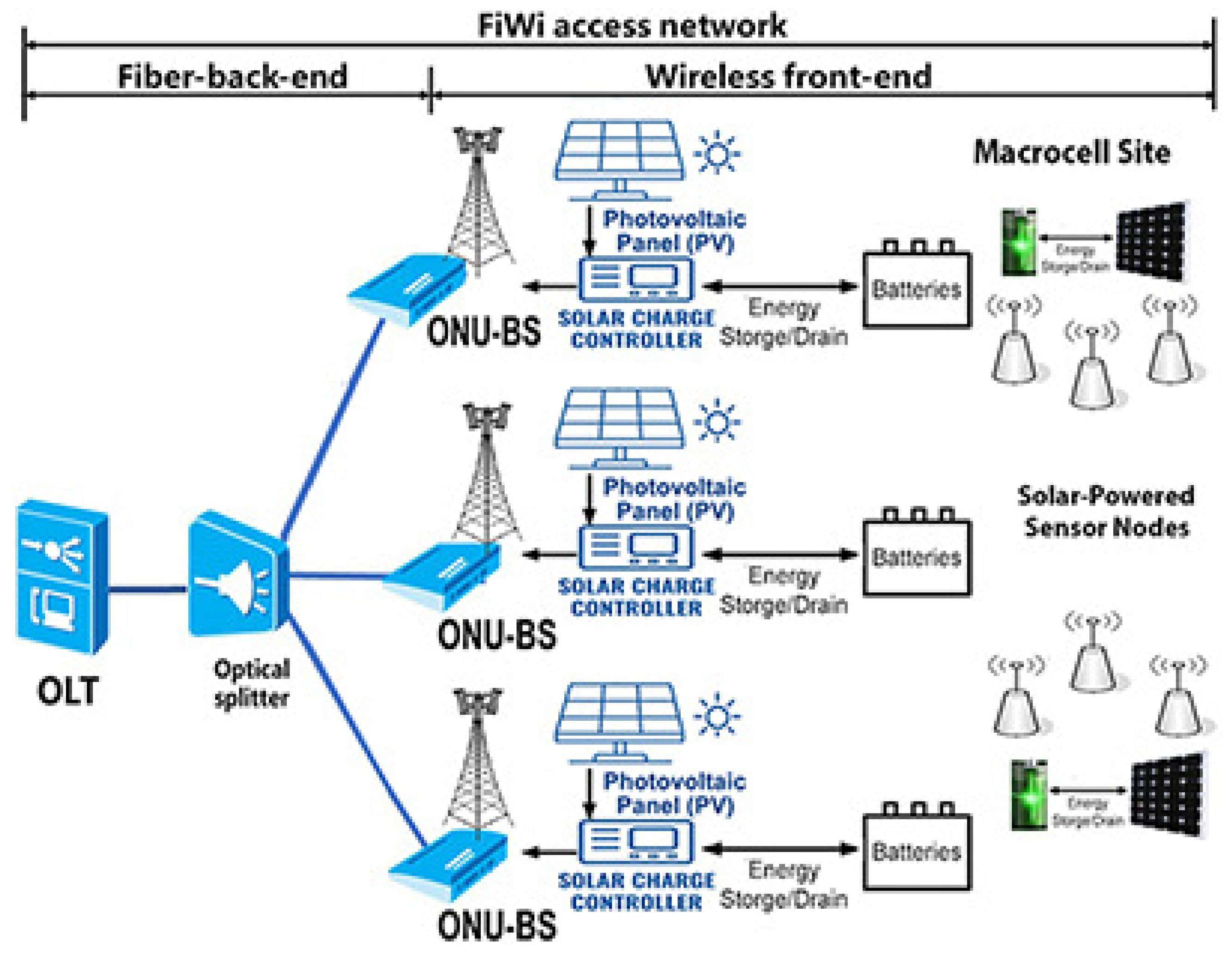
1. Introduction
Renewable energy sources, including solar, wind, and geothermal, have already been integrated into domestic and utility power systems to reduce the carbon footprints and environmental degradation. As solar energy is easily available, it is the most commonly used form of renewable energy [
1].
The ever-growing demand to provide broadband coverage to urban and rural regions may cause a significant increase in energy consumption, especially in rural areas, where the grid power supply is limited. Moreover, for sensor devices and Internet of Things (IoT) setups, power supply can be even more challenging, since environmental-monitoring IoT applications may be deployed in remote areas where no power grid is available [
2,
3,
4]. In such grid-less installations, the power supply of the access points (APs) collecting data from sensors is a crucial issue [
5]. Therefore, the exploitation of solar energy using photovoltaic (PV) technology, such as solar panels, is very crucial. From a networking point of view, a lot of capacity to satisfy the increasing bandwidth demands of numerous users and IoT devices. Thus, fiber-wireless (FiWi) networks are a perfect choice since they exploit both optical and wireless technologies for a large aggregate bandwidth and cordless deployment of sensors, respectively [
6]. The architecture of a FiWi network contains a passive optical network (PON) backbone comprising a number of optical network units (ONUs) connected to APs and providing, through them, connectivity to a number of wireless sensors. In such network setups, including devices that should operate in areas far from the power grid, renewable energy sources, mainly solar, have to be exploited to power their components, i.e., ONUs and APs.
