step 2.2: “The primary neighbor zone” accommodates loads that link directly to the attacked zone only through a normally open ACS, as shown in
Figure 4. This normally open ACS is responsible for performing the first maneuvering process for automatic load transfer from the attacked zone to the primary neighbor zone.
Step 2.3: “The secondary neighbor zone” accommodates the loads that link the secondary neighbor zone through a normally open ACS (
Figure 4) to perform the second maneuvering process, which is represented by redistributing the loads among the primary and secondary neighbor zones after breaking the EL related to the maximum feeder current in the first maneuvering process.
Step 3: This step is responsible for generating one feasible solution among several ones as follows.
Step 3.1: If there is more than one maneuvering process, the proposed algorithm performs the maneuvering process that feeds the highest-priority loads.
Step 3.2: The proposed algorithm arranges the ACS to feed the largest load first.
Step 3.3: If the proposed algorithm generates more than one feasible solution, the algorithm chooses the solution that achieves the following:
- (i).
The minimum number of ACSs;
- (ii).
The minimum power loss as estimated by a load flow study.
The steps of the proposed algorithm are described in Algorithm 1.
| Algorithm 1: The steps of the proposed algorithm |
![Electronics 14 02641 i001]() |
3. Results and Discussion
The proposed algorithm is based on achieving self-healing after the occurrence of a single or simultaneous CAs hitting the ACS in the SDS, without breaking seven ELs.
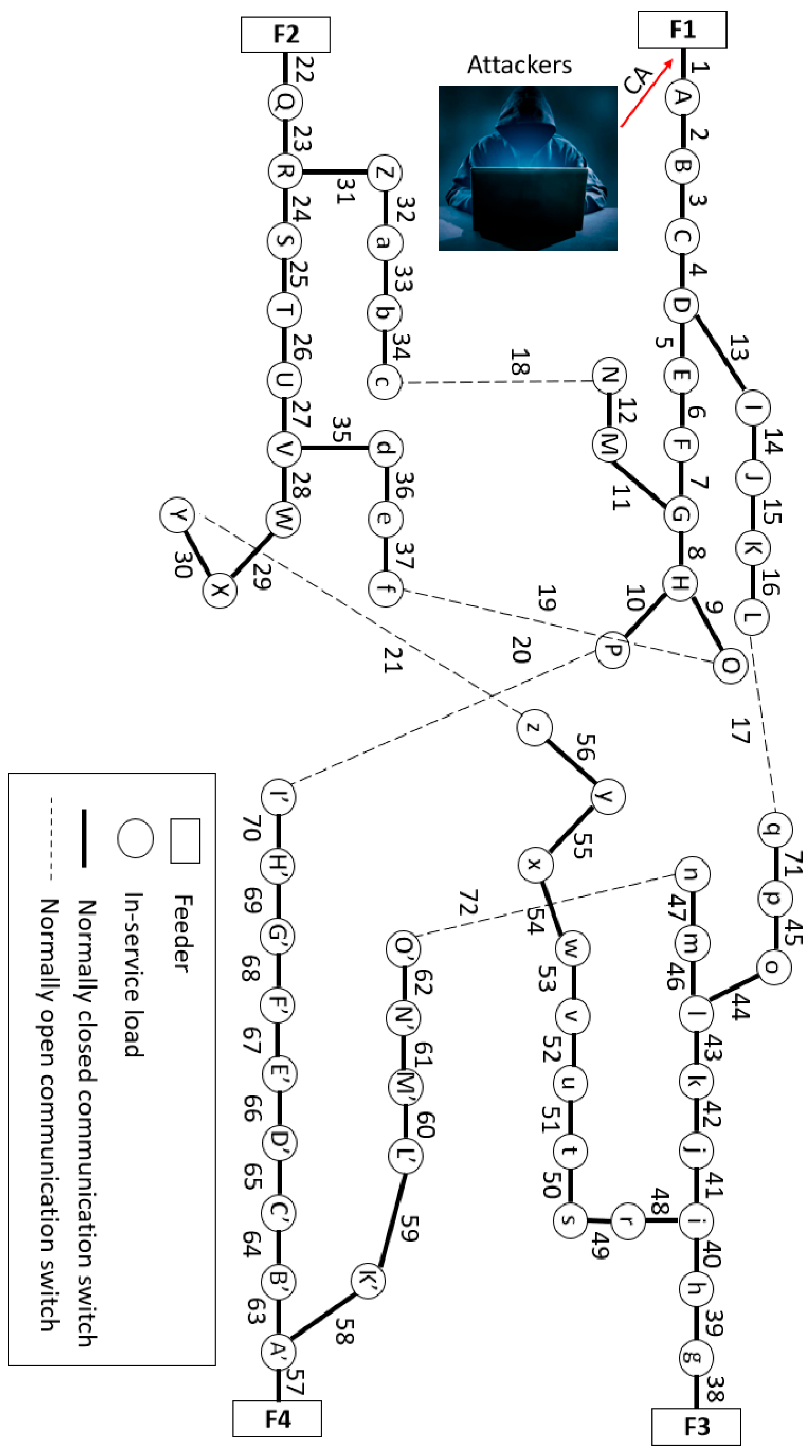
Figure 5 shows the SDS used for the testing of the proposed algorithm. This system consists of a 70-bus setup with four electric supply feeders. In power engineering terminology, tie and sectionalize switches are adopted. However, the terminology used here refers to these switches as normally open communication and normally closed communication switches, respectively. The circle represents the load, the solid line represents a normally closed ACS, and the dashed line represents a normally open ACS, while the rectangle represents the feeder. There is a priority index assigned to each load, i.e., high, medium, and low. It is worth mentioning that the efficiency of the proposed algorithm following the occurrence of a CA does not change according to the priority index of the load.
