Abstract
To address the problem that the traditional access-control model is no longer suitable for access control and authorization in the super business system—which has the characteristics of many businesses and complex permissions—a business entity-based access-control model (BE-BAC) is proposed in this paper. The BE-BAC model realizes the relationship between users, business entities, and business permissions. Firstly, according to the characteristics of the super business system, the concept of business entity is put forward, introducing the composition and relationship of the business entity. Secondly, the business entity is introduced into the access-control model, formally describing the basic relationship, constraint, mapping, and authorization strategy of the BE-BAC model. Finally, the access-control workflow, based on the business entity, is designed, and the security analysis and comprehensive comparison of the model are carried out. Compared with the existing access-control model, the BE-BAC model has higher security and flexibility, and better protects resources, through more secure access-request decisions.
1. Introduction
With the arrival of the high-speed and developed mobile internet era, mobile applications have become a necessity of life for the public, and have gradually become the core carrier of network applications and information data. With the new generation of information technology as the driving force, super business systems have emerged. The super business system combines and integrates a number of business services, and improves user experience, winning the industry (industry, region) ecology and intelligent application scenarios, so that users can spend more and longer time on the applications, to profit from them.
The super business system has the advantages and characteristics of being ‘full-featured’, ‘personalized’, and ‘super-flexible’. The interconnection of super business systems eliminates information islands, realizes the data sharing of multi-network, multi-platform, and multi-business systems, and makes the use and management of the system more convenient [1].
The appearance of the super business system not only brings convenience, but also brings new challenges to information security. Access-control technology is one of the best methods of protecting information security, and granting and revoking user rights [2,3]. In the face of a variety of business systems, the application authority is very complex when performing access-control authorization, and the problems of low access efficiency and low security may occur in the access process. Therefore, because of the above problems, we used the role-based access control (RBAC) idea for reference, abstracted the attributes of the business system, and built the BE-BAC.
The main contributions of this paper are as follows: (1) it puts forward the concept of business entity, and constructs the structure of the business entity, which is composed of attributes, methods, and mechanisms; (2) the access-control model based on the business entity is described, and the related elements are described formally; (3) the access-control flow, based on the business entity, is designed, and the security of the model is proved.
The second section of this paper introduces the related work of the access-control model; the third section introduces the business entity-based access-control model, the concept and structure of the business entity, the relationship, and the constraints between the models; the fourth section introduces the business entity-based access-control model workflow; the fifth section analyzes and compares the model; and the last section summarizes the work.
2. Related Work
With the development of new-generation information technology, there are more and more data resources. The access and authorization of data resources have always been the focus of people’s attention [4]; therefore, research on the access-control model is also a hot topic. Since the 1960s and 1970s, relevant researchers have proposed the discretionary access-control model (DAC) [5] and the mandatory access-control model (MAC) [6]. The characteristics of these two models are that the access subject is directly related to the authority, and they cannot well adapt to frequent access requests.
At present, RBAC is the most widely used in application systems [7,8]. The role is introduced into the research of the access-control model, and the RBAC management scheme of centralized management is given. The core idea of RBAC is the authorization of user roles and role permission. The permission is given to a role, and then the role is assigned to a user, so that the user has this permission. For the unified authentication and authorization of multiple business systems, Zhang Rui et al. [9] proposed a role-based access-control policy, including user groups and resource groups, and implemented a unified authentication and authorization system. The RBAC2 model added the definition of constraints, to specify the mandatory rules that should be followed when permissions are assigned to roles or roles are assigned to users. Blundo et al. defined two constraints in the literature [10]: one was the number of permissions that a role can contain; the other was the number of roles assigned to any user. These two constraints can be used to change the roles automatically output by the mining program, and to effectively capture the organization’s status. The RBAC model has been continuously improved and expanded. Xiong Houren et al. [11] proposed an extensible access-control model, based on double-layer roles and organizations, to solve the problem of role or authority redundancy in a multi-domain environment caused by a single role. This model was more suitable than the RBAC model for application in a distributed environment composed of multiple similar organizations. Rao et al. [12] aimed at the rapidly changing environment, added a role recommendation model in the RBAC system, optimized user role allocation according to user behavior, and improved the access efficiency of the model. Cai Ting [13] and others proposed an RBAC model based on role expansion, given the shortcomings of RBAC in complex organizational structures and authority inheritance relationships. Xiong Tianhong et al. [14] proposed an access-control model based on position role, introduced the concept of the business role, realized access control in the workflow management system, and realized the decoupling of the organization model and the business model.
