1. Introduction
Cryptographic algorithms are a cornerstone of modern information security systems, with block symmetric ciphers being a particularly notable category. These ciphers are designed to efficiently encrypt large volumes of data and are implemented as hardware modules in nearly all modern processors, including mobile platforms.
The operation of modern ciphers is founded on the encryption principles of diffusion and confusion, introduced by Claude Shannon [
1]. A central challenge in designing block symmetric ciphers lies in implementing the concept of confusion, which is achieved through nonlinear components known as S-boxes. S-boxes are critical elements of modern ciphers, significantly influencing their resilience to modern cryptanalysis techniques and often determining the overall performance of cryptographic transformations. Consequently, developing high-quality S-boxes is one of the most crucial tasks in modern cryptography.
Today, a standard set of cryptographic quality criteria is applied to S-boxes, which includes the following basic requirements:
Nonlinearity;
Strict avalanche criterion (SAC);
Bit independence criterion (BIC);
Linear approximation probability (LAP);
Differential approximation probability (DAP);
Correlation independence of output and input vectors of the S-box.
Often, other criteria, such as periods of return to the initial state [
2], and sets of criteria that indicate the cryptographic properties of the S-box when it is represented by component functions of many-valued logic are also considered [
3].
The first two criteria, implying nonlinearity and the strict avalanche criterion, are the most fundamental for modern S-boxes and thus receive the most attention from researchers. For example, highly nonlinear S-boxes reaching practically maximal values of nonlinearity can be synthesized in Galois fields via the Nyberg construction, which is used in the AES (Rijndael) cryptographic algorithm [
4]. After they are generated through the Galois field construction, these cryptographic S-boxes undergo an affine transformation applied to the output binary vectors to enhance their avalanche and correlation properties.
The S-box is a fundamental component of most modern ciphers, playing a crucial role in determining the overall security level of the encryption algorithm. Various methods have been proposed for synthesizing S-boxes with high cryptographic quality.
For example, Zahid et al. [
5] utilized trigonometric transformations, where the number of possible S-box designs is limited only by the encryption keys and computational resources, enabling a large design space.
A series of works explored the use of chaotic systems as the basis for S-box generation. Zahid et al. [
6] introduced a novel chaotic map combined with nonlinearity tweaking techniques to produce dynamic S-boxes with improved resistance to cryptanalysis. Shakir et al. [
7] proposed a hybrid approach that integrates chaotic systems with DNA computing to generate dynamic S-boxes offering a balance of complexity and cryptographic strength. Aydın and Özkaynak [
8] developed an automated tool for chaos-driven S-box generation, allowing for enhanced analysis and cryptographic performance. Youssef et al. [
9] applied dynamic S-box generation in the context of satellite image encryption, combining hyperchaotic systems with the SVD and RC5 encryption schemes. Zhang et al. [
10] proposed a dynamic S-box design based on quantum random walks controlled by hyperchaotic maps, achieving high levels of randomness and cryptographic robustness.
In parallel, evolutionary and heuristic techniques have also gained popularity. Kuznetsov et al. [
11] presented an evolutionary approach to S-box synthesis, optimizing nonlinear substitutions using genetic programming principles. Zahid et al. [
12] proposed a heuristic evolutionary method for generating dynamic S-boxes with high nonlinearity, demonstrating superior performance over traditional methods. Abdurazzokov [
13] described a method for constructing S-boxes by generating non-singular adjacency matrices via genetic algorithms, achieving improved algebraic properties. Finally, Artuğer [
14] introduced a construction based on the Josephus problem, providing an innovative deterministic approach for generating strong S-boxes with desirable cryptographic characteristics.
The authors of [
15] combined the strengths of genetic algorithms and the theory of dynamic chaos to develop innovative S-boxes with enhanced cryptographic properties.