However, apart from the energy issues, the security of such solar-powered (SP) FiWi networks’ infrastructure is a significant issue as well, since they are typically deployed outdoors in remote areas. They can become targets of attackers who may want to disrupt network services and bring them down, thereby causing high repair costs [
7]. Hence, energy awareness, as well as the security and secure operation of solar- and/or battery-powered devices that are vital parts of SP FiWi networks, is a real challenge that has to be addressed. Particularly, it is of fundamental importance in such networks that the battery operation characteristics of their devices should ensure online operation, overcoming various challenges. Predominantly, the battery capacity should ensure the uninterrupted functionality of the network system, taking into consideration the fluctuations of solar energy. During cloudy days, such a system may not be able to reach full battery capacity, resulting in possible power outages that should be avoided. Moreover, as such networks operate far from urban environments, they are prone to a range of attacks such as tampering and intrusions. Including, but not limited to, the man-in-the-middle (MITM) attack, which stands as one of the purposes behind tampering the physical devices of the premises of a SP PON network. Dictated by the fact that MITM attacks can result in network outages through denial of service (DoS) attacks, the presence of a communication protocol that could mitigate the results of this type of threat has become more and more of a necessity for modern SP PON-based FiWi networks.
In this paper we deal with the following problem. We consider an SP PON-based FiWi access network that consists of an OLT, a number of battery-powered ONUs and employs an ONU energy saving mechanism based on control message exchanges between OLT and ONUs. We also consider the presence of an attacker that intercepts the downstream communication and acts as a MITM aiming to attack the energy saving mechanism so as to drain the ONU’s battery-based energy resources. We propose mechanisms to improve energy saving for the ONU in case of normal operation as well as proactively countermeasure attacks that aim to drain its energy resources.
The two proposed energy-aware mechanisms, namely the wake-up and time-out mechanisms, operate in the PON part of the network. We employ a formal verification analysis along with probabilistic model checking as a means to verify their energy impact. The main idea is to model these mechanisms on a SP PON-based FiWi network under a MITM attack and derive quantitative results that verify the improvements in ONU energy expenditure. Our analysis shows that both of them can effectively decrease the ONUs’ energy consumption, while the latter can additionally countermeasure the battery drain caused by a MITM attack.
The rest of the paper is organized as follows.
Section 2 discusses the importance and real-life applications of SP FiWi networks, related energy-aware studies regarding ONU devices, and the novelty of this work.
Section 3 presents and describes the proposed energy-efficient mechanisms, namely the
wake-up and
time-out mechanisms, appropriate for SP PON-based FiWi networks. Preliminaries of formal verification are explained in
Section 4. In
Section 5 the model we designed is presented, while
Section 6 discusses our quantitative verification results. Finally,
Section 7 concludes the paper.
3. Improving Energy Efficiency in a Solar-Powered Fiwi Access Network
In this paper, we design and evaluate two energy-aware mechanisms to study the energy-efficiency of a SP PON-based FiWi network: (i) the wake-up mechanism, in which the optical line terminal (OLT) sends a wake-up message to the ONU to receive downstream traffic once the latter has completed the listen or sleep cycle; (ii) the time-out mechanism, which notifies the ONU to transit to the listen and sleep modes when no request message has been received for a pre-defined interval period, i.e., an indication of a MITM attack.
In more detail, the ONU has three different modes of operation,
active,
listen, and
sleep, where the energy consumption of each power mode is 3.85 W, 1.28 W, and 0.75 W, respectively, according to the work of [
21]. Both ONU and OLT have their own upstream and downstream queues, respectively, and exchange their traffic. Assuming that the ONU is currently in active mode, our baseline mechanism [
21] dictates that once the OLT queue is empty, the OLT should send a
request message to the ONU. When the ONU receives the request, it replies with an
message if the ONU queue is empty and transits to the listen mode, or with a
message if it is not, and stays in the active mode to proceed with data transmission.
