Abstract
Security protocols are the basis of modern network communication, proving that the security problem of protocols is one of the hot research topics today. The data in industrial IoT are usually transmitted through insecure channels, which brings certain security risks. The Logic of Events is a formal method for proving the security properties of protocols based on event systems. The new theoretical extension is based on the Logic of Events theory, which proposes new event classes Compurte, TimeGap, Construct, and Reconstruct and an axiom AxiomRe and related inference rules for malicious attacks and security privacy issues in emerging protocols, as well as extending the matching descriptions of protocol behaviours in complex cryptographic algorithms and information sharing techniques for applications for the formal analysis of authentication protocols for the Industrial Internet of Things. Finally, formal analysis is carried out using the example of a secure multi-factor authentication protocol for the industrial IoT, which proves the security of the protocol.
1. Introduction
The Internet of Things (IoT) plays an indispensable role in the smart era. IoT data are extremely private and valuable, and privacy protection and secure communication have always been the focus of attention [1]. Data are often transmitted through insecure channels, which gives rise to security and privacy issues arising from malicious attacks on the IoT [2]. In order to defend against malicious attacks by adversaries and to secure the transmitted data, researchers have proposed a large number of key negotiation schemes, which require the formal analysis of the security properties of security protocols [3]. The commonly used formal methods include theorem proving [4] and Model Checking [5]. Currently, the commonly used formal description techniques for protocols include the finite state machine model, the Petri net model, the Logic of Events theory, and the Common Authentication Protocol Specification Language (CAPSL) [6].
The Logic of Events theory is a theorem-proving formal logic used for analysing the security of distributed systems [7]. In 2009, Xiao Meihua et al. [8,9,10] used the Logic of Events for the first time in the formal analysis of security protocols. The Logic of Events theory mainly includes event systems, axiom systems, inference rules, and formal description protocols. The Logic of Events theory can formally describe cryptographic protocols and security properties by deriving the interactions between honest subjects in cryptographic protocols without analysing the behaviour of the attackers [11].
The multi-factor authentication protocols for the Industrial Internet of Things aim at fulfilling user authentication and key agreement schemes dealing with security and privacy issues. In 1991, Chang et al. pioneered a smartcard-based authentication scheme, which is also the basis of a three-factor authentication scheme [12]. In 2014, Yuan [13] first used finger-print-based biometrics to implement a lightweight authentication protocol for wireless sensor networks, but it was later shown to be incapable of resist offline password guessing attacks, privileged insider attacks, and gateway node masquerading attacks, and offers no protection against interrogation results. In 2017, Srinivas et al. [14] demonstrated that the Das scheme is not able to withstand denial-of-service attacks and node intrusion attacks. To secure communication in wireless sensor networks, Srinivas et al. proposed an improved authentication scheme that addresses the irreversibility and privacy issues of traditional biometrics. In 2018, Wang et al. [15] found that Srinivas et al.’s scheme is susceptible to offline guessing attacks and does not support users’ anonymity. In 2018, Li et al. designed an IoT-oriented three-factor authentication scheme using biometrics for the Internet and proposed a three-factor authentication scheme based on ECC (Elliptic Curve Cryptography), but the scheme could not resist smart card loss attacks and did not provide forward security. In 2019, Guo et al. [16] found that the protocol of Wu et al. could not resist offline password and identity guessing attacks, insider attacks, and user tracking attacks, sensor forgery attacks, and proposed a provably secure three-factor AKA (authentication and key agreement) protocol for mobile lightweight devices based on extended chaotic mapping. In 2020, Yu et al. [17] combined IoT with cloud computing and proposed an improved IoT-based authentication scheme for cloud computing environments.
This paper develops a theoretical extension related to the security and privacy issues arising from malicious attacks in IoT protocols based on the Logic of Events (LoET). The secure multi-factor authentication protocol [18] for the industrial IoT is defined as an example, and a formal description of the protocol is given to prove the security of the protocol. The contributions of this paper are as follows:
- The introduction of the computational event class with corresponding inference rules extends the ability of Logic of Events to describe algorithms;
- The definition of is given, and the relationship of time during protocol interaction is given according to its definition;
- The and the corresponding axiom are introduced for describing the key decomposition and reconstruction, and successfully proving some of the security properties of multi-factor authentication protocols for the Industrial Internet of Things.
