Protective Factors for Developing Cognitive Skills against Cyberattacks
Abstract
:1. Introduction
- (i)
- Is there a variation in cyberattacks during the period of the COVID-19 pandemic?
- (ii)
- Has the context of the COVID-19 pandemic increased the susceptibility of being a victim of cyberattacks?
- (iii)
- How can we model user behavior during the COVID-19 pandemic in the face of a cyberattack employing the steps of the cyber kill chain?
2. Exploratory Analysis of Social Engineering Attacks during the COVID-19 Pandemic
2.1. Social Engineering Attacks
2.2. Attacks on Teleconference Systems
2.3. Fake News
2.4. Malware
2.5. Phishing
3. Methods and Techniques
RQ1: Is there a variation in cyberattacks during the period of the COVID-19 pandemic?
RQ2: Has the context of the COVID-19 pandemic increased the susceptibility of being a victim of cyberattacks?
RQ3: How can we model user behavior during the COVID-19 pandemic in the face of a cyberattack employing the steps of the cyber kill chain?
“(COVID-19)” AND “(CYBERATTACKS OR CYBERSECURITY)”;
“(COVID-19)” AND “(HUMAN FACTORS)”;
“(COVID-19)” AND “(HUMAN BEHAVIOUR)”;
“(COVID-19)” AND “(VECTOR ATTACKS)”.
| Security Attacks | Number of Sources | Main Sources |
|---|---|---|
| Fake news and missing information | 9 | [39,40,41,42,43,44,45,46,47] |
| IoT | 1 | [48] |
| Phishing | 6 | [49,50,51,52,53,54,55] |
| Wi-Fi attacks | 1 | [56] |
| Malware | 1 | [57] |
| DDoS | 2 | [58,59] |
| Ransomware | 1 | [60] |
| Info stealer | 2 | [61,62] |
4. Exploratory Study of Human Factors in Cyberattacks during the COVID-19 Pandemic
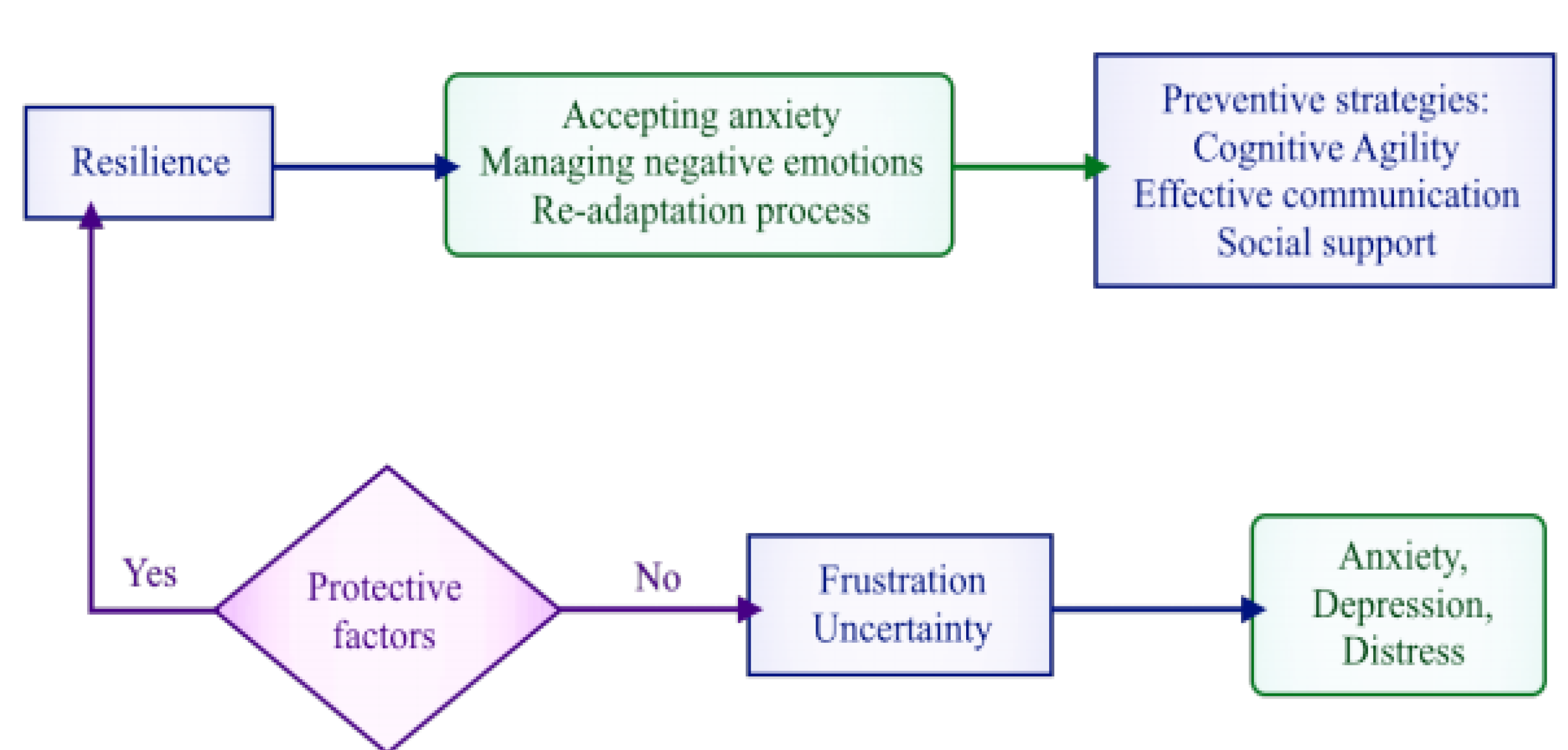
4.1. Psychological Impact and Behaviors during the Pandemic
4.2. Results of Extraction of Human Factor Used during Cyberattacks
RQ1. Is there a variation in security attacks during the period of the COVID-19 pandemic?
