Abstract
Blockchain is a recently developed advanced technology. It has been assisted by a lot of interest in a decentralized and distributed public ledger system integrated as a peer-to-peer network. A tamper-proof digital framework is created for sharing and storing data, where the linked block structure is utilized to verify and store the data. A trusted consensus method has been adopted to synchronize the changes in the original data. However, it is challenging for Ethereum to maintain security at all blockchain levels. As such, “public–private key cryptography” can be utilized to provide privacy over Ethereum networks. Several privacy issues make it difficult to use blockchain approaches over various applications. Another issue is that the existing blockchain systems operate poorly over large-scale data. Owing to these issues, a novel blockchain framework in the Ethereum network with soft computing is proposed. The major intent of the proposed technology is to preserve the data for transmission purposes. This new model is enhanced with the help of a new hybrid algorithm: Adaptive Border Collie Rain Optimization Algorithm (ABC-ROA). This hybrid algorithm generates the optimal key for data restoration and sanitization. Optimal key generation is followed by deriving the multi objective constraints. Here, some of the noteworthy objectives, such as information preservation (IP) rate, degree of modification (DM), false rule (FR) generation, and hiding failure (HF) rate are considered. Finally, the proposed method is successfully implemented, and its results are validated through various measures. The recommended module ensures a higher security level for data sharing.
1. Introduction
Developers can create many distributed apps based on smart contracts over the Ethereum programming platform. For example, voting, financial transactions, business administration, and contract signing are the applications used in the Ethereum platform [1]. During data sharing, the protection of privacy is very important. If shared data fall into the wrong hands, the data could be misused and accessed by intruders, the denial of loans and health insurance, and victimization of a person by financial fraud [2]. However, if the data can be shared with the right users, then there is no information to be stolen and misused by unauthorized entities [3]. The newly developed privacy-preserving data publishing (PPDP) and privacy-preserving data mining (PPDM) approaches are utilized to reduce privacy issues [4]. Data analysis contains commodity data, and mining turns it into economic value [5]. The digital world increases the possibility of losing control over all of one’s own intellectual, emotional, and situational knowledge, breaking the informational privacy area and losing one’s autonomy [6]. The primary problem in this situation is that control of privacy leakage by every individual requires high freedom in the flow of information the technology enables, the connections it facilitates, and the advantage supplied by the information source [7]. Government organizations also create legislative guidelines to protect personal data, including what purposes the particular data is used for, how it is gathered, and how it should be preserved. Corporate privacy issues are also solved by these guidelines [8].
Ethereum is a programming environment that makes it possible to provide privacy preservation with the help of blockchain by building over distributed applications [9]. With “smartcontract”, the contract may be carried out without needing a centralized authority after it has been installed. The smart contract executes intent in a perfect world, and it produces reliable results [10]. Blockchain is a new technology that has gained popularity due to the rise of cryptocurrency such as Ethereum and Bitcoin [11]. It may be considered a distributed ledger with cryptography, and accurately records the results of every transaction. A transaction recorded on the blockchain cannot be changed beyond that point, and everyone can see it [12]. Every network member will reach a consensus on the blockchain, ensuring that all valid transactions are recorded [13]. Secondly, every network member will reach a consensus on the blockchain, ensuring that no invalid transactions are recorded. Thirdly, all transactions recorded on the blockchain are auditable by network members and cannot be tampered with by other issues. Smart contracts are being deployed alongside the advancement of blockchain technology such as Ethereum and Hyperledger to increase the potentiality of blockchain [14]. Addressing a transaction for a certain smart contract’s address will cause it to be activated [15]. When a smart contract is activated, it can run the predefined program independently through a centralized authority.
The challenges of the existing supply chain are shown below. Rival actors can be found in the same supply chain, which makes data sharing very difficult [16]. Due to these challenges, research on and implementation of traceability are growing slowly. Although there has been work to create supply chain traceability, it is not practical in the actual world. The work demonstrates several procedures in a centralized system’s data structures and transparent framework. Researchers’ interest in blockchain technology and its application to the supply chain has grown over the last few years [17]. Some limitations of the existing research and their techniques are depicted here. The supply chains’ global character makes it challenging to achieve the desired traceability. Several methods are implemented to provide better privacy-preserved data transfer in the supply chain network. However, these methods fail to address issues with certificate verifiability and raise concerns about the existence of privacy-sensitive information. A hash network links the blockchain in chronological order. For each node, it has a copy of a ledger, and few mutually distrusting nodes often maintain this hash network. This system provides better confidentiality and non-repudiation over the Ethereum networks, but the cost requirement is high and the system’s feasibility low. To overcome these challenges, a novel blockchain-based privacy preservation model is implemented in the Ethereum network to provide better privacy preservation.
The contributions of the designed Ethereum-based privacy preservation model are listed below.
- To design a blockchain-based data privacy preservation model with a hybrid meta-heuristic algorithm over the supply chain network to secure information exchange and guarantee the privacy of data access in the Ethereum platform. Here, the performance improvement of the proposed model is applicable to different applications regarding cryptocurrency, food supply chains, and sealed-bid auctions.
- To generate the key with the help of developed ABC-ROA for exchanging the secured data in the supply chain framework using data restoration and data sanitization procedures in the Ethereum environment. The developed ABC-ROA algorithm is utilized to restore the data from the receiver side. Consequently, it helps to access the original data that can be generated from the original key.
- To implement the hybrid meta-heuristic algorithm known as ABC-ROA for choosing the best optimal key to maximize the performance of the developed blockchain-based privacy preservation model. Here, the designed ABC-ROA algorithm improves the system’s robustness. It is also used to solve complex issues.
- To compare the developed ABC-ROA-based privacy preservation system with existing meta-heuristic algorithms using a variety of metrics to verify the performance of the developed model.
This paper is split into the following sections. The merits and demerits of recent privacy preservation in the Ethereum network model based on blockchain are described in Section 2. The suggested dataset for the blockchain-based privacy preservation system in Ethereum and the model explanation offered are covered in Section 3. The procedures used to create the privacy preservation model, such as data restoration and sanitization in the supply chain method, are shown in Section 4. The Ethereum privacy preservation model with the ABC-ROA algorithm, optimal key details, and objective function details are described in Section 5. The acquired outcomes of the recommended method are summarized in Section 6. The paper is concluded in Section 7.
2. Literature Survey
2.1. Related Works
In 2021, Lin et al. [18] introduced privacy-preserving blockchain architecture (PPChain), and PPChain’s design has been changed in Ethereum. PPChain’s architecture allowed regulation to provide security. They specifically incorporated cryptographic primitives such as broadcast encryption and group signature into a workable byzantine fault tolerance consensus protocol with a separation mechanism to remove the transaction fee and mine for a reward instead of using the existing mining model. They offered in-depth security and privacy analysis and a performance study to demonstrate the usefulness of PPChain. Examples from the food supply chain, sealed-bid auctions, and cryptocurrency described how the PPChain might be used in regulation applications. In 2022, Rahmadika et al. [19] implemented an efficient architecture for secure misbehavior detection in lightweight IoMT tools in the “artificial pancreas” model (APS). The suggested method used deep learning, which protected privacy, and boosted security by integrating blockchain technology built on the Ethereum smart contract ecosystem. The efficacy of the developed system has been empirically tested for commensurate incentive schemes, exhaustiveness with compact findings, and an untraceable characteristic from a different neural deep learning technique. Consequently, the model has a high recall rate, demonstrating that it is almost completely capable of identifying harmful events in the case being studied.
In 2022, Xiong et al. [20] designed a secure privacy preservation authentication mechanism for inter-constellation collaboration. They created both permanent and transient identities for each satellite to protect privacy. The permanent identity was used for inter-constellation collaboration, whereas the temporary identity was utilized for communication inside the constellation. For information exchange among cooperative satellite constellations, a consortium blockchain was introduced. A replica storage node mechanism has been suggested to enable effective authentication with minimal resources, where well-resourced satellites cache the duplicated data exchanged across the blockchain. A branch-and-bound approach has been used to address the integer programming issue of choosing the replica storage node. According to a security study, the suggested authentication technique was secure against various possible attacks, which included formal analysis using informal verification and BAN Logic. The suggested system provided efficiency in communication overheads, signaling, and processing with greater performance, based on a comparison between it and other privacy preservation schemes. Evaluations showed that the suggested onboard caching approach achieved minimal storage costs and communication delay.