Attribute-based access control (ABAC) has become a research hotspot in recent years. This method proposes the concept of attributes, and uses the attributes of the subject and the object to replace the RBAC rights allocation, to achieve fine-grained and dynamic access control [15,16]. The ABAC is mostly used in cloud environments and multi-domain environments. Zhu et al. [17] discussed building a user-friendly and easy-to-manage secure attribute-based access-control mechanism for cloud storage services. Attribute-Based Encryption (ABE) implements an attribute hierarchy similar to the user hierarchy in RBAC, enabling flexible control of data access in the cloud. Bai et al. [18] proposed a multi-domain access-control scheme suitable for smart city construction. The huge device group is divided into multiple domains for parallel and distributed management, and the ABAC is used to improve data-processing efficiency. Zhang et al. [19] proposed an ABAC that supports anonymous access in smart cities, which enhances the identitylessness of ABAC by incorporating homomorphic attribute-based signatures (HABS) that do not send subject attributes to the authority, reducing the subject attributes and the risk of re-identification. The research on the ABAC is not isolated. Combined with the new generation of information technologies, such as the Internet of Things and blockchain, a corresponding model is proposed. The literatures [20,21] combined the attribute-based access-control model with blockchain technology, and applied it to the environment of the Internet of Things, ensuring data security in the Internet of Things, and enhancing the effectiveness of access management.
To solve the access-control problem in the product data management system, Wei Dongdong [22] and others proposed to combine the RBAC and ABAC methods, and to add attribute elements as the basis for authorization. Experiments showed that the model significantly improved the execution efficiency of the system. At present, there are also many types of research on models and algorithms that combine attributes and RBAC. Wang Jingyu [23] and others designed a role-mining algorithm, based on minimum disturbance, to solve this problem. The experimental results showed that the effectiveness of this algorithm had been significantly improved. Mahdi [24] and others combined trust with the RBAC model, which was a new RBAC model based on trust and reputation. This model can not only properly resist the security threat of the trust-based RBAC model, but also has a reasonable execution time.
Like the RBAC model, the ABAC model has also been studied in combination with trust, and an access-control model based on trust and attributes has been proposed. In [25], Wang et al. proposed an access-control model based on trust attributes, which introduced a trust evaluation module, and combined dynamic trust attributes and static multi-attribute comprehensive constraints, to complete authorization. Mohd [26] et al. proposed a trust-based access-control model, to protect sensitive attributes and to provide a new quantitative method for calculating the two attributes of user credibility, making the evaluation of user credibility more accurate, and solving the problem of sensitive attribute protection. On the other hand, the combination of the RBAC and the ABAC research, whether it is the RBAC or the ABAC, has its advantages and disadvantages in large-scale enterprise applications; therefore, Sun et al. [27] combined the advantages of the two models, and proposed a simple method in a generic framework for implementing hybrid access control that combined the advantages of the RBAC and the ABAC. This model supported dynamic authentication and authorization by using attribute policies based on the RBAC infrastructure framework.
By analyzing the related research work of access-control models at home and abroad, it can be seen that there is no research on access-control authorization in super business systems. Therefore, we propose a new method for super business systems based on the complex characteristics of business systems in super business systems. The access-control model of the system abstracts the complex business system into a business entity, and realizes the access-control authorization in the super business system.
3. Access-Control Model Based on Business Entity
In this section, we introduce the composition structure of the access-control model based on the business entity, and show the basic elements, relationships and constraints of the model. In addition, the related concepts, the composition of business entities, and the relationship between business entities are described in detail; thereby, we propose a complete access-control model diagram based on business entities.
3.1. The Basic Elements
The basic elements of the BE-BAC model include users, business systems, business entities, operations, permissions, sessions, and constraints. The specific description is as follows:
- (1)
- User: the access subjects, which have certain attributes and requests to access business system resources. It is recorded as User = {user1, user2, …, usern}. The attributes of the access user mainly include intrinsic attributes and security levels, which are recorded as UAttr = {Intrinsic, Safetylevel}.
- (2)
- Business system: the access object refers to the object operated by the access user and the accessed resource entity, which is recorded as BS = {bs1, bs2, …, bsn}. Attributes mainly include business attributes and security levels, which are recorded as BUsattr = {Permission, Safetylevel}.
- (3)
- Business entity: an abstract description of a business system. It is an abstract data structure composed of attributes, methods, and events. It is the carrier of business system permissions. It is recorded as BE = {be1, be2, …, ben}.
- (4)
- Operation: the operation that the user can perform on the business entity is recorded as OP = {op1, op2, …, opn}.
- (5)
- Permission: refers to the access mode that the access user can use to access the business entity. It is recorded as P = {p1, p2, …, pn}. P has two values: the read permission, rp, and the write permission, wp; the latter includes three operations: add, delete, and modify, and also includes rp.
- (6)
- Session: the mapping that establishes the corresponding relationship between the user and the business entity set is recorded as Session = {session1, session2, …, sessionn}.
- (7)
- Constraint: the restriction in the whole access-control process, mainly including cardinality constraint, space–time constraint, time constraint, responsibility separation constraint, minimum permission principle, and data abstraction principle.