There is also a more classical but no less effective approach, which consists of using polynomial transformations over the GF(2
8). In [
16], a new approach is proposed, which includes the use of polynomial transformations, dynamic affine transformations, and a permutation technique created by the authors. Similarly, in [
17], an algorithm is described for generating S-boxes using the direct product of cyclic groups, achieving high efficiency and enabling the creation of up to 983040 nearly optimal S-boxes, each in just 0.01 s.
Algorithms based on the theory of elliptic curves have also gained popularity. For example, the authors of [
18] propose S-box generation methods compatible with existing protocols, offering a high cryptographic strength, dynamism, and increased encryption performance with minimal computational costs. Additionally, in [
19], an approach for synthesizing S-boxes designed for lightweight cryptography is outlined, ensuring high adaptability and strong resistance to attacks.
In recent years, artificial intelligence techniques have also been actively applied to the construction of cryptographically strong S-boxes. These approaches typically rely on neural networks, evolutionary algorithms, or swarm intelligence to optimize nonlinearity, avalanche criteria, and resistance to attacks.
Rong et al. [
20] proposed an S-box construction algorithm that combines neural networks with genetic algorithms. Their approach trains a neural network to learn optimal transformation structures and then refines them using genetic evolution to improve cryptographic properties. Long and Wang [
15] introduced a method based on a discrete chaotic map integrated with an improved artificial bee colony (ABC) algorithm. Their model exploits the global search capabilities of the ABC algorithm to find S-boxes with enhanced nonlinearity and avalanche characteristics. Ahmad and Al-Solami [
21] developed an innovative approach using fractional-order Hopfield neural networks to evolve dynamic S-boxes. Their method leverages fractional-order systems’ chaotic dynamics and enhanced convergence properties to generate S-boxes with good nonlinearity and a high level of strict avalanche criterion compliance. Although artificial intelligence methods are still relatively rare in the synthesis of S-boxes, they are increasingly utilized in developing sophisticated attacks. For instance, deep learning models are vulnerable to backdoor attacks that cause targeted misclassification while preserving high accuracy on benign inputs. Lee T. et al. in a recent study [
22] demonstrated multi-targeted backdoor attacks in BERT-based models by manipulating trigger word choice and position, achieving success rates of over 95% with minimal accuracy loss on clean data. Such findings underline the growing role of AI in security research and stress the need for S-box constructions to withstand not only classical cryptanalysis but also AI-assisted adversarial techniques.
However, despite the many advantages and wide range of possibilities presented by the above approaches, they also exhibit several persistent limitations, as reported in the literature [
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22] and confirmed by our comparative analysis:
- -
The avalanche properties of most S-boxes are far from ideal;
- -
In most cases, the correlation properties of the S-box are flawed;
- -
Only small sets of S-boxes with good cryptographic properties can be synthesized using certain methods.
Moreover, the problem of synthesizing optimal S-boxes that simultaneously satisfy all major cryptographic criteria remains unsolved in the general case. Despite notable progress in chaos-based, heuristic, and AI-assisted designs, modern constructions often represent trade-offs between conflicting properties, and no universal solution has yet been established.
These circumstances necessitate the creation of new methods for synthesizing large sets of high-quality S-boxes.
Recently, methods for developing and analyzing cryptographic constructions using many-valued logic functions have gained significant attention in cryptography. They facilitate substantial improvements in the quality of cryptographic constructions, enhancing their correspondence to cryptographic quality criteria.
Modern cryptographic systems demand S-boxes that simultaneously optimize multiple conflicting properties: high nonlinearity, strict avalanche criteria, and low computational overhead. While the existing approaches excel in addressing individual metrics, they often fail to deliver balanced solutions. This paper bridges that gap by introducing a novel integration of the Nyberg construction with optimized GF(4) affine transformations. Our unique approach combines the following: mathematically guaranteed algebraic properties from finite field theory, enhanced four-valued avalanche characteristics that are unattainable in binary systems, and practical implementation efficiency through configurable lookup table (LUT)/arithmetic modes. This trifecta of advantages addresses several critical considerations in cipher design, maintaining theoretical security bounds while enabling real-world deployment across a diverse range of platforms, from hardware security modules to lightweight IoT devices.
