Security First, Safety Next: The Next-Generation Embedded Sensors for Autonomous Vehicles
Abstract
1. Introduction
2. Automotive Sensors: The Big Picture
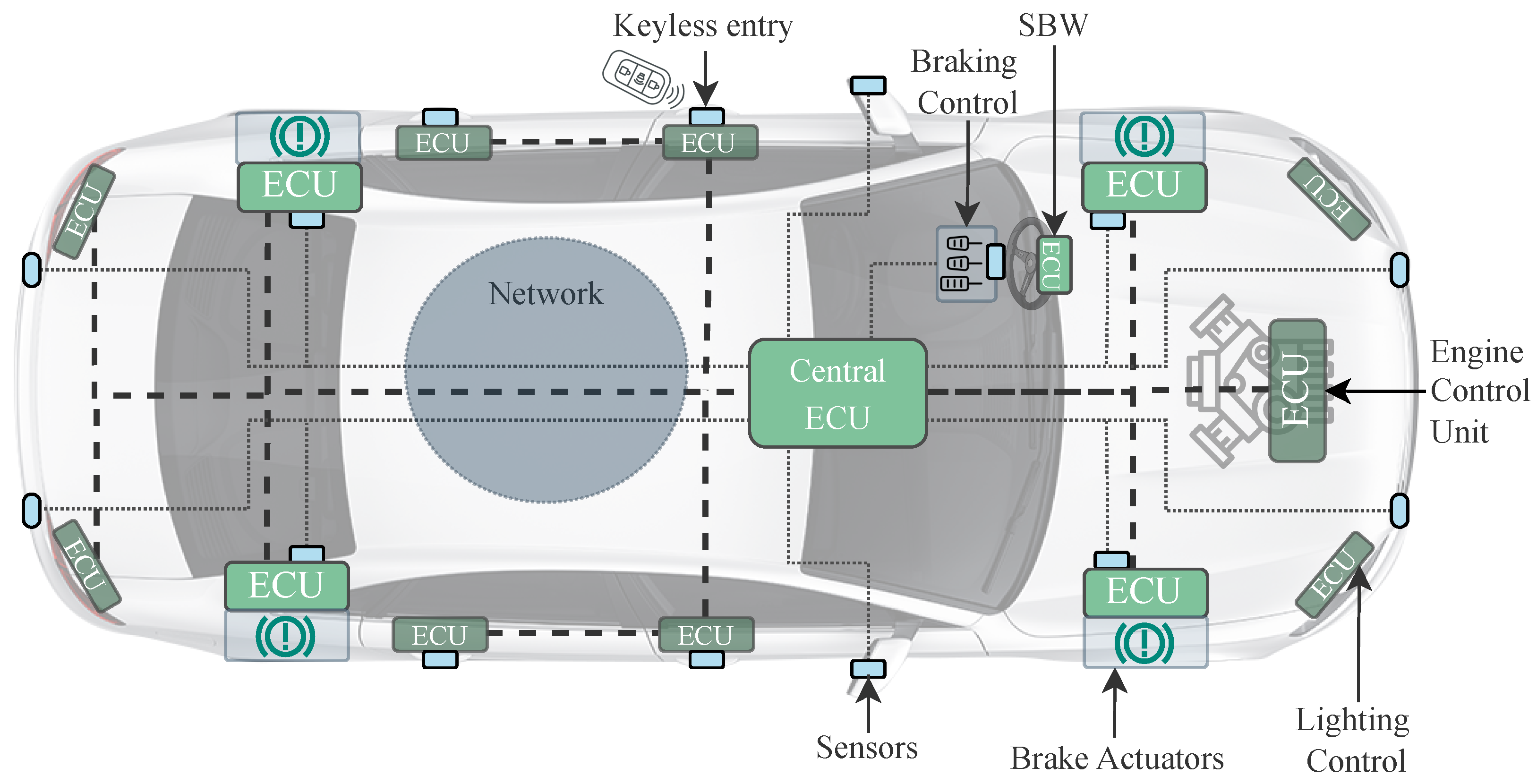
2.1. Automotive Architecture
- Powertrain: ECUs in this domain are responsible for controlling components that generate the power necessary for the car to move. They usually handle tasks regarding to engine control, e.g, throttle-by-wire, transmission control, battery management. A failure in one of these subsystems can represent a severe safety risk such as unintentional acceleration in the car. As such, systems associated with this domain typically have ASIL-D certification [24,25].
- Chassis: ECUs in this domain oversee the control of several chassis components, including wheels, brakes, and suspension. Tasks within this domain encompass critical functionalities such as anti-lock braking system (ABS), brake-by-wire (BBW), and SBW. A malfunction in any of these subsystems can pose a significant safety risk, such as the vehicle failing to respond to steering commands. Consequently, systems within this domain typically boast ASIL-D certification to ensure their reliability and safety [26,27].
- Body: This subsystem is notably diverse, encompassing a wide range of functionalities. It includes passive safety tasks like airbag deployment and seat-belt monitoring, as well as comfort and convenience features such as central locking systems, heating, and parking assistance. The ASIL classifications within this domain vary significantly depending on the specific subsystem. For instance, airbag systems typically boast ASIL-D certification [28], whereas heating systems may only necessitate ASIL-B certification.
- Infotainment and telematics: Subsystems within this domain manage a variety of features, including audio control, video, smart display, Global Positioning System (GPS) navigation, and wireless communication. Typically, these subsystems only require ASIL certifications up to level B [29]. Precise vehicle positioning and environmental perception are critical system requirements for autonomous driving. Recent advancements in ADAS have increased the need for high-accuracy absolute positioning [30], typically achieved through global navigation satellite systems (GNSS), as well as relative positioning between vehicles using vision or LiDAR sensors [31]. Given their role in real-time decision making, these systems may require certification up to ASIL-D [32]. Moreover, ensuring the integrity and authenticity of spatiotemporal reference data is increasingly important to protect against spoofing, jamming, or malicious manipulation of localization inputs.