The paper is organised as follows: Section 1 introduces the Logic of Events and related theories and proposes related extensions based on the Logic of Events; Section 2 introduces the secure multi-factor authentication protocol for the industrial IoT; Section 3 provides a detailed proof of the secure multi-factor authentication protocol for the industrial IoT; and Section 4 concludes the paper.
2. Logic of Events Theory
The Logic of Events Affiliation Theorem-Proving Method is a formal method that is based on the design of message automata and defines the possible protocol actions. The method provides new proof rules and mechanisms for protocol actions by assigning keys, challenge numbers, and different types of messages. The security of cryptographic protocols can be verified through the Logic of Events theory approach, which constructs an authentication theory by defining events, event classes, and event structures and proves the strong authentication nature of the protocol.
2.1. Basic Concepts
Security protocols can be abstracted into a model with addresses and events as basic types that have the characteristics of concurrent systems, including temporality and spatiality. The different addresses communicate with each other through message interactions. Information is stored in the addresses in various forms and passed between the different addresses according to different message forms. To describe the different message forms, the following table lists the interpretation and semantics of some of the Logic of Events symbols. The basic notations and semantics are given in Table 1.

Table 1.
Basic symbols and semantics.
There are three main proto-type values used to construct the Logic of Events theory authentication, including Boolean values, identifiers, and atomic types. Boolean values are used to determine the truth and falsehoods, identifiers are used to separate the subjects, and the atomic type denotes unguessable information, where the members are denoted by , and are unpredictable. -type members are basic elements that have no structure and cannot be generated. is the first step in building a model, the computational system is a generic model in distributed systems, i.e., message automata.
Independence refers to the logical theory of events that defines to denote the state in which the subject emerges after the event occurs, and the event is essentially a space or point in time. , it is a term of the paradigm , of which is a parameter. The independence proposition is true if, and only if, is the value , and exists, satisfying .
Event structure is the formal model of distributed computing that can be defined for distributed system arithmetic and authentication. In computing, messages such as , , are migrated, and the initial stage of information interaction is . The set of events is the spatial time point of the appearance of the event in some storage location of the message (e.g., the subject at the time of the event processes, or threads); the events do not overlap at a single location time point because it they have an overall order. Regardless of any migration (message passing and message sharing), causal sequences are generated between the subjects of the event.
2.1.1. Threads and Matching Sessions
A thread is an ordered list, the elements of which are the actions of a single state, but at a given location, and its formal formula is defined as follows.
and are two threads. There is a sequential or causal relationship between and . That is, both threads, and , may occur adjacent to each other before the other, and there is a causal relationship. The only information interacting in the threads is and , and the corresponding actions and .
If two messages exist, and , where message is a sending message, and message is a receiving message with the same content as message , then message forms a weak match with message , denoted as . If a sequential relationship between message and message exists, in which message is preceded by message , then there exists a direct causal relationship between message and message , and then a strong match is formed, denoted as .
2.1.2. Protocol Descriptions
LoET defines the protocols using basic sequences of the type Basic, which are formally described as predicates on state relations. One can formally define the protocol Pr steps as follows: assume that an honest subject A that follows the protocol, and that subject B is also an honest subject that follows the protocol. If subject A initiates an instance of a basic sequence, subject B initiates a response sequence that forms a legitimate matching dialog with A’s sequence, and the first and second message-matching sessions in the basic sequence of the protocol are formed from the above instance.