In this light, we have to note that S-boxes represent an essential component of any block symmetric cipher, in line with Shannon’s principles of confusion and diffusion. The cryptographic quality of an S-box fundamentally determines the strength and efficiency of the overall cipher. Consequently, improvements in the S-box structure can directly impact the cipher’s performance, potentially allowing for fewer encryption rounds or reducing the complexity of the core transformation. Therefore, developing robust, high-quality S-boxes remains a central objective in modern cryptographic design.
In this paper, we introduce the use of affine transformation matrices over the GF(4) with practically valuable orders to enhance the cryptographic properties of S-boxes. We also propose a novel scheme for applying these matrices to S-boxes with optimal avalanche properties, improving their nonlinearity.
The paper presents techniques for synthesizing the complete set of affine transformation matrices over the GF(4) of order , as well as constructions for synthesizing a large collection of quaternary affine transformation matrices of order . Furthermore, we introduce a recursive construction for generating affine transformation matrices over the GF(4) for arbitrary orders n.
New S-boxes based on the original Nyberg construction are synthesized with the help of matrices of affine transformation over the GF(4), and their cryptographic properties are superior to known analogs. The nonlinearity values of S-boxes corresponding to the SAC and the criterion of the absence of correlation between the output and input vectors increase.
To demonstrate the practical viability of our approach, we embed the proposed S-box into the AES encryption algorithm and conduct extensive testing using the NIST statistical suite. The results show improved randomness and cryptographic robustness compared to the standard AES S-box, confirming the method’s effectiveness for real-world cryptographic applications.
The purpose of this paper is to improve the cryptographic quality of bijective S-boxes by synthesizing affine transformations over GF(4).
The paper is organized as follows:
- -
Section 2 describes the fundamental criteria for evaluating the cryptographic quality of S-boxes and introduces the constructions to which the proposed affine transformations are applied, including the Nyberg construction and S-boxes with maximal avalanche characteristics.
- -
Section 3 addresses the synthesis of non-binary affine transformation matrices. In this section, we also present our algorithm for applying affine transformations to S-boxes with optimal avalanche properties, ensuring the preservation of these properties while enhancing the S-box nonlinearity.
- -
Section 4 focuses on analyzing the cryptographic properties of the constructed S-boxes and provides a discussion of the results obtained.
- -
Section 5 concludes the paper with a summary of the research findings.
2. Materials and Methods
The level of implementation of Shannon’s encryption concepts—diffusion and confusion—depends on the quality of the chosen cryptographic transformation. The S-box is the most important component of modern ciphers, allowing them to resist the main types of cryptanalysis attacks, such as linear cryptanalysis, differential cryptanalysis, and correlation cryptanalysis. As such, cryptographic S-boxes receive a great deal of attention from modern researchers. Estimations of the cryptographic quality of S-boxes are currently made with a generally accepted set of cryptographic quality criteria, which assume that the S-box is represented as a set of component Boolean functions where is the number of outputs/inputs of the S-box.
A component Boolean function is an individual output bit function of an S-box, where the S-box is represented as a vector of such functions.
After the S-box has been represented in the form of component Boolean functions, the corresponding cryptographic quality criteria are applied.
The nonlinearity distance of an S-box can be defined as the minimum of the Hamming distance between its component Boolean functions and all codewords of the affine code
where
is a component Boolean function;
are the codewords of the affine
-code; and
is the operator for the Hamming distance evaluation.
An alternative way to find the nonlinearity distance of a component Boolean function
is to use the Walsh–Hadamard transform
where
is the Walsh–Hadamard transform vector of the Boolean function
that can be found using the product of its truth table represented as an exponential form
on the Walsh–Hadamard matrix
where
As is the case when estimating the nonlinearity distance in the time domain (1), when estimating the nonlinearity distance of component Boolean functions in the Walsh–Hadamard transform domain (2), the total nonlinearity distance of the entire S-box is determined as the minimum of nonlinearity distance among each of the component Boolean functions .
