A Novel Key Generation Method for Group-Based Physically Unclonable Function Designs
Abstract
:1. Introduction
2. Background and Previous Works
2.1. PUF Key Generation
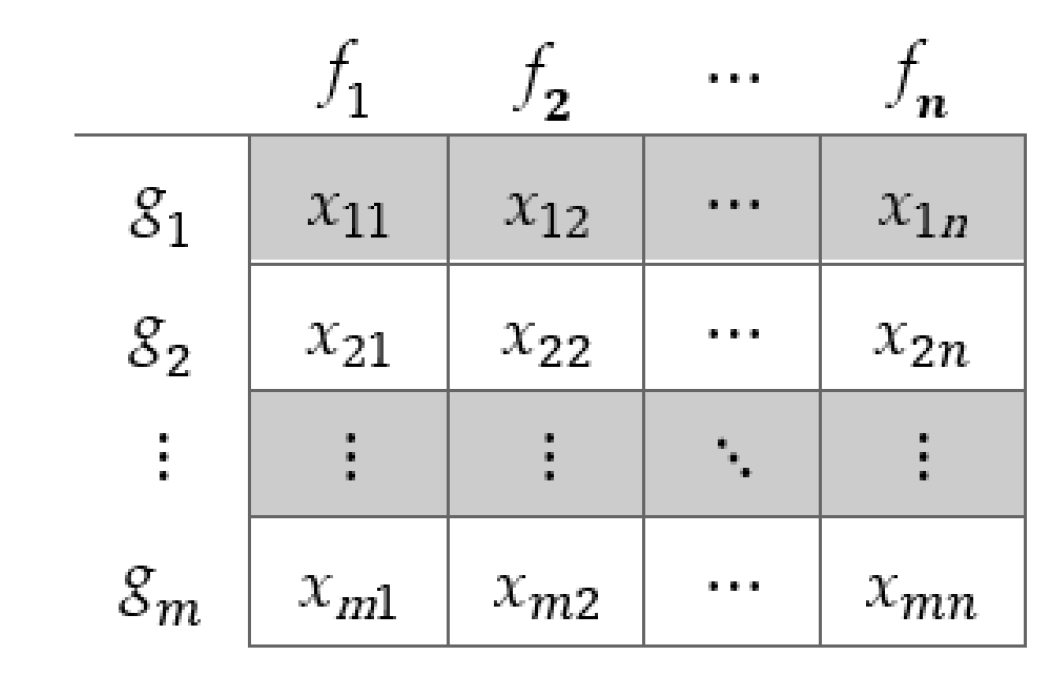
2.2. Group-Based Key Generation
- for all elements in the same subgroup
- for all elements in the same subgroup
- for all elements in the same subgroup
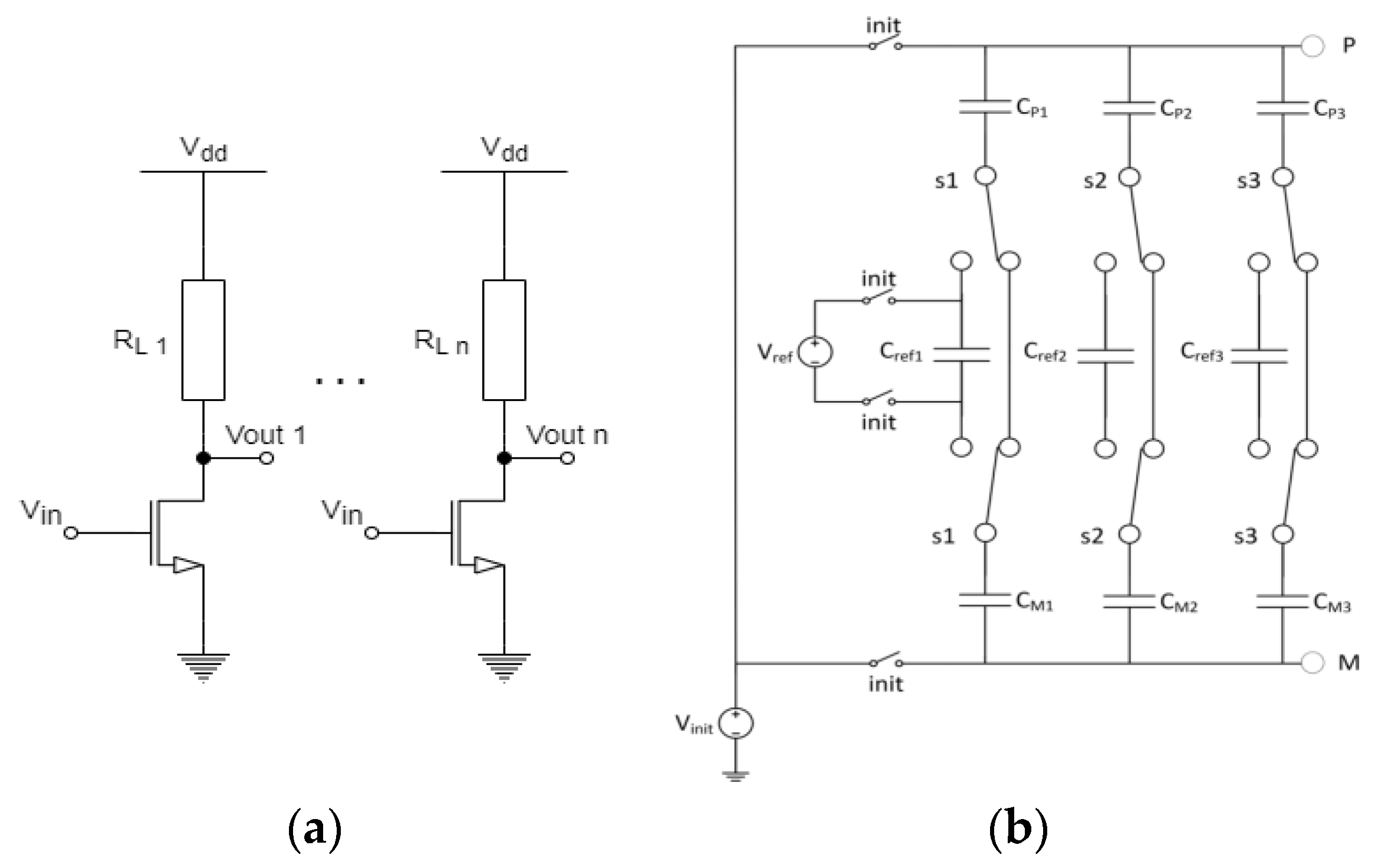
2.3. Syndrome Coding