2.1.3. Event Class
An event class () refers to the Logic of Events theory using event sequences and another key concept event class, which describes the protocol by categorising the events in the protocol. During the protocol operation, there are message sending and receiving, challenge number generation, signing, signature verification, and encryption and decryption events; events in each class have associated information, and the type of this information depends on the event class. The following is a list of types of these seven event classes:
2.1.4. Key Axiom
Key axioms () specify the relationships between the keys. These relationships include key matching, which is a symmetric relationship. When using symmetric encryption algorithms, the key matches itself, whereas in asymmetric encryption algorithms, the subject’s private key is matched only with the corresponding public key. The public key is usually represented by a subject identifier, and different subjects will not have the same private key. This means that each subject’s private key is unique. The function is defined to represent the matching relationship between two keys, and the function is defined to assign an private key to each subject. The details are shown below:
2.1.5. Honest Axiom
Honesty axioms ( and ), according to the Logic of Events theory, contain the function , which makes an assumption about the honest subject and that the honest subject’s private key will not be released. The signature event, encryption event and decryption event all occur on the current honest subject, and the honesty axiom characterises the nature of the honest signer as follows:
2.1.6. Causal Axioms
Causal axioms () are the event axioms corresponding to receive , verify , and decrypt in the event class, and the relationship between the receive axiom , verify axiom , and decrypt axiom is integrated. The receive axiom is similar to the verify axiom in that any receive or verify event is preceded by a corresponding send or sign event with the same message content. The formal expression is as follows:
The decryption axiom indicates that any decryption event must be preceded by a corresponding encryption event, and that the encryption and decryption events have the same plaintext and ciphertext, and the ciphertexts match, as defined below:
2.2. Event Classes and Related Axiomatic Extensions
Among the current emerging protocols, the protocol encryption mechanisms are more diverse, and the behaviour of the participants is more complex, so four new event classes and a new axiom are proposed to describe the protocols more accurately.
2.2.1. Compute
The information associated with the event in the event class is of type ternary. If an event exists that satisfies with , then the event on the subject encrypts the data item using a hash function and generates the encrypted message . Once a responder receives the message, then also holds. In other words, applies to both the senders and responders.
2.2.2. TimeGap
An honest subject exists with events and , and an honest subject exists with events and , where . The honest subject sends a message containing , and the honest subject receives a message containing and records the current time and compares the size of the two to generate , which is used to verify that the time interval is within a reasonable range, i.e., ; the formal definition of the time interval is as follows:
2.2.3. Construct
The event class has an event with the ternary type. A number of subjects exist, in which the event is divided into at least parts, and and are indivisible. Each subject gets one of these parts . A single subject cannot learn anything about because they only hold one of the and cannot derive the other points.
2.2.4. Reconstruct
Event class : There are events in which there are ternary types. An honest subject exists that receives from multiple participants and reconstructs . Note that at least are needed here to reconstruct , and a lack of enough will cause the reconstruction to fail.
2.2.5. Reconstruct Axioms
Reconstruction axiom (): In the event classes and , the event has the type ternary. If there is an event that satisfies and has , then the subject of the event occurs when splits the secret value into a number of interconnected sub-secrets to be distributed to the authorised participants, and . If there is an event that satisfies and has , then the authorised participants can reconstruct the secret value using the established method by sending the sub-secret to the trusted participants. The formal expression is as follows:
2.3. Proof of Agreement Process
The proof process of a protocol consists of a formal description and the derivation of security properties. The following is a simplified proof process:
- Formally describe the protocol using Logic of Events theory approach to define the sequences of initiator and responder actions and to standardise the basic sequences of the protocol. Confirm that the strong authentication property to be proved satisfies the security requirements of the protocol.
- Perform one-way proofs of the strong authentication properties. Assuming that all the participants are honest and comply with the protocol, define an instance of the basic sequence of the protocol and determine the actions and matching events on the instance. Analyse the matching events to determine if a matching session exists and if there are matching events within the matching session that require further proofs.
- Perform match event exclusion analysis. Check whether the relevant matching event matches the matching session, and if it does, perform the inside-out proof of the matching session; if it does not, perform the next round of screening proof of the matching event to confirm whether the whole matching event satisfies the weak match.
- Confirm the nature of strong authentication. Confirm that the matching session belongs to weak matching, analyse the length of the matching session during the protocol interaction, and confirm the strong matching session according to the relevant axioms.
- After the one-way proof has been successful, the two-way strong authentication nature is proved. If the proof is successful, it indicates that the protocol is secure. Throughout the proof process, if the matching event of one party fails to satisfy a weak match, this indicates that the protocol does not satisfy the strong authentication property and cannot realise two-way authentication. This makes the protocol vulnerable to masquerading identity attacks and message replay, and hence, the protocol body is not secure.