- 2.
Strict Avalanche Criterion (SAC) [
24].
The definition of the strict avalanche criterion of S-boxes is based on the definition of the error propagation criterion. It corresponds to the error propagation criterion [
5], which is evaluated using the minimum and maximum values of the weight of the derivatives of the component Boolean functions
along all directions
, where
is a linear vector space of vectors of length
, and
is the operator for evaluation of the Hamming weight. The ideal case, in which all derivatives (5) are balanced, i.e., their Hamming weights are equal to
, means that the component Boolean function corresponds to the strict avalanche criterion, i.e., the probability of changing its output when changing the value of any of its inputs is equal to
.
- 3.
Bit Independence Criterion (BIC) [
25].
Consider two component Boolean functions and of an S-box for given values . If the new Boolean function , formed as a superposition of these two component Boolean functions, is highly nonlinear and satisfies the SAC, then the S-box is said to satisfy the BIC. Essentially, the BIC evaluates the correlation between the component Boolean functions of the S-box, and in order for an S-box to meet the BIC, its component Boolean functions must be independent of each other.
- 4.
Linear Approximation Probability (LAP) [
26].
The linear approximation probability for an S-box is the probability that its inputs will approach its outputs linearly for a given number of input–output pairs. A weaker S-box will have a higher linear approximation probability due to its greater susceptibility to linear attacks. On the other hand, a lower linear approximation probability indicates a stronger S-box that is more resistant to linear attacks. The following formula can be used to calculate the linear approximation probability:
where
are the input and output masks, respectively, and notation [
s] denotes extraction of the
s-th bit, while
denotes the bitwise logical AND.
- 5.
Differential Approximation Probability (DAP) [
27].
The differential approximation probability of an S-box estimates the likelihood that a specific input differential of the S-box will result in a particular output differential over a specified number of rounds. This can be used to quantify the likelihood of a certain differential feature occurring within the S-box. To calculate the differential approximation probability, an exhaustive search is typically performed over all possible input and output differentials for a given number of rounds. The occurrences of each differential are counted, and the probability is calculated as the ratio of the occurrences of the desired differential to the total number of input–output pairs tested.
A lower differential approximation probability indicates that the S-box is more resistant to differential cryptanalysis. Such a probability suggests that the S-box does not exhibit any strong differentials, making it more challenging for attackers to exploit these features and break the cipher:
where
and
are the input and output differentials, respectively.
- 6.
Correlation independence of output and input vectors of the S-box [
28].
To estimate how the S-box corresponds to the correlation independence of output and input vectors, we use the maximum along the absolute values of the correlation coefficients
of the correlation matrix
, which determines the degree of the linear relationship between the output
and input
vectors of the S-box:
Lower values of indicate a higher level of cryptographic quality in the S-box.
One of the new approaches for estimating the cryptographic quality of S-boxes involves using the representation of the S-box not only in the form of component Boolean functions, but also component functions of many-valued logic, as described in [
29].
Definition 1 ([29]). A function of q-valued logic of variables is a mapping .
Many-valued logic functions are more general mathematical objects than Boolean functions. So, for value , Definition 1 is the definition of Boolean functions.
Many-valued logic involves expanding the boundaries of awareness and the formal description of the logical connections of the real world. While binary logic is generally accepted, J. Łukasiewicz [
30] drew attention to many-valued logic as a means of expressing various shades of information in sentences. After its discovery, famous mathematicians, economists, and philosophers began to implement this strategy and expressed interest in improving the quality of information transfer.
When analyzing a cipher, a cryptanalyst is not limited to the mathematical apparatus of Boolean functions but may use all possible representations of cipher constructions, particularly cryptographic S-boxes. Thus, S-boxes with four inputs of length
can be represented by four component Boolean functions or two component 4-functions (see
Table 1 [
29] for an example, which is a simplified illustration for a small S-box).
