Location Privacy Protection in Edge Computing: Co-Design of Differential Privacy and Offloading Mode
Abstract
1. Introduction
2. Related Work
2.1. Resource Optimization
2.2. Privacy Protection
3. System Model and Background Knowledge
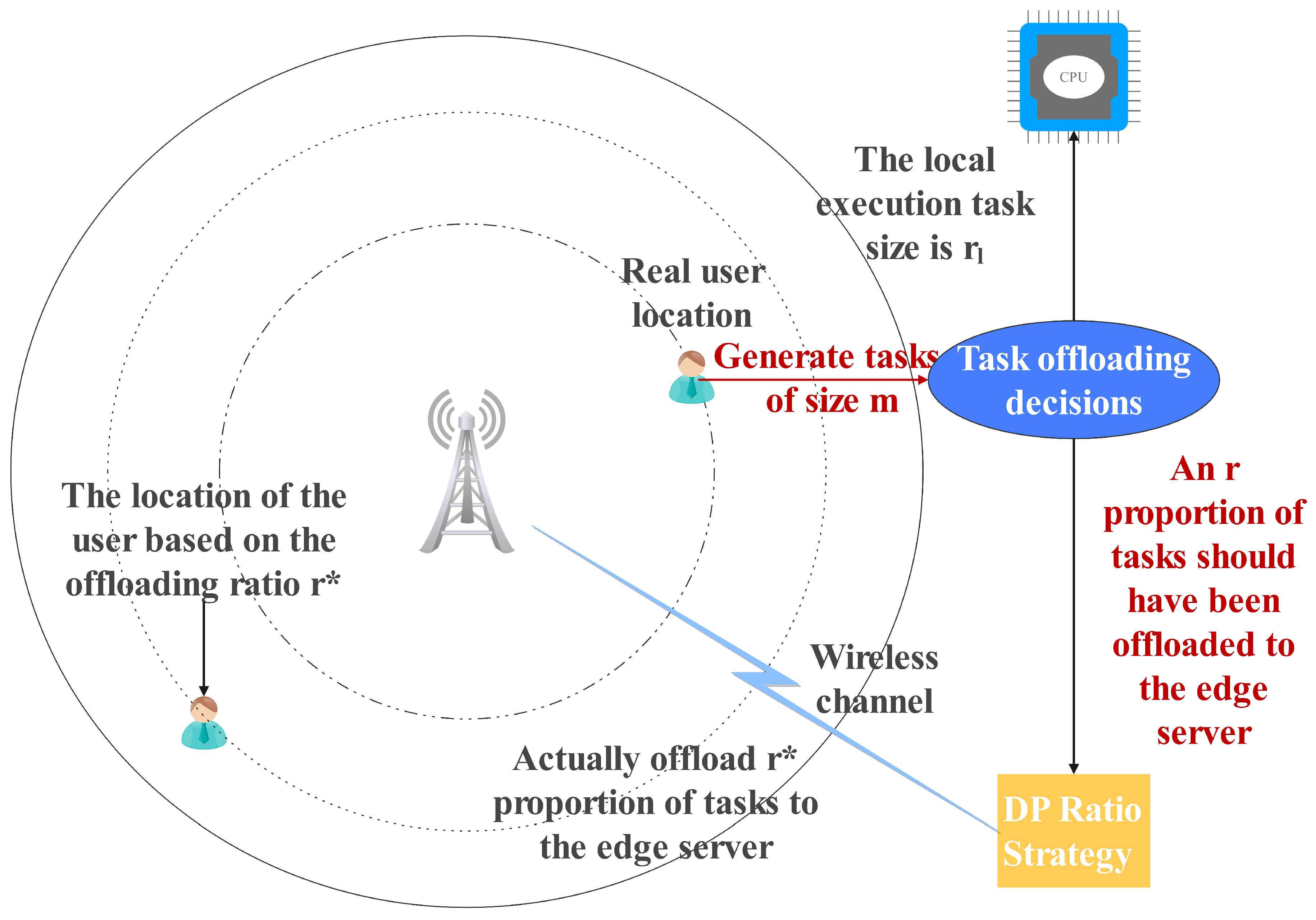
3.1. System Model
3.2. Local Computational Models
3.3. Edge Server Computing Models
3.4. Overall Calculation Models
3.5. Attack Models
4. Location Privacy-Preserving Task Offloading Optimization
4.1. Overview of Mechanism
4.2. Probability Density Function Design
4.3. Privacy Measure Function Design
5. Design of User Privacy Protection Mechanism
5.1. The Model without Privacy Protection
| Algorithm 1: Optimal offloading proportion selection algorithm without privacy |
Input: Computing power of the user’s mobile device Number of CPU cycles consumed by the mobile device to complete the task per bit User mobile device intrinsic parameters k Channel bandwidth for edge servers B Denotes the transmission power of the mobile device p Denotes background noise Denotes the wireless channel gain S Indicates the proportion of bandwidth allocated To this mobile device Denotes the computing power of the edge server Output: Unloading ratio without adding differential privacy r 1. If 2. r = 0; 3. elseif 4. r = 1; 5. elseIf 6. If and r = 0; 7. elseif and r = 1; 8. elseif 9. r = 1 when ; 10. r = 0 when ; elseif r = |
5.2. Design of Optimal Confusion Range Selection Algorithm
| Algorithm 2: Optimal confusion range selection algorithm |
Input: True unloading ratio without differential privacy r At each timestamp t, the amount of tasks generated on the user’s device side m At each timestamp t, the wireless channel condition between the user and the server R Cooling rate Initial temperature coefficient n Energy consumption factor , latency factor and privacy protection factor The law of transformation Output: upper and lower bounds on the integration of the unloaded proportional confusion function , 1. Let , . 2. Calculate the privacy preserving and unloading utility C at this upper and lower bound, so that the initial temperature . The termination temperature 3. make sth. happen , 4. Calculate the utility under new 5. If , then accept the new solution and use and as the current solution 6. If , then with probability 7. Let 8. Repeat 3–7 and stop iterating when 9. Output the final solution |
5.3. Design of Task Offloading Optimization Algorithm for Location Privacy Protection
| Algorithm 3: Task offloading optimization algorithm for location privacy protection |
Input: All inputs for Algorithms 1 and 2 Output: The proportion of offloading after obfuscation 1. Calculate the true offloading ratio according to Algorithm 1 2. Calculate the optimal confusion range according to Algorithm 2 3. Use the Pdf obfuscation function to compute the obfuscated offloading ratio |
6. Experimental Evaluation
6.1. Simulation Parameter Setting
6.2. Evaluation within the Model
6.3. Experimental Comparison among Models
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix A.1
Appendix A.2
References
- Arun, V.; Azhagiri, M. Design of Long-Term Evolution Based Mobile Edge Computing Systems to Improve 5G Systems. In Proceedings of the Second International Conference on Edge Computing and Applications, Coimbatore, India, 20–21 March 2023; Volume 979–83503–47579. [Google Scholar]