- (8)
- Spatiotemporal environment: refers to the environment of the whole system during access control; it is recorded as TS = {ts1, ts2, …, tsn}. Its attributes include, for example, time and location, which is recorded as TSAttr = {Time, Location}. According to this attribute, you can get different permissions in different spatiotemporal environments.
3.2. The Business Entity
To solve the access-control problem when there are many services in the super business system, and to improve the security and efficiency of the access-control process, we propose the concept of a business entity. The concept and composition of the business entity are described in detail below.
3.2.1. The Basic Concepts
The Business Entity is an abstract description of the business system, and it is the carrier of a certain amount of authority in the business system. Different business bodies are mapped according to the attribute characteristics of the business system; the access permission of the business system is encapsulated into the business entity; the user and the business entity are mapped; and the user indirectly accesses the business system through the business entity. A business entity is an abstract data structure composed of properties, methods, and events.
Based on the role-based access-control architecture idea, the concept of a business body is proposed, to solve the complex problem of access objects, and to realize the mapping relationship between users, business entities, and business systems. The RBAC model proposes the concept of role for the complex access subject. The user obtains the role by becoming an appropriate role, and has permissions, which realizes the decoupling of the user and the permission; we propose the concept of a business entity for the complex access object and the integration of the business system, which is abstracted as a business entity. The business entity is the carrier of the authority of the business system. The user has a mapping relationship with the business entity, and indirectly obtains the corresponding business system authority through the business entity, which simplifies the management of the authority. In the actual application scenario, there are many relationships between users and business entities, and between business entities and business systems, and there are hierarchical inheritance relationships between business entities. Therefore, the permissions owned by users are the minimum set of permissions owned by the business entities they map.
3.2.2. The Basic Composition
The business entity is an abstract data structure for the business system, which helps access-users to access business system resources, and simplifies the complexity of the access process when accessing objects. It consists of three parts: attributes, methods, and events. The attributes represent the characteristics of the business entity, including ID, business system attributes, user attributes, space–time attributes, and security level. The ID is the unique identifier of the business entity, and the business system attribute describes the characteristics of the abstracted business system. This attribute belongs to Static attributes, whose attribute values remain unchanged, mainly including business system permissions and business attributes; ‘user attributes’ refers to the attributes of access-users, including inherent attributes and security levels; ‘space-time attributes’ refers to the attributes of the space–time environment where the access request occurs. Mainly including time and location, the security level guarantees the confidentiality of access authorization. The method includes the initialization method, calculation method, and attribute-acquisition method, and realizes the functions of initialization, processing, and calculation in the access-control process. As part of the business entity, the event mainly realizes the response function. When an access request occurs, its response method will be activated, and it will then activate the attribute acquisition-method in the business entity method, complete its corresponding operations, realize the mapping between the user and the business entity, and then complete the access-control authorization. As an abstract description of the business system, the business entity maintains the control relationship between the user and the business system during the access-control process. The data structure of the business entity can be described by the following code.
Abstract Business Entity
{
String BeId;//Business Entity ID
String BeSL;//Security level attribute of business entity
String BusAttr[] = {Permission, SafetyLevel }//Business system attributes
String UAttr[] = {Inherent,SafetyLevel}//User attribute
String TSAttr[] = {Time,Location}//Time and space attribute
String GetBusAttr(BusAttr)//Get the attribute value method that constitutes the business system
String GetRequest(Request)//Get access request method
String GetUAttr(TSAttr)//Get user attribute method
String GetTSAttr(TSAttr)//Get space–time attribute method
String Request[] = {user,bs}//Access request method
String Answer(Request)//Response method
String InitBE(BusAttr)//Initialize the business entity method
String SInitBE(InitBE(BusAttr)∩TSAttr)//Secondary initialization business entity method
String map()//Mapping method between a business entity and user
String authorization()//Authorization method
}
In accordance with the above description, the structure diagram of the business entity is shown in Figure 1.
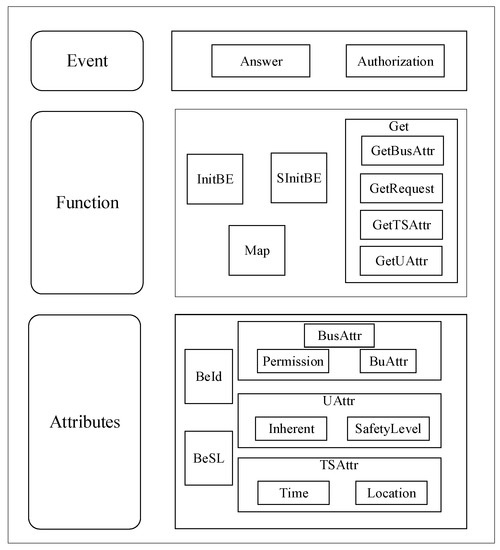
Figure 1.
Structure of business entity.
