Detection of False Data Injection Attacks on Smart Grids Based on A-BiTG Approach
Abstract
1. Introduction
- For the first time, an A-BiTG model is proposed for the detection of FDIAs in power grids. The A-BiTG model is able to effectively capture the diversity of local information data in power grids and enhance the model’s ability to perceive dynamic changes in the time series. Meanwhile, the model solves the common problems of gradient vanishing and explosion in neural networks and also helps the model to better capture the long-term dependencies between input information.
- Secondly, the proposed BiTCN-BiGRU parallel structure enhances the parallel processing capability of the model, enabling it to manage multiple input streams simultaneously and improving the computational speed. Furthermore, the integration of the attention layer into the BiGRU layer helps to dynamically adjust the weights of each time step in the learning process, which enhances the expressive ability of the model and improves the accuracy of the model detection.
- Finally, this study conducted experiments on the IEEE 14-bus and IEEE 118-bus datasets to evaluate the performance of the A-BiTG model. The experimental results indicate that compared to some mainstream detection models, the proposed A-BiTG model demonstrates a superior detection accuracy and precision when facing covert attacks. It also exhibits lower false positive rates, a faster convergence speed of neural networks, and better stability and robustness.
2. Related Work
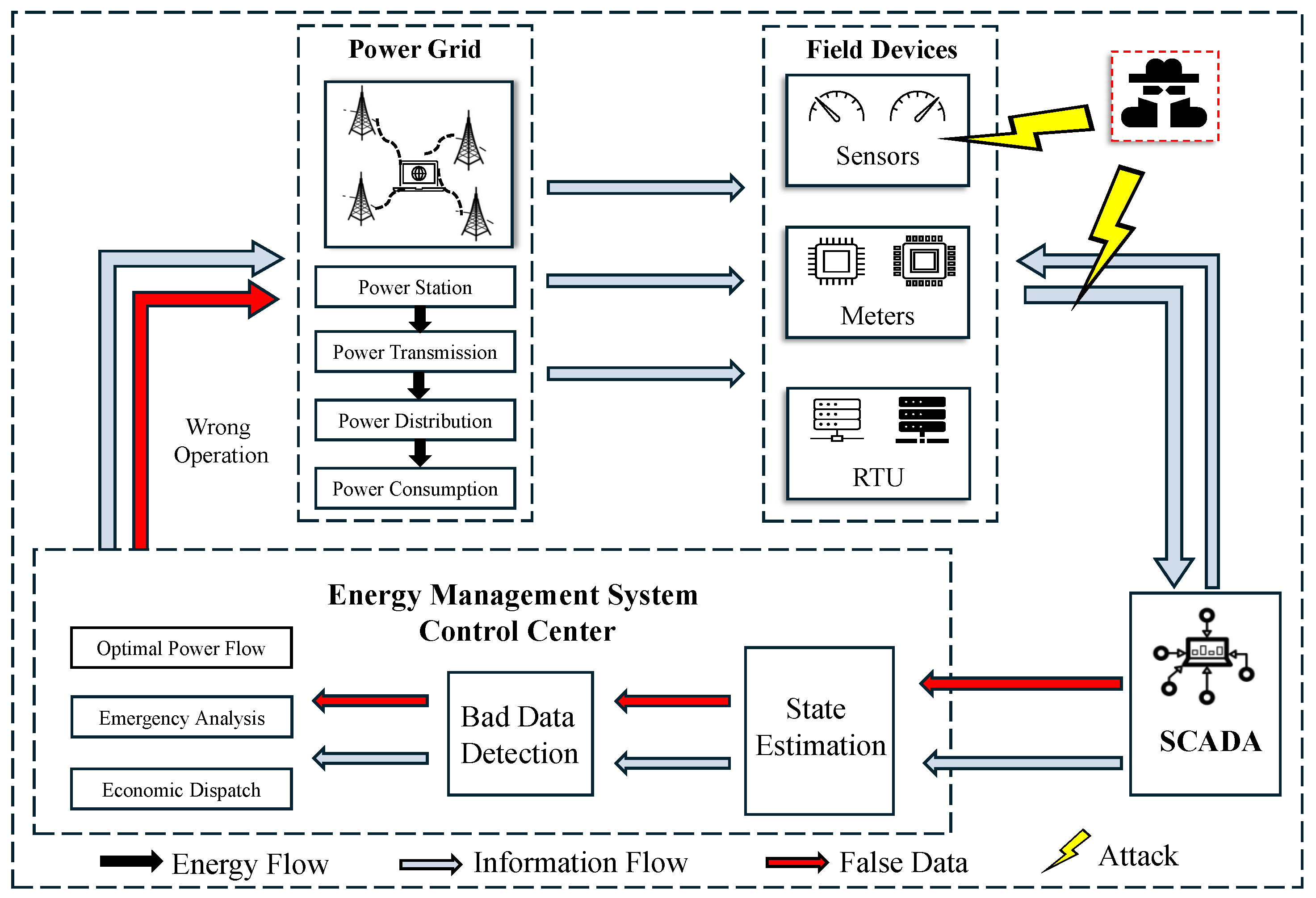
3. Model Description of Power Systems
3.1. Power System State Estimation
3.2. Bad Data Detection
3.3. False Data Injection Attacks
4. A-BiTG Detection Model
4.1. Input and Output Module
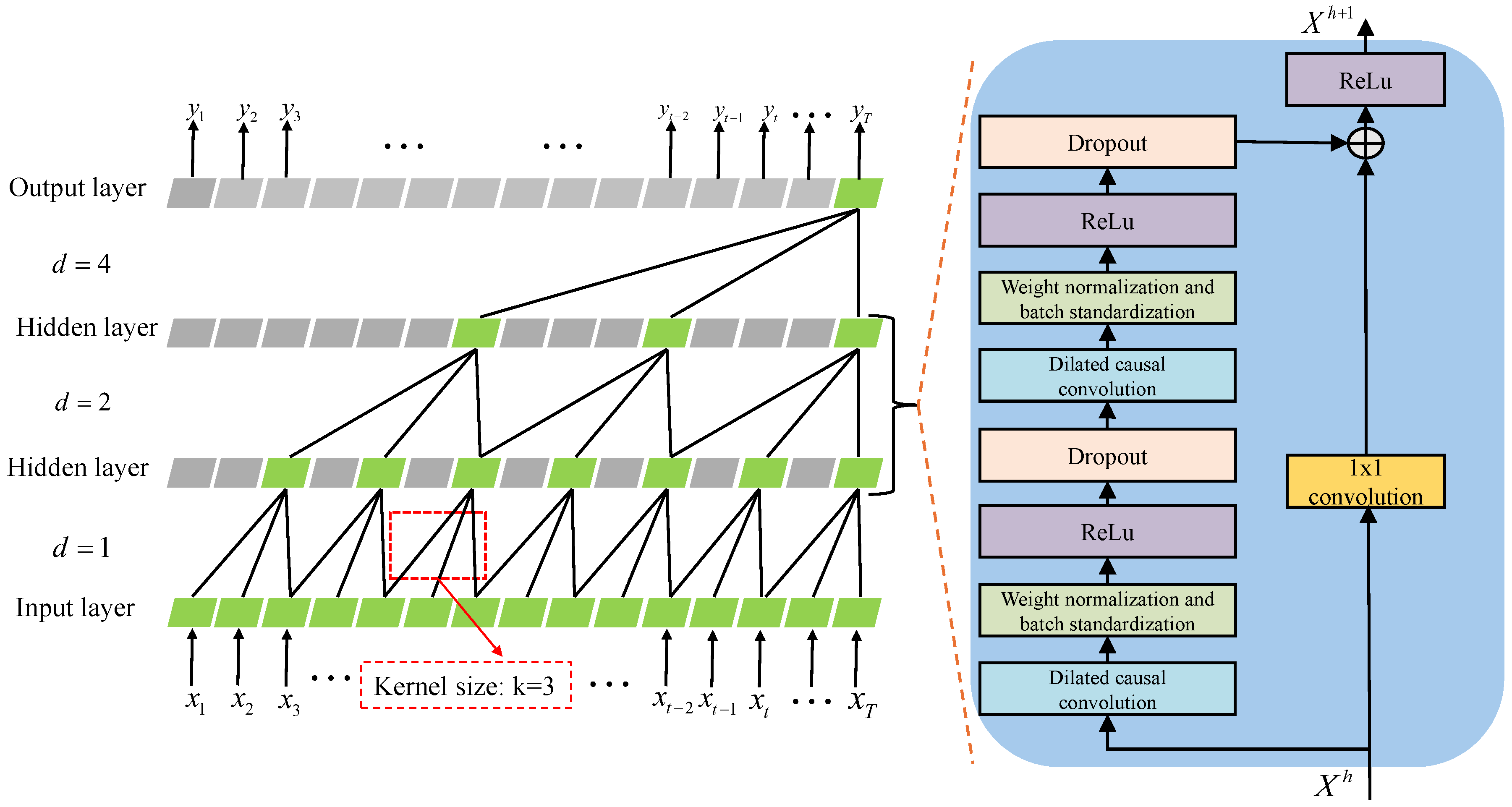
4.2. BiTCN Module
4.2.1. BiTCN Module Architecture
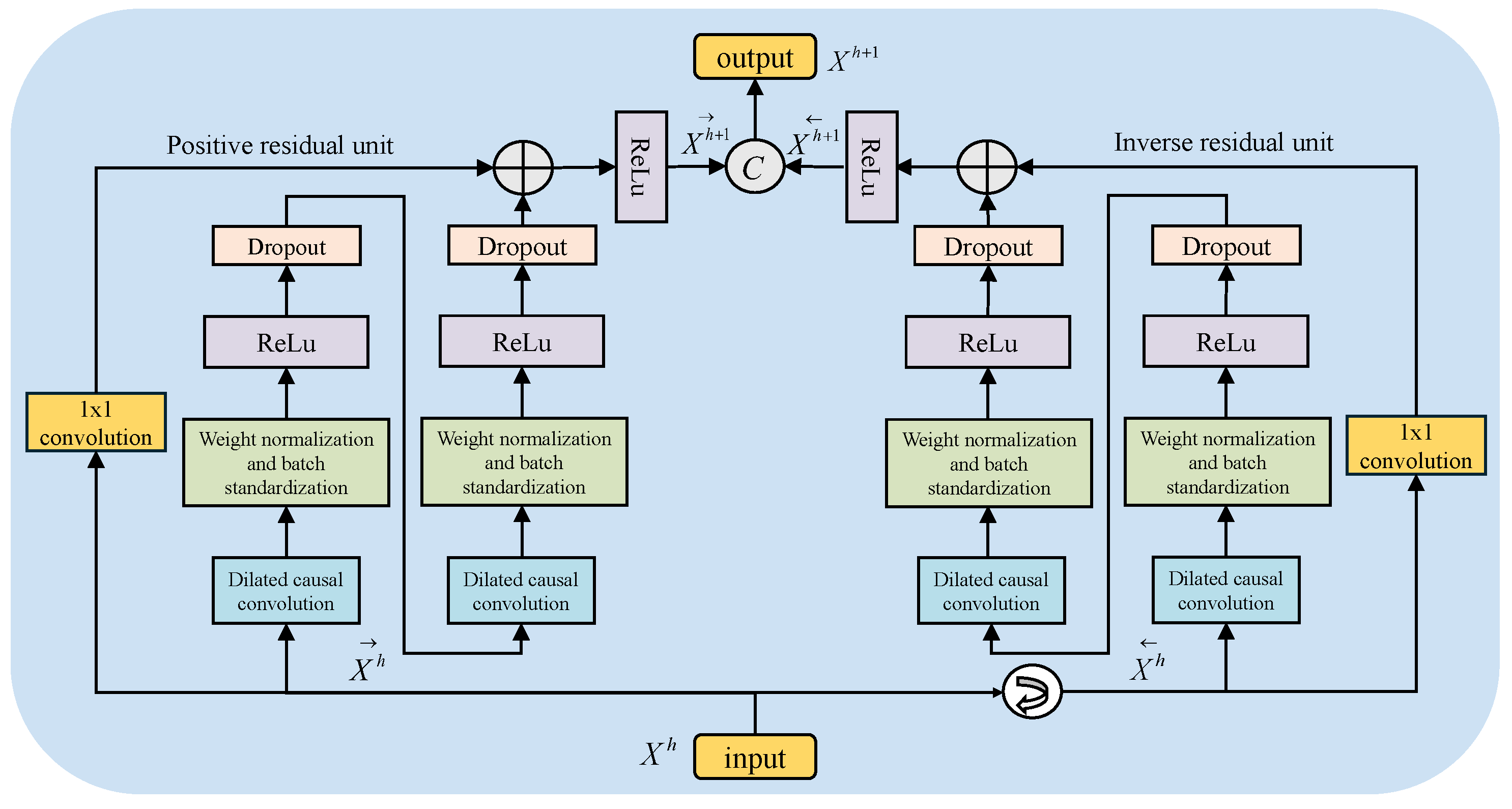
4.2.2. BiTCN Residual Block
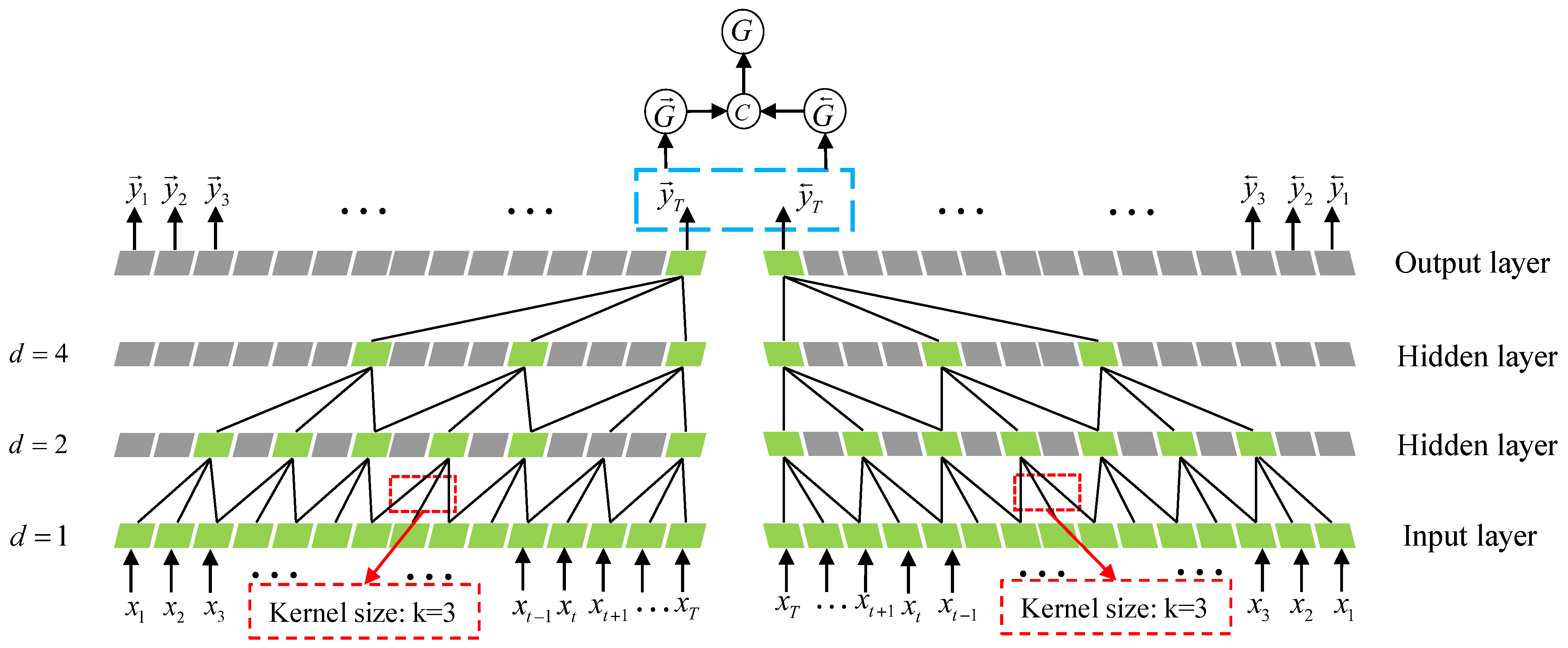
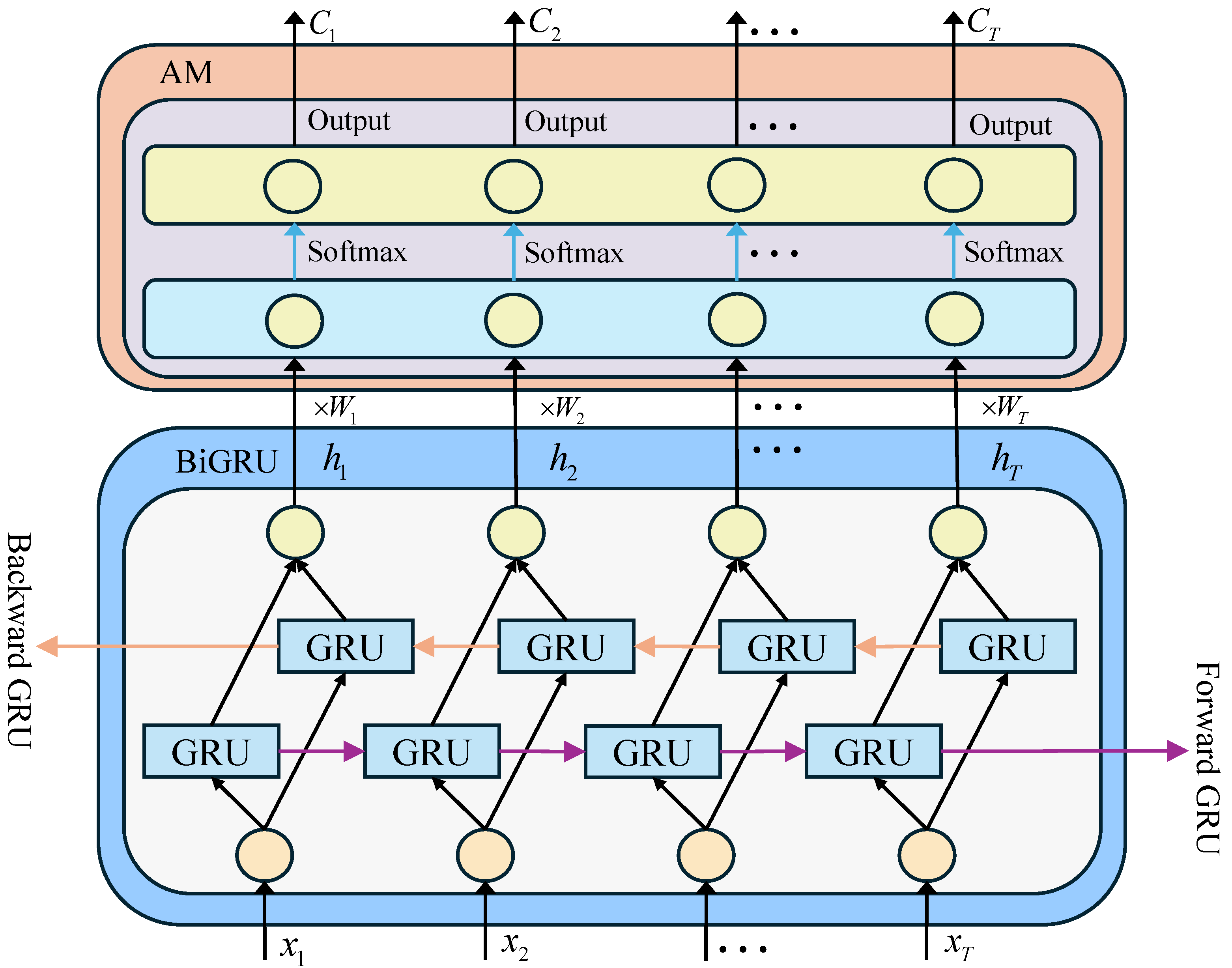
4.3. BiGRU Module
4.3.1. BiGRU Module Architecture
4.3.2. Attention Mechanism Module
4.4. The A-BiTG Overall Framework and Loss Function
4.5. FDIA Detection Steps Based on A-BiTG Model
- Preprocessing the measurement data from the SCADA system involves segmenting the processed time series data, dividing them into training and testing sets, and using them as input for the A-BiTG model.
- In the model training phase, the training set data are imported into the constructed A-BiTG model, and the model parameters are iteratively updated according to the set number of training epochs. The best-performing model is selectively chosen and saved.
- During the testing phase, the trained model is applied to the test set data for validation; then, computational model evaluation metrics are obtained, completing the model testing process.