Figure 2a depicts the idea of the
wake-up mechanism, which complements the aforementioned baseline mechanism to achieve higher energy saving for the ONU. More precisely, once the ONU replies with an
message, the ONU will transit to the listen mode. While in listen mode, all downstream traffic is buffered in the OLT’s queue. If any upstream traffic appears during the listen mode, the ONU will transit to the active mode and transmit it. Once the listening cycle has been completed, the ONU will receive a
wake-up notification message from the OLT in case downstream traffic appears during its listening cycle; thus, it returns to the active mode in order to receive that downstream traffic. If neither downstream traffic has appeared in the OLT’s queue nor upstream traffic has appeared in ONU’s queue during ONU’s listening cycle, the ONU will not receive any
wake-up message and will, thus, transit to the sleep mode.
The ONU sleep mode cannot be interrupted, and as a result, both the OLT and the ONU will buffer their packets until the ONU completes the sleep cycle. There are three possible transition choices once the ONU’s sleep cycle expires: (i) if upstream traffic has arrived in the ONU’s queue during its sleep cycle, the ONU will transit to the active mode to serve it; (ii) if downstream traffic has arrived in the OLT’s queue during ONU’s sleep cycle, the ONU will receive a wake-up message to transit to active mode in order to receive this traffic; and (iii) if neither upstream nor downstream traffic appears during the ONU’s sleep cycle, the ONU will transit to the listen mode.
Figure 2b shows how the ONU can transit among the active, listen, and sleep states following the
wake-up mechanism. Transitions among the ONU states are identified by the messages exchanged between the OLT and ONU using the labels
,
, or
wake-up, while the traffic within the queues is identified by either the label “Traffic” or “No traffic”. Furthermore, the ONU’s transition rates between the active, listen and sleep power modes are presented, where notation
expresses the transition rate from state x to x’. The time period
specifies the rate to stay in the state, i.e.,
. In more detail, as
specifies the time period to remain in the listening state, the rate
is used. This means that if the listen period is too long, the energy saving would be deteriorated, and if the listen period is too short, the ONU would be forced to make early transitions to sleep, which would increase the packets’ delay. In addition, the rate at which we remain in sleep state can be expressed as
for a period of
duration. The trade-off under consideration is significantly influenced by the length of the sleep period because short sleep periods increase packet delay but reduce overall energy savings. In this work, we derive the
and
values from our previous analysis [
18]. However, both of them can be configured according to the problem under investigation, since they are parameters in the model.
The transition times for ONU’s state transitions derived by [
18] are presented in
Table 2. As shown in
Table 2, transitions from active to listen mode is of the nanoseconds’ order and, thus, the corresponding transition rate,
, and as with
, the rate
is not taken into account in the model. Further, the table shows the transition time needed between listen to the sleep mode. When the listen period expires, the ONU transits to the sleep mode with rate
in 2.88 μs, which is the time required by the ONU to turn off its transceiver. Finally, the transition time from sleep to active mode is shown. In the event that
expires, the ONU transits to the active mode with rate
, which requires a significant amount of time, i.e., 2 ms, in order to turn on its transceivers and to synchronize with the network [
19].
Since PONs are vulnerable to attacks because of their broadcasting architecture, we assume that a MITM attack, which is inspired by the work of [
21], disrupts the operation of the
wake-up mechanism.
Figure 3a shows that an attacker stands between the OLT and the ONU, intercepts the OLT’s sleep requests meant for the ONU and replies steadily with a
message in order to force the ONU to stay in the energy-consuming active mode. In the case of a battery-powered ONU, the attacker can successfully execute a DoS attack. Our way to countermeasure such attacks is by applying the
time-out mechanism, as shown in
Figure 3b.
We define a time-out interval period that resets every time: (i) the ONU receives downstream traffic from the OLT, (ii) the ONU transmits upstream traffic to the OLT, and (iii) the ONU receives a sleep request from the OLT. If the ONU does not receive or transmit any traffic nor receive any sleep request during this interval period, it transits to the listen mode. Namely, no activity during the time-out period operates as an alarm indication, which protects ONU’s energy levels by forcing it to leave the active mode.
Considering the ONU’s power consumption in active, listen, and sleep modes, the two suggested mechanisms contributed to the reduction in the ONU’s energy consumption, which entails energy efficiency improvement on a SP PON-based FiWi.
Figure 2a shows that the ONU wakes up, by receiving the
wake-up message sent by the OLT and transits to active mode only when downstream traffic appears. Otherwise, it does not receive it, and, thus, it transits to the listen mode, and then to the sleep mode, reducing its power consumption. Moreover, in
Figure 3a, the ONU increases its power consumption since the attacker forces the ONU to stay in active mode [
21].
On the contrary, the proposed
time-out mechanism acts as a guard time and prevents energy exhaustion for the ONU. While the ONU’s queue is empty, the device change to the listen and sleep mode successively. Due to the
time-out interval, the ONU is not deceived by the attacker’s
messages, and it transits to the listen mode and eventually to the sleep mode, as shown in
Figure 3b. Thus, it reduces its energy consumption since it stays for less time in the active mode. That way, the system avoids the service outage and countermeasures the attack.