RQ2. Has the context of the COVID-19 pandemic increased the susceptibility of being a victim of cyberattacks?
RQ3. How can we model the user behavior during the COVID-19 pandemic in the face of a cyberattack employing the steps of the cyber kill chain?
5. Modeling of Cyberattacks Based on the Cyber Kill Chain
5.1. Psychological Impact and Behaviors during the Pandemic
5.2. Modeling Cyberattacks with Cyber Kill Chain
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Office for National Statistics. Coronavirus and the Social Impacts on Great Britain. 2021. Available online: https://www.ons.gov.uk/peoplepopulationandcommunity/ (accessed on 31 October 2022).
- UNICEF. COVID-19 Archives. UNICEF DATA. 2021. Available online: https://data.unicef.org/resources/resource-topic/covid-19/ (accessed on 31 October 2022).
- Sodhi, A.; Social Media Law & Cybercrime. Social Science Research Network SSRN. 2020. Available online: https://ssrn.com/abstract=3541485 (accessed on 31 October 2022).
- Serafini, G.; Parmigiani, B.; Amerio, A.; Aguglia, A.; Sher, L.; Amore, M. The psychological impact of COVID-19 on the mental health in the general population. QJM Int. J. Med. 2020, 113, 531–537. [Google Scholar] [CrossRef] [PubMed]
- Interpol. INTERPOL Report Shows Alarming Rate of Cyberattacks During COVID-19. 2020. Available online: https://www.interpol.int/News-and-Events/News/2020/INTERPOL-reportshows-alarming-rate-of-cyberattacks-during-COVID-19 (accessed on 31 October 2022).
- Europol. Office of the European Union, Luxembourg. 2020. Available online: https://www.europol.europa.eu/sites/default/files/documents/european_union_terrorism_situation_and_trend_report_te-sat_2020_0.pdf (accessed on 31 October 2022).
- McAfee. 2017. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-mar-2017.pdf (accessed on 3 November 2022).
- McAfee. 2018. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-mar-2018.pdf (accessed on 3 November 2022).
- McAfee. 2019. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-mar-2019.pdf (accessed on 3 November 2022).
- McAfee. 2020. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-mar-2020.pdf (accessed on 3 November 2022).
- McAfee. 2021. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-mar-2021.pdf (accessed on 3 November 2022).
- McAfee. 2022. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-mar-2022.pdf (accessed on 3 November 2022).
- Anti-Phishing Work Group—APWG. Interisle Study Shows 61% Increase in Phishing Attacks, More Brands Targeted, and 257% Increase in Cryptocurrency Phishing. 2022. Available online: https://apwg.org/interisle-study-shows-61-increase-in-phishing-attacks-more-brands-targeted-and-257-increase-in-cryptocurrency-phishing/ (accessed on 3 November 2022).
- Albladi, S.M.; Weir, G.R.S. User characteristics that influence judgment of social engineering attacks in social networks. Hum. Centric Comput. Inf. Sci. 2018, 8, 5. [Google Scholar] [CrossRef]
- Arya, S.; Kaji, A.H.; Boermeester, M.A. PRISMA Reporting Guidelines for Meta-analyses and Systematic Reviews. JAMA Surg. 2021, 156, 789–790. [Google Scholar] [CrossRef] [PubMed]
- Venkatesha, S.; Reddy, K.R.; Chandavarkar, B.R. Social Engineering Attacks during the COVID-19 Pandemic. SN Comput. Sci. 2021, 2, 1–9. [Google Scholar] [CrossRef] [PubMed]
- Susukailo, V.; Opirskyy, I.; Vaslyshyn, S. Analysis of the attack vectors used by threat actors during the pandemic. In Proceedings of the IEEE 15th International Conference on Computer Sciences and Information Technologies, Zbarazh, Ukraine, 23–26 September 2020; pp. 261–264. [Google Scholar] [CrossRef]
- Setera, K.; FBI. FBI Warns of Teleconferencing and Online Classroom Hijacking during COVID-19 Pandemic: March. 2020. Available online: https://www.fbi.gov/contact-us/field-offices/boston/news/press-releases/fbi-warns-of-teleconferencing-and-online-classroom-hijacking-during-covid-19-pandemic (accessed on 13 November 2022).
