1. Introduction
The Global Positioning System (GPS) [
1] has been successfully applied in outdoor environments with high positioning accuracy in practice. In general, GPS technology mainly relies on the propagation of signals through the air. However, when encountering complex buildings (such as supermarkets, commercial centers, hospitals, airports, etc.), signal transmission is easily subjected to interference from plenty of uncertain factors. Weak reception of signals, lack of line of sight between users and satellite, radio multi-path effects, as well as dispersal and fading in indoor environments all contribute to the poor indoor performance of GPS. As a result, GPS is not suitable for indoor positioning. Furthermore, thermal techniques on Wi-Fi [
2], Bluetooth [
3], RFID [
4], and magnetic fields [
5] are capable of realizing superior positioning effects in indoor environments, promoting the application of a wide number of indoor positioning systems (IPS) [
6]. Wi-Fi-based IPS, in particular, has become one of the most practicable approaches because of the widespread availability and ease of deployment of Wi-Fi infrastructure [
7].
The IPS based on Wi-Fi can generally be divided into two categories [
8]: trilateral measurement algorithms and fingerprint-based location algorithms. The trilateral measurement algorithm calculates the distance between the target and the access point (AP) through time of arrival (TOA), time difference of arrival (TDOA), angle of arrival (AOA), and radio wave propagation model (RPM). Such schemes are strongly dependent on complex transmitters and receivers [
9], making them difficult to implement on every Wi-Fi device. In contrast, a fingerprint-based location method is a classic scene analysis algorithm with broad applicability that does not require precise access point position or additional investment in infrastructure and line-of-sight measurement.
A positioning system based on fingerprints is often composed of two stages [
10]: the offline training stage and the online positioning stage. In the training stage, some points with known locations are first selected as training points, and then RSSI data are collected from APs detected at each training point. Therefore, the fingerprint of each training point is made up of these RSSI vectors. In general, we always train the RSSI vectors, and the trained vectors are utilized as RP fingerprints. All fingerprints are stored in a database for online localization. In the online stage, RSSI vectors are collected at the corresponding location and transferred to the back-end server. Subsequently, the back-end server matches the received online RSSI vectors with the stored fingerprints to obtain a set of RPs with fingerprints close to the online received RSSI vectors, thereby estimating the target. The fingerprint database is the key to the RSSI-based method. However, in complex indoor scenes, various noise characteristics such as interference, reflection, and refraction can affect signal transmission, resulting in spike noise during RSSI signal acquisition. This actually cannot fully ensure the accuracy and authenticity of data collection in the fingerprint database.
By reason of the foregoing, to improve the accuracy of the fingerprint database and online RSSI vectors with noise reduction, we use JRPCA to train offline fingerprints and online RSSI vectors. The online matching stage often requires traversing the entire fingerprint database, which leads to resource consumption, as well as matching some more distant reference points, increasing the localization error. An efficient clustering strategy is proposed, which divides offline fingerprint data into multiple clusters, and further uses the localization algorithm to find the cluster where the target is located. Finally, the final location is estimated for the user within the potential clusters.
This article is an extension of our conference paper accepted by ICDH2022. In our previous work, the HCS-based clustering method was used to solve the problem of search overhead; however, it did not consider the problem of the existence of boundary point localization in real scenarios. In addition, we also discuss and analyze the proposed method in more detail in this paper and add more test experiments based on real scenarios, aiming to indicate the superiority of the proposed method.
The main contributions of this paper can be summarized as follows:
The JRPCA model is proposed, which enhances the low-rankness of the fingerprint database using the prior knowledge of singular values to make the data more accurate and thus improve the localization accuracy;
An effective fingerprint clustering strategy is proposed to reduce the search overhead and radio map size by integrating similar RSSI patterns. A reasonable subset of RPs is obtained adaptively on the basis of predefined RPs to further increase the differences between similar fingerprints.
The rest of this article is organized as follows. We review the related work in
Section 2.
Section 3 gives an overview of the system and describes the associated processes.
Section 4 details the algorithms used in this paper, the JRPCA model optimization algorithm, the one-way hierarchical clustering algorithm, and the localization algorithm. The experiments and the corresponding experimental results are introduced in
Section 5. Finally,
Section 6 summarizes the whole paper.
2. Related Work
This section displays a brief introduction of some relevant studies on indoor location based on the fingerprint. Bahl and Padmanabhan [
11] created the first WLAN-based indoor localization system, Radar, and adopted the Euclidean distance to select a few nearby RPs to estimate the location of target points. It should be noted that random noise was not taken into account in their work. Horus employed the probability distribution histogram of each RP in the offline training phase for further position prediction based on the signal’s probability distribution [
12]. Chai and Yang [
13] developed a relatively coarse calibration-based technique for estimating signal intensity using an interpolation function. Some studies focus on fingerprint training to enhance accuracy. Youssef et al. [
14] developed a MaxMean approach to construct the fingerprint database, which helps to pick several strongest APs in the offline stage that can cover the full localization region. Despite the ability of such a strategy in intensifying the robustness of an offline fingerprint database, it excludes unusual occurrences during the online phase.
On the other hand, a variety of clustering techniques have been put out to address the issue of the huge demand for fingerprint storage. One of these is the k-means clustering method [
15], which divides the entire wireless map into
k clusters by a recursive approach. The advantage of low calculation cost has advanced its extensive use in fingerprint localization. Such systems based on k-means clustering, however, fall short of providing perfect localization accuracy, as the random selection of initial cluster members or samples increases the risk of incorrect cluster selection. To increase the localization accuracy by overlapping between clusters produced by the k-means algorithm, two types of enhanced clustering technologies have been proposed [
15]: the multiple nearest neighbor (MNN) overlap clustering strategy and the Voronoi (VRN)-based overlap clustering strategy. Although both overlapping strategies are superior to the k-means strategy in terms of localization accuracy, the resulted in higher calculation complexity still cannot be ignored, as shown in [
16].