In 2022, Singh et al. [21] implemented a privacy preservation model in smart healthcare using a blockchain-based federated learning method for preserving privacy, which used IoT cloud platforms to provide privacy and security. Scalable machine learning applications such as health-care use federated learning technologies. Users could also utilize a well-trained deep learning system without putting their private information in the cloud. Additionally, it covered the uses of federated learning in a smart city’s distributed secure environment. In 2020, Guo et al. [22] implemented a blockchain-based privacy preservation system in the Ethereum network to provide better privacy preservation data. In that model, they used various mechanisms in the blockchain. Privacy protection and analyzing anonymity methods were used in digital currency. The aim of the encryption mechanism was focused on the privacy protection scheme.
In 2022, Mohan et al. [23] designed the proof of authority (PoA) consensus process, which required little computational power, and it has been implemented on a Raspberry Pi network. The elliptic integrated encryption process used a double-encryption process to protect the secrecy of data. With a speed of at least 25 transactions per second, it has been reported to perform well in contrast to previous systems. It was also readily expandable to accommodate various health-care workers. A new range of real-time health monitoring tools with excellent security and data privacy might come from further work on this concept, potentially leading to significant innovation in the IoMT sector. In 2018, Elisa et al. [24] developed a model for a decentralized deep learning e-government system utilizing a blockchain framework that guaranteed data confidentiality and privacy and boosted public sector confidence. A prototype of the suggested system was also provided, supported by a theoretical and in-depth examination of the system’s security and privacy consequences.
In 2022, Dewangan et al. [25] suggested a system that used tokens to create pupils’ identities and saved them in a file system. The suggested model used SHA-256 for cryptographic hashing, Edwards-curve digital signature algorithm (EdDSA), and IPFS for digital signature and verification. The results of this suggested method show the transaction speed, the time needed for validating and signing a transaction, and the time needed for each transaction. They evaluated the privacy, transaction costs, huge file storage, blockchain registration, and implementation costs of this system to those of the already built solutions.
2.2. Statement of Problem
Personal information is stolen by many hackers and intruders, so privacy preservation is much needed nowadays. Personal data information theft, virus threats, and spamming are illegal activities. However, limited hardware resources in IoT applications, including network bandwidth, computing power, and storage pose unique challenges to the blockchain. Therefore, various researchers have developed efficient technique to secure the data along with the blockchain technology. Some of the disadvantages and advantages of the existing blockchain-based privacy preservation techniques are listed in Table 1. PPChain [18] provides qualitative security and efficient privacy over personal data. Additionally, it ignores the correlation between variables to enhance training performance. However, it is not sufficiently developed to achieve conflicting properties, such as regulation, transparency, anonymity, and confidentiality, and is computationally expensive. Bi-LSTM [19] significantly increases the storage cost. Additionally, it achieves higher prediction accuracy, precision, and f1 score, yet it requires more time for training and is slow compared to other convolutional techniques and does not contain expensive hardware to perform complex mathematical calculations. Signs [20] indicate a high percentage of false positives. Additionally, the board caching method achieves low storage costs and communication latency. However, it does not access the service anywhere and does not provide any security system for communication and privacy protection, so it suffers slightly from the security perspective. Federated learning [21] achieves efficiency in computation, communication overheads, and low signaling with more functionality. Additionally, it achieves high authentication with replica storage and limited resources, yet the efficiency is low when compressing the massive number of devices in the security system and it is very expensive. Data encryption [22] efficiently achieves strict rights management, mainly used for several functions. Additionally, it increases the integrity of the data, and it is very cheap to implement. However, it provides less computation for compatibility and the scalability is very low. For the Raspberry Pi network [23], the implementation cost is low. Additionally, the implementation cost is low, yet to handle a large amount of data, more storage is needed in this network, and it does not provide a proper balance between connectivity and storage requirements. Peer-to-peer technology [24] improves computation rationality and identity anonymity. Additionally, it is easy to set up the client data and does not need any special knowledge. However, the data confidentiality is very poor, and the file resources do not centrally organize, so it takes more time. EdDSA [25] improves the immutability and transparency to enhance the privacy system. Additionally, it reduces the computational complexity of the decentralization algorithms, yet while using the enormous data, the private key is sometimes leaked and does not support merging complex data. Therefore, these challenges motivated us to develop an efficient privacy-preserving system with blockchain technology.

Table 1.
Features and disadvantages of the existing blockchain-based privacy preservation techniques with blockchain technology in Ethereum.
3. Privacy Preservation of Supply Chain Management Data: New Meta-Heuristic with Ethereum Blockchain
3.1. Data Used for Privacy Preservation
Client data are protected to establish a privacy preservation system. SCM gathers input data from a dataset called DataCo Smart Supply Chain for Big Data Analysis. It is available at https://www.kaggle.com/shivkp/customer-behaviour (accessed on 10 January 2023). The firm DataCo Global uses these data related to supply networks for their analysis. This dataset comprises registered operations that allow using R software areas and machine learning techniques, such as commercial distribution, sales, production, and supply. It also incorporates the relationship between organized and unstructured data. The gathered data are separated into three subsets: dataset 1, which comprises manufacturer data, dataset 2 counts transmitted data to managers who are present in different nations, and dataset 3 contains data transferred to each firm in each country.
3.2. SCM Privacy Preservation Framework
SCM is one of the best-known commercial organizations due to its capacity for improving the efficiency of the firm. Supply chains and Ethereum blockchains are coupled to improve the security of supply chain networks. Many methods for ensuring the data privacy preservation and security of the Ethereum network with blockchains were introduced, including a VMI mode system, homomorphic encryption, fully observable supply chain management, PBFT algorithm, and consensus-based collaborative management mechanism. These methods help with cost-effective reconciliation, minimizing dispute settlement, increasing security, reducing dwell time, enhancing transparency, decentralizing data distribution, lowering complexity, increasing throughput, and addressing issues with information sharing and data tracking. The architectural representation of the Ethereum blockchain technology developed for privacy preservation is given in Figure 1.
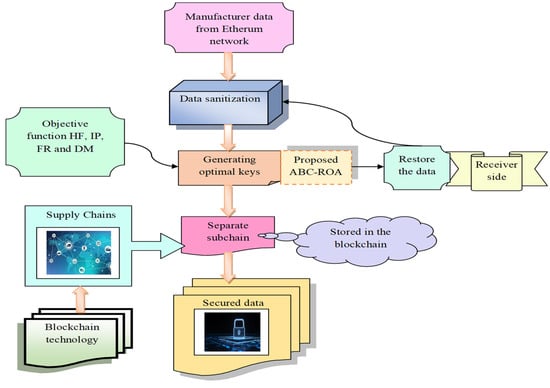
Figure 1.
Architectural representation of the privacy preservation platform developed in the Ethereum blockchain.
Owing to these issues, higher credibility and dependability of data sharing and keeping security in the Ethereum blockchain technology, a data privacy preservation model using blockchain has been established. Initially, the desired data are gathered from publicly available online databases. Data restoration and data sanitization are the two stages of secured data transfer in the developed model. The initial manufacturer data are cleaned during the sanitization procedure to guarantee the security of the data during transmission. Here, the originally collected data undergo sanitization. Then, the optimal key is generated with the ABC-ROA algorithm, which follows multi objective functions, such as HF, IP, FR, and DM. Then, the sanitized data progress to the restoration process, where they are stored. The restored data are transferred to the supply chain framework, where the blockchain is adapted to preserve the data during transmission. These overall processes are done in an Ethereum environment using blockchain technology. This technique sends the sanitized data over a single blockchain to prevent unauthorized access and delay in data transmission. The performance of this blockchain-based privacy preservation model is verified through various heuristic algorithms regarding key sensitivity, cost function, Euclidean distance, and harmonic mean.
