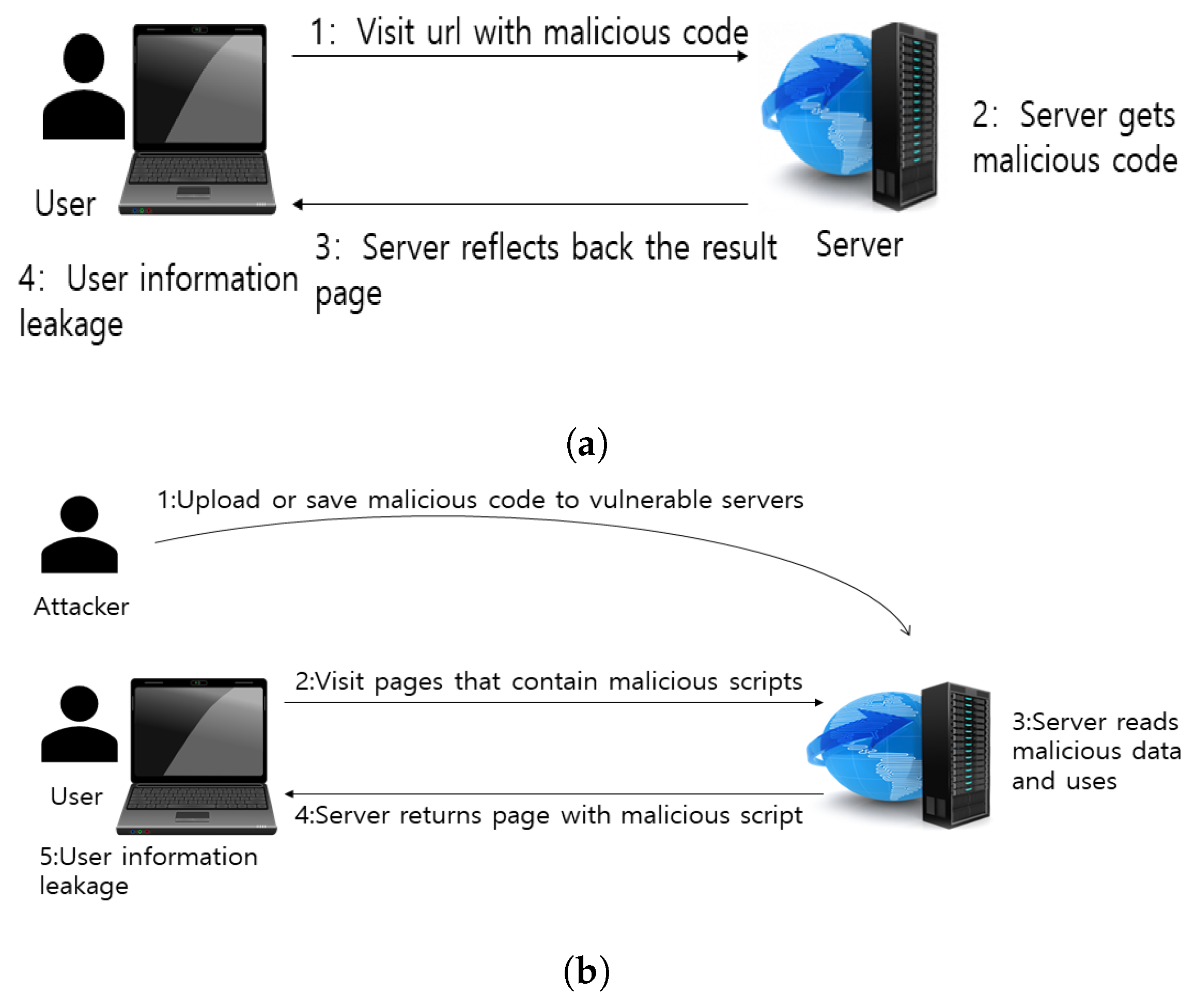
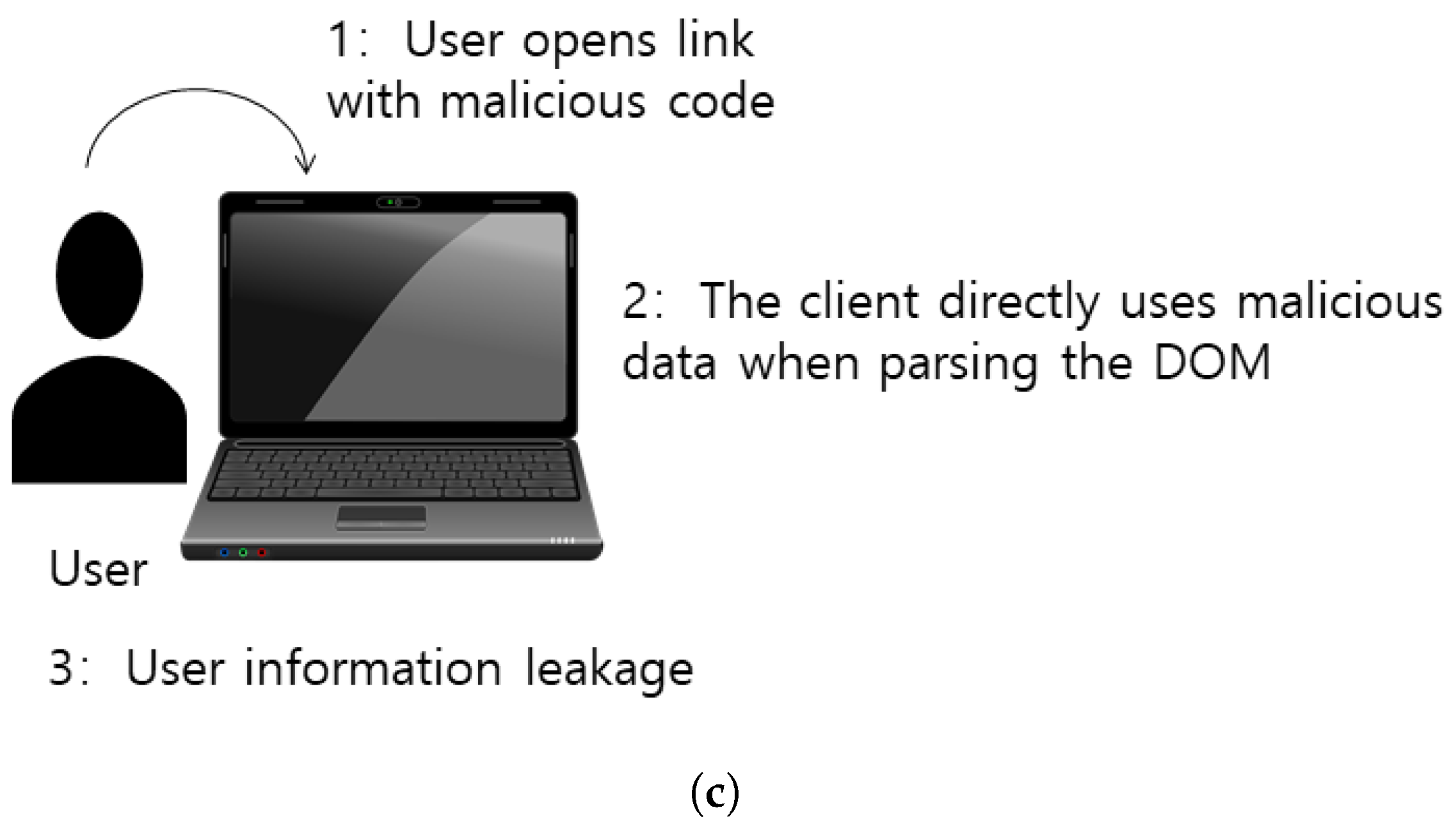