Unlike the k-means clustering technique, affinity propagation (AFP) clustering [
17] can acquire the ideal cluster head and its related cluster by iteratively transferring two types of information between data points. It has been widely employed in numerous fingerprint systems. AFP clustering does not require a certain number of clusters to be generated, nor does it require a random selection of samples as input. Nevertheless, when applied to datasets with complex structures, the negative Euclidean distance [
18] between samples and individual data points, as a measure of similarity, can dramatically impair the effectiveness of such clustering. Another approach for forming training location clusters based on AP virtual locations was proposed in [
19] for fingerprint-based indoor localization. However, this clustering technique performs best in indoor conditions without linear limitations. The hierarchical clustering strategy (HCS) proposed by [
20] partitions the fingerprint data into a set of non-overlapping clusters. Each cluster contains the training positions that receive the strongest signal from a certain number of APs, which are organized by hierarchical level definitions to form a fixed sequence. Therefore, the number of clusters created by HCS is easily determined based on the number of APs deployed in the localization region and the hierarchy level selected by [
20].
Specifically, compared to k-means clustering and the two overlapping strategies shown in [
15], the HCS method assigns a unique ID to each formed cluster based on the order of the strongest signals provided by the AP, thus greatly reducing the search overhead and localization errors. On this basis, we propose a two-phase fingerprint-matching algorithm of JRPCA based on clustering, which uses the JRPCA model to further compress the fingerprint database by training the fingerprints through the augmented Lagrange multiplier (ALM) algorithm [
21].
3. System Framework
We first establish some fundamental symbols to clearly depict the system framework. In the positioning area, suppose there are n APs and N RPs. The APs’ location, transmission power, manufacturers, and owners are not needed to be known. The location of RP
is
, and suppose that all APs can be detected at RP
. We measure the RSSI signal multiple times at each RP, and the average of the RSSI signals collected at each reference point is taken as the fingerprint of that point. Suppose that the fingerprint of RP
is
, where
is the RSSI collected from
. All RPs’ locations form the location dataset
, and all RPs’ fingerprints denote
. The offline fingerprints database consists of reference point location and its corresponding RSSI value, where the structure is
.
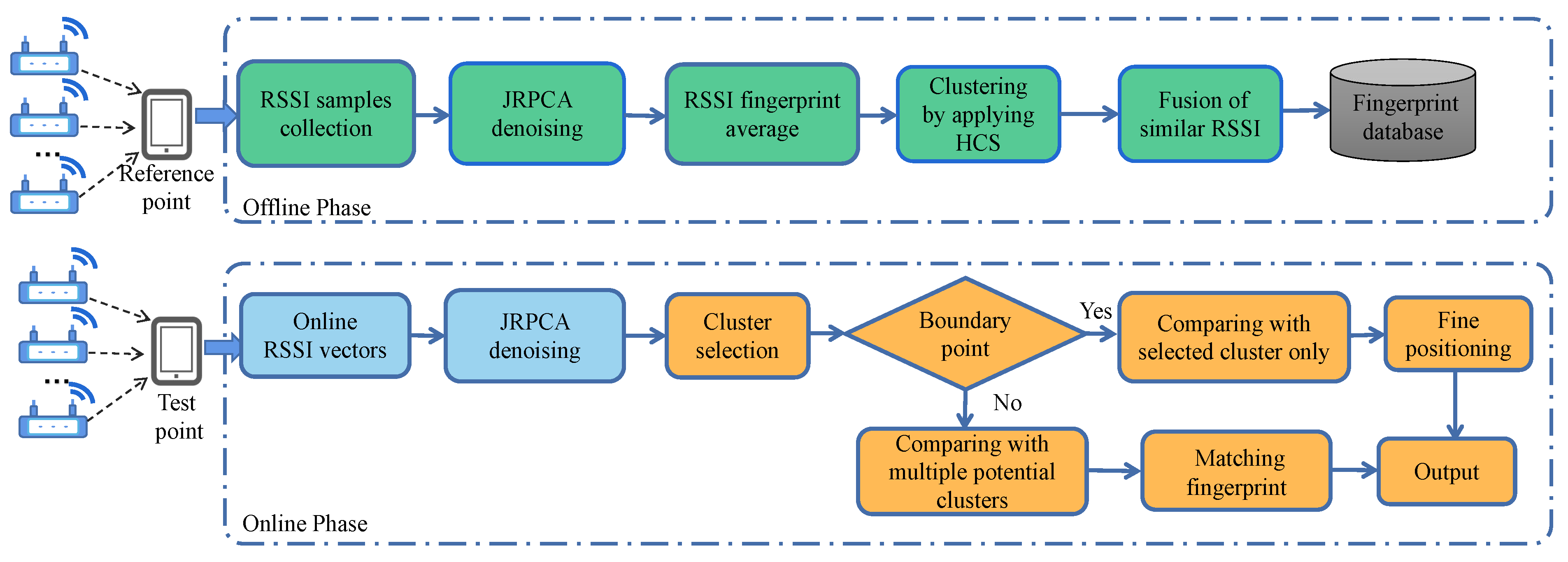
The proposed Wi-Fi fingerprint localization system adopts a robust noise suppression technique and an efficient clustering method for location estimation in two stages. The framework of the localization system is shown in
Figure 1. In the offline phase, the sparse peak noise of the fingerprint database is reduced by the JRPCA model after the fingerprints are collected. The denoised fingerprints are then clustered to reduce the subsequent search overhead by integrating similar RSSI patterns. The offline fingerprint database is constructed by denoising and clustering processes for online matching. In the online phase, online fingerprints are constructed by the same denoising process. After processing the offline fingerprint database and online fingerprints, suitable clusters are matched based on the strongest signal received from the AP by the online fingerprints. Finally, the WKNN algorithm is used to estimate the position of the target point in the selected clusters. The detailed design and working methods of the noise suppression technique, clustering strategy, and localization technique of the fingerprint system proposed in this paper are given in
Section 4.