4. Supply Chain Network Creation and Privacy Preservation Steps Handled
4.1. Supply Chain Networks
The supply chain network is divided into key levels: level 1 indicates the raw materials, level 2 denotes the supplier, level 3 indicates the manufacturer, level 4 denotes the manager, level 5 indicates the delivery, and level 6 denotes the customer. The network is then incorporated into the blockchain to raise the level of information-sharing security. Here, the manufacturer’s data undergo data sanitization to conceal them by employing the “chosen optimal key” created by the ABC-ROA algorithm. Then, in the restoration phase, these cleaned data are restored using the same optimum key through the authenticated users on the receiver end. These actions protect the confidentiality of the data shared in supply chain networks. The proposed data privacy preservation model divides the supply chain network into four main levels: level 1 designates the product’s manufacturer, level 2 the management, level 3 the product delivery, and level 4 the vendor. The phenomena that are a part of the supply chain network are further characterized. Manufacturers in various industries create their databases with information on the price, weight, product manager, delivery method, and suppliers of their manufactured goods. The manufacturer’s data are concealed or cleaned up using an ideal key. Then, the managers upload their data into the blockchain, dividing it into various subchains to increase security.
Additionally, the data are sent appropriately in their supply chain subchains when transferred from the first management level to the last delivery level. The data restoration then happens at the vendor level. By restoring the actual data, the vendor utilizes the best key to access the private information. Five manufacturers with their required production goods are part of the supply chain network. Pretend these companies produce leather, cosmetics, electronics, paper, and wooden goods. They create a database based on the product information, which contains information such as item price, description, weight (kg), amount, brand, controlled by vendor manager, and shipment mode (delivery). The price, item quality, brand, and item description are understood to be the sensitive fields in this situation, and they must be sanitized using the created EF-HHO algorithm.
The manufacturer’s subchains are shown in Equation (1).
The terms and are the sub-chains and are calculated using Equation (2).
The single blockchain is created by combining these subchains.
These data are then transferred to the manager level. The managers and their corresponding subchains are shown in Equations (3) and (4).
The subchains of the manager are given in Equation (5).
The vendors and their corresponding subchains are measured by Equation (6) and Equation (7), respectively.
The single blockchain is indicated by .
Then, the subchains of the manager are denoted in below Equation (8).
Finally, the delivery level is represented in Equation (9).
Here, the term is a single delivery level. The term is vendor value in the supply chain.
The representation of the supply chain network with blockchain is given in Figure 2.
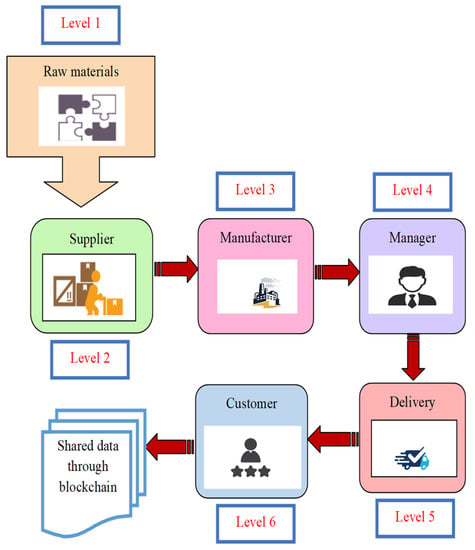
Figure 2.
Supply chain network with blockchain.
4.2. Data Sanitization and Data Restoration
The sanitization and restoration techniques used in this blockchain-based privacy preservation system are described below.
Sanitization [26]: The data sanitization phase over the recommended data privacy preservation system in the Ethereum network is described in this section. The collected data from the real databases undergo data sanitization. In most cases, the sanitization process occurs at the manufacturer level, and blockchain sanitization also happens. The sensitive data in the blockchains’ subblocks are cleaned after being separated into subblocks. It is not necessary to sanitize the non-sensitive data in the subblocks. The term is a blockchain-sanitized database calculated by Equation (10).
The term is actual data, and the binarized sanitized data is . The term is a sensitive field, and the corresponding subchain is represented by . The data columns are to be sanitized in the blockchain . The sensitive field is given in the blockchain matrix . The blockchain matrix is given in Equation (11).
The term is a sensitive matrix. It is from the blockchain matrix and is given in Equation (12).
Here, the result of the sanitized matrix in the blockchain matrix based on the rule is given. The sensitive data is present in the binarized data . The subblock is indicated by , and the identity matrix is denoted by . In addition, the term and are added to the sanitized data .
Restoration: The restoration process is very efficient for a privacy-preserving system. When employing the ABC-ROA algorithm on the receiver side, the receiver can access the original data using the generated optimal key. The first step is to binarize the blockchain. The key generation methods, the data , and the sanitized blockchain are binarized. The sanitized data’s binarized form is further altered through the unit phase. To extract the restored data , the binarized key matrix and binarized are subtracted. The data restoration process is measured using Equation (13).
Then, the newly designed ABC-ROA algorithm is used to recreate the sanitized key . The restored data are denoted by ,and hence the lossless function can be performed. The data sanitization and restoration process in the Ethereum blockchain network for the data privacy preservation system is depicted in Figure 3.
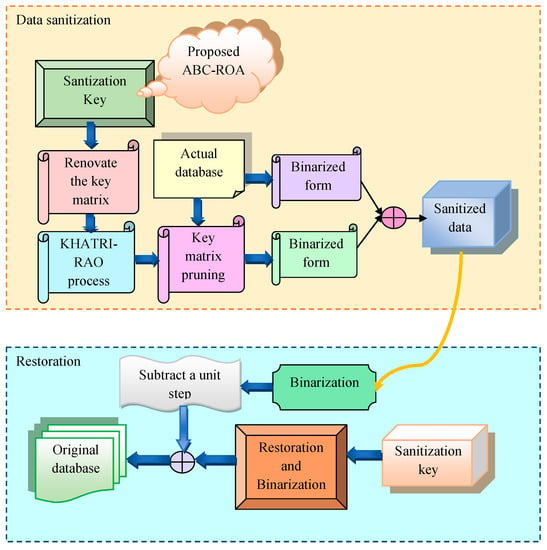
Figure 3.
Data sanitization and data restoration process in the blockchain-based privacy preservation system.
5. Adaptive Border Collie Rain Optimization Algorithm with Ethereum Blockchain for SCM Data Privacy Preservation
5.1. Optimal Key Generation
In the above section, the selected sensitive fields are chosen based on the sanitization process. The ABC-ROA optimization algorithm chooses the optimal key in sensitive fields. The term is an optimal key value. In the key generation phase, the Khatri–Rao product is adapted to transfer the solution. The optimal key is recreated with the matrix dimension and calculated using Equation (14).
Here, the term is sanitized data. The rule-hiding technique is used in the sanitized database. The ABC-ROA algorithm is adapted to optimize the key values between and , respectively. The length of the key value is the same as that of the number of sensitive fields. The key length is determined by using . Finally, the optimal key is formed by using the ABC-ROA algorithm.
5.2. Objective Function
The ABC-ROA-based privacy preservation system chooses the optimal key in the restoration and sanitization process. These methods are used to solve constraints such &. The objective function of the model is calculated by Equation (15).
The selected optimal key is denoted by . The term is normalized data and measured using Equation (16).
The number of sensitive rules is given in Equation (18). The ratio of sensitive rules to the number of sensitive rules is presented below in Equation (19).
The information preservation ratio is calculated using Equation (20).
The information loss is measured using Equation (22).
Here, the term is a false rule generation. The false rules generation is calculated by Equation (23).
The modified degree is measured in Equation (26).
The optimal key is generated in the blockchain-based privacy preservation system. The optimal key selection improves the performance of the model.