The performance of the proposed algorithm is evaluated as follows:
The recovery efficiency is equal to the ratio of the number of successful cases to the number of all possible cases.
The recovery time represents the time from the occurrence of the CA until the time of recovery of the OOSLs.
The following seven electric limitations (ELs) are satisfied:
3.1 EL1 addresses the maximum branch current and node voltage limits.
3.2 EL2 guarantees the maintenance of system radiality.
3.3 EL3 considers the load priority.
3.4 EL4 aims at minimizing the total system power loss.
3.5 EL5 aims at minimizing the number of commanded ACSs.
3.6 EL6 considers the sequence of the commanded ACSs.
3.7 EL7 restores OOSLs with the occurrence of simultaneous CAs.
3.1. Electric Service Recovery in SDS Following Exposure to Single CA
The number of possible cases of a single CA is equal to 66.
Table 1 shows the performance of the proposed algorithm under all possible cases of a single CA. The proposed algorithm achieves supply recovery for all OOSLs with efficiency of 100% after the occurrence of a CA on a single ACS, without breaking the ELs. For example, consider a single CA occurring at ACS No. 1, which results in disconnecting load nodes from A through P. The proposed algorithm generates feasible outputs in the sequence
,
,
,
,
, which results in supply recovery for all OOSLs in 194 ms without breaking the ELs.
There are many infeasible solutions that the proposed algorithm does not generate. Among the infeasible solutions is , which breaks the EL related to the overloading of feeder F3, with the subsequent outage of its loads and without supply recovery of the OOSL from A through P. The second infeasible solution is which breaks the EL related to the overloading of feeder F2, with a subsequent outage for its loads and without supply recovery of the OOSL from A through P. The third infeasible solution is , which breaks the EL related to the overloading of feeder F4, with a subsequent outage for its loads and without supply recovery of the OOSL from A through P. The fourth infeasible solution is , , ,, which leads to the breakage of the EL related to this sequence of ACSs. The fifth infeasible solution is , , ,, which breaks the EL related to minimizing the number of ACSs.