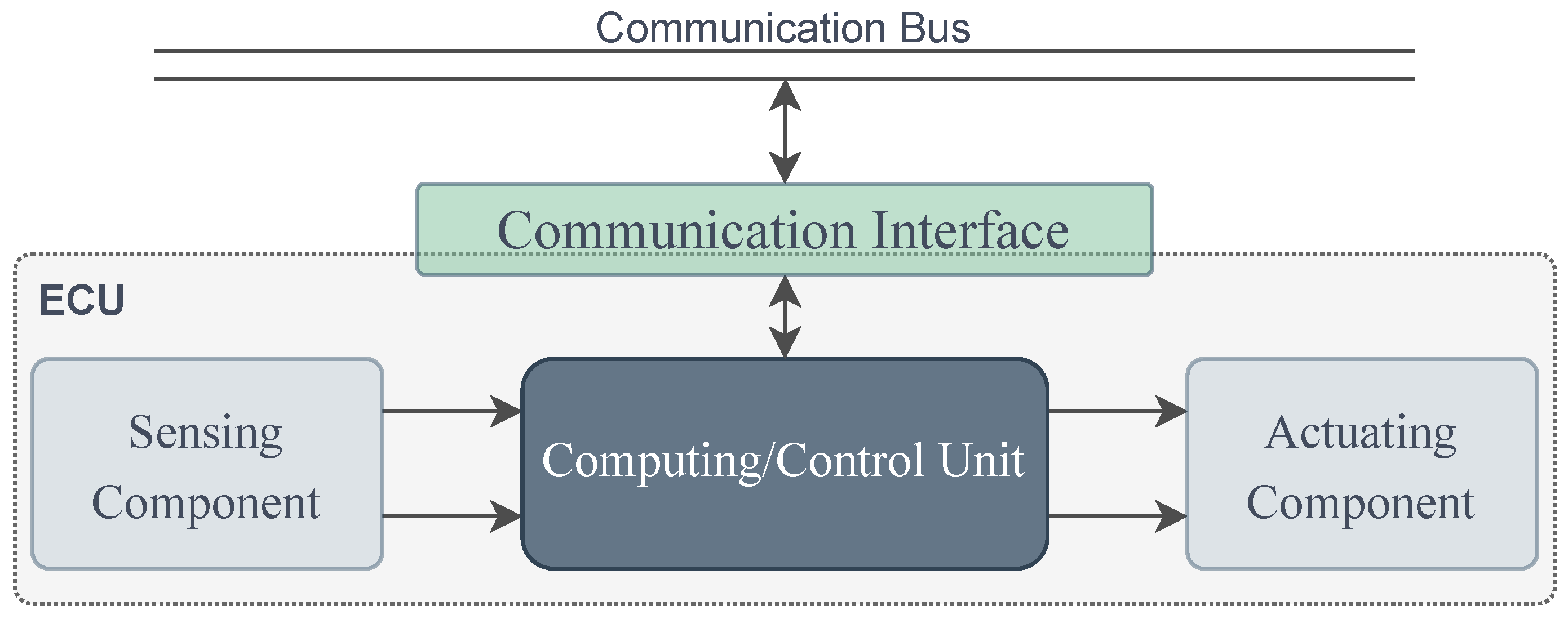
2.2. ECU Architecture
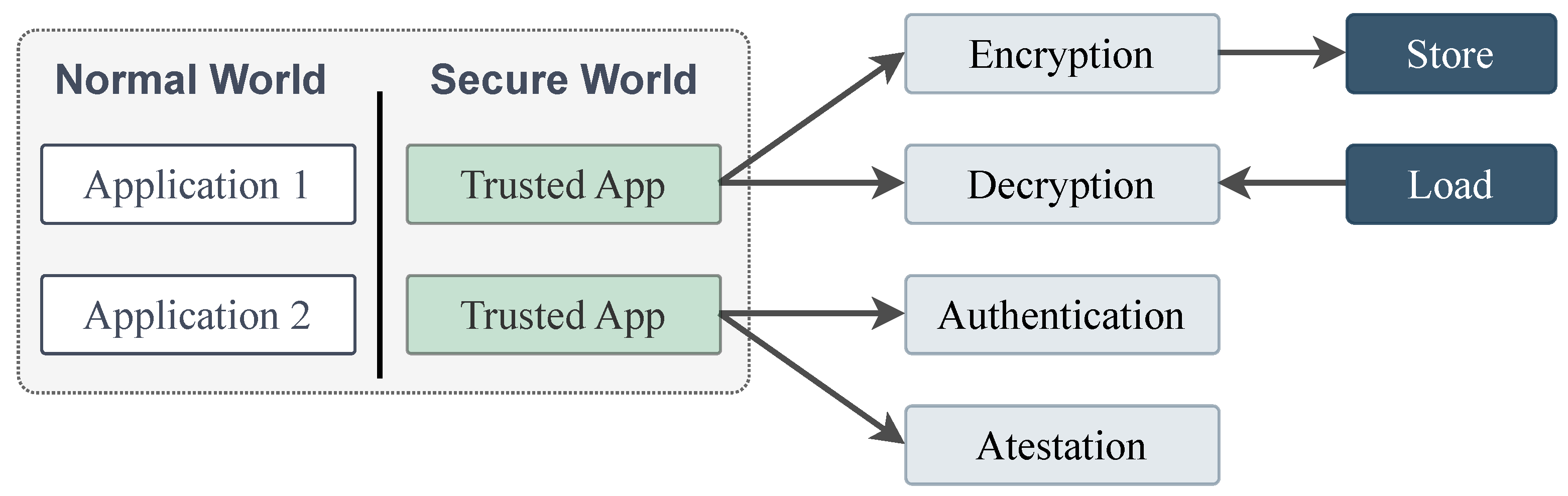
3. Securing Automotive Systems: The Role of Hardware Security Primitives
3.1. Use Case Example
3.2. Currently Used Hardware Primitives
3.3. Side-Channel Attacks
4. Automotive Reliability: Redundancy as the Key to Availability
4.1. Software, Hardware, and Hybrid Redundancy—Pros & Cons
4.2. Use Case Example
4.3. Currently Used Redundancy
5. Final Discussion and Future Directions
- Addressing hardware security primitives: The majority of automotive solutions do not meet all the requirements for memory and I/O isolation as they lack robust memory protection and system-wide protection technologies. Despite the recent shift towards more mature security-focused MCUs, this transition is still in its early stages. Moreover, security considerations must be integrated from the ground up when developing new vehicular architectures, going all the way from the simplest ECUs to complex inter-vehicular communication networks. As security threats emerge continuously and as vehicles are deployed in the field, possibly for decades, it is necessary to secure them with more mature security-focused hardware architectures, eliminating the compromise between performance and security.