3.3. The Basic Relationship
The relationship between each element is shown in Table 1. Each element set is connected through the relationship set, to realize the operation between elements.

Table 1.
Description of access-control model relationship, based on business entity.
3.4. The Relationship between Business Entities
The concept of a business entity is put forward in the access-control model based on the business entity. There is a corresponding hierarchy-inheritance relationship between business entities, which reflects the relationship between power and responsibility, and provides convenience for permission management. As shown in Figure 2: business entity be5 inherits the permissions of business entities be1 and be2; business entity be4 inherits the permissions of business entity be3; and business entity be6 inherits all the permissions of business entities be1, be2, be3, be4, and be5.
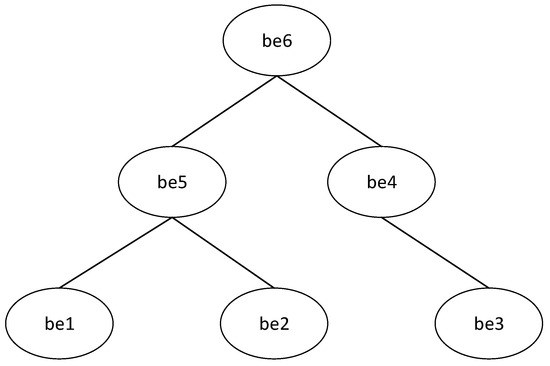
Figure 2.
Business entity hierarchy-inheritance diagram.
BEH ⊆ BE × Be indicates the partial-order relationship inherited in the business entity set, and is marked as “≥”. bei ≥ bej represents the business entity bei inherited by the business entity bej.
3.5. The Safety Level
The security level of a business entity is calculated according to the security level of the business system. Because the mapping relationship between a business entity and a business system is many-to-many, and a business entity corresponds to multiple business systems, the security level of a business entity is calculated by the average of the security level values of the mapped multiple business systems, expressed as:
BESL = aver(BS) = (bs1.sl + bs2.sl + ⋯ + bsn.sl)/n
3.6. The Basic Constraints
The constraint is an essential part of the access-control process. It exists in the whole process of access-control. Its purpose is to limit the user’s operation authority on resources, prevent the occurrence of ultra vires, and judge whether the value in the access process can be accepted. Only the accepted value can be allowed to access [28,29], which enhances the security of access authorization. In this study, constraints mainly include the following: cardinality constraint, separation-of-responsibilities constraint, minimum-permission principle, data-abstraction principle, space–time constraint, and time constraint.
- (1)
- Cardinality Constraint (CardCons): refers to the restriction on the number of mappings between users and business entities, the number of users assigned by business entities, the number of permissions assigned to business entities, and the number of business entities that can be assigned permissions.CardCons ⊆ {cardcons_u, cardcons_beu, cardcons_be, cardcons_bep}
For example: cardcons_u (user) ≤ m indicates that a user can only be mapped to m business entities at most; cardcons_beu (business entity) ≤ n indicates that the business entity can only be assigned to n users at most; cardcons_be (business entity) ≤ k indicates that a business entity can only map up to k authorizations; and cardcons_bea (authority) ≤ t means that the authorization authority can only assign up to t business entities.
- (2)
- Attribute-Conflict Constraint (AttCCons): means that in the initial initialization process of the business entity, the attributes set between the business bodies cannot be conflicting attributes, and for the ID attribute in the business entity, its attribute value likewise cannot conflict.
- (3)
- Static Separation of Duty (SSD): defines the inheritance relationship between business entities in the business entity-based access-control model. If the SSD relationship is used between business entities, the inheritance relationship can’t be defined between business entities.
- (4)
- Dynamic Separation of Duty (DSD): restricts the user’s authority. If there is a DSD between two business entities, both business entities can be assigned to users, but users cannot activate the two business entities in the same session.
- (5)
- Time Constraint (Time Constraint, TimeCons): refers to the effective time in which the user has permission during the access process. If the access time exceeds the constraint time, the permission needs to be updated again.
- (6)
- Time–Space Constraint (TSCons): refers to the time, network environment, and geographic location constraints of the user during the access process.
- (7)
- The principle of least privilege: means that each user has the minimum privilege set necessary to complete the operation, and this model sets the business entity to the minimum privilege set required to complete the task.
- (8)
- Principle of data abstraction: the abstraction of data is embodied by the abstraction of authority, and the business entity is the abstract description of the business system, thus realizing the protection of data in the business system.
The above describes in detail the basic elements, basic concepts, and basic relationships involved in the business entity-based access-control model, and draws the business entity-based access-control model diagram, according to the above description, as shown in Figure 3.
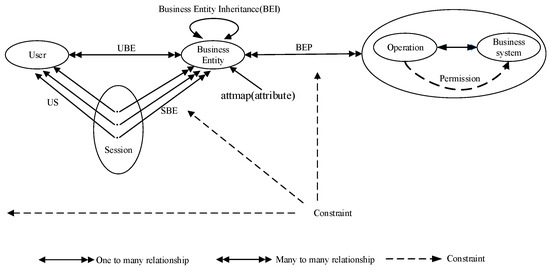
Figure 3.
