An Efficient Encryption Scheme with Fully Hidden Access Policy for Medical Data
Abstract
1. Introduction
2. Related Work
3. Preliminaries
3.1. Bilinear Map
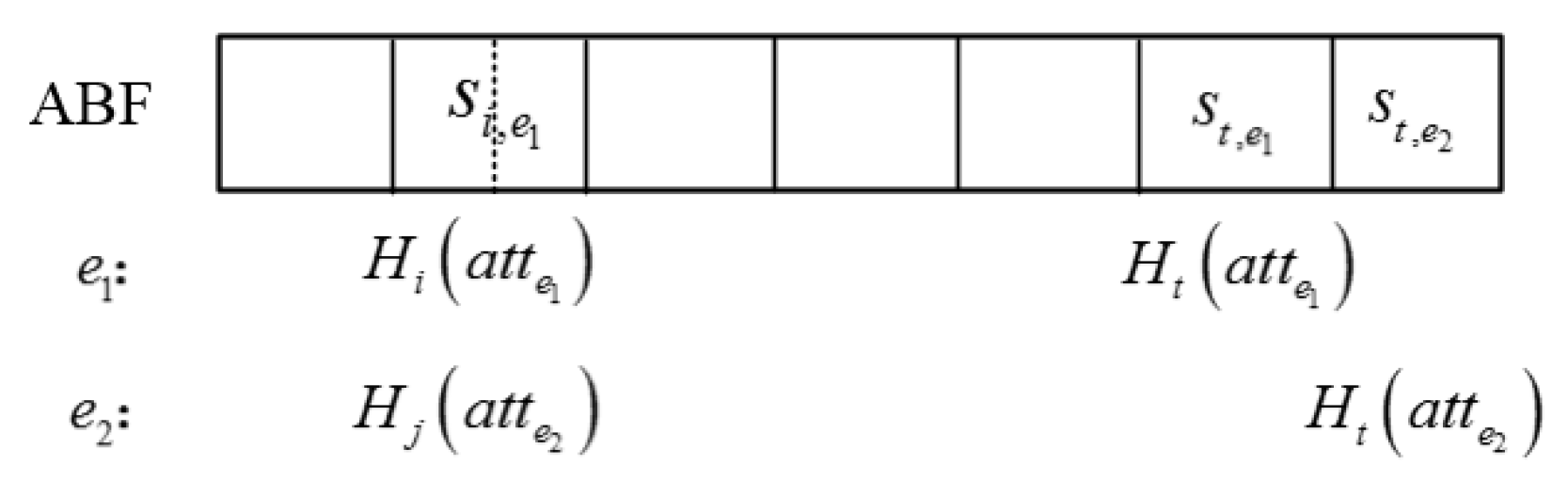
3.2. Bloom Filter
3.3. (q − 1)-BDHE Assumption
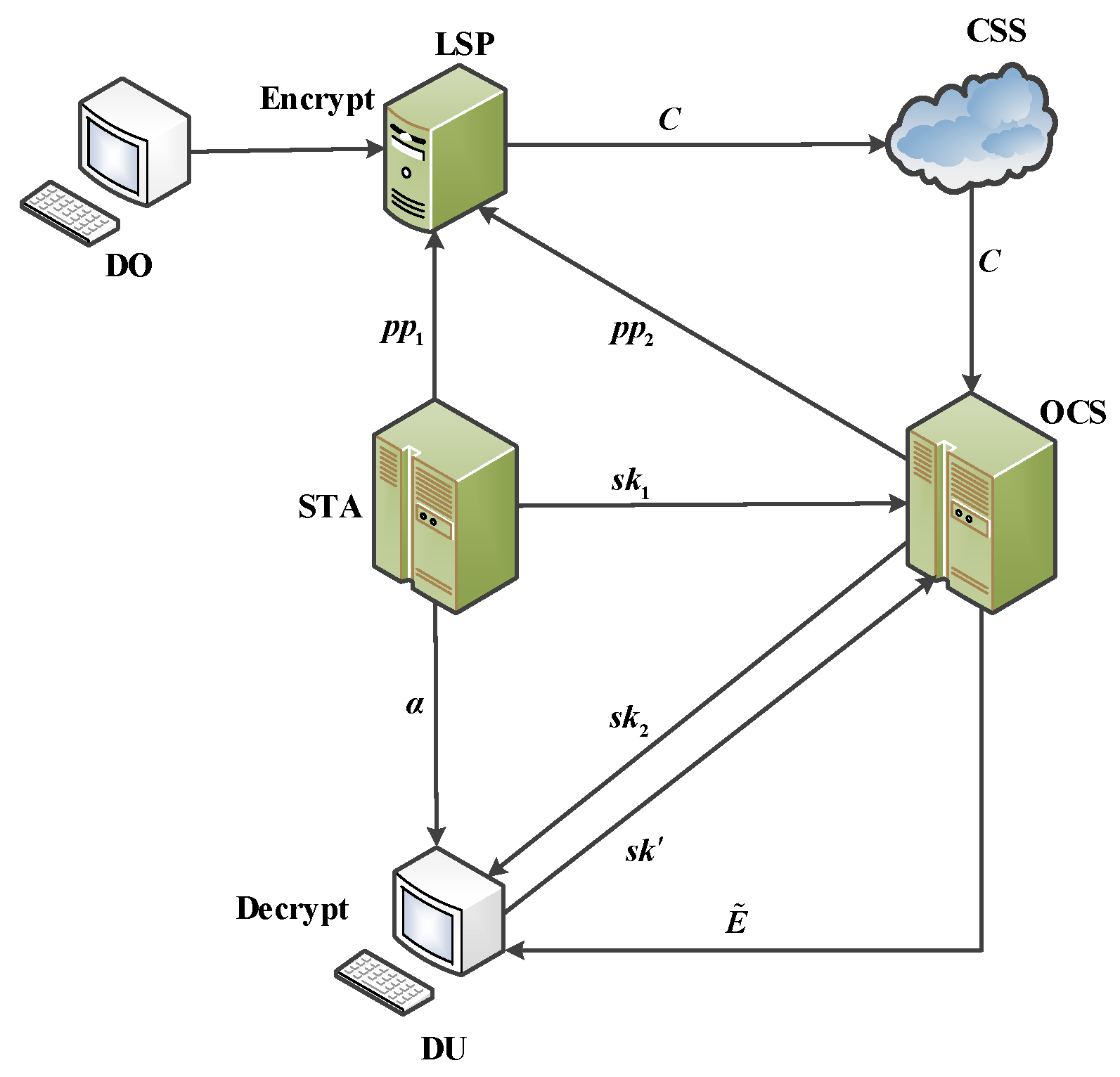
4. System Model
4.1. The Entity of the Model
4.2. The Definition of the Model
- The algorithm inputs the user attribute R and the attribute bloom filter . If the attribute R meets the access policy, it outputs . It then executes the following decryption phase; otherwise, it outputs . It terminates the decryption operations.
- Outsourced decryption phase. It continues to perform the decryption operation as follows:The transformation key generation algorithm takes the user secret key as input. It generates the transformation secret key and the outsourced decryption key .It inputs the transformation secret key and the partial ciphertext . The CSS generates the intermediate value , which is irrelevant to the medical data.The outsourced decryption algorithm takes as input the intermediate value , the outsourced decryption key , and the ciphertext c. The DU generates medical data by the algorithm.
4.3. The Security Definition of the Model
4.3.1. Data Privacy Security of the Model
- Init: In this phase, the adversary gives the challenge access structure to the challenger .
- Setup: First of all, executes the and phase. The STA generates the key pair . The OCS generates the key pair . transmits the public parameter to . The STA and the OCS, respectively, store the master secret keys and .
- Phase 1: makes a secret key query, where the secret key is related to attributes the R. However, R is not satisfied with the challenge access structure . generates by executing and sends it to .
- Challenge: sends two equal-size challenge plaintext messages and to , as well as the challenge access policy . firstly uses the two symmetric keys and to, respectively, encrypt medical data and . Then, encrypts by using CP-ABE, where . The challenge ciphertext is obtained by running the and algorithm and sending to .
- Phase 2: The query is the same as the secret key query in Phase 1. However, obtains , which is different from Phase 1. They also do not satisfy the challenge access policy .
- Guess: The adversary outputs the guess . If , wins the game.
4.3.2. Hiding the Access Policy Security of the Model
- Init: In this phase, the adversary gives the challenge access policies and to the challenger .
- Setup: First of all, executes the and phase. The STA generates the key pair . The OCS generates the key pair . transmits the public parameter to . The STA and the OCS save the master secret keys and by themselves.
- Phase 1: makes a secret key query, where the secret key is related to the attributes R. However, the attribute R is not satisfied with the challenge access structure . generates by executing and sends it to .