- Mouha, R.A. Internet of Things (IoT). J. Data Anal. Inf. Process. 2021, 9, 77–101. [Google Scholar]
- Wang, Y.; Zhao, S. Research on Fine-Grained Task Offloading in Mobile Edge Computing. In Proceedings of the 2023 4th International Conference on Information Science, Parallel and Distributed Systems (ISPDS), Guangzhou, China, 14–16 July 2023; pp. 526–529. [Google Scholar]
- Lu, G.; Zhang, W.; Liu, M.; Hou, R.; Gao, L. Construction of Edge Computing Cloud Service Platform Based on BP Neural Network. In Proceedings of the 2023 International Conference on Networking, Informatics and Computing (ICNETIC), Palermo, Italy, 29–31 May 2023; pp. 487–491. [Google Scholar]
- Zhang, R.; Zhou, C. A Computation Task Offloading Scheme based on Mobile-Cloud and Edge Computing for WBANs. In Proceedings of the ICC 2022—IEEE International Conference on Communications, Seoul, Republic of Korea, 16–20 May 2022; pp. 4504–4509. [Google Scholar]
- Leo, L.M.; Yogalakshmi, S.; Veeramuthu, A.; Kalist, V.; Joe, A.A.F. Experimental Analysis of Data Storage and Integrity Management over Cloud Environment using Integrated Data Security Strategy. In Proceedings of the 2022 International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; pp. 952–957. [Google Scholar]
- Hensh, F.; Gupta, M.; Nene, M.J. Mist-Edge-Cloud (MEC) Computing: An Integrated Computing Architecture. In Proceedings of the 2021 Second International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 4–6 August 2021; pp. 1035–1040. [Google Scholar]
- Ding, N.; Liu, Y.; Farokhi, F. A Linear Reduction Method for Local Differential Privacy and Log-lift. In Proceedings of the 2021 IEEE International Symposium on Information Theory (ISIT), Virtual Event, 12–20 July 2021. [Google Scholar]
- Zhang, P.; Wang, C.; Aujla, G.S.; Batth, R.S. ReLeDP: Reinforcement-Learning-Assisted Dynamic Pricing for Wireless Smart Grid. IEEE Wirel. Commun. 2021, 28, 62–69. [Google Scholar] [CrossRef]
- Wang, C.; Yuan, Z.; Zhou, P.; Xu, Z.; Li, R.; Wu, D.O. The Security and Privacy of Mobile-Edge Computing: An Artificial Intelligence Perspective. IEEE Internet Things J. 2023, 10, 22008–22032. [Google Scholar] [CrossRef]
- Pusti, B.; Sankaran, S. Security and Energy-Aware Resource Allocation in Mobile Edge Computing (MEC). In Proceedings of the 2022 IEEE International Symposium on Smart Electronic Systems (iSES), Warangal, India, 19–21 December 2022; pp. 293–296. [Google Scholar]
- Radouane, B.; Lyamine, G.; Ahmed, K.; Kamel, B. Scalable Mobile Computing: From Cloud Computing to Mobile Edge Computing. In Proceedings of the 2022 5th International Conference on Networking, Information Systems and Security: Envisage Intelligent Systems in 5g//6G-based Interconnected Digital Worlds (NISS), Bandung, Indonesia, 30–31 March 2022; pp. 1–6. [Google Scholar]
- Liu, L.; Feng, J.; Mu, X.; Pei, Q.; Lan, D.; Xiao, M. Asynchronous Deep Reinforcement Learning for Collaborative Task Computing and On-Demand Resource Allocation in Vehicular Edge Computing. IEEE Trans. Intell. Transp. Syst. 2022, 24, 15513–15526. [Google Scholar] [CrossRef]
- Mei, J.; Tong, Z.; Li, K.; Zhang, L.; Li, K. Energy-Efficient Heuristic Computation Offloading With Delay Constraints in Mobile Edge Computing. IEEE Trans. Serv. Comput. 2023, 16, 4404–4417. [Google Scholar] [CrossRef]