3. Proposed Key Generation Method
3.1. Positioning Syndrome Coding
3.2. Integer Linear Programming
- Each measured value cannot be the member of more than one subgroup:
- If the distance between two PUF measurements is less than the threshold value, they cannot be members of the same subgroup:
4. Results and Discussions
4.1. Datasets for Testing
4.2. Key Generation
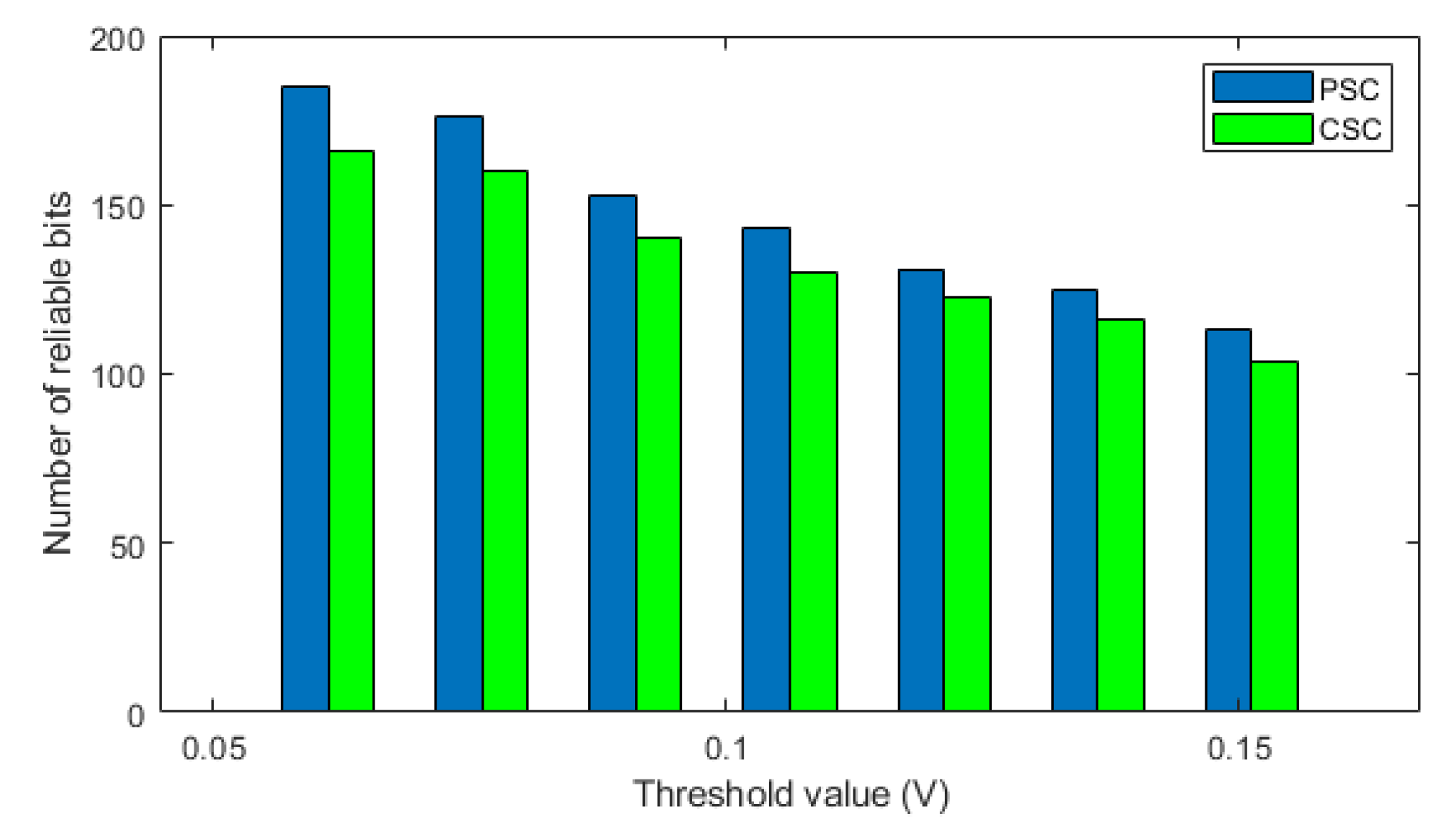
4.3. Positioning Syndrome Coding
