Differential Privacy-Enabled Multi-Party Learning with Dynamic Privacy Budget Allocating Strategy
Abstract
1. Introduction
- We propose an adaptive differentially private multi-party learning framework based on the zero-concentrated differential privacy technique, which yields stronger privacy guarantees and permits tighter bounds for privacy computations.
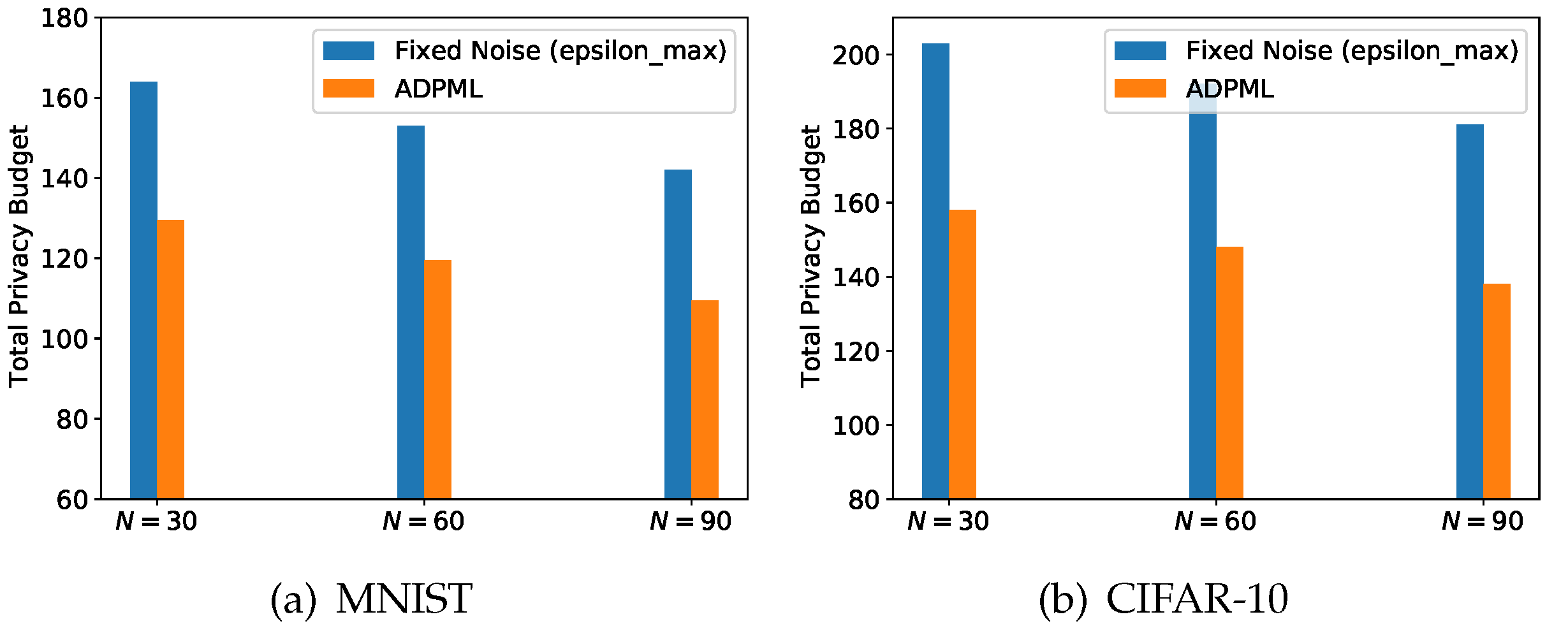
- We design a dynamic privacy budget allocating strategy to avoid superfluous injection of noise and achieve the maximization of model accuracy under a high privacy-preserving level. This strategy can effectively reduce total privacy budgets and outperform fixed noise allocation.
- We experimentally validate the utility of ADPML on two benchmark datasets. Qualitative and quantitative experiments demonstrated that ADPML had better model performance, while decreasing privacy loss.