5.3. Ethereum Blockchain Technology
A blockchain is a decentralized ledger of data kept by network nodes, and a single entity does not control it. The blockchain data blocks are connected using cryptographic concepts. Everyone on a blockchain is responsible for their actions since the transaction data are immutable and open to the public. A blockchain-based application is transparent and attack-resistant. Ethereum is an open-source blockchain framework for decentralized applications that manage digital wealth. “Smart contracts” refers to the applications that operate on the Ethereum virtual machine (EVM). Two widely used scripting languages for creating smart contracts on Ethereum are Solidity and Vyper. The two types of accounts in Ethereum are contract accounts and externally owned accounts (EOA). Every account type contains a different 20-byte hexadecimal string-based unique address. The data are transmitted with the help of the owner’s private key and thus, it controls the EOA, which has an ether balance (i.e., sending data to prompt the initiation of a smart contract). There is no code associated with an EOA. On the other hand, the corresponding code for a contract account with an ether balance is triggered by a transaction or another smart contract. A few benefits of this model’s use of Ethereum blockchain technology include restricted access to the consumer’s or generator’s private data, practical calculation techniques that may be implemented on the smart contract, and complete decentralization, achieving transparent on-chain market clearing. The architecture representation of Ethereum blockchain technology is given in Figure 4.
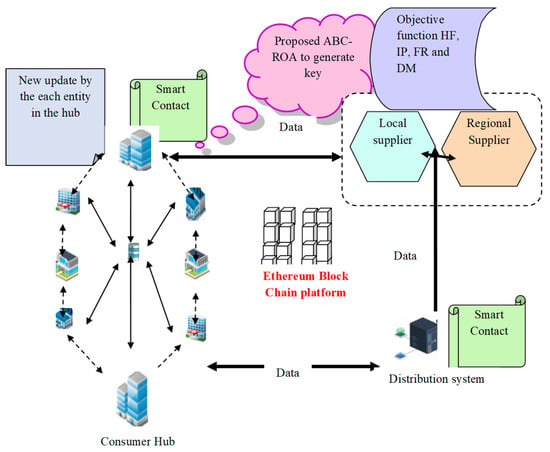
Figure 4.
Privacy preservation framework in Ethereum blockchain technology.
5.4. Proposed ABC-ROA
The ABC-ROA algorithm is designed to enhance the effectiveness of the developed data privacy preservation system to select the optimal key in the data sanitization and data restoration process in the SCM. The existing algorithms face a few challenges in privacy preservation in Ethereum blockchain technology, where the existing heuristic algorithms have a limited number of resources to store the data. Hence, they face security and scalability challenges. The existing ROA and BCO algorithms are utilized for this work. Here, the BCO algorithm is selected in the developed method to increase the performance and robustness of the model. Additionally, it reduces the errors to increase the effectiveness concerning precision, f1score, and accuracy. The BCO is solving the multi objective combinational optimization problems. However, it gains low scalability and utility. Due to the issues in the BCO algorithm, the ABC-ROA algorithm is developed by combining the ROA. ROA is chosen in the implemented model since it can perform in parallel computing and is mostly helped for high privacy protection. It is used to improve the user experience. These advantages in both BCO and ROA make the efficient performance in the suggested blockchain-based privacy preservation system by overcoming these conventional issues. The ABC-ROA algorithm is used to improve the performance of the developed blockchain-based data privacy preservation system. The ABC-ROA algorithm is implemented based on the current fitness and average fitness function. The term defines the current fitness , and the average fitness is denoted by the term . If , choose the random parameter otherwise, select as the random parameter value. However, in the conventional algorithm, the random parameter is selected randomly in the interval between . If then, select the ROA algorithm otherwise, select the BCO algorithm. The developed ABC-ROA algorithm increases the fitness function.
BCO [27]: Three dogs and sheep are considered in the Border collie optimization process. In a real-world scenario, one dog can manage the herd by himself. However, three dogs are considered because the search space for certain optimization issues might be large. When the algorithm is started, a group of three dogs and some lambs are exhibited here. The dogs are in charge of returning the sheep to the farm after they have gone out in different directions for grazing.
Random variables are used to initialize the positions of sheep and dogs. According to their positions, the dogs are designated lead, left, and right. From the front, the lead dog directs the herd. The person with the fitness is chosen to be the dog in front of the herd or the lead dog.
The major task of these dogs is to observe and stalk the herd. The terms and denotes the fitness values. The fitness of the sheep is known as . The velocity of the lead dog is calculated using Equation (28).
Then, the velocity of the left dog is measured using the given Equation (29).
The term is the acceleration of the dog and the term is the dog’s position. The term indicates the velocity of the dog. The right dog velocity is calculated using Equation (30).
Here, the variables , and is denoted by the velocity of time at for the right, left, and lead dogs. Moreover, the terms ,, and denotes the acceleration for lead, right, and left dogs. ,, and describes the position of lead, right, and left dogs.
Gathering: In the sheep gathering method, the updated sheep velocity is considered. The approaches of stalking, gathering and eyeing are used in this algorithm. The sheep near the lead dog follow the lead dog’s direction. The sheep that is closer to the lead dog is determined using Equation (31). Here, the term determines the positive shows the sheep nearer to the lead dog.
Equation (32) indicates the sheep’s velocity. The term is the current sheep location.
The variable is defined as the velocity of the sheep that is influenced by the lead dog.
Stalking: To keep the dogs to guide, they must stalk the sheep closer to the left and right dogs. The stalked sheep velocity is updated using Equations (33) and (34), respectively.
Consequently, the term represents the velocities of left and right dogs. Hence, the traversing angles of and is considered randomly.
Eyeing: In this scenario, it is anticipated that the least fit dog will follow the sheep and give them a close look. The velocity of the left dog is given in Equation (36). The variable and is described the velocity and acceleration of the left dog. Additionally, the term and is defined as the velocity and acceleration of the right dog. Hence, the term defines the collection of sheep that are presented in the current location. Additionally, the average time of individual can be represented as .
The velocity of the right dog is given in Equation (37).
The updated acceleration of the sheep and dog is calculated by Equation (38).
The updated time of the sheep and dog is measured by Equation (39).
The lead dog’s position is updated using Equation (40).
The left dog’s position is updated and calculated by Equation (41).
The position of the right dog is updated using Equation (42).
The updated locations of the sheep are determined using Equation (43) and Equation (44), respectively.
The eyed sheep are updated, and it is determined using below Equation (45).
Then, the sheep go to the track with the help of dog guidance, which is given in Equation (46).
The stalking, gathering and eyeing behavior over the sheep by a dog is described. By substituting the value of in Equations (46) and (47), the population values are attained based on the gathered sheep, left dog, stalked sheep, eyed sheep, and right dog.
ROA [28]: Raindrops fall on the ground randomly. A raindrop can serve as a metaphor for each possible solution. As raindrops fall randomly on the ground, certain places in the solution space can be chosen randomly. Each raindrop’s radius is the most distinguishing characteristic. As time passes and a raindrop is joined to other droplets, its radius can decrease time. The radius of each droplet can decrease the time and also increase the connectivity of other droplets within a suitable range after the first population of replies is generated. Every droplet checks its nearest neighborhood based on its size at each cycle. Check for the end of the area that a single droplet has covered if it is still unconnected to any other droplet. Every droplet has variables while we are addressing a problem in n dimensions. Here, the term is a large drop in radius.
Then, the radius and makes a large form of the raindrop. The term defines the variables in each droplet and is calculated using Equation (47).
Therefore, by increasing the number of iterations, weak droplets disappear, or the droplets create strong droplets.
The initial population will decrease continuously, causing a speed of determining the correct answer.
The term represents the soil characteristic given in Equation (48).
Here, the variable is the radius that does not move on the properties of the soil, which is depicted as . As a result, the droplet’s radius will be used to establish the lower and upper bounds of the variable in the initial stage. Two endpoints of the variable are examined in the next stage, and so on until the last variable. The term is an ordering cost and is measured using Equation (49).
The initial droplet cost would be adjusted at this point. The inventory holding cost is indicated by , and is given in Equation (50).