The proposed algorithm succeeds in recovering the OOSL in the SDS following exposure to a single CA for all 66 possible cases, with efficiency of 100%—see
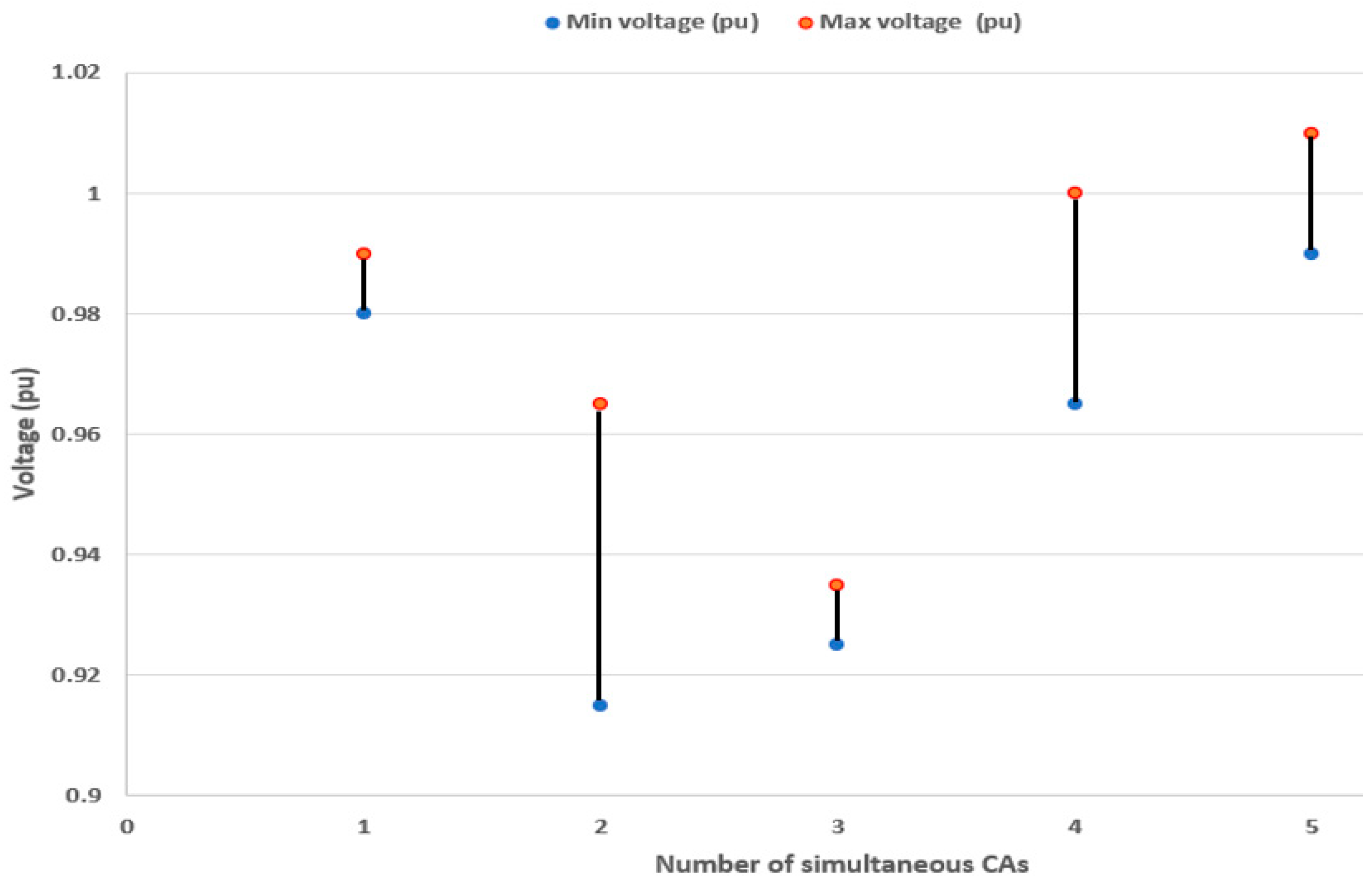
Table 2. The electric supply restoration time for each possible solution for a single CA lies within the range of 190–199 ms. The limit of the node voltage when applying the proposed algorithm