2. Preliminaries
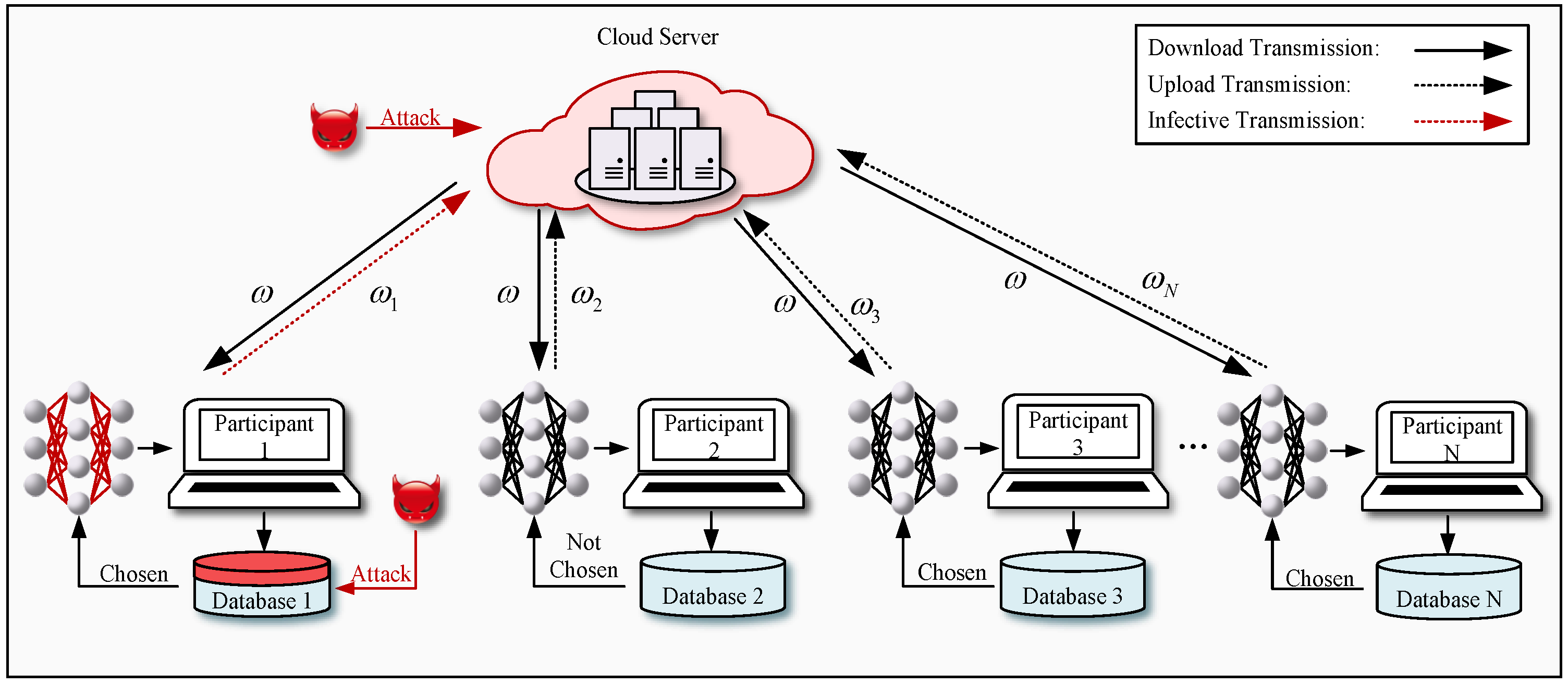
2.1. Multi-Party Learning
- The selected participants first conduct local training, based on their private data, and then upload the trained parameters to the cloud server.
- The cloud server aggregates the parameters uploaded by all active participants, and then conveys the aggregated parameters to the chosen participants.
- Participants update their models via the aggregated parameters. The iterative training process continues until the convergence criterion of the updated model is satisfied.
2.2. Differential Privacy
2.3. Zero-Concentrated Differential Privacy
3. Methodology
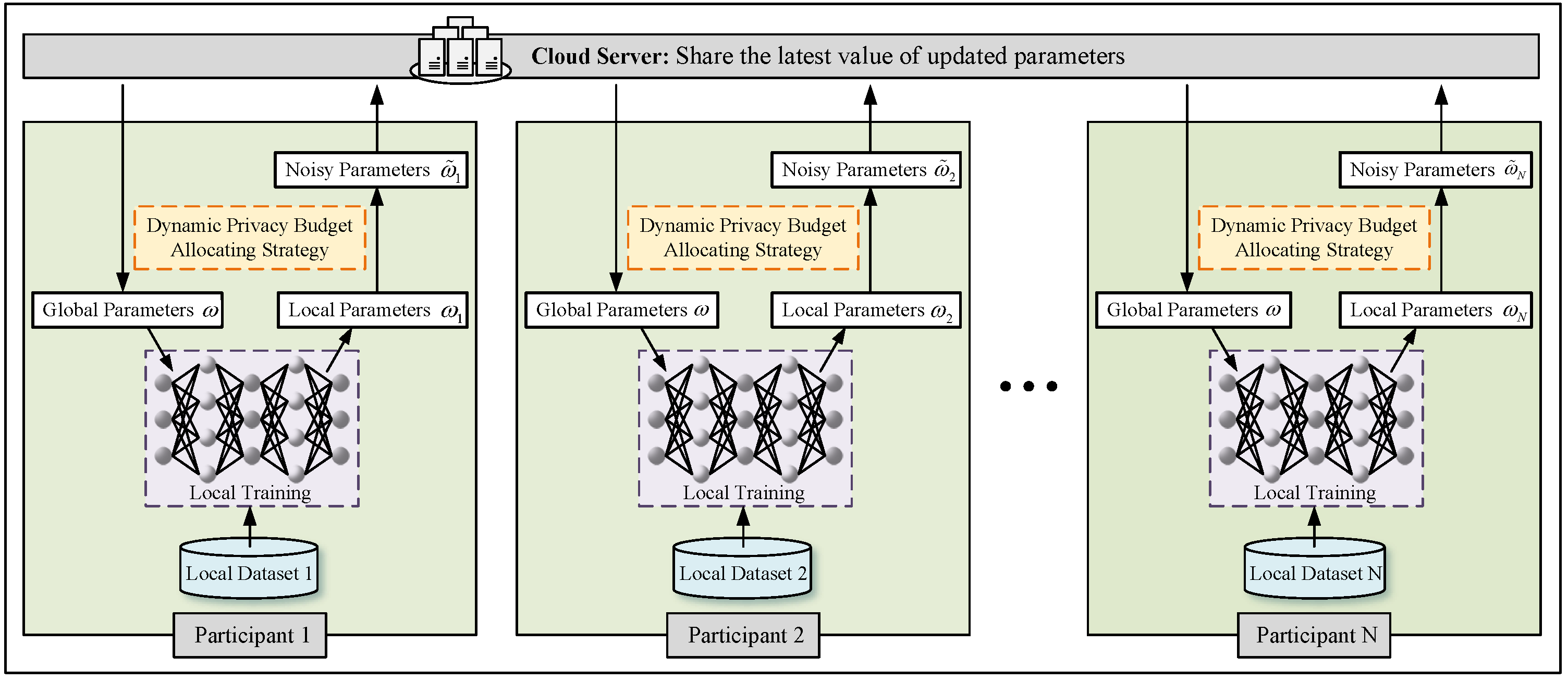
3.1. Overview
3.2. Dynamic Privacy Budget Allocating
- Parameter clipping. We calculated the noisy parameter via the Gaussian mechanism with variance . relied on the maximum effect an element can have on , which was determined by . Therefore, for the purpose of providing a boundary to the impact on , we computed local parameters and divided local parameters by , given a predefined clipping threshold C. Thus, the sensitivity of parameters was bound by C.