- Addressing reliability challenges: Automotive ECUs currently incorporate fault-tolerant components to achieve high-reliability levels, primarily through redundancy. Nevertheless, these systems face challenges in meeting the strict safety and dependability requirements of automotive systems without compromising hard real-time constraints and increasing costs. The additional redundancy in fault-tolerant designs must not compromise the real-time performance of automotive systems. As such, as ECUs start to become more complex, the need for more lightweight and hybrid redundancy solutions is growing.
- Addressing system integration and partitioning: Integrating different ASIL systems into the same ECU is essential to address current SWAP-C metrics for automotive systems. To overcome these challenges, future research should explore advanced partitioning techniques to isolate safety-critical functions from non-critical ones onto the same platform. Virtualization-based solutions can help to consolidate MCSs while maintaining the robust security and reliability of each independent system.
- Enhancing protection against side-channel attacks: Side-channel attacks pose significant risks to automotive ECUs. From electromagnetic radiation to timing variations, attackers can exploit these side-channels to gain insight into system operations and potentially compromise sensitive data. However, side-channel attack can be challenging to defend against, as they may occur due to implementation flaws rather than design mistakes. Therefore, to effectively protect against side-channel attack, a thorough understanding of all the components within an ECU is essential. Future research should concentrate on actively detecting potential side-channels and developing advanced techniques to detect and mitigate these attacks.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Daily, M.; Medasani, S.; Behringer, R.; Trivedi, M. Self-Driving Cars. Computer 2017, 50, 18–23. [Google Scholar] [CrossRef]
- Staron, M. Automotive Software Architectures; Springer: Berlin/Heidelberg, Germany, 2021. [Google Scholar]
- Urmson, C.; Anhalt, J.; Bagnell, D.; Baker, C.; Bittner, R.; Clark, M.N.; Dolan, J.; Duggins, D.; Galatali, T.; Geyer, C.; et al. Autonomous driving in urban environments: Boss and the Urban Challenge. J. Field Robot. 2008, 25, 425–466. [Google Scholar] [CrossRef]
- Shahian Jahromi, B.; Tulabandhula, T.; Cetin, S. Real-Time Hybrid Multi-Sensor Fusion Framework for Perception in Autonomous Vehicles. Sensors 2019, 19, 4357. [Google Scholar] [CrossRef]
- Wilwert, C.; Navet, N.; Song, Y.Q.; Simonot-Lion, F. Design of automotive X-by-Wire systems. In The Industrial Communication Technology Handbook; Zurawski, R., Ed.; CRC Press: Boca Raton, FL, USA, 2005. [Google Scholar]
- Heiser, G. No Safety Without (Cyber-)Security! ACM SIGBED. 2020. Available online: https://microkerneldude.org/2020/11/07/no-safety-without-cyber-security/ (accessed on 20 August 2024).
- Miller, C. Lessons learned from hacking a car. IEEE Design Test 2019, 36, 7–9. [Google Scholar] [CrossRef]
- Greenberg, A. The Jeep Hackers Are Back to Prove Car Hacking Can Get Much Worse. WIRED. 2016. Available online: https://www.wired.com/2016/08/jeep-hackers-return-high-speed-steering-acceleration-hacks/ (accessed on 23 April 2024).
- Greenberg, A. This Bluetooth Attack Can Steal a Tesla Model X in Minutes. WIRED. 2020. Available online: https://www.wired.com/story/tesla-model-x-hack-bluetooth/ (accessed on 23 April 2024).
- Gomes, T.; Sousa, P.; Silva, M.; Ekpanyapong, M.; Pinto, S. FAC-V: An FPGA-Based AES Coprocessor for RISC-V. J. Low Power Electron. Appl. 2022, 12, 50. [Google Scholar] [CrossRef]
- Kocher, P.C. Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems. In Proceedings of the Advances in Cryptology—CRYPTO’96, Santa Barbara, CA, USA, 18–22 August 1996; Koblitz, N., Ed.; Springer: Berlin/Heidelberg, Germany, 1996; pp. 104–113. [Google Scholar]
- Kocher, P.; Horn, J.; Fogh, A.; Genkin, D.; Gruss, D.; Haas, W.; Hamburg, M.; Lipp, M.; Mangard, S.; Prescher, T.; et al. Spectre Attacks: Exploiting Speculative Execution. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 1–19. [Google Scholar]
- Lipp, M.; Schwarz, M.; Gruss, D.; Prescher, T.; Haas, W.; Fogh, A.; Horn, J.; Mangard, S.; Kocher, P.; Genkin, D.; et al. Meltdown: Reading Kernel Memory from User Space. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 973–990. [Google Scholar]
- Luo, M.; Myers, A.C.; Suh, G.E. Stealthy Tracking of Autonomous Vehicles with Cache Side Channels. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; pp. 859–876. [Google Scholar]
- Trippel, T.; Weisse, O.; Xu, W.; Honeyman, P.; Fu, K. WALNUT: Waging Doubt on the Integrity of MEMS Accelerometers with Acoustic Injection Attacks. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy (EuroS&P), Paris, France, 26–28 April 2017; pp. 3–18. [Google Scholar]
- Wirthlin, M.J.; Keller, A.M.; McCloskey, C.; Ridd, P.; Lee, D.; Draper, J. SEU Mitigation and Validation of the LEON3 Soft Processor Using Triple Modular Redundancy for Space Processing. In Proceedings of the 2016 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays, Monterey, CA, USA, 21–23 February 2016; pp. 205–214. [Google Scholar]
- Koopman, P.; Wagner, M. Autonomous Vehicle Safety: An Interdisciplinary Challenge. IEEE Intell. Transp. Syst. Mag. 2017, 9, 90–96. [Google Scholar] [CrossRef]
- Pinto, S.; Tavares, A.; Montenegro, S. Space and time partitioning with hardware support for space applications. In Proceedings of the DAta Systems in Aerospace Conference, DASIA, Tallinn, Estonia, 10–12 May 2016. [Google Scholar]
- Masmano, M.; Ripoll, I.; Crespo, A.; Jean-Jacques, M. XtratuM: A Hypervisor for Safety Critical Embedded Systems. In Proceedings of the 11th Real Time Linux Workshop, Dresden, Germany, 28–30 September 2009. [Google Scholar]
- Placek, M. Automotive Electronics Worldwide—Statistics & Facts. 2023. Available online: https://www.statista.com/topics/7983/automotive-electronics-worldwide/ (accessed on 12 April 2024).