5. Experimental Simulation and Result Analysis
5.1. Evaluation Metrics
5.2. Experimental Environment
5.3. Dataset Settings
5.3.1. FDIA Data Generation
5.3.2. Dataset Partitioning
5.4. Model Detection Performance Analysis
5.4.1. Comparison of Detection Performance of Different Models
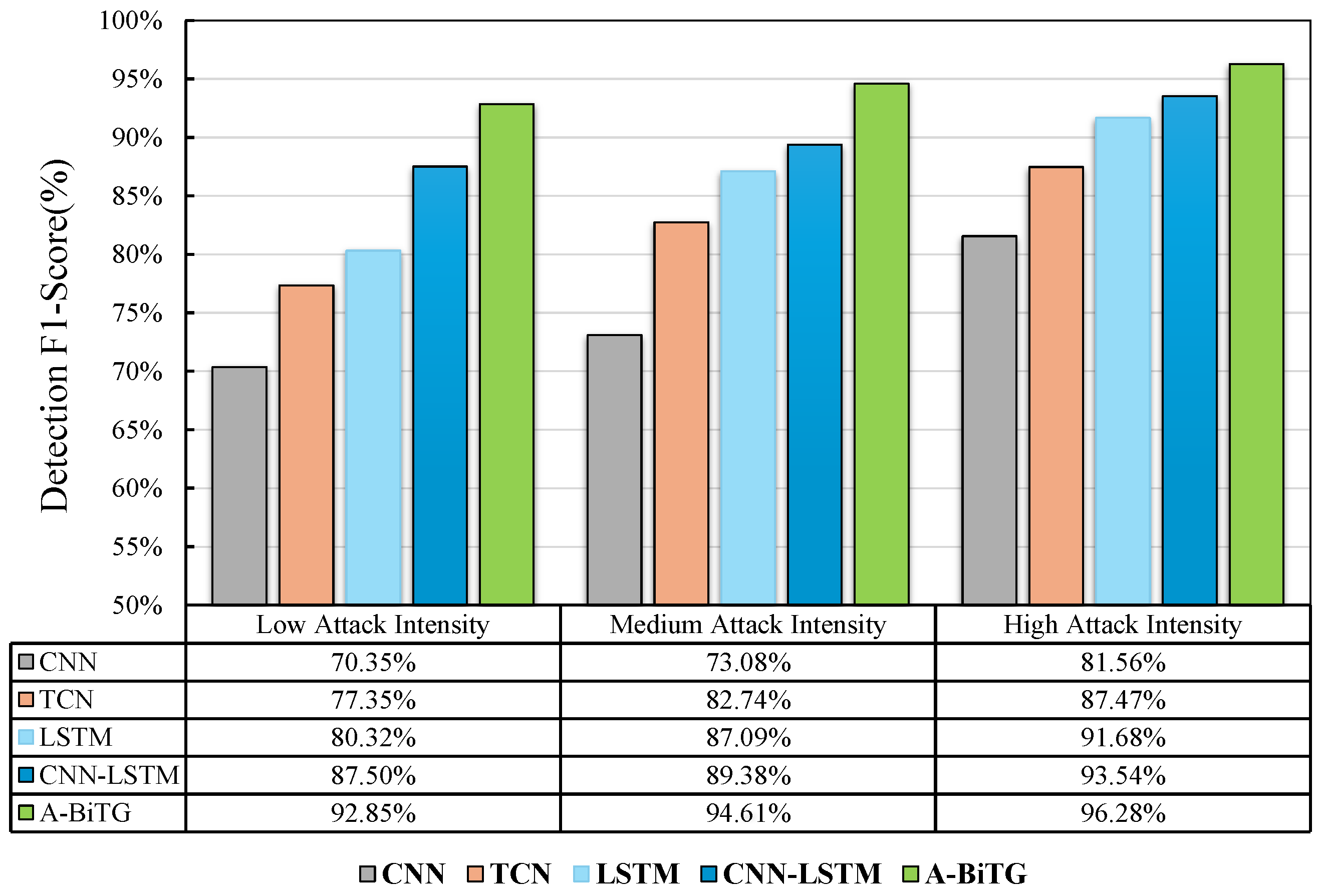
5.4.2. Impact of Attack Intensity
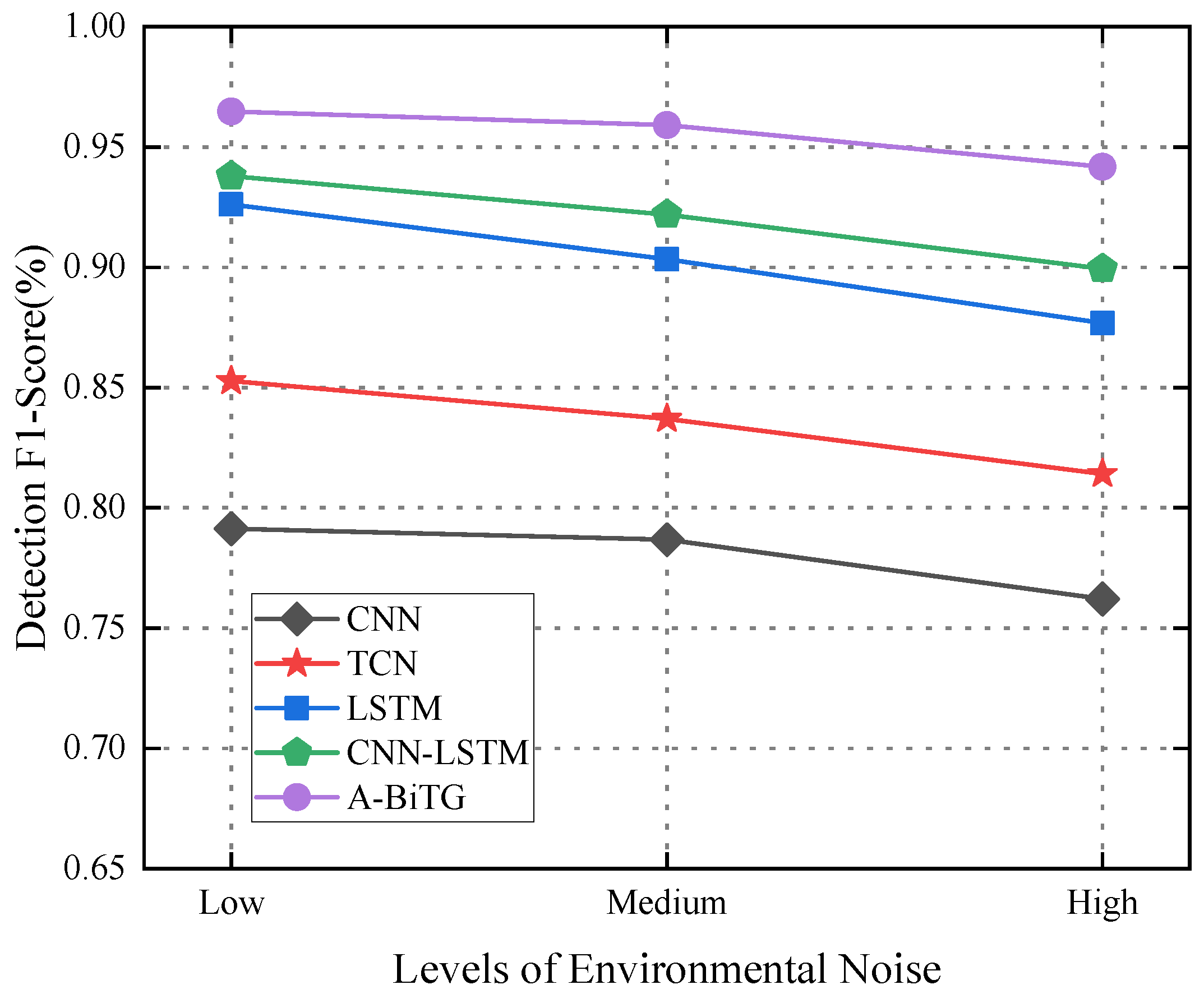
5.4.3. Impact of Environmental Noise
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Li, Y.; Wei, X.; Li, Y.; Dong, Z.; Shahidehpour, M. Detection of False Data Injection Attacks in Smart Grid: A Secure Federated Deep Learning Approach. IEEE Trans. Smart Grid 2022, 13, 4862–4872. [Google Scholar] [CrossRef]
- Jin, B.; Zhao, X.; Yuan, D. Attack–Defense Confrontation Analysis and Optimal Defense Strategy Selection Using Hybrid Game Theoretic Methods. Symmetry 2024, 16, 156. [Google Scholar] [CrossRef]
- Yang, H.; Li, T.; Yan, J.; Elvira, V. Hierarchical Average Fusion With GM-PHD Filters Against FDI and DoS Attacks. IEEE Signal Process. Lett. 2024, 31, 934–938. [Google Scholar] [CrossRef]
- Sriranjani, R.; M, B.K.; K, P.A.; Saleem, M.; Hemavathi, N.; Parvathy, A. Machine Learning Based Intrusion Detection Scheme to Detect Replay Attacks in Smart Grid. In Proceedings of the 2023 IEEE International Students’ Conference on Electrical, Electronics and Computer Science (SCEECS), Bhopal, India, 18–19 February 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Gao, S.; He, Z.; Wei, X.; Liu, Y.; Huang, T.; Lei, J. Bilevel Model for Protection-Branch Measurements-Based Topology Attack Against DC and AC State Estimations. IEEE Syst. J. 2022, 16, 5369–5379. [Google Scholar] [CrossRef]
- Baul, A.; Sarker, G.C.; Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A. XTM: A Novel Transformer and LSTM-Based Model for Detection and Localization of Formally Verified FDI Attack in Smart Grid. Electronics 2023, 12, 797. [Google Scholar] [CrossRef]
- Shen, K.; Yan, W.; Ni, H.; Chu, J. Localization of False Data Injection Attack in Smart Grids Based on SSA-CNN. Information 2023, 14, 180. [Google Scholar] [CrossRef]
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A Survey on the Detection Algorithms for False Data Injection Attacks in Smart Grids. IEEE Trans. Smart Grid 2020, 11, 2218–2234. [Google Scholar] [CrossRef]
- Mo, Y.; Chabukswar, R.; Sinopoli, B. Detecting Integrity Attacks on SCADA Systems. IEEE Trans. Control Syst. Technol. 2014, 22, 1396–1407. [Google Scholar] [CrossRef]
- Long, H.; Wu, Z.; Fang, C.; Gu, W.; Wei, X.; Zhan, H. Cyber-attack Detection Strategy Based on Distribution System State Estimation. J. Mod. Power Syst. Clean Energy 2020, 8, 669–678. [Google Scholar] [CrossRef]
- Lisheng, W.; Qian, Z. Detection of False Data Injection Attack in Smart Grid Based on Improved UKF. J. Syst. Simul. 2023, 35, 1508–1516. [Google Scholar]
- Wang, Z.; Zhang, Q.; Sun, H.; Hu, J. Detection of False Data Injection Attacks in smart grids based on cubature Kalman Filtering. In Proceedings of the 2021 33rd Chinese Control and Decision Conference (CCDC), Kunming, China, 22–24 May 2021; pp. 2526–2532. [Google Scholar] [CrossRef]