3. Protocols
3.1. Brief Description of the Protocol
In this paper, we use industrial IoT multi-factor authentication protocol as an example to verify the extended theory. The basic notations and semantics are given in Table 2.

Table 2.
Notations and descriptions.
The following are the specific steps of the authentication phase protocol.
First, after receiving message from , first checks the freshness of the login request and verifies the timestamp in the message. When the verification result is true, may retrieve the database and obtain the corresponding . denotes the computation of and checks whether is equal to to verify the authenticity of . If the verification is successful, generates a random and timestamp. Subsequently, computes , and encrypts the parameters in for secure transmission to each legitimate sensing device. Then, computes to help the sensing device to authenticate . Finally, sends the message .
Second, each sensing device receives the broadcast message, decrypts and obtains the relevant parameters. verifies the identity of by calculating the condition . If successful, each sends . Then, it calculates and generates the current timestamp and returns the message to .
When receives a message from a sensing device, it verifies the timestamp, computes , reconstructs the secret , and counts . computes with the help of the new timestamp and the current timestamp. Finally, sends the message to respectively, and sends the message to those legitimate participants who helped reconstruct the secret.
When receives the message , each sensing device computes and the session key . Finally, computes and sends it to the current user to verify the shared session key.
Finally, when receives the message from , it first verifies the timestamp, and then decrypts . verifies the session consistency by checking whether .
The authentication process of the secure multi-factor authentication protocol for industrial IoT is shown in Figure 1.
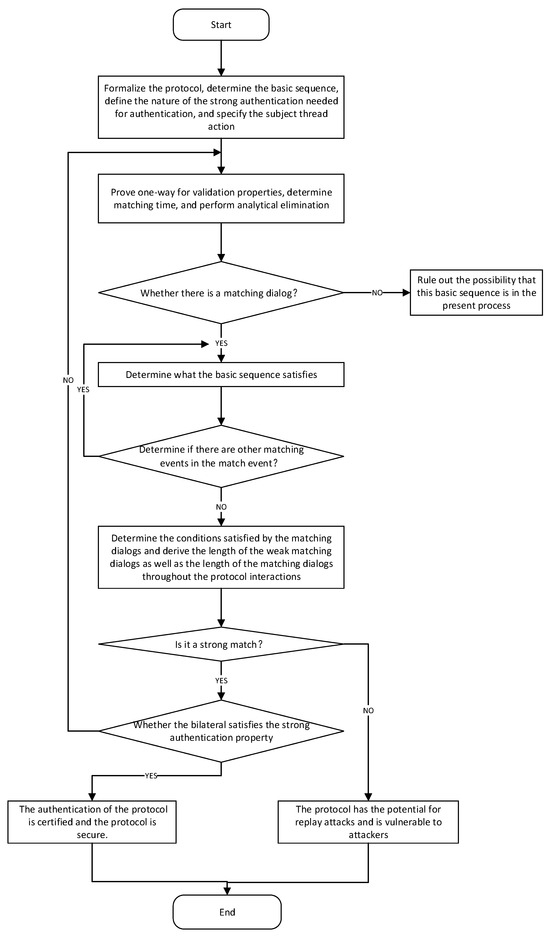
Figure 1.
Proof of security agreement process.
3.2. Formal Description of Protocol Authentication
The basic sequence ordering of a secure multi-factor authentication protocol for industrial IoT using the Logic of Events was performed. The protocol description is shown in Figure 2. A formal description of the protocol interaction process is shown in Figure 3 where is the action generated by the user during the protocol interaction, is the action generated by the gateway during the protocol interaction, and is the action generated by the wireless sensor during the protocol interaction.
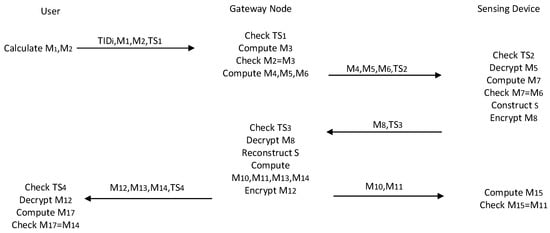
Figure 2.