- Anansaringkarn, P.; Neo, R. How can state regulations over the online sphere continue to respect the freedom of expression? A case study of contemporary ‘fake news’ regulations in Thailand. Inf. Commun. Technol. Law 2021, 30, 283–303. [Google Scholar] [CrossRef]
- Bracci, A.; Nadini, M.; Aliapoulios, M.; McCoy, D.; Gray, I.; Teytelboym, A.; Gallo, A.; Baronchelli, A. Dark Web Marketplaces and COVID-19: Before the vaccine. EPJ Data Sci. 2021, 10, 6. [Google Scholar] [CrossRef] [PubMed]
- Check Point Blog. Check Point. Coronavirus-Themed Domains 50% More Likely to be Malicious than Other Domains. 2020. Available online: https://blog.checkpoint.com/2020/03/05/update-coronavirus-themed-domains-50-morelikely-to-be-malicious-than-other-domains/ (accessed on 15 November 2022).
- Roberts, G.; Avast. The Year of Fake News, COVID-19 Scams and Ransomware. 2020. Available online: https://blog.avast.com/es/2020-year-in-review-avast (accessed on 15 November 2022).
- Kent, J. Cequence security. Tales from the Front Lines: Attackers on Lockdown Focus on API. 2020. Available online: https://www.cequence.ai/blog/tales-from-the-frontlines-attackers-on-lockdown-focus-on-apis/ (accessed on 15 November 2022).
- Burgess, M.; Wired. Secret NHS Files Reveal Plans for Coronavirus Contact Tracing App. 2020. Available online: https://www.wired.co.uk/article/nhs-covid-19-app-health-status-future (accessed on 18 November 2022).
- Kovacs, E.; Security Week. Over 6400 Edison Mail Users Hit by Security Bug in iOS App. 2020. Available online: https://www.securityweek.com/over-6400-edison-mail-users-hitsecurity-bug-ios-app (accessed on 25 November 2022).
- Sushma, K.; Jayalakshmi, M.; Guha, T. Deep Learning for Phishing Website Detection. In Proceedings of the 2022 IEEE 2nd 183 Mysore Sub Section International Conference (MysuruCon), Mysuru, India, 16–17 October 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar]
- FBI’s IC3. 2020 Internet Crime Report; Federal Bureau of Investigation—Internet Crime Complaint Center: Washington, DC, USA, 2020; pp. 1–28. [Google Scholar]
- Bikov, T.D.; Iliev, T.B.; Mihaylov, G.Y.; Stoyanov, I.S. Phishing in Depth—Modern Methods of Detection and Risk Mitigation. In Proceedings of the 2019 42nd International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 20–24 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 447–450. [Google Scholar] [CrossRef]
- AlGhanboosi, B.; Ali, S.; Tarhini, A. Examining the effect of regulatory factors on avoiding online blackmail threats on social media: A structural equation modeling approach. Comput. Hum. Behav. 2023, 144, 107702. [Google Scholar] [CrossRef]
- Cole, S.; Kvavilashvili, L. Spontaneous and deliberate future thinking: A dual process account. Psychol. Res. 2021, 85, 464–479. [Google Scholar] [CrossRef]
- Algarni, A.; Xu, Y.; Chan, T. Social Engineering in Social Networking Sites: The Art of Impersonation. In Proceedings of the 2014 IEEE International Conference on Services Computing, Anchorage, AK, USA, 27 June–2 July 2014; pp. 797–804. [Google Scholar] [CrossRef]
- Jones, H.S.; Towse, J.N.; Race, N. Susceptibility to email fraud: A review of psychological perspectives, data-collection methods, and ethical considerations. Int. J. Cyber Behav. Psychol. Learn. 2015, 5, 13–29. [Google Scholar] [CrossRef]
- Valaskivi, K. Hybrid CoE Strategic Analysis 5: Beyond Fake News: Content Confusion and Understanding the Dynamics of the Contemporary Media Environment. Version 4 June 2023 submitted to Journal Not Specified 7 of 7. 2018. Available online: https://www.hybridcoe.fi/publications/hybrid-coe-strategic-analysis-5-beyond-fake-news-content-confusion-and-understanding-the-dynamics-of-the-contemporary-media-environment/ (accessed on 25 November 2022).