- Challenge: sends the medical data to . It uses the symmetric key to encrypt . randomly chooses the value . It embeds into the CP-ABE ciphertext. Finally, obtains the challenge ciphertext and sends it to .
- Phase 2: The query is the same as the secret key query in Phase 1. However, obtains , which is different from Phase 1. They also do not satisfy the challenge access policy .
- Guess: outputs a guess about b. If , wins the game.
4.3.3. Outsourced Decryption Security of the Model
- Init: In this phase, the adversary gives the challenge access structure to the challenger .
- Setup: First of all, sets a tuple . executes the and phase. The STA generates the key pair . the OCS generates the key pair . Then, transmits the public parameter to . The STA and the OCS conserve the master secret keys and by themselves.
- Phase 1: makes a secret key query and transformation key query, where the secret key is related to the attributes R. However, R is not satisfied with challenge access structure . generates by executing . executes to generate the transformation secret key and the outsourced decryption key . It stores by itself. saves and to T and sends T to . If T exists, performs the phase; otherwise, it cannot perform the decryption operations.
- Challenge: sends two equal-size challenge plaintext messages and to . , respectively, encrypts and with the two symmetric keys and . uses the challenge access policy to encrypt the symmetric key , where . The challenge ciphertext is obtained by running the and algorithms and sending to .
- Phase 2: The query is the same as the secret key query and the transformation key query in Phase 1. However, obtains T, which is different from Phase 1. They also do not satisfy the challenge access policy .
- Guess: outputs a guess value . If , wins the game.
5. Construction
- In the ABF, the DU firstly uses the hash function to compute the index value of the user attribute R. The DU obtains the string location, which is . If the attribute R is not in the ABF, the attribute does not meet the access policy. So, it outputs and terminates the decryption operation. If it outputs , it continues to execute the outsourced decryption algorithm. It also takes as outputs, where i is the attribute row number in the access matrix P.