Description of the authentication phase.

Figure 3.
Formal description of the protocol interaction flow.
The formal analysis of the Logic of Events is used to define the authentication properties that need to be satisfied to validate the Industrial IoT Secure Multi-Factor Authentication Protocol security. The basic sequence of the secure multi-factor authentication protocol for the industrial IoT is shown in Figure 4.

Figure 4.
The basic sequence of the protocol.
Based on the basic sequence relations defined, the protocol is defined as ; the authentication of the protocol can be formally stated as:
3.3. Agreement Certification Process
In the Industrial IoT Secure Multi-Factor Authentication Protocol, is considered fully trustworthy and is responsible for registering the users and sensing devices.
Assuming and that they are honestly adhering to the interaction process of the Industrial IoT Multi-Factor Secure Authentication Protocol, then the thread is an instance in the basic sequence . If is an event on the thread , and the body of is , then the address of event is also . For an atomic type of message , there is the following formula:
Using the axioms and , it follows that there is an event such that:
From this, it follows:
Since follows the interaction flow of the Multi-Factor Secure Authentication Protocol for the Industrial IoT, the event is an instance of an action belonging to one of the basic sequences of the protocol. Among the basic sequences, the sequence containing the encryption action is , so the sequence matching the event will be filtered from these sequences above.
If is an instance of the sequence , then for the atomic-type messages, etc., there is an event on the body .
From the comparison between and , we can see that the encryption event is different from , so we can exclude the possibility that has in it. Similarly, can also be excluded.
If is an instance in the sequence , then for the atomic types of information, , etc., there is
Here, the encryption event is not the same as the event , so is excluded. Since there is no cryptographic event in the sequence, and occur after , and can be excluded.
If is an instance in the sequence , then for the atomic types of information, , etc., and the subjects , there is
The above equation is satisfied.
It can be shown that is an instance in the sequence with , which can be obtained.
From the axioms and , it follows that the event must exist and satisfy Eq:
is honest and follows the protocol interaction flow. The event is an instance of one of the basic sequences based on the protocol; the sequence containing the encryption action is , in which the sequence is , where has not yet occurred. Thus, it can be excluded, as occurs on the subject , and then is excluded, leading to the conclusion that may be present in .
If is an instance of that exists for the atoms , etc., then on subject , there is
Then, there is
Another event exists and satisfies Eq:
Such that the expression holds. If the event is an instance in the sequence , then for the atom , there is the event for which the following equation holds:
The above equation satisfies
So this can be obtained:
This is obtained from with the above proof:
The next step in proving a strong matching dialogue is to prove . Let us start with as an example.
Assuming and that the subjects are honest and abide by the protocol, according to the random number axiom and the flow relation primitives, there is a send event between and , releasing a random number , and if , then can be obtained, and it is necessary to exclude .
If , then must be a member instance of some other thread that is the subject . Although the protocol may have other basic sequences releasing random numbers before releasing the random number , it follows from threads and matching sessions that there is no send action between and in the thread , and then the random number will not be released before , so can be ruled out. Similarly, can be proved.
3.4. Proof of Results
In summary, there are four strong matching dialogues for the thread on the subject , and is proved.
Similarly, there are two strong matches present in the subject , and the thread is fully interactive; can be proved.
Thus, this proof process has been completed to prove the strong authentication property of the protocol . Therefore, the authentication of the Multi-Factor Secure Authentication Protocol for the Industrial IoT has been proved, and the attacker is not able to replay the attack by disguising the legitimate user, so the protocol is secure.
4. Logic of Events vs. Other Approaches
The formal analysis methods for security protocols are divided into three categories, model detection methods, modal logic methods, and theorem-proving methods, each with a different focus.
4.1. Comparison of LoET and Modal Logic
Modal logic is the most widely used formal method, including BAN logic and BAN-like logic, of which BAN-like logic contains more than ten kinds of logic methods [19]. This method is simple and direct and is very widely used. However, it has some insurmountable drawbacks; one is that the idealisation process of the protocol is very difficult, and the other is that the method lacks a mechanism for the derivation of the subject’s behaviour.