- Adaptive noise injection. In order to reduce the total privacy budgets, while maintaining the model performance, we adaptively redistributed privacy loss for adjusting noise scale, based on the dynamic privacy budget allocating strategy. We first transformed -DP to -zCDP through Proposition 1 and defined a privacy loss increase rate . Then, we gradually increased the privacy loss to the maximum , based on , with the direction of the gradient descent becoming more accurate.
| Algorithm 1 Adaptive Differentially Private Multi-Party Learning (ADPML). |
|
3.3. Sensitivity and Privacy Analysis
4. Experiments
4.1. Experimental Setup
- MNIST [39] is a benchmark dataset that is related to handwritten grey-level images of digits from 0 to 9. MNIST contains 70,000 grey-level images including 60,000 training examples and 10,000 test examples, and each example is a image.
- CIFAR-10 [40] comprises 60,000 RGB color images with ten categories, such as cars, cats, dogs, ships, and so on. There are 50,000 training examples and 10,000 test examples in CIFAR-10, and each example has size with three channels.
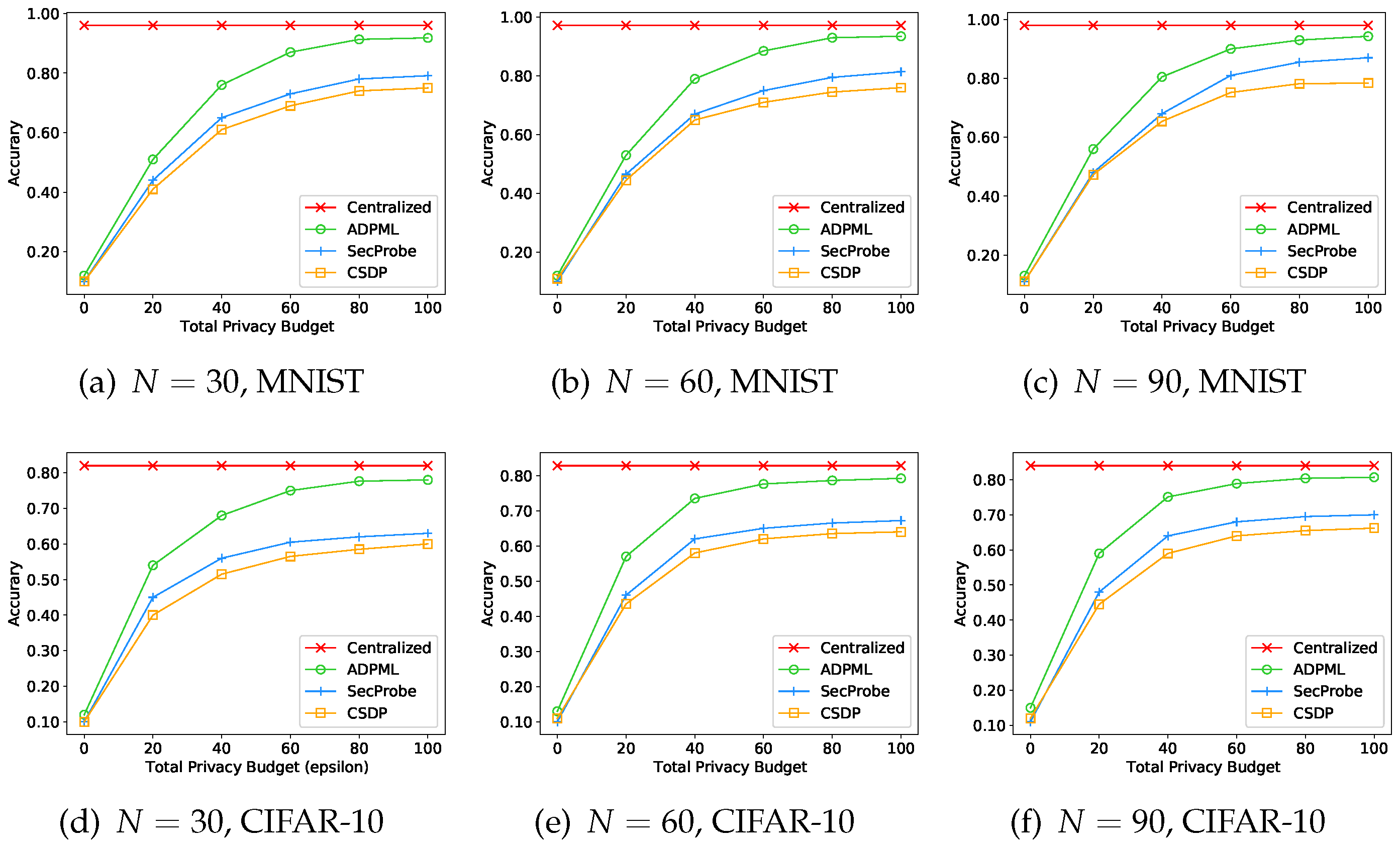
- ADPML, a differential privacy-enabled multi-party learning framework with a dynamic privacy budget allocating strategy.
