Forensic Analysis of TikTok Alternatives on Android and iOS Devices: Byte, Dubsmash, and Triller
Abstract
1. Introduction
- What forensically relevant data can be recovered from these apps?
- What are some of the privacy concerns associated with these apps?
- What sensitive user data do these apps collect?
- Conducted a forensic analysis of the Byte, Dubsmash, and Triller apps on Android 10 and iOS 13.3.1, which increases understanding and highlights what data these apps can access.
- Identified the locations of relevant artifacts pertaining to a mobile forensic investigation.
- Compared the privacy concerns of these apps with those of TikTok, previously identified in the literature.
- Increased understanding of how Magnet AXIOM mobile forensic investigation tool can be applied to moderately-known apps.
- Provided a forensic investigative framework for investigators who may encounter these or similar apps in future cases.
2. Literature Review
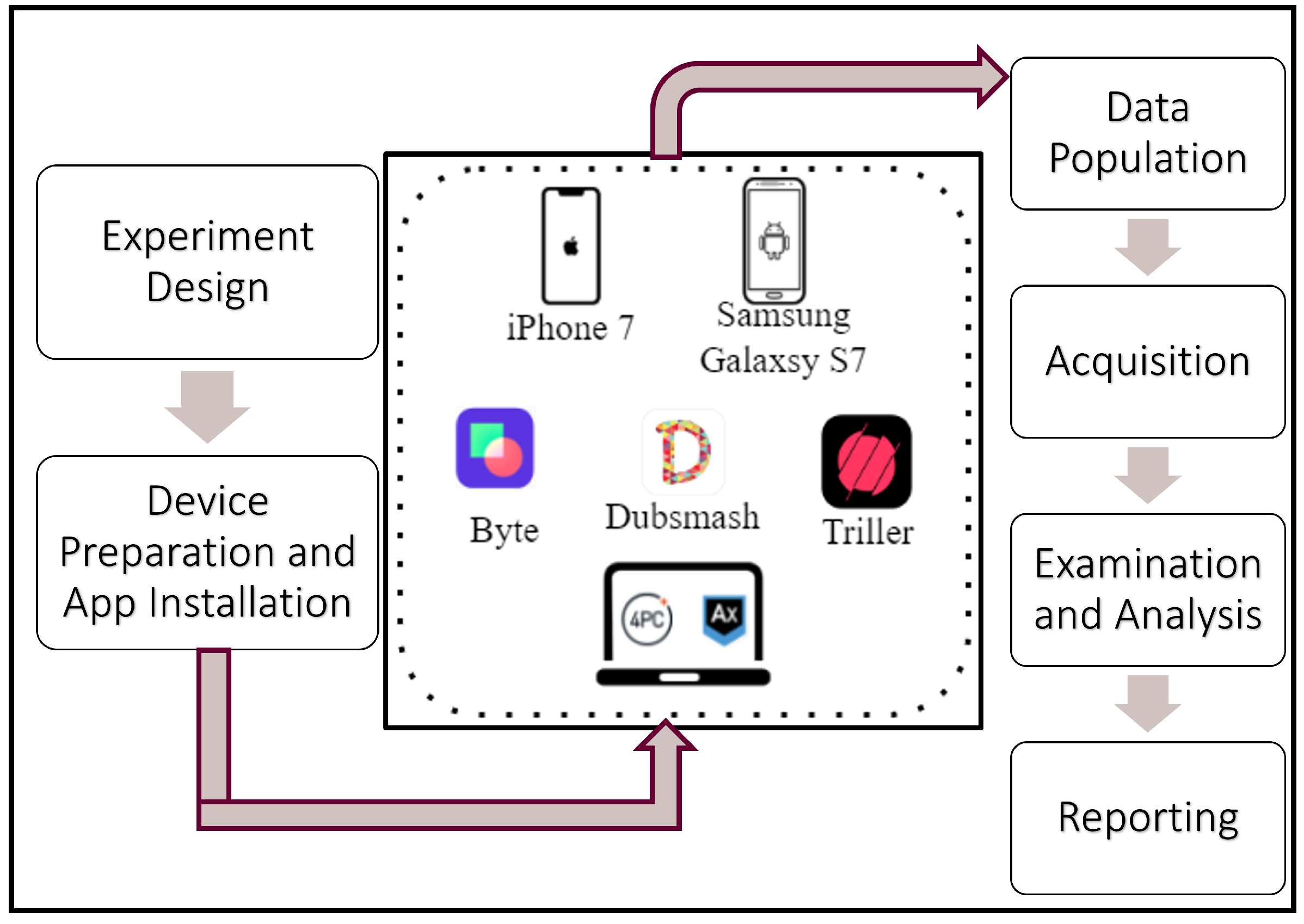
3. Methodology
3.1. Data Population
- Factory reset the iPhone 7.
- Rooted the Samsung Galaxy S7.
- Signed into the new Apple and Google accounts on the iPhone 7 and Samsung Galaxy S7, respectively.
- Populated each device with data, as necessary, following the NIST guidelines [22]. Downloaded and installed the three apps (Byte, Dubsmash, and Triller) from the App Store and the Google Play Store on the respective handsets. The app versions are given in Table 1. For each app, we did the following:
- (a)
- Created two accounts through the app, one used on the iPhone 7 (focyber21) and the other on the Samsung Galaxy S7 (focyber86).
- (b)
- Used each smartphone to interact with the app and each other.
- Performed a full acquisition of both devices.
- Examined both forensic images using AXIOM Examine.
Social Media App Interactions
- Create and set up an account on each app.
- Setting up the bio on each app.
- Create a video and post it on the app’s wall.
- –
- Video #1: Create a video, save it in the phone’s gallery, and post it on the app’s wall.
- –
- Video #2: Create and post a self-destruction video (with timer) and post it on the app’s wall.
- –
- Video #3: Create and post a video and delete it from the app’s wall.
- –
- Video #4: Create, but never post, a video, and instead save it in the app’s draft storage.
- Search for keywords using the application’s search feature.
- Chatted through the chat feature of the apps.
- –
- Saved a draft message while chatting.
- –
- Exchanged GIFs, emojis, voice notes, photos, and videos.
- Interaction with other accounts on the apps.
- –
- Follow other people’s accounts and unfollow some of them.
- –
- Follow other’s people’s accounts and block some of them.
- –
- Press the like button on some videos of the people you are following.
- –
- Press the share button on some videos of the people you are following.
- –
- Like some hashtags trending on the app (not necessarily the trending one though).
- –
- Download (or export) some of the videos of the people you are following in the phone’s local storage.
3.2. Acquisition
3.3. Analysis
4. Findings
- Login Information: artifacts in this category include the app user’s email address, password, and login tokens.
- Profile Information: artifacts in this category include the app user’s username, user ID, profile picture, bio, and birth date.
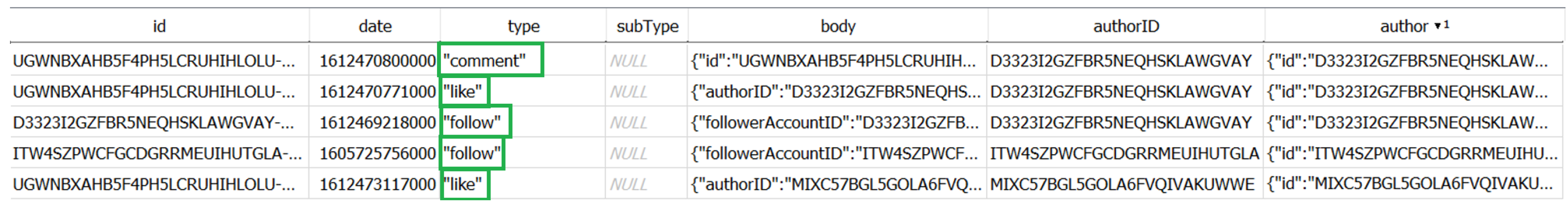
- Posting Activity: these artifacts include timestamps, posted videos, video likes and comments, deleted videos, account follow, unfollow, blocking activity, and search queries.
- Chat Information: artifacts in this category include messages sent/received through the app.
- App Usage Information: artifacts in this category include information on how the user used the app, including session information and devices used.
4.1. Byte Forensic Artifacts
4.1.1. Byte Android Artifacts
Login and Profile Information
Communication between Byte Accounts
Posting Activity
App Usage Activity
4.1.2. Byte iOS Artifacts
4.2. Dubsmash Forensic Artifacts
4.2.1. Dubsmash Android Artifacts
- The iOS account user (focyber21) sent a message to the Android user (focyber86) saying “Hey this is a chat sweetfire21”
- The Android user then replied “hi sweetfire21 dubsmash chat reply”.
- The iOS user replied saying “Can’t send anything other than text sweetfire21”.
- The iOS user sent an emoji that was not rendered by Magnet AXIOM.
- The Android user replied with an emoji.
4.2.2. Dubsmash iOS Artifacts
4.3. Triller Forensic Artifacts
4.3.1. Triller Android Artifacts
4.3.2. Triller iOS Artifacts
Login and Profile Information
5. Discussion
- The previous literature on the analysis of apps (on Android and iOS) helped authors target specific data points, directories, and formats, thus saving crucial examination time. However, the analysis of these three apps still gave us expected yet unique data points, directories, and formats.
- Adoption of NIST guidelines for mobile forensics helped us formulate guidelines for these apps and provide an investigative framework for investigators who may encounter these or similar apps in the future.