following exposure to a single CA lies within the range of 0.98–0.99 pu—see
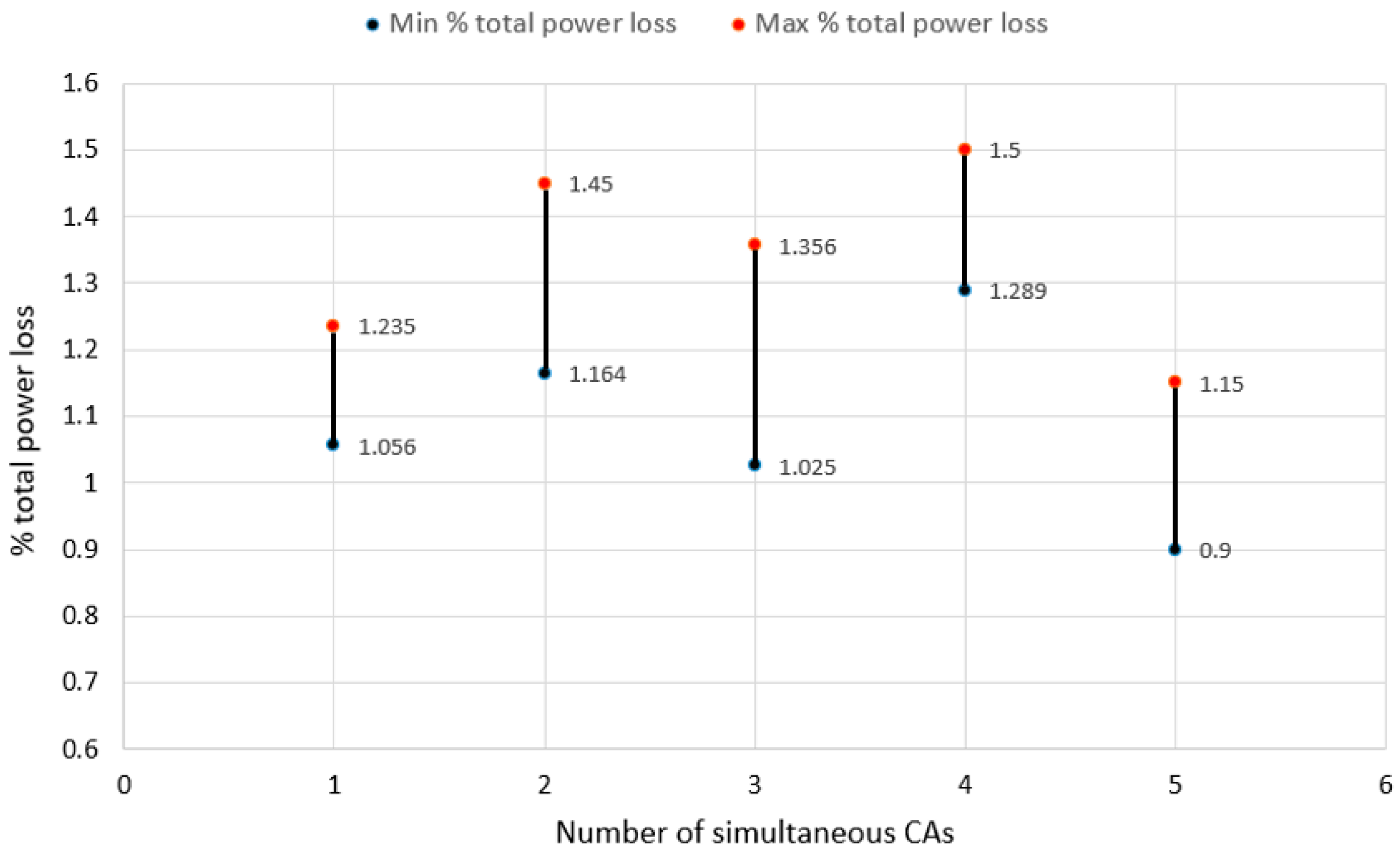
Figure 6. The total system power loss after applying the proposed algorithm following exposure to a single CA lies within the range of 1.056–1.235%. Such power loss is much smaller than that in a classical 70-bus SDS with four electric supply feeders [
32]—see
Figure 7.