- Verkijika, S.F. “If you know what to do, will you take action to avoid mobile phishing attacks”: Self-efficacy, anticipated regret, and gender. Comput. Hum. Behav. 2019, 101, 286–296. [Google Scholar] [CrossRef]
- Singh, K.; Aggarwal, P.; Rajivan, P.; Gonzalez, C. Training to Detect Phishing Emails: Effects of the Frequency of Experienced Phishing Emails. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting, Seattle, WA, USA, 28 October–1 November 2019; Volume 63, pp. 453–457. [Google Scholar] [CrossRef]
- Weil, T.; Murugesan, S. IT Risk and Resilience—Cybersecurity Response to COVID-19. IT Prof. 2020, 22, 4–10. [Google Scholar] [CrossRef]
- Gupta, A.; Singh, A.; Bharadwaj, D.; Mondal, A. Humans and Robots: A Mutually Inclusive Relationship in a Contagious World. Int. J. Autom. Comput. 2021, 18, 185–203. [Google Scholar] [CrossRef]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M.; Saldamli, G. Predicting and preventing cyber attacks during covid-19 time using data analysis and proposed secure IoT layered model. In Proceedings of the Fourth International Conference on Multimedia Computing, Valencia, Spain, 19–22 October 2020; pp. 113–118. [Google Scholar] [CrossRef]
- Schuetz, S.W.; Sykes, T.A.; Venkatesh, V. Combating COVID-19 fake news on social media through fact checking: Antecedents and consequences. Eur. J. Inf. Syst. 2021, 30, 376–388. [Google Scholar] [CrossRef]
- Maakoul, O.; Boucht, S.; El Hachimi, K.; Azzouzi, S. Towards Evaluating the COVID’19 related Fake News Problem: Case of Morocco. In Proceedings of the 2020 IEEE 2nd International Conference on Electronics, Control, Optimization and Computer Science (ICECOCS), Kenitra, Morocco, 2–3 December 2020. [Google Scholar] [CrossRef]
- Yoshikawa, K.; Awa, T.; Kusano, R.; Sato, H.; Ichino, M.; Yoshiura, H. A Fake News Dissemination Model Based on Updating Reliability and Doubt among Individuals. In Proceedings of the 2020 11th International Conference on Awareness Science and Technology (iCAST), Qingdao, China, 7–9 December 2020. [Google Scholar] [CrossRef]
- Zaeem, R.N.; Li, C.; Barber, K.S. On Sentiment of Online Fake News. In Proceedings of the 2020 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (ASONAM), The Hague, The Netherlands, 7–10 December 2020. [Google Scholar] [CrossRef]
- Abdelminaam, D.S.; Ismail, F.H.; Taha, M.; Taha, A.; Houssein, E.H.; Nabil, A. CoAID-DEEP: An Optimized Intelligent Framework for Automated Detecting COVID-19 Misleading Information on Twitter. IEEE Access 2021, 9, 27840–27867. [Google Scholar] [CrossRef] [PubMed]
- De, S.; Agarwal, D. A novel model of supervised clustering using sentiment and contextual analysis for fake news detection. In Proceedings of the Third International Conference on Multimedia Processing, Communication Information Technology (MPCIT), Shivamogga, India, 11–12 December 2020; pp. 112–117. [Google Scholar]
- Verma, S.; Paul, A.; Kariyannavar, S.S.; Katarya, R. Understanding the Applications of Natural Language Processing on COVID-19 Data. In Proceedings of the 2020 4th International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 5–7 November 2020. [Google Scholar] [CrossRef]
- Hawa, S.; Lobo, L.; Dogra, U.; Kamble, V. Combating misinformation dissemination through verification and content driven recommendation. In Proceedings of the Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; pp. 917–924. [Google Scholar] [CrossRef]
- Kapusta, J.; Benko, Ľ.; Munk, M. Fake News Identification Based on Sentiment and Frequency Analysis. In Learning and Analytics in Intelligent Systems; Springer: Cham, Switzerland, 2020; pp. 400–409. [Google Scholar] [CrossRef]
- Hussain, F.; Abbas, S.G.; Shah, G.A.; Pires, I.M.; Fayyaz, U.U.; Shahzad, F.; Garcia, N.M.; Zdravevski, E. A Framework for Malicious Traffic Detection in IoT Healthcare Environment. Sensors 2021, 21, 3025. [Google Scholar] [CrossRef] [PubMed]
- Abroshan, H.; Devos, J.; Poels, G.; Laermans, E. A phishing Mitigation Solution using Human Behaviour and Emotions that Influence the Success of Phishing Attacks. In Proceedings of the 29th ACM Conference on User Modeling, Adaptation and Personalization, Utrecht, The Netherlands, 21–25 June 2021. [Google Scholar] [CrossRef]
- Akdemir, N.; Yenal, S. How Phishers Exploit the Coronavirus Pandemic: A Content Analysis of COVID-19 Themed Phishing Emails. SAGE Open 2021, 11, 215824402110318. [Google Scholar] [CrossRef]
- Furini, M.; Mirri, S.; Montangero, M.; Prandi, C. Untangling between fake-news and truth in social media to understand the COVID-19 Coronavirus. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020. [Google Scholar] [CrossRef]
- Al-Turkistani, H.F.; Ali, H. Enhancing Users’ Wireless Network Cyber Security and Privacy Concerns during COVID-19. In Proceedings of the 2021 1st International Conference on Artificial Intelligence and Data Analytics (CAIDA), Riyadh, Saudi Arabia, 6–7 April 2021. [Google Scholar] [CrossRef]
- Hijji, M.; Alam, G. A Multivocal Literature Review on Growing Social Engineering Based Cyber-Attacks/Threats During the COVID-19 Pandemic: Challenges and Prospective Solutions. IEEE Access 2021, 9, 7152–7169. [Google Scholar] [CrossRef]