- From the literature, we observed that Snapchat Forensics [21] also employs the usage of Magnet AXIOM for analysis. Similarly, our research provides an increased understanding of this tool and how it can be applied to moderately-known apps.
- The previous literature also shows the difficulty in recovering deleted content, especially videos, which is the unique selling point of these apps. By employing our proposed methodology, any researcher would be able to extract these data points that are otherwise reported under failure in data recovery.
- Some disadvantages are clearly present as well. At the time of beginning this research, the authors did not save the privacy policies present on the websites, as these are usually present in archives. However, in the surge of discussions around a potential TikTok ban, these apps drastically changed their policies without providing access to their archive. Thus, comparing the websites and our found privacy policies proved difficult.
5.1. Implications for Research
5.2. Implications for Practice
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| XML | Extensible Markup Language |
| FTK | Forensic Toolkit |
| OS | Operating System |
| HPC | Hardware Performance counter |
| COPPA | Children’s Online Privacy Protection Act |
| GPS | Global Positioning System |
| ADB | Android Debug Bridge |
| NIST | National Institute of Standards and Technology |
| UFED | Universal Forensics Extraction Device |
| CFTT | Computer Forensics Tool Testing |
| GIF | Graphics Interchange Format |
| SIM | Subscriber Identity Module |
| URL | Uniform Resource Locator |
| JSON | JavaScript Object Notation |
| Plist | Property List |
| JPG | Joint Photographic Expert Group |
| SQL | Structured Query Language |
References
- TikTok Revenue and Usage Statistics. Available online: https://www.businessofapps.com/data/tik-tok-statistics/ (accessed on 4 May 2021).
- TikTok—Apps on Google Play. Available online: https://play.google.com/store/apps/details?id=com.zhiliaoapp.musically&hl=en_US&gl=US (accessed on 10 April 2022).
- Why Dubsmash Is Shutting Down in February 2022? Available online: https://www.makeuseof.com/why-dubsmash-is-shutting-down/ (accessed on 12 December 2021).
- Dziedzic, S. Australian Intelligence Agencies Investigate Chinese-Owned TikTok over Security Concerns. Available online: https://www.abc.net.au/news/2020-08-02/tiktok-under-investigation-in-australia-over-privacy-concerns/12513466 (accessed on 15 May 2021).
- Constine, J. How Dubsmash Revived Itself as #2 to TikTok. Available online: https://techcrunch.com/2020/01/31/dubsmash-songs/ (accessed on 10 May 2021).
- How Much Time Do People Spend on Social Media in 2021? Available online: https://techjury.net/blog/time-spent-on-social-media/#:~:text=Anaverageuserspent2,of40minperday (accessed on 15 May 2021).
- Indiablooms. Ban Chinese Video-Sharing Apps Like Likee and Tik Tok: Bangladesh Security Force Chief: Indiablooms—First Portal on Digital News Management. Available online: https://www.indiablooms.com/world-details/SA/29714/ban-chinese-video-sharing-apps-like-likee-and-tik-tok-bangladesh-security-force-chief.html (accessed on 23 July 2021).
- Suleman, M.; Soomro, T.R.; Ghazal, T.M.; Alshurideh, M. Combating Against Potentially Harmful Mobile Apps. In Proceedings of the International Conference on Artificial Intelligence and Computer Vision (AICV2021), Settat, Morocco, 28–30 June 2021; Hassanien, A.E., Haqiq, A., Tonellato, P.J., Bellatreche, L., Goundar, S., Azar, A.T., Sabir, E., Bouzidi, D., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2021; pp. 154–173. [Google Scholar]
- Ryan, F.; Fritz, A.; Impiombato, D. TikTok and WeChat.: Curating and Controlling Global Information Flows. 2020, pp. 1–70. Available online: https://s3-ap-southeast-2.amazonaws.com/ad-aspi/2020-09/TikTok%20and%20WeChat.pdf?7BNJWaoHImPVE_6KKcBP1JRD5fRnAVTZ= (accessed on 23 July 2021).
- Parker, K.; Igielnik, R. What We Know about Gen Z So Far. 2020. Available online: https://www.pewresearch.org/social-trends/2020/05/14/on-the-cusp-of-adulthood-and-facing-an-uncertain-future-what-we-know-about-gen-z-so-far-2/ (accessed on 23 July 2021).
- Khoa, N.H.; Duy, P.T.; Do Hoang, H.; Pham, V.H. Forensic analysis of TikTok application to seek digital artifacts on Android smartphone. In Proceedings of the 2020 RIVF International Conference on Computing and Communication Technologies (RIVF), Ho Chi Minh City, Vietnam, 14–15 October 2020; pp. 1–5. [Google Scholar]
- Domingues, P.; Nogueira, R.; Francisco, J.C.; Frade, M. Post-mortem digital forensic artifacts of TikTok Android App. In Proceedings of the ACM International Conference Proceeding Series, Online, 24–29 June 2020. [Google Scholar] [CrossRef]
- Domingues, P.; Nogueira, R.; Francisco, J.C.; Frade, M. Analyzing TikTok from a Digital Forensics Perspective. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2021, 12, 87–115. [Google Scholar]
- Neyaz, A.; Kumar, A.; Krishnan, S.; Placker, J.; Liu, Q. Security, Privacy and Steganographic Analysis of FaceApp and TikTok. Int. J. Comput. Sci. Secur. 2020, 14, 38–59. [Google Scholar]
- Pandela, T.; Riadi, I. Browser forensics on web-based tiktok applications. Int. J. Comput. Appl. 2020, 175, 47–52. [Google Scholar] [CrossRef]
- Ovens, K.M.; Morison, G. Forensic analysis of kik messenger on ios devices. Digit. Investig. 2016, 17, 40–52. [Google Scholar] [CrossRef][Green Version]
- Jadhav Bhatt, A.; Gupta, C.; Mittal, S. Network Forensics Analysis of iOS Social Networking and Messaging Apps. In Proceedings of the 2018 11th International Conference on Contemporary Computing, IC3 2018, Noida, India, 2–4 August 2018. [Google Scholar] [CrossRef]
- Basu, K.; Hussain, S.S.; Gupta, U.; Karri, R. COPPTCHA: COPPA Tracking by Checking Hardware-Level Activity. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3213–3226. [Google Scholar] [CrossRef]
- Salamh, F.E.; Mirza, M.M.; Hutchinson, S.; Yoon, Y.H.; Karabiyik, U. What’s on the Horizon? An In-Depth Forensic Analysis of Android and iOS Applications. IEEE Access 2021, 9, 99421–99454. [Google Scholar] [CrossRef]
- Hutchinson, S.; Shantaram, N.; Karabiyik, U. Forensic analysis of dating applications on android and ios devices. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 10–13 November 2020; pp. 836–847. [Google Scholar]
- Alyahya, T.; Kausar, F. Snapchat analysis to discover digital forensic artifacts on android smartphone. Procedia Comput. Sci. 2017, 109, 1035–1040. [Google Scholar] [CrossRef]
- Ayers, R.; Brothers, S.; Jansen, W. Guidelines on mobile device forensics (draft). NIST Spec. Publ. 2013, 800, 101. [Google Scholar]
- Computer Forensics Tool Testing Program (CFTT). Available online: https://www.nist.gov/itl/ssd/software-quality-group/computer-forensics-tool-testing-program-cftt (accessed on 23 June 2021).
- Epoch Converter. Available online: https://www.epochconverter.com/ (accessed on 23 July 2021).
- One-time TikTok Rival Byte Relaunches as Clash, an App for Video Creators and Their Top Fans. Available online: https://techcrunch.com/2021/10/12/one-time-tiktok-rival-byte-relaunches-as-clash-an-app-for-video-creators-and-their-top-fans/ (accessed on 30 August 2021).