- Schäuffele, J.; Zurawka, T. Automotive Software Engineering: Principles, Processes, Methods, and Tools; SAE International: Warrendale, PA, USA, 2005. [Google Scholar]
- Eckstein, L.; Hesse, L.; Klein, M. Steer-by-Wire, Potential, and Challenges. In Encyclopedia of Automotive Engineering; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2014; pp. 1–14. [Google Scholar]
- ISO 26262-1:2018; Road Vehicles—Functional Safety—Part 1: Vocabulary. International Organization for Standardization: Geneva, Switzerland, 2018.
- Bosch Mobility. Vehicle Control Unit. Available online: https://www.bosch-mobility.com/en/solutions/control-units/vehicle-control-unit/ (accessed on 24 March 2025).
- McKay, B.; Qian, L. Integrated Power Electronics: The Road Merges. Technical Report, APTIV. 2022. Available online: https://www.aptiv.com/en/insights/article/integrated-power-electronics-the-road-merges (accessed on 24 March 2024).
- Bosch Mobility. The Electric Power Steering System with Belt Drive Servo Unit. Available online: https://www.bosch-mobility.com/en/solutions/steering/electric-power-steering-belt-drive-servo-unit/ (accessed on 24 March 2025).
- Hitachi Automotive Systems Americas, Inc. Steering System. Available online: https://www.hitachi-automotive.us/Products/oem/DCS/Steering/index.htm (accessed on 24 March 2025).
- Infineon Technologies AG. Airbag Control. Available online: https://www.infineon.com/cms/en/applications/automotive/chassis-safety-and-adas/airbag-system/ (accessed on 24 March 2025).
- Sukumar, K.K.; Oberkönig, M.; Noopuran, S.; Cypress. Functional Safety for Automotive HMI Systems. 2019. Available online: https://passive-components.eu/functional-safety-for-automotive-hmi-systems/ (accessed on 24 March 2025).
- Liu, T.; Liu, J.; Wang, J.; Zhang, H.; Zhang, B.; Ma, Y.; Sun, M.; Lv, Z.; Xu, G. Pseudolites to Support Location Services in Smart Cities: Review and Prospects. Smart Cities 2023, 6, 2081–2105. [Google Scholar] [CrossRef]
- Roriz, R.; Cabral, J.; Gomes, T. Automotive LiDAR Technology: A Survey. IEEE Trans. Intell. Transp. Syst. 2022, 23, 6282–6297. [Google Scholar] [CrossRef]
- Joubert, N.; Reid, T.G.R.; Noble, F. Developments in Modern GNSS and Its Impact on Autonomous Vehicle Architectures. In Proceedings of the 2020 IEEE Intelligent Vehicles Symposium (IV), Las Vegas, NV, USA, 19 October–13 November 2020; pp. 2029–2036. [Google Scholar]
- Costa, D.; Cuomo, L.; Oliveira, D.; Savino, I.M.; Morelli, B.; Martins, J.; Biasci, A.; Pinto, S. IRQ Coloring and the Subtle Art of Mitigating Interrupt-generated Interference. arXiv 2023, arXiv:22308.00997. [Google Scholar]
- Costa, D.; Moreira, G.; Oliveira, A.; Martins, J.; Pinto, S. SP-IMPact: A Framework for Static Partitioning Interference Mitigation and Performance Analysis. In Proceedings of the Sixth Workshop on Next Generation Real-Time Embedded Systems (NG-RES 2025), Barcelona, Spain, 20–22 January 2025; Volume 128, pp. 5:1–5:15. [Google Scholar]
- Zalman, R. Rugged Autonomous Vehicles; Morgan Kaufmann: Burlington, MA, USA, 2017. [Google Scholar]
- Vailshery, L.S. Microcontrollers—Statistics & Facts. 2024. Available online: https://www.statista.com/topics/9939/microcontrollers/#topicOverview (accessed on 12 April 2024).
- Pinto, S.; Santos, N. Demystifying Arm TrustZone: A Comprehensive Survey. ACM Comput. Surv. 2019, 51, 1–36. [Google Scholar] [CrossRef]
- PSA Certified. What Is a Root of Trust? Available online: https://www.psacertified.org/blog/what-is-a-root-of-trust/ (accessed on 24 March 2025).
- McGrath, T.; Bagci, I.E.; Wang, Z.M.; Roedig, U.; Young, R.J. A PUF taxonomy. Appl. Phys. Rev. 2019, 6, 011303. [Google Scholar] [CrossRef]
- Wolf, M.; Gendrullis, T. Design, implementation, and evaluation of a vehicular hardware security module. In Proceedings of the 14th International Conference on Information Security and Cryptology, Seoul, Republic of Korea, 30 November–2 December 2011; pp. 302–318. [Google Scholar]
- Goodin, D. Found: New Android Malware with Never-Before-Seen Spying Capabilities. 2018. Available online: https://arstechnica.com/information-technology/2018/01/found-new-android-malware-with-never-before-seen-spying-capabilities/ (accessed on 24 March 2025).
- Dave, L. Apple’s App Store Infected with XcodeGhost Malware in China. 2015. Available online: https://www.bbc.com/news/technology-34311203 (accessed on 24 March 2025).