- Baseskioglu, M.O.; Tepecik, A. Cybersecurity, Computer Networks Phishing, Malware, Ransomware, and Social Engineering Anti-Piracy Reviews. In Proceedings of the 2021 3rd International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 11–13 June 2021. [Google Scholar] [CrossRef]
- Chandra, N.A.; Putri Ratna, A.A.; Ramli, K. Development of a Cyber-Situational Awareness Model of Risk Maturity Using Fuzzy FMEA. In Proceedings of the 2020 International Workshop on Big Data and Information Security (IWBIS), Depok, Indonesia, 17–18 October 2020. [Google Scholar] [CrossRef]
- Sharma, R.; Sharma, N.; Mangla, M. An Analysis and Investigation of InfoStealers Attacks during COVID’19: A Case Study. In Proceedings of the 2021 2nd International Conference on Secure Cyber Computing and Communications (ICSCCC), Jalandhar, India, 21–23 May 2021. [Google Scholar] [CrossRef]
- Muttoo, S.; Badhani, S. An Analysis of Malware Detection and Control through COVID-19 Pandemic. In Proceedings of the 2021 8th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 17–19 March 2021; pp. 637–641. [Google Scholar]
- Cvitić, I.; Peraković, D.; Periša, M.; Jurcut, A.D. Methodology for Detecting Cyber Intrusions in e-Learning Systems during COVID-19 Pandemic. Mob. Netw. Appl. 2021, 28, 231. [Google Scholar] [CrossRef]
- Said Elsayed, M.; Le-Khac, N.-A.; Jurcut, A.D. Dealing With COVID-19 Network Traffic Spikes [Cybercrime and Forensics]. IEEE Secur. Priv. 2021, 19, 90–94. [Google Scholar] [CrossRef]
- Jarjoui, S.; Murimi, R.; Murimi, R. Hold My Beer: A Case Study of how Ransomware Affected an Australian Beverage Company. In Proceedings of the 2021 International Conference on Cyber Situational Awareness, Data Analytics and Assessment (CyberSA), Dublin, Ireland, 14–18 June 2021. [Google Scholar] [CrossRef]
- Ahsan Pritom, M.M.; Schweitzer, K.M.; Bateman, R.M.; Xu, M.; Xu, S. Data-Driven Characterization and Detection of COVID-19 Themed Malicious Websites. In Proceedings of the 2020 IEEE International Conference on Intelligence and Security Informatics (ISI), Arlington, VA, USA, 9–10 November 2020. [Google Scholar] [CrossRef]
- Wang, L.; He, R.; Wang, H.; Xia, P.; Li, Y.; Wu, L.; Zhou, Y.; Luo, X.; Sui, Y.; Guo, Y.; et al. Beyond the virus: A first look at coronavirus-themed Android malware. Empir. Softw. Eng. 2021, 26, 82. [Google Scholar] [CrossRef]
- UK Data Service. UK Data Service COVID-19 Data. 2020. Available online: https://www.ukdataservice.ac.uk/get-data/themes/covid-19/covid-19-data.aspx (accessed on 25 November 2022).
- Staszkiewicz, P.; Chomiak-Orsa, I.; Staszkiewicz, I. Dynamics of the COVID-19 Contagion and Mortality: Country Factors, Social Media, and Market Response Evidence From a Global Panel Analysis. IEEE Access 2020, 8, 106009–106022. [Google Scholar] [CrossRef]
- Burton, S.; Puddephatt, J.; Baines, L.; UNICEF Innocenti: Children and COVID-19 Research Library. UNICEF Office of Research—Innocenti. 2021. Available online: https://www.unicefirc.org/covid-children-library?tag=behaviour (accessed on 5 December 2022).
- Balanzá-Martínez, V.; Kapczinski, F.; de Azevedo Cardoso, T.; Atienza-Carbonell, B.; Rosa, A.R.; Mota, J.C.; De Boni, R.B. The assessment of lifestyle changes during the COVID-19 pandemic using a multidimensional scale. Rev. Psiquiatr. Salud Ment. 2021, 14, 16–26. [Google Scholar] [CrossRef] [PubMed]
- World Bank. Understanding the Coronavirus (COVID-19) Pandemic Through Data. Universal Health Coverage Data. 2021. Available online: https://datatopics.worldbank.org/universal-health-coverage/coronavirus/ (accessed on 25 November 2022).
- University of Essex, Institute for Social and Economic Research. Understanding Society: COVID-19 Study, 2020: Special Licence Access, School Codes; UK Data Service; University of Essex, Institute for Social and Economic Research: Colchester, UK, 2021. [Google Scholar] [CrossRef]
- World Bank. World Bank Education COVID-19 School Closures Map. 2020. Available online: https://www.worldbank.org/en/data/interactive/2020/03/24/world-bank-educationand-covid-19 (accessed on 25 November 2022).
- Eurofond. Living, Working and COVID-19 Data. Data.Europa.Eu. 2020. Available online: https://data.europa.eu/data/datasets/living-working-and-covid-19-data?locale=en (accessed on 25 November 2022).
- Crooks, C.L.; Hogg, J.L.; Martin, S.M.; Grant, J.; Lemoie, K.; Robbins, M. Understanding Generational Factors in the Workplace: Current Considerations for Telework Practices and the Digital Native. In Proceedings of the 2020 IEEE International Professional Communication Conference (ProComm), Kennesaw, GA, USA, 19–22 July 2020. [Google Scholar]
- Government of Canada. Percentage of Workforce Teleworking or Working Remotely, and Percentage of Workforce Expected to Continue Teleworking or Working Remotely after the Pandemic, by Business Characteristics. 2020. Available online: https://open.canada.ca/data/en/dataset/9909c57f-b84e-4cc9-9255-3d526f60ef4d (accessed on 28 November 2022).
