Access-Control Model of Super Business System Based on Business Entity
Abstract
:1. Introduction
2. Related Work
3. Access-Control Model Based on Business Entity
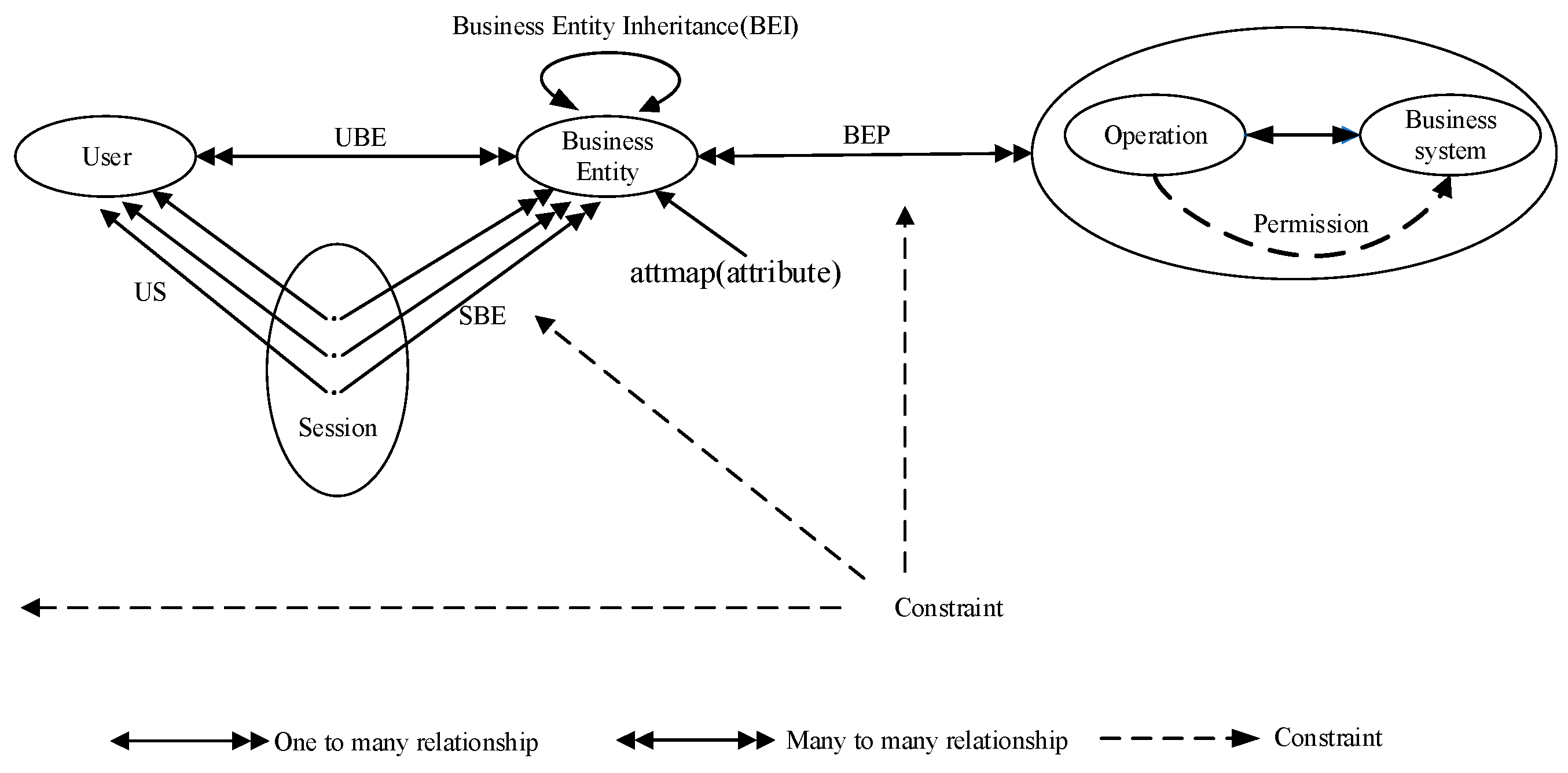
3.1. The Basic Elements
- (1)
- User: the access subjects, which have certain attributes and requests to access business system resources. It is recorded as User = {user1, user2, …, usern}. The attributes of the access user mainly include intrinsic attributes and security levels, which are recorded as UAttr = {Intrinsic, Safetylevel}.
- (2)
- Business system: the access object refers to the object operated by the access user and the accessed resource entity, which is recorded as BS = {bs1, bs2, …, bsn}. Attributes mainly include business attributes and security levels, which are recorded as BUsattr = {Permission, Safetylevel}.
