Routing Protocol for MANET Based on QoS-Aware Service Composition with Dynamic Secured Broker Selection
Abstract
:1. Introduction
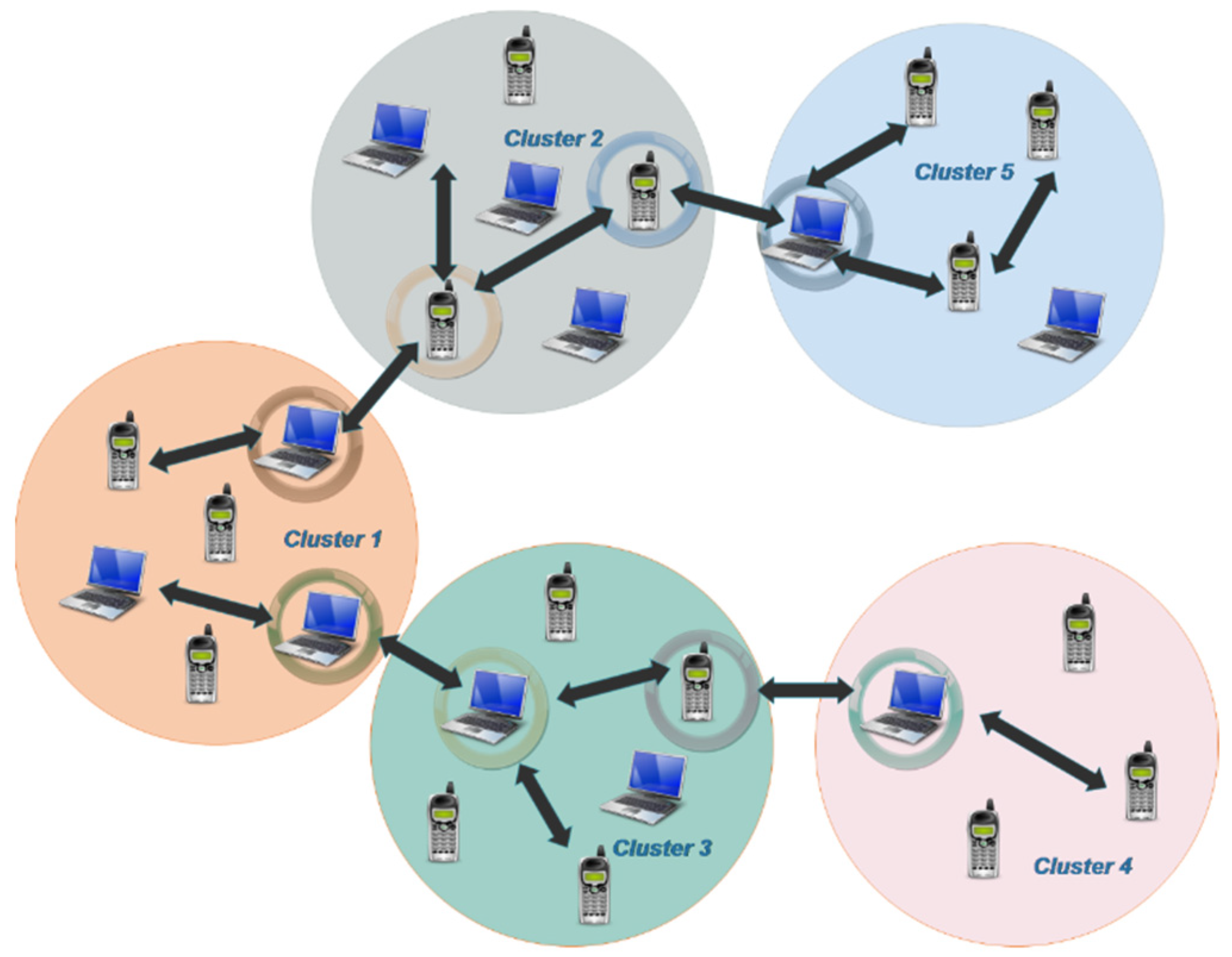
- Initially, an efficient cluster formation mechanism, namely the MCHG algorithm, is introduced to balance the load in the network.
- A dynamic broker selection based on the QoS metrics is formulated to select an active broker and routing path.
- A secured communication link within the intra-cluster is designed based on symmetric encryption and key-exchange protocol to prevent intrusion in the network.
2. Related Work
- Maximum utilization of a resource such as battery power;
- Header should be capable of withstanding any packet traffic;
- Load balancing;
- Lesser node mobility.
3. Problem Definition
- Cluster formation of mobile nodes;
- Routing protocol;
- Dynamic broker selection;
- Secure broker selection.