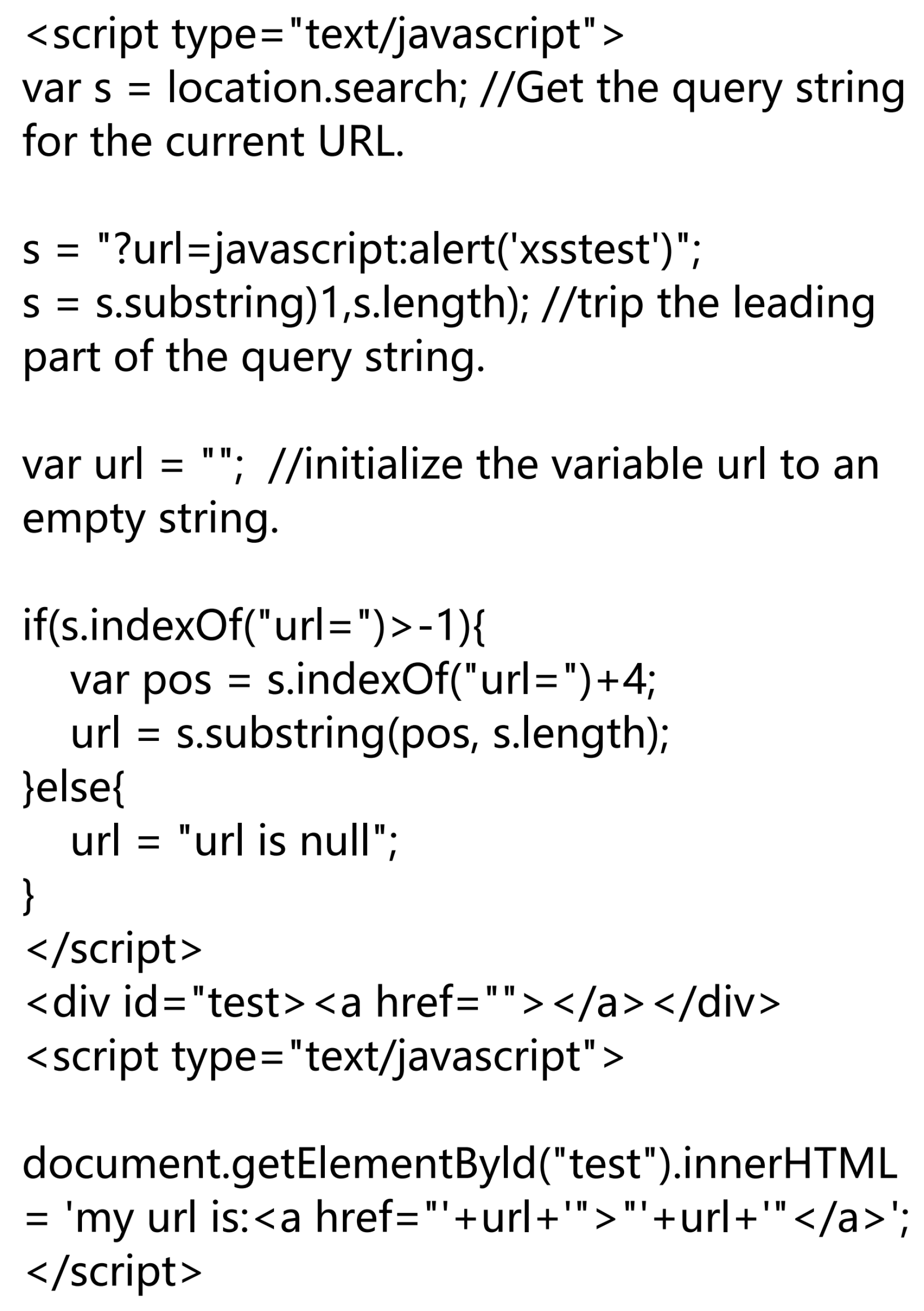
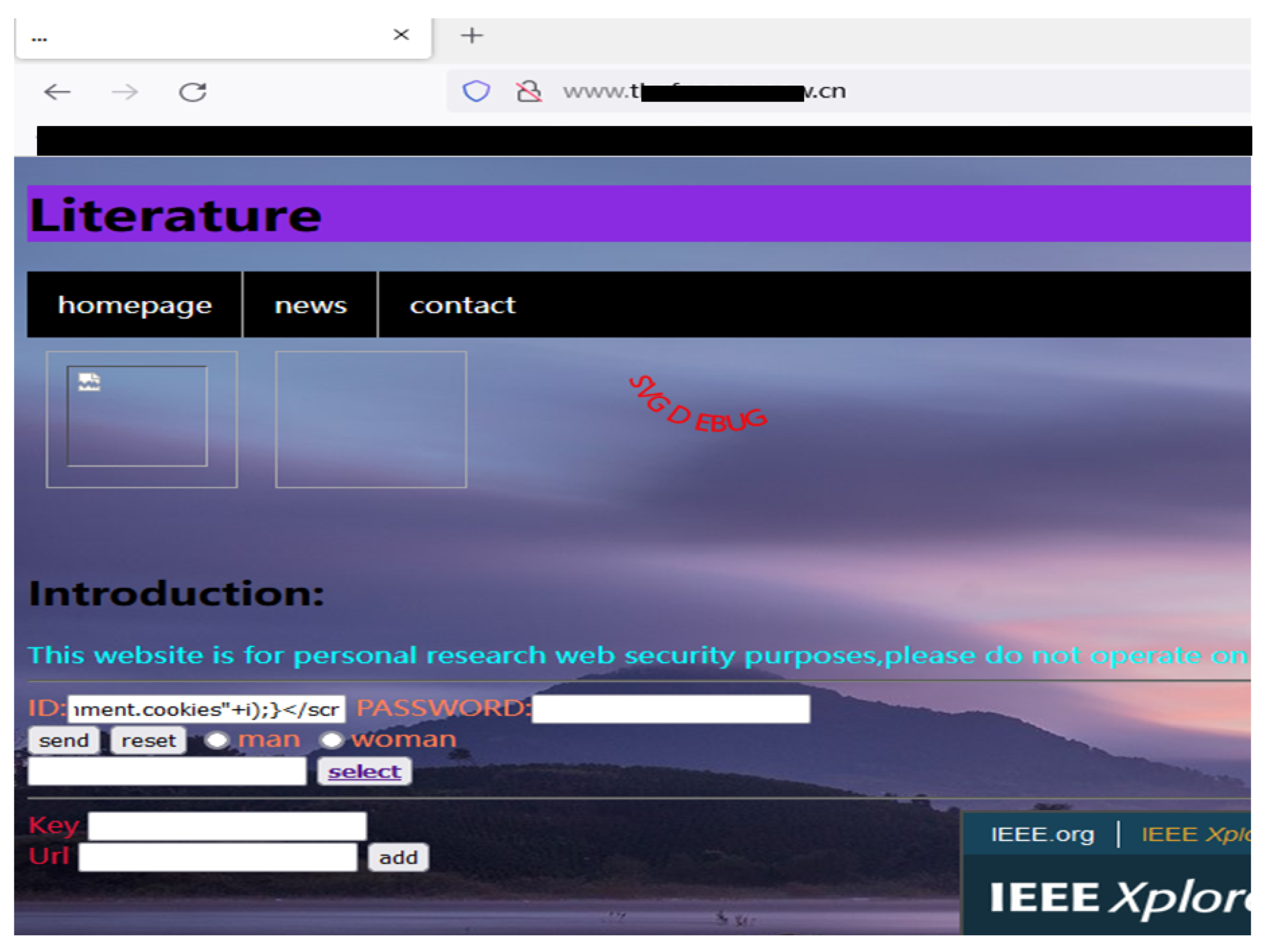
4.4. Research and Analysis
First, a risk ranking was constructed by counting the past CVE data [
31] of each framework (as of 10 January 2022) in
Table 3.
