1. Introduction
A neighbor election is a distributed algorithm for the nodes to coordinate with their competing neighbors for slot access in wireless ad hoc networks. It was first proposed as neighborhood-aware contention resolution (NCR) [
1] and then adopted as a multiple access scheme in WiMAX mesh mode for transmitting control messages [
2,
3]. In recent years, there has been an increasing demand for developing next-generation multiple access schemes for the evolving fifth-generation (5G) and sixth-generation (6G) wireless networks, Internet of Things (IoT) [
4,
5,
6] and wireless sensor networks (WSN) [
7,
8], where the nodes are expected to schedule themselves in a distributed manner with the knowledge of their neighbors. With the characteristics of neighborhood awareness, the neighbor election has then attracted recent research interest again [
9,
10,
11]. Different from the well-known contention-based slotted aloha (SA) and Carrier-Sense Multiple Access (CSMA), where the nodes randomly initiate transmissions without any prior knowledge about their neighboring network, neighbor election performs contention resolution by getting acquainted with their neighbors. To avoid collisions, a node using neighbor election needs to maintain the information updates from its one-hop and two-hop neighbors to ensure whether they will compete for a specific slot. This lightweight information maintenance will not require the successful two-way handshake processes between transmitters and receivers in reservation-based distributed coordination function (DCF) and other scheduling mechanisms, which may reduce the required control message overhead. If the information of a neighbor node cannot be timely updated, it will also be considered as a potential competitor, leading to an increasing number of competing neighbors. As a result, the insufficient timeliness of neighbor maintenance will decrease the probability of a node winning an election and starting its transmission [
9]. Meanwhile, the maintenance of frequent neighbor updates is fundamentally supported by the communication among nodes, which implies an interaction relationship between the transmission probability of nodes and the timeliness of information maintenance.
The timeliness of information maintained in a neighbor election is first modeled in [
9] as a function of the number of relaying nodes and the packet loss rate of wireless links. In contrast, the impact of a message transmission on the maintenance process is ignored. In the recent decade, the concept of age of information (AoI) [
12] has been introduced as a novel metric to evaluate the information freshness in communication networks. As we are discussing the neighbor election-based slot access, throughout this paper, the AoI is determined as the age of maintained information updates from the neighbors of a receiver node [
13]. For time-restricted applications, the timeliness of information maintenance can also be evaluated by the probability that AoI exceeds a given age threshold, which is termed as the age violation probability [
14,
15] or outage probability of AoI [
16]. In [
12], the real-time status updating by multiple information sources is comprehensively discussed. In [
14], the age violation probability is derived based on the probability-generating function (pgf) of peak age at a steady state. The upper bound of age violation probability is given and tightened in [
16]. While in [
15], Hu et al. derive the mean age violation probability by analyzing the different cases that the AoI that may exceed an arbitrary age constraint and provide statistical results. This work makes it easy to analyze age violation probability by intuitively mapping the violation period within the evolution path of AoI.
Besides evaluating the AoI metric and its variations, some literature also try to build the connection between AoI and the concerned indicators in CSMA networks to bring more insights. The relation between beacon interval and AoI is given in [
17], and the relation of AoI and the stability in control loops over non-beacon CSMA network is presented in [
18]. However, the transmission timing in CSMA networks does not depend on AoI, as nodes using CSMA-based schemes only rely on direct channel sensing to initiate transmissions. Hence the change of AoI cannot affect the transmission process of nodes, and these analyses cannot be directly applied to the analysis of neighbor election process where interaction relationship between AoI and transmissions of nodes exists.
The main contributions of this paper are given as follows:
We propose an approximated analytical model of the transmission probability of nodes in a wireless ad hoc network concerning its interaction relationship with the age violation probability of neighbor election-based distributed slot access. To our best knowledge, it is the first work that analyzes such interaction relationships in distributed multiple access schemes, which provides theoretical guidance for enhancing the design of distributed multiple access schemes with network-aware algorithms from the information freshness perspective.
We define the concept of timely maintained neighbors in which information can be updated by a typical node on time. We then consider the competing probability of these neighbor nodes by analyzing the intersection of election intervals
We verify the proposed approximation model by performing numerical simulations under different parameters, including the number of neighbors, the ratio of relaying nodes, and the packet loss rate. According to the simulation results, the proposed approximation model can enhance the accuracy of evaluating the transmission probability of nodes, which shows that the consideration of age violation probability of neighbor information is necessary.