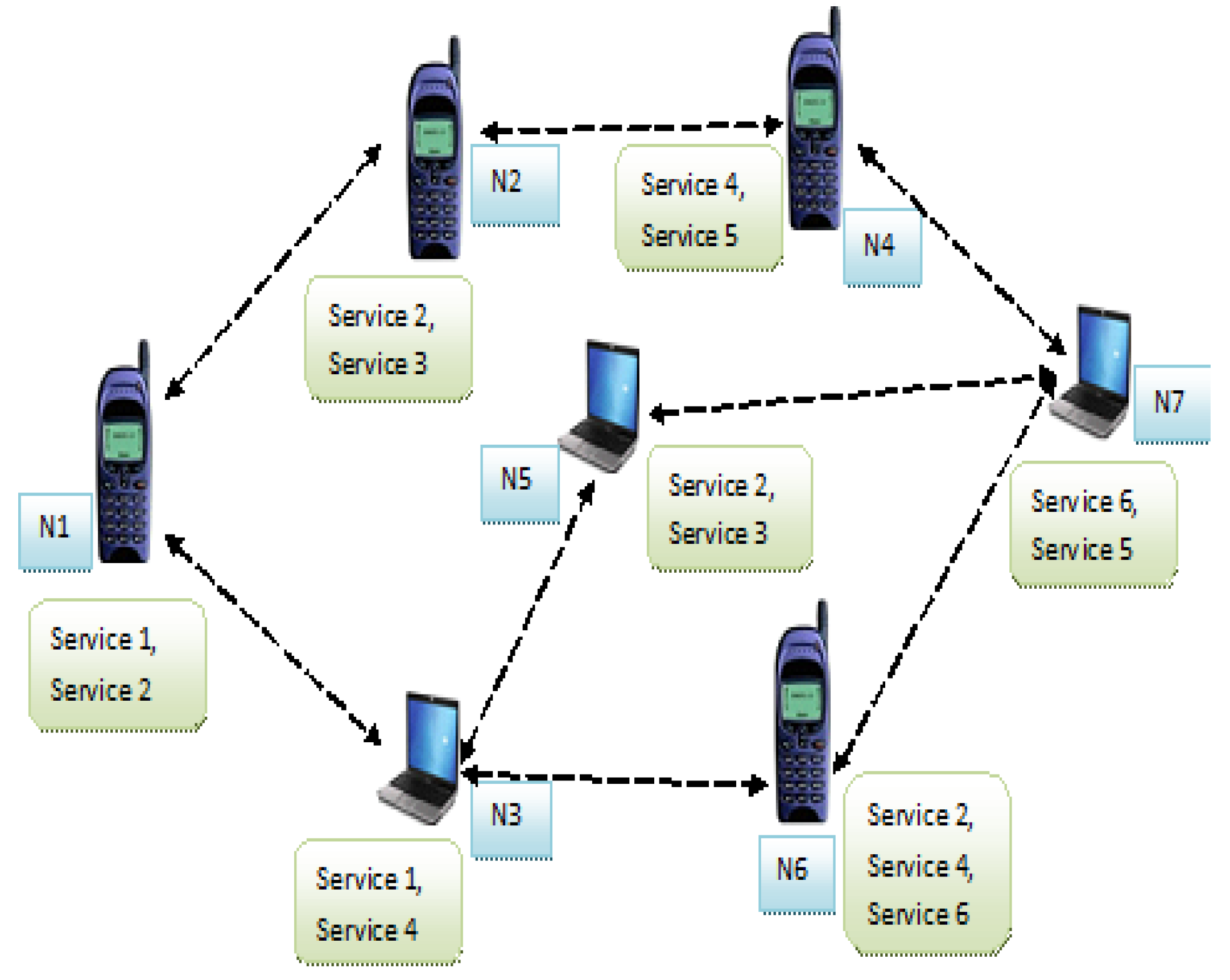
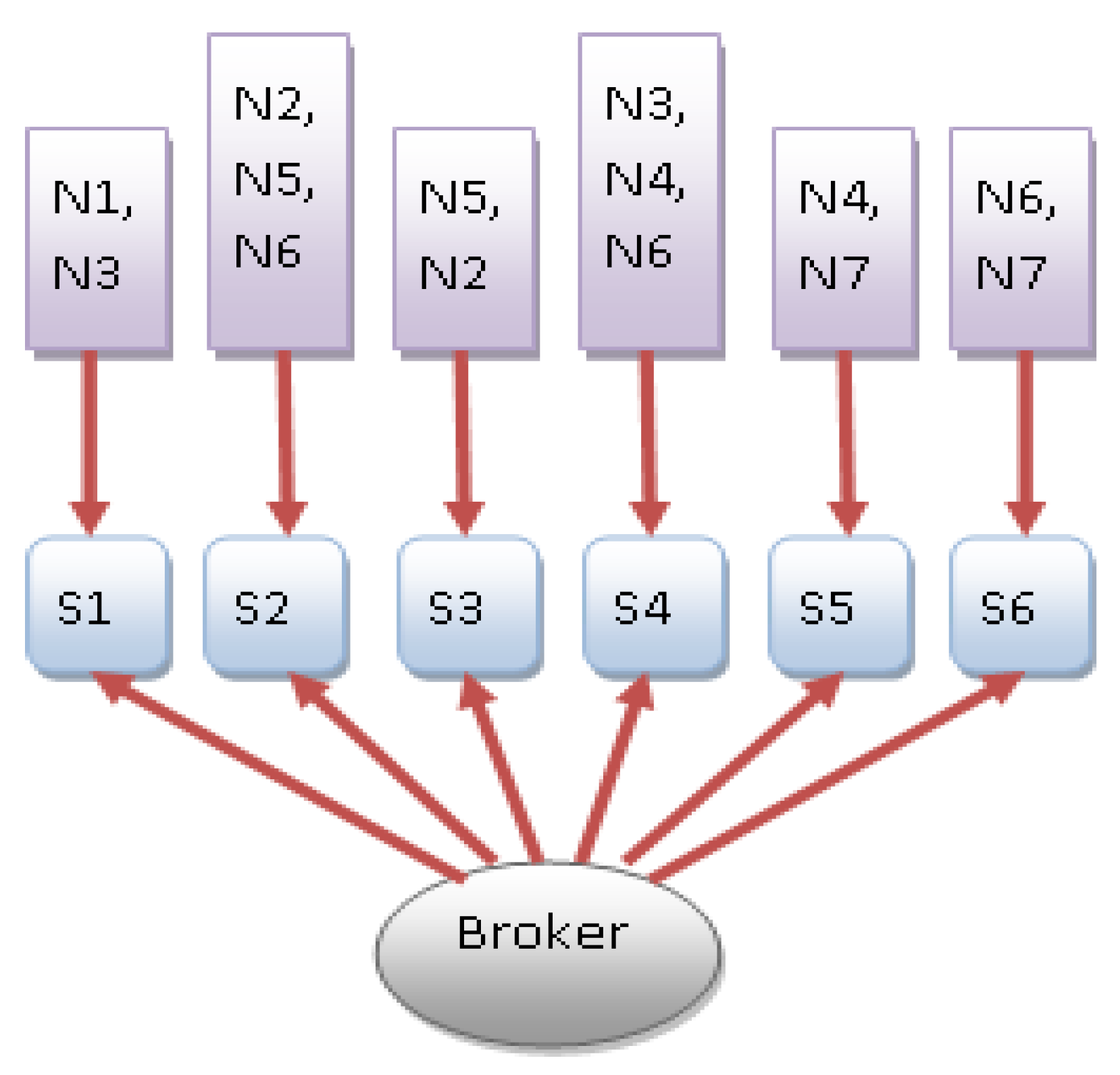
4. QoSDSBS System Model
- N1 = [Service 1, Service 2]
- N2 = [Service 2, Service 3]
- N3 = [Service 1, Service 4]
- N4 = [Service 4, Service 5]
- N5 = [Service 2, Service 3]
- N6 = [Service 2, Service 4, Service 6]
- N7 = [Service 5, Service 6]
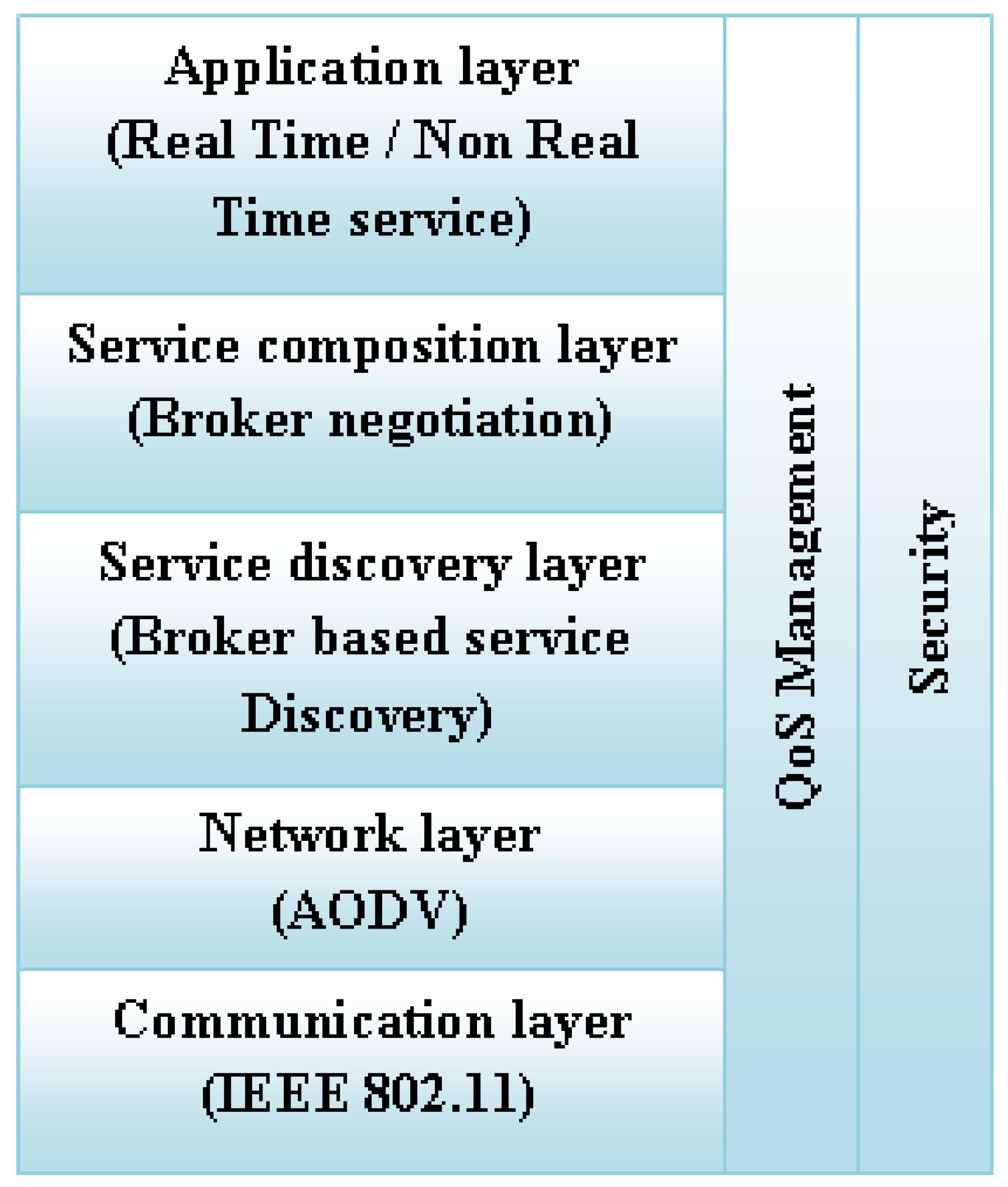
5. Proposed System
5.1. Cluster Formation of Mobile Nodes
5.2. Routing Protocol
5.3. Dynamic Broker Selection
| Algorithm 1 Broker Formation |
| 1. Input: Consider nodes, Calculate the QoS metrics and compute 2. For every node n in N 3. If > where // is the neighbor set of nodes n 4. Then 5. Broker = 6. For every weight factor // is the set of uncovered nodes 7. If distance (Broker, z) <= Broker transmission-range 8. Then 9. Broker Z = Broker 10. End for 11. End for |
- Availability
- Data Packet Delivery Rate
- Data Packet Loss Rate
- Comparative Mobility
- Energy
- Network Load Balancing
- Delay
- Throughput
- Node Memory Capacity
5.4. Secure Broker Selection
| Algorithm 2 Intra-Cluster Security |
| 1. Input: Select Prime Number “p”, an element g which is the prime root of “p”, and consider two nodes A and B 2. For any “n” node in the cluster 3. “A” select random integer X.A. < p 4. Compute 5. YA = 6. Set 7. Private KeyA = XA 8. “B” select random integer X.B. < p 9. Compute 10. YB = 11. Set 12. Private KeyB = XB 13. Broadcast “Y” 14. “A” compute 15. K = 16. “B” compute 17. K = 18. End for |
| Algorithm 3 Inter-Cluster Security |
| 1. For any “n” node 2. If (broker-node + Wn) exceeds then //Wn is the Net Weight of a particular node 3. Listen (Address, Channel) 4. If (Listen + Wn) exceeds then 5. Update (Routing Table) 6. End if 7. End if 8. If (Listen) then 9. Stegnomsg (Listen) //Compute steganography for listen hello message 10. Find (Channel, Address) 11. End if 12. If (Update) 13. Update Routing table 14. End if 15. End for |
6. Simulation and Results Discussion
6.1. Simulation Setup
6.2. Results and Discussion
