Abstract
threshold progressive secret image sharing (PSIS) has become an important issue in recent years. In PSIS, a secret image is encrypted into n shadows such that k to n shadows can gradually reconstruct the secret image. Since an image can usually be divided into different regions in such a way that each region includes information with different importance levels, region-based PSIS has also been proposed where the reconstruction of different regions requires different thresholds on the shadow numbers. In this work, we propose new region-based PSIS that achieves a novel reconstruction model, where all regions possess the property of threshold progressive reconstruction, but the same number of shadows recovers a lower proportion of information in regions with a higher importance level. This new reconstruction model can further complete the application of region-based PSIS, where each region has an equal minimum threshold for reconstruction, and the difference in importance levels between regions can be reflected in the proportion of the recovered image using the same number of shadows. A theoretical analysis proves the correctness of the proposed scheme, and the experimental results from four secret images also show the practicality and effectiveness of the proposed scheme.
1. Introduction
The secret image sharing (SIS) scheme has become a popular issue in the field of image security in recent years. It provides a way of protecting secret images among multiple participants. In a SIS scheme, a secret image is encrypted into n shadows in such a way that it satisfies the following two rules: (1) no information is reconstructed at all when there are less than k shadows and (2) the image can be reconstructed with k or more shadows. Different from traditional image encryption and image-based information hiding, which are another two issues in the field of image security, SIS is an image protection solution that is established between multiple participants. It can solve security problems such as the tampering and leakage of secret images during transmission and storage, and it is fault-tolerant. In addition, there is no need to consider the key distribution and computational complexity of encryption and decryption in traditional image encryption. There are mainly two approaches to achieving SIS schemes. For instance, the works in [1,2,3,4,5] were visual cryptography-based SIS schemes, and the SIS schemes in [6,7,8,9] were based on Lagrange interpolation polynomials.
Recently, a new decoding model in SIS schemes, which is called progressive decoding, was proposed. This new decoding model satisfies the following rules: (1) no information of the secret image is reconstructed when there are less than k shadows and (2) k to n shadows can progressively reconstruct the image. Since the idea of progressive decoding was introduced, many SIS schemes that satisfy progressive decoding models have been proposed. Some of these can satisfy the general threshold, some can satisfy the property of smooth progressive reconstruction, some of these focus on reducing shadow size, and some of these are based on visual cryptography and other approaches. This novel decoding model in PSIS can not only solve the problem of the single-image reconstruction mode in the previous solution but also further expand the application scenarios of SIS schemes. For instance, the authors of [10] provided a PSIS scheme for traffic surveillance image management, the authors of [11] combined the Internet of Things with PSIS and proposed a secret image sharing scheme with a key information hiding function, and the authors of [12] applied PSIS to the industrial Internet.
In most previous PSIS schemes, the feature of image reconstruction is that the entire image can be progressively reconstructed from k to n shadows, and more information can be reconstructed from more participating shadows. Although this feature of progressive reconstruction is improved from the traditional threshold reconstruction, the strategy of image reconstruction can still be further improved. In this work, we constructed a PSIS scheme with a new image reconstruction strategy such that one secret image can be segmented into different regions with different importance levels, and different reconstruction strategies are applied for different regions. The theoretical analysis proves the correctness of the proposed scheme, and the experimental results also show the practicality and effectiveness of the proposed scheme. With the new image reconstruction strategy in our scheme, PSIS schemes can be further carried out in more complicated applications.
The rest of this paper is organized as follows. Section 2 provides some related works, which include the formal definition of PSIS and some results of PSIS schemes. In Section 3, we describe the proposed PSIS with the new progressive decoding model, and a theoretical analysis is used to show the correctness of our scheme. Section 4 presents the experimental results of the proposed scheme, and a comparison between the proposed scheme and other PSIS schemes is also shown in this section. Section 5 provides the conclusions of our work at the end.
2. Related Works
In this part, we provide the definition of a PSIS scheme and list some related results on existing PSIS schemes.