- Luo, X.; Bai, M.; Wang, X.; Sun, X. Square-root Extended Kalman Filter-based Detection of False Data Injection Attack in Smart Grids. In Proceedings of the 2021 IEEE 5th Conference on Energy Internet and Energy System Integration (EI2), Taiyuan, China, 22–24 October 2021; pp. 2376–2381. [Google Scholar] [CrossRef]
- Yang, L.; Wen, C.; Wen, T. Multilevel Fine Fingerprint Authentication Method for Key Operating Equipment Identification in Cyber-Physical Systems. IEEE Trans. Ind. Inform. 2023, 19, 1217–1226. [Google Scholar] [CrossRef]
- Rashed, M.; Gondal, I.; Kamruzzaman, J.; Islam, S. State Estimation within IED Based Smart Grid Using Kalman Estimates. Electronics 2021, 10, 1783. [Google Scholar] [CrossRef]
- Musleh, A.S.; Chen, G.; Yang Dong, Z.; Wang, C.; Chen, S. Spatio-temporal data-driven detection of false data injection attacks in power distribution systems. Int. J. Electr. Power Energy Syst. 2023, 145, 108612. [Google Scholar] [CrossRef]
- Niu, X.; Li, J.; Sun, J.; Tomsovic, K. Dynamic Detection of False Data Injection Attack in Smart Grid using Deep Learning. In Proceedings of the 2019 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 18–21 February 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Zhao, Y.; Jia, X.; An, D.; Yang, Q. LSTM-Based False Data Injection Attack Detection in Smart Grids. In Proceedings of the 2020 35th Youth Academic Annual Conference of Chinese Association of Automation (YAC), Zhanjiang, China, 16–18 October 2020; pp. 638–644. [Google Scholar] [CrossRef]
- Zhang, G.; Li, J.; Bamisile, O.; Cai, D.; Hu, W.; Huang, Q. Spatio-Temporal Correlation-Based False Data Injection Attack Detection Using Deep Convolutional Neural Network. IEEE Trans. Smart Grid 2022, 13, 750–761. [Google Scholar] [CrossRef]
- Wahid, A.; Breslin, J.G.; Intizar, M.A. Prediction of Machine Failure in Industry 4.0: A Hybrid CNN-LSTM Framework. Appl. Sci. 2022, 12, 4221. [Google Scholar] [CrossRef]
- Raghuvamsi, Y.; Kalyani, V.; Teeparthi, K.; Geetha, S.N.; Srimannarayana, Y.; Batchu, S. Temporal Convolutional Network-based Locational Detection of False Data Injection Attacks in Power System State Estimation. In Proceedings of the 2023 7th International Conference on Computer Applications in Electrical Engineering-Recent Advances (CERA), Roorkee, India, 27–29 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Su, X.; Deng, C.; Yang, J.; Li, F.; Li, C.; Fu, Y.; Dong, Z.Y. DAMGAT Based Interpretable Detection of False Data Injection Attacks in Smart Grids. IEEE Trans. Smart Grid, 2024; early access. [Google Scholar] [CrossRef]
- Gaggero, G.B.; Caviglia, R.; Armellin, A.; Rossi, M.; Girdinio, P.; Marchese, M. Detecting Cyberattacks on Electrical Storage Systems through Neural Network Based Anomaly Detection Algorithm. Sensors 2022, 22, 3933. [Google Scholar] [CrossRef]