6.2.1. Bandwidth vs. End-to-End Delay
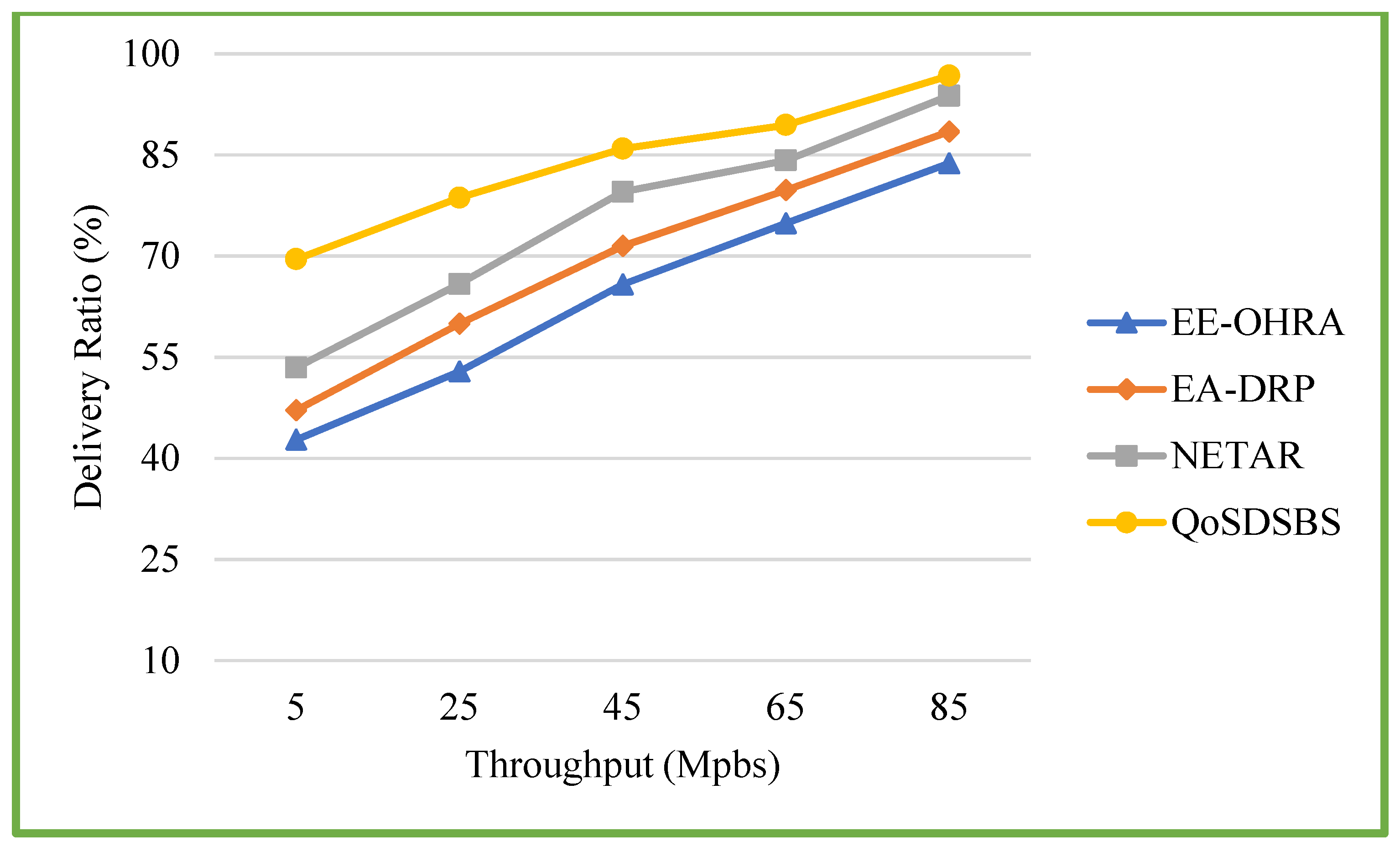
6.2.2. Throughput vs. Delivery Ratio
6.2.3. Lifetime with Routing Control Overhead
6.2.4. Throughput vs. Delay
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Wang, N.-C.; Chen, J.-S.; Huang, Y.-F.; Su, Y.-L. A power-aware multicast routing protocol for mobile ad hoc networks with mobility prediction. Wirel. Pers. Commun. 2005, 43, 1479–1497. [Google Scholar] [CrossRef]
- Vazifehdan, J.; Prasad, R.V.; Onur, E.; Niemegeers, I. Energy-aware routing algorithms for wireless ad hoc networks with heterogeneous power supplies. Comput. Netw. 2011, 55, 3256–3274. [Google Scholar] [CrossRef]
- Chen, M.; Tan, T.H.; Sun, J.; Liu, Y.; Pang, J.; Li, X. Verification of functional and non-functional requirements of web service composition. In International Conference on Formal Engineering Methods; Springer: Berlin/Heidelberg, Germany, 2013; pp. 313–328. [Google Scholar]
- Karunamurthy, R.; Khendek, F.; Glitho, R.H. A novel architecture for Web service composition. J. Netw. Comput. Appl. 2012, 35, 787–802. [Google Scholar] [CrossRef]
- Duarte Filho, N.F.; Barbosa, E.F. A contribution to the establishment of reference architectures for mobile learning environments. IEEE Rev. Iberoam. Tecnol. Del Aprendiz. 2015, 10, 234–241. [Google Scholar]
- Romero, O.J. Cognitively-inspired agent-based service composition for mobile and pervasive computing. In International Conference on AI and Mobile Services; Springer: Cham, Switzerland, 2019; pp. 101–117. [Google Scholar]
- Saghian, M.; Ravanmehr, R. Efficient QoS-Aware Middleware for Resource Discovery in Mobile Ad Hoc Networks. Adhoc Sens. Wirel. Netw. 2019, 43, 283–312. [Google Scholar]
- Veeresh, P.; Sam, R.P.; Bin, C.S. Reliable fault tolerance system for service composition in mobile Ad Hoc network. Int. J. Electr. Comput. Eng. (2088–8708) 2019, 9, 2523–2533. [Google Scholar]