Access-control model diagram, based on business entity.
4. Access-Control Process, Based on Business Entity
In Section 3, the composition of the access-control model, based on business entities, was introduced. In this section, the access mechanism and access-control process of the model are introduced. This section is divided into three parts. Firstly, the initialization process is introduced; secondly, the mapping principle and authorization principle used are described; and finally, the access process of the model is summarized.
4.1. Initialization
In this study, the initialization of the business entity is divided into two parts. The first part is the initial initialization, which realizes from the business system to the business entity, and forms the initial business entity beInit. The second part is to combine the initial business entity with the user’s access request and the environment attribute, when the access control occurs after the access request occurs, to form a business entity and complete the secondary initialization.
4.1.1. Initial Initialization
In an access-control process based on a business entity, the business system in the system should be initialized as a business entity (Algorithm 1). Firstly, the GetBsAttr function is used to obtain the business system attribute and security level, and then the business system BS is initialized as the initial business entity beInit, according to the InitBE function. The initial initialization flow chart is shown in Figure 4.
| Algorithm 1: Initial initialization algorithm of business entity |
| > |
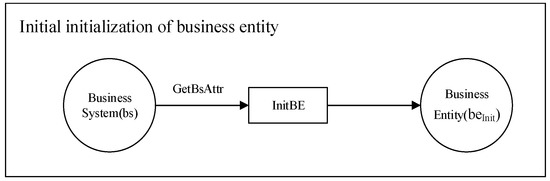
Figure 4.
Initial initialization flow chart.
4.1.2. Secondary Initialization
After receiving the user’s access request, secondary initialization is performed (Algorithm 2). The user and the beInit establish a relationship through a session, activate the response event in the business entity beInit, use the GetTSAttr method in the business entity to obtain the space–time attribute of the environment where the access request is made, and the system uses the SInitBE function to form a business entity. The secondary initialization process is shown in Figure 5.
| Algorithm 2: Secondary initialization algorithm |
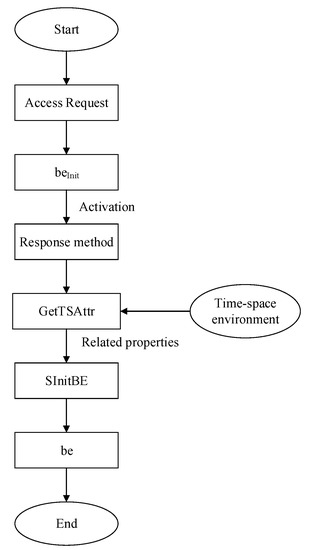
Figure 5.
Secondary initialization flow chart.
4.2. Mapping Rules and Authorization Rules
In the access-control model based on the business entity, the access authorization rules are implemented, based on the business entity. After the user sends an access request and completes the secondary initialization of the business entity, the getUAttr method in the business entity obtains the security level of the access user, and then compares the security level of the user with the access level of the business entity. If the security level of the user is greater than or equal to the security level of the business entity, the mapping between the user and the business entity can be realized through the map function (Algorithm 3). After the mapping between the user and the business entity is realized, it is determined whether the operation in the user access request belongs to the permission set of the business entity. If it belongs to the permission set, the access-control authorization can be realized; otherwise, the access is denied (Algorithm 4). The specific rules of the two algorithms are as follows:
| Algorithm 3: Mapping function |
| Algorithm 4: Authorization rules |
4.3. Access-Control Process
The system-access authorization is based on the business entity, and controls the user’s access. The access authorization process is as follows: the system first initializes the business entity, and then initializes the business system, bs, to the business entity, beInit; after the user sends an access request, the business entity obtains the detailed information of the access request, = (user, bs), and then performs the secondary initialization of the business body to form the business entity, be. Then, the mapping between the user and the business entity is judged and, finally, the access authority is judged according to the access authorization rules. The access-control flow chart is shown in Figure 6. The specific access-control steps are as follows:
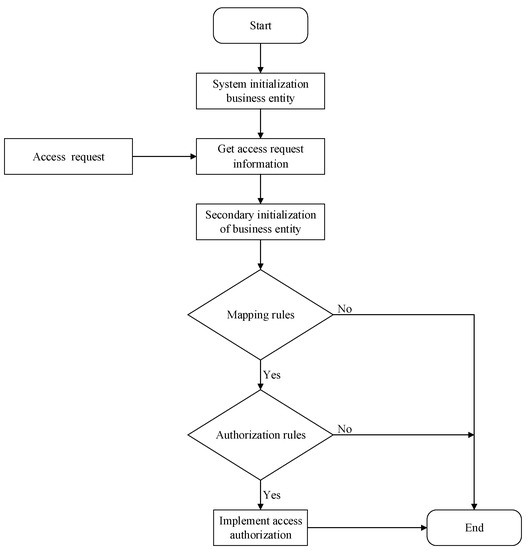
Figure 6.