It is worth mentioning that the cyber-attack will not hit switches 17 through 21 as these represent tie switches in the system, which are usually open ones. If the CA hits the tie switch to be closed, the system automatically opens a sectionalized switch to maintain the radiality of the system without intervention with the proposed algorithm.
3.2. Electric Service Recovery in SDS Following Exposure to Two Simultaneous CAs
For two simultaneous CAs, the number of possible cases is equal to 2145.
Table 3 shows examples of the performance of the proposed algorithm when the SDS is exposed to two simultaneous CAs. The proposed algorithm achieves self-healing under all possible cases of exposure to two simultaneous CAs. The supply recovery time for each possible solution under two simultaneous CAs lies within the range of 190–199 ms. For two simultaneous CAs occurring at ACSs No. 1 and 32, the load nodes from A through P and from node a through node c are disconnected. The proposed algorithm generates a feasible output in the sequence
,
,
,
,
,
,
,
which results in the supply recovery of all OOSLs in 197 ms, without breaking the ELs.
The proposed algorithm succeeds in recovering the OOSL in the SDS following exposure to two simultaneous CAs in all 2145 cases, with efficiency of 100%—see
Table 2. Applying the proposed algorithm with exposure to two simultaneous CAs results in node voltages in the range of 0.915–0.965 pu—see
Figure 6—and total system power losses within the range of 1.164–1.45%. Such power loss is much smaller than that in a classical 70-bus SDS with four electric supply feeders [
32]—see
Figure 7.
3.3. Electric Service Recovery in SDS Following Exposure to Three Simultaneous CAs
For three simultaneous CAs, the number of possible cases is equal to 45,760.
Table 4 shows examples of the performance of the proposed algorithm when the SDS is exposed to three simultaneous CAs. The proposed algorithm achieves efficiency equal to 97.6% under all possible cases of exposure to three simultaneous CAs. The supply recovery time for each possible case of three simultaneous CAs lies in the range of 190–199 ms. For three simultaneous CAs occurring at ACSs No. 35, 54, and 44, the load nodes from d through f, from x through z, and from o through q are disconnected. The proposed algorithm generates a feasible output in the sequence
,
,
which results in the supply recovery of all OOSLs in 197 ms, without breaking the ELs.
The proposed algorithm succeeds in recovering the OOSL in the SDS following exposure to three simultaneous CAs in 44,662 cases among the total of 45,760, with efficiency of 97.6%—see
Table 2. Applying the proposed algorithm with exposure to three simultaneous CAs results in node voltages in the range of 0.925–0.935 pu—see
Figure 6—and total system power losses within the range of 1.025–1.356%, which is much smaller than that in a classical 70-bus SDS with four electric supply feeders [
32]—see
Figure 7.
3.4. Electric Service Recovery in SDS Following Exposure to Four Simultaneous CAs
For four simultaneous CAs, the number of possible cases is equal to 720,720.
Table 5 shows examples of the performance of the proposed algorithm when the SDS is exposed to four simultaneous CAs. The proposed algorithm achieves efficiency equal to 97.1% under all possible cases of exposure to four simultaneous CAs. The supply recovery time for each possible case of four simultaneous CAs lies the range 190–199 ms. For four simultaneous CAs occurring at ACSs No. 9, 11, 45, and 54, the load nodes from M through O, from p through q, and from x through z are disconnected. The proposed algorithm generates a feasible output in the sequence
,
,
,
which results in the supply recovery of all OOSLs in 190 ms, without breaking the ELs.