The shortage of the cost is denoted by and is shown in Equation (51).
The term is a transportation cost measured using Equation (52).
The objective of the solution is calculated by Equation (53).
Here, the term denotes the total cost. The total investment is indicated by , and it is shown in Equation (54).
Here, the term is an inventory capacity level. The fixed cost is represented by .
The term is total time calculated by Equation (55).
The number of raindrops is denoted by and the number of warehouses is represented by .
For each droplet, this situation would be repeated. Nearby droplets in their route may interact with one another, greatly speeding up the process. A droplet’s radius continuously decreased at the lowest point, greatly improving the accuracy of the response. The pseudocode of the implemented ABC-ROA is presented in Algorithm 1.
| Algorithm 1: Developed ABC-ROA |
| Initialize the population and acceleration value |
| Find the fitness solution |
| Calculate the velocity Using Equation (29). |
| For |
| For |
| If |
| Assign the value of |
| Else |
| Assign the value of |
| End if |
| If |
| Select the radius of the raindrop using Equation (50). |
| Update the solution with the ROA algorithm using Equation (51). |
| Else |
| Update the solution with the BCO algorithm using Equation (38). |
| Determine the best fitness of the sheep |
| Update the velocity of the sheep in the BCO algorithm |
| Evaluate the sheep’s position |
| Update the position of the sheep using Equation (32). |
| End if |
| End |
| End |
| Obtain the best position |
| End |
6. Results and Discussion
6.1. Simulation Setting
The developed ABC-ROA-based privacy preservation model over the Ethereum network by blockchain technology was implemented in the MATLAB environment. In this developed system, the chromosome length was set at five, and the population size was set at 10. The efficiency analysis was conducted over key sensitivity, cost function, Euclidean distance, known-plaintext attack (KPA), harmonic mean, known ciphertext attack (KCA), arithmetic mean, CCA, and CPA. The efficiency of the developed model has been compared through various heuristic algorithms such as Harris hawks optimizer (HHO) [28], entity framework Harris hawks optimizer (EF-HHO) [29], BCO [26], and ROA [27].
6.2. Effectiveness Analysis Using Euclidean Distance
The overall analysis of the recommended ABC-ROA-based privacy preservation model over the Ethereum network with three datasets in terms of Euclidean distance is given in Figure 5. From the analysis, dataset 2 gives a very low Euclidean distance than dataset 1 and 2. While using dataset 2, the developed ABC-ROA-based privacy preservation model gives improved Euclidean distance of 36.03%, 8.62%, 2.54%, and 8.77% over HHO, EF-HHO, BCO, and ROA. In the graph analysis, the developed ABC-ROA method is utilized to show effective performance. Here, the existing EF-HHO algorithm attains second-best performance. While considering all three datasets, the Euclidean distance of the proposed method shows better performance in dataset 2. Thus, the developed ABC-ROA-based data privacy preservation model over the Ethereum network gives higher effectiveness than the other heuristic algorithms.
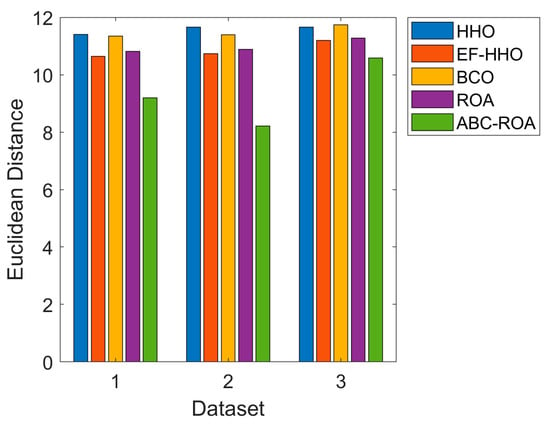
Figure 5.
Effectiveness analysis on the offered blockchain-based privacy preservation model using Euclidean distance.
6.3. Performance Analysis Using the Harmonic Mean
The harmonic mean analysis in terms of Euclidean distance, Pearson correlation, and the spearman correlation on the developed privacy preservation system over the Ethereum network among various datasets is given in Figure 6. In dataset 2, the developed ABC-ROA-based privacy preservation system over the Ethereum network provides enhanced harmonic means of25.71%, 27.77%, 35%, and 27.1% than HHO, EF-HHO, BCO, and ROA. From the given graph analysis, the Pearson correlation can be analyzed to measure the strength and direction between the two variables. Here, the Pearson correlation lies in the range of [−1 to 1]. Moreover, the negative correlation is denoted as “−1” as well as the positive correlation can be represented as “1”. However, Spearman’s correlation can be used to measure the association between the variables. As a result, the analysis of the designed ABC-ROA-based privacy preservation system is superior to the other heuristic approaches.
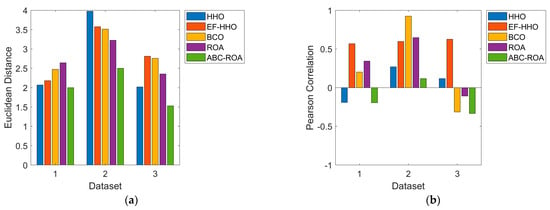
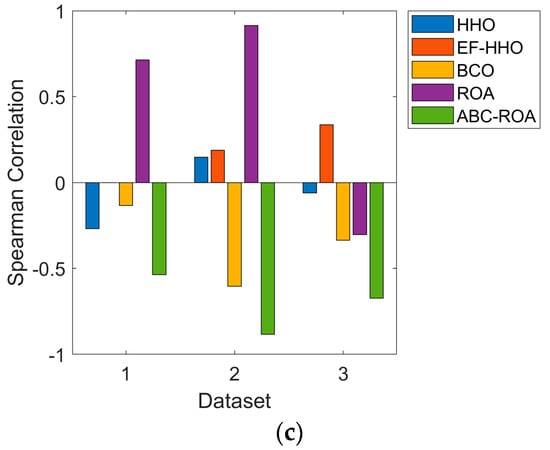
Figure 6.
Effectiveness analysis of the developed blockchain-based privacy preservation system to (a) Euclidean distance, (b) Pearson correlation and (c) Spearman correlation.
6.4. Effectiveness Analysis Using the Arithmetic Mean
Comparison of the Pearson and Spearman correlations of the designed ABC-ROA-based privacy preservation system among various heuristic algorithms is shown in Figure 7. The sum of the numerical values of each observation divided by the total number of observations is known as the arithmetic mean. From the analysis, the developed ABC-ROA-based privacy preservation achieves secured data transfer when dataset 3 shows a low value. Regarding the spearman correlation value in dataset 2, the developed ABC-ROA-based privacy preservation model has high arithmetic means of 40%, 20%, 20%, and 34.4%, better than HHO, EF-HHO, BCO, and ROA. As a result, the designed ABC-ROA-based privacy preservation system over the Ethereum network shows higher effectiveness than other heuristic algorithms.
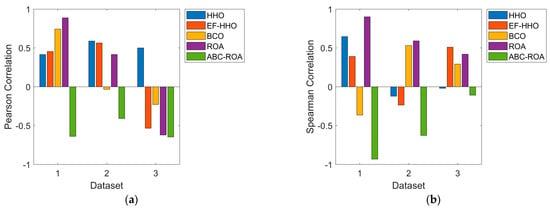
Figure 7.
Effectiveness analysis of the designed blockchain-based privacy preservation model in terms of (a) Pearson correlation and (b) Spearman correlation.
6.5. Cost Function Analysis on the Proposed Model
Comparison of the proposed ABC-ROA-based privacy preservation system convergence rate to existing meta-heuristic algorithms with various datasets is shown in Figure 8. Compared to HHO, EF-HHO, BCO, and ROA, the performance of the ABC-ROA-based privacy preservation system, the cost function is highly improved by 2.98%, 3.07%, 3.56%, and 4.12%, respectively, in dataset 3 at iteration value of 15. If the iteration increases, then the cost function of the designed ABC-ROA method gets decreased. Hence, the graph analysis shows better performance in the recommended method. The existing EF-HHO algorithm achieves second-best performance. As a result, the developed ABC-ROA-based privacy preservation model using blockchain technology performs more effectively than other algorithms.