- Centralized, a centralized model training on the entire datasets from all participants without any privacy consideration.
- SecProbe [22], which protects the privacy of each participant by inserting perturbation into the objective function based on the functional mechanism.
- CSDP [21], which injects perturbation into the sum of all updates from each participant.
- Fixed Noise (), a differentially private multi-party learning framework with a fixed minimum noise level .
- Fixed Noise (), a differentially private multi-party learning framework with a fixed maximum noise level .
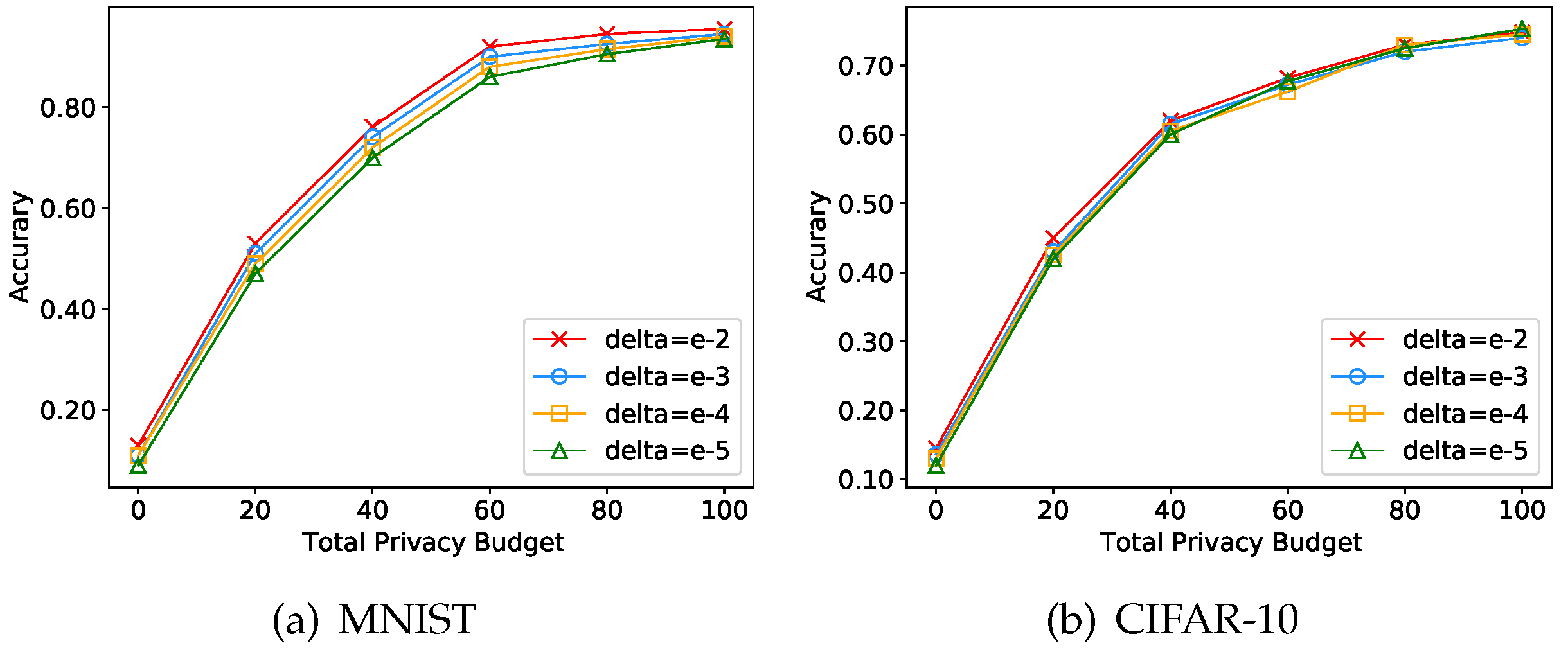
4.2. Experiments on the Level of Privacy Guarantees
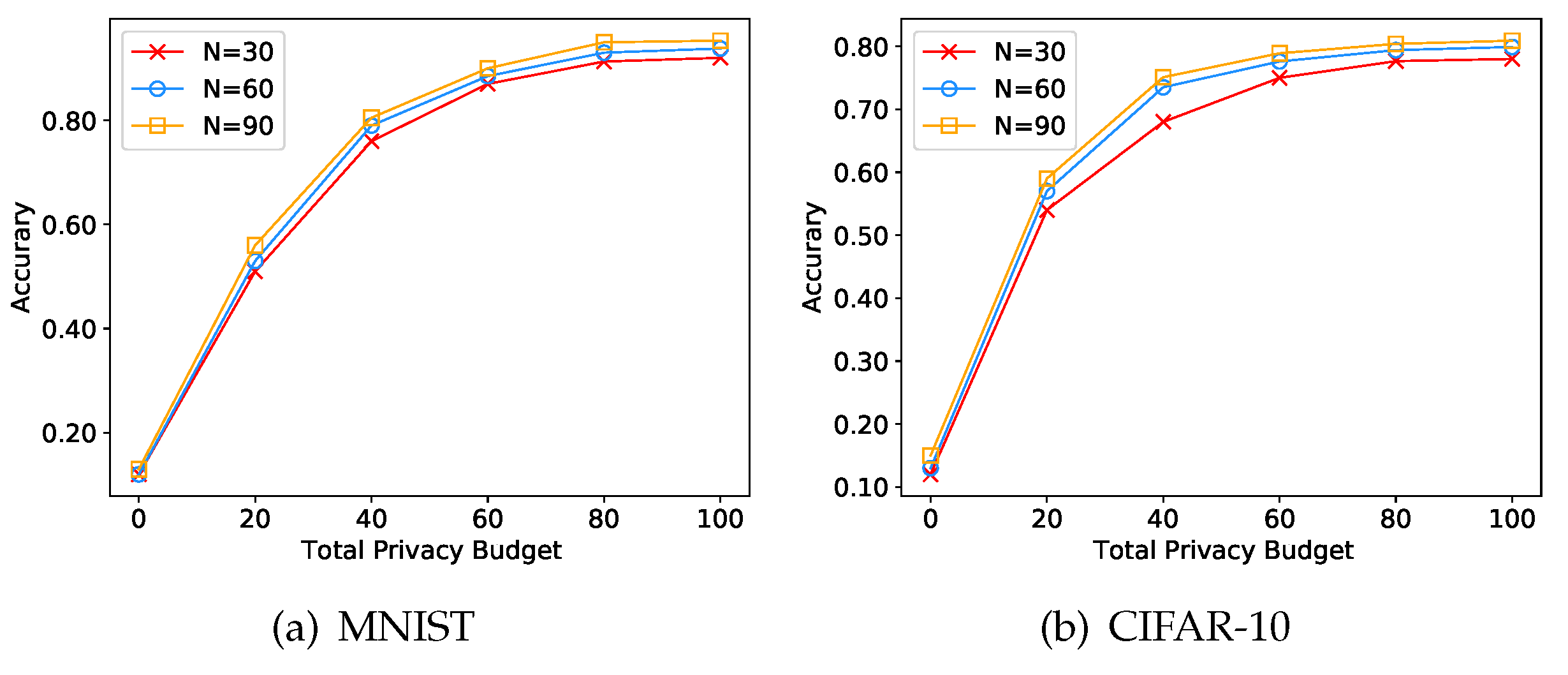
4.3. Experiments on the Number of Participants
4.4. Experiments on the Relaxation Factor
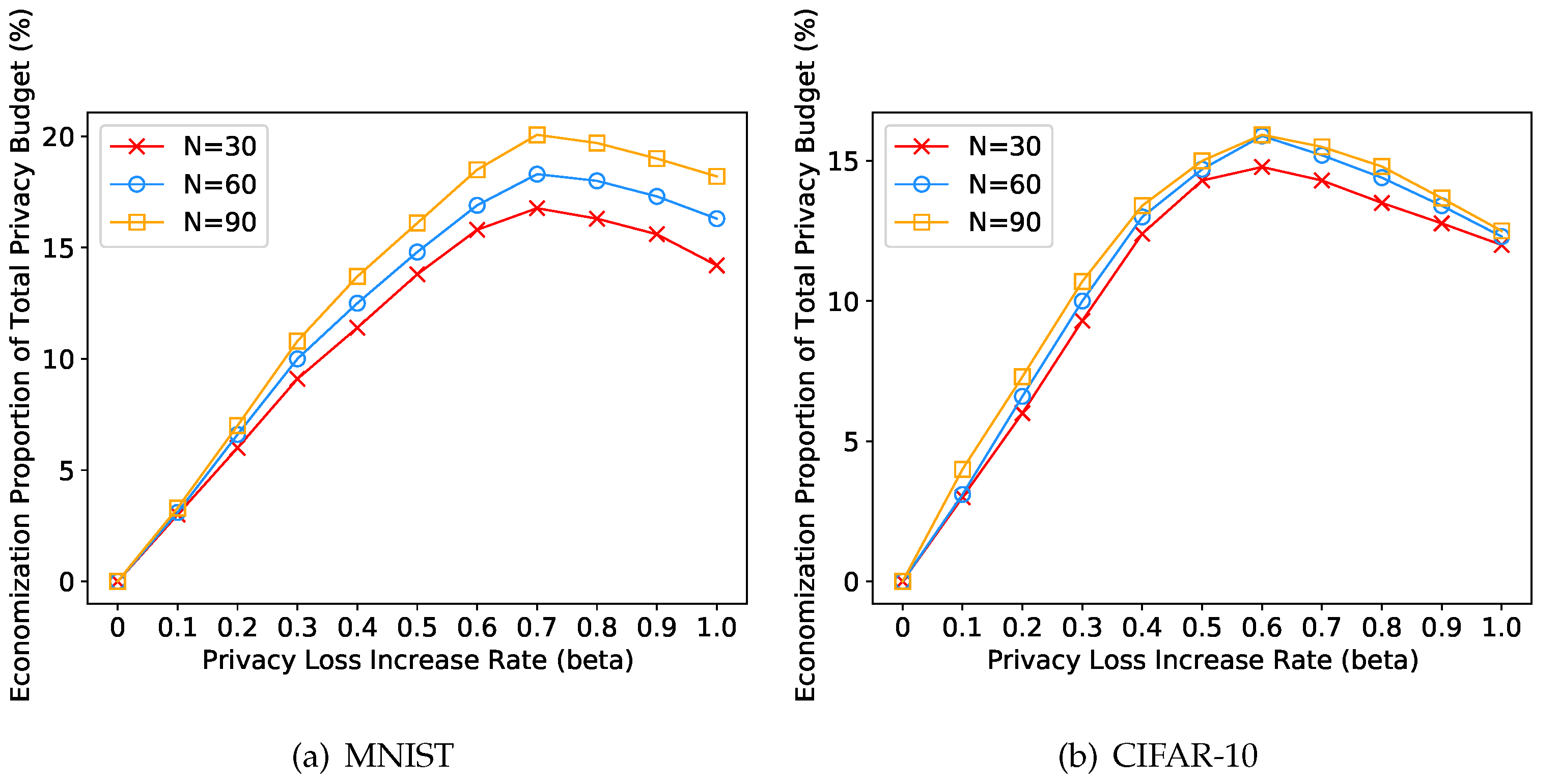
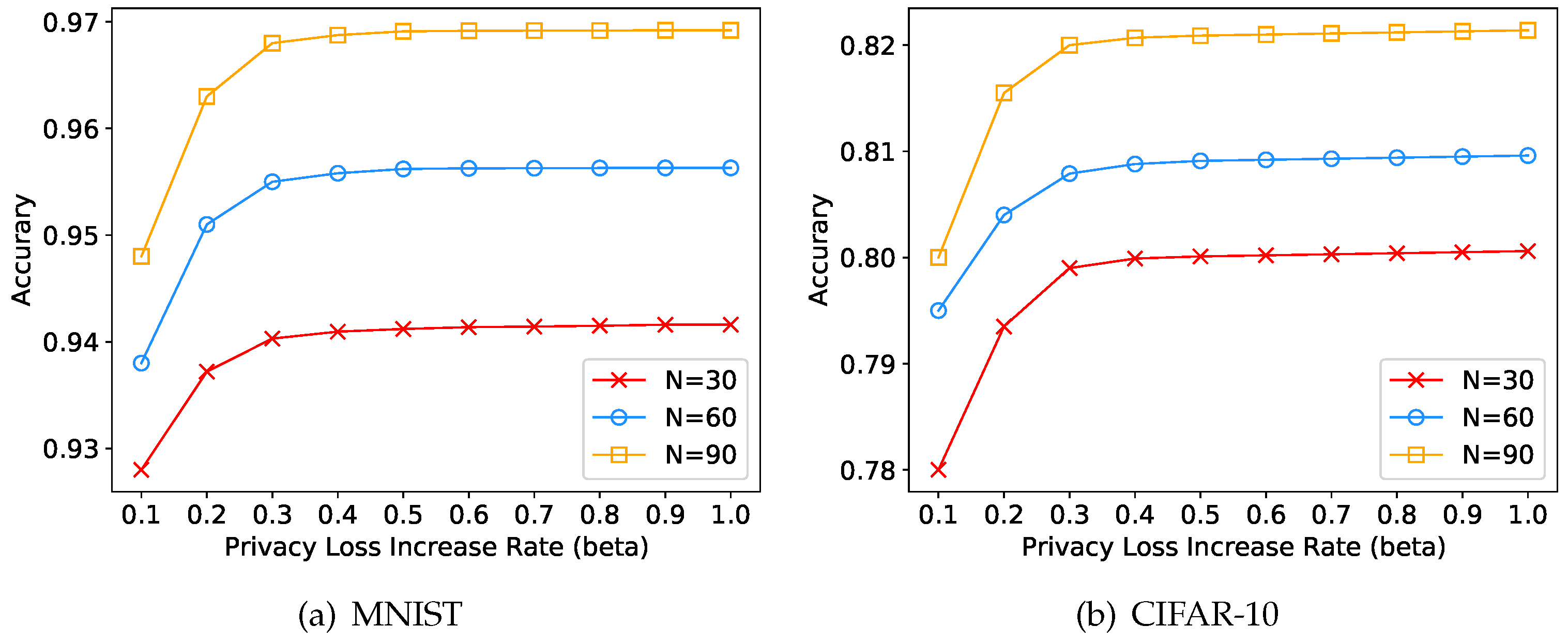
4.5. Experiments on the Privacy Loss Increase Rate
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AI | Artificial intelligence |
| GAN | Generative adversarial network |
| SMC | Secure multi-party computation |
| HE | Homomorphic encryption |
| DP | Differential privacy |
| zCDP | Zero-concentrated differential privacy |
| ADPML | Adaptive differentially private multi-party learning |
References
- Lee, S.; Lee, S.; Seong, H.; Hyun, J.; Kim, E. Fallen person detection for autonomous driving. Expert Syst. Appl. 2023, 213, 119242. [Google Scholar] [CrossRef]
- Bogdoll, D.; Nitsche, M.; Zöllner, J.M. Anomaly Detection in Autonomous Driving: A Survey. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, LA, USA, 18–24 June 2022; pp. 4488–4499. [Google Scholar]
- Touvron, H.; Bojanowski, P.; Caron, M.; Cord, M.; El-Nouby, A.; Grave, E.; Izacard, G.; Joulin, A.; Synnaeve, G.; Verbeek, J.; et al. Resmlp: Feedforward networks for image classification with data-efficient training. IEEE Trans. Pattern Anal. Mach. Intell. 2022, 1–9, early access. [Google Scholar] [CrossRef] [PubMed]
- Tang, C.; Zhao, Y.; Wang, G.; Luo, C.; Xie, W.; Zeng, W. Sparse MLP for image recognition: Is self-attention really necessary? In Proceedings of the AAAI Conference on Artificial Intelligence, virtual, 22 February–1 March 2022; Volume 36, pp. 2344–2351. [Google Scholar]
- Sun, L.; Zhao, G.; Zheng, Y.; Wu, Z. Spectral–Spatial Feature Tokenization Transformer for Hyperspectral Image Classification. IEEE Trans. Geosci. Remote Sens. 2022, 60, 1–14. [Google Scholar] [CrossRef]