4. Positioning Algorithm
4.1. JRPCA in Offline and Online Phase
In this section, we first introduce the limitations of the RPCA [
22] model for training fingerprints. Then, the JRPCA is proposed and the details of solving the JRPCA model by ALM in the offline phase are shown.
4.1.1. RPCA Noise Reduction Optimization Model
Let
be the offline fingerprint database constructed by n APs and N RPs,
be the reconstructed database, and
be the noise. The RPCA model can be represented as
The problem is to reduce the peak noise
and reconstruct robust
:
where
is applied to force
to be sparse, and the parameter
(
) controls the tradeoff between rank
and
.
Due to the non-convex and non-smooth properties of rank and
in optimization, in general, the problem is converted into solving a convex optimization problem. Then (3) is transformed into
where
is a convex hull of
over the set
. Therefore, (4) is convex with a unique minimum value.
4.1.2. Fingerprint Database Reconstruction Based on JRPCA
Here, we propose JRPCA to improve the fingerprint noise and make the data more accurate, thus improving the positioning accuracy.
The nuclear norm
assigns equal and constant threshold values to all singular values of the matrix, ignoring the different data characteristics represented by different singular values in the matrix. Thus, the concept of weighted is introduced in the nuclear norm optimization model. Relative to the
-norm, the
-norm can produce row (or column) based sparsity, thus improving the model by using the
-norm. In this way, the robustness of the model has been enhanced while ensuring no excessive data loss. On this basis, a JRPCA model based on the weighted nuclear norm and
-norm is constructed to recover the low-rank matrix of the original data. The model is shown as follows:
where
refers to the weight of noise and is a known quantity.
The ALM method is used to solve the JRPCA model in this paper. The solution procedure and the block diagram of the algorithm are described in detail in the next subsection.
4.1.3. Model Solution
In this section, the ALM method is adopted to solve the proposed model, which solves the constrained optimization by transforming it into an unconstrained optimization problem. To solve the proposed optimization problem by using ALM, we introduce the preliminary definitions and theorems as follows:
Shrinkage Operator: For any
and
, the shrinkage operator
is defined as
Soft-thresholding Operator: For any
and
with a singular value decomposition
, the soft-thresholding operator is
For any
and
, the shrinkage operator is the optimal solution of the function as
For any
and
, the soft-thresholding operator is the optimal solution of the function as
To solve the optimization problem, we first convert the constrained optimization problem into an unconstrained optimization problem by introducing a Lagrangian multiplier
Y and a quadratic penalty term and then formulating the augmented Lagrange function as follows:
where
Y is a Lagrange multiplier,
is a positive scalar, and <
> is an iterative procedure.
The alternating direction method is used to iterate (10), update the matrices and , and loop the algorithm to the termination criterion. The updating process is shown as follows.
- 1.
Fix
,
Y,
, that is, when
, iteratively update
.
- 2.
Fix
,
Y,
, when
, the matrix
in (10) is iteratively updated to obtain:
- 3.
When the matrices
and
converge, i.e.,
and
, the matrices
Y and
in Equation (
10) are updated iteratively:
The iterative update of
Y is obtained from Equation (
13) as:
where the iterative update of the positive penalty coefficient
is:
- 4.
The selection of the weight vector
W(
) is the key to the solution. The unknown weight vector
W can be obtained by updating the matrix
. In the matrix, the information of the data represented by the large singular value is more reflective of the important components of the data compared to the small singular value. Therefore, the contraction range of the small singular values can be increased and the contraction range of the large singular values can be decreased to retain the important information in the data. Thus, the singular value
is inversely proportional to the weight vector
W:
where
is a constant, and
ensures that the weights can still be calculated when
is 0.