Analysis revealed that, among the Java frameworks, the most popular spring framework ranks second in terms of the number of vulnerability submissions, and the attack reports involved in the experiment accounted for 19.04% of the figure. Thus, spring framework exhibits high web security risk, and it is not suitable for programmers who lack experience in web security. In contrast, the Vert.x-Web framework with relatively few users was observed to have exhibited only one vulnerability report in recent years, corresponding to the CSRF attack. Despite this disadvantage, Vert.x-Web is the leading open-source framework in terms of web security. The framework is mostly developer-friendly as it enables decent security even in the absence of relevant expertise; several important observations were noted in the case of PHP frameworks as well. According to Google’s PHP framework ranking, Larravel and Symfony are the most used PHP frameworks by a significant margin. However, they were observed to rank second and third in terms of the number of vulnerabilities in Symfony, 23.08% of the vulnerabilities in the report were related to our experiment attack; this indicates that websites using the Symfony framework are inefficient at filtering attacks, such as XSS. We believe that CakePHP is more suitable for web developers who are proficient in PHP, but not proficient in web security.
To illustrate this argument, we conducted further research on Symfony. We configured the PHP-related filters listed in
Table 2 sequentially in the Symfony framework used in the experiment and estimated the detection rate with its twig native template [
32]. The results are depicted in
Table 4.
It is evident that even with updated twig to three versions, the rate is less than the XSS detection rate of open-source filters. However, Symfony’s twig template exhibits the best defense against SQL injection. Testing revealed that the old version of twig1.x contained reference instances such as ‘_self’=>’ this’, which could lead to the use of the ‘_self’ variable to return the /Twig/Template instance; this is indicative of the env property of the Twig_Environment, rendering it vulnerable to attack. The new version changes the role of _self, which improves security, but lacks filtering of name values, resulting in problematic code, e.g., [0, 0]|reduce(“system”, “calc”) detection can be bypassed. Thus, in web applications designed using Symfony, twig templates should be avoided or the HTML Purifier filter should be used; this is the relevant advice in this article for PHP practitioners.
As the number of risk vulnerabilities related to Java frameworks is significantly smaller than those related to PHP frameworks, comparative tests between Java’s native templates and open-source filters were omitted from this study. By
Table 3, Java is more secure than PHP in terms of web development. Next, the detection rates of open-source filters in the two languages were compared. To reduce the influence of the framework on the detection rate, Vert.x-Web (JDK8 or above) and CakePHP were used owing to high framework security. Different filters were configured into the framework. For example, the PHP-XSS-Filter was configured into CakePHP by copying its xss_filter.class.php file to the routing directory in CakePHP and adding it through the DispatcheFactory class in config/bootstrap.php. Java filters rely on Maven packages. The filter rules were not changed; meanwhile, the following testing data were acquired.
The filtering and detection results of 216 XSS codes and 248 SQL injection codes using 12 filters are depicted in
Table 5. Among the open-source filters in the Java language, the XSS HTML Filter exhibited the highest detection rate exceeding 97.69%, followed by jsoup with 97.22%. Corresponding to SQL injection, all filters used in the experiment exhibited detection rates exceeding 95%. Unfortunately, none of the current popular Java open-source filters were observed to exhibit a detection rate of 100%. In fact, the detection rate of Lucy-XSS was only 67.59%. Thus, these popular filters are not effective in defending against advanced malicious codes, and web developers should avoid using Lucy-XSS. In the experiment, Lucy-XSS filtered out the keywords of the executive function, such as alert(), but failed to filter out the payload executed by eval() plus encoding, as illustrated below:
In contrast, among the open-source filters in the PHP language, two XSS filters, PHP-XSS-Filter and PHP Anti- XSS, exhibited 100% filtering under experimental detection. The other two filters also exhibited detection rates exceeding 95%. However, the detection rate of the filters involved in SQL injection detection were low, with the lowest detection rate of 86.69% exhibited by phpClassFilter. Therefore, the filtering rules of phpClassFilter were analyzed in depth and concluded that, although it cannot be injected directly owing to its lack of filtering of SQL method functions, it can be brute-force cracked after method testing. For example, using the following payloads:
the malicious code is used to test the length of the password, which is obtained after multiple cycles. After the password length is confirmed, brute-force cracking is performed using the password dictionary.