- Zheng, Y.; Lu, R.; Zhang, S.; Guan, Y.; Shao, J.; Wang, F.; Zhu, H. PMRQ: Achieving Efficient and Privacy-Preserving Multi-Dimensional Range Query in eHealthcare. IEEE Internet Things J. 2022, 9, 17468–17479. [Google Scholar] [CrossRef]
- Chen, Z.; Tian, Z.; Zhu, J.; Li, C.; Du, S. C-CAM: Causal CAM for Weakly Supervised Semantic Segmentation on Medical Image. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, LA, USA, 18–24 June 2022; pp. 11676–11685. [Google Scholar]
- Fang, C.; Wang, L.; Zhang, D.; Xu, J.; Yuan, Y.; Han, J. Incremental Cross-view Mutual Distillation for Self-supervised Medical CT Synthesis. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, New Orleans, LA, USA, 18–24 June 2022; pp. 20677–20686. [Google Scholar]
- Shokri, R.; Shmatikov, V. Privacy-Preserving Deep Learning. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 1310–1321. [Google Scholar]
- Konecný, J.; McMahan, H.B.; Ramage, D.; Richtárik, P. Federated Optimization: Distributed Machine Learning for On-Device Intelligence. arXiv 2016, arXiv:1610.02527. [Google Scholar]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; y Arcas, B.A. Communication-Efficient Learning of Deep Networks from Decentralized Data. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, Fort Lauderdale, FL, USA, 9–11 May 2017; pp. 1273–1282. [Google Scholar]
- Fredrikson, M.; Lantz, E.; Jha, S.; Lin, S.M.; Page, D.; Ristenpart, T. Privacy in Pharmacogenetics: An End-to-End Case Study of Personalized Warfarin Dosing. In Proceedings of the 23rd USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 17–32. [Google Scholar]
- Fredrikson, M.; Jha, S.; Ristenpart, T. Model Inversion Attacks that Exploit Confidence Information and Basic Countermeasures. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 1322–1333. [Google Scholar]
- Phong, L.T.; Aono, Y.; Hayashi, T.; Wang, L.; Moriai, S. Privacy-Preserving Deep Learning: Revisited and Enhanced. In Proceedings of the Applications and Techniques in Information Security—8th International Conference, Auckland, New Zealand, 6–7 July 2017; pp. 100–110. [Google Scholar]
- Hitaj, B.; Ateniese, G.; Pérez-Cruz, F. Deep Models Under the GAN: Information Leakage from Collaborative Deep Learning. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October– 3 November 2017; pp. 603–618. [Google Scholar]
- Shokri, R.; Stronati, M.; Song, C.; Shmatikov, V. Membership Inference Attacks Against Machine Learning Models. In Proceedings of the 2017 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–24 May 2017; pp. 3–18. [Google Scholar]