| Application | Version (February 2021) | |
|---|---|---|
| Android | iOS | |
| Byte | 1.2.43 | 0.6.0 |
| Dubsmash | 5.19.0 | 5.20.0 |
| Triller | v19.1b8 | 22 |
| Tool | Version (February 2021) | Purpose |
|---|---|---|
| Magnet AXIOM Examine | 4.9.1.23338-1 | Viewing artifacts from forensic image |
| DB Browser for SQLite | 3.12.2 | Viewing database files |
| DCode | 5.1 | Converting timestamps |
| OS | Package Path |
|---|---|
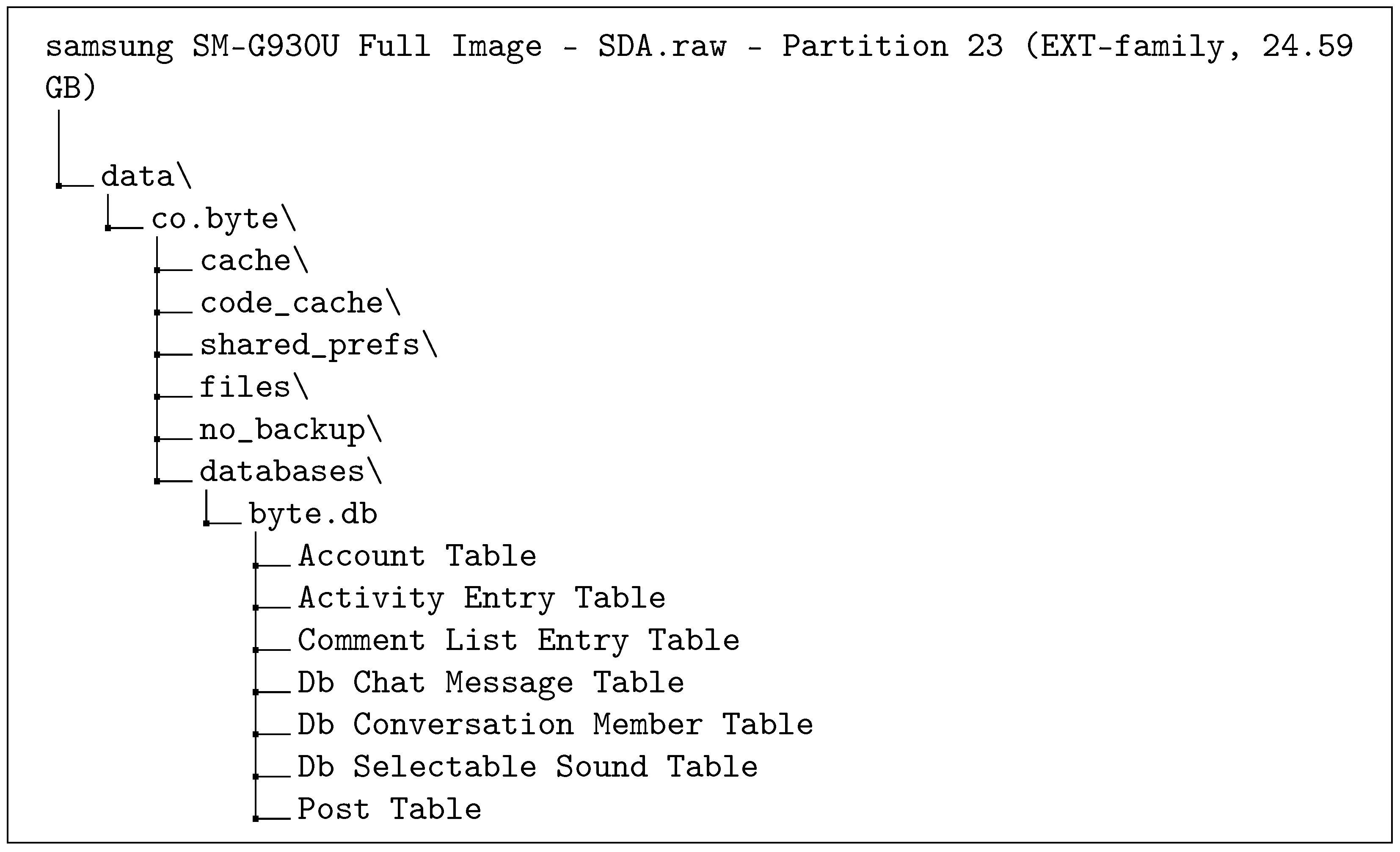
| Android | samsung SM-G930U Full Image - SDA.raw - Partition 23 (EXT-family, 24.59 GB)\data\co.byte |
| iOS | FullFileSystem.1.dar\private\var\mobile\Containers\Data\Application\23B078E4-6E9E-44E0-AEA9-E3B859503D4F |
| S.No. | Artifact Type | Android Location | Artifact Data Value/File Name |
|---|---|---|---|
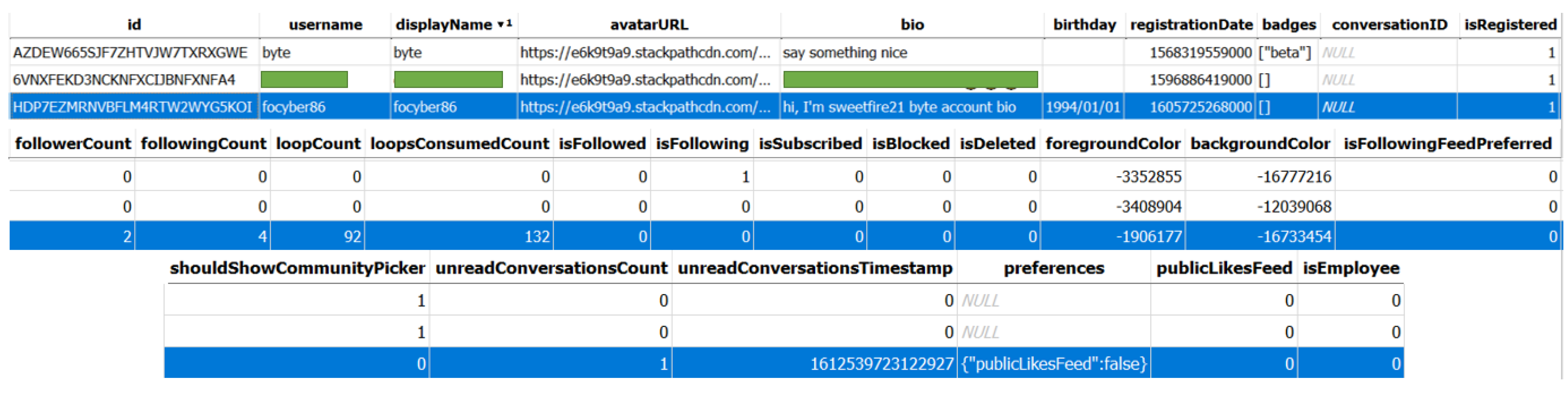
| 1 | Android Account username | *\databases\byte.db\Account | focyber86 |
| 2 | iPhone’s Account username | *\databases\byte.db\Account | focyber21 |
| 3 | Account avatarURL | *\databases\byte.db\Account | https://e6k9t9a9.stackpathcdn.com/avatars/P2GJL2KURBFGPMAI74VRWXLTYU.jpg |
| 4 | Account Registration Date and Time | *\databases\byte.db\Account | 1605725268000 (Epoch Time) |
| 5 | Account Bio (Profile) | *\databases\byte.db\Account | hi, i’m sweetfire21 byte account info |
| 6 | Account Other Info | *\databases\byte.db\Account | date of birth, conversation ID, follower count, following count, Block Count, unread Conversation Count, isEmployee |
| 7 | UserID (or authorID) of focyber86 | *\databases\byte.db\Account | |
| 8 | Conversation ID with focyber21 | *\databases\byte.db\Account | YOV2WIXTYJETBDEHP6A2GEGYUE |
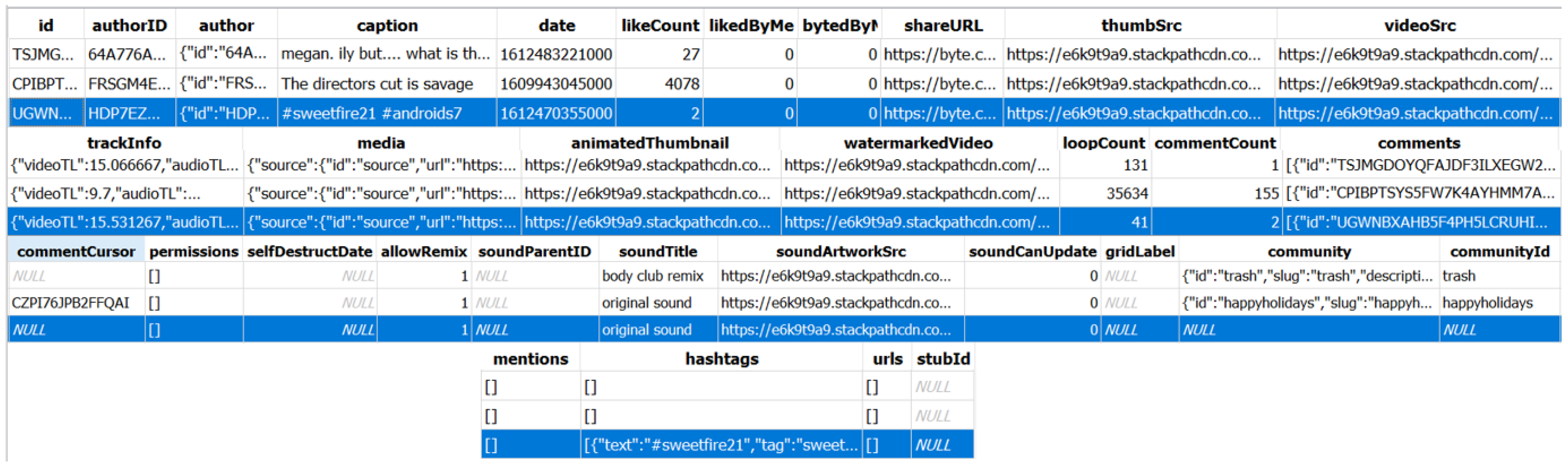
| 9 | Video #1 (recovered from Phone’s gallery) | *\cache\v | sweetfire21 android first video 02/04 hashtag: #sweetfire21 #androids7 Filename:UGWNBXAHB5F4PH5LCRUHI -HLOLU.0 |
| 10 | Video #1 (recovered from cloud I) | *\byte.db\Post\videoSrc | https://e6k9t9a9.stackpathcdn.com/videos/LCH4M4F7DFGM3CG7HLM4CBFVBQ-h264.mp4 |
| 11 | Video #1 (recovered from cloud II ) | *\byte.db\Post\cloudwatermarkedVideo | https://e6k9t9a9.stackpathcdn.com/videos/LCH4M4F7DFGM3CG7HLM4CBFVBQ-watermarked.mp4 |