- (3)
- Business entity: an abstract description of a business system. It is an abstract data structure composed of attributes, methods, and events. It is the carrier of business system permissions. It is recorded as BE = {be1, be2, …, ben}.
- (4)
- Operation: the operation that the user can perform on the business entity is recorded as OP = {op1, op2, …, opn}.
- (5)
- Permission: refers to the access mode that the access user can use to access the business entity. It is recorded as P = {p1, p2, …, pn}. P has two values: the read permission, rp, and the write permission, wp; the latter includes three operations: add, delete, and modify, and also includes rp.
- (6)
- Session: the mapping that establishes the corresponding relationship between the user and the business entity set is recorded as Session = {session1, session2, …, sessionn}.
- (7)
- Constraint: the restriction in the whole access-control process, mainly including cardinality constraint, space–time constraint, time constraint, responsibility separation constraint, minimum permission principle, and data abstraction principle.
- (8)
- Spatiotemporal environment: refers to the environment of the whole system during access control; it is recorded as TS = {ts1, ts2, …, tsn}. Its attributes include, for example, time and location, which is recorded as TSAttr = {Time, Location}. According to this attribute, you can get different permissions in different spatiotemporal environments.
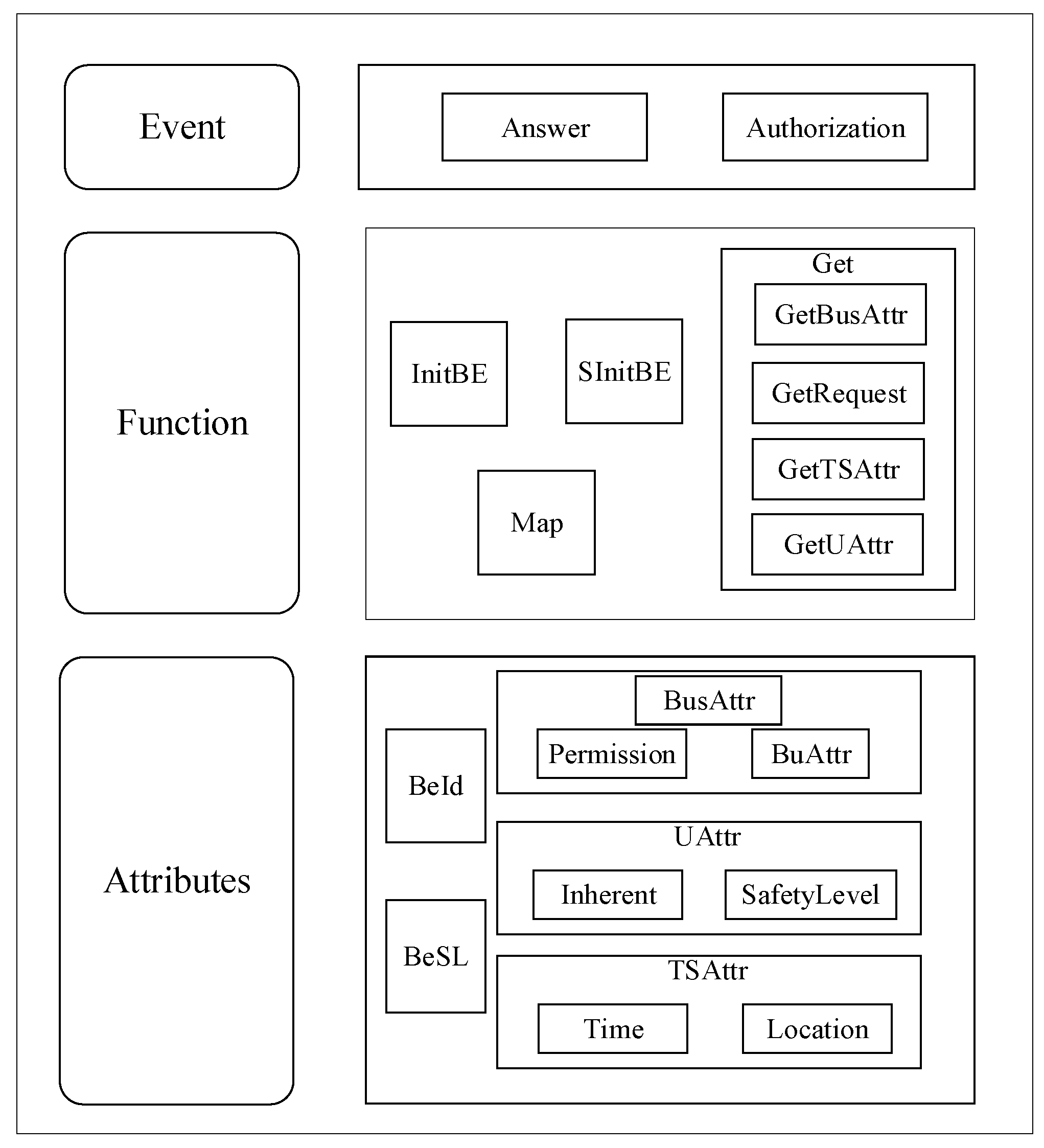
3.2. The Business Entity
3.2.1. The Basic Concepts
3.2.2. The Basic Composition
3.3. The Basic Relationship
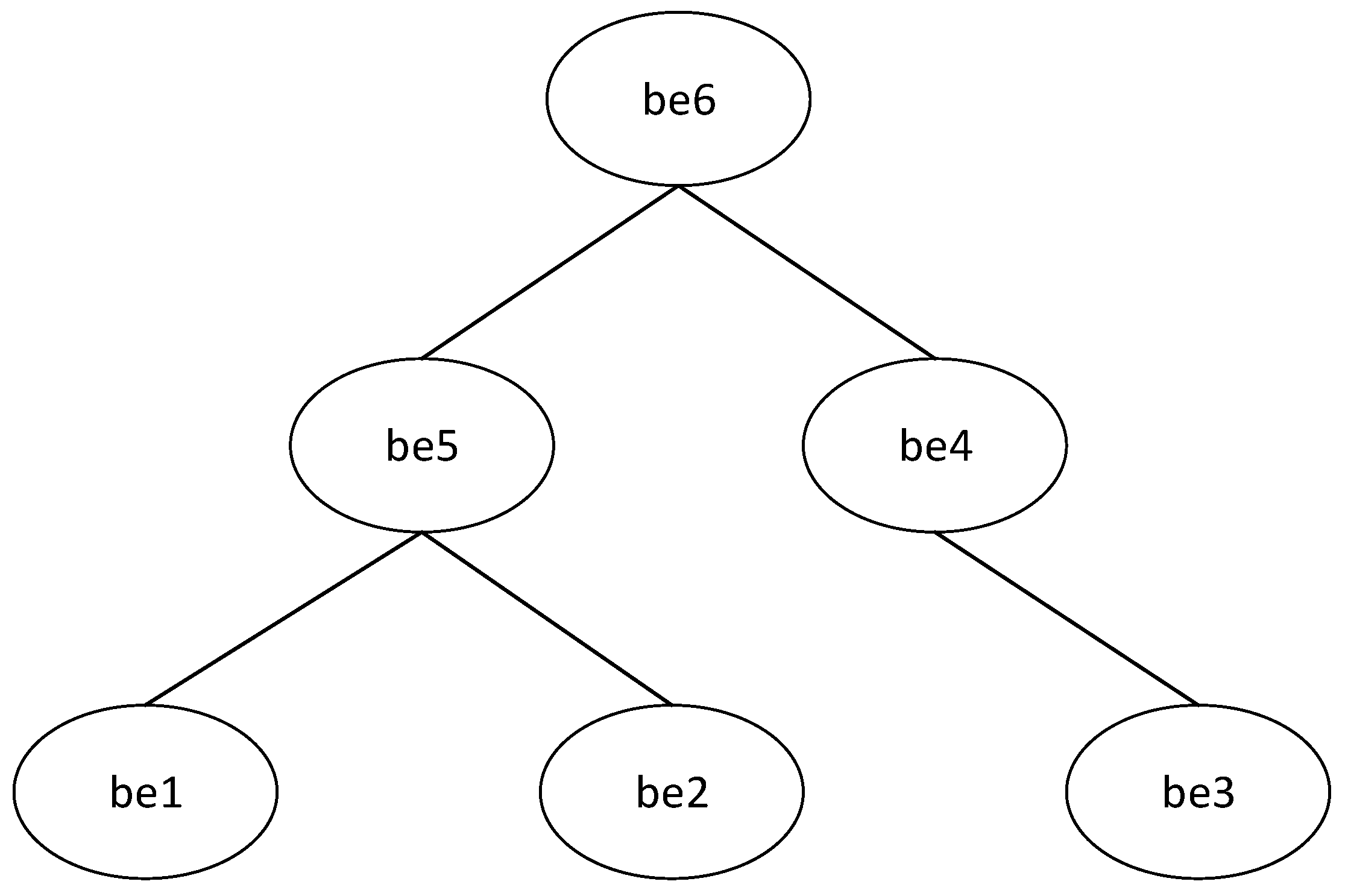
3.4. The Relationship between Business Entities
3.5. The Safety Level
3.6. The Basic Constraints
- (1)
- Cardinality Constraint (CardCons): refers to the restriction on the number of mappings between users and business entities, the number of users assigned by business entities, the number of permissions assigned to business entities, and the number of business entities that can be assigned permissions.CardCons ⊆ {cardcons_u, cardcons_beu, cardcons_be, cardcons_bep}
- (2)
- Attribute-Conflict Constraint (AttCCons): means that in the initial initialization process of the business entity, the attributes set between the business bodies cannot be conflicting attributes, and for the ID attribute in the business entity, its attribute value likewise cannot conflict.