Access-control process, based on business entity.
- (1)
- The system initializes the business entity for the first time, and initializes the business system, bs, as the initial business entity, beInit;
- (2)
- Extract user-access request information request = (user,bs);
- (3)
- GetRequest(request) (user,bs)
- (4)
- Secondary initialization: use the SInitBE function to perform secondary initialization to form a business entity, be;
- (5)
- Mapping: use the function map(user, be) to realize the mapping between user and business entity, be; if the mapping rule is satisfied, continue to step 5; if not, then execute step 6;
- (6)
- Access authorization: use authorization rules to judge the access authorization; complete the access-control authorization, if it is satisfied; execute step 6, if it is not satisfied;
- (7)
- Access request is denied.
5. Model Analysis
In this section, we carry out a security analysis and model comparison of the access-control model proposed in this paper. Firstly, we prove the security of the proposed model, using finite-state machine (FSM) theory [30]. Then, we compare the proposed model with other control models, and note the advantages of the business entity-based access-control model, in many aspects.
5.1. Safety Analysis
In this study, we use the FSM theory to prove the security of the access-control model, based on the business entity. FSM describes the BE-BAC model as an abstract mathematical state. Firstly, we verify that the initial state of the model is safe, and that all state transition functions are safe. If the above two conditions are met, the whole system is safe. The state transition is shown in Figure 7.
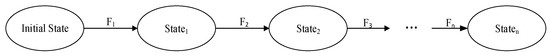
Figure 7.
State transition diagram.
- (1)
- Define relevant state variables
The finite-state transition system of the BE-BAC model is formally described as M = (S, S0, F, I), where: S denotes a finite state set, S = {S0, …, Sn}; S0 indicates the initial state of the model; I represents an input set; and F represents the state transition function, F: P × S→Sn. This indicates that the model state changes from the current state to the next state under the driving of the input. In accordance with the above state variables, the access-control state settings are shown in Table 2.

Table 2.
Access-control state settings table.
- (1)
- Define the initial state, and analyze its security
In the initial state, there is no access-request operation, the business entity has not been initialized, and the access policy has not been called, which meets the security requirements of the finite-state machine. Therefore, the initial state S_0 is secure.
- (2)
- Define the state transition function, and analyze its security
The safety state transition functions of the BE-BAC model include:
F1: S0 × I0→S1: this function represents accepting the user-access request, and initializing the service entity;
F2: S1 × I1→S2: this function indicates that the business entity response event is activated;
F3: S2 × I2→S3: this function indicates that the get method of the business entity is activated, to obtain relevant properties;
F4: S3 × I3→S4/S6: this function indicates that the get method of the business entity is activated, to obtain relevant properties;
F5: S4 × I4→S5/S6: this function indicates that, in the process of access authorization, it is judged according to the authorization rules; the business system is accessed when the conditions are met, or accessed without permission;
F6: S5 × I5→S7: this function indicates that, in the process of access authorization, it is judged according to the authorization rules; the business system is accessed when the conditions are met; or accessed without permission;
F7: S6 × I6→S7: this function indicates that, in the process of access authorization, it is judged according to the authorization rules; the business system is accessed when the conditions are met, or accessed without permission;
The schematic diagram of state transition is shown in Figure 8.
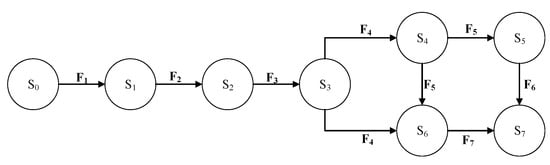
Figure 8.
Schematic diagrams of state transition.
The final state transition function can be expressed as F = F1 × F2 × F3 × F4 × F5 × F6 × F7. When the user sends an access request, the system state S1 is safe. After initialization, the business entity automatically accepts the user’s access request, and activates the response event. Therefore, the system state S2 is safe. The business entity attribute acquisition method makes corresponding operations for the response event, so the system state S3 is safe. Through the mapping rules, the user-service body mapping is completed, and the system state S4 is safe. Judging the access rights according to the authorization rules, if the conditions are met, the access is allowed, and the system state S5 is safe. If it is not satisfied, the system security remains unchanged, so the system state S6 is safe. To sum up, because the initial state S0 is safe, and the state transition function F is also safe, which satisfies the definition of finite state machine safety, the BE-BAC model is safe.