- Outsourced Decryption Phase: During the outsourced decryption phase, we always ensure that medical data are securely transmitted and stored in ciphertext. The DU generates the transformation key and the outsourced decryption key based on the generated by the STA. When outsourced decryption is performed, the OCS generates an intermediate value unrelated to the plaintext based on and the ciphertext C, which does not reveal the medical data information and the symmetric key information during transmission. The DU generates the symmetric key based on the intermediate value and . The DU continues to perform the following decryption operation to obtain the symmetric key :The DU executes the algorithm to generate the transformation key pair . It randomly selects . It calculates the transformation key and the outsourced decryption key , whereThe DU sends the transformation key to OCS. It randomly picks the constants and . It runs the algorithm and finally generates an intermediate value , where the intermediate value is not associated with the symmetric key . It computes:Finally, it sends the obtained intermediate value to the DU.It inputs the outsourced decryption keys , , and on the decryptor of the DU. Finally, it obtains by calculatingThe DU obtains the symmetric key to decrypt the medical data .
6. Performance Analysis
6.1. Data Security Analysis
6.2. Hiding Access Policy Security Analysis
6.3. Outsourced Decryption Security Analysis
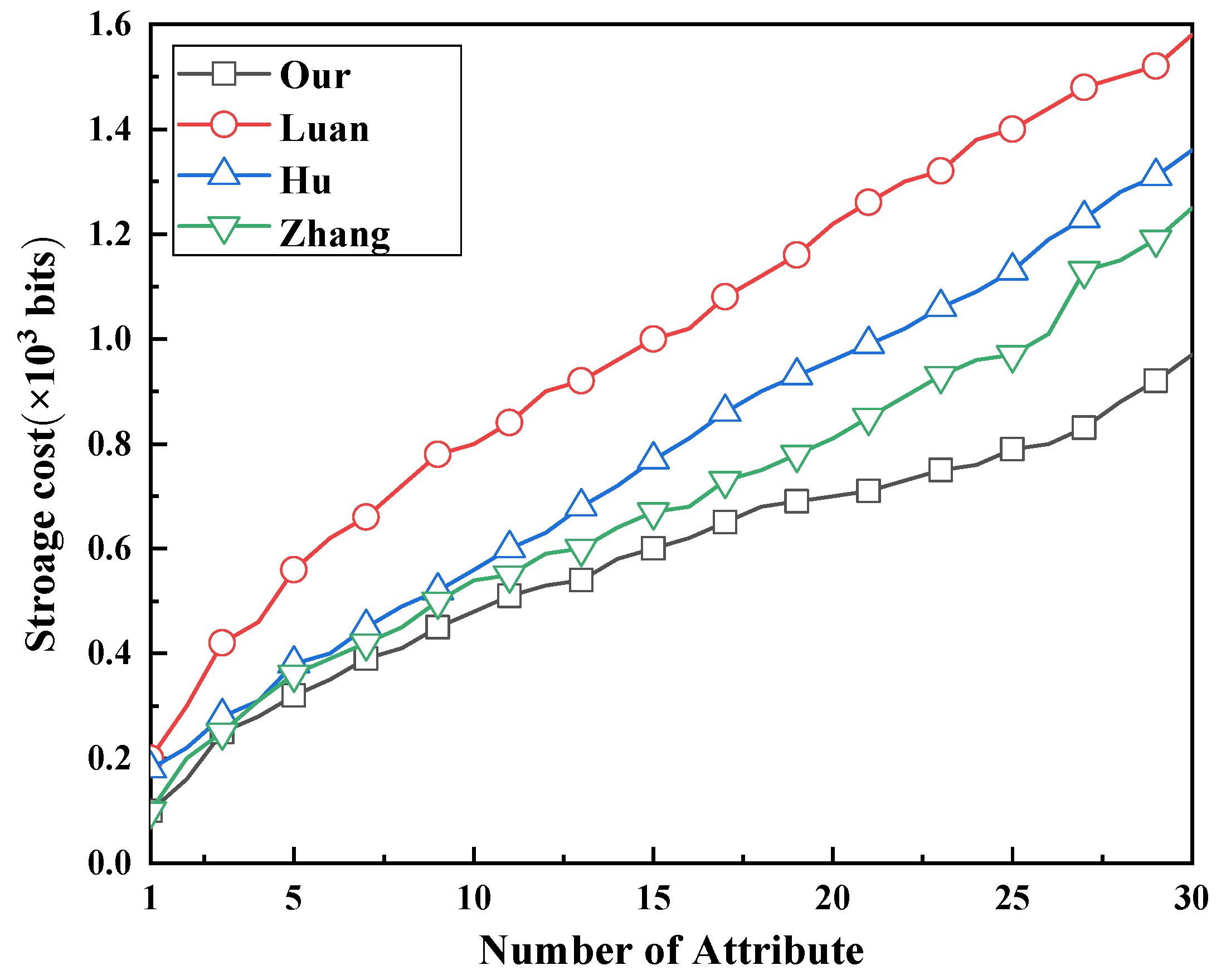
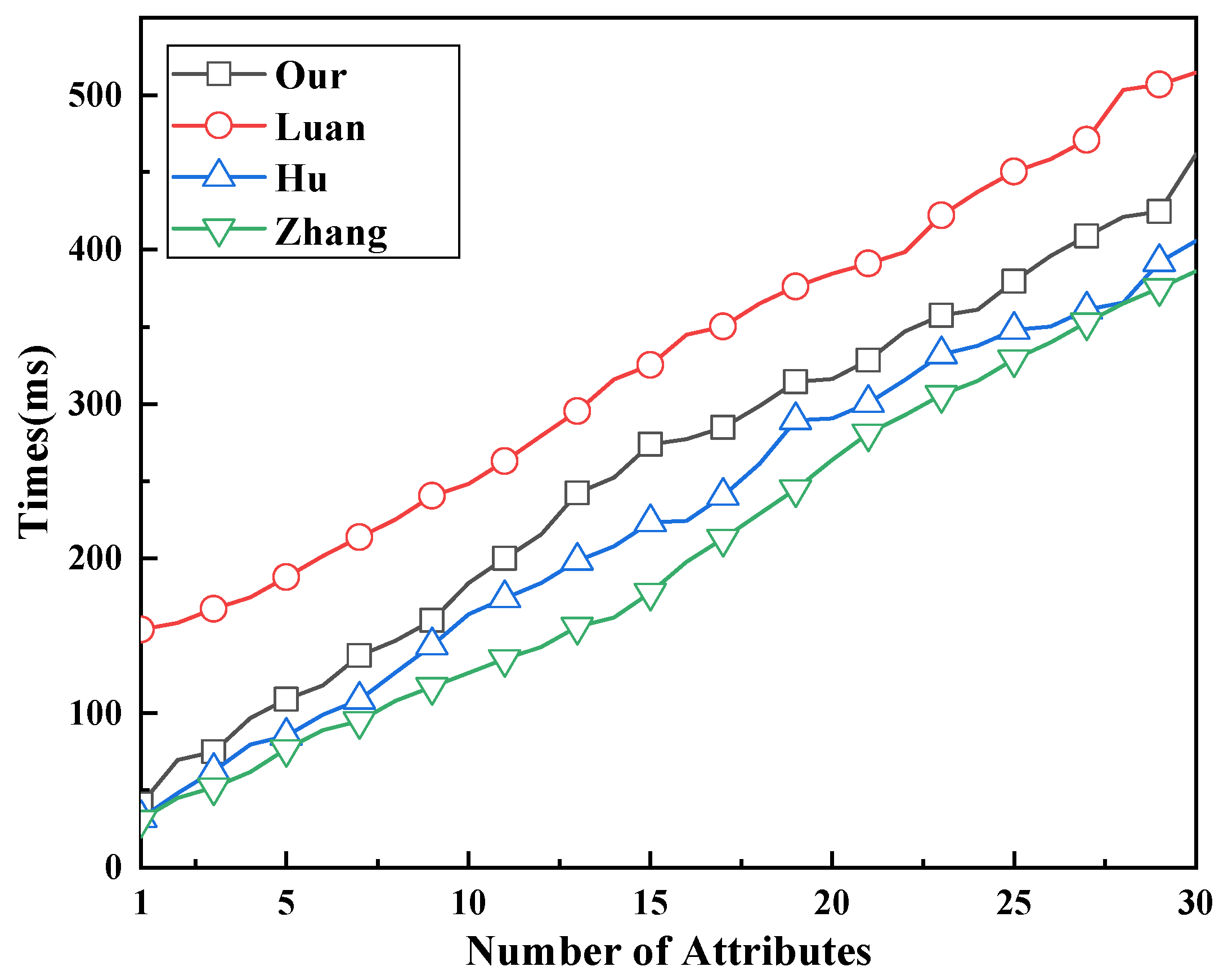
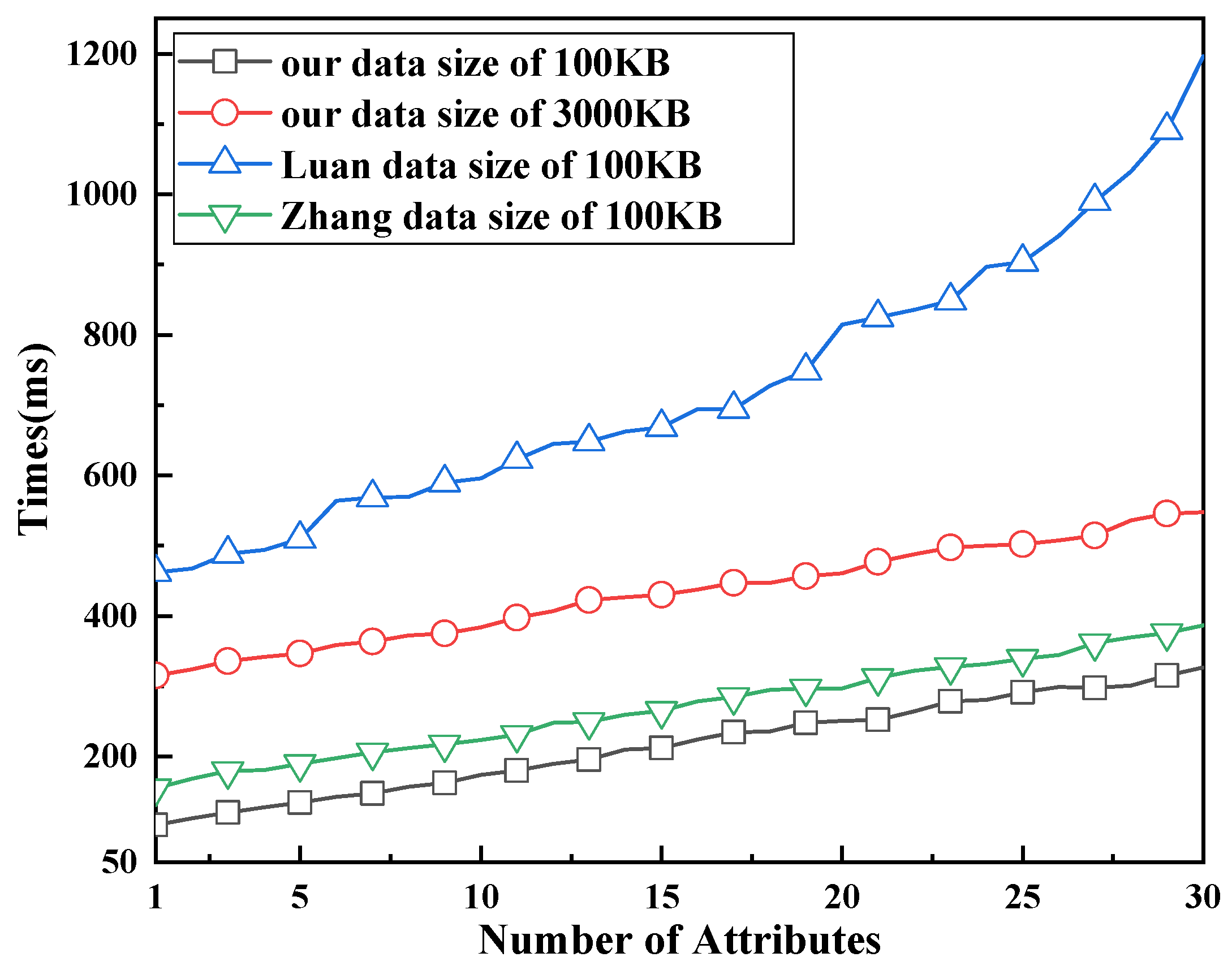
7. Experimental Analysis
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| CPA | Chosen-plaintext attack |
| ABE | Attribute-based encryption |
| ABF | Attribute bloom filter |
| DO | Data owner |
| DU | Data user |
| LSP | Local service provider |
| STA | Semi-trust authority |
| CSS | Cloud storage server |
| OCS | Outsourced cloud server |
References
- Lei, Z.; Hu, X.; Qiong, H.; Li, J.; Choo, K.R.; Li, J. Cryptographic Solutions for Cloud Storage: Challenges and Research Opportunities. IEEE Trans. Serv. Comput. 2019, 15, 567–587. [Google Scholar]
- Abouelmehdi, K.; Hssane, A.B.; Khaloufi, H.; Saadi, M. Big data security and privacy in healthcare: A Review. In Proceedings of the 8th International Conference on Emerging Ubiquitous Systems and Pervasive Networks (EUSPN 2017)/7th International Conference on Current and Future Trends of Information and Communication Technologies in Healthcare (ICTH-2017)/Affiliated Workshops, Lund, Sweden, 18–20 September 2017; pp. 73–80. [Google Scholar]