The rest of the paper is organized as follows. We first introduce the system model of a wireless ad hoc network where the nodes use neighbor election-based slotted access in
Section 2. Also, we first derive the interaction relationship between the transmission probability of nodes, the age violation probability of neighbor information, and the competing probability of timely maintained neighbors. Next, we discuss the election process of two neighboring nodes in
Section 3 and linearly approximate their competing probability to simplify the derivations.
Section 4 focuses on the information maintenance from the two-hop neighborhood, and the age violation probability is derived as the mean violation duration divided by the average maintenance interval. Numerical simulation results are illustrated in
Section 5. The conclusions of this paper and future research aspects are summarized in
Section 6.
3. Competing Probability of Timely Maintained Neighbors
We concentrate on the election process of typical node
i and a timely maintained neighbor node
j within two-hop distance. These two nodes will not win the same election and thus have different transmitting slots. To analyze the competing probability
of
j, we suppose that node
i and
j enter their new election cycles at slot
and
respectively. Let
denote the residual slot number of the previous election cycle of
j when
i has entered its new one. Node
i will consider
j as a competing node during the intersections of their valid election intervals, which can be divided into three cases as illustrated in
Figure 2. Let
denote the duration ratio of an intersection to node
i’s related valid election interval. From the perspective of
i, the competing probability of
j can be written as the expectation of
:
where
is the probability mass function (pmf) of
Q, and
is the expectation of
under the condition of
.
Since
Q is geometric distributed with parameter
, the pmf of
Q is written as:
where
for simplifying notations.
In the first and second cases of
Figure 2, which conditions are
and
respectively, there should be
. Hence only the third case will happen when
. The expectation of
conditioned by
is then defined as:
where
is the pmf of residual slot number
R of node
j:
and
is the pmf of election cycle’s duration
:
The definition in Equation (
5) is based on the fact that when
is given,
R is uniformly distributed in the range
.
To derive
as a function of
, we start from the derivation of
. When
, Equation (
5) can be simplified as:
As for
, Equation (
5) is truncated, and difficult to have a simple expression by reduction to a common denominator. According to [
19], the limit distribution of the residual slot number
R in a renewal process satisfies the following formula:
Thus when
is given, Equation (
5) can be approximated as:
With the expression in Equations (
7) and (
9), we obtain the mean of
when
and
respectively as follow:
where
denotes the mean of
Q and is written as:
and the approximation in Equation (
12) holds as
goes to zero when
V is sufficiently large. For the same reason,
, and the increment of
when
is approximated as:
As
q grows,
goes to zero and so
gradually tends to
. Thus we consider to approximate
by a linear function defined as follow:
where the value of
and
are approximated by substituting Equations (
9) and (
12) into Equation (
11):
Substitute Equations (
15) and (
16) into Equation (
14), we have the expression of
as follow:
where
and
.
Finally, we obtain the approximated expression of
by some transformations and simplifications as follow:
4. Age Violation Probability of Neighborhood Maintenance
We focus on analyzing the age violation probability of the neighborhood maintenance process in this section. Consider that node i successfully receives a message from its neighbor node j for the k-th time. Let and denote the slot indices that node j transmits and node i successfully receives . Let denote the transmitting slot index of the last maintained update at slot t. The age of this update is denoted as .
An illustration of the AoI process of node
j observed at node
i is presented in
Figure 3, where
denotes the consumed time of
k-th successful maintenance,
denotes the interval between two consecutive and successfully maintained updates,
denotes the duration of
k-th maintenance interval. Let
denote the age threshold that a neighbor cannot be timely updated as referred to in
Section 2, and let
denote the violation duration that AoI exceeds the threshold
in
k-th maintenance interval.
According to the derivation of Equation (
25) in [
15], the age violation probability of an update is defined as
where the mean of
and
will be derived in the following two subsections.