The proposed mechanisms do not increase the computational overhead of the system implementation. The mechanisms employ only control message exchanges, which does not require any additional computation. The main addition is related to the existence of a timer that fires the next transition without the use for polling mechanisms or any other CPU-demanding processes. Computational time is affected only in the study of the approach via model checking, as it affects the time the model requires to finish.
4. Formal Verification for SP PON-Based FiWi Energy Analysis
Model checking is an automated verification and validation technique based on exploring the states of a model of a real-life system [
25]. Probabilistic model checking computes probabilities and quantitative measurements, such as the expected power consumption. It can be successfully applied to many application domains, e.g., new communication technologies, communication protocols, security protocols, etc. Furthermore, it requires the construction of a probabilistic model, e.g., Markov chain,
M, derived from a description of a probabilistic system by using a high-level modelling language and the formal specification of quantitative properties which are declared as formulae
based on temporal logic. To verify the quantitative properties of a system model, probabilistic model checking typically explores the model’s full state space [
18]. On this basis, we assess the energy impact of the two suggested energy-efficient mechanisms on an SP PON-based FiWi from
Section 3.
In order to represent a system with probabilistic behavior, we build a Markov-based model that contains a set of states and a number of state transitions from one state to another. There are a number of probabilistic models, namely discrete-time Markov chains (DTMCs) and continuous-time Markov chains (CTMCs), Markov decision processes (MDPs), etc. Among them, DTMC is fully probabilistic, in the sense that one can specify the probability of making a transition from one state to another. While CTMCs represent probabilistic choice similarly to DTMCs, they also permit modeling of continuous real time, rather than discrete time-steps, and specify the rate of state transitions. From a probabilistic model checking perspective, CTMC is a suitable choice due to its advantage to represent transitions that occur between each pair of states specified by a value and labels.
In this work, our model represents the ONU-OLT communication along with the mechanisms discussed in
Section 3, as well as an MITM attack scenario disrupting their operation using CTMC [
26]. For the proposed model, the ONU’s transition rates among its states, i.e., active, listen, sleep, as they presented at the state machine of
Figure 2b, the attacker’s rate and the packet’s arrival and service rates correspond to the CTMCs primitives. Because of this, we opted for CTMC since it perfectly fits for our modeling. Along the same lines, similar proposals were made in previous works published in the literature, concerning the use of CTMC modeling. For example, in [
27], CTMC is also used in a model that concerns the computational and transmission costs of security protocols in hardware-constrained environments; additionally, in [
28], the near field communication (NFC) protocol is tested against a relay attack by means of model checking and CTMC, as well as the authors in [
21] develop a CTMC representation of an MITM attack on an Ethernet passive optical network (EPON) energy-efficiency mechanism together with cost-related properties that are verified over the full state space of the model.
The CTMC principles are further described in order to explain the observed model’s behavior. Formally, the proposed model which is a tuple
, consists of
S, which is a countable set of states,
is the initial state, a transition rate matrix
and a labeling function
. The rates
are stored in the so-called rate matrix
R, which represents a transition from a state
s to
within time
t. The probability of this transition is described as a negative exponential distribution
, the parameter of which is the transition rate of
[
25]. Labels are defined to model the transitions of the system by the labeling function
that assigns one or more of
taken from the set
, to any state
s of the system.
In addition to the probabilistic results, CTMC supports also rewards to receive quantitative results of the system model, such as power consumption. A reward structure enhances the structure of a given CTMC model. It consists of a tuple, where is the state reward function and is the transition reward function. Although there are four types of rewards, we use in our model the cumulative reward of the form , which states that the expected reward cumulated up to time-instant t is , and the instantaneous reward property of the form , which states that the expected value of the reward at time-instant t is , where the relation operator .
In our analysis, instantaneous rewards represent the expected packet delay, whereas cumulative rewards represent the expected energy consumption. The time property of these rewards is usually derived using probabilistic results.
5. Modeling of the Energy-Aware Mechanisms
In this paper, we use probabilistic model checking as a way to verify improvements in energy saving achieved by the two proposed mechanisms, namely the
wake-up and the
time-out mechanisms. We assume SP PON-based FiWi under a MITM attack, an EPON system in our case, taking into account our initial findings [
21].
In practice, we use the Prism model checker [
26] and define five modules, namely
,
,
,
,
, which correspond to the OLT and ONU devices, their own queues, and the attacker, respectively. The behavior of each module of our CTMC model is described by a set of commands.
The modules and represent the queues of OLT and ONU, respectively. They receive and buffer a number of data packets in either downstream or upstream directions, correspondingly. Packets’ arrival and service are controlled by the rates: (i) for downstream packets’ arrival; (ii) for the upstream packets’ arrival; and (iii) for their service rate.