Although almost all scripting languages provide the function of file inclusion to facilitate programming, LFI attacks primarily exist in PHP programs, which is a drawback of the language design [
33,
34]. Therefore, in this experiment, the LFI vulnerability of PHP programs was tested. As LFI vulnerabilities may arise from poor coding habits of developers, false-positive data generated by personal factors using DVWA’s LFI test were avoided. The injection test of 79 LFI codes corresponding to every level of DVWA was used to obtain the data listed in
Table 6.
Testing data indicated the absence of any filtering mechanism at lower levels, while at the medium level, the pass rate following the blacklist mechanism was only 49.36%. At a high level, the whitelist mechanism was used, yielding a rate of only 18.98%. Finally, under the whitelist mechanism at the impossible level, complete defense against exploitable LFI vulnerabilities as of February 2022 was achieved. It is evident from the open-source code of the impossible level that effective defense against LFI is not difficult. As long as the allowed PHP file is not executed, an error is reported. Therefore, although LFI vulnerability is a great threat to web programs written in PHP, relevant defense is not as complicated as that against XSS attacks. Moreover, after updating PHP to version 8.0, the string in php://filter .strip_tags is removed, which makes PHP-based web application less vulnerable to LFI.
Finally, we used the framework with the LDAP service listed in
Table 1 to perform the LDAP injection test. The LDAP rules defined in the official LDAP website [
35] were followed to obtain the following statistics on the LDAP filter types of the LDAP open-source services of different frameworks:
PresenceFilters, EqualityFilters, Greater-Or-Equal Filters, OR Filters, AND Filters, NOT Filters, Extensible Match Filters, The String Representation of LDAP Filters.
PresenceFilters, EqualityFilters, Greater-Or-Equal Filters, OR Filters, AND Filters, NOT Filters, The String Representation of LDAP Filters.
PresenceFilters, EqualityFilters, Greater-Or-Equal Filters, OR Filters, AND Filters, NOT Filters, Substring Filters, Less-Or-Equal Filters, Approximate Match Filters, The String Representation of LDAP Filters.
PresenceFilters, EqualityFilters, Greater-Or-Equal Filters, OR Filters, AND Filters, NOT Filters, Extensible Match Filters, The String Representation of LDAP Filters.
PresenceFilters, EqualityFilters, Greater-Or-Equal Filters, OR Filters, AND Filters, NOT Filters, Substring Filters, Less-Or-Equal Filters, Approximate Match Filters, The String Representation of LDAP Filters.
PresenceFilters, EqualityFilters, Greater-Or-Equal Filters, OR Filters, AND Filters, NOT Filters, The String Representation of LDAP Filters.