- Alshehri, S.; Radziszowski, S.P.; Raj, R.K. Secure Access for Healthcare Data in the Cloud Using Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the Workshops Proceedings of the IEEE 28th International Conference on Data Engineering, ICDE 2012, Arlington, VA, USA, 1–5 April 2012; pp. 143–146. [Google Scholar]
- Lee, Y.S.; Alasaarela, E.; Lee, H.J. An efficient encryption scheme using elliptic curve cryptography (ECC) with symmetric algorithm for healthcare system. Int. J. Secur. Its Appl. 2014, 8, 63–70. [Google Scholar] [CrossRef]
- Bocu, R.; Costache, C. A homomorphic encryption-based system for securely managing personal health metrics data. Ibm J. Res. Dev. 2018, 62, 1:1–1:10. [Google Scholar] [CrossRef]
- Yan, H.; Li, X.; Li, J. Secure Personal Health Record System with Attribute-Based Encryption in Cloud Computing. In Proceedings of the 2014 Ninth International Conference on P2P, Parallel, Grid, Cloud and Internet Computing, Guangzhou, China, 8–10 November 2014; pp. 329–332. [Google Scholar]
- Sahai, A.; Waters, B. Fuzzy Identity-Based Encryption. In Proceedings of the Advances in Cryptology–EUROCRYPT 2005, 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; pp. 457–473. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-Policy Attribute-Based Encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (S&P 2007), Oakland, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Luan, I.; Muhammad, A.; Milan, P. Secure management of personal health records by applying attribute-based encryption. In Proceedings of the 6th International Workshop on Wearable, Micro, and Nano Technologies for Personalized Health, Oslo, Norway, 24–26 June 2009; pp. 71–74. [Google Scholar]
- Liu, L.; Lai, J.; Deng, R.H.; Li, Y. Ciphertext-policy attribute-based encryption with partially hidden access structure and its application to privacy-preserving electronic medical record system in cloud environment. Secur. Commun. Netw. 2016, 9, 4897–4913. [Google Scholar] [CrossRef]
- Hahn, C.; Kwon, H.; Hur, J. Efficient Attribute-Based Secure Data Sharing with Hidden Policies and Traceability in Mobile Health Networks. Mob. Inf. Syst. 2016, 2016, 6545873:1–6545873:13. [Google Scholar] [CrossRef]