- Li, J.; Liang, W.; Xu, W.; Xu, Z.; Jia, X.; Zhou, W.; Zhao, J. Maximizing User Service Satisfaction for Delay-Sensitive IoT Applications in Edge Computing. IEEE Trans. Parallel Distrib. Syst. 2022, 33, 1199–1212. [Google Scholar] [CrossRef]
- Sun, J.; Gu, Q.; Zheng, T.; Dong, P.; Valera, A.; Qin, Y. Joint Optimization of Computation Offloading and Task Scheduling in Vehicular Edge Computing Networks. IEEE Access 2020, 8, 10466–10477. [Google Scholar] [CrossRef]
- Zeng, Y.; Liu, D. Computation Offloading Based on Improved Sparrow Search Algorithm in Edge Computing Scenario. In Proceedings of the 2022 International Conference on Computing, Communication, Perception and Quantum Technology (CCPQT), Xiamen, China, 28–30 October 2022; pp. 231–236. [Google Scholar]
- Wang, L.; Deng, X.; Gui, J.; Zhang, H.; Yu, S. Computation Placement Orchestrator for Mobile-Edge Computing in Heterogeneous Vehicular Networks. IEEE Internet Things J. 2023, 10, 22686–22702. [Google Scholar] [CrossRef]
- Zhuo, Z.; Dong, S.; Zheng, H.; Zhang, Y. Method of Minimizing Energy Consumption for RIS Assisted UAV Mobile Edge Computing System. IEEE Access 2024, 12, 39678–39688. [Google Scholar] [CrossRef]
- Zakarya, M.; Gillam, L.; Ali, H.; Rahman, I.U.; Salah, K.; Khan, R.; Rana, O.; Buyya, R. epcAware: A Game-Based, Energy, Performance and Cost-Efficient Resource Management Technique for Multi-Access Edge Computing. IEEE Trans. Serv. Comput. 2022, 15, 1634–1648. [Google Scholar] [CrossRef]
- Khazali, A. Joint Task Assignment, Power Allocation and Node Grouping for Cooperative Computing in NOMA-mmWave Mobile Edge Computing. IEEE Access 2023, 11, 93664–93678. [Google Scholar] [CrossRef]
- Shinde, S.S.; Bozorgchenani, A.; Tarchi, D.; Ni, Q. On the Design of Federated Learning in Latency and Energy Constrained Computation Offloading Operations in Vehicular Edge Computing Systems. IEEE Trans. Veh. Technol. 2022, 71, 2041–2057. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, G. Joint Service Caching, Resource Allocation and Computation Offloading in Three-Tier Cooperative Mobile Edge Computing System. IEEE Trans. Netw. Sci. Eng. 2023, 10, 3343–3353. [Google Scholar] [CrossRef]
- Samir, R.; El-Hennawy, H.; El-Badawy, H.M. Orchestration of MEC Computation Jobs and Energy Consumption Challenges in 5G and Beyond. IEEE Access 2022, 10, 18645–18652. [Google Scholar] [CrossRef]
- Qin, Z.; Ye, J.; Meng, J.; Lu, B.; Wang, L. Privacy-Preserving Blockchain-Based Federated Learning for Marine Internet of Things. IEEE Trans. Comput. Soc. Syst. 2022, 9, 159–173. [Google Scholar] [CrossRef]
- Asheralieva, A.; Niyato, D.; Xiong, Z. Auction-and-Learning Based Lagrange Coded Computing Model for Privacy-Preserving, Secure, and Resilient Mobile Edge Computing. IEEE Trans. Mob. Comput. 2023, 22, 744–764. [Google Scholar] [CrossRef]
- Liu, T.; Di, B.; An, P.; Song, L. Privacy-Preserving Incentive Mechanism Design for Federated Cloud-Edge Learning. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2588–2600. [Google Scholar] [CrossRef]
- Wang, H.; Fan, K.; Zhang, K.; Wang, Z.; Li, H.; Yang, Y. Secure and Efficient Data-Privacy-Preserving Scheme for Mobile Cyber–Physical Systems. IEEE Internet Things J. 2022, 9, 22375–22388. [Google Scholar] [CrossRef]