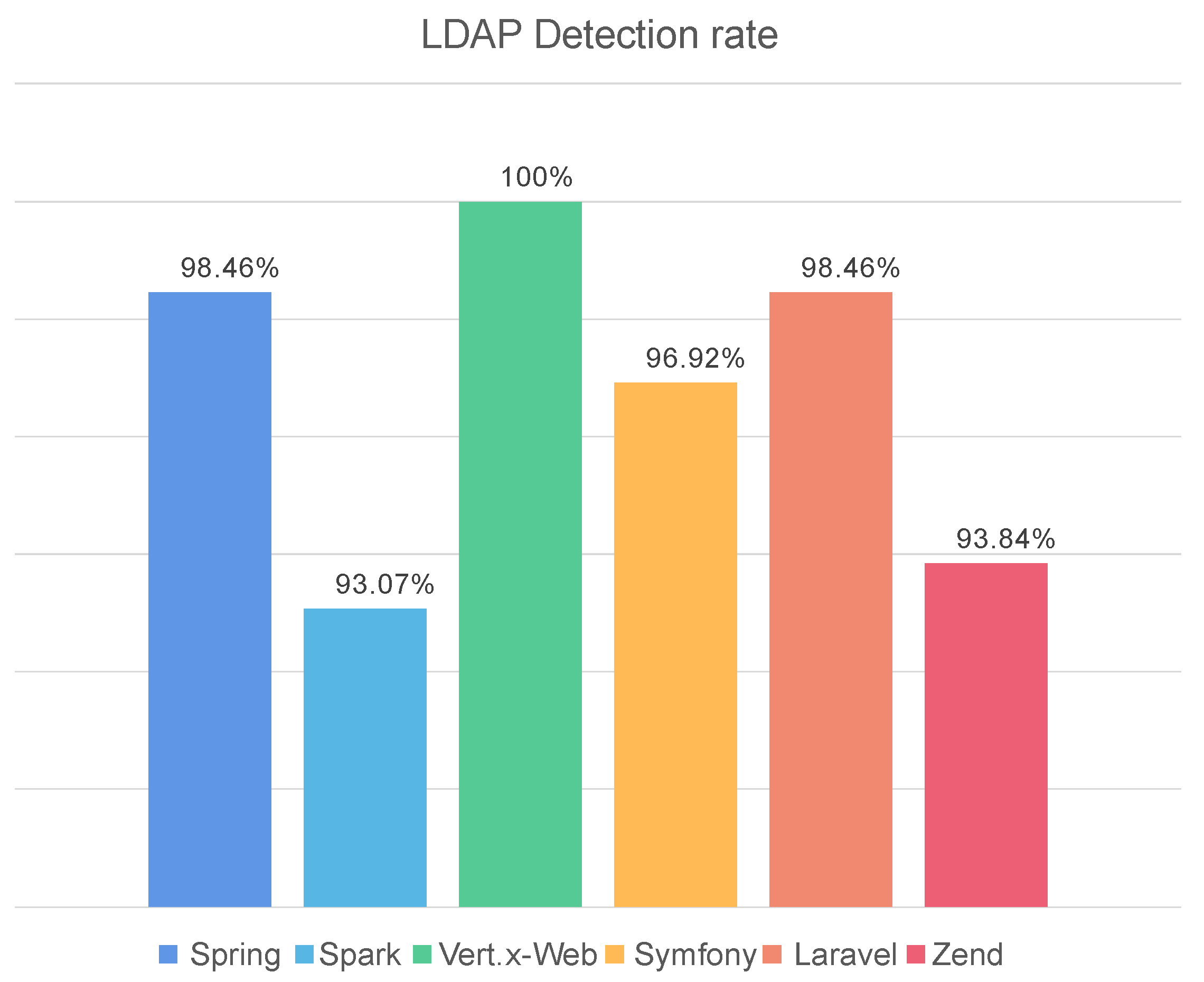
The data shown in the
Figure 5 are obtained by manually injecting 130 malicious codes, and experimental results revealed that among the popular frameworks with LDAP services, only Vert.x-Web-related filtering mechanism completely filtered the malicious code used in the experiment. In terms of effectiveness, it was followed by PHP-based Laravel and Java-based Spring, which exhibited a detection rate of 98.46% and only allowed two malicious codes to pass. The detection rates of Laravel and Spring were equal, but they have different LDAP filtering mechanisms. Some filtering mechanisms may be particularly important, while others could have little effect. Thus, only six types of filtering mechanisms were retained—Presence Filters, Equality Filters, OR Filters, AND Filters, NOT Filters, and Substring Filters—and they were repeatedly tested. The detection rate of Spring was observed to be 95.38% and that of Laravel was 94.61%, which were almost identical to those of other open-source projects, except for Vert.x-Web; this indicates that some filtering mechanisms are particularly important for defense against LDAP attacks. This indicates that expertise in the effects of different filtering mechanisms and the most suitable filtering positions is essential in security personnel. The difference in detection rates between identical filtering mechanisms was attributed to the filtering range within the mechanism, which depends on the professional capacity of the developer. The security analysis of open-source web software has been presented, and security suggestions have been proposed for web developers using open-source projects. In turn, advice to maintain web security and improve the detection rate is presented in this study.