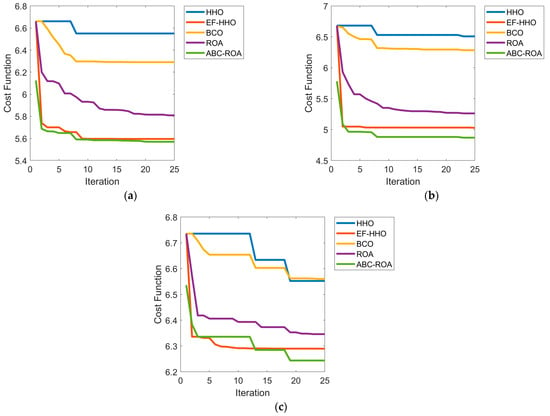
Figure 8.
Convergence analysis on developed blockchain-based privacy preservation model in terms (a) dataset 1, (b) dataset 2, and (c) dataset 3.
6.6. Effectiveness Analysis Using Key Sensitivity
The key sensitivity of the obtained optimum key in the ABC-ROA-based privacy preservation system for three datasets with various existing meta-heuristic algorithms at various percentage levels is shown in Figure 9. The key sensitivity of the proposed system is noticed as a lower value while increasing the percentage of the key for all the three datasets. From the analysis, the developed model shows key sensitivity improvements of 11%, 15%, 20%, and 19% to heuristic algorithms such as HHO, EF-HHO, BCO, and ROA, respectively. In the given graph analysis, it shows the equivalence performance. Based on the key sensitivity value, the ROA algorithm is not effective to secure the data in the blockchain. At learning percentage 30, the key sensitivity of the existing EF-HHO algorithm secures second-best performance. As a result, the suggested blockchain-based privacy preservation model executes more effectively than other heuristic algorithms.
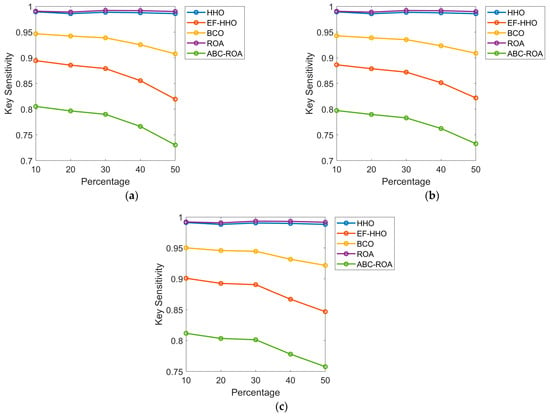
Figure 9.
Performance analysis of the designed blockchain-based privacy preservation model concerning (a) dataset 1, (b) dataset 2, and (c) dataset 3.
6.7. Performance Analysis Using CPA and CCA
Comparison of performance analysis of the ABC-ROA-based privacy preservation system over the existing heuristic algorithms in terms of chosen ciphertext attacks (CCA) and chosen plaintext attacks (CPA) with three datasets is given in Table 2 and Table 3, respectively. In CPA, the attacker can be used to encrypt the message. Hence, the goal of the CPA attack is to reduce the security of the encryption scheme. Here, symmetric and asymmetric cryptography can be used. However, the CPA is often feasible in the diverse applications. Since the CPA is essential for public key cryptography where the encryption key is public and so attackers can encrypt any plaintext they choose. Moreover, the CCA can able to decrypt the ciphertext message. Here, the CCA can be widely used in cryptanalysis to collect information by obtaining the decryptions of the chosen ciphertext, since it needs to recover the hidden secret key which is used for the decryption. The proposed model has more secure shared data in the transmission while analyzing the results. The CCA value of the developed system is guaranteed with a lower value on raising the proportion of key variations for all three datasets. From the dataset 2 analysis of CPA, the ABC-ROA-based privacy preservation model has high performance of 7.58%, 5.93%, 4.15%, and 7.64% than HHO, EF-HHO, BCO, and ROA for the key variations of 50. The proposed blockchain-based privacy preservation model is more effective than other heuristic algorithms.

Table 2.
Effectiveness analysis using CCA with three datasets for the developed blockchain-based data privacy preservation system over Ethereum network.

Table 3.
Effectiveness analysis using CPA with three datasets for the developed blockchain-based data privacy preservation system over Ethereum network.
6.8. Statistical Analysis of the Designed Method
The statistical analysis of the designed blockchain-based data privacy preservation system over the Ethereum network is shown in Table 4. The designed ABC-ROA method attains 14.9%, 0.7%, 11.4%, and 4.1% better performance than HHO, EF-HHO, BCO, and ROA regarding dataset 1. Throughout the analysis, the experimental outcome has attained superior performance when compared to other traditional approaches.

Table 4.
Statistical analysis on developed data privacy preservation model over the Ethereum network.
6.9. ANOVA Test for the Developed Data Privacy Preservation Model over the Ethereum Network
The validation of the ANOVA test for the designed ABC-ROA method regarding fitness function is shown in Figure 10. Thus, the experimental result of the developed method attains superior performance compared to other traditional approaches.
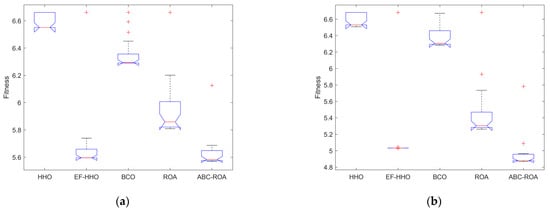
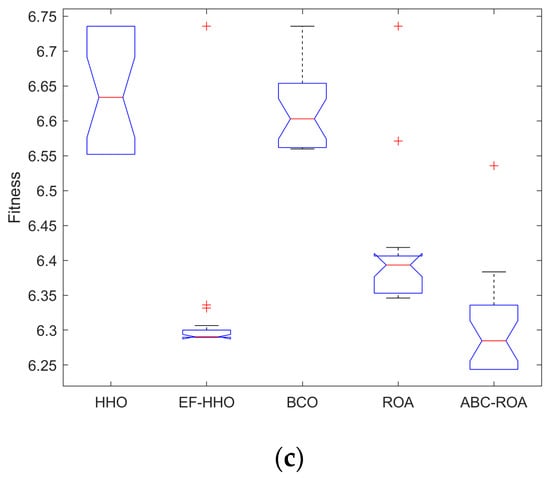
Figure 10.
ANOVA of the designed method for privacy preservation over the Ethereum network regarding fitness function (a) dataset 1, (b) dataset 2, and (c) dataset 3.
6.10. Validation of Control for Parameters of Different Algorithms Using the Designed Method
The validation of control for parameters of different existing algorithms regarding Euclidean distance and Pearson and Spearman correlations is shown in Figure 11. Here, the evaluation of the parameter for the proposed ABC-ROA method is taken as ird = 0.06. Throughout the analysis, the developed method achieves enhanced performance compared to the other existing methods.
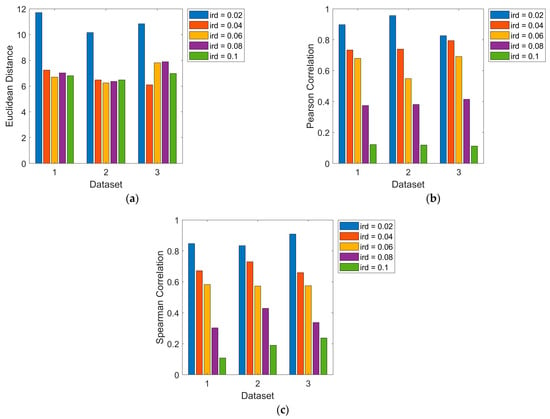
Figure 11.
Analysis of controlling the parameters of the designed method using (a) Euclidean distance, (b) Pearson correlation, and (c) Spearman correlation.