4.1. Mean Duration of Maintenance Interval
We first analyze the mean of
. Since the updates happen along with the generation of messages, there is no queuing time, and so
. Therefore, the mean of
should be
since the expectations of
and
are statistically equal. Equation (
20) shows that
has the same mean of
. Consider that during the
k-th maintenance interval, node
i fails to maintain the updates from
j for
M times. Let
denote the successful maintenance probability of an update. As
M is geometric distributed of parameter
, the mean of
M is
, and the mean of
is written as:
The analysis of
is given as follow. Note that the nodes should forward the updates of their one-hop neighbors to realize two-hop neighbor maintenance in a distributed neighbor election. Thus, node
i can capture the updates of a one-hop neighbor by receiving messages from either the direct link or the forwarding links from their common one-hop neighbors. For the simplicity of analysis, we assume that a node’s two-hop coverage area is four times as large as its one-hop coverage, and each node has the same number of one-hop and two-hop neighbors. Hence we can have the number of one-hop and two-hop neighbors as
and
respectively. Suppose there are several
common one-hop neighbors between node
i and
j. They will transmit at least one time in the hold-off interval of
j after its transmission. The probability that
i can capture the update of
j in an arbitrary slot via forwarding links can be considered as the service rate:
where
is the identical outage rate of all the wireless links.
If
i receives from
j via direct link, there is no need to wait for the forwarded messages, and the time is only consumed in the forwarding process, and the pmf of
can be written as:
Finally, according to the definition of , it can be given as the cumulative probability of , i.e., .
4.2. Mean Violation Duration within a Maintenance Interval
Next, we analyze the mean of
. Since the AoI at the start of
k-th maintaining interval is
and always smaller than
,
can be obtained as given in [
15]:
The mean of
can be written as follow:
where
. In the second term of the rhs where
and
are independently distributed, there is
. So
M can only be 1 and
. The pmf of
can then be written as:
where
.
5. Numerical and Simulation Analysis
According to the IEEE 802.16/WiMAX standard [
2], the value of
V and
H are determined by the related duration exponents, i.e.,
and
. The duration exponents are usually set to
and
, where
x is an non-negative integer [
9]. Here we set
and so
,
.
To verify the accuracy of our approximations, we first take the age violation probability
as an independent variable to analyze its impact on the transmission probability
. We substitute Equation (
18) into Equation (
1) and obtain the approximated value of
as the positive root of a quadratic equation, which is given as follow:
where the coefficients are adjusted as
,
, and
.
To intuitively present the impact of
on
, we compare the numerical results of the approximated and exact value of
under different
in
Figure 4. The exact value of
is obtained by directly calculating the result of Equation (
4) without approximation. We can observe that as
increases, the neighbors are more likely to be competing nodes, which leads to a decreasing value of
. We also find that the linear approximation of Equation (
14) is tight when
N is between 16 to 32, while for
or
, the value of
is slightly overestimated due to the imperfection of linear approximation.
Next we consider that
is also related to
by summarizing the derivations in
Section 4:
To obtain the approximation results, we search the value of
which can satisfy both Equations (
27) and (
28) simultaneously under different parameters including the number of neighbors
N, the ratio of relaying nodes
and the packet loss rate
.
As the interaction between
and
is now concerned, a C++-based virtual simulation platform is implemented to provide high-fidelity simulation results of the neighbor election based distributed slot access. This platform consists of virtual network nodes and wireless channels, where the synchronization procedures among nodes are predetermined to let them have the same timing of slot numbers and the start of slots. In each simulation slot, the transmitting nodes disseminate their messages to the relevant receiving nodes via virtual channels configured with different packet loss rates. The platform monitors the action of nodes and calculates the transmission probability and age violation probability from statistics. The simulation and approximation results are compared in
Figure 5, where the analytical results in [
9] are also plotted by black lines. We can first observe that for a greater packet loss rate, it is harder for the nodes to maintain the information updates, leading to a greater value of
and hence the transmission probability decreases. For
, the result from [
9] is underestimated when
, while it is slightly tighter than our approximations when
. For greater packet loss rate, saying
, our approximation is tighter than the one in [
9] when
, which shows that our approximation method is valid for greater
.
After verifying the accuracy of our approximation models, we also want to investigate the impact of the outage rate
of wireless links onto the age violation probability
, which is shown in
Figure 6.
We can see that as rises, also monotonically increases. For , the value of is lower than 0.1 when , while it increases rapidly when compared to other cases with a smaller number of neighbors. This is because when reaches a given level, the nodes cannot timely maintain the information from the two-hop and even one-hop neighbors, leading to higher age violation probability.