In the aforementioned experiments, the effect of both PHP- and Java-based filter mechanism were better in case of whitelisted ones than blacklisted ones. However, in practical filters, prevention of the transmission of malicious code must coexist with the transmission of normal code [
36]. For example, if the <img> tag is added to the blacklist, users will be blocked from uploading images freely, while if it is added to the whitelist, it will become an injection point for further processing. To make the experimental results more obvious, Lucy-XSS and PHP-Anti-XSS were selected using the whitelist mechanism and PHP-XSS-Filter using the blacklist mechanism, and manually entered 100 benign codes, such as <img src=’picture’>, into the system. The transmission rate test was carried out, and the results are listed in the following
Table 7.
The results indicated that, although the detection rate of Lucy-XSS was low, its transmission rate for benign codes was close to 100%. However, the detection rate of PHP-Anti-XSS was 100%, but benign codes were almost completely filtered out. In actual web applications, allowing free inputs by users is nearly impossible. The transmission rate of PHP-XSS-Filters was 60%—thus, it is the most suitable open-source filter for actual web applications. To improve the transmission rate of this filter, some contents of the PHP XSS filters blacklist were altered to a whitelist. However, this strategy failed as the priority of the blacklist is higher than that of the whitelist [
37], and consequently, even when previously blacklisted content is whitelisted, the blacklist still takes precedence. Conversely, if the content in the blacklist is deleted directly, the detection rate falls short of 100%. For example, deleting the case check causes ‘.php’ and ‘.PHP’ to generate file parsing errors and form an attack vulnerability. From this perspective, it is not advisable to improve the filter performance using blacklist mechanisms with a 100% detection rate. Next, we attempted to improve the performance of Lucy-XSS and PHP-Anti- XSS using the whitelist mechanism. The blacklist and whitelist mechanisms of PHP-Anti-XSS were opened, and the test results were compared when only the whitelist mechanism was opened. The results are presented in
Table 8.
The test results reveal a transmission rate of 8% and a detection rate of 100%. Therefore, when a whitelist mechanism is used to achieve a 100% detection rate, the use of a blacklist does not affect its detection rate of malicious payloads. However, it may have a negative impact on the transmission rate of benign payloads.
Motivate by the excellent transmission rate for benign payloads and weak detection rate for malicious payloads of the Lucy-XSS filter, the experimental results of the experiments filters were compared, and corresponding code analysis. It is assumed that tag elements such as <img>, <a>, <button> cannot be placed on the blacklist because this would restrict the relevant embedded elements and attributes greatly, degrading the transmission rate for benign payloads. Elements capable of carrying malicious payloads, such as attribute elements, should be blacklisted or screened. To establish this, a simple blacklist was added to the Lucy-XSS filter, add all attribute elements such as ‘href’ in the whitelist, to the blacklist. The results were as expected—the detection rate of the Lucy-XSS filter increased to 100%, but its transmission rate decreased to 74%. It was found that most of the benign payloads that were not transmitted were <a href=""> and <img src=>. However, most users use image and link functions. To resolve these disadvantages, ‘src’ and ‘herf’ were re-labeled and inserted back into the whitelist, ‘http://’ was added to the content after ‘herf’, and a strip_tags() function was processed after the ‘src’ element, so that the elements in it can only return such as ‘png’. The code is given in
Figure 6. After re-testing, the detection rate of malicious payloads was observed to be 100%, and the transmission rate of benign payloads was 96%, which satisfies the expectations of our experiment. It is important to indicate that this detection rate is affected by the experimental environment and has limitations. This method to has not yet been applied to other open-source filters, and the difference in payloads will also lead to fluctuations in the detection rate, but the two-way improvement of the filter is certain.