Based on the above discussion, the complete JRPCA algorithm (Algorithm 1) flow is presented here, as shown below:
| Algorithm 1: JRPCA Algorithm |
Intput: data matrix , parameter , . Initialize:, , , Whiledo Calculate the weight when solve use when solve use Update Update to Output: |
4.2. Proposed Clustering Strategy
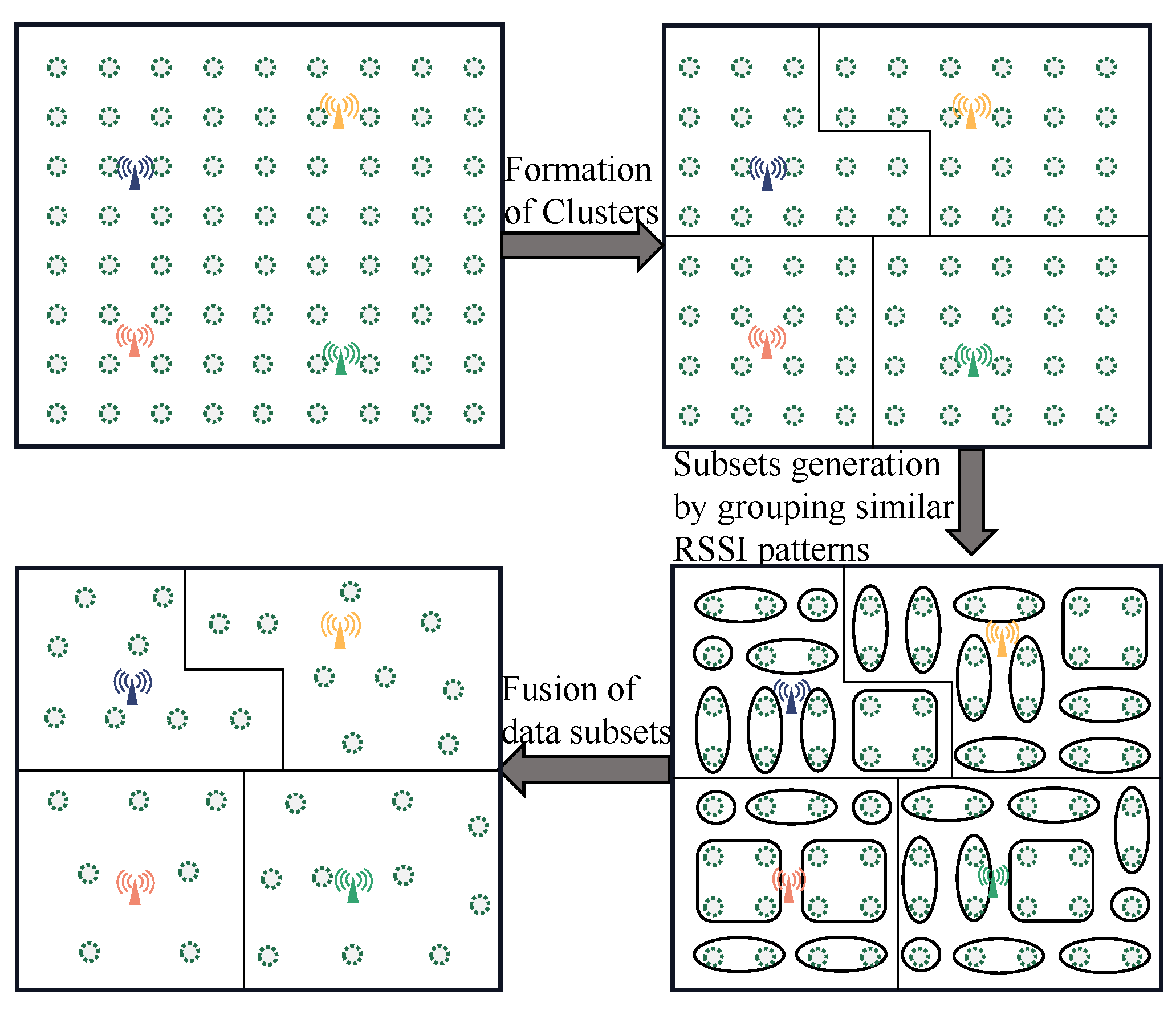
The fingerprint clustering technique proposed in this paper is divided into three main steps. The radio map is first separated into several distinct clusters by the one-way hierarchical clustering strategy’s basic operating concept (one-way HCS). The norm is that only the strongest RSSI from a particular AP is sent to the collection of training locations that make up a cluster. Although the RSSI samples measured by a specific AP at a location fluctuate over time, the RSSI values collected by the same AP are spatially correlated. Therefore, the number of clusters created is equal to the number of APs deployed in the location area. Second, the Euclidean distance between any pair of RPs belonging to the same cluster is calculated, and then subsets are generated by fusing RPs whose distance is within a certain range (called threshold). Finally, a representative RSSI vector for each subset in each cluster is calculated. The RPs with similar RSSI in the same subset are fused on average to obtain a new RP representing the subset. Combining our proposed noise reduction algorithm with this clustering strategy, a two-phase fingerprint matching algorithm of JRPCA based on clustering is proposed to further increase the difference between similar RPs and thus improve the localization accuracy.
The whole working process when applying the clustering technique of this paper to the localization region of the 4 APs is shown in
Figure 2. Either only one RP or multiple RPs are included in each generated subset. The introduced new parameter threshold (denoted as
) sets the upper limit of the Euclidean distance between each pair of RSSI-similar reference points that can be classified as a subset of the same cluster. After fusing the RPs of each subset, the fingerprint database construction is completed. The fingerprint of each subset comprises a representative RSSI vector of that subset and the location coordinates of all points in the subset. The RSSI of all reference points of the subset (such as
kth subset in
ith cluster) and their position coordinates are averaged and fused separately to obtain the representative RSSI vector. The estimation results of the representative RSSI vector
and location coordinates
of the subsets are shown below:
where
b is the number of reference points within
kth subset in the cluster
, and the set of RSSI computed at those b reference points are denoted as
.
where
denotes the positional coordinates of
b training locations within
kth subset in the cluster
.
As shown in
Figure 2, after applying one-way HCS clustering, an important issue is how to choose the initial training location to start the data fusion process within each cluster. In order to divide each cluster into the optimal number of subsets, the strategy we propose uses the RP with the largest RSSI value obtained by AP as the starting point of the data fusion process within the cluster. Formally, for the
ith cluster (
), the RP with the largest RSSI obtained from AP
i (strongest AP for cluster
) is used as the initial data point, and then the fusion process starts. Compared with other clustering techniques, this clustering technology greatly reduces the storage requirements of radio maps and the search overhead in the localization phase, and is known as an efficient clustering technique.