- Manoranjan, G.; Rathnamma, M.V.; Ramana, V.V.; Anil, G.R. Service Composition in Mobile Ad Hoc Networks (MANET’s) with the Help of Optimal QoS Constraints. In International Conference on Computational and Bio Engineering; Springer: Cham, Switzerland, 2019; pp. 375–390. [Google Scholar]
- Kaur, M. Quality of Service Maintenance in MANET with Improved QASEC Technique. In Proceedings of the 2022 6th International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 28–30 April 2022; pp. 690–696. [Google Scholar]
- Thirunavukkarasu, V.; Kumar, A.S.; Prakasam, P. Cluster and angular based energy proficient trusted routing protocol for mobile ad-hoc network. Peer-to-Peer Netw. Appl. 2022, 1–13. [Google Scholar] [CrossRef]
- Kaisar, S.; Kamruzzaman, J.; Karmakar, G.; Rashid, M. Decentralized content sharing in mobile ad-hoc networks: A survey. Digit. Commun. Netw. 2022, in press. [Google Scholar] [CrossRef]
- Jain, A.; Thakur, D.S.; Malviya, V. A novel approach for gateway node election method for clustering in wireless mobile ad hoc networks. In International Conference on Advanced Computing Networking and Informatics; Springer: Singapore, 2019; pp. 205–214. [Google Scholar]
- Zeng, L.; Benatallah, B.; Dumas, M.; Kalagnanam, J.; Sheng, Q.Z. Quality driven web services composition. In Proceedings of the 12th International Conference on World Wide Web, Budapest, Hungary, 20–24 May 2003; pp. 411–421. [Google Scholar] [CrossRef]
- Aggarwal, R.; Verma, K.; Miller, J.; Milnor, W. Constraint driven web service composition in METEOR-S. In Proceedings of the IEEE International Conference on Services Computing, 2004. (SCC 2004), Shanghai, China, 15–18 September 2004; pp. 23–30. [Google Scholar] [CrossRef]
- Feng, X.; Ren, Y.; Hu, J.; Wu, Q.; Jia, Y. A model for service composition with multiple QoS constraints. In Proceedings of the 2007 International Conference on Computing: Theory and Applications (ICCTA’07), Kolkata, India, 5–7 March 2007; pp. 208–213. [Google Scholar] [CrossRef]
- Zeng, L.; Benatallah, B.; Ngu, A.; Dumas, M.; Kalagnanam, J.; Chang, H. QoS-aware middleware for web services composition. IEEE Trans. Softw. Eng. 2004, 30, 311–327. [Google Scholar] [CrossRef]