| 12 | Video #1 (Byte shareable URL) | *byte.db\Post\shareURL | https://byte.co/b/JSBkLSkw3eX |
| 13 | Video #2 (Stored Locally) | *\cache\v | 6FGXFSTCABCX5NMAGBS4VVH42Y.0 |
| 14 | Video #3 (Deleted Video) | *\cache\v | ITVIXVIX5BH4LBFFBABNHC53M4.0 |
| 15 | Video #4 (Self-destruction Video) | *\cache\v | JJKHFJE42RF7FJC3YBEMAC2XDI.0 |
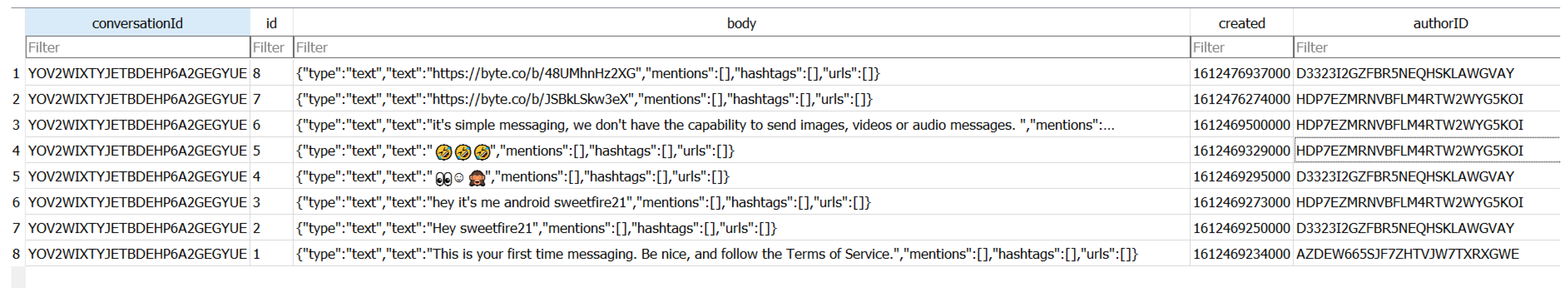
| 16 | Exchanged messages in chat | *\databases\byte.db\DbChatmessage | hey it’s me android sweetfire21 |
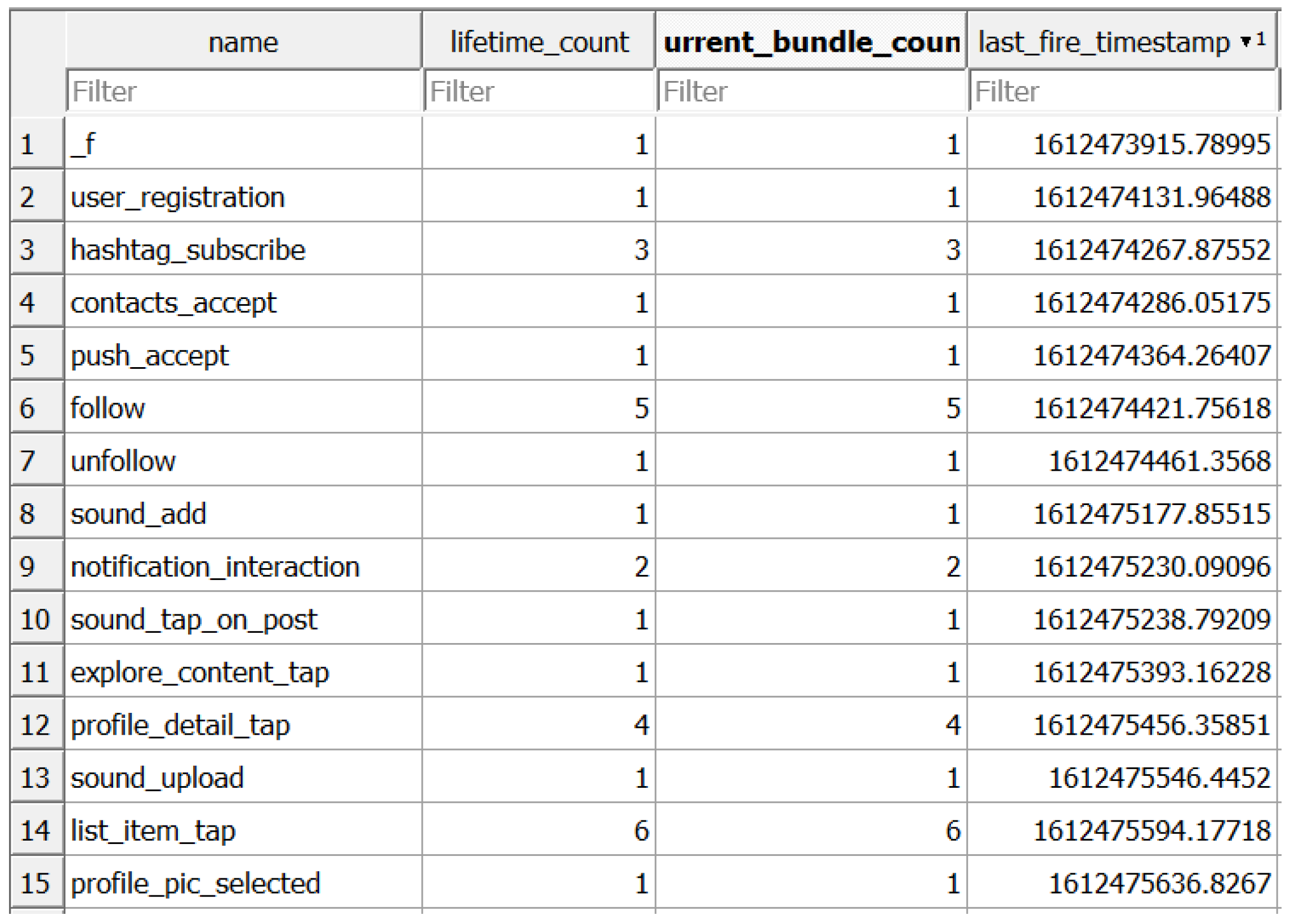
| 17 | Posting Activity | *\databases\byte.db\ActivityEntry | #likes, #follow, #comments |
| *Partition 23\data\co.byte. | |||
| S.No. | Artifact Type | iOS Location | Artifact Data Value |
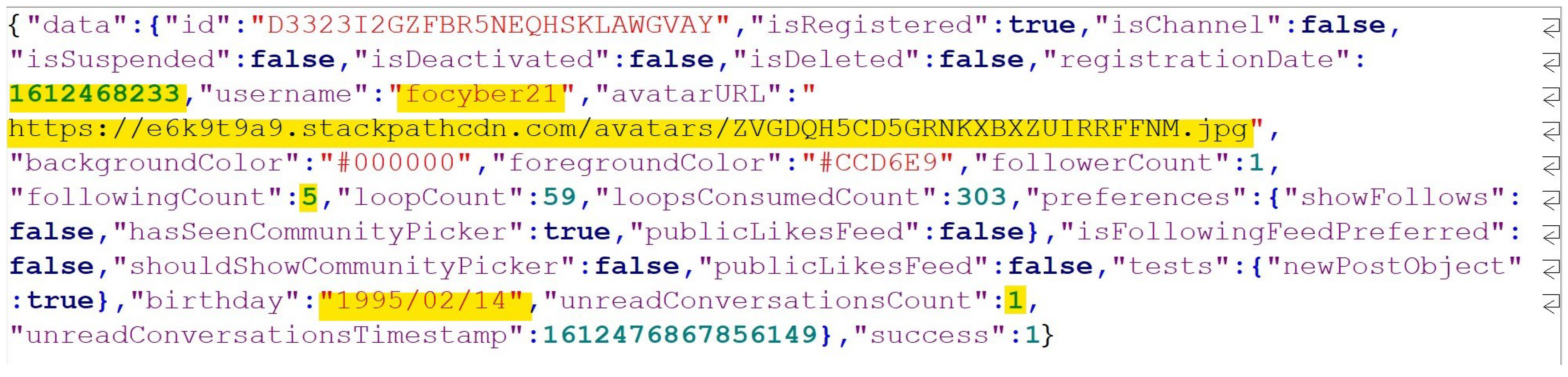
| 1 | iPhone’s Account username | *\Cache.db\cfurl\cache\receiver\data | focyber21 |
| 2 | Account avatarURL | *\Cache.db\cfurl\cache\receiver\data | https://e6k9t9a9.stackpathcdn.com/avatars/ZVGDQH5CD5GRNKXBXZUIRRFFNM.jpg |
| 3 | Account Registration Date and Time | *\Cache.db\cfurl\cache\receiver\data | 1612468233 (Epoch Time) |
| 4 | Video #1 | *\Library\Caches\videos | CNQSSNIEJBABLJZLXXY4- 6LJROM-progressive.mp4 |
| 5 | Video #2 | *\Library\Caches\videos | Y324SVBX3ZFYBAWZUTKQM7I6XU- progressive.mp4 |
| 6 | Saved Video (made by someone else) | *\Documents\videos\export\byteby Kiera.Edwards.mp4 | CNQSSNIEJBABLJZLXXY46LJROM -progressive.mp4 |
| 7 | Deleted Video | *\Library\Caches\co.byte.video\Cache.db | captioned: “Gonna delete this one sweetfire21 |
| 8 | Blocked Account | *\Library\Caches\co.byte.video\Cache.db | Blocked account display name: kaylanatsumi |
| 9 | Exchanged Messages In Chat | *\Library\Caches\co.byte.video\Cache.db | Conversation ID: YOV2WIXTYJ ETBDEHP6A2GEGYUE |
| *...23B078E4-6E9E-44E0-AEA9-E3B859503D4F... |
| OS | Package Path |
|---|---|
| Android | samsungSM-G930UFullImage-SDA.raw-Partition23(EXT-family,24.59 GB)\data\com.mobilemotion.dubsmash |
| iOS | FullFileSystem.1.dar\private\var\mobile\Containers\Data\Application\4C82EECD-902E-4393-A7F2-2E32BF63E0A7 |