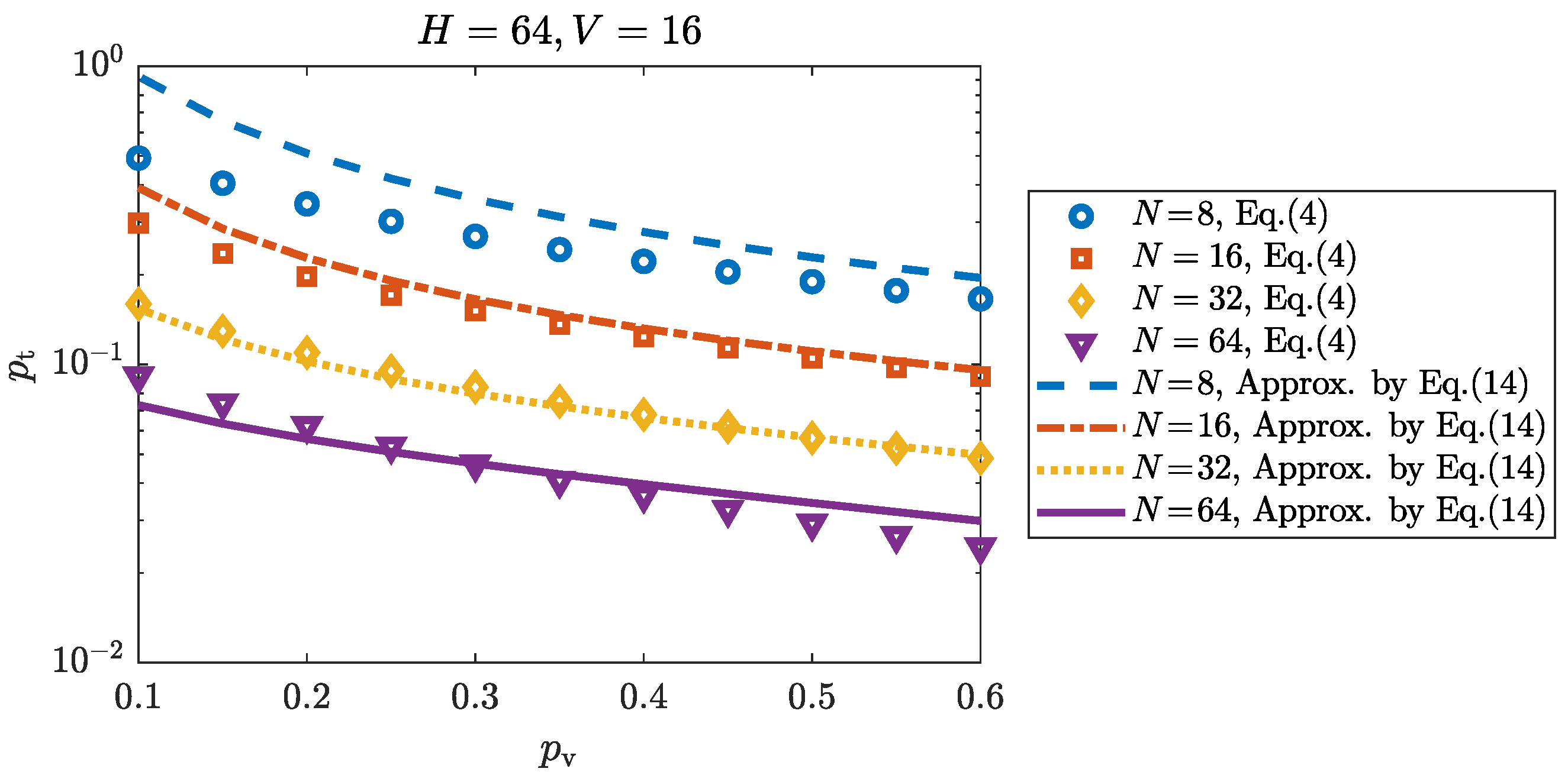
In
Figure 7, the approximation and simulation results of
are illustrated against the ratio of relaying nodes, which reflects the connectivity of network topology. It shows that a growing ratio of relaying nodes is beneficial to the value of
as the information updates from neighbors can be timely maintained with higher probability. Meanwhile our approximation is tight when
and
, and quite underestimated when
and
due to imperfection linear approximation and should be improved.