- Melis, L.; Song, C.; Cristofaro, E.D.; Shmatikov, V. Exploiting Unintended Feature Leakage in Collaborative Learning. In Proceedings of the 2019 IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 20–22 May 2019; pp. 691–706. [Google Scholar]
- Wang, Z.; Song, M.; Zhang, Z.; Song, Y.; Wang, Q.; Qi, H. Beyond Inferring Class Representatives: User-Level Privacy Leakage From Federated Learning. In Proceedings of the 2019 IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; pp. 2512–2520. [Google Scholar]
- Goodfellow, I.J.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.C.; Bengio, Y. Generative Adversarial Nets. In Proceedings of the Advances in Neural Information Processing Systems, Montreal, ON, Canada, 8–13 December 2014; pp. 2672–2680. [Google Scholar]
- Phong, L.T.; Aono, Y.; Hayashi, T.; Wang, L.; Moriai, S. Privacy-Preserving Deep Learning via Additively Homomorphic Encryption. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1333–1345. [Google Scholar] [CrossRef]
- Geyer, R.C.; Klein, T.; Nabi, M. Differentially Private Federated Learning: A Client Level Perspective. arXiv 2017, arXiv:1712.07557. [Google Scholar]
- Zhao, L.; Wang, Q.; Zou, Q.; Zhang, Y.; Chen, Y. Privacy-Preserving Collaborative Deep Learning With Unreliable Participants. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1486–1500. [Google Scholar] [CrossRef]
- Bonawitz, K.; Ivanov, V.; Kreuter, B.; Marcedone, A.; McMahan, H.B.; Patel, S.; Ramage, D.; Segal, A.; Seth, K. Practical Secure Aggregation for Privacy-Preserving Machine Learning. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1175–1191. [Google Scholar]
- Ghazi, B.; Pagh, R.; Velingker, A. Scalable and Differentially Private Distributed Aggregation in the Shuffled Model. arXiv 2019, arXiv:1906.08320. [Google Scholar]
- Zhang, X.; Ji, S.; Wang, H.; Wang, T. Private, Yet Practical, Multiparty Deep Learning. In Proceedings of the 37th IEEE International Conference on Distributed Computing Systems, Atlanta, GA, USA, 5–8 June 2017; pp. 1442–1452. [Google Scholar]
- Agarwal, N.; Suresh, A.T.; Yu, F.X.; Kumar, S.; McMahan, B. cpSGD: Communication-efficient and differentially-private distributed SGD. In Proceedings of the Advances in Neural Information Processing Systems 2018, Montreal, ON, Canada, 3–8 December 2018; pp. 7575–7586. [Google Scholar]
- Bhowmick, A.; Duchi, J.C.; Freudiger, J.; Kapoor, G.; Rogers, R. Protection Against Reconstruction and Its Applications in Private Federated Learning. arXiv 2018, arXiv:1812.00984. [Google Scholar]