| S.No. | Artifact Type | Android Location | Artifact Data Value |
|---|---|---|---|
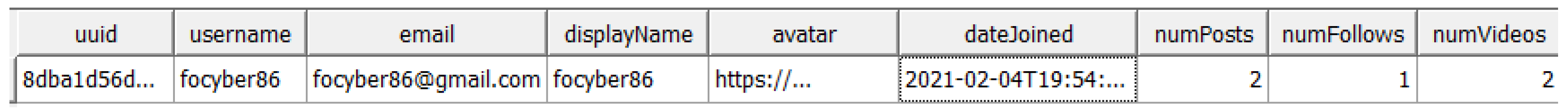
| 1 | Account username | databases\dubsmashdatabase.db | focyber86 |
| 2 | Account email address | databases\dubsmashdatabase.db | forcyber86@gmail.com |
| 3 | User’s uuid | databases\dubsmashdatabase.db | 8dba1d56d73f4914958448dd207694c8 |
| 4 | Account Profile Picture URL | databases\dubsmashdatabase.db | https://d2nr8mwohhwyyc.cloudfront.net/profile_pictures/b83d41d0-8147-4914-851d-6ded3e6ce6ba.jpeg |
| 5 | Account Registration Date | databases\dubsmashdatabase.db | 04-Feb-21 2:54:24 PM |
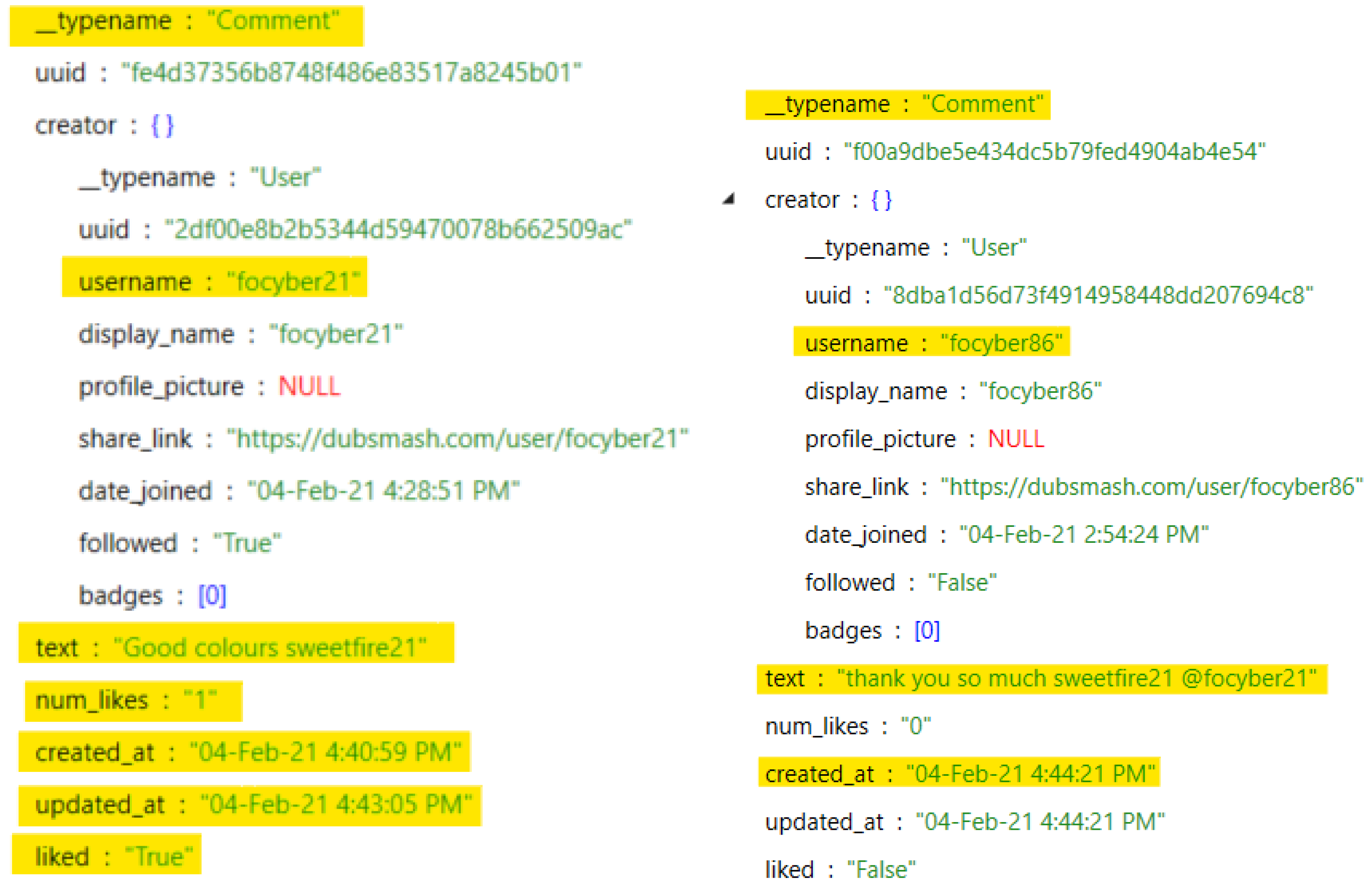
| 6 | Account Bio (Profile) | databases\dubsmashdatabase.db | hi, I’m sweetfire21 bio for dubsmash |
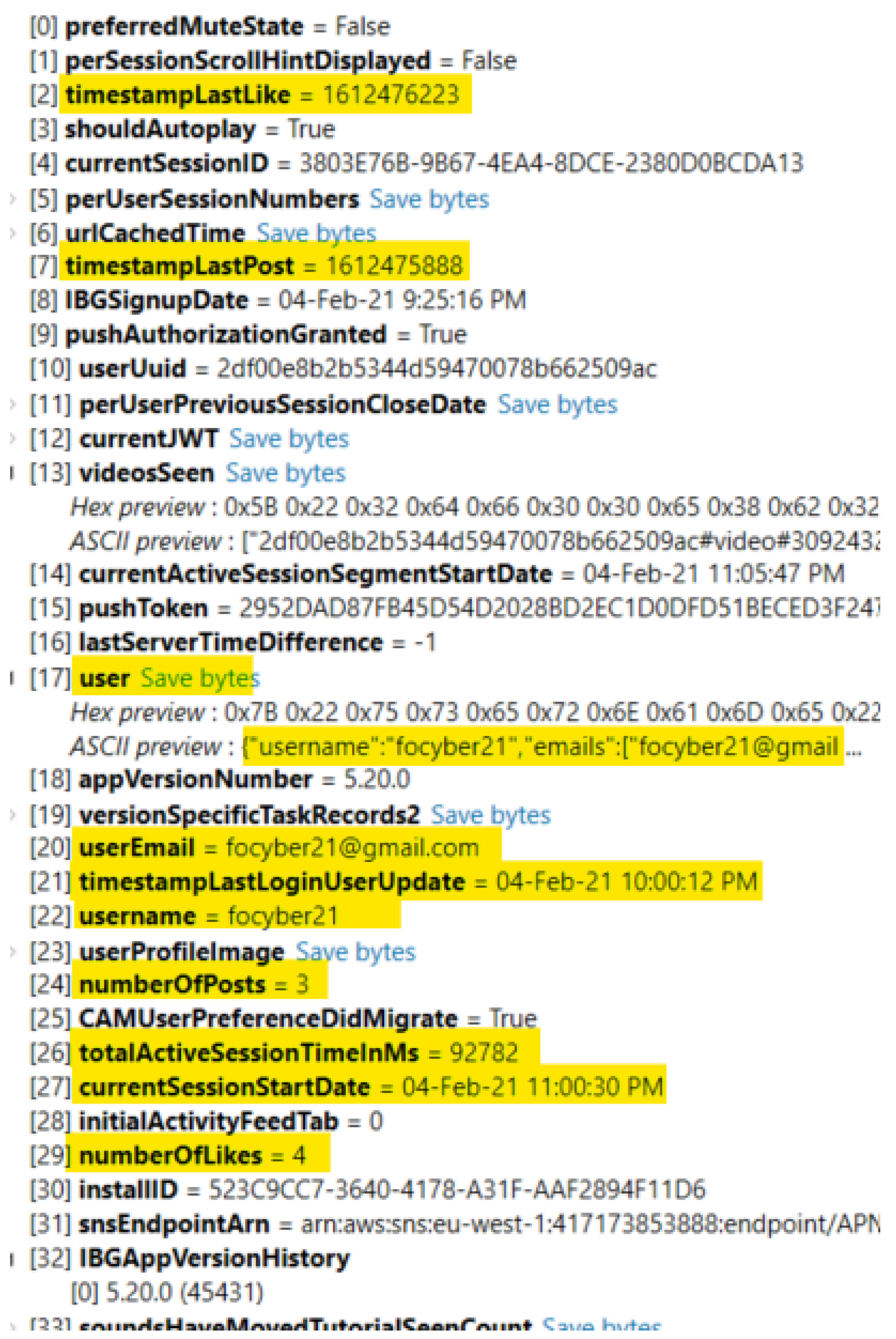
| 7 | Account Activity | databases\dubsmashdatabase.db | number of posts, number of private posts, number of videos, first and last name (if entered) |
| 8 | iPhone’s Account username | cache\httpcache\887dcbd43636363ab5103158710b63d7.1 | focyber21 |
| 9 | iPhone Account uuid | cache\httpcache\887dcbd43636363ab5103158710b63d7.1 | 2df00e8b2b5344d59470078b662509ac |
| 10 | iPhone Account Registration Date | cache\httpcache\887dcbd43636363ab5103158710b63d7.1 | 04-Feb-21 4:28:51 PM |
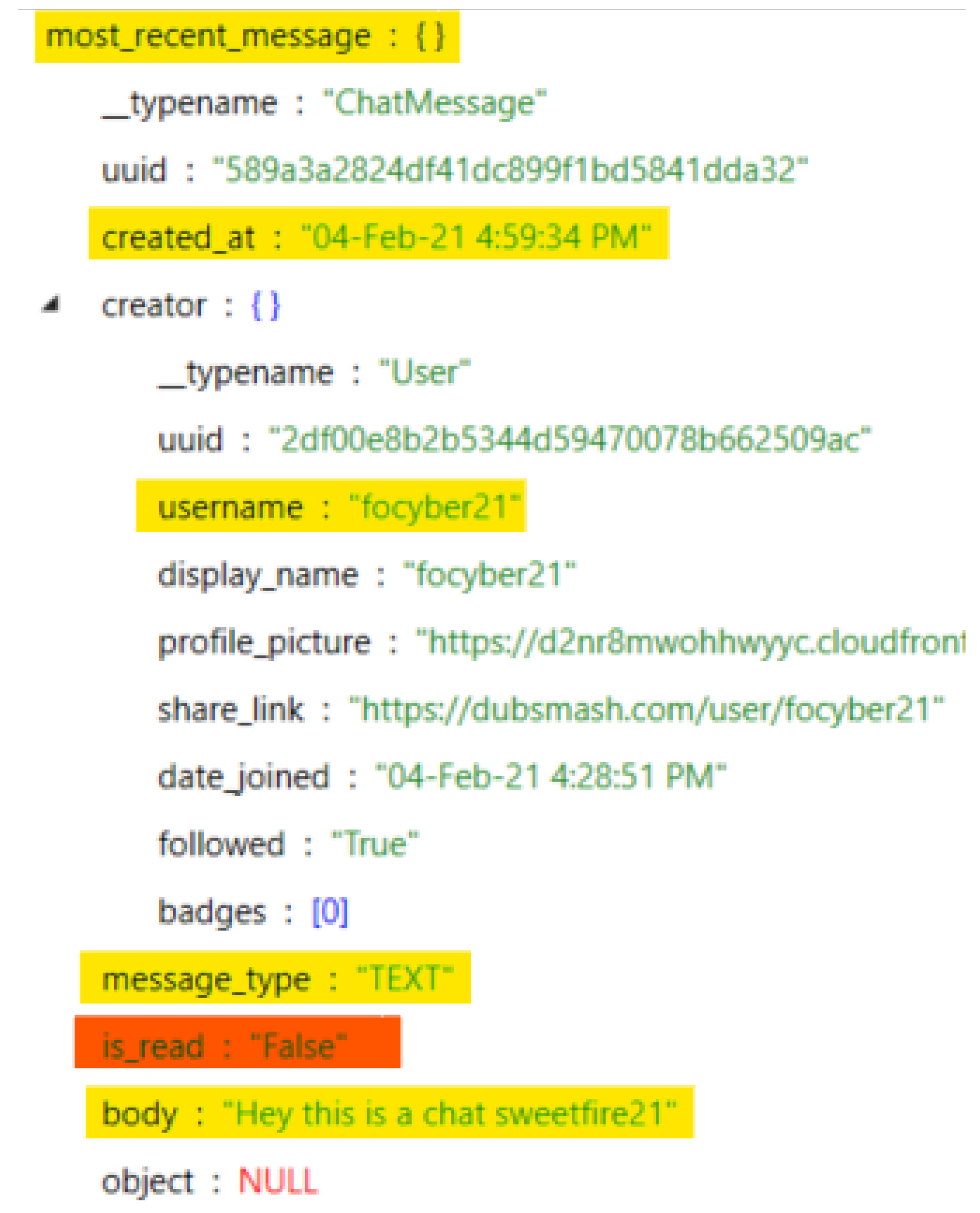
| 11 | Conversation uuid with focyber21 | cache\httpcache\e49c8c935df4d90bf243ed9f3f8601b6.1 | 1a05ed42368d4194a0c16a255bdee8f3 |
| 12 | Exchanged Messages in chat | cache\httpcache\e49c8c935df4d90bf243ed9f3f8601b6.1 | see Figure 12 |
| 13 | Search Queries | cache\httpcache\5345cde3b206ce1ad55bd06b773e1236.1, | |
| 14 | Notifications | cache\httpcache420f989fe442f13b6fcf3591924432.1 | see Figure 9 |
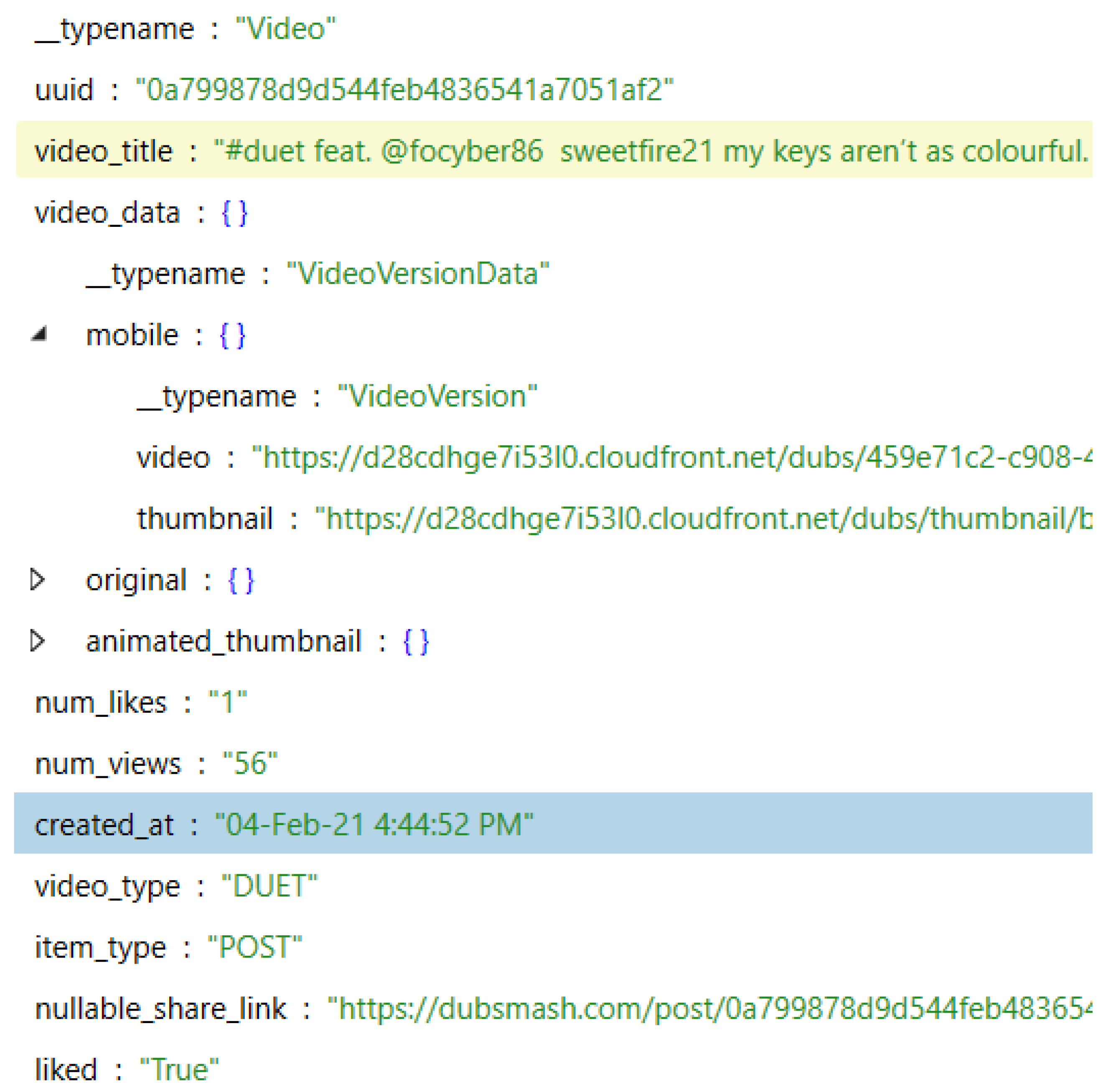
| 15 | Video #1 (app’s storage) | files\recordingcacheupload\408ca681-6e36-422b-bbf8-46872e3a49aboverlayed.mp4 | |
| 16 | Video #1 (Byte shareable URL) | cache\httpcache\758d2aa5e2169d4ba9ef136ed5b664e7.1 | |
| 17 | iPhone Account Posted Videos (URL) | cache\httpcache\7472eeb55afa96525691d944b77f32fd.1 | https://d28cdhge7i53l0.cloudfront.net/dubs/459e71c2-c908-4896-ae25-c3aa08be192b.mp4 (accessed on 6 July 2021) |