- Zideh, M.J.; Chatterjee, P.; Srivastava, A.K. Physics-Informed Machine Learning for Data Anomaly Detection, Classification, Localization, and Mitigation: A Review, Challenges, and Path Forward. IEEE Access 2024, 12, 4597–4617. [Google Scholar] [CrossRef]
- Li, H.; Dou, C.; Yue, D.; Hancke, G.P.; Zeng, Z.; Guo, W.; Xu, L. End-Edge-Cloud Collaboration-Based False Data Injection Attack Detection in Distribution Networks. IEEE Trans. Ind. Inform. 2024, 20, 1786–1797. [Google Scholar] [CrossRef]
- Li, B.; Wu, Y.; Song, J.; Lu, R.; Li, T.; Zhao, L. DeepFed: Federated Deep Learning for Intrusion Detection in Industrial Cyber–Physical Systems. IEEE Trans. Ind. Inform. 2021, 17, 5615–5624. [Google Scholar] [CrossRef]
- Wang, Y.; Xia, M.; Yang, Q.; Song, Y.; Chen, Q.; Chen, Y. Augmented State Estimation of Line Parameters in Active Power Distribution Systems with Phasor Measurement Units. IEEE Trans. Power Deliv. 2022, 37, 3835–3845. [Google Scholar] [CrossRef]
- Abur, A.; Expósito, A.G. Power System State Estimation: Theory and Implementation; CRC Press: Boca Raton, FL, USA, 2004. [Google Scholar]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 13. [Google Scholar] [CrossRef]
- Jorjani, M.; Seifi, H.; Varjani, A.Y. A Graph Theory-Based Approach to Detect False Data Injection Attacks in Power System AC State Estimation. IEEE Trans. Ind. Inform. 2021, 17, 2465–2475. [Google Scholar] [CrossRef]
- Bai, S.; Kolter, J.Z.; Koltun, V. An Empirical Evaluation of Generic Convolutional and Recurrent Networks for Sequence Modeling. arXiv 2018, arXiv:1803.01271, 01271. [Google Scholar]
- Wang, Y.; Chen, J.; Chen, X.; Zeng, X.; Kong, Y.; Sun, S.; Guo, Y.; Liu, Y. Short-Term Load Forecasting for Industrial Customers Based on TCN-LightGBM. IEEE Trans. Power Syst. 2021, 36, 1984–1997. [Google Scholar] [CrossRef]
- Xuan, B.; Li, J.; Song, Y. BiTCN malware classification method based on multi-feature fusion. In Proceedings of the 2022 International Conference on Image Processing, Computer Vision and Machine Learning (ICICML), Xi’an, China, 28–30 October 2022; pp. 359–364. [Google Scholar] [CrossRef]
- Chung, J.; Gulcehre, C.; Cho, K.; Bengio, Y. Empirical Evaluation of Gated Recurrent Neural Networks on Sequence Modeling. arXiv 2014, arXiv:1412.3555. [Google Scholar]
- Bahdanau, D.; Cho, K.; Bengio, Y. Neural Machine Translation by Jointly Learning to Align and Translate. arXiv 2016, arXiv:1409.0473. [Google Scholar]
- Zhang, Y.; Wang, J.; Chen, B. Detecting False Data Injection Attacks in Smart Grids: A Semi-Supervised Deep Learning Approach. IEEE Trans. Smart Grid 2021, 12, 623–634. [Google Scholar] [CrossRef]
- Feng, H.; Han, Y.; Si, F.; Zhao, Q. Detection of False Data Injection Attacks in Cyber-Physical Power Systems: An Adaptive Adversarial Dual Autoencoder with Graph Representation Learning Approach. IEEE Trans. Instrum. Meas. 2024, 73, 9000411. [Google Scholar] [CrossRef]





| Dataset | Labels | ||
|---|---|---|---|
| Normal Samples | FDIA Samples | Total Samples | |
| Training | 5600 | 5600 | 11,200 |
| Test | 2400 | 2400 | 4800 |
| F1-Score | |||||
|---|---|---|---|---|---|