- Larrea-Araujo, C.; Ayala-Granja, J.; Vinueza-Cabezas, A.; Acosta-Vargas, P. Ergonomic Risk Factors of Teleworking in Ecuador during the COVID-19 Pandemic: A Cross-Sectional Study. Int. J. Environ. Res. Public Health 2021, 18, 5063. [Google Scholar] [CrossRef] [PubMed]
- Kalinowski, A.; Research Sources and Guides: COVID-19’s Impact on Business: Data. Stanford Graduate School of Business Library. 2020. Available online: https://libguides.stanford.edu/covid19 (accessed on 29 November 2022).
- Georgetown University. Tracking COVID-19 Unemployment and Job Losses. 2021. Available online: https://cew.georgetown.edu/cew-reports/jobtracker/#tool-3-tracking (accessed on 30 November 2022).
- Kolokotroni, O.; Mosquera, M.C.; Quattrocchi, A.; Heraclides, A.; Demetriou, C.; Philippou, E. Lifestyle habits of adults during the COVID-19 pandemic lockdown in Cyprus: Evidence from a cross-sectional study. BMC Public Health 2021, 21, 786. [Google Scholar] [CrossRef] [PubMed]
- Tarnowski, I. How to use cyber kill chain model to build cybersecurity? Eur. J. High. Educ. IT 2017. Available online: https://tnc17.geant.org/getfile/tnc17_paper_TNC17-IreneuszTarnowski-HowToUseCyberKillChainModelToBuildCybersecurity_-En.pdf (accessed on 5 December 2022).
- Chandola, T.; Kumari, M.; Booker, C.L.; Benzeval, M. The mental health impact of COVID-19 and lockdown-related stressors among adults in the UK. Psychol. Med. 2020, 52, 2997–3006. [Google Scholar] [CrossRef] [PubMed]
- Sokolov, M.; The Drum. The Pandemic Infodemic: How Social Media Helps (and Hurts) during the Coronavirus Outbreak. 2020. Available online: https://www.thedrum.com/opinion/2020/03/03/the-pandemic-infodemic-how-socialmedia-helps-and-hurts-during-the-coronavirus (accessed on 5 December 2022).
- Kaspersky. Google Blocking 18 m Coronavirus Scam e-mails Every Day. 2020. Available online: https://www.kaspersky.com/resource-center/definitions/cookies (accessed on 5 December 2022).
- Chin, S.W.; Zheng, J.Y. Seeing is believing examining self-efficacy and trait hope as moderators of youths’ positive risk-taking intention. J. Risk Res. 2020, 24, 819–832. [Google Scholar] [CrossRef]
- Ding, B.; Zhang, R.; Xu, L.; Liu, G.; Yang, S.; Liu, Y.; Zhang, Q. U2D2Net: Unsupervised Unified Image Dehazing and Denoising Network for Single Hazy Image Enhancement. IEEE Trans. Multimed. 2023, 1–16. [Google Scholar] [CrossRef]