- Cerdeira, D.; Santos, N.; Fonseca, P.; Pinto, S. SoK: Understanding the Prevailing Security Vulnerabilities in TrustZone-assisted TEE Systems. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 1416–1432. [Google Scholar]
- Hu, S.; Chen, Q.A.; Joung, J.; Carlak, C.; Feng, Y.; Mao, Z.M.; Liu, H.X. CVShield: Guarding Sensor Data in Connected Vehicle with Trusted Execution Environment. In Proceedings of the Second ACM Workshop on Automotive and Aerial Vehicle Security, New Orleans, LA, USA, 18 March 2020; Association for Computing Machinery: New York, NY, USA, 2020. [Google Scholar]
- Pinto, S.; Araujo, H.; Oliveira, D.; Martins, J.; Tavares, A. Virtualization on TrustZone-Enabled Microcontrollers? Voilà! In Proceedings of the 2019 IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS), Montreal, QC, Canada, 16–18 April 2019; pp. 293–304. [Google Scholar]
- Oliveira, D.; Gomes, T.; Pinto, S. uTango: An Open-Source TEE for IoT Devices. IEEE Access 2022, 10, 23913–23930. [Google Scholar] [CrossRef]
- Garlati, C.; Pinto, S. A Clean Slate Approach to Linux Security RISC-V Enclaves. In Proceedings of the Embedded World Conference (EWC), Nuremberg, Germany, 25–27 February 2020. [Google Scholar]
- Rivain, M.; Prouff, E. Provably Secure Higher-Order Masking of AES. In Proceedings of the Cryptographic Hardware and Embedded Systems, CHES 2010, Santa Barbara, CA, USA, 17–20 August 2010; pp. 413–427. [Google Scholar]
- Yan, C.; Shin, H.; Bolton, C.; Xu, W.; Kim, Y.; Fu, K. SoK: A Minimalist Approach to Formalizing Analog Sensor Security. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 233–248. [Google Scholar]
- Petit, J.; Stottelaar, B.; Feiri, M. Remote Attacks on Automated Vehicles Sensors: Experiments on Camera and LiDAR. In Proceedings of the Black Hat Europe, Amsterdam, The Netherlands, 10–13 November 2015. [Google Scholar]
- Shin, H.; Kim, D.; Kwon, Y.; Kim, Y. Illusion and Dazzle: Adversarial Optical Channel Exploits Against Lidars for Automotive Applications. In Proceedings of the Cryptographic Hardware and Embedded Systems–CHES 2017, Taipei, Taiwan, 25–28 September 2017. [Google Scholar]
- Yan, C.; Xu, W.; Liu, J. Can You Trust Autonomous Vehicles: Contactless Attacks against Sensors of Self-driving Vehicle. In Proceedings of the DEF CON 24, Las Vegas, NV, USA, 4–7 August 2016. [Google Scholar]
- Camurati, G.; Poeplau, S.; Muench, M.; Hayes, T.; Francillon, A. Screaming Channels: When Electromagnetic Side Channels Meet Radio Transceivers. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; Association for Computing Machinery: New York, NY, USA, 2018. [Google Scholar]
- Zhan, Z.; Zhang, Z.; Liang, S.; Yao, F.; Koutsoukos, X. Graphics Peeping Unit: Exploiting EM Side-Channel Information of GPUs to Eavesdrop on Your Neighbors. In Proceedings of the 2022 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 22–26 May 2022. [Google Scholar]
- Gandolfi, K.; Mourtel, C.; Olivier, F. Electromagnetic Analysis: Concrete Results. In Proceedings of the Third International Workshop on Cryptographic Hardware and Embedded Systems, Paris, France, 14–16 May 2001; pp. 251–261. [Google Scholar]
- Xu, W.; Yan, C.; Jia, W.; Ji, X.; Liu, J. Analyzing and Enhancing the Security of Ultrasonic Sensors for Autonomous Vehicles. IEEE Internet Things J. 2018, 5, 5015–5029. [Google Scholar] [CrossRef]
- Bhunia, S.; Tehranipoor, M. Side-Channel Attacks. In Hardware Security; Bhunia, S., Tehranipoor, M., Eds.; Morgan Kaufmann: Cambridge, MA, USA, 2019. [Google Scholar]
- Van Bulck, J.; Piessens, F.; Strackx, R. Nemesis: Studying Microarchitectural Timing Leaks in Rudimentary CPU Interrupt Logic. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 178–195. [Google Scholar]
- Rodrigues, C.; Oliveira, D.; Pinto, S. BUSted!!! Microarchitectural Side-Channel Attacks on the MCU Bus Interconnect. In Proceedings of the 2024 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–23 May 2024; pp. 3679–3696. [Google Scholar]
- Van Bulck, J.; Mühlberg, J.T.; Piessens, F. VulCAN: Efficient Component Authentication and Software Isolation for Automotive Control Networks. In Proceedings of the 33rd Annual Computer Security Applications Conference, Orlando, FL, USA, 4–8 December 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 225–237. [Google Scholar]
- Avizienis, A. Toward systematic design of fault-tolerant systems. Computer 1997, 30, 51–58. [Google Scholar] [CrossRef]
- Pimentel, A.D. A Case for Security-Aware Design-Space Exploration of Embedded Systems. J. Low Power Electron. Appl. 2020, 10, 22. [Google Scholar] [CrossRef]
- Akter, S.; Khalil, K.; Bayoumi, M. A Survey on Hardware Security: Current Trends and Challenges. IEEE Access 2023, 11, 77543–77565. [Google Scholar] [CrossRef]
- Avizienis, A.; Laprie, J.C.; Randell, B.; Landwehr, C. Basic concepts and taxonomy of dependable and secure computing. IEEE Trans. Dependable Secur. Comput. 2004, 1, 11–33. [Google Scholar] [CrossRef]
- Richter-Brockmann, J.; Sasdrich, P.; Bache, F.; Güneysu, T. Concurrent error detection revisited: Hardware protection against fault and side-channel attacks. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Virtual Event, 25–28 August 2020. [Google Scholar]
- Wang, L.; Hu, M.; Bian, Y.; Guo, G.; Li, S.E.; Chen, B.; Zhong, Z. Periodic Event-Triggered Fault Detection for Safe Platooning Control of Intelligent and Connected Vehicles. IEEE Trans. Veh. Technol. 2024, 73, 5064–5077. [Google Scholar] [CrossRef]
- Hasan, M.; Goraya, M.S. Fault tolerance in cloud computing environment: A systematic survey. Comput. Ind. 2018, 99, 156–172. [Google Scholar] [CrossRef]
- Rosenstatter, T.; Strandberg, K.; Jolak, R.; Scandariato, R.; Olovsson, T. REMIND: A Framework for the Resilient Design of Automotive Systems. In Proceedings of the 2020 IEEE Secure Development (SecDev), Virtual Event, 28–30 September 2020; pp. 81–95. [Google Scholar]
- Kasap, S.; Weber Wachter, E.; Zhai, X.; Ehsan, S.; McDonald-Maier, K. Novel lockstep-based fault mitigation approach for SoCs with roll-back and roll-forward recovery. Microelectron. Reliab. 2021, 124, 114297. [Google Scholar] [CrossRef]
- Somani, A.K.; Vaidya, N.H. Understanding Fault Tolerance and Reliability. Computer 1997, 30, 45–50. [Google Scholar] [CrossRef]