- (3)
- Static Separation of Duty (SSD): defines the inheritance relationship between business entities in the business entity-based access-control model. If the SSD relationship is used between business entities, the inheritance relationship can’t be defined between business entities.
- (4)
- Dynamic Separation of Duty (DSD): restricts the user’s authority. If there is a DSD between two business entities, both business entities can be assigned to users, but users cannot activate the two business entities in the same session.
- (5)
- Time Constraint (Time Constraint, TimeCons): refers to the effective time in which the user has permission during the access process. If the access time exceeds the constraint time, the permission needs to be updated again.
- (6)
- Time–Space Constraint (TSCons): refers to the time, network environment, and geographic location constraints of the user during the access process.
- (7)
- The principle of least privilege: means that each user has the minimum privilege set necessary to complete the operation, and this model sets the business entity to the minimum privilege set required to complete the task.
- (8)
- Principle of data abstraction: the abstraction of data is embodied by the abstraction of authority, and the business entity is the abstract description of the business system, thus realizing the protection of data in the business system.
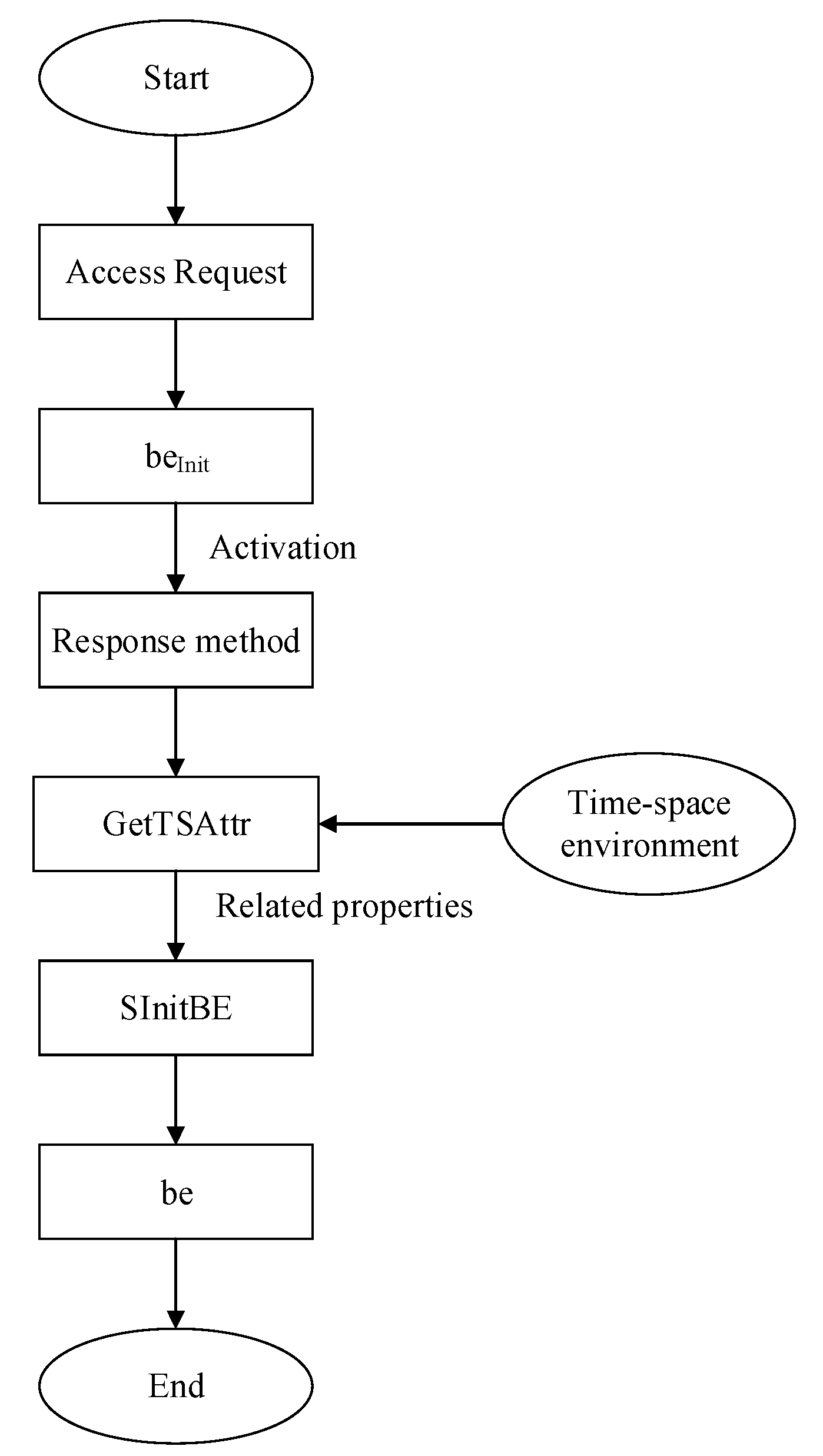
4. Access-Control Process, Based on Business Entity
4.1. Initialization
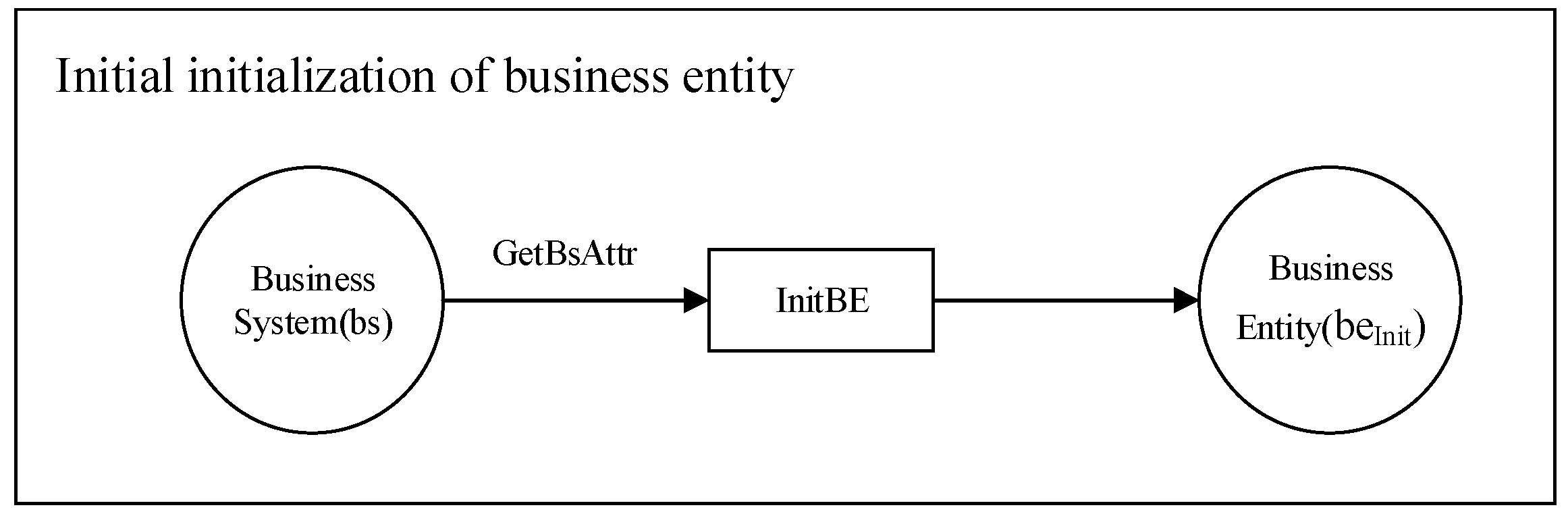
4.1.1. Initial Initialization
| Algorithm 1: Initial initialization algorithm of business entity |
| > |
4.1.2. Secondary Initialization
| Algorithm 2: Secondary initialization algorithm |
4.2. Mapping Rules and Authorization Rules
| Algorithm 3: Mapping function |
| Algorithm 4: Authorization rules |
4.3. Access-Control Process
- (1)
- The system initializes the business entity for the first time, and initializes the business system, bs, as the initial business entity, beInit;
- (2)
- Extract user-access request information request = (user,bs);
- (3)
- GetRequest(request) (user,bs)
- (4)
- Secondary initialization: use the SInitBE function to perform secondary initialization to form a business entity, be;
- (5)
- Mapping: use the function map(user, be) to realize the mapping between user and business entity, be; if the mapping rule is satisfied, continue to step 5; if not, then execute step 6;
- (6)
- Access authorization: use authorization rules to judge the access authorization; complete the access-control authorization, if it is satisfied; execute step 6, if it is not satisfied;
- (7)
- Access request is denied.