Similarly, eight-input S-boxes of length , which are the de facto standard in modern cryptographic algorithms, can be represented using eight component Boolean functions, four component 4-functions, and two component 16-functions.
On the other hand, ref. [
31] introduces a definition of an SAC for
q-functions.
Definition 2 ([31]). The weight of a q-valued vector is the number of its nonzero components.
Definition 3 ([31]). The derivative of the function with respect to the direction of the vector u is the function
where
means the modulo
q addition.
Definition 4 ([31]). The function of q-valued logic satisfies the propagation criterion with respect to the vector if its derivative in the direction u is a balanced function, i.e., values are taken with equal probabilities: for all . In other words, , where is the number of sets of variable values for which the derivative takes the value . The function of q-valued logic satisfies the propagation criterion of degree if it satisfies the propagation criterion with respect to all vectors u of weight .
Definition 5 ([31]). The function of q-valued logic satisfies the SAC if it satisfies the propagation criterion of degree 1.
In this paper, we not only evaluate the obtained S-boxes using the classical set of criteria for the cryptographic quality of component Boolean functions but also estimate their component 4-functions’ compliance with the SAC, according to the results presented in [
31].
We note that the efficient evaluation of cryptographic quality indicators, such as nonlinearity, avalanche properties, and differential uniformity, for large S-boxes is a critical and still unresolved task. In this study, we relied on efficiently written MATLAB version R2023b scripts based on vectorized and bitwise operations, which were sufficient for analyzing 8-bit S-boxes. Nevertheless, the development of general-purpose, scalable tools for evaluating large S-boxes remains an important direction for future research.
While the cryptographic analysis in this manuscript focuses on classical metrics, it is important to note that the effectiveness of modern attacks, such as deep learning-assisted differential attacks or algebraic side-channel vulnerabilities, is often influenced by the same cryptographic properties (e.g., diffusion, confusion) that are evaluated using classical methods. Future work may explore how these modern attacks interact with traditional cryptographic metrics.
Let us consider two S-box constructions that are used as source material in this paper.
One of the most practically applicable is the cryptographic S-box of the Nyberg construction [
32], which is used in the AES cryptographic algorithm.
The classical Nyberg construction is based on the multiplicative inversion of the input S-box values in the extended Galois field,
where
denotes the operation of taking an element by double modulo, and
is the primitive irreducible polynomial. For example, in the AES cryptographic algorithm, the type of primitive irreducible polynomial is fixed as
, while the specific S-box, which is built on the basis of this primitive irreducible polynomial, is presented in
Table 2 [
32].
Galois fields provide excellent confusion, which is a key property for cryptographic S-boxes. However, the diffusion achieved by Galois field constructions alone can be insufficient. To address this limitation, affine transformations are applied in the S-box design. These affine transformations improve diffusion by spreading the input values more evenly across the output, which enhances the overall cryptographic strength of the S-box. The combination of Galois field-based constructions with affine transformations ensures both strong confusion and adequate diffusion, making the design more resistant to cryptanalytic attacks.