The behavior of the legitimate OLT and ONU devices is modeled by the modules
and
, respectively. The packets’ transmission between the OLT and the ONU in either direction depends on the aforementioned rates, i.e.,
,
, and
, as well as on the ONU’s state, i.e., active, listen, or sleep. In the module
, the time spent in the listen mode is denoted as
and specifies the rate
of staying in this mode, while the time spent in the sleep mode is defined as
and specifies the rate
of staying in the sleep mode. The devices communicate when the ONU is in active mode, while the other two modes contribute to the ONU’s energy saving when no traffic exists. Regarding the baseline energy-aware mechanism [
21], it is modeled by exchanging the control messages, i.e.,
,
, and
, between the OLT and the ONU.
The module models the attacker’s behavior, which connects a fake OLT device between the legitimate OLT and ONU. The fake OLT intercepts the requests, sent by the legitimate OLT, and replies with messages in respect with a rate of . Values of range from 0 to 1 corresponding to the rate of the attacker’s intervention, i.e., 0 means that the attacker does not intercept any request, while 1 means that the attacker intercepts all requests. In brief, higher rates correspond to higher chances of a successful request interception. Once the attacker successfully intercepts a request, it responds with a message back to the OLT to keep the ONU in active mode and, hence, to consume power.
Our model activates the
wake-up mechanisms,
Figure 2a, when the downstream packet arrival rate
is at the low-end, i.e., light traffic conditions, and the OLT queue is empty. Hence, the OLT sends a
request to the ONU, and the ONU replies with an
message since the upstream arrival rate
is light and there may not exist any upstream traffic on
during this period of time. Then, it transits from the active to the listen mode in negligible time [
18] and stays in it for a time period
. If any downstream traffic is received during the listen mode period, which depends on
, it was buffered at the OLT’s queue, and once the listen period expired the ONU received a
wake-up message from the OLT in order to transit to the active mode and receive the buffered downstream packets. Once the OLT’s queue becomes empty again, the OLT sends a
request to the ONU. If the ONU’s queue is also empty, it replies with an
message and transits first to the listen mode and then to sleep mode in 2.88 μs that corresponds to the time needed by the ONU to turn off its transceiver [
19]. It should be noted that this transition occurred because there was no downstream traffic while in listen mode. The ONU stays in sleep mode for a period
and, as a result, saves energy.
During the sleep period, the received down/up stream traffic is buffered at the OLT’s and the ONU’s queues. The sleep mode period cannot be interrupted by neither downstream nor upstream traffic arrivals. Moreover, if any downstream traffic received during sleep mode (which depends on ) is buffered at the OLT’s queue and once the sleep period expires the ONU will receive a wake-up message from the OLT in order to transit to the active mode and receive the buffered downstream packets. If the OLT’s queue is still empty at the time the sleep mode period expires, the ONU will not receive a wake-up message and instead, will or will not wake up depending on the ONU’s queue status.
The
time-out mechanism is activated and serves to countermeasure a MITM attack (
Figure 3a) during which the attacker receives the
request from the legitimate OLT and replies with a
message with a rate depending on the
parameter’s value. In the
module, we define
as the
time-out interval period, which specifies the rate
for the ONU’s transition to the listen mode when neither traffic nor
requests arrive at the device (
Figure 3b).
Inside the Prism model, we also define properties to express its expected behavior. Probabilistic results are derived by the application of the probability operator into sets of states and paths,
, where the relation operator
and the probability bound
. In the proposed model, we use the form of the probabilistic property
, where = ? replaces the bound operator
p,
F stands for “eventually” and
represents the path formulae. The aim is to calculate the probability that the model “eventually” satisfies the path formulae
, e.g., the probability that a number of upstream packets have been successfully received by the OLT [
26]. Moreover, we define reward properties in our CTMC model using the operator
R to receive quantitative results, such as the expected energy consumption within a certain time period.
6. Quantitative Verification Results
Prism model checker [
26] was used for the design and analysis of the proposed
wake-up and
time-out mechanisms, and we derive quantitative verification results were run on a core i7 2.4 GHz system with 8 GB of RAM. To align our model with the specifications of an EPON access network, we assume
C = 1.25 Gbps for both down and upstream channel and
l = 1518 bytes for packet length.
Table 3 contains information regarding the state space produced once our CTMC model is built and no attack has occurred (i.e.,
= 0). We notice that increasing the number of transmitted packets in both down/up stream directions causes a non-linear increase in the state space (S) in line with the total number of the model’s states, the number of transitions among them, the number of iterations, and the time needed to solve the model. The rest of modeling parameters, i.e., packet arrival and service rates (
), the duration of listen, sleep, and
time-out periods (
), as well as the rate of attacker’s intervention (
) do not affect the model’s state space.