5. Model Analysis
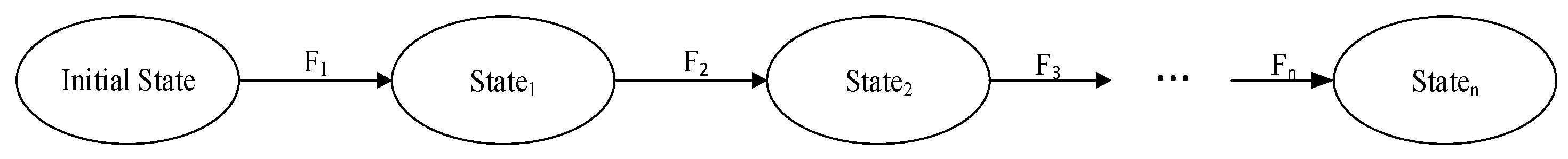
5.1. Safety Analysis
- (1)
- Define relevant state variables
- (1)
- Define the initial state, and analyze its security
- (2)
- Define the state transition function, and analyze its security
5.2. Model Characteristics
6. Summary
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Xu, F.; Qiu, L.; Lin, H. Research on network security situational awareness technology based on multi-service system interconnection. Audio Eng. 2022, 46, 124–128. [Google Scholar]
- Aftab, M.U.; Hamza, A.; Oluwasanmi, A.; Nie, X.Y.; Sarfraz, M.S.; Shehzad, D.; Qin, Z.G.; Rafiq, A. Traditional and Hybrid Access Control Models: A Detailed Survey. Secur. Commun. Netw. 2022, 2022, 1560885. [Google Scholar] [CrossRef]
- Cai, F.; Zhu, N.; He, J. Survey of access control models and technologies for cloud computing. Clust. Comput. 2019, 22, 6111–6122. [Google Scholar] [CrossRef]
- Vijayalakshmi, K.; Jayalakshmi, V. A Study on Curreny Research and Challenges in Attribute-based Access Control Model. Lect. Notes Data Eng. Commun. Technol. 2022, 101, 17–31. [Google Scholar]
- Snyder, L. Formal Models of Capability-Based Protection Systems. IEEE Trans. Comput. 1981, 30, 172–181. [Google Scholar] [CrossRef]
- Cho, C.; Seong, Y.; Won, Y. Mandatory Access Control Method for Windows Embedded OS Security. Electronics 2021, 10, 2478. [Google Scholar] [CrossRef]
- Singh, M.P.; Sural, S.; Vaidya, J.; Atluri, V. A Role-Based Administrative Model for Administration of Heterogeneous Access Control Policies and its Security Analysis. Inf. Syst. Front. 2021. [Google Scholar] [CrossRef]
- Sahani, G.J.; Thaker, C.S.; Shah, S.M. Scalable RBAC model for large-scale applications with automatic user-role assignment. Int. J. Commun. Netw. Distrib. Syst. 2022, 28, 76–102. [Google Scholar] [CrossRef]
- Zhang, R.; Zhang, J.L.; Sun, G.Z. Research and design of uniform authentication and authorization of multiple business system. Comput. Eng. Des. 2009, 30, 1826–1828. [Google Scholar]
- Blundo, C.; Cimato, S.; Siniscalchi, L. Role Mining Heuristics for Permission-Role-Usage Cardinality Constraints. Comput. J. 2021, 65, 1386–1411. [Google Scholar] [CrossRef]
- Xiong, H.R.; Chen, X.Y.; Zhang, B.; Du, X.H. Scalable Access Control Model Based on Double-tier Role and Organization. J. Electron. Inf. Technol. 2015, 37, 1612–1619. [Google Scholar]
- Rao, K.R.; Nayak, A.; Ray, I.G.; Rahulamathavan, Y.; Rajarajan, M. Role recommender-RBAC: Optimizing user-role assignments in RBAC. Comput. Commun. 2021, 166, 140–153. [Google Scholar] [CrossRef]
- Cai, T.; Nie, Q.B.; Ou, Y.K.; Zhou, J.L. Role-extended-based RBAC model. Appl. Res. Comput. 2016, 33, 882–885. [Google Scholar]
- Xiong, T.H.; Yu, Y.; Lou, D.J. Research on PRBAC Access Control Model in Workflow System. J. Appl. Sci. 2020, 38, 672–681. [Google Scholar]
- Aghili, F.F.; Sedaghat, M.; Single, D.; Gupta, M. MLS-ABAC: Efficient Multi-Level Security Attribute-Based Access Control scheme. Future Gener. Comput. Syst. 2022, 131, 75–90. [Google Scholar] [CrossRef]