- Răzvan, S.; Csaba, S. Software Redundancy Implementation Strategy in Reconfigurable Hardware Framework. In Proceedings of the 2019 8th International Conference on Modern Power Systems (MPS), Cluj-Napoca, Romania, 21–23 May 2019; pp. 1–6. [Google Scholar]
- Afzaal, U.; Lee, J.A. Low-cost Hardware Redundancy for Fault-mitigation in Power-constrained IoT Systems. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 21–23 October 2020; pp. 60–62. [Google Scholar]
- Mallavarapu, P.; Upadhyay, H.N.; Rajkumar, G.; Elamaran, V. Fault-tolerant digital filters on FPGA using hardware redundancy techniques. In Proceedings of the 2017 International Conference of Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 20–22 April 2017; Volume 2, pp. 256–259. [Google Scholar]
- Alavizadeh, H.; Hong, J.B.; Kim, D.S.; Jang-Jaccard, J. Evaluating the effectiveness of shuffle and redundancy MTD techniques in the cloud. Comput. Secur. 2021, 102, 102091. [Google Scholar] [CrossRef]
- Afonso, F.; Silva, C.; Brito, N.; Montenegro, S.; Tavares, A. Aspect-oriented fault tolerance for real-time embedded systems. In Proceedings of the 2008 AOSD Workshop on Aspects, Components, and Patterns for Infrastructure Software, Brussels, Belgium, 1 April 2008. [Google Scholar]
- Shajahan, M.A. Fault Tolerance and Reliability in AUTOSAR Stack Development: Redundancy and Error Handling Strategies. Technol. Manag. Rev. 2018, 3, 27–45. [Google Scholar]
- Ertugrul, E.; Sahingoz, O.K. Fault Tolerance in Real-Time Systems: A Review. In Proceedings of the Intelligent Systems Design and Applications, Vellore, India, 6–8 December 2018; Abraham, A., Muhuri, P.K., Muda, A.K., Gandhi, N., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 283–293. [Google Scholar]
- Abdulnabi, M.S.; Ahmed, H. Design of Efficient Cyclic Redundancy Check-32 using FPGA. In Proceedings of the 2018 International Conference on Computer, Control, Electrical, and Electronics Engineering (ICCCEEE), Khartoum, Sudan, 12–14 August 2018; pp. 1–5. [Google Scholar]
- Gao, Z.; Cecati, C.; Ding, S.X. A Survey of Fault Diagnosis and Fault-Tolerant Techniques—Part I: Fault Diagnosis with Model-Based and Signal-Based Approaches. IEEE Trans. Ind. Electron. 2015, 62, 3757–3767. [Google Scholar] [CrossRef]
- Şinca, R.; Szász, C. Fault-tolerant digital systems development using triple modular redundancy. Int. Rev. Appl. Sci. Eng. IRASE 2017, 8, 3–7. [Google Scholar] [CrossRef]
- Abbaspour, A.; Mokhtari, S.; Sargolzaei, A.; Yen, K.K. A Survey on Active Fault-Tolerant Control Systems. Electronics 2020, 9, 1513. [Google Scholar] [CrossRef]
- Safari, S.; Ansari, M.; Khdr, H.; Gohari-Nazari, P.; Yari-Karin, S.; Yeganeh-Khaksar, A.; Hessabi, S.; Ejlali, A.; Henkel, J. A Survey of Fault-Tolerance Techniques for Embedded Systems From the Perspective of Power, Energy, and Thermal Issues. IEEE Access 2022, 10, 12229–12251. [Google Scholar] [CrossRef]
- Peña-Fernández, M.; Serrano-Cases, A.; Lindoso, A.; Cuenca-Asensi, S.; Entrena, L.; Morilla, Y.; Martín-Holgado, P.; Martínez-Álvarez, A. Hybrid Lockstep Technique for Soft Error Mitigation. IEEE Trans. Nucl. Sci. 2022, 69, 1574–1581. [Google Scholar] [CrossRef]
- Iturbe, X.; Venu, B.; Ozer, E.; Poupat, J.L.; Gimenez, G.; Zurek, H.U. The Arm Triple Core Lock-Step (TCLS) Processor. ACM Trans. Comput. Syst. 2019, 36, 3323917. [Google Scholar] [CrossRef]
- Kaufman, L.; Bhide, S.; Johnson, B. Modeling of common-mode failures in digital embedded systems. In Proceedings of the Annual Reliability and Maintainability Symposium, Los Angeles, CA, USA, 24–27 January 2000; 2000 Proceedings; International Symposium on Product Quality and Integrity (Cat. No.00CH37055). pp. 350–357. [Google Scholar]
- Sim, M.T.; Zhuang, Y. A Dual Lockstep Processor System-on-a-Chip for Fast Error Recovery in Safety-Critical Applications. In Proceedings of the IECON 2020 The 46th Annual Conference of the IEEE Industrial Electronics Society, Singapore, 18–21 October 2020; pp. 2231–2238. [Google Scholar]
- Kottke, T.; Steininger, A. A Reconfigurable Generic Dual-Core Architecture. In Proceedings of the International Conference on Dependable Systems and Networks (DSN’06), Philadelphia, PA, USA, 25–28 June 2006; pp. 45–54. [Google Scholar]
- Marques, I.; Rodrigues, C.; Tavares, A.; Pinto, S.; Gomes, T. Lock-V: A heterogeneous fault tolerance architecture based on Arm and RISC-V. Microelectron. Reliab. 2021, 120, 114120. [Google Scholar] [CrossRef]
- Ren, S.; Zhang, Y.; Pan, L.; Xiao, Z. Phantasy: Low-Latency Virtualization-Based Fault Tolerance via Asynchronous Prefetching. IEEE Trans. Comput. 2019, 68, 225–238. [Google Scholar] [CrossRef]
- Tkachov, V.; Hunko, M.; Volotka, V. Scenarios for Implementation of Nested Virtualization Technology in Task of Improving Cloud Firewall Fault Tolerance. In Proceedings of the 2019 IEEE International Scientific-Practical Conference Problems of Infocommunications, Science and Technology (PIC S&T), Kyiv, Ukraine, 8–11 October 2019; pp. 759–763. [Google Scholar]
- Lorch, J.R.; Baumann, A.; Glendenning, L.; Meyer, D.; Warfield, A. Tardigrade: Leveraging Lightweight Virtual Machines to Easily and Efficiently Construct Fault-Tolerant Services. In Proceedings of the 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI 15), Oakland, CA, USA, 4–6 May 2015. [Google Scholar]
- Martins, J.; Pinto, S. Shedding Light on Static Partitioning Hypervisors for Arm-based Mixed-Criticality Systems. In Proceedings of the IEEE 29th Real-Time and Embedded Technology and Applications Symposium (RTAS), San Antonio, TX, USA, 9–12 May 2023; pp. 40–53. [Google Scholar]
- Santos, A.; Martins, J.; Sousa, J.; Rodríguez, M.; Pinto, S. Let’s Get Physical: Rethinking the Static Partitioning Hypervisor Architecture for an MMU-less Memory Model. Authorea 2025. [Google Scholar] [CrossRef]
- Pinto, S.; Martins, J.; Rodriguez, M.; Cunha, L.; Schmalz, G.; Moslehner, U.; Dieffenbach, K.; Roecker, T. RISC-V Needs Secure ’Wheels’: The MCU Initiator-Side Perspective. arXiv 2024, arXiv:2410.09839. [Google Scholar]
- IEC 61508-1:2010; Functional Safety of Electrical/Electronic/Programmable Electronic Safety-Related Systems—Part 1. International Electrotechnical Commission: Geneva, Switzerland, 2010.