2.1. Definition of PSIS
Traditional SIS schemes encode a secret image into n shadows and satisfy the following two conditions: (1) k or more shadows can decode the entire image and (2) no information about the image at all is reconstructed when there is less than k shadows. PSIS schemes can also encode secret images into n shadows but satisfy a different decoding model, called the progressive decoding model, which is as follows:
- At less than k shadows, no information about the image is reconstructed.
- k to n shadows can gradually decode the image. Let the symbol be the proportion of recovered information to the entire image using t shadows; we then have .
In PSIS schemes, more participating shadows are able to recover more information about the secret image, which is reasonable in many conditions. Thus, PSIS can improve the application value of SIS.
2.2. Previous Results on PSIS
In the first polynomial-based PSIS scheme [13], 2 to n shadows can gradually decode a secret image. However, the scheme in [13] does not meet the general threshold. Later, Yang et al. [14] proposed a polynomial-based generalized PSIS, and the shadow size was reduced to of the image. Later, Yang et al. introduced another two PSIS schemes [15,16], where the progressive decoding model satisfies a smooth decoding property. The difference between the schemes [15,16] is that an equal number of shadows decode the same regions using the scheme in [15] but decode different regions using that in [16] when the shadows change. The scheme in [17] proposed a way to further reduce shadow size in previous PSIS schemes. The PSIS schemes in [13,18] are based on visual cryptography. Besides interpolation polynomial and visual cryptography, there are also other approaches for PSIS: the scheme in [19] is based on error correction codes, and the scheme in [20] is based on a GEMD data-hiding algorithm.
The main idea of previous PSIS schemes can be concluded as follows: a secret image is first segmented into multiple regions; each region is encoded into n sub-shadows using different thresholds where t can be chosen from the set . The shadow for each participant is combined with a sub-shadow from each region; thus, the entire image can be progressively decoded from an increasing number of shadows. In fact, these PSIS schemes have been combined with multiple-threshold SIS schemes for each region, and the decoding model for each region uses the threshold, where the parameter t is unchangeable. In this work, we constructed a PSIS scheme with a different progressive decoding model, where each region of the secret image satisfies a progressive decoding model, and when t shadows are involved in image decoding, the proportion of decoded information from each region is different according to the region’s importance level. The same number of shadows can recover lower proportions of information in regions with higher importance levels. This new progressive decoding model could further the applications of PSIS, such as in important applications where all regions have an equal minimum requirement for starting reconstruction, and the difference in the importance level of a region can also be reflected in the different proportions of recovered information.
3. Proposed Scheme
In this part, we construct a new PSIS scheme that satisfies the progressive reconstruction model, but it is different from previous PSIS schemes. The motivation of our work is described in Section 3.1, and the proposed scheme is then introduced in Section 3.2.
3.1. Motivation
All previous PSIS schemes can gradually decode secret images from k to n shadows. The approaches of these schemes can be summarized as follows:
- The secret image O is segmented into multiple regions .
- Each region is encoded into n sub-shadows using threshold approaches, where m is chosen from the set according to the importance level of the corresponding region.
- The shadow is a combination of all l sub-shadows that come from different l regions.
Basically, these PSIS schemes are a combination of multiple threshold SIS schemes where . One characteristic in these schemes is that a group of shadows can reconstruct some regions losslessly but cannot obtain any information about other regions at all. However, some applications segment one secret image into multiple regions, and the minimum reconstruction thresholds for all regions are equal. In other words, each of these regions satisfies a progressive reconstruction model, which is different from previous PSIS schemes. The difference in importance level between different regions can be reflected by the proportion of reconstructed information using the same number of shadows in different regions. For example, if region is more important than , both and can be gradually reconstructed from k to n shadows, but any m shadows, , can recover a larger proportion of information in than in . This new progressive reconstruction model is suitable in many situations. For instance, a traffic image O consists of three regions and that include information on the road, vehicle, and person. Any k to n authorized participants can gradually reconstruct the image, while k participants can reconstruct rough information about the type of road, the category of vehicle, and the number of persons; participants can reconstruct the road’s width, the brand of vehicle, the sex of the persons, and so on. Since the importance levels satisfy , the proportion of recovered information on region o using m shadows satisfies for any .