Taking BAN logic as an example, compared to the Logic of Events theoretical approach, BAN logic has to carry out a lot of idealisation, which contains the protocol’s premises, the protocol itself, the protocol goals, etc., and these actions are realised through formal descriptions [20]. BAN logic describes the initialisation assumptions of the protocol and the expected goals of the security protocol through formal descriptions, which are similar steps to the LoET theoretical approach. However, BAN logic is too dependent on initial assumptions, such as the execution environment in which it is implemented, the subjects involved in the execution of the protocol, and the keys used by the protocol. In contrast, the LoET theory deals with protocol initialisation in a more abstract way, while making reasonable assumptions about the objective environment of the protocol. BAN logic over-idealises the protocols and relies too much on the analyst’s intuition. This idealisation process may lead to problems, making the idealised protocol somewhat different from the original protocol. For example, the preconditions or contents of the protocol may be ignored or added, and the description of the protocol goals may not be accurate enough, which may lead to discrepancies between the analysis results and the original protocol design. The theory of LoET [21], on the other hand, regulates a series of axioms and inference rules using rigorous mathematical rules, which ensures the rigour of the process of proving the nature of strong authentication. BAN logic carries out step-by-step reasoning using the rules and applies rigorous logic during the reasoning process to prove the security of the protocol. However, the semantic carve-out of BAN logic is not very clear, and the proof process of this logic may not be fully convincing. Also, BAN logic does not provide a good guarantee of the practicality of protocol proofs. In contrast, the LoET theory defines clear and explicit theorem rules with a clear and unambiguous structure, which can guarantee the authenticity and reliability of protocols in the proving process and make the protocol security properties more credible.
4.2. Comparison of LoET and Model Detection
The model detection of security protocols considers the limited behaviour of the protocols and detects whether they are slow to rule some correct conditions. The method is more suitable for discovering attacks on protocols rather than proving the correctness of the protocols, for example, the process of FDR analysis is to test whether the protocols satisfy the statute or not.
The model detection methods can only analyse finite state systems, but the actual network environment may allow each subject to run multiple protocol entities at the same time, allowing the concurrent operation of an infinite number of protocol instances to inevitably lead to an infinite protocol model state space [22]. LoET, on the other hand, can simplify the processing of complex protocol objects and simplify the protocol interaction process. For example, data transmission and interaction in the physical layer, network layer, etc., and this information in the formal description of the LoET theory are not used to perform figurative processing for the message Msg to define. However, the protocol action should be clearly marked for message processing to ensure the effectiveness of the LoET theory method in the information transfer process of protocol modelling. The model detection of the biggest problem is a state space explosion problem, generally taken to limit the small system model, in the introduction of some special methods (such as symbolisation methods, etc.) for model detection. But the biggest advantage of model detection is that it can be completely automated, often effectively finding the vulnerability of security protocols, so the design and analysis of security protocols play a role in falsification. Currently, LoET relies more on manual proofs, and further research on distribution automation is needed.
4.3. Comparison of LoET and Theorem Proving
The LoET theory is a kind of theorem-proving method. The advantage of a theorem-proving method is that it can analyse protocols of an infinite size and does not limit the rounds in which the subject participates in the operation of the protocol. Its disadvantage is that the proof process cannot be fully automated and requires manual “expert” intervention, and many theorem-proving methods are incomplete, such as the type theory proof methods based on Spi algorithms that can prove the security of the protocol, but it is difficult to construct a secure protocol corresponding to the type system; when there is no constructed type system to prove that the protocol meets the security, it cannot be said that the protocol is vulnerable. To satisfy security, the protocol cannot be shown as vulnerable.