- Munir, A. Safety Assessment and Design of Dependable Cybercars: For today and the future. IEEE Consum. Electron. Mag. 2017, 6, 69–77. [Google Scholar] [CrossRef]



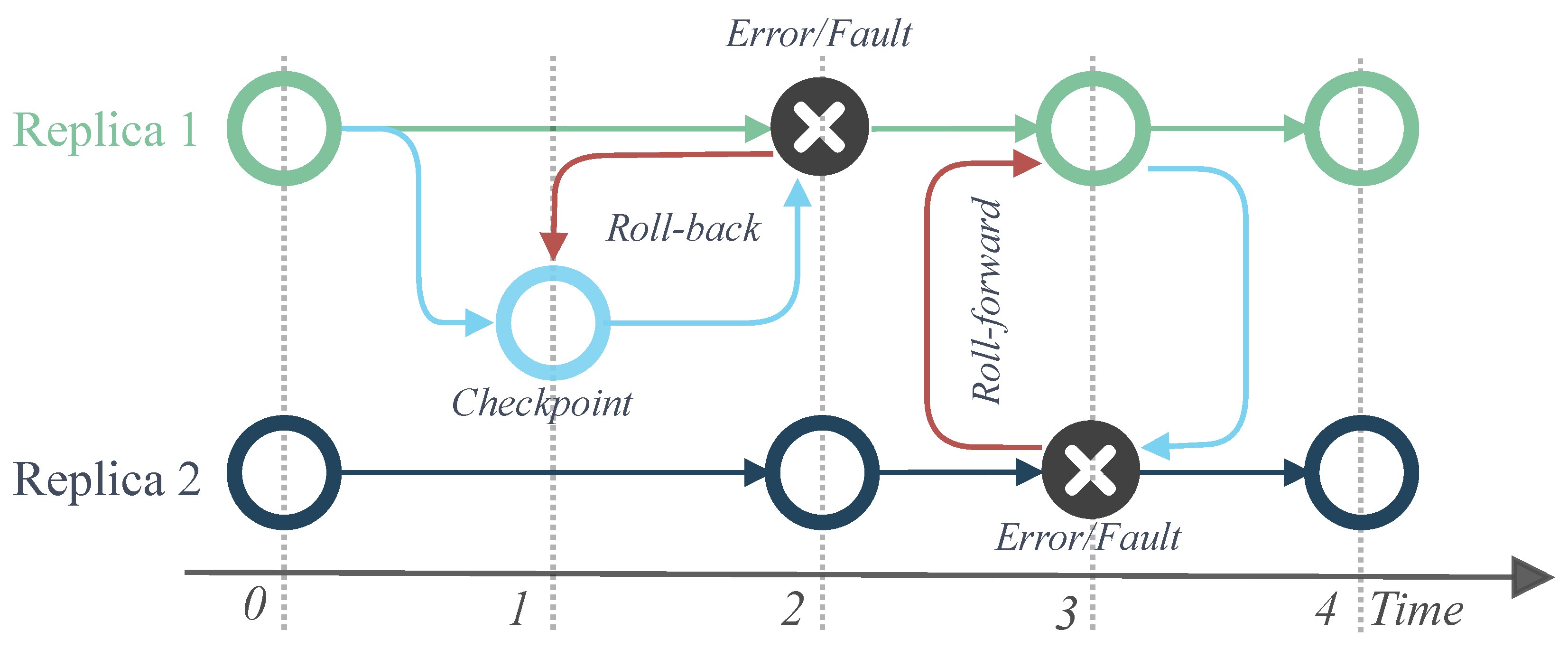
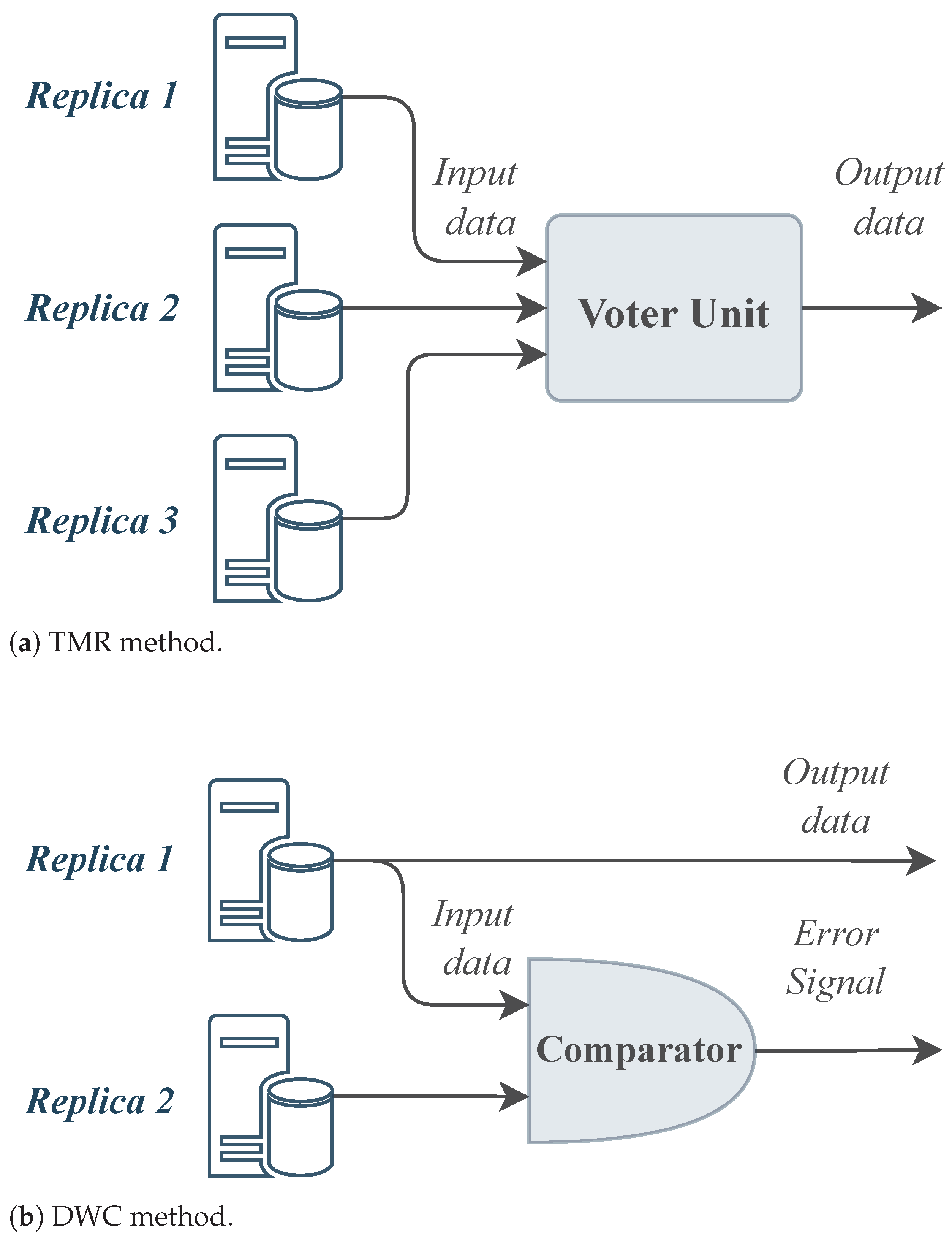

| MCU Families | ARM | PowerPC | V850 |
|---|---|---|---|
| Infineon Technologies | ✓ | ||
| NXP Semiconductors | ✓ | ✓ | |
| Renesas Electronics | ✓ | ✓ | |
| Texas Instruments Inc. | ✓ | ||
| STMicroelectronics | ✓ | ✓ |
| Primitive/ Techniques | Encryption | Memory Isolation | Hardware RoT | Secure Coprocessors | Cryptographic Accelerators | TEE | Secure Boot |
|---|---|---|---|---|---|---|---|
| MPU/PMP | ✓ | ||||||
| TrustZone/WG | ✓ | ✓ | ✓ | ||||
| Secure Elements | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| TPM | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | |
| HSM | ✓ | ✓ | ✓ | ✓ | |||
| RNG | ✓ | ✓ | |||||
| OTP | ✓ | ✓ | |||||
| ROM | ✓ | ✓ | |||||
| PUF | ✓ | ✓ |
| Vendor | Armv8-M Support | Armv8-M Automotive Line |
|---|---|---|
| Infineon Technologies | ||
| NXP Semiconductors | ✓ | ✓ |
| Renesas Electronics | ✓ | |
| Texas Instruments Inc. | ||
| STMicroelectronics | ✓ |
| Attack Vector | Target Component | Countermeasures |
|---|---|---|
| Electromagnetic injection | LiDAR, radar, MCUs | Shielding, signal filtering, protocol-level redundancy |
| Acoustic injection | MEMS gyroscopes and accelerometers | Mechanical damping, frequency filters, casing design |
| Timing attacks | MCUs, control software | Constant-time algorithms, TEE isolation, jitter insertion |
| Cache side-channels | Software stack, control units | Cache partitioning, access pattern obfuscation, TEE support |
| Bus arbitration leakage | MCU interconnects | Hardware-level redesign, bus access scheduling randomization |
| Radio interference | Ultrasonic, RF sensors | Spread-spectrum techniques, authentication protocols |
| Redundancy Technique | Approach | Area | Performance Overhead | Flexibility | Maintainability | Fault Coverage | |
|---|---|---|---|---|---|---|---|
| SW | HW | ||||||