We can summarize the differences in reconstruction strategies between previous PSIS schemes and our proposed PSIS scheme as follows:
- Previous PSIS schemes applied the same progressive reconstruction strategy on the entire secret image.
- Our PSIS scheme first segments a secret image into different regions, where each region contains information with different importance levels, and then different progressive reconstruction strategies are applied to different regions.
3.2. Proposed PSIS Scheme
In this part, we describe a new PSIS scheme that is consistent with the motivation and then present a theoretical analysis. Before describing our scheme, we propose a new algorithm for generating n shadow pixels of one pixel. A definition of a k-group distribution vector is also proposed together with this algorithm below.
For example, let and pixel . Then, is a group of five shadow pixels of p, since . Here, we define the concept of Difference on the set V, denoted as . can be computed as . For example, if , ; if , .
Based on Algorithm 1, the proposed scheme is introduced in Scheme 1.
| Algorithm 1 n shadow pixels for one pixel |
Input: one pixel p; output: n shadow-pixels .
|
Scheme 1: Proposed PSIS scheme.
Shadow Generation phase: Input: image O; Output n shadows .
- 1
- The image O is segmented into multiple regions with different importance levels. We use the symbol to denote the importance level of ; without loss of generality, let .
- 2
- Generate k-dimensional vectors that satisfy .
- 3
- For each region , which consists of pixels ,
- (1)
- Generate a group of n shadow pixels for each pixel using Algorithm 1. All these groups of n shadow pixels use the same k-dimensional vector .
- (2)
- The n sub-shadows for region are .
- 4
- The n shadows for image O are .
Image Reconstruction phase: Input: m shadows ; output: partial image .
- 1
- Suppose that the m shadows are . Each shadow is a combination of l sub-shadows on all l regions, . Reconstruct the partial image using the equation .
- 2
- The reconstructed partial image is .
Next, we use theoretical analysis to explain the properties of the progressive reconstruction in the proposed scheme. The following Theorem 1 is the basis for Theorems 2 and 3. Theorem 2 shows that the entire secret image O can be gradually reconstructed from k to n shadows, and Theorem 3 proves that when the same number of shadows are involved in the image decoding, a larger proportion of information can be reconstructed in the region with a lower importance level.
Theorem 1.
Suppose a region o is encoded into n sub-shadows under the k-dimensional vector , then the proportion of reconstructed information on o using m sub-shadows is .
Proof.
According to Algorithm 1 and Scheme 1, a region o is encoded into n sub-shadows under the k-dimensional vector , which means that each pixel p included in o is encoded into n shadow pixels from the set of k shadow pixels under the same k-dimensional vector . When randomly choosing m shadow pixels, the pixel can be decoded correctly only when at least one shadow pixel on each is included in these m selected shadow pixels. The total number for this situations is , and the number of selected shadow pixels m out of n is ; therefore, the probability of correctly decoding pixel p from random m shadow pixels is . Since the region o consists of multiple pixels, the proportion of reconstructed information of o equals the probability of correctly decoding each pixel. Thus, the proportion of reconstructed information of region o from random m sub-shadows under a k-dimensional vector is . □
Using the conclusion in Theorem 1, we describe Theorem 2 to analyze the progressive reconstruction property of the proposed scheme.
Theorem 2.
Our scheme satisfies the progressive reconstruction model, where k to n shadows can gradually reconstruct the secret image.
Proof.
In our scheme, the secret image O is first segmented into l regions ; each region generates n sub-shadows , and the shadow is a combination of l sub-shadows that comes from each region, . In order to prove the progress reconstruction model on secret image O, we only need to prove that each region satisfies the progress reconstruction model on these n sub-shadows .