- Dwork, C.; McSherry, F.; Nissim, K.; Smith, A.D. Calibrating Noise to Sensitivity in Private Data Analysis. In Proceedings of the Third Theory of Cryptography Conference, New York, NY, USA, 4–7 March 2006; pp. 265–284. [Google Scholar]
- Dwork, C. Differential Privacy: A Survey of Results. In Proceedings of the Conference on Theory and Applications of Models of Computation, Xi’an, China, 25–29 April 2008; pp. 1–19. [Google Scholar]
- Dwork, C.; Roth, A. The Algorithmic Foundations of Differential Privacy. Found. Trends Theor. Comput. Sci. 2014, 9, 211–407. [Google Scholar] [CrossRef]
- Wang, Q.; Zhang, Y.; Lu, X.; Wang, Z.; Qin, Z.; Ren, K. Real-Time and Spatio-Temporal Crowd-Sourced Social Network Data Publishing with Differential Privacy. IEEE Trans. Dependable Secur. Comput. 2018, 15, 591–606. [Google Scholar] [CrossRef]
- Proserpio, D.; Goldberg, S.; McSherry, F. Calibrating Data to Sensitivity in Private Data Analysis. Proc. VLDB Endow. 2014, 7, 637–648. [Google Scholar] [CrossRef]
- Machanavajjhala, A.; Kifer, D.; Gehrke, J. L-diversity: Privacy beyond k-anonymity. ACM Trans. Knowl. Discov. Data 2007, 1, 3–8. [Google Scholar] [CrossRef]
- Li, N.; Li, T.; Venkatasubramanian, S. t-Closeness: Privacy Beyond k-Anonymity and l-Diversity. In Proceedings of the IEEE International Conference on Data Engineering, Istanbul, Turkey, 17–20 April 2007; pp. 106–115. [Google Scholar]
- Wong, R.C.; Li, J.; Fu, A.W.; Wang, K. (α, k)-anonymity: An enhanced k-anonymity model for privacy-preserving data publishing. In Proceedings of the ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, Philadelphia, PA, USA, 20–23 August 2006; pp. 754–759. [Google Scholar]
- Xiao, X.; Tao, Y. M-invariance: Towards privacy preserving re-publication of dynamic datasets. In Proceedings of the ACM SIGMOD International Conference on Management of Data, Beijing, China, 11–14 June 2007; pp. 689–700. [Google Scholar]
- Bun, M.; Steinke, T. Concentrated Differential Privacy: Simplifications, Extensions, and Lower Bounds. In Proceedings of the Theory of Cryptography—14th International Conference, Beijing, China, 31 October–3 November 2016; pp. 635–658. [Google Scholar]
- Lee, J.; Kifer, D. Concentrated Differentially Private Gradient Descent with Adaptive per-Iteration Privacy Budget. In Proceedings of the 24th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining, London, UK, 19–23 August 2018; ACM: New York, NY, USA, 2018; pp. 1656–1665. [Google Scholar]