Shortly after the building phase, model checking verifies the properties of interest expressed in continuous-time stochastic (CSL) logic. We start with the proof-of-concept property,
, which evaluates the probability of finding final states before the time interval specified by
has elapsed, for which the formula “finish” is true. This formula represents the Boolean expression that controls whether all packets defined in the following CSL query have been transmitted and received successfully. More specifically, the query is:
provides the probability that 1000 downstream packets will be transmitted by the OLT and received successfully by the ONU and 1000 upstream packets will be transmitted by the ONU and received successfully by the OLT within 100 ms when arrival rate
varies from
to
packets/ms and
is fixed at
packets/ms. Different
values express different downstream traffic arrival rates, hence, in case of our model
= 0.2, 0.6 and 1 represents light, medium and high downstream traffic, respectively The
parameter is set to zero, since we firstly consider a non-attack scenario, while the
is predefined at a balanced value of 35 ms. This choice takes into account that a low value will cause the ONU to
time-out often causing delays even without the presence of an attacker but will result in higher energy saving, while a high
value will cause a low delay but high energy consumption when an attacker is present. Being a parameter in the proposed model,
can be modified accordingly to follow the specific characteristics of a PON. As already mentioned, the same applies for the values of parameters
and
whose choices are derived by [
19]. The impact of the
parameter on the trade-off between energy consumption and packet delay is demonstrated later on this section (Figures 11 and 12).
Results of
are depicted in
Figure 4, where the proposed model (solid line) is being compared with [
21] (dotted line). We notice that the curves of our model move to the left as the downstream packet arrival rate,
, increases. This indicates that the model is completed sooner.
Specifically, in the work of [
21], the curve corresponding to
reaches probability
when
ms, while at this time probability is
and
for
and
, respectively. Lower values of the rate
entail a higher probability for the OLT to send sleep requests and for the ONU to respond with an
message, causing delays in the model’s completion.
On the other hand, when we employ the proposed
wake-up and
time-out mechanisms, the curves move further to the left, which entails that the model is completed even sooner. A major difference from [
21] is that, at time
ms, this model has been completed even for
. This is anticipated since the ONU turns to active mode more often as a result of the
wake-up mechanism. More specifically, when
the model needs 100 ms to finish, when
the model needs 40 ms to finish; and when
, the model needs 38 ms to finish. For a better comparison regarding the time that the model is being completed, i.e., reaches probability
,
Figure 5 shows the bars of time in ms for different values of
. Comparing the yellow bars [
21] with the purple ones that correspond to our proposed model, we notice that the latter finish,
,
, and
times faster when
,
and
, respectively.
In addition to the probabilistic results, we evaluate the impact of both wake-up and time-out mechanisms, taking into consideration the case of a MITM attack on the energy-aware mechanism. We employ rewards to receive quantitative results of the system model, such as power consumption. Specifically, we use the cumulated reward property of the form to measure the consequences of a MITM attack on the energy levels of a solar-powered ONU.
We derive results of
Figure 6 defining the query:
which provides the expected energy consumption in line with the
arrival rate, taking into account different values of the
parameter.
In
Figure 6, the blue, green, and red curves represent the different values of intervention rate, i.e., 0 (blue),
(green), and 1 (red), which denote that the attacker does not intercept any sleep request from the OLT, intercepts half of the sleep request messages that the OLT sends or all of them, correspondingly. In this figure, the expected energy consumption is plotted for different values of
, keeping the
. The dotted line represents the results from [
21], while the dashed line refers to the proposed model having only the
wake-up mechanism activated and the solid line having both energy-saving mechanisms activated.
It is clear that using our proposed mechanisms, the expected energy consumption at the ONU decreases with the increase in
. This is the case when the
wake-up mechanism is used, and it is amplified with lower levels of energy consumption when it is employed in conjunction with the
time-out one. On the contrary, in [
21] the energy consumption increases as both
and the
rate increase. This is owed to the decrease in sleep requests’ acceptance ratio. In fact, the impact of the
wake-up mechanism is more evident for higher
rates, since the packets’ transmission is completed sooner and the ONU transits to the sleep mode. Meanwhile, the impact of the
time-out mechanism on the energy consumption compared to [
21] is enhanced for higher
rates, since the sleep request acceptances decrease and the ONU transits to sleep mode due to the
time-out.
To highlight the advantage of applying the proposed mechanisms simultaneously,
Figure 7 displays the energy consumption for different
rates when
and
. As shown in the figure, the
wake-up mechanism provides lower energy consumption for mild and low interception rates as much as
under medium-class intervention by the attacker (
) compared to [
21]. Applying both the proposed mechanisms, the system achieves the best performance concerning energy efficiency outperforming the [
21] by almost
(
),
(
), and
(
) less energy consumption compared to [
21]. All in all, both mechanisms work together efficiently, decreasing the energy consumption even for high rates of
and
.