| CNN | 81.91% | 80.84% | 80.72% | 78.72% | |
| TCN | 85.03% | 92.33% | 76.37% | 83.60% | |
| LSTM | 91.83% | 95.10% | 87.18% | 91.42% | |
| CNN-LSTM | 93.23% | 93.61% | 93.18% | 93.39% | |
| A-BiTG | 96.23% | 95.47% | 97.27% | 96.37% |
| F1-Score | |||||
|---|---|---|---|---|---|
| CNN | 80.75% | 82.55% | 78.04% | 78.68% | |
| TCN | 84.60% | 88.77% | 79.17% | 83.70% | |
| LSTM | 90.13% | 88.48% | 92.26% | 90.33% | |
| CNN-LSTM | 92.03% | 92.77% | 91.62% | 92.19% | |
| A-BiTG | 95.77% | 95.14% | 96.69% | 95.91% |
| Model Methods | Total Training Time of the Models(s) | |
|---|---|---|
| IEEE 14 | IEEE 118 | |
| CNN | 71.26 | 697.19 |
| TCN | 82.18 | 842.43 |
| LSTM | 89.45 | 975.78 |
| CNN-LSTM | 124.37 | 1229.19 |
| A-BiTG | 115.64 | 1075.69 |
| Model Methods | Low Attack Intensity | Medium Attack Intensity | High Attack Intensity | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Accuracy | Precision | Recall | Accuracy | Precision | Recall | Accuracy | Precision | Recall | |
| CNN | 76.98% | 79.06% | 73.56% | 80.18% | 81.18% | 77.55% | 86.30% | 85.93% | 87.66% |
| TCN | 80.51% | 82.31% | 77.80% | 84.87% | 82.42% | 88.58% | 90.73% | 88.34% | 94.42% |
| LSTM | 86.87% | 86.85% | 86.85% | 89.30% | 87.60% | 91.52% | 92.87% | 90.53% | 96.17% |
| CNN-LSTM | 90.93% | 90.22% | 91.29% | 91.70% | 90.02% | 94.29% | 95.03% | 94.21% | 96.23% |
| A-BiTG | 94.33% | 96.96% | 91.79% | 95.77% | 96.39% | 95.32% | 97.15% | 98.84% | 96.72% |
| Model Methods | Low Attack Intensity | Medium Attack Intensity | High Attack Intensity | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Accuracy | Precision | Recall | Accuracy | Precision | Recall | Accuracy | Precision | Recall | |
| CNN | 73.49% | 75.31% | 70.04% | 76.02% | 76.45% | 73.40% | 83.49% | 85.52% | 80.92% |
| TCN | 79.73% | 80.64% | 77.15% | 82.10% | 79.79% | 85.91% | 88.00% | 91.35% | 83.91% |
| LSTM | 82.34% | 83.75% | 79.59% | 86.30% | 82.26% | 92.52% | 91.73% | 94.86% | 88.70% |
| CNN-LSTM | 87.43% | 86.90% | 88.12% | 89.53% | 90.55% | 88.25% | 93.37% | 93.51% | 93.57% |
| A-BiTG | 92.67% | 90.49% | 95.33% | 94.31% | 91.87% | 96.53% | 96.42% | 98.15% | 94.82% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, W.; Liu, W.; Wen, C.; Yang, Q. Detection of False Data Injection Attacks on Smart Grids Based on A-BiTG Approach. Electronics 2024, 13, 1938. https://doi.org/10.3390/electronics13101938
He W, Liu W, Wen C, Yang Q. Detection of False Data Injection Attacks on Smart Grids Based on A-BiTG Approach. Electronics. 2024; 13(10):1938. https://doi.org/10.3390/electronics13101938
Chicago/Turabian StyleHe, Wei, Weifeng Liu, Chenglin Wen, and Qingqing Yang. 2024. "Detection of False Data Injection Attacks on Smart Grids Based on A-BiTG Approach" Electronics 13, no. 10: 1938. https://doi.org/10.3390/electronics13101938
APA StyleHe, W., Liu, W., Wen, C., & Yang, Q. (2024). Detection of False Data Injection Attacks on Smart Grids Based on A-BiTG Approach. Electronics, 13(10), 1938. https://doi.org/10.3390/electronics13101938