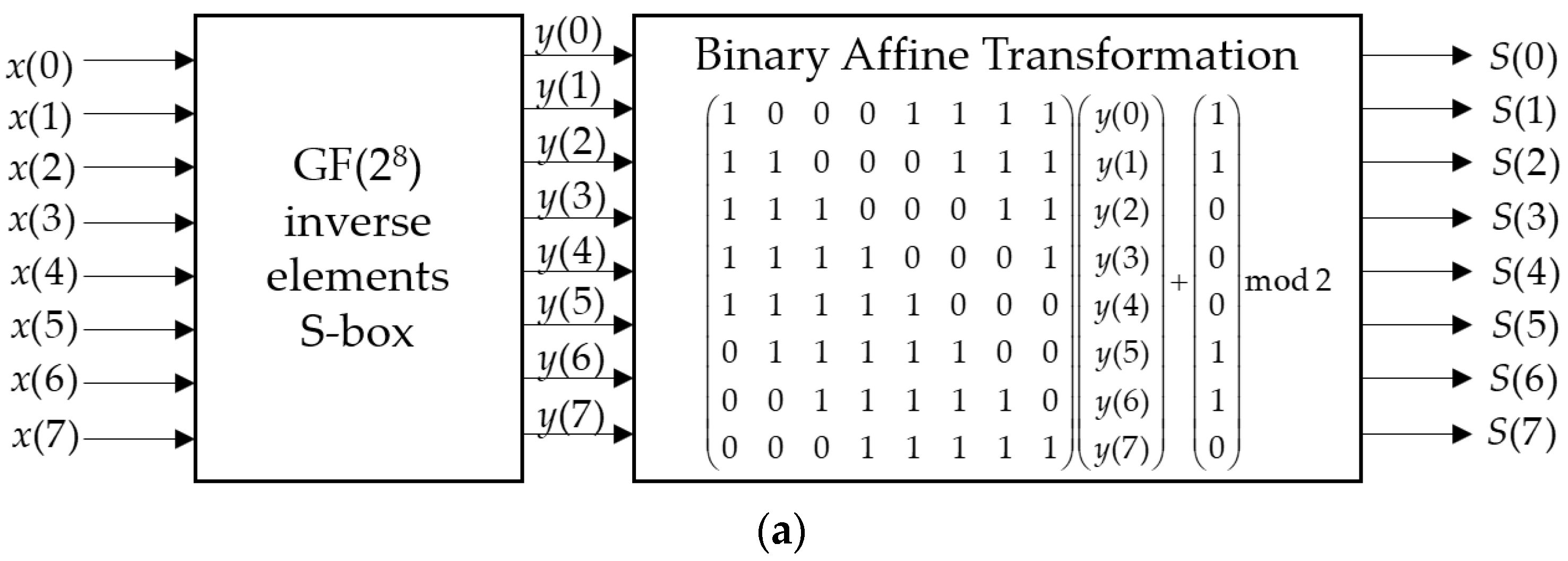
The Nyberg construction further improves the cryptographic quality of the S-box obtained using (10) by applying an affine transformation, which is specified using the following formula:
In this case, the original AES cryptographic algorithm uses the following form of the affine transformation matrix
and vector
:
Using an affine transformation can improve the cryptographic properties of the S-box. However, according to the research performed in this paper, the cryptographic properties of the S-box can be improved further using non-binary matrices of affine transformation.
The second example of the source material for the S-boxes used in this paper, together with proposed GF(4) affine transformations, are the S-boxes synthesized according to the method outlined in [
33]. To comprehensively present this material, we will briefly summarize the key steps of this method.
Step 1. Using Method M1 (Method M1 is a recursive synthesis technique that constructs S-boxes with optimal avalanche properties by combining algebraic filtering, combinatorial optimization, and many-valued logic decomposition) [
34], synthesize a set of
high-quality S-boxes of length
, which meet the strict avalanche criterion of component 4-functions and the criterion of maximum avalanche effect of component Boolean functions.
Step 2. Going through the entire set of S-boxes obtained in Step 1, decompose them into component 4-functions. After decomposing the obtained 4-functions into two component Boolean functions, select those in which both component Boolean functions meet the SAC conditions.
Step 3. From the obtained set of 4-functions, it is necessary to select those that are unique.
After duplicates have been removed from this set, obtain 769 suitable functions.
Step 4. Combining the obtained 4-functions by applying theorem [
35], generate a set of S-boxes, selecting those that are bijective. The theorem referred to in this context is Kim’s theorem, which facilitates the construction of S-boxes based on component functions. It introduces a property where all linear combinations of the component functions must be balanced. This property helps simplify the process of S-box construction.
After completing Step 4, obtain a set with the cardinality of unique S-boxes.
An example S-box is presented in
Table 3 [
33], and the values of the main indicators of the cryptographic quality of this S-box are presented further. This S-box belongs to a specific class of S-boxes that can be used in cases where ideal avalanche and correlation properties are of the utmost importance. However, the nonlinearity of this S-box is poor.