What is interesting enough is the fact that the energy-saving characteristic of the proposed schemes does not come with high packet delay. For this, delay-related results in
Figure 8 derived by the following query:
The query
provides the downstream packet delay for different values of
in case of model [
21] (dotted line), as well as when both
wake-up and
time-out mechanisms are applied (solid line). For the delay performance, our model is augmented with the reward structure
X = delay which counts queuing and transmission delay. The packets that arrive while the ONU is sleeping do not have to wait for a sleep cycle to complete, since the
wake-up mechanism is active. The comparative results are shown in
Figure 8.
At the beginning, packets start to arrive in the OLT queue, resulting in the increase in packet delay. In case of [
21] (dotted lines), disrupting the ONU’s sleep cycle is not possible, causing the OLT to buffer any incoming downstream packets increasing the OLT queue eventually, resulting to higher delay compared to our model (solid lines), whose
wake-up mechanism causes the ONU to stop the sleep cycle in order to receive packets from the OLT queue. For example, when
the blue, dotted line [
21] has a peak average packet delay of 7.6 ms, which is clearly higher compared to 4.6 ms provided by the corresponding solid blue line (both mechanisms). After their peak (at
ms model time), both blue lines decline, indicating the delay decreases due to the fact that the OLT queue is emptying of packets. Obviously, higher values of
entails lower packets’ delay since the ONU stays in the active state and receives them. The same behavior is exhibited for
and 1 giving again to the proposed model constantly lower values of delay, proving the efficiency of the introduced mechanisms.
The query
provides the expected number of
wake-up mechanism activations for different
and different
values. The comparative results are shown in
Figure 9.
As shown in
Figure 9, the
wake-up mechanism is activated more frequently in the absence of an attacker (
= 0, solid line) since the ONU transits to the sleep state without any barrier caused by a potential attacker. As expected, when
= 10 ms, the
wake-up mechanism activates more times compared to higher
values, since the ONU transits to sleep more frequently. For high
values, the
wake-up seems less effective, since the ONU transits to the sleep state less frequently. Additionally, for high
rates (
= 1 dashed line), the
wake-up mechanism is rarely activated, since the attacker intercepts all
sleep requests, resulting to ONU staying active for longer periods of times. Consequently, the
wake-up mechanism is more effective for low
values while an attacker is not present. It should be reminded that the
wake-up mechanism does not counter a MITM attack, instead, it is a mechanism that results to lower packet delay and higher energy saving as shown in previous figures.
The query
provides the expected number of
time-out mechanism activations for different
and different
values. The comparative results are shown in
Figure 10.
As shown in
Figure 10, the
time-out mechanism really shows its potential for lower
and higher
values. For
= 10 ms the blue lines are higher as expected, since the ONU time-outs more frequently. In case of
= 0, the
time-out mechanism has a lower effect, since it is designed to counter a MITM attack. Although, as shown in
Figure 10, the
time-out mechanism is also expected to activate for
=
.
values higher than
do not really have much of effect in our model in case of not having a MITM attack. Additionally, as expected, setting a higher
value results to less mechanism activations. Setting a lower
value results to more
time-out mechanism activations which entails the ONU transits to sleep mode more often, hence, increasing the overall packet delay. Finally, in order to set the optimal
we need to take into consideration various model parameters such as
,
, delay and energy consumption. Consequently, if a system aims to maximize energy saving while tolerating an increase in packet delay, low
values (such as 10 ms) should be considered. On the other, if a system aims to minimize delay, higher
values (such as 35 ms) are optimal.