- LeCun, Y.; Bottou, L.; Bengio, Y.; Haffner, P. Gradient-based learning applied to document recognition. Proc. IEEE 1998, 86, 2278–2324. [Google Scholar] [CrossRef]
- Krizhevsky, A.; Hinton, G.E. Learning Multiple Layers of Features from Tiny Images; Technical Report; University of Toronto: Toronto, ON, Canada, 2009. [Google Scholar]
- Yu, D.; Zhang, H.; Chen, W.; Yin, J.; Liu, T. Gradient Perturbation is Underrated for Differentially Private Convex Optimization. In Proceedings of the Twenty-Ninth International Joint Conference on Artificial Intelligence, Yokohama, Japan, 7–15 January 2021; pp. 3117–3123. [Google Scholar]

| Notations | Explanation |
|---|---|
| Randomized algorithm | |
| Adjacent datasets | |
| Privacy budget | |
| Relaxation factor | |
| Sensitivity | |
| The privacy loss related to zCDP | |
| The privacy loss in the current epoch | |
| N | The number of all participants |
| K | The number of chosen participants |
| T | The number of communication rounds |
| t | The index of the current t-th communication round |
| The vector of model parameters after aggregating | |
| Local loss function of the i-th participant | |
| The vector of model parameters for the i-th participant | |
| Noisy model parameters for the i-th participant | |
| C | Clipping threshold for bounding |
| Privacy loss increase rate |
| Dataset | Participants | Methods | ||
|---|---|---|---|---|
| Fixed Noise () | Fixed Noise () | ADPML | ||
| MNIST | 16 | 18 | 18 | |
| 15 | 17 | 17 | ||
| 14 | 16 | 16 | ||
| CIFAR-10 | 20 | 23 | 23 | |
| 19 | 22 | 22 | ||
| 18 | 21 | 21 | ||
| Dataset | Participants | Methods | ||
|---|---|---|---|---|
| Fixed Noise () | Fixed Noise () | ADPML | ||
| MNIST | ||||
| CIFAR-10 | ||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pan, K.; Feng, K. Differential Privacy-Enabled Multi-Party Learning with Dynamic Privacy Budget Allocating Strategy. Electronics 2023, 12, 658. https://doi.org/10.3390/electronics12030658
Pan K, Feng K. Differential Privacy-Enabled Multi-Party Learning with Dynamic Privacy Budget Allocating Strategy. Electronics. 2023; 12(3):658. https://doi.org/10.3390/electronics12030658
Chicago/Turabian StylePan, Ke, and Kaiyuan Feng. 2023. "Differential Privacy-Enabled Multi-Party Learning with Dynamic Privacy Budget Allocating Strategy" Electronics 12, no. 3: 658. https://doi.org/10.3390/electronics12030658
APA StylePan, K., & Feng, K. (2023). Differential Privacy-Enabled Multi-Party Learning with Dynamic Privacy Budget Allocating Strategy. Electronics, 12(3), 658. https://doi.org/10.3390/electronics12030658