The cryptographic properties of this S-box can be improved by using a modified version of the GF(4) affine transformations scheme.
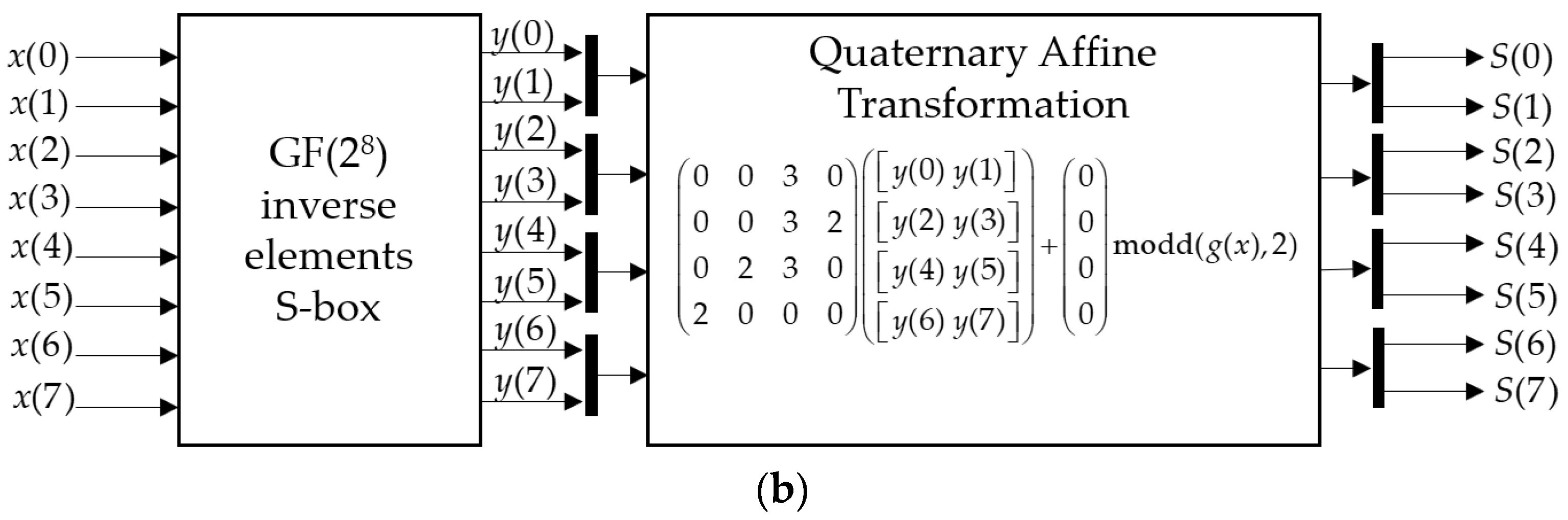
3. Results
The basic idea of the transition to GF(4) affine transformations is to rewrite (11) with respect to the arithmetic of the Galois field GF(4). The arithmetic of the Galois field GF(4) can be constructed only based on one primitive irreducible polynomial
. We present the multiplication and addition tables of the Galois field
:
Thus, we can rewrite (11) with respect to Galois field
arithmetic:
where
and
are represented as vectors consisting of elements of the Galois field GF(4), while
and
are a matrix and a vector over the Galois field GF(4). Note that when using (14) instead of (11) for an S-box of length
, vectors
,
in the case of representation over the Galois field GF(4) will consist of four elements, instead of eight, as in the case of the Galois field GF(2). Thus, to ensure the operation of the scheme, we need matrices
of the affine transformation of a two-fold smaller order (
Figure 1).
For a specific practical application of (14), it is necessary to construct matrices of the affine transformation that would ensure the bijectivity of the resulting S-box. Below, we present a method for synthesizing such matrices for practically valuable values of their orders as well as a recurrent construction for arbitrary n.