- Mohamed, G.; Visumathi, J.; Mahdal, M.; Anand, J.; Elangovan, M. An Effective and Secure Mechanism for Phishing Attacks Using a Machine Learning Approach. Processes 2022, 10, 1356. [Google Scholar] [CrossRef]
- Zhang, R.; Yang, S.; Zhang, Q.; Xu, L.; He, Y.; Zhang, F. Graph-based few-shot learning with transformed feature propagation and optimal class allocation. Neurocomputing 2022, 470, 247–256. [Google Scholar] [CrossRef]
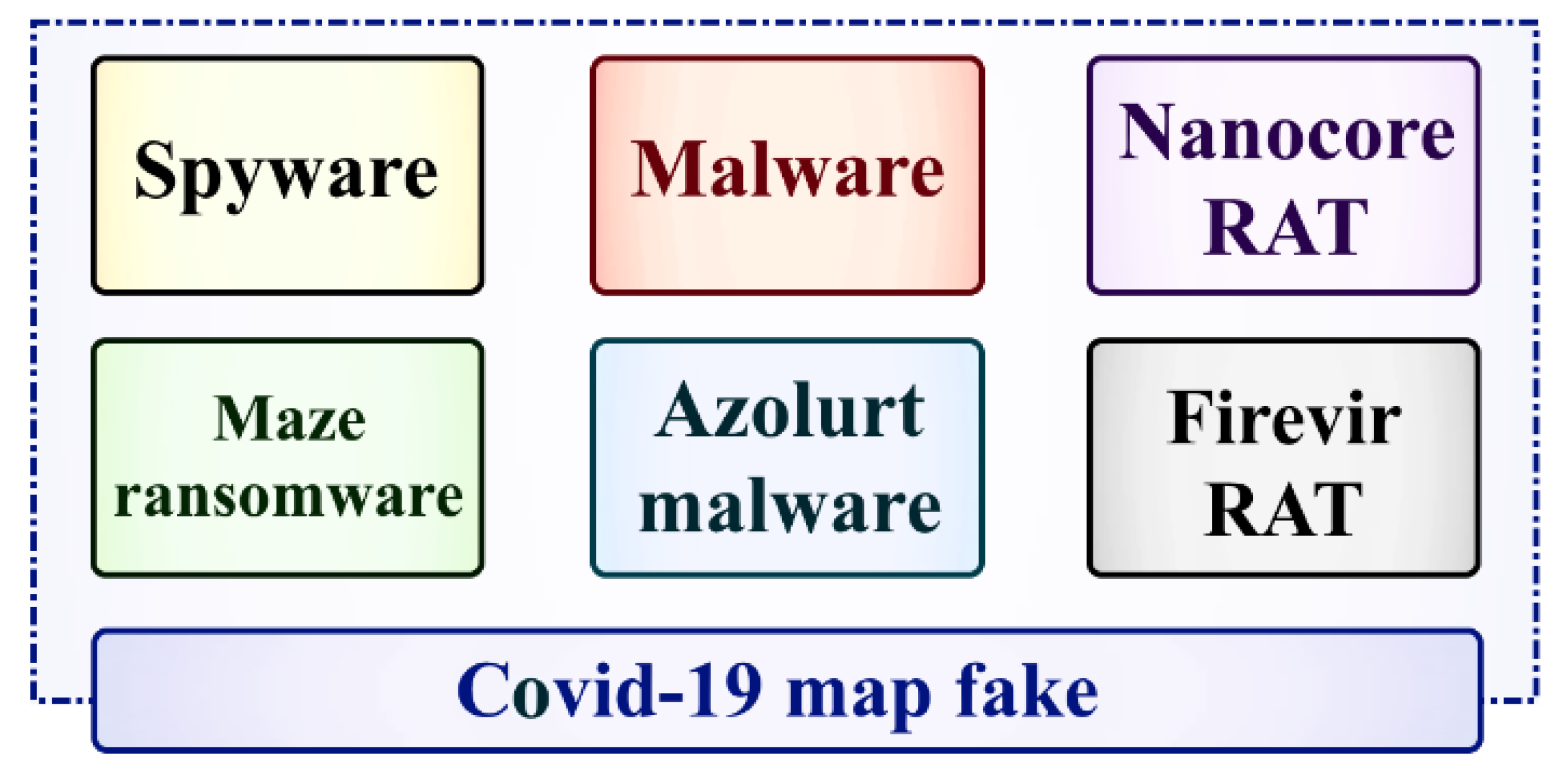


| Cyberattacks | 2018 [8] | 2019 [9] | 2020 [10] |
|---|---|---|---|
| Malware | 700,000,000 | 900,000,000 | 1,200,000,000 |
| Ransomware | 16,000,000 | 1,000,000 | 1,250,000 |
| Year | 2019 [9] | 2020 [10] | 2021 [11] | 2022 [12] |
|---|---|---|---|---|
| Spam traffic | 56.36% | 52.48% | 56.33% | 45.56% |
| An anti-phishing system was triggered | 246,231,645 times | 482,465,211 times | 434,898,635 times | 253,365,212 times |
| Type | Description |
|---|---|
| Baiting | It is a social engineering technique where the attacker arouses the victim’s interest or curiosity in a trap to steal information or access their system through malware. |
| Invoice Fraud | This technique is used to gain access to a victim’s email address. In an example of this technique, the recipient is tricked into believing that they must make an immediate payment. |
| Phishing | It is one of the most-used social engineering techniques, where attackers trick users to obtain information or breach their devices. Attackers impersonate a legitimate organization or entity to send emails to deceive recipients. |
| Vishing | Also known as voice phishing. It is a social engineering attack focused on phone lines. The attacker performs the scam by calling a legitimate entity to obtain confidential information, such as credit card details. |
| Pretexting | Pretexting is another type of social engineering. The attacker creates a good pretext, scenario, and coherent story to steal information from the victims. |
| Spear Phishing | It is a phishing attack where the objective is to obtain information from a specific user or organization. A previous study is made to choose the victim. |
| Scareware | It is a type of malware used with social engineering techniques. It seeks to scare, cause fear, and shock the user to install and buy software that is not needed. |
| Mobility | Health | Shopping | Human Contact |
|---|---|---|---|
| Stayed at home more | Washed hands more | Went to shops less | Applied social distancing |
| Traveled less | Cleaned the house more | Shopped online more | Wore protective face masks outside |