- Amudhavel, J.; Padmapriya, S.; Nandhini, R.; Kavipriya, G.; Dhavachelvan, P.; Venkatachalapathy, V.S.K. Recursive ant colony optimization routing in wireless mesh network. In Proceedings of the Second International Conference on Computer and Communication Technologies; Springer: New Delhi, India, 2016; pp. 341–351. [Google Scholar] [CrossRef]
- Pushpalatha, M.; Srinivasan, M.; Ramadevi, P. A QoS Multicast Protocol Optimization for MANET in Wireless Communications. Mater. Today Proc. 2021, in press. [Google Scholar] [CrossRef]
- Xiong, P.; Fan, Y.; Zhou, M. Web service configuration under multiple quality-of-service attributes. IEEE Trans. Autom. Sci. Eng. 2009, 6, 311–321. [Google Scholar] [CrossRef]
- Singh, S.; Pise, A.; Alfarraj, O.; Tolba, A.; Yoon, B. A cryptographic approach to prevent network incursion for enhancement of QoS in sustainable smart city using MANET. Sustain. Cities Soc. 2021, 79, 103483. [Google Scholar] [CrossRef]
- Velusamy, B.; Karunanithy, K.; Sauveron, D.; Akram, R.; Cho, J. Multi-objective function-based node-disjoint multipath routing for mobile ad hoc networks. Electronics 2021, 10, 1781. [Google Scholar] [CrossRef]
- Basu, P.; Ke, W.; Little, T. A novel approach for execution of distributed tasks on mobile ad hoc networks. In Proceedings of the 2002 IEEE Wireless Communications and Networking Conference Record. WCNC 2002 (Cat. No. 02TH8609), Orlando, FL, USA, 17–21 March 2002; Volume 2, pp. 579–585. [Google Scholar] [CrossRef]
- Baker, D.; Ephremides, A. The architectural organization of a mobile radio network via a distributed algorithm. IEEE Trans. Commun. 1981, 29, 1694–1701. [Google Scholar] [CrossRef]
- Rajakumar, R.; Dinesh, K.; Vengattaraman, T. An energy-efficient cluster formation in wireless sensor network using grey wolf optimisation. Int. J. Appl. Manag. Sci. 2021, 13, 124–140. [Google Scholar] [CrossRef]