According to the conclusion of Theorem 1, any m sub-shadows can reconstruct a proportion of on the corresponding region . In order to prove the progressive reconstruction property on the region , we only need to prove . In fact, . For each combination of satisfying , there exist up to k different combinations satisfying (). Then, we can obtain that . Generally, ; then, we have . Thus, we have proven that . In addition, it is easy to prove that and when . Thus, each region in O satisfies the progressive reconstruction property, and the entire image satisfies the progressive reconstruction property as a result. □
Theorem 2 explain that our proposed scheme satisfies the progressive reconstruction property, which is the same as other progressive SIS schemes, and it also shows the difference from other schemes in that each region in the entire image also satisfies the progressive reconstruction property. The regions have different importance levels, and previous PSIS schemes adopted different thresholds for different regions. In contrast, in our scheme, for all regions subject to progressive reconstruction, the different important levels of regions can be reflected from the proportions of reconstructed information using the same number of shadows on different regions. In the following, Theorem 3 provides the proof accordingly.
Theorem 3.
In our scheme, m shadows can reconstruct a larger proportion of information about a region with a lower importance level.
Proof.
In our scheme, suppose two regions and are segmented from secret image O, where the importance levels satisfy . According to Scheme 1, sub-shadows on and are generated using two k-dimensional vectors and with . The proportions of the reconstructed information on and using any m shadows are and , respectively. Here, we are going to prove .
According to Theorem 1, these two proportions are . Thus, we only need to compare the two numerators . Without loss of generality, we consider the case where and ; then, . The following three situations are considered separately: (1) , (2) , and (3) . For case (1), . If we regard as a variable x, then is the function . In order to prove , we only need to explain that is a decreasing function, since , which means that the variable x is larger in than in . For simplicity, we use the special case that , and thus, . The first derivative of is . Because , can be deduced from . Therefore, as , is a decreasing function, and thus, . For case (2), . Since , we can obtain that . For case (3), . From the analysis of the three cases, we can obtain the conclusion that in our proposed scheme, m shadows can reconstruct a larger proportion of information about a region with a lower importance level. □
4. Experimental Results and Comparisons
In this part, we present two experiments to show the performance of the proposed scheme. In experiment 1, two PSIS schemes are used on an original image. One of them is a previous PSIS scheme, where the whole image is encrypted into shadows; 3 to 6 shadows can gradually reconstruct the image. The other is our proposed PSIS scheme, where the original image is first segmented into three regions with different importance levels, and then shadows are generated using our approach. During image reconstruction, each region can be gradually reconstructed from 3 to 6 shadows, but the same number of shadows can recover less information about a region with a higher importance level. Figure 1 and Figure 2 show the results of the image reconstruction using the previous PSIS and proposed PSIS schemes, respectively, and the percentages of the recovered image and each recovered region are listed in Table 1. From this experiment, we could see that, compared to the previous PSIS scheme, our proposed scheme can employ different progressive reconstruction models on different regions from one secret image, where each region contains information with different important levels. Therefore, our scheme can provide a more complicated progressive reconstruction model than previous PSIS schemes. This feature allows our solution to be applied to more scenarios.
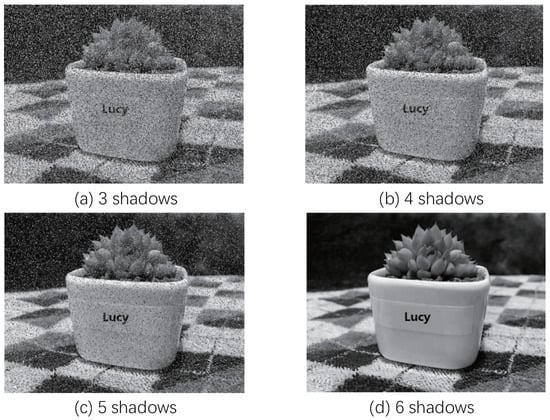
Figure 1.
Image reconstruction using previous PSIS scheme.