The proposed algorithm succeeds in recovering the OOSL in the SDS following exposure to four simultaneous CAs in 699,819 cases among the total of 720,720, with efficiency of 97.1%—see
Table 2. The limit of the node voltage after applying the proposed algorithm under exposure to four simultaneous CAs lies within the range of 0.965–1.0 pu—see
Figure 6—with a range of 1.289-1.5% for the total system power loss. Such power loss is much smaller than that in a classical 70-bus SDS with four electric supply feeders [
32]—see
Figure 7.
3.5. Electric Service Recovery in SDS Following Exposure to Five Simultaneous CAs
For five simultaneous CAs, the number of possible cases is equal to 8,936,928.
Table 6 shows examples of the performance of the proposed algorithm when the SDS is exposed to five simultaneous CAs. The proposed algorithm achieves efficiency equal to 96.4% under all possible cases of exposure to five simultaneous CAs. The supply recovery time for each possible case of five simultaneous CAs lies in the range 190–199 ms. For five simultaneous CAs occurring at ACSs No. 32, 28, 62, 44, and 11, the load nodes from W through Y, from o through q, from M through N, and f and N are disconnected. The proposed algorithm generates a feasible output in the sequence
,
,
,
,
which results in the supply recovery of all OOSLs in 199 ms, without breaking the ELs.
The proposed algorithm succeeds in recovering the OOSL in the SDS following exposure to five simultaneous CAs in 8,615,199 cases among the total of 8,936,928, with efficiency of 96.4%—see
Table 2. The limit of the node voltage after applying the proposed algorithm under exposure to five simultaneous CAs lies within the range 0.99–1.01 pu—see
Figure 6—with a range of 0.9-1.15% for the total system power loss. Such power loss is much smaller than that in a classical 70-bus SDS with four electric supply feeders [
32]—see
Figure 7.
Table 2 summarizes the efficiency of the proposed algorithm in recovering the OOSL in the SDS following exposure to a single and simultaneous CAs.
Table 7 shows a comparison between the proposed algorithm and other algorithms reported in the literature.
4. Conclusions
An algorithm is proposed to recover the electric supply for OOSLs in the SDS after exposure to a CA resulting in interruptions in the INSL. The proposed algorithm is based on three steps. The first step is based on building the SDS in matrix form. The second step is based on classifying the SDS into three zones: the attacked zone and the primary and secondary neighbor zones. The third step is based on obtaining five types of MP to recover the OOSL without breaking the ELs.
The proposed algorithm takes into consideration the ELs related to the maximum branch current, the nodes’ voltage, the load priority, the radiality maintenance of the SDS, the minimum total system power loss, and the instruction sequence of ACSs.
The proposed algorithm achieved self-healing after exposure to a single or double CAs without breaking the ELs when tested under a 70-bus SDS with four electric supply feeders.
The proposed algorithm succeeded in recovering the OOSLs in the investigated 70-bus SDS following exposure to a single CA in all 66 possible case studies, as well as in 2145 cases of exposure to two simultaneous CAs.
The proposed algorithm succeeded in recovering the OOSLs in the investigated 70-bus SDS following exposure to three simultaneous CAs in 44,662 cases out of 45,760, as well as in 699,819 cases out of 720,720 and 8,615,199 cases out of 8,936,928 of exposure to four and five simultaneous CAs, respectively.
The proposed algorithm achieved the recovery of the electric supply for three, four, and five ACSs exposed to CAs at efficiency values of 97.6%, 97.1%, and 96.4%, respectively, without breaking the ELs in the investigated 70-bus SDS.
The mathematical model, computational requirements, and integration of the proposed algorithm with the hardware components represent a research gap for future work. Implementing a defense algorithm against cyber-threats is also a task for future work.
In future research, the application of virtual bids [
33] and mobile energy storage [
34] in this context is also worth investigating.
Recommendations for future researchers include the integration of modern technology like artificial intelligence, machine learning, big data, and data mining within this research topic.
Challenges regarding merging the restoration algorithm with distribution power systems that contain hybrid switches, i.e., “manual and automatic” switches, should also be taken into consideration.