3.1. Synthesis of Matrices of GF(4) Affine Transformations of Order
The solution to the problem of synthesizing matrices of affine transformation over a Galois field GF(4) of practically important order to ensure the operation of S-boxes of practically valuable length by the exhaustive search method is associated with the enumeration of elements using fairly computationally expensive operations over the Galois field GF(4). Therefore, we propose a regular method for synthesizing these matrices based on matrices of affine transformations of lower order .
We have established the synthesis of a complete set of matrices (all possible existing structures) of affine transformation over a Galois field GF(4) that would ensure the bijectivity of the resulting S-boxes can be performed on the basis of four basic constructions:
where in
index 3 means the order
of the matrix, and index 1 means the number of structures.
In this case, the parameter includes all possible combinations of values from the given set, including repetitions.
The value always forms a constant column consisting of uncombined values, that is, only 1, or only 2, or only 3 values are possible there. There cannot be any combined values.
Note that each of the structures allows all possible row permutations, the number of which is . Thus, we can calculate the cardinality of the affine transformations generated by the structure as .
In this case, the cardinality of the sets generated by the matrices is defined as .
Thus, the total cardinality of the constructed set of affine transformation matrices is . This was confirmed by the exhaustive search method. The four constructions in Construction (15) became the basis for constructing a complete class of affine transformations of order , which have the greatest practical significance for synthesizing S-boxes.
S-boxes with a length of 256 represent a versatile and robust solution, making them highly suitable for modern cryptographic systems and practical implementations.
To construct such S-boxes, it is essential to develop new rules within the GF(4), enabling operations and mappings capable of accommodating larger S-box structures. A logical starting point is to build upon existing constructions, particularly those based on (15).
These constructions serve as the basis for generating new transformations, which can be specifically designed to meet the requirements of 256-length S-boxes.
We present a new construction for affine transformations of order
based on a matrix
:
The structure
can be extended to the case of an arbitrary order of matrices of affine transformation over GF(4), defined by the following recurrent formula:
In this case, the cardinality of the class generated by the construction is In the case of , we have .
Additionally, matrices of affine transformations over the Galois field GF(4) can be constructed on the basis of constructions
by concatenating a column and a row containing all zeros and one element
x at the crosshair. In particular, the following matrix can be constructed on the basis of the construction
:
Based on the construction
, the following matrix of the affine transformation of order
can be constructed:
Based on the construction
, we obtain the following matrix:
It is clear that the cardinality of the affine transformation matrices that can be constructed on the basis of constructions is .
Thus, the total number of affine transformation matrices over the Galois field that are synthesized based on all proposed constructions of order is .
As a result, we have constructed new rules for order of the affine transformation matrix, enabling construction of S-boxes with good cryptographic properties of length .
3.2. S-Box Synthesis
We use formula (14) to synthesize a cryptographic S-box, applying the following type of GF(4) affine transformation:
Table 4 shows the specific form of the S-box after applying the affine transformation (21) based on the S-box of the Nyberg construction (
Table 2).
The cryptographic properties of the obtained S-box, which is given in
Table 4, are shown further.
3.3. Proposed Algorithm for Affine Transformation
We have proposed a modified scheme of affine transformation over the Galois field GF(4). When combined with S-boxes [
33] that satisfy the SAC for both component Boolean functions and 4-functions, this scheme enables the creation of high-cryptographic-quality S-boxes.
According to our proposed method, the affine transformation of S-boxes is performed as follows:
where the notation
denotes taking the
-th quaternary digit of the
-th element of the S-box element, while the notation
denotes extracting the element with indices
from the matrix
, and
denotes multiplication in the Galois field following the multiplication table (13). Modified constructions of
are used as matrices
:
Our research established that the best-quality results were achieved by matrices constructed based on (23), which do not contain a value of 1 in their composition. Let us consider a specific matrix,
and then construct a new S-box using (22) and the S-box given in
Table 3, which corresponds to the SAC of component Boolean functions and 4-functions. The resulting S-box is presented in
Table 5.
In this case, the cryptographic properties of the S-box in
Table 5 are shown further.