- Nurlan, Z.; Zhukabayeva, T.; Othman, M. EZ-SEP: Extended Z-SEP routing protocol with hierarchical clustering approach for wireless heterogeneous sensor network. Sensors 2021, 21, 1021. [Google Scholar] [CrossRef]
- Yang, X.; Chen, Q.; Chen, C.; Zhao, J. Improved ZRP routing protocol based on clustering. Procedia Comput. Sci. 2018, 131, 992–1000. [Google Scholar] [CrossRef]
- Thenmozhi, R.; Karthikeyan, P.; Vijayakumar, V.; Keerthana, M.; Amudhavel, J. Backtracking performance analysis of Internet protocol for DDoS flooding detection. In Proceedings of the 2015 International Conference on Circuits, Power and Computing Technologies [ICCPCT-2015], Nagercoil, India, 19–20 March 2015; pp. 1–4. [Google Scholar] [CrossRef]
- Rajeswari, M.; Sambasivam, G.; Balaji, N.; Basha, M.S.; Vengattaraman, T.; Dhavachelvan, P. Appraisal and analysis on various web service composition approaches based on QoS factors. J. King Saud Univ.—Comput. Inf. Sci. 2014, 26, 143–152. [Google Scholar] [CrossRef]
- Perkins, C.; Belding-Royer, E.; Das, S. RFC3561: Ad Hoc On-Demand Distance Vector (AODV) Routing. 2003. Available online: https://www.rfc-editor.org/rfc/rfc3561.html (accessed on 5 July 2022).
- Perkins, C.E.; Bhagwat, P. Highly dynamic destination-sequenced distance-vector routing (DSDV) for mobile computers. ACM SIGCOMM Comput. Commun. Rev. 1994, 24, 234–244. [Google Scholar] [CrossRef]
- Chakraborty, D.; Joshi, A.; Yesha, Y.; Finin, T. GSD: A novel group-based service discovery protocol for MANETS. In Proceedings of the 4th International Workshop on Mobile and Wireless Communications Network, Stockholm, Sweden, 9–11 September 2002; pp. 140–144. [Google Scholar]
- Gao, Z.; Wang, L.; Yang, X.; Wen, D. PCPGSD: An enhanced GSD service discovery protocol for MANETs. Comput. Commun. 2006, 29, 2433–2445. [Google Scholar] [CrossRef]
- NS-2 Simulator. Available online: https://www.isi.edu/nsnam/ns/ (accessed on 5 July 2022).
- Broch, J.; Maltz, D.A.; Johnson, D.B.; Hu, Y.-C.; Jetcheva, J. A performance comparison of multi-hop wireless ad hoc network routing protocols. In Proceedings of the 4th Annual ACM/IEEE International Conference on Mobile Computing and Networking, Dallas, TX, USA, 25–30 October 1998; pp. 85–97. [Google Scholar]