5.2. Model Characteristics
The biggest advantage of RBAC is that it simplifies the management of users and permissions. By classifying users, roles and permissions are associated, while users and permissions become indirect associations. The authorization management of users becomes very simple and easy to maintain. With the help of the role-based access-control idea, the proposal of the business entity-based access control abstracts the complex business system into a business entity that reasonably divides the permissions, realizes the mapping relationship between users, business entities, and business systems, greatly facilitates the management of permissions, and adds security level attributes to users and business entities, to ensure the confidentiality and security of object data, thus realizing fast, secure-access authorization.
In order to analyze and compare the capabilities, performance, and security of the BE-BAC model and other access-control models more intuitively and concisely, this paper selects five access-control models, and compares them from 10 aspects. The comprehensive analysis and comparison are shown in Table 3. The DAC model and MAC model are less flexible, due to the characteristics of the application scenarios, and cannot adapt to frequent access requests. The literature [9] designed a unified authentication and authorization system using the RBAC model in a multi-service system. As the most widely used model in the application system, the RBAC model is also the basis of this study; however, due to the low flexibility of model authorization, it will not change due to changes in the space–time environment, and it is unable to conduct multi-level security management. The ABAC model introduces attribute elements, to achieve fine-grained dynamic access-control authorization, but it still does not take multi-level security management into account. The literature [27] combines the RBAC model with the ABAC model, and proposes a RACAC model to implement access-control authorization in large enterprise applications; however, it only considers the environment attribute, not the time attribute, and it does not propose multi-level security management. Based on the above research results, this paper proposes an access-control model based on the business entity, abstracts the business system into a business entity, and sets the security level for the business entity. The time, environment, and other dynamic space–time attributes of the subject are introduced into the authorization, to achieve flexible access authorization.

Table 3.
Comprehensive analysis and comparison of access-control models.
6. Summary
This paper focused on access-control technology in the application environment of the super business system, comprehensively analyzed the advantages and disadvantages of the current common access-control models, and found that the existing models were not suitable for the super business system. Therefore, this paper put forward the concept of the business entity, designed the access-control model, based on the business entity, and implemented the access-control authorization, based on the business entity. At the same time, the security of the BE-BAC model was analyzed, and compared with the existing models. The results show that the model can achieve secure access-control authorization in the super business system. In future work, our plan is to design a prototype system, and to further evaluate and verify the designed model, from the implementation level.
Author Contributions
Conceptualization, B.Z. and Y.G.; methodology, B.Z., G.Z., Y.G. and Y.Z.; writing—original draft preparation, G.Z.; writing—review and editing, B.Z. and Y.G.; visualization, Y.G.; supervision, B.Z.; project administration, funding acquisition, B.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Natural Science Foundation of Shandong Province, research on Key Technologies of Dynamic Game Access Control based on Blockchain, fund number ZR2020MF029, and the Natural Science Foundation of Shandong Province, fund number ZR2020MF058.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Xu, F.; Qiu, L.; Lin, H. Research on network security situational awareness technology based on multi-service system interconnection. Audio Eng. 2022, 46, 124–128. [Google Scholar]
- Aftab, M.U.; Hamza, A.; Oluwasanmi, A.; Nie, X.Y.; Sarfraz, M.S.; Shehzad, D.; Qin, Z.G.; Rafiq, A. Traditional and Hybrid Access Control Models: A Detailed Survey. Secur. Commun. Netw. 2022, 2022, 1560885. [Google Scholar] [CrossRef]
- Cai, F.; Zhu, N.; He, J. Survey of access control models and technologies for cloud computing. Clust. Comput. 2019, 22, 6111–6122. [Google Scholar] [CrossRef]
- Vijayalakshmi, K.; Jayalakshmi, V. A Study on Curreny Research and Challenges in Attribute-based Access Control Model. Lect. Notes Data Eng. Commun. Technol. 2022, 101, 17–31. [Google Scholar]