- Fang, L.; Yin, L.H.; Guo, Y.C.; Fang, B.X. A Survey of Key Technologies in Attribute-Based Access Control Scheme. Chin. J. Comput. 2017, 40, 1680–1698. [Google Scholar]
- Zhu, Y.; Huang, D.; Hu, C.J.; Wang, X. From RBAC to ABAC: Constructing Flexible Data Access Control for Cloud Storage Services. IEEE Trans. Serv. Comput. 2015, 8, 601–616. [Google Scholar] [CrossRef]
- Bai, L.; Fan, K.; Bai, Y.; Cheng, X.C.; Li, H.; Yang, Y.T. Cross-domain access control based on trusted third-party and attribute mapping center. J. Syst. Archit. 2020, 116, 101957. [Google Scholar] [CrossRef]
- Zhang, R.N.; Liu, G.; Li, S.C.; Wei, Y.H.; Wang, Q. ABSAC: Attribute-Based Access Control Model Supporting Anonymous Access for Smart Cities. Secur. Commun. Netw. 2021, 2021, 5531369. [Google Scholar] [CrossRef]
- Yang, Q.L.; Zhang, M.R.; Zhou, Y.W.; Wang, T.; Xia, Z.; Yang, B. A Non-Interactive Attribute-Based Access Control Scheme by Blockchain for IoT. Electronics 2021, 10, 1855. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A Novel Attribute-Based Access Control Scheme Using Blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Wei, D.D.; Sheng, B.Y.; Xiang, W.J. Access Control Model in PDM System Based on Role and Attribute. Mach. Des. Manuf. 2019, 346, 259–263. [Google Scholar]
- Wang, J.Y.; Zhang, W. Research on access control model and algorithm based on attribute and RBAC. J. Chin. Comput. Syst. 2022, 43, 1523–1528. [Google Scholar]
- Ghafoorian, M.; Abbasinezhad-Mood, D.; Shakeri, H. A Thorough Trust and Reputation Based RBAC Model for Secure Data Storage in the Cloud. IEEE Trans. Parallel Distrib. Syst. 2019, 30, 778–788. [Google Scholar] [CrossRef]
- Wang, J.; Wang, H.; Zhang, H.B.; Cao, N. Trust and Attribute-Based Dynamic Access Control Model for Internet of Things. In Proceedings of the 2017 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Nanjing, China, 12–14 October 2017. [Google Scholar]
- Salji, M.R.; Udzir, N.L.; Ninggal, M.L.H.; Sani, N.F.M.; Lbrahim, H. Trust-based Access Control Model with Quantification Method for Protecting Sensitive Attributes. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 695–707. [Google Scholar] [CrossRef]
- Sun, L.; Li, Y. RACAC: An Approach toward RBAC and ABAC Combining Access Control. In Proceedings of the 2019 IEEE 5th International Conference on Computer and Communications (ICCC), Chengdu, China, 6–9 December 2019. [Google Scholar]
- Blundo, C.; Cimato, S.; Siniscalchi, L. Managing Constraints in Role Based Access Control. IEEE Access 2020, 8, 140497–140511. [Google Scholar] [CrossRef]
- Li, Z.X.; Liu, L.; Wang, X. A constraint-based for virtual machine data access control in cloud platform. Commun. Comput. Inf. Sci. 2018, 901, 426–443. [Google Scholar]
- Ipate, F.; Gheorghe, M.; Lefticaru, R. Fundamental results for learning deterministic extended finite state machines from queries. Theor. Comput. Sci. 2020, 862, 160–173. [Google Scholar] [CrossRef]