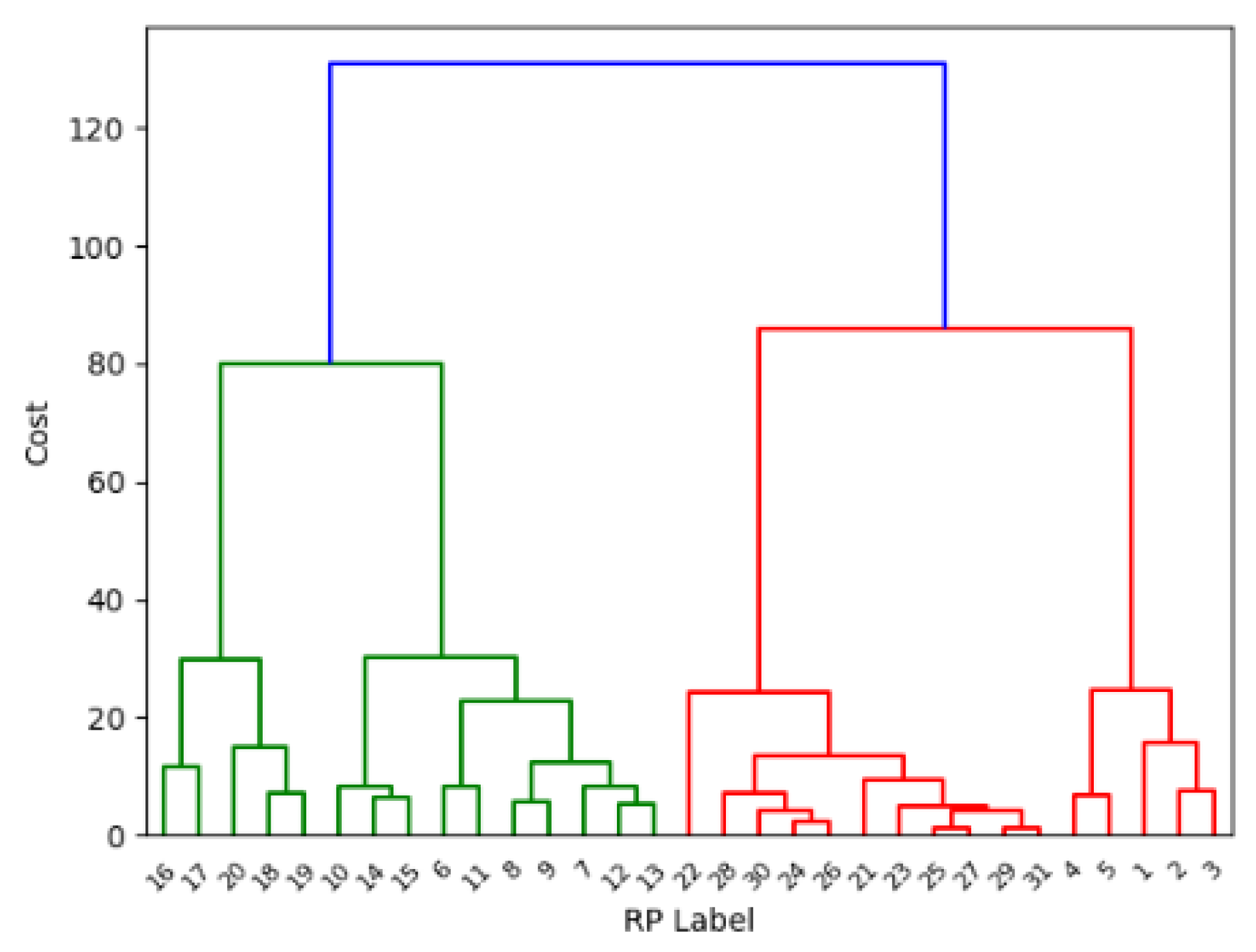
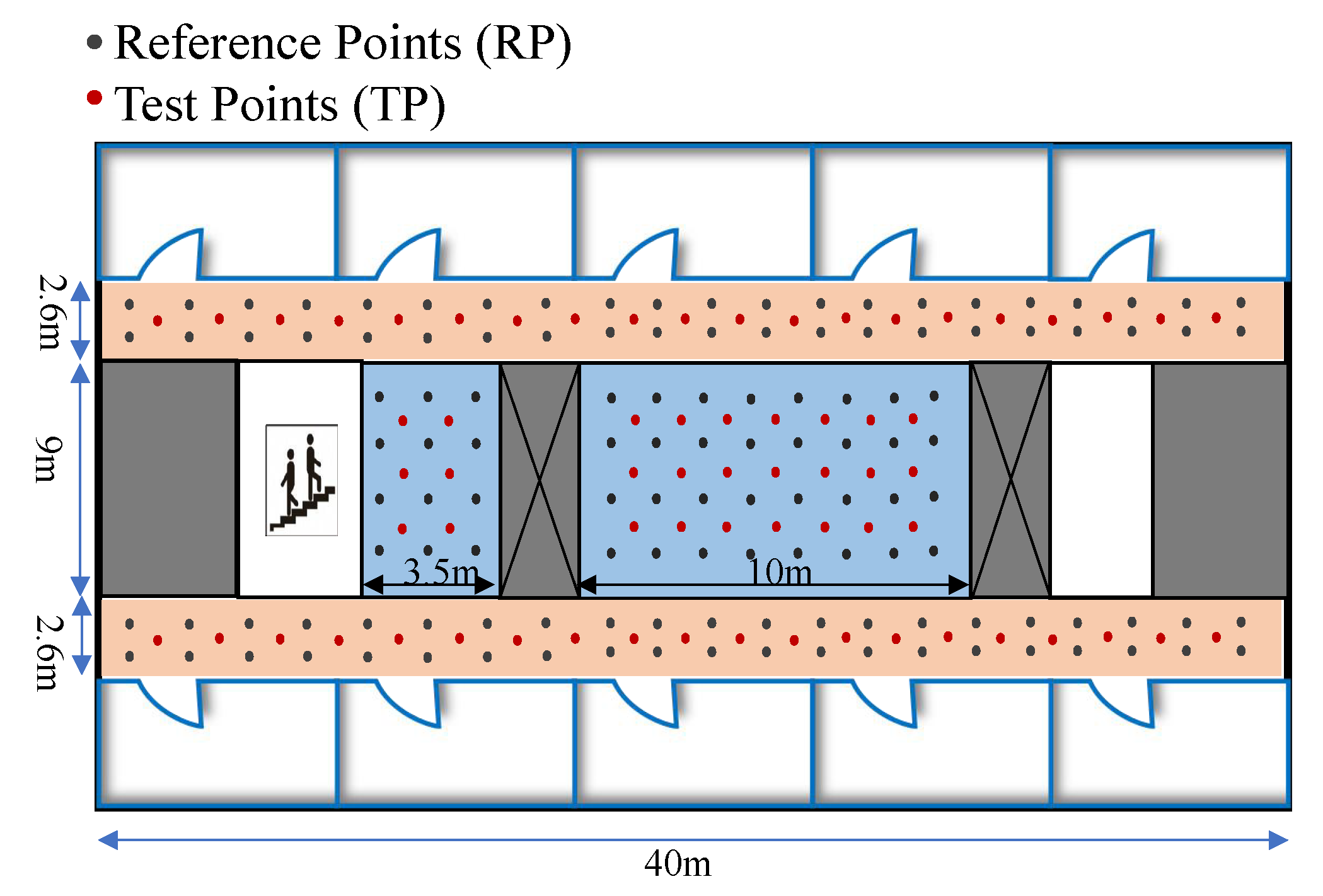
Figure 3 details the process of the designed clustering method. In the offline phase, all the pre-defined RPs are divided into clusters, and the cluster with