- Snyder, L. Formal Models of Capability-Based Protection Systems. IEEE Trans. Comput. 1981, 30, 172–181. [Google Scholar] [CrossRef]
- Cho, C.; Seong, Y.; Won, Y. Mandatory Access Control Method for Windows Embedded OS Security. Electronics 2021, 10, 2478. [Google Scholar] [CrossRef]
- Singh, M.P.; Sural, S.; Vaidya, J.; Atluri, V. A Role-Based Administrative Model for Administration of Heterogeneous Access Control Policies and its Security Analysis. Inf. Syst. Front. 2021. [Google Scholar] [CrossRef]
- Sahani, G.J.; Thaker, C.S.; Shah, S.M. Scalable RBAC model for large-scale applications with automatic user-role assignment. Int. J. Commun. Netw. Distrib. Syst. 2022, 28, 76–102. [Google Scholar] [CrossRef]
- Zhang, R.; Zhang, J.L.; Sun, G.Z. Research and design of uniform authentication and authorization of multiple business system. Comput. Eng. Des. 2009, 30, 1826–1828. [Google Scholar]
- Blundo, C.; Cimato, S.; Siniscalchi, L. Role Mining Heuristics for Permission-Role-Usage Cardinality Constraints. Comput. J. 2021, 65, 1386–1411. [Google Scholar] [CrossRef]
- Xiong, H.R.; Chen, X.Y.; Zhang, B.; Du, X.H. Scalable Access Control Model Based on Double-tier Role and Organization. J. Electron. Inf. Technol. 2015, 37, 1612–1619. [Google Scholar]
- Rao, K.R.; Nayak, A.; Ray, I.G.; Rahulamathavan, Y.; Rajarajan, M. Role recommender-RBAC: Optimizing user-role assignments in RBAC. Comput. Commun. 2021, 166, 140–153. [Google Scholar] [CrossRef]
- Cai, T.; Nie, Q.B.; Ou, Y.K.; Zhou, J.L. Role-extended-based RBAC model. Appl. Res. Comput. 2016, 33, 882–885. [Google Scholar]
- Xiong, T.H.; Yu, Y.; Lou, D.J. Research on PRBAC Access Control Model in Workflow System. J. Appl. Sci. 2020, 38, 672–681. [Google Scholar]
- Aghili, F.F.; Sedaghat, M.; Single, D.; Gupta, M. MLS-ABAC: Efficient Multi-Level Security Attribute-Based Access Control scheme. Future Gener. Comput. Syst. 2022, 131, 75–90. [Google Scholar] [CrossRef]
- Fang, L.; Yin, L.H.; Guo, Y.C.; Fang, B.X. A Survey of Key Technologies in Attribute-Based Access Control Scheme. Chin. J. Comput. 2017, 40, 1680–1698. [Google Scholar]
- Zhu, Y.; Huang, D.; Hu, C.J.; Wang, X. From RBAC to ABAC: Constructing Flexible Data Access Control for Cloud Storage Services. IEEE Trans. Serv. Comput. 2015, 8, 601–616. [Google Scholar] [CrossRef]
- Bai, L.; Fan, K.; Bai, Y.; Cheng, X.C.; Li, H.; Yang, Y.T. Cross-domain access control based on trusted third-party and attribute mapping center. J. Syst. Archit. 2020, 116, 101957. [Google Scholar] [CrossRef]
- Zhang, R.N.; Liu, G.; Li, S.C.; Wei, Y.H.; Wang, Q. ABSAC: Attribute-Based Access Control Model Supporting Anonymous Access for Smart Cities. Secur. Commun. Netw. 2021, 2021, 5531369. [Google Scholar] [CrossRef]
- Yang, Q.L.; Zhang, M.R.; Zhou, Y.W.; Wang, T.; Xia, Z.; Yang, B. A Non-Interactive Attribute-Based Access Control Scheme by Blockchain for IoT. Electronics 2021, 10, 1855. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A Novel Attribute-Based Access Control Scheme Using Blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Wei, D.D.; Sheng, B.Y.; Xiang, W.J. Access Control Model in PDM System Based on Role and Attribute. Mach. Des. Manuf. 2019, 346, 259–263. [Google Scholar]
- Wang, J.Y.; Zhang, W. Research on access control model and algorithm based on attribute and RBAC. J. Chin. Comput. Syst. 2022, 43, 1523–1528. [Google Scholar]
- Ghafoorian, M.; Abbasinezhad-Mood, D.; Shakeri, H. A Thorough Trust and Reputation Based RBAC Model for Secure Data Storage in the Cloud. IEEE Trans. Parallel Distrib. Syst. 2019, 30, 778–788. [Google Scholar] [CrossRef]
- Wang, J.; Wang, H.; Zhang, H.B.; Cao, N. Trust and Attribute-Based Dynamic Access Control Model for Internet of Things. In Proceedings of the 2017 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Nanjing, China, 12–14 October 2017. [Google Scholar]
- Salji, M.R.; Udzir, N.L.; Ninggal, M.L.H.; Sani, N.F.M.; Lbrahim, H. Trust-based Access Control Model with Quantification Method for Protecting Sensitive Attributes. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 695–707. [Google Scholar] [CrossRef]
- Sun, L.; Li, Y. RACAC: An Approach toward RBAC and ABAC Combining Access Control. In Proceedings of the 2019 IEEE 5th International Conference on Computer and Communications (ICCC), Chengdu, China, 6–9 December 2019. [Google Scholar]
- Blundo, C.; Cimato, S.; Siniscalchi, L. Managing Constraints in Role Based Access Control. IEEE Access 2020, 8, 140497–140511. [Google Scholar] [CrossRef]
- Li, Z.X.; Liu, L.; Wang, X. A constraint-based for virtual machine data access control in cloud platform. Commun. Comput. Inf. Sci. 2018, 901, 426–443. [Google Scholar]
- Ipate, F.; Gheorghe, M.; Lefticaru, R. Fundamental results for learning deterministic extended finite state machines from queries. Theor. Comput. Sci. 2020, 862, 160–173. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).