- Aljawarneh, S.A.; Yassein, M.O.B.; Talafha, W.A. A resource-efficient encryption algorithm for multimedia big data. Multim. Tools Appl. 2017, 76, 22703–22724. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, CCS 2006, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98. [Google Scholar]
- Green, M.; Hohenberger, S.; Waters, B. Outsourcing the Decryption of ABE Ciphertexts. In Proceedings of the 20th USENIX Security Symposium, San Francisco, CA, USA, 8–12 August 2011; USENIX Association: Berkeley, CA, USA, 2011. [Google Scholar]
- Imam, R.; Kumar, K.; Raza, S.M.; Sadaf, R.; Anwer, F.; Fatima, N.; Nadeem, M.; Abbas, M.; Rahman, O. A systematic literature review of attribute based encryption in health services. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 6743–6774. [Google Scholar] [CrossRef]
- Jiang, Y.; Xu, X.; Xiao, F. Attribute-Based Encryption with Blockchain Protection Scheme for Electronic Health Records. IEEE Trans. Netw. Serv. Manag. 2022, 19, 3884–3895. [Google Scholar] [CrossRef]
- Zhang, F.; Zhang, Y.; Han, G. Blockchain-based attribute-based keyword searchable encryption for health cloud system. Int. J. Embed. Syst. 2022, 15, 493–504. [Google Scholar] [CrossRef]
- Li, W.; Xu, L.; Wen, Y.; Zhang, F. Conjunctive multi-key searchable encryption with attribute-based access control for EHR systems. Comput. Stand. Interfaces 2022, 82, 103606. [Google Scholar] [CrossRef]
- Saravanan, N.; Arumugam, U. Enhanced attribute based encryption technique for secured access in cloud storage for personal health records. Concurr. Comput. Pract. Exp. 2022, 34. [Google Scholar]
- Yang, X.; Li, W.; Fan, K. A revocable attribute-based encryption EHR sharing scheme with multiple authorities in blockchain. Peer Peer Netw. Appl. 2023, 16, 107–125. [Google Scholar] [CrossRef]
- Pussewalage, H.S.G.; Oleshchuk, V.A. A Delegatable Attribute Based Encryption Scheme for a Collaborative E-Health Cloud. IEEE Trans. Serv. Comput. 2023, 16, 787–801. [Google Scholar] [CrossRef]
- Nishide, T.; Yoneyama, K.; Ohta, K. Attribute-Based Encryption with Partially Hidden Encryptor-Specified Access Structures. In Proceedings of the Applied Cryptography and Network Security, 6th International Conference, ACNS 2008, New York, NY, USA, 3–6 June 2008; pp. 111–129. [Google Scholar]