| 18 | iPhone Account Posted Videos (app’s storage) | files\downloaddir\6\25.0.1612475155868.v3.exo | |
| S.No. | Artifact Type | iOS Location | Artifact Data Value |
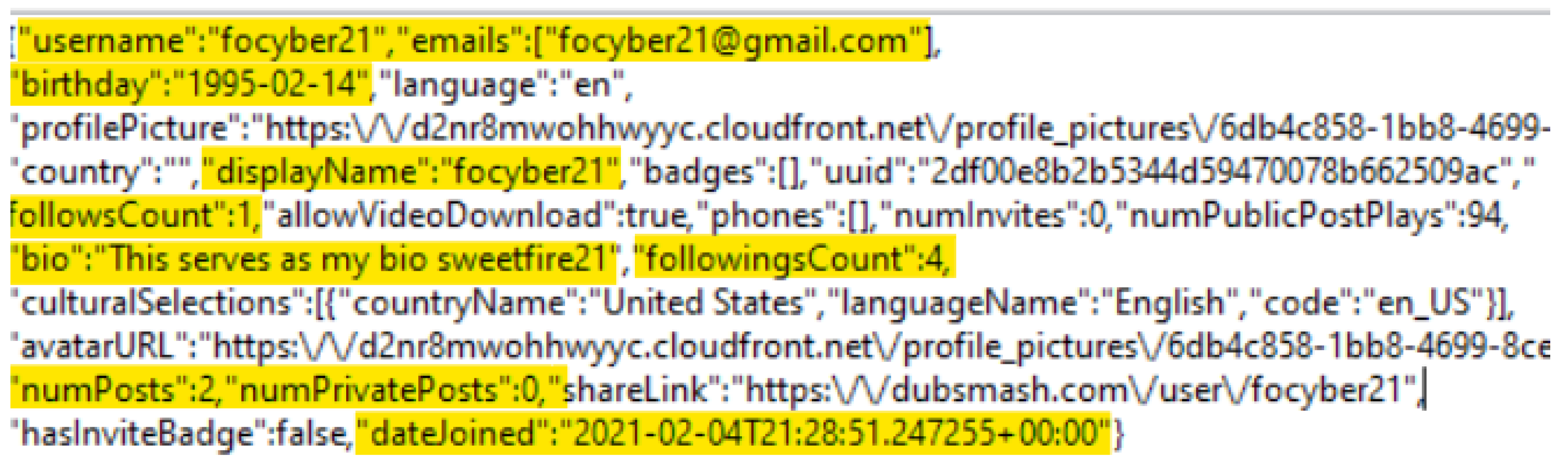
| 1 | Account username | Library\Preferences\com.mobilemotion.dubsmash.plist | focyber21 |
| 2 | Account email address | Library\Preferences\com.mobilemotion.dubsmash.plist | focyber21@gmail.com |
| 3 | User’s birthday | Library\Preferences\com.mobilemotion.dubsmash.plist | 1995-02-14 |
| 4 | User’s uuid | Library\Preferences\com.mobilemotion.dubsmash.plistt | 2df00e8b2b5344d59470078b662509ac |
| 5 | Account Profile Picture URL | Library\Preferences\com.mobilemotion.dubsmash.plist | |
| 6 | Account Registration Date | Library\Preferences\com.mobilemotion.dubsmash.plist | 2021-02-04T21:28:51.247255+00:00 |
| 7 | Account Bio (Profile) | Library\Preferences\com.mobilemotion.dubsmash.plist | This serves as my bio sweetfire21 |
| 8 | Account Activity | Library\ApplicationSupport\Google\Measurement\google-app-measurement.sql |
| OS | Package Path |
|---|---|
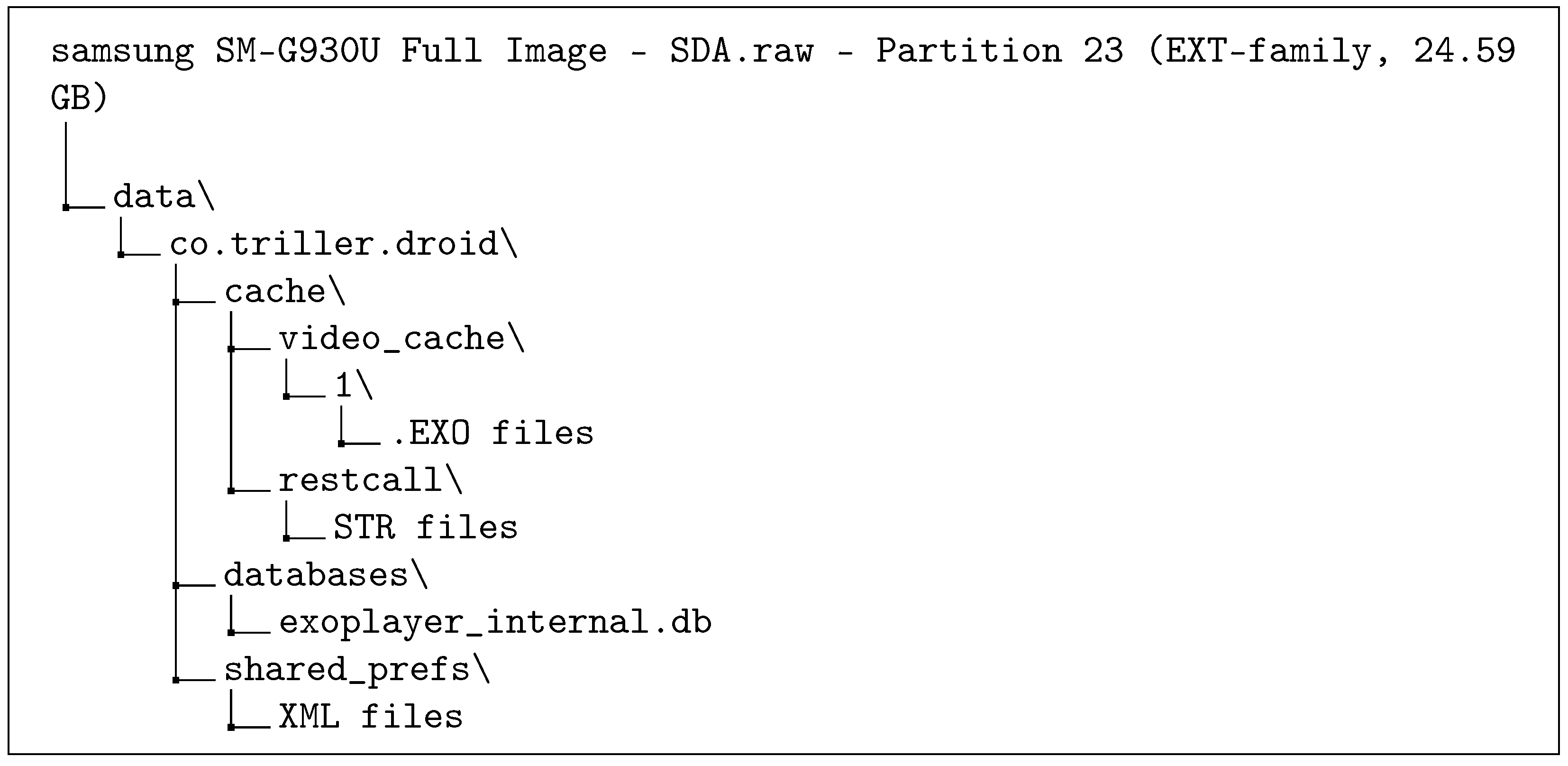
| Android | app\co.triller.droid-SRvrgEx7zBOjSRrwr8XxdQ==\base.apk |
| iOS* | FullFileSystem.1.dar\private\var\mobile\Containers\Data\Application\123AF72F-5457-4018-8A51-74675C385DF0 |
| iOS** | FullFileSystem.1.dar\private\var\Containers\Shared\AppGroup24052E8-AAC9-4742-B73C-F481D51E0915 |
| S.No. | Artifact Type | Android Location | Artifact Data Value |
|---|---|---|---|
| 1 | Account Username | \system_ce\0\accounts_ce.db | focyber86 |
| 2 | Account Email Address | \system_ce\0\accounts_ce.db | focyber86@gmail.com |
| 3 | UserID for focyber86 | \system_ce\0\accounts_ce.db | 601c505b569aa78a64c6dcfb |
| 4 | Account Picture Profile Symbol | \system_ce\0\accounts_ce.db | profile picture symbol: “P” |
| 5 | Account Registration date | \system_ce\0\accounts_ce.db | 02/04/2021 10:18:40 PM |
| 6 | Account’s Bio (Profile) | \system_ce\0\accounts_ce.db | hi, i’m sweetfire21 triller bio account |
| 7 | Account Other Information | \system_ce\0\accounts_ce.db | liked videos, followers, blocked, and following count |