- Kumar, S.V.; Anuratha, V. Energy Efficient Routing for Manet Using Optimized Hierarchical Routing Algorithm (Eeohra). Int. J. Sci. Technol. Res. 2020, 9, 2. [Google Scholar]
- Rajendra Prasad, P.S. Efficient Performance Analysis of Energy Aware on Demand Routing Protocol in Mobile Ad-Hoc Network. Eng. Rep. 2 2020, 3, e12116. [Google Scholar]
- Usha, M.S.; Ravishankar, K.C. Implementation of trust-based novel approach for security enhancements in MANETs. SN Comput. Sci. 2021, 2, 1–7. [Google Scholar] [CrossRef]




| P. Name | Node ID | Services | QoS Metrics | |||||||
|---|---|---|---|---|---|---|---|---|---|---|
| S1 | S2 | S3 | S4 | S5 | S6 | Cost | A | T(s) | ||
| SP1 | 10.10.1.1 | √ | √ | √ | 245 | 0.90 | 0.5 | |||
| SP2 | 10.10.12.2 | √ | √ | 754 | 0.87 | 0.9 | ||||
| SP3 | 10.10.32.5 | √ | √ | √ | √ | 438 | 0.70 | 1.4 | ||
| SP4 | 10.10.3.28 | √ | √ | √ | √ | 783 | 0.96 | 0.67 | ||
| S. No. | Parameter | Value |
|---|---|---|
| 1. | Number of nodes | 53 |
| 2. | Number of mobile nodes | 35 |
| 3. | Number of brokers | 12 |
| 4. | Number of packets | 8 |
| 5. | Area size | 1000 × 1000 (m2) |
| 6. | Mobility | 0–15 m/s |
| 7. | Data rate | 1 Mbps |
| 8. | Transmission range | 250 m |
| 9. | Routing protocol | AODV |
| 10. | Speed | 10 m/s |
| 11. | Buffer size | 25,600 Bits |
| 12. | Bandwidth | 1000 KHz |
| 13. | Simulation time | 450 s |
| Bandwidth (Mbps) | End-to-End Delay | |||
|---|---|---|---|---|
| EE-OHRA | EA-DRP | NETAR | QoSDSBS | |
| 10 | 49.1023 | 47.75 | 45.15 | 43.141 |
| 15 | 47.2451 | 44.73 | 42.57 | 39.5123 |
| 20 | 34.691 | 31.69 | 27.91 | 24.4581 |
| 25 | 24.742 | 22.16 | 19.13 | 15.762 |
| Throughput (Mbps) | Delivery Ratio (%) | |||
|---|---|---|---|---|
| EE-OHRA | EA-DRP | NETAR | QoSDSBS | |
| 5 | 42.75 | 47.13 | 53.45 | 69.51 |
| 25 | 52.87 | 59.94 | 65.84 | 78.63 |
| 45 | 65.78 | 71.48 | 79.51 | 85.91 |
| 65 | 74.84 | 79.76 | 84.17 | 89.42 |