7. Security Analysis
The developed ABC-ROA-based privacy preservation system model is evaluated with various attacks such as KCA, KPA, adaptive chosen-plaintext analysis (ACPA), and Ciphertext-Only Analysis (COA) assessed based on three datasets by comparing with recently used algorithms, as shown in Figure 12, Figure 13, Figure 14 and Figure 15, respectively. Correlating one original datum with all original data and one sanitized datum with all sanitized data defines KPA analysis. KCA analysis is described as correlating each sanitized data with its data restored data. The ACPA attack is similar to the CPA attack. It selects the plaintext and ciphertext that are learned from past encryptions. In a COA attack, it uses known data collection. In the ABC-ROA-based privacy preservation system, the ACPA, COA, KPA, and KCA analysis shows the lowest value and indicates the minimum error. While analyzing the evaluation of different attacks for the designed ABC-ROA method, it is revealed that the designed ABC-ROA based privacy preservation over the Ethereum network attains effective performance.
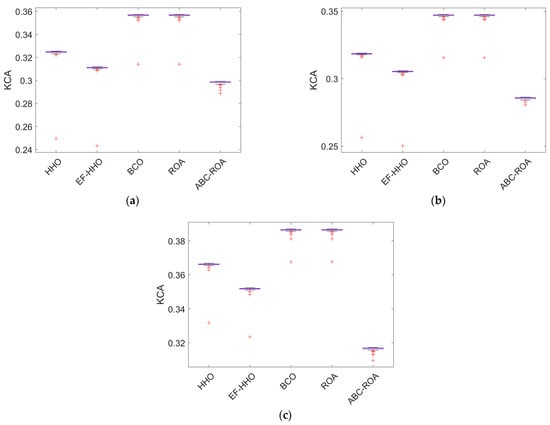
Figure 12.
Effectiveness analysis of the implemented ABC-ROA based privacy preservation model using KCA in terms of (a) dataset 1, (b) dataset 2, and (c) dataset 3.
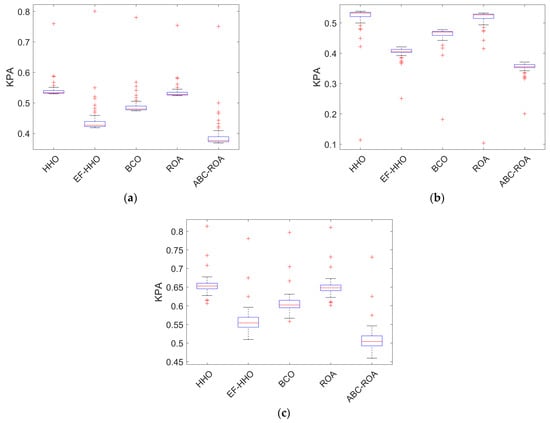
Figure 13.
Performance analysis of the developed ABC-ROA based privacy preservation model using KPA regarding (a) dataset 1, (b) dataset 2, and (c) dataset 3.
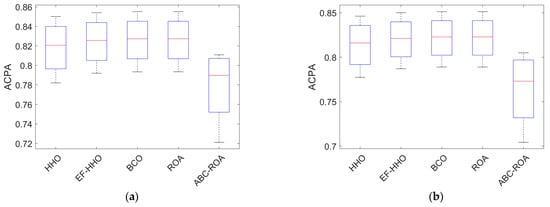
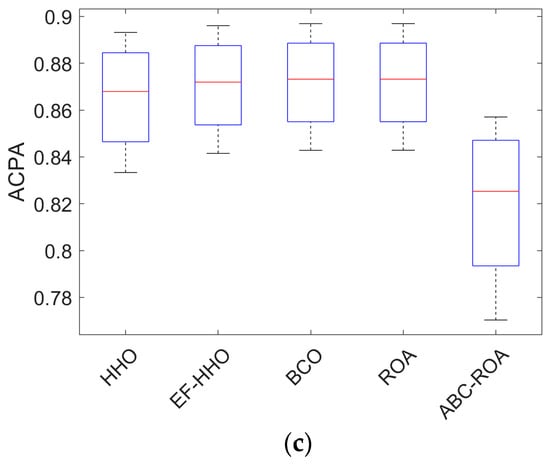
Figure 14.
Performance analysis of the developed ABC-ROA based privacy preservation model using ACPA regarding (a) dataset 1, (b) dataset 2, and (c) dataset 3.
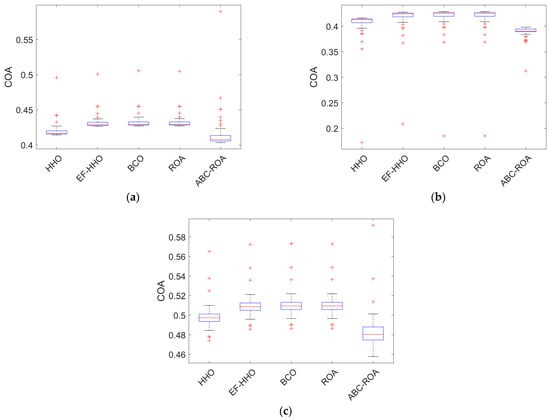
Figure 15.
Performance analysis of the developed ABC-ROA based privacy preservation model using COA regarding (a) dataset 1, (b) dataset 2, and (c) dataset 3.
8. Conclusions
A new blockchain-based privacy preservation model over the Ethereum network was developed for preserving data privacy using blockchain technology. The data were collected from standard databases. Initially, the data were sanitized, and an optimal key developed using the ABC-ROA algorithm. The optimal key generation followed the objective functions HF rate, IP rate, FR, and DM. The sanitized data progressed to the data restoration process, which restored the data in the database. These data were formed as subchains, known as the supply chain framework. The developed blockchain framework gave better privacy for the data over the supply chain network with the help of the generated optimal key. The effectiveness of the proposed blockchain-based privacy preservation model was compared with the existing privacy preservation models. The proposed ABC-ROA-based privacy preservation model performed 20.2% better than HHO, 17.4% better than EF-HHO, 13.7% better than BCO, and 20.7% better than ROA while considering dataset 2 with the key variation of 50. Therefore, compared to other privacy preservation approaches, the developed ABC-ROA-based privacy preservation model performs better for all key variations than other heuristic algorithms. One of the most important challenges in the existing privacy preservation model over the Ethereum network is scalability. Due to the scalability issues, it cannot provide the optimal solution, and also it generates issues such as inefficiency and limited block size. In this research, the developed ABC-ROA method was utilized to solve these issues. The estimation of convergence and optimization of deep-structure architectures were utilized to resolve the scalability issues. Moreover, implementing standard machine learning and deep learning approaches provides the ability to solve these issues.
Author Contributions
Conceptualization, Y.V.R.S.V.; Methodology, Y.V.R.S.V.; Data curation, Y.V.R.S.V.; Writing—Original draft preparation, Y.V.R.S.V.; Visualization, K.J.; Investigation, K.J.; Validation, Y.V.R.S.V.; Reviewing and Editing, K.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research did not receive any specific funding.