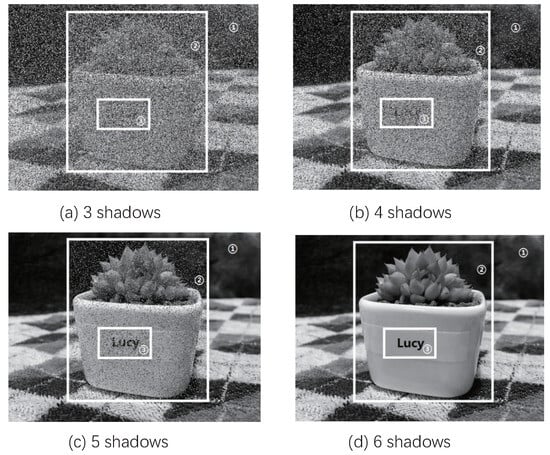
Figure 2.
Image reconstruction using proposed PSIS scheme.

Table 1.
Percentages of recovered image from two PSIS schemes.
In experiment 2, two PSIS schemes were used, a previous PSIS scheme and our proposed PSIS scheme. In both schemes, the original image was encrypted into shadows; 3 to 6 shadows can gradually reconstruct the image using the previous PSIS scheme. In our proposed PSIS scheme, the original image is first segmented into four regions with different importance levels, and then shadows are generated using our approach. During image reconstruction, each region can be gradually reconstructed from 4 to 8 shadows, but the same number of shadows can recover less information about a region with a higher importance level. Figure 3 and Figure 4 show the results of the image reconstruction using the previous PSIS and proposed PSIS schemes, respectively, and the percentages of the recovered image and each recovered region are listed in Table 2. Normally, the selection of parameters k and n depends on the specific application scenarios of secret image sharing. The parameter n is determined based on the number of users, and the parameter k is half or a little more than half of n, which matches the majority principle. In the experiments of this work, the images are simple, and we assume that there are few participants. However, in some large-scale application scenarios, the parameters of k and n can be in the hundreds or even larger than that.

Figure 3.
Image reconstruction using previous PSIS scheme.

Figure 4.
Image reconstruction using proposed PSIS scheme.

Table 2.
Percentages of recovered image using two PSIS schemes.
5. Conclusions
In PSIS schemes, an image can be gradually reconstructed from k to n shadows. Some PSIS schemes segment secret images into multiple regions with different importance levels, where more shadows can recover regions with higher importance levels. Such reconstruction models have a property ensuring that the regions can be either fully recovered or not recovered at all. In this work, we introduced a new reconstruction model for region-based PSIS, where each region can be gradually reconstructed from k to n shadows, and the same number of shadows can reconstruct a lower proportion of information about a region with a higher importance level. The theoretical analysis and experimental results prove the effectiveness of the proposed scheme. This novel reconstruction model can expand the utilization of PSIS to more applications.
Author Contributions
Conceptualization, Q.S. and Y.L.; formal analysis, Z.Y.; methodology, Y.Z.; writing—original draft, W.Z. and D.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded in part by the Natural Science Foundation of China under Grant 62172331; the Youth Innovation Team of Shaanxi Universities (No.: 2019-38); the Natural Science Foundation of Sichuan Province (Nos.: 2022NSFSC0554, 2022NSFSC0549, and 2023NSFSC0502); the Youth Innovation Team Construction of the Shaanxi Provincial Department of Education under Grants 21JP081 and 22JP059; the Natural Science Foundation of Shaanxi under Grant 2023-YBGY-271; the Guangxi Key Laboratory of Trusted Software (No.: KX202036); and the Xi’an Science and Technology Plan under Grant 22GXFW0083, 22GXFW0079.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors would like to thank the editor and the anonymous reviewers for their valuable comments.