the smallest distance is iteratively integrated into a new cluster.
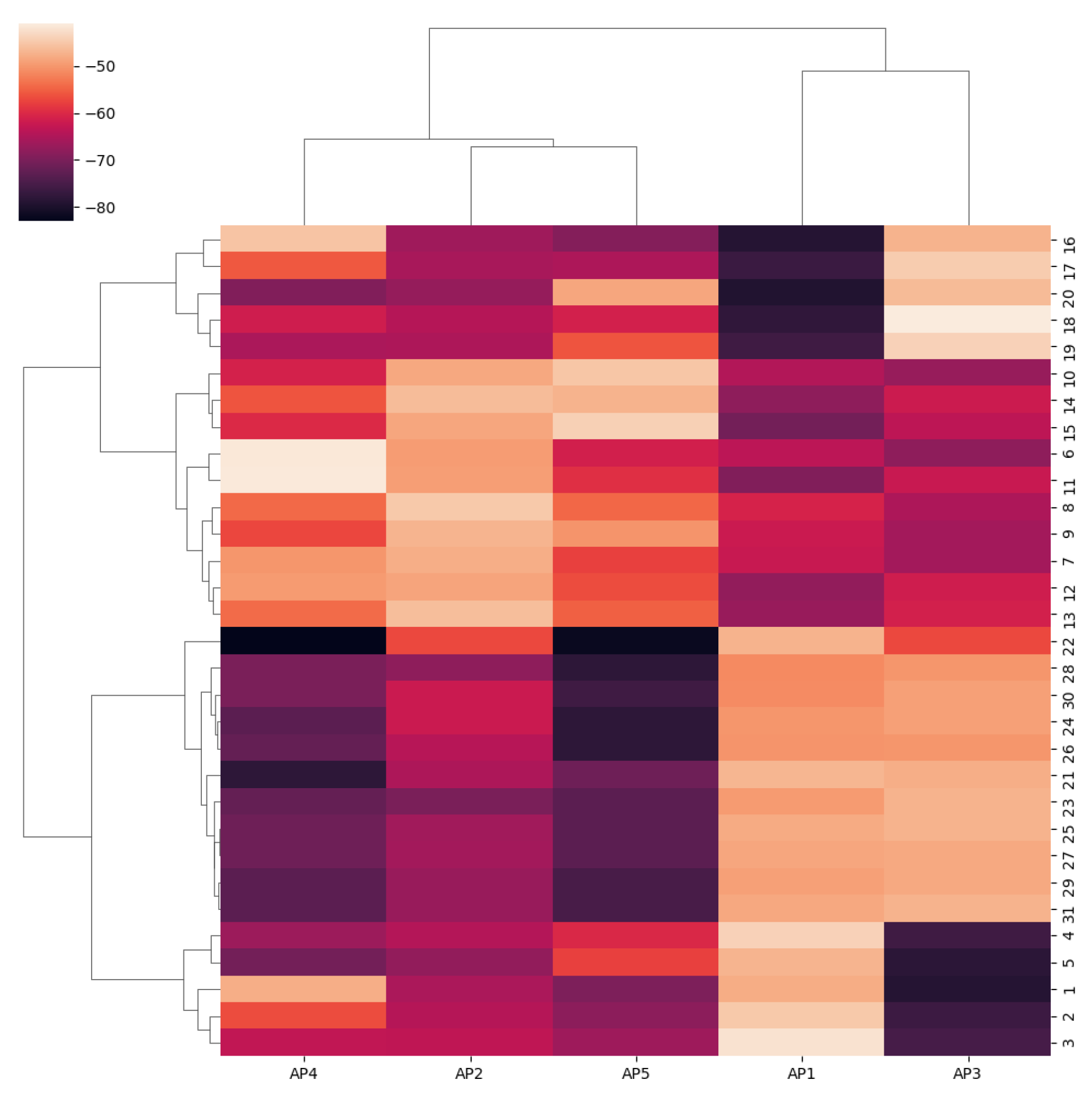
Figure 4 shows the heat map of hierarchical clustering, and the color shades in the figure represent the corresponding RSSI values.