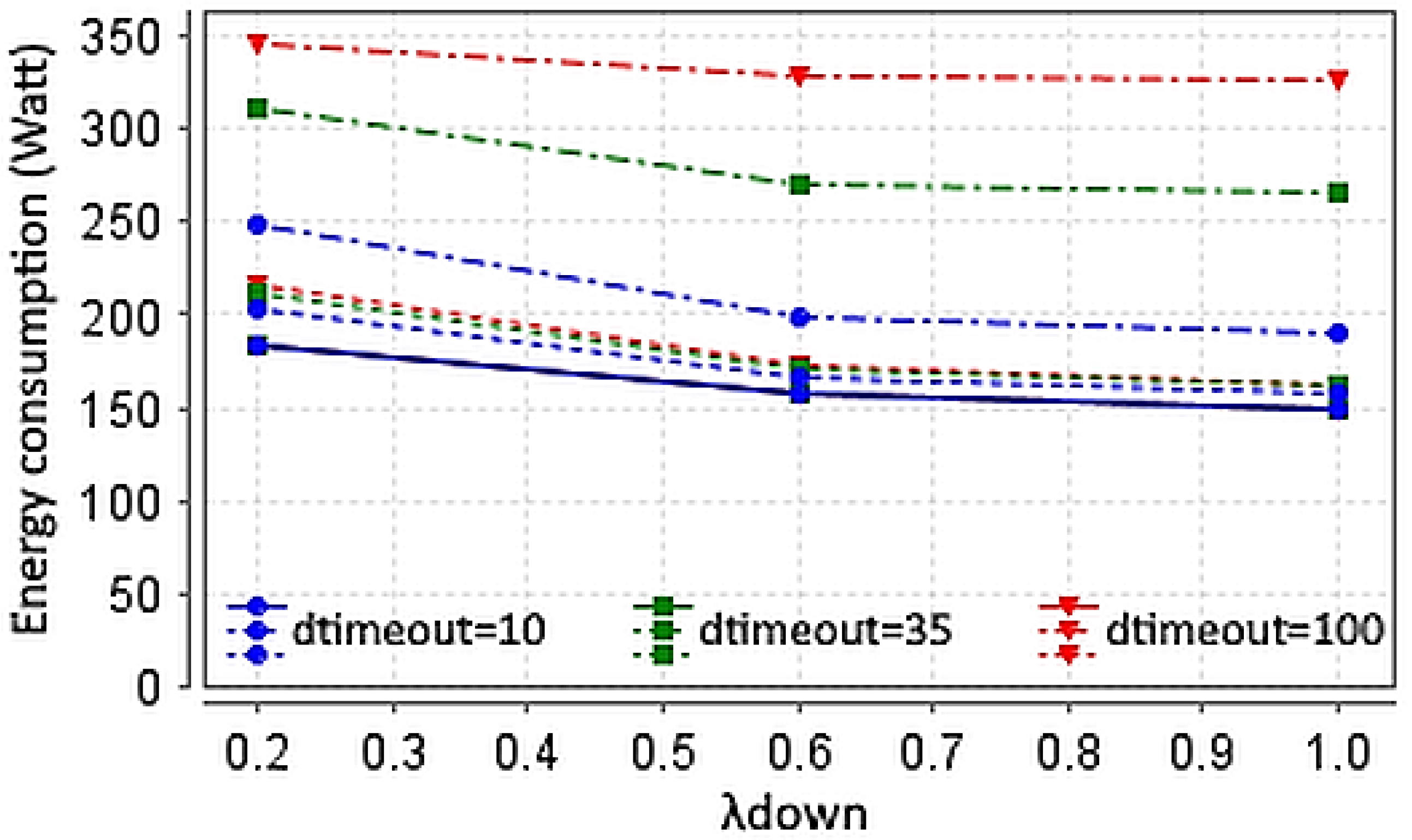
The query
provides the expected energy consumption for different
and different
values. The comparative results are shown in
Figure 11.
In
Figure 11, the blue, green, and red curves represent the different
values, i.e., 10 (blue), 35 (green), and 100 (red), which denote the
time-out interval period until
time-out activation. In this figure, the expected energy consumption is plotted for different values of
, keeping the
. The solid line represents a model where the attacker is not present (
= 0), while the dashed line refers to a model where the attacker intercepts all
sleep requests sent from the OLT (
= 1) and the dotted line a model where half of the
sleep requests are intercepted (
=
).
As shown, the energy consumption is higher when = 1 and it reaches its highest point when = 100 ms, showing that such a high value is inappropriate. Comparing = 10 ms when = 1 (blue dashed line) and = 35 ms when = 1 (green dashed line), the first clearly has the advantage in terms of energy consumption since the ONU transits to the sleep state more frequently, but in the expense of expected increased packet delay. Additionally, while = 0 (solid lines), different values have the same outcome, since the time-out mechanism is not as effective in the absence of an attacker. As shown, when = 0.5, the results between different values are almost identical.
Finally, as already mentioned, lower
values result to increased packet delay. For this, delay related results in
Figure 12 derived by the query
:
In
Figure 12, the expected packet delay is plotted for different values of
, keeping the
while the attacker intercepts all
sleep requests (
= 1) since it is shown from earlier figures that the
time-out mechanism is more effective for higher
values. The solid lines represent the results when
= 35 ms, while the dotted lines refers to
= 10 ms. When we set
= 10 ms the curves move further to the right, which entails increased delay in comparison to
= 35 ms. This shift to the right is more distinctive when
=
, while higher
values have an identical result in terms of delay.
Comparing
Figure 11 and
Figure 12 when
= 0.2 the energy consumption of
= 10 ms (blue circle point) is lower than
= 35 ms (green square point) by ∼20%, while the delay of
= 35 ms (blue solid curve) is lower than
= 10 ms (blue dotted curve) and after
, it continues to maintain a distance ranging between
and
. Therefore, setting the optimal
value should take into consideration the trade-off between energy consumption and packet delay, based on each application/system preferences.