| Single-version | ✓ | (1⇒N)x | High | High | High | Low | |
| N-version programming | ✓ | (1⇒N)x | High | High | High | Medium | |
| Time-based redundancy | ✓ | (1⇒N)x | High | High | High | Medium | |
| Parity check | ✓ | - | - | High | High | Low | |
| Cyclic code checksum | ✓ | - | - | High | High | Low | |
| TMR | ✓ | ∼3x | Low | Low | Low | High | |
| DWC | ✓ | ∼2x | Medium | Low | Low | High | |
| NMR | ✓ | (1⇒N)x | Low | Medium | Low | High | |
| DCLS | ✓ | ✓ | ∼2x | Medium | Medium | Medium | High |
| TCLS | ✓ | ✓ | ∼3x | Low | Medium | Medium | High |
| Hypervisors | ✓ | ✓ | (1⇒N) | Medium | High | High | High |
| Vendor | Platform Name | Lockstep Type | CPU Architecture | Level 2 MPU |
|---|---|---|---|---|
| Infineon Technologies | Aurix | TCLS | TC2x/TC3x/TC4x | |
| NXP Semiconductors | MPC564xL/S32E/ Z/K | DCLS | Arm Cortex R52/Cortex-M33/E200 Z4/Cortex-M7 | |
| Renesas Electronics | RH850/U2A16 | DCLS | RH850 G4MH | |
| Texas Instruments Inc. | Hercules | DCLS | Arm Cortex-R4F/Arm Cortex-R5F | |
| STMicroelectronics | Stellar | MCLS | Arm Cortex R52+/Cortex-M4/Cortex-M7 | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cunha, L.; Sousa, J.; Azevedo, J.; Pinto, S.; Gomes, T. Security First, Safety Next: The Next-Generation Embedded Sensors for Autonomous Vehicles. Electronics 2025, 14, 2172. https://doi.org/10.3390/electronics14112172
Cunha L, Sousa J, Azevedo J, Pinto S, Gomes T. Security First, Safety Next: The Next-Generation Embedded Sensors for Autonomous Vehicles. Electronics. 2025; 14(11):2172. https://doi.org/10.3390/electronics14112172
Chicago/Turabian StyleCunha, Luís, João Sousa, José Azevedo, Sandro Pinto, and Tiago Gomes. 2025. "Security First, Safety Next: The Next-Generation Embedded Sensors for Autonomous Vehicles" Electronics 14, no. 11: 2172. https://doi.org/10.3390/electronics14112172
APA StyleCunha, L., Sousa, J., Azevedo, J., Pinto, S., & Gomes, T. (2025). Security First, Safety Next: The Next-Generation Embedded Sensors for Autonomous Vehicles. Electronics, 14(11), 2172. https://doi.org/10.3390/electronics14112172