4.3. Online Target Positioning
In this phase, the user terminal receives RSSI information X at the real-time location, and the proposed noise suppression technique is applied to X to obtain the noise-reduced real-time RSSI vector . Next, the mean value processing is performed to obtain the RSSI information of the point to be located. The trained RSSI is then compared to determine the AP with the strongest signal strength, and the potential clusters of are identified based on this AP. After mapping a cluster, we filter out the RP of other clusters and use only the RP in the potential cluster region for localization, which greatly reduces the computational effort.
However, in the real scenario, the problem of boundary point localization often arises. At this time, we can no longer directly localize a potential cluster by simply clustering it out, and we must also consider whether other clusters have a greater effect on the target point. Therefore, a boundary point judgment is required.
If the target point is a boundary point, is divided into multiple neighboring potential clusters and matched with all fingerprint data in these clusters. If the target point is not a boundary point, then is divided into one potential cluster and matched with all fingerprint data in that cluster only. Finally, the location of the user is further estimated using WKNN based on the location of the known reference points.
WKNN is a popular algorithm improved from the KNN technique [
11] with simple computation and high estimation accuracy. The estimation of the WKNN algorithm is based on the Euclidean distance:
where
is the
-norm operator,
is the Euclidean distance, and
is the
jth fingerprint of the potential clusters.
In the WKNN algorithm, the distance values are given weight:
where
is a small positive number introduced in order to control the denominator as not being zero, and
j is the index of the reference point that obeys
.