As an example, PCL is a logical method for proving the security system of cryptographic protocols. In protocol security property verification, the PCL method can be used to inscribe the security properties of some protocols, but it cannot inscribe the authentication properties of the data signature protocols. In contrast, the theorem-proving approach based on the LoET theory can perform authentication for the other security properties. The PCL approach suffers from a lack of rigour in modelling protocol interaction actions and lacks a definition of the mechanism for describing the sequence of preceding actions of a thread. The LoET theory approach defines the thread mechanism for the formal modelling of protocols and regulates the sequential thread state of events through atomic independence, which makes the modelling more standardised. The PCL approach lacks the necessary constraints and limitations on the data types of protocol information, while the LoET theory ensures that the data types of protocol information are well regulated by defining the unique type to regulate the definition of the basic elements that are unstructured and cannot be generated. The data types are adequately regulated. In particular, the PCL approach has major limitations in describing the behaviour of the Diffie–Hellman algebra and the Hash function, which the LoET theory chooses to portray when dealing with encryption actions. Taking the Hash function encryption in this paper as an example, during the message decryption verification process, the LoET theory approach generates a new Hash encryption by means of a valid message, and then proves it by comparing it with the inscribed encryption action.
In conclusion, the existing formal analysis methods for security protocols have their own advantages and disadvantages, and although the research in this area has become a hotspot, its application deserves further exploration. The main reason for this status quo is that the formal modelling and analysis of security protocols are very difficult, and the existing formal methods can often only analyse one or two security properties (generally confidentiality and authentication), while the existing security protocols tend to have more security goals; there is a lack of a unified formal model for analysing and verifying a variety of security properties under a unified framework. Therefore, mature theories or methods to study more security properties and how to analyse and verify the security properties under a unified formal framework are issues worthy of future research.
5. Discussion
This paper extends the definition of in the event class based on the existing Logic of Events theory to simplify the description of complex encryption behaviours in industrial IoT protocols. The extension of the relevant rules based on the event class is mainly used to describe more complex encryption behaviours and encryption mechanisms in industrial IoT security protocols and to verify the causal relationship between protocol events more effectively. In this paper, we use Logic of Events and its extension theory to analyse the security of multi-factor security authentication protocols for the industrial IoT, formally analyse the interaction actions between different initiators and receivers of the three types of subjects, portray the security properties of industrial IoT security protocols, and verify the security of the protocols using an axiomatic system. The theory is applicable to the formal analysis of some industrial IoT security protocols.
The future work on LoET theory should include the following. The proof method of LoET relies more on manual proofs, and by defining the individual steps of the method, the next step is to investigate the implementation of distribution automation. The concept of step-by-step implementation is added to the security protocol verification system being constructed, thus realizing the automated proof of network security protocol authentication. LoET is still complex and cumbersome in the process of proving the security of protocols, and it is considered to simplify the process of protocol proving, improve the efficiency of proving, and make the method more popular and easy to understand. The future research direction is how to achieve the analytical proof of the other security attributes in security protocols, further improve and refine the relevant theory, and analyse more industrial IoT protocols by example.
Author Contributions
Conceptualization, M.X. and Y.C.; methodology, Y.C.; validation, Y.C., Z.L. and Q.C.; formal analysis, Y.C.; investigation, Y.C.; writing—original draft preparation, Y.C. and R.X.; writing—review and editing, M.X. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Natural Science Foundation of China (No. 61962020, No. 62362033), Jiangxi “Double Thousand Plan” (No. JXSQ2023201009), and Jiangxi Provincial Natural Science Foundation (No. 20224ACB202006).
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors would especially like to thank Fangping Chen from Jiangxi University of Software Professional Technology. He was involved in the design of the program and formal analysis and validation during the initial stage of this research; he provided useful and constructive comments during the revision stage of the paper, which greatly improved the manuscript. His help with the manuscript was indispensable.
Conflicts of Interest
The authors declared no conflicts of interest.