- Lai, J.; Deng, R.H.; Li, Y. Expressive CP-ABE with partially hidden access structures. In Proceedings of the 7th ACM Symposium on Information, Compuer and Communications Security, ASIACCS’12, Seoul, Republic of Korea, 2–4 May 2012; pp. 18–19. [Google Scholar]
- Xiong, H.; Zhao, Y.; Peng, L.; Zhang, H.; Yeh, K. Partially policy-hidden attribute-based broadcast encryption with secure delegation in edge computing. Future Gener. Comput. Syst. 2019, 97, 453–461. [Google Scholar] [CrossRef]
- Cui, H.; Deng, R.H.; Lai, J.; Yi, X.; Nepal, S. An efficient and expressive ciphertext-policy attribute-based encryption scheme with partially hidden access structures, revisited. Comput. Netw. 2018, 133, 157–165. [Google Scholar] [CrossRef]
- Hu, G.; Zhang, L.; Mu, Y.; Gao, X. An Expressive “Test-Decrypt-Verify” Attribute-Based Encryption Scheme with Hidden Policy for Smart Medical Cloud. IEEE Syst. J. 2021, 15, 365–376. [Google Scholar] [CrossRef]
- Gan, T.; Liao, Y.; Liang, Y.; Zhou, Z.; Zhang, G. Partial policy hiding attribute-based encryption in vehicular fog computing. Soft Comput. 2021, 25, 10543–10559. [Google Scholar] [CrossRef]
- Phuong, T.V.X.; Yang, G.; Susilo, W. Hidden Ciphertext Policy Attribute-Based Encryption Under Standard Assumptions. IEEE Trans. Inf. Forensics Secur. 2016, 11, 35–45. [Google Scholar] [CrossRef]
- Yang, K.; Han, Q.; Li, H.; Zheng, K.; Su, Z.; Shen, X. An Efficient and Fine-Grained Big Data Access Control Scheme with Privacy-Preserving Policy. IEEE Internet Things J. 2017, 4, 563–571. [Google Scholar] [CrossRef]
- Ramu, G. A secure cloud framework to share EHRs using modified CP-ABE and the attribute bloom filter. Educ. Inf. Technol. 2018, 23, 2213–2233. [Google Scholar] [CrossRef]
- Hao, J.; Cheng, H.; Ni, J.; Rong, H.; Xian, M.; Shen, X.S. Fine-grained data access control with attribute-hiding policy for cloud-based IoT. Comput. Netw. 2019, 153, 1–10. [Google Scholar] [CrossRef]
- Zhang, L.; Ren, J.; Li, K.; Wang, B. Decentralizing Multi-Authority Attribute-Based Access Control Scheme with Fully Hidden Policy. Int. J. Netw. Secur. 2021, 23, 588–603. [Google Scholar]
- Su, J.; Zhang, L.; Mu, Y. BA-RMKABSE: Blockchain-aided Ranked Multi-keyword Attribute-based Searchable Encryption with Hiding Policy for Smart Health System. Future Gener. Comput. Syst. 2022, 132, 299–309. [Google Scholar] [CrossRef]