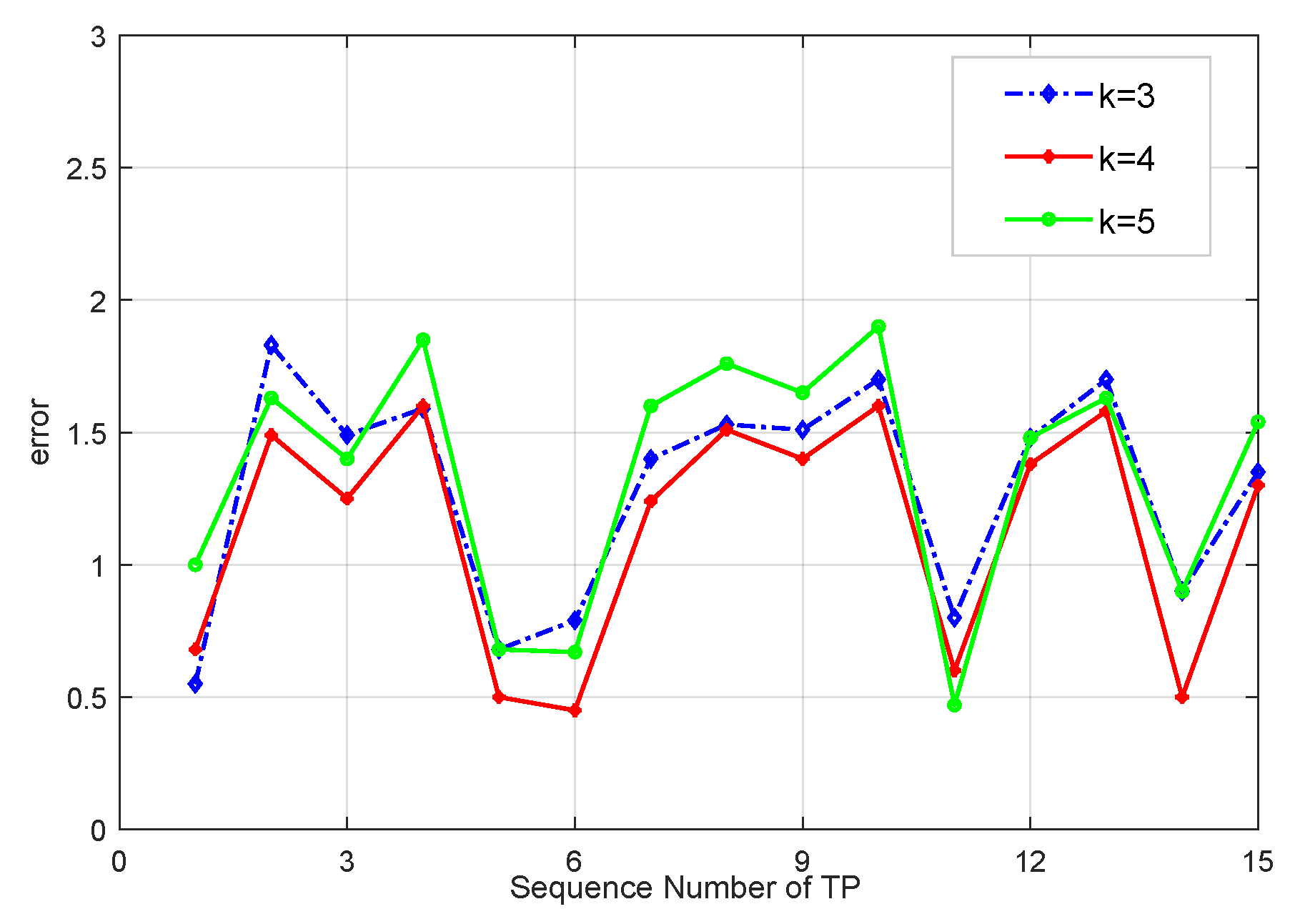
Then
reference points with the shortest Euclidean distance are selected as candidate locations in the potential clusters, and the user’s location is obtained by averaging the
k candidate locations, as follows:
6. Conclusions and Future Work
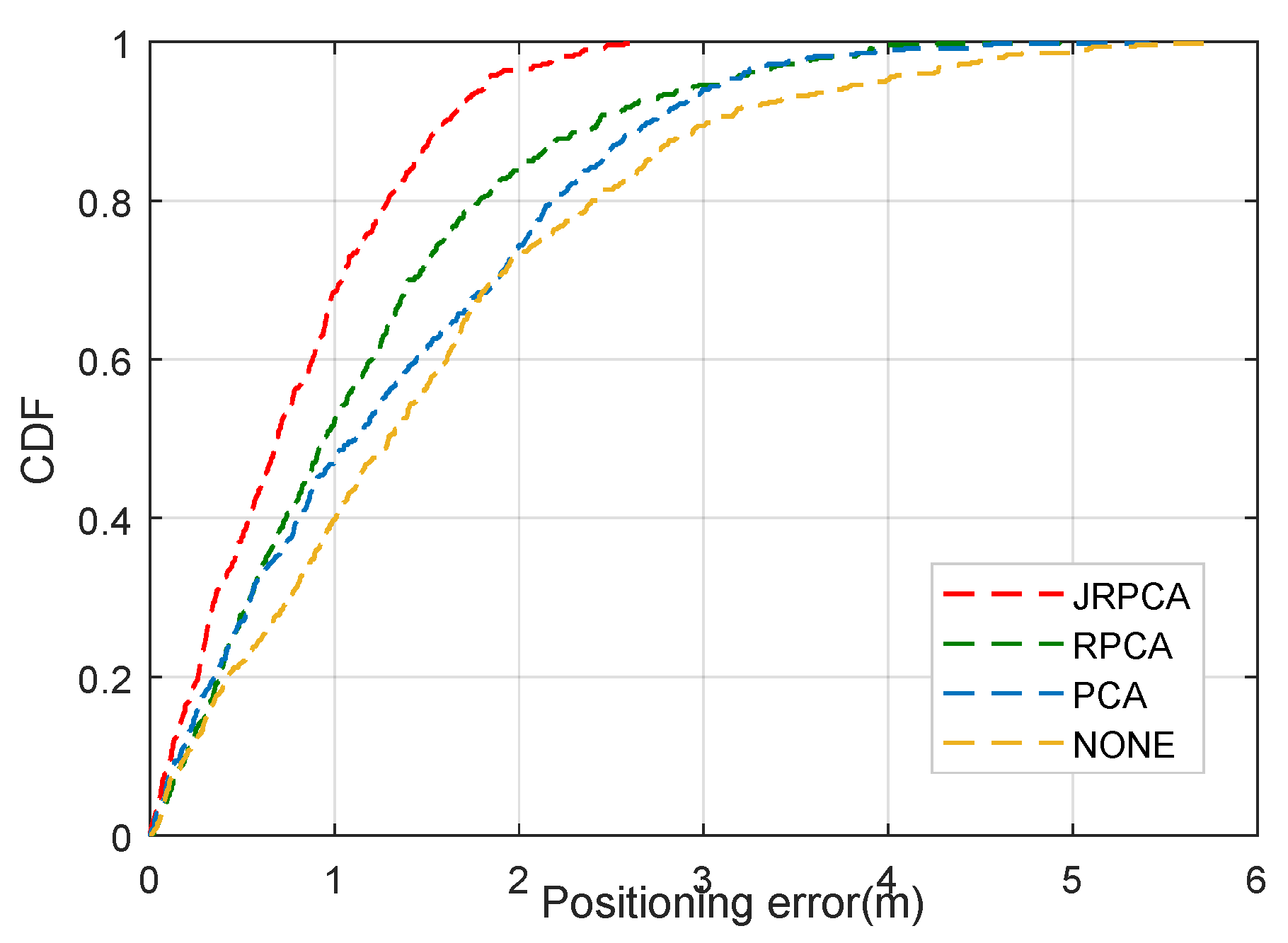
Due to the existence of signal measurement noise, the indoor localization method based on fingerprints often results in matching a set of scattered nearest neighbor RPs. Hence, the estimation results are often unsatisfactory. To alleviate this problem and improve robustness, a two-stage fingerprint localization method of JRPCA based on clustering is proposed in this paper. The method estimates target points only in potential clusters, considering the influence of measurement noise during target localization. JRPCA is used to train offline fingerprints and online RSSI vectors. In addition, considering the storage requirement and search cost of radio maps in fingerprint-based indoor positioning systems, a clustering method based on the one-way hierarchy is proposed to obtain reasonable RP clusters adaptively in accordance with predefined RPs. Experimental results demonstrate that the proposed method outperforms other algorithms with respect to robustness and accuracy.
As is well known, WiFi-based indoor positioning technology is easily influenced by different smartphones. This experiment is carried out using only one kind of device without consideration of the influences of different types of devices and receiving terminals on RSSI signals. Therefore, the selection of smart devices is also a significant research topic for indoor positioning. Moreover, the target to be tested is stationary during the experiment, and the localization of the moving target in the WLAN environment is to be solved in the next step. Consequently, future research will further concentrate on exploring the above factors.