- Cao, B.; Li, Z.; Liu, X.; Lv, Z. Privacy-Preserving Task Offloading in Vehicular Edge Computing", in Privacy-Preserving Scheme for Mobile Cyber–Physical Systems. In Proceedings of the 2023 Asia Symposium on Image Processing (ASIP), Tianjin, China, 15–17 June 2023; pp. 156–160. [Google Scholar]
- Wang, Z.; Sun, Y.; Liu, D.; Hu, J.; Pang, X.; Hu, Y.; Ren, K. Location Privacy-Aware Task Offloading in Mobile Edge Computing. IEEE Trans. Mob. Comput. 2024, 23, 2269–2283. [Google Scholar] [CrossRef]
- Zhang, S.; Hu, B.; Liang, W.; Li, K.-C.; Gupta, B.B. A Caching-Based Dual K-Anonymous Location Privacy-Preserving Scheme for Edge Computing. IEEE Internet Things J. 2023, 10, 9768–9781. [Google Scholar] [CrossRef]
- Du, J.; Zhang, G.; Yuan, X.; Zang, X. P²SPA: Privacy Preservation Strategy with Pseudo-Addresses for Edge Computing Networks. IEEE Access 2024, 12, 40962–40972. [Google Scholar] [CrossRef]
- Yao, A.; Pal, S.; Dong, C.; Li, X.; Liu, X. A Framework for User Biometric Privacy Protection in UAV Delivery Systems with Edge Computing. In Proceedings of the 2024 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Biarritz, France, 11–15 March 2024; pp. 631–636. [Google Scholar]
- Jiang, B.; Li, J.; Wang, H.; Song, H. Privacy-Preserving Federated Learning for Industrial Edge Computing via Hybrid Differential Privacy and Adaptive Compression. IEEE Trans. Ind. Informatics 2023, 19, 1136–1144. [Google Scholar] [CrossRef]
- EUA Datasets. Available online: https://github.com/PhuLai/eua-dataset (accessed on 2 March 2024).
- Li, Y.; Li, L. Computation Offloading and Resource Allocation in MEC-enabled Vehicular Networks: Partial Offloading Versus Binary Offloading. In Proceedings of the 2024 7th World Conference on Computing and Communication Technologies (WCCCT), Chengdu, China, 12–14 April 2024; pp. 260–266. [Google Scholar]






| Parameters | Values | Unit |
|---|---|---|
| Channel bandwidth, B | 10 | MHz |
| Background noise, | −174 | dBM/Hz |
| Path attenuation constant, | −40 | dB |
| User CPU frequency | 1 | GHz |
| Edge server CPU frequency | 10 | GHz |
| Transmission power, p | 500 | mw |
| Density of computation, | 1000 | cycle/bit |
| Standard distance, | 1 | m |
| Computing power of the user, | 1 | GHz |
| Computing power of edge servers, | 10 | GHz |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, G.; Zhang, S.; Man, Z.; Cui, C.; Hu, W. Location Privacy Protection in Edge Computing: Co-Design of Differential Privacy and Offloading Mode. Electronics 2024, 13, 2668. https://doi.org/10.3390/electronics13132668
Zhang G, Zhang S, Man Z, Cui C, Hu W. Location Privacy Protection in Edge Computing: Co-Design of Differential Privacy and Offloading Mode. Electronics. 2024; 13(13):2668. https://doi.org/10.3390/electronics13132668
Chicago/Turabian StyleZhang, Guowei, Shengjian Zhang, Zhiyi Man, Chenlin Cui, and Wenli Hu. 2024. "Location Privacy Protection in Edge Computing: Co-Design of Differential Privacy and Offloading Mode" Electronics 13, no. 13: 2668. https://doi.org/10.3390/electronics13132668
APA StyleZhang, G., Zhang, S., Man, Z., Cui, C., & Hu, W. (2024). Location Privacy Protection in Edge Computing: Co-Design of Differential Privacy and Offloading Mode. Electronics, 13(13), 2668. https://doi.org/10.3390/electronics13132668