| 85 | 83.75 | 88.45 | 93.75 | 96.74 |
| Lifetime (ms) | Routing Overhead (104 Packets) | |||
|---|---|---|---|---|
| EE-OHRA | EA-DRP | NETAR | QoSDSBS | |
| 2 | 3.9178 | 3.5879 | 2.8451 | 2.4456 |
| 3 | 3.1128 | 2.8421 | 2.507 | 2.207 |
| 4 | 2.7423 | 2.6124 | 2.387 | 2.014 |
| 5 | 2.4712 | 2.3156 | 2.145 | 1.8098 |
| 6 | 1.9023 | 1.8612 | 1.7451 | 1.5256 |
| 8 | 1.437 | 1.372 | 1.278 | 1.0162 |
| 12 | 1.254 | 1.197 | 1.1345 | 0.9489 |
| Throughput (Mbps) | Delay (ms) | |||
|---|---|---|---|---|
| EE-OHRA | EA-DRP | NETAR | QoSDSBS | |
| 5 | 17.0178 | 15.789 | 12.842 | 8.518 |
| 25 | 19.8112 | 17.459 | 13.741 | 11.314 |
| 45 | 26.4712 | 23.541 | 20.845 | 15.8256 |
| 65 | 29.4712 | 27.8423 | 25.842 | 23.0362 |
| 85 | 38.0023 | 35.7121 | 31.8745 | 29.9489 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramalingam, R.; Muniyan, R.; Dumka, A.; Singh, D.P.; Mohamed, H.G.; Singh, R.; Anand, D.; Noya, I.D. Routing Protocol for MANET Based on QoS-Aware Service Composition with Dynamic Secured Broker Selection. Electronics 2022, 11, 2637. https://doi.org/10.3390/electronics11172637
Ramalingam R, Muniyan R, Dumka A, Singh DP, Mohamed HG, Singh R, Anand D, Noya ID. Routing Protocol for MANET Based on QoS-Aware Service Composition with Dynamic Secured Broker Selection. Electronics. 2022; 11(17):2637. https://doi.org/10.3390/electronics11172637
Chicago/Turabian StyleRamalingam, Rajakumar, Rajeswari Muniyan, Ankur Dumka, Devesh Pratap Singh, Heba G. Mohamed, Rajesh Singh, Divya Anand, and Irene Delgado Noya. 2022. "Routing Protocol for MANET Based on QoS-Aware Service Composition with Dynamic Secured Broker Selection" Electronics 11, no. 17: 2637. https://doi.org/10.3390/electronics11172637
APA StyleRamalingam, R., Muniyan, R., Dumka, A., Singh, D. P., Mohamed, H. G., Singh, R., Anand, D., & Noya, I. D. (2022). Routing Protocol for MANET Based on QoS-Aware Service Composition with Dynamic Secured Broker Selection. Electronics, 11(17), 2637. https://doi.org/10.3390/electronics11172637