| Name | Meaning | Express |
|---|---|---|
| BEP | Business entity authority assignment BEP ⊆ BE × Permission | Represents the many-to-many relationship between business entities and permissions |
| UBE | User business entity assignment UBE ⊆ User × BE | Represents the many-to-many relationship between users and business entities |
| BEH | Business entity inherits BEH ⊆ BE × BE | Indicates the partial-order relationship inherited on the business entity set, and is marked as “≥” |
| US | User and session relationship in the US | Represents a function that maps a session to a single user |
| SBE | Session and business entity relationship SBE | Session and business entity relationship |
| attrmap | Attribute business entity correspondence | Represents a function that maps attributes to the corresponding single business entity |
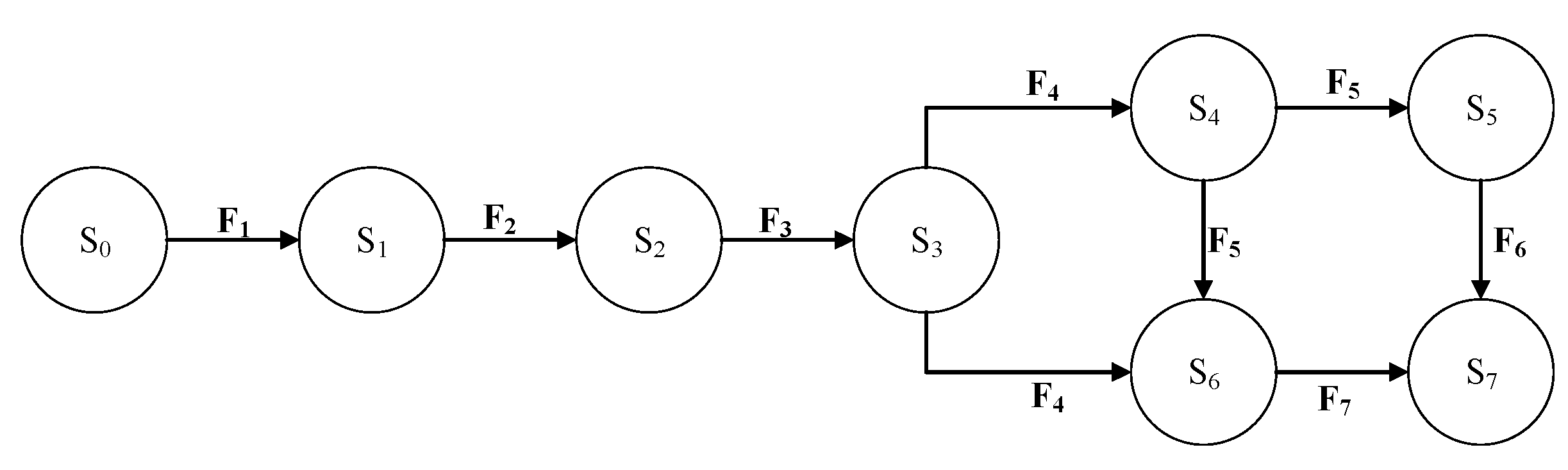
| Status Collection S | Input Collection I |
|---|---|
| S0: System initial state | I0: The system receives the access request, and initializes the business entity |
| S1: Answer (Request) | I1: The business entity responds to the user’s request |
| S2: GetUAttr, GetTSAttr | I2: Obtain user attributes and spatiotemporal attributes, according to the method |
| S3: SInitBE | I3: Secondary initialization of the business entity |
| S4: map | I4: Implement user business entity mapping, according to security level |
| S5: Authorization | I5: Users normally access the business system |
| S6: Revoke-access | I6: Access conditions are not met |
| S7: System end status | I7: The access-control process is completed |
| Models | Principle of Minimum Privilege | Dynamic Behavior | Separation of Duties | Authorization Flexibility | Time | Environment | Privacy | Audit | Safety Level | Model Security |
|---|---|---|---|---|---|---|---|---|---|---|
| DAC | O | O | O | ✓ | O | O | O | ✓ | O | Low |
| MAC | O | O | O | O | O | O | ✓ | ✓ | ✓ | Low |
| Ref [9] | ✓ | O | ✓ | O | O | O | ✓ | ✓ | O | Medium |
| ABAC | ✓ | ✓ | ✓ | ✓ | O | ✓ | O | ✓ | O | Low |
| Ref [27] | ✓ | ✓ | ✓ | ✓ | O | ✓ | ✓ | ✓ | O | High |
| BE-BAC | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | High |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, B.; Zheng, G.; Gao, Y.; Zhao, Y. Access-Control Model of Super Business System Based on Business Entity. Electronics 2022, 11, 3073. https://doi.org/10.3390/electronics11193073
Zhao B, Zheng G, Gao Y, Zhao Y. Access-Control Model of Super Business System Based on Business Entity. Electronics. 2022; 11(19):3073. https://doi.org/10.3390/electronics11193073
Chicago/Turabian StyleZhao, Bin, Guiyue Zheng, Yilong Gao, and Yanchen Zhao. 2022. "Access-Control Model of Super Business System Based on Business Entity" Electronics 11, no. 19: 3073. https://doi.org/10.3390/electronics11193073
APA StyleZhao, B., Zheng, G., Gao, Y., & Zhao, Y. (2022). Access-Control Model of Super Business System Based on Business Entity. Electronics, 11(19), 3073. https://doi.org/10.3390/electronics11193073