| Avoided public transport | Did more exercise | Used less cash | Avoided public places like bars and restaurants |
| Worked from home | Visited more mental health services | Avoided certain shopping times | Canceled plans with family or friends |
| Category | Brand | Description |
|---|---|---|
| Entertainment | Netflix | Free access |
| Disney Plus | Suspension notification | |
| Cancellation confirmation | ||
| Update payment details | ||
| Create new password | ||
| Unusual activity | ||
| Governance | OMS | Vaccine (process, post-effects) |
| WHO | Cures and treatment for COVID-19 | |
| Health organizations | COVID-19 spreading | |
| FBI | COVID-19 symptoms | |
| INTERPOL | ||
| EUROPOL | ||
| Commerce | Walmart | Schedule time |
| Best Buy | Vaccine distribution | |
| Woolworths | Gift cards | |
| Marks and Spencer | Open shops | |
| Amazon |
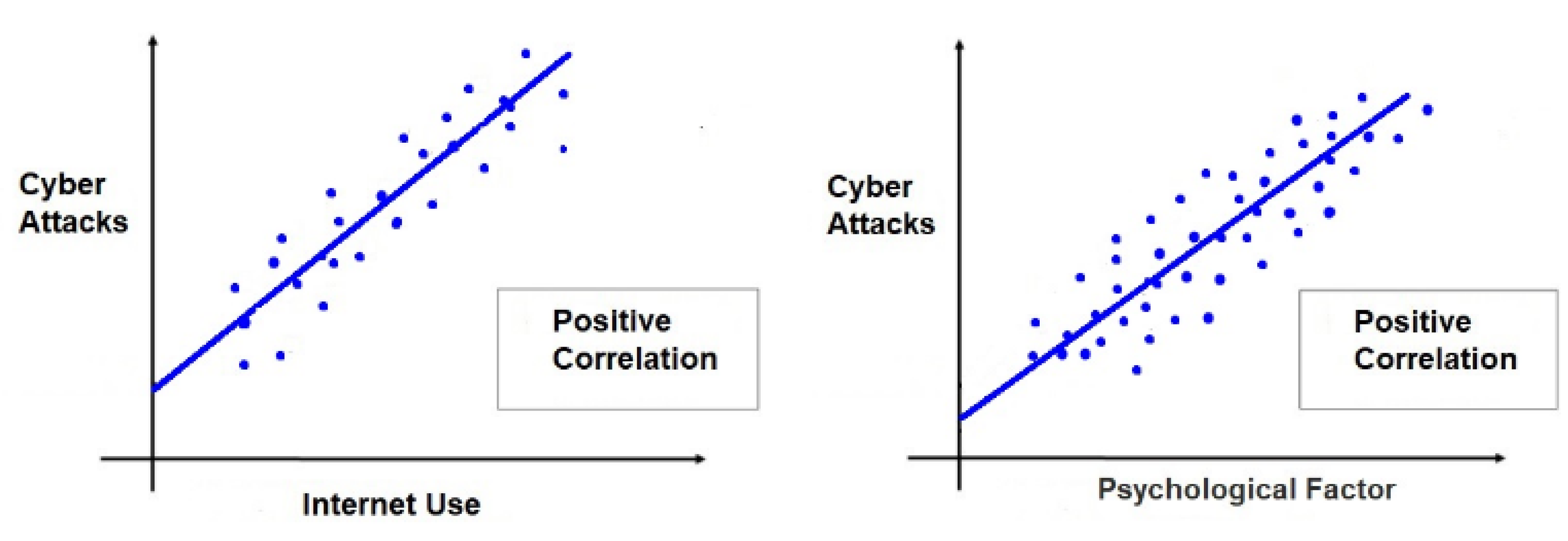
| Correlations | ||||
|---|---|---|---|---|
| Computer Attack | Psychological Factor | System Vulnerability | ||
| Computer Attack | Pearson’s Correlation | 1.000 | 0.210 ** | 0.430 ** |
| Sig. (Bilateral) | 0.000 | 0.000 | ||
| N | 51.931 | 51.931 | 51.931 | |
| Psychological Factor | Pearson’s Correlation | 0.210 ** | 1.000 | −0.015 ** |
| Sig. (Bilateral) | 0.000 | 0.001 | ||
| N | 51.931 | 51.931 | 51.931 | |
| System Vulnerability | Pearson’s Correlation | 0.430 ** | −0.015 ** | 1.000 |
| Sig. (Bilateral) | 0.000 | 0.001 | ||
| N | 51.931 | 51.931 | 51.931 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cazares, M.; Fuertes, W.; Andrade, R.; Ortiz-Garcés, I.; Rubio, M.S. Protective Factors for Developing Cognitive Skills against Cyberattacks. Electronics 2023, 12, 4007. https://doi.org/10.3390/electronics12194007
Cazares M, Fuertes W, Andrade R, Ortiz-Garcés I, Rubio MS. Protective Factors for Developing Cognitive Skills against Cyberattacks. Electronics. 2023; 12(19):4007. https://doi.org/10.3390/electronics12194007
Chicago/Turabian StyleCazares, María, Walter Fuertes, Roberto Andrade, Iván Ortiz-Garcés, and Manuel Sánchez Rubio. 2023. "Protective Factors for Developing Cognitive Skills against Cyberattacks" Electronics 12, no. 19: 4007. https://doi.org/10.3390/electronics12194007
APA StyleCazares, M., Fuertes, W., Andrade, R., Ortiz-Garcés, I., & Rubio, M. S. (2023). Protective Factors for Developing Cognitive Skills against Cyberattacks. Electronics, 12(19), 4007. https://doi.org/10.3390/electronics12194007