- Kim, I.; Susilo, W.; Baek, J.; Kim, J. Harnessing Policy Authenticity for Hidden Ciphertext Policy Attribute-Based Encryption. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1856–1870. [Google Scholar] [CrossRef]
- Belguith, S.; Kaaniche, N.; Laurent, M.; Jemai, A.; Attia, R. Phoabe: Securely outsourcing multi-authority attribute based encryption with policy hidden for cloud assisted iot. Comput. Netw. 2018, 133, 141–156. [Google Scholar] [CrossRef]
- Zhang, J.; Cheng, Z.; Cheng, X.; Chen, B. OAC-HAS: Outsourced access control with hidden access structures in fog-enhanced IoT systems. Connect. Sci. 2021, 33, 1060–1076. [Google Scholar] [CrossRef]
- Lin, S.; Zhang, R.; Ma, H.; Wang, S. Revisiting Attribute-Based Encryption with Verifiable Outsourced Decryption. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2119–2130. [Google Scholar] [CrossRef]
- Bloom, B.H. Space/Time Trade-offs in Hash Coding with Allowable Errors. Commun. ACM 1970, 13, 422–426. [Google Scholar] [CrossRef]
- Rouselakis, Y.; Waters, B. Practical constructions and new proof methods for large universe attribute-based encryption. In Proceedings of the 2013 ACM SIGSAC Conference on Computer and Communications Security, CCS’13, Berlin, Germany, 4–8 November 2013; pp. 463–474. [Google Scholar]
- Saha, K.; Mani, S. Basic HealthCare Data. 2016. Available online: https://github.com/csbond007/Basic_Health_Care (accessed on 25 April 2023).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, M.; Shao, F.; Zheng, R.; Liu, M.; Ji, Z. An Efficient Encryption Scheme with Fully Hidden Access Policy for Medical Data. Electronics 2023, 12, 2930. https://doi.org/10.3390/electronics12132930
Zhang M, Shao F, Zheng R, Liu M, Ji Z. An Efficient Encryption Scheme with Fully Hidden Access Policy for Medical Data. Electronics. 2023; 12(13):2930. https://doi.org/10.3390/electronics12132930
Chicago/Turabian StyleZhang, Moli, Feijiao Shao, Ruijuan Zheng, Muhua Liu, and Zhihang Ji. 2023. "An Efficient Encryption Scheme with Fully Hidden Access Policy for Medical Data" Electronics 12, no. 13: 2930. https://doi.org/10.3390/electronics12132930
APA StyleZhang, M., Shao, F., Zheng, R., Liu, M., & Ji, Z. (2023). An Efficient Encryption Scheme with Fully Hidden Access Policy for Medical Data. Electronics, 12(13), 2930. https://doi.org/10.3390/electronics12132930