References
- Niu, S.; Shao, H.; Su, Y.; Wang, C. Efficient heterogeneous signcryption scheme based on Edge Computing for Industrial Internet of Things. J. Syst. Archit. 2023, 136, 102836. [Google Scholar] [CrossRef]
- Rana, B.; Singh, Y.; Singh, P.K. A systematic survey on internet of things: Energy efficiency and interoperability perspective. Trans. Emerg. Telecommun. Technol. 2021, 32, e4166. [Google Scholar] [CrossRef]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial internet of things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Wang, X.; Kou, M.; Li, C.; Zhao, L. Implementation of Theorem Prover for PPTL with Indexed Expressions. J. Softw. 2022, 33, 2172–2188. [Google Scholar] [CrossRef]
- Kokologiannakis, M.; Vafeiadis, V. GenMC: A model checker for weak memory models. In Proceedings of the 33rd International Conference on Computer Aided Verification, Virtual Event, 20–23 July 2021; Silva, A., Leino, K.R.M., Eds.; Springer: Berlin/Heidelberg, Germany, 2021; pp. 427–440. [Google Scholar]
- Xu, Q.; Lin, J.T. Formal description and verification of message authenticate safety layer in rssp-II. Comput. Appl. Softw. 2023, 40, 77–82+180. [Google Scholar]
- Zhong, X.M.; Xiao, M.H.; Yang, K.; Luo, Y. Formal analysis of PUFs authentication protocol based on logic of events. Sci. Technol. (Nat. Sci. Ed.) 2022, 1–8. [Google Scholar] [CrossRef]
- Zhong, X.; Xiao, M.; Zhang, T.; Yang, K.; Luo, Y. Proving Mutual Authentication Property of RCIA Protocol in RFID Based on Logic of Events. Chin. J. Electron. 2022, 31, 79–88. [Google Scholar]
- Constable, R.; Bickford, M. Intuitionistic completeness of first-order logic. Ann. Pure Appl. Log. 2014, 165, 164–198. [Google Scholar] [CrossRef]
- Xiao, M.H. Formal Analysis and Verification of Security Protocol; Science Press: Beijing, China, 2019. [Google Scholar]
- Xie, R.C.; Wen, W.; Tang, Q.Q. Survey on rail transit mobile edge computing network security. J. Commun. 2023, 44, 201–215. [Google Scholar]
- Huang, X.; Xiang, Y.; Bertino, E.; Zhou, J.; Xu, L. Robust multi-factor authentication for fragile communications. IEEE Trans. Dependable Secur. Comput. 2014, 11, 568–581. [Google Scholar] [CrossRef]
- Yuan, J.J. An enhanced two-factor user authentication in wireless sensor networks. Telecommun. Syst. 2014, 55, 105–113. [Google Scholar] [CrossRef]
- Srinivas, J.; Mukhopadhyay, S.; Mishra, D. Secure and efficient user authentication scheme for multi-gateway wireless sensor networks. Ad Hoc Netw. 2017, 54, 147–169. [Google Scholar] [CrossRef]
- Wang, D.; Li, W.; Wang, P. Measuring two-factor authentication schemes for real-time data access in industrial wireless sensor networks. IEEE Trans. Ind. Inform. 2018, 14, 4081–4092. [Google Scholar] [CrossRef]
- Guo, H.; Gao, Y.; Xu, T.; Zhang, X.; Ye, J. A secure and efficient three-factor multi-gateway authentication protocol for wireless sensor net-works. Ad Hoc Netw. 2019, 95, 101965. [Google Scholar] [CrossRef]
- Yu, Y.; Hu, L.; Chu, J. A secure authentication and key agreement scheme for IoT-based cloud computing environment. Symmetry 2020, 12, 150. [Google Scholar] [CrossRef]
- Vinoth, R.; Deborah, L.J.; Vijayakumar, P.; Kumar, N. Secure multifactor authenticated key agreement scheme for industrial IoT. IEEE Internet Things J. 2020, 8, 3801–3811. [Google Scholar] [CrossRef]
- Yogesh, P.R. Formal Verification of Secure Evidence Collection Protocol using BAN Logic and AVISPA. Procedia Comput. Sci. 2020, 167, 1334–1344. [Google Scholar] [CrossRef]
- Li, L.L.; Dong, Q.K.; Chen, M.M. Cloud-based Lightweight RFID Group Tag Authentication Protocol. Comput. Sci. 2019, 46, 182–189. [Google Scholar]
- Yang, K.; Xiao, M.; Zhong, X.; Zhong, Y. A novel formal logic for formal analysis of timeliness in non-repudiation protocols. J. King Saud Univ. Comput. Inf. Sci. 2023, 35, 101664. [Google Scholar] [CrossRef]
- Yang, K.; Xiao, M.; Zhong, X.M. Review of Temporal Logic and Its Expressive Power. J. East China Jiaotong Univ. 2023, 40, 57–70. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).