| 8 | Android account username | \system_ce\0\accounts_ce.db | Focyber86 |
| 9 | Android Triller App ID | SqualkDatabaseV4.sqlite\json_messages_table2 | 7fc2dc9c-2c7b-4d5a-b5a7-62e6e8796aad@triller.app |
| 10 | Android account registration date | \system_ce\0\accounts_ce.db | 01/26/2021 7:07:50PM |
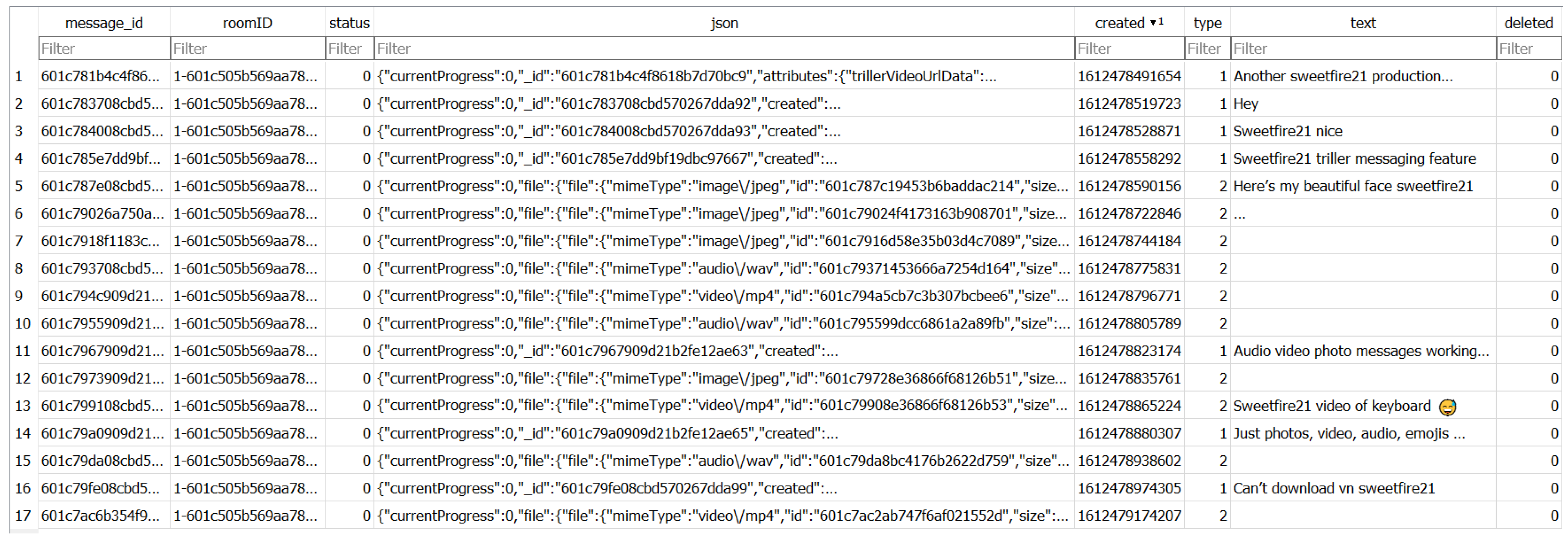
| 11 | Message ID with Focyber21 | data\co.triller.droid\databases \7fc2dc9c-2c7b-4d5a-b5a7-62e6e8796aad_Squalk_7_DB | 601c781b4c4f8618b7d70bc9 |
| 12 | Exchanged messages in chat | data\co.triller.droid\databases \7fc2dc9c-2c7b-4d5a-b5a7-62e6e8796aad_Squalk_7_DB | Text: Another sweetfire21 production... |
| 13 | Video #1 (Music Video) | data\co.triller.droid\cache\video_cache\1\518.0.1612478529621.v3.exo | Music video uploaded at 5:46 pm Triller |
| 14 | Video #2 (Sweetfire Private Video) | media\0\Android\data\co.triller.droid\files\SDK_TRILLER_FILES \7fc2dc9c-2c7b-4d5a-b5a7-62e6e8796aad | This is a private video sweetfire21 Triller video created by @focyber86 |
| 15 | Video #3 (Recovered from Cloud) | \files\projects\c3836662-9788-46f9-9646-5dd0f4e81de4\takes \1612479717050\clips\1612479717050\video.mp4 | video.mp4 |
| S.No. | Artifact Type | iOS Location | Artifact Data Value |
| 1 | iPhone’s Account username | **\Library\Preferences\group.com.triller.projectx.plist | focyber21 |
| 2 | Android’s Account username | **\Library\Preferences\group.com.triller.projectx.plist | focyber86 |
| 3 | Account’s Avatar URL | *\Library\Caches\com.triller.projectx\Cache.db | https://uploads.cdn.triller.co/v1/avatars/416923600/1612478290_avatar.jpg |
| 4 | Account Registration Date and Time | *\Library\Caches\com.triller.projectx\ Cache.db\cfurl_cache_receiver_data | 04/02/2021 at 1612477130329 (5:18:50.329 PM) |
| 5 | Account Bio (Profile) | *\Library\Caches\com.triller.projectx\Cache.db | This is my sweetfire21 triller bio |
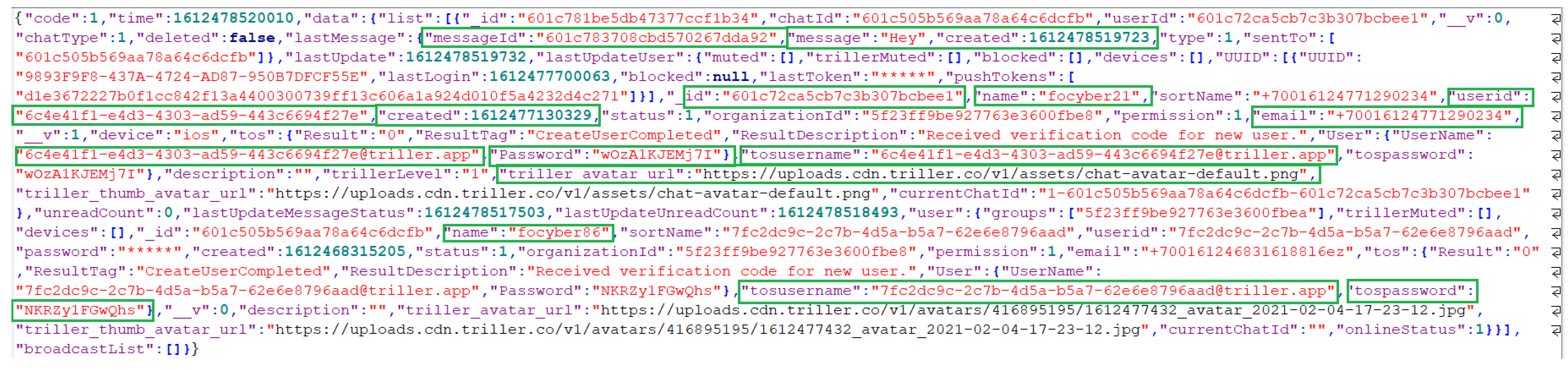
| 6 | Chats with focyber86 (Location 1) | *\Library\Caches\com.triller.projectx\ Cache.db\cfurl_cache_receiver_data | |
| 7 | Chats with focyber86 (Location 2) | **user_6c4e41f1-e4d3-4303-ad59-443c6694f27e\ SqualkDatabaseV4.sqlite\json_messages_table2 | |