Data Availability Statement
The data underlying this article are available in DataCo Smart Supply Chain for Big Data Analysis database, at https://www.kaggle.com/shivkp/customer-behaviour (accessed on 10 January 2023).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Weng, J.; Weng, J.; Zhang, J.; Li, M.; Zhang, Y.; Luo, W. DeepChain: Auditable and Privacy-Preserving Deep Learning with Blockchain-Based Incentive. IEEE Trans. Dependable Secur. Comput. 2021, 18, 2438–2455. [Google Scholar] [CrossRef]
- Tahir, S.; Tahir, H.; Sajjad, A.; Rajarajan, M.; Khan, F. Privacy-preserving COVID-19 contact tracing using blockchain. J. Commun. Netw. 2021, 23, 360–373. [Google Scholar] [CrossRef]
- Huang, C.; Zhao, Y.; Chen, H.; Wang, X.; Zhang, Q.; Chen, Y.; Wang, H.; Lam, K.-Y. ZkRep: A Privacy-Preserving Scheme for Reputation-Based Blockchain System. IEEE Internet Things J. 2021, 9, 4330–4342. [Google Scholar] [CrossRef]
- Wu, G.; Wang, S.; Ning, Z.; Zhu, B. Privacy-Preserved Electronic Medical Record Exchanging and Sharing: A Blockchain-Based Smart Healthcare System. IEEE J. Biomed. Health Inform. 2021, 26, 1917–1927. [Google Scholar] [CrossRef] [PubMed]
- Yang, Y.; Wu, J.; Long, C.; Liang, W.; Lin, Y.-B. Blockchain-Enabled Multiparty Computation for Privacy Preserving and Public Audit in Industrial IoT. IEEE Trans. Ind. Inform. 2022, 18, 9259–9267. [Google Scholar] [CrossRef]
- Du, R.; Ma, C.; Li, M. Privacy-Preserving Searchable Encryption Scheme Based on Public and Private Blockchains. Tsinghua Sci. Technol. 2023, 28, 13–26. [Google Scholar] [CrossRef]
- Yang, Q.; Wang, H. Privacy-Preserving Transactive Energy Management for IoT-Aided Smart Homes via Blockchain. IEEE Internet Things J. 2021, 8, 11463–11475. [Google Scholar] [CrossRef]
- Tran, Q.N.; Turnbull, B.P.; Wu, H.-T.; de Silva, A.J.S.; Kormusheva, K.; Hu, J. A Survey on Privacy-Preserving Blockchain Systems (PPBS) and a Novel PPBS-Based Framework for Smart Agriculture. IEEE Open J. Comput. Soc. 2021, 2, 72–84. [Google Scholar] [CrossRef]
- Yang, Y.; Wei, L.; Wu, J.; Long, C.; Li, B. A Blockchain-Based Multidomain Authentication Scheme for Conditional Privacy Preserving in Vehicular Ad-Hoc Network. IEEE Internet Things J. 2021, 9, 8078–8090. [Google Scholar] [CrossRef]
- Baza, M.; Sherif, A.; Mahmoud, M.M.E.A.; Bakiras, S.; Alasmary, W.; Abdallah, M.; Lin, X. Privacy-Preserving Blockchain-Based Energy Trading Schemes for Electric Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 9369–9384. [Google Scholar] [CrossRef]
- Zhang, X.; Jiang, S.; Liu, Y.; Jiang, T.; Zhou, Y. Privacy-Preserving Scheme with Account-Mapping and Noise-Adding for Energy Trading Based on Consortium Blockchain. IEEE Trans. Netw. Serv. Manag. 2021, 19, 569–581. [Google Scholar] [CrossRef]
- Wu, Y.; Tang, S.; Zhao, B.; Peng, Z. BPTM: Blockchain-Based Privacy-Preserving Task Matching in Crowdsourcing. IEEE Access 2019, 7, 45605–45617. [Google Scholar] [CrossRef]
- Abdelsalam, H.A.; Srivastava, A.K.; Eldosouky, A. Blockchain-Based Privacy Preserving and Energy Saving Mechanism for Electricity Prosumers. IEEE Trans. Sustain. Energy 2021, 13, 302–314. [Google Scholar] [CrossRef]
- Zou, S.; Xi, J.; Xu, G.; Zhang, M.; Lu, Y. CrowdHB: A Decentralized Location Privacy-Preserving Crowdsensing System Based on a Hybrid Blockchain Network. IEEE Internet Things J. 2021, 9, 14803–14817. [Google Scholar] [CrossRef]
- Rahman, M.S.; Khalil, I.; Moustafa, N.; Kalapaaking, A.P.; Bouras, A. A Blockchain-Enabled Privacy-Preserving Verifiable Query Framework for Securing Cloud-Assisted Industrial Internet of Things Systems. IEEE Trans. Ind. Inform. 2021, 18, 5007–5017. [Google Scholar] [CrossRef]
- Zhang, C.; Zhu, L.; Xu, C.; Sharif, K. PRVB: Achieving Privacy-Preserving and Reliable Vehicular Crowdsensing via Blockchain Oracle. IEEE Trans. Veh. Technol. 2020, 70, 831–843. [Google Scholar] [CrossRef]
- Chulerttiyawong, D.; Jamalipour, A. A Blockchain Assisted Vehicular Pseudonym Issuance and Management System for Conditional Privacy Enhancement. IEEE Access 2021, 9, 127305–127319. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Huang, X.; Xie, X.; Choo, K.-K.R. PPChain: A Privacy-Preserving Permissioned Blockchain Architecture for Cryptocurrency and Other Regulated Applications. IEEE Syst. J. 2021, 15, 4367–4378. [Google Scholar] [CrossRef]
- Rahmadika, S.; Astillo, P.V.; Choudhary, G.; Duguma, D.G.; Sharma, V.; You, I. Blockchain-Based Privacy Preservation Scheme for Misbehavior Detection in Lightweight IoMT Devices. IEEE J. Biomed. Health Inform. 2022, 27, 710–721. [Google Scholar] [CrossRef]
- Xiong, T.; Zhang, R.; Liu, J.; Huang, T.; Liu, Y.; Yu, F.R. A blockchain-based and privacy-preserved authentication scheme for inter-constellation collaboration in Space-Ground Integrated Networks. Comput. Netw. 2022, 206, 108793. [Google Scholar] [CrossRef]
- Singh, S.; Rathore, S.; Alfarraj, O.; Tolba, A.; Yoon, B. A framework for privacy-preservation of IoT healthcare data using Federated Learning and blockchain technology. Futur. Gener. Comput. Syst. 2021, 129, 380–388. [Google Scholar] [CrossRef]
- Guo, L.; Xie, H.; Li, Y. Data encryption based blockchain and privacy preserving mechanisms towards big data. J. Vis. Commun. Image Represent. 2019, 70, 102741. [Google Scholar] [CrossRef]
- Mohan, D.; Alwin, L.; Neeraja, P.; Lawrence, K.D.; Pathari, V. A private Ethereum blockchain implementation for secure data handling in Internet of Medical Things. J. Reliab. Intell. Environ. 2021, 8, 379–396. [Google Scholar] [CrossRef]
- Elisa, N.; Yang, L.; Chao, F.; Cao, Y. A framework of blockchain-based secure and privacy-preserving E-government system. Wirel. Netw. 2018, 1–11. [Google Scholar] [CrossRef]
- Dewangan, N.K.; Chandrakar, P.; Kumari, S.; Rodrigues, J.J. Enhanced privacy-preserving in student certificate management in blockchain and interplanetary file system. Multimedia Tools Appl. 2022, 1–20. [Google Scholar] [CrossRef]
- Abidi, M.H.; Alkhalefah, H.; Umer, U.; Mohammed, M.K. Blockchain-based secure information sharing for supply chain management: Optimization assisted data sanitization process. Int. J. Intell. Syst. 2020, 36, 260–290. [Google Scholar] [CrossRef]
- Dutta, T.; Bhattacharyya, S.; Dey, S.; Platos, J. Border Collie Optimization. IEEE Access 2020, 8, 109177–109197. [Google Scholar] [CrossRef]
- Moazzeni, A.R.; Khamehchi, E. Rain optimization algorithm (ROA): A new metaheuristic method for drilling optimization solutions. J. Pet. Sci. Eng. 2020, 195, 107512. [Google Scholar] [CrossRef]
- Elgamal, Z.M.; Yasin, N.B.M.; Tubishat, M.; Alswaitti, M.; Mirjalili, S. An Improved Harris Hawks Optimization Algorithm with Simulated Annealing for Feature Selection in the Medical Field. IEEE Access 2020, 8, 186638–186652. [Google Scholar] [CrossRef]
- Hu, H.; Ao, Y.; Bai, Y.; Cheng, R.; Xu, T. An Improved Harris’s Hawks Optimization for SAR Target Recognition and Stock Market Index Prediction. IEEE Access 2020, 8, 65891–65910. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).