Conflicts of Interest
The authors declare no conflicts of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| PSIS | Progressive secret image sharing; |
| SIS | Secret image sharing; |
| GEMD | Generalized exploiting modification directions. |
References
- Yang, C.N.; Chung, T.H. A general multi-secret visual cryptography schemes. Opt. Commun. 2010, 283, 4949–4962. [Google Scholar] [CrossRef]
- Shyu, S.J.; Jiang, H.W. General constructions for threshold multiple-secret visual cryptography schemes. IEEE Trans. Inf. Forensics Secur. 2013, 8, 733–743. [Google Scholar] [CrossRef]
- Hou, Y.C.; Quan, Z.Y.; Tsai, C.F.; Tseng, A.Y. Block-based progressive visual secret sharing. Inf. Sci. 2013, 233, 290–304. [Google Scholar] [CrossRef]
- Jia, X.X.; Wang, D.S.; Nie, D.X.; Zhang, C.Y. Collaborative visual cryptography schemes. IEEE Trans. Circuits Syst. Video 2018, 28, 1056–1070. [Google Scholar] [CrossRef]
- Wu, X.T.; Feng, X.J. Size invariant visual cryptography schemes with evolving threshold access structures. IEEE Trans. Multimed. 2024, 26, 1488–1503. [Google Scholar] [CrossRef]
- Thien, C.C.; Lin, J.C. Secret image sharing. Comput. Graph. 2002, 26, 765–770. [Google Scholar] [CrossRef]
- Lin, C.C.; Tsai, W.H. Secret image sharing with steganography and authentication. J. Syst. Softw. 2004, 73, 405–414. [Google Scholar] [CrossRef]
- Yang, C.N.; Ouyang, J.F.; Harn, L. Steganography and authentication in image sharing without party bits. Opt. Commun. 2012, 285, 1725–1735. [Google Scholar] [CrossRef]
- Wang, R.Z.; Su, C.H. Secret image sharing with smaller shadow images. Pattern Recognit. Lett. 2006, 27, 551–555. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Sun, Q.D. Thresholds based image extraction schemes in big data environment in intelligent traffic management. IEEE Trans. Intell. Transp. Syst. 2021, 22, 3952–3960. [Google Scholar] [CrossRef]
- Wu, W.; Peng, H.P.; Tong, F.H.; Li, L.X. A chaotic compressed sensing-based multigroup secret image sharing method for IoT with critical information concealment function. IEEE Internet Things J. 2023, 10, 1192–1270. [Google Scholar] [CrossRef]
- Xiong, L.Z.; Han, X.; Zhong, X.W.; Yang, C.N.; Xiong, N. RSIS: A secure and reliable secret image sharing system based on extended hamming codes in industrial internet of things. IEEE Internet Things J. 2023, 10, 1933–1945. [Google Scholar] [CrossRef]
- Wang, R.Z. Region incrementing visual cryptography. IEEE Signal Process. Lett. 2009, 16, 659–662. [Google Scholar] [CrossRef]
- Yang, C.N.; Shih, H.W.; Harn, L. k out of n region incrementing scheme in visual cryptography. IEEE Trans. Circuits Syst. Video Technol. 2012, 22, 799–810. [Google Scholar] [CrossRef]
- Yang, C.N.; Huang, S.M. Constructions and properties of k out of n scalable secret image sharing. Opt. Commun. 2010, 283, 1750–1762. [Google Scholar] [CrossRef]
- Yang, C.N.; Chu, Y.Y. A general (k,n) scalable secret image sharing scheme with the smooth scalability. J. Syst. Softw. 2011, 84, 1726–1733. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N. Reducing shadow size in smooth scalable secret image sharing. Secur. Commun. Netw. 2014, 7, 2237–2244. [Google Scholar] [CrossRef]
- Hou, Y.C.; Quan, Z.Y. Progressive visual cryptography with unexpanded shares. IEEE Trans. Circuits Syst. Video Technol. 2011, 21, 1760–1764. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Wu, S.Y.; Chou, Y.S. Progressive (k,n) secret image sharing schemes based on Boolean operations and covering codes. Signal Process. Image Commun. 2018, 66, 77–86. [Google Scholar] [CrossRef]
- Liu, Y.X.; Yang, C.N.; Wu, S.Y.; Chou, Y.S.; Sun, Q.D. Progressive (k,n) secret image sharing scheme with meaningful shadow images by GEMD and RGEMD. J. Vis. Commun. Image Represent. 2018, 55, 766–777. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).