| 8 | UserID of focyber21 (iPhone user) | -Same as above - | 601c72ca5cb7c3b307bcbee1 |
| 9 | UserID of focyber86 (Android user) | -Same as above - | 601c505b569aa78a64c6dcfb |
| 10 | Triller ID of focyber86 (Android user) | -Same as above - | 7fc2dc9c-2c7b-4d5a-b5a7-62e6e8796aad@triller.app |
| 11 | Triller ID of focyber21 (iPhone user) | -Same as above - | 6c4e41f1-e4d3-4303-ad59-443c6694f27e@triller.app |
| 12 | Draft Message | *\Library\Preferences\group.com.triller.projectx.plist | |
| 13 | Video shared over chat | ** \user_6c4e41f1-e4d3-4303-ad59-443c6694f27e\files\videos | 601c7ac2ab747f6af021552d_VIDEO_20210204_175244.mp4 |
| 14 | Audio shared over chat | ** \user_6c4e41f1-e4d3-4303-ad59-443c6694f27e\files\audios\ | audio_gNdECAW7_DTS_04-02-2021_DTE.wav |
| 15 | Image shared over chat | ** \user_6c4e41f1-e4d3-4303-ad59-443c6694f27e\files\images\ | 601c7916d58e35b03d4c7089_IMAGE_20210204_174542.jpg |
| 16 | Video #4(Private Video) | *\Library\Caches\com.triller.projectx\Cache.db | This is a private video sweetfire21 Triller video created by @focyber21 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Keim, Y.; Hutchinson, S.; Shrivastava, A.; Karabiyik, U. Forensic Analysis of TikTok Alternatives on Android and iOS Devices: Byte, Dubsmash, and Triller. Electronics 2022, 11, 2972. https://doi.org/10.3390/electronics11182972
Keim Y, Hutchinson S, Shrivastava A, Karabiyik U. Forensic Analysis of TikTok Alternatives on Android and iOS Devices: Byte, Dubsmash, and Triller. Electronics. 2022; 11(18):2972. https://doi.org/10.3390/electronics11182972
Chicago/Turabian StyleKeim, Yansi, Shinelle Hutchinson, Apoorva Shrivastava, and Umit Karabiyik. 2022. "Forensic Analysis of TikTok Alternatives on Android and iOS Devices: Byte, Dubsmash, and Triller" Electronics 11, no. 18: 2972. https://doi.org/10.3390/electronics11182972
APA StyleKeim, Y., Hutchinson, S., Shrivastava, A., & Karabiyik, U. (2022). Forensic Analysis of TikTok Alternatives on Android and iOS Devices: Byte, Dubsmash, and Triller. Electronics, 11(18), 2972. https://doi.org/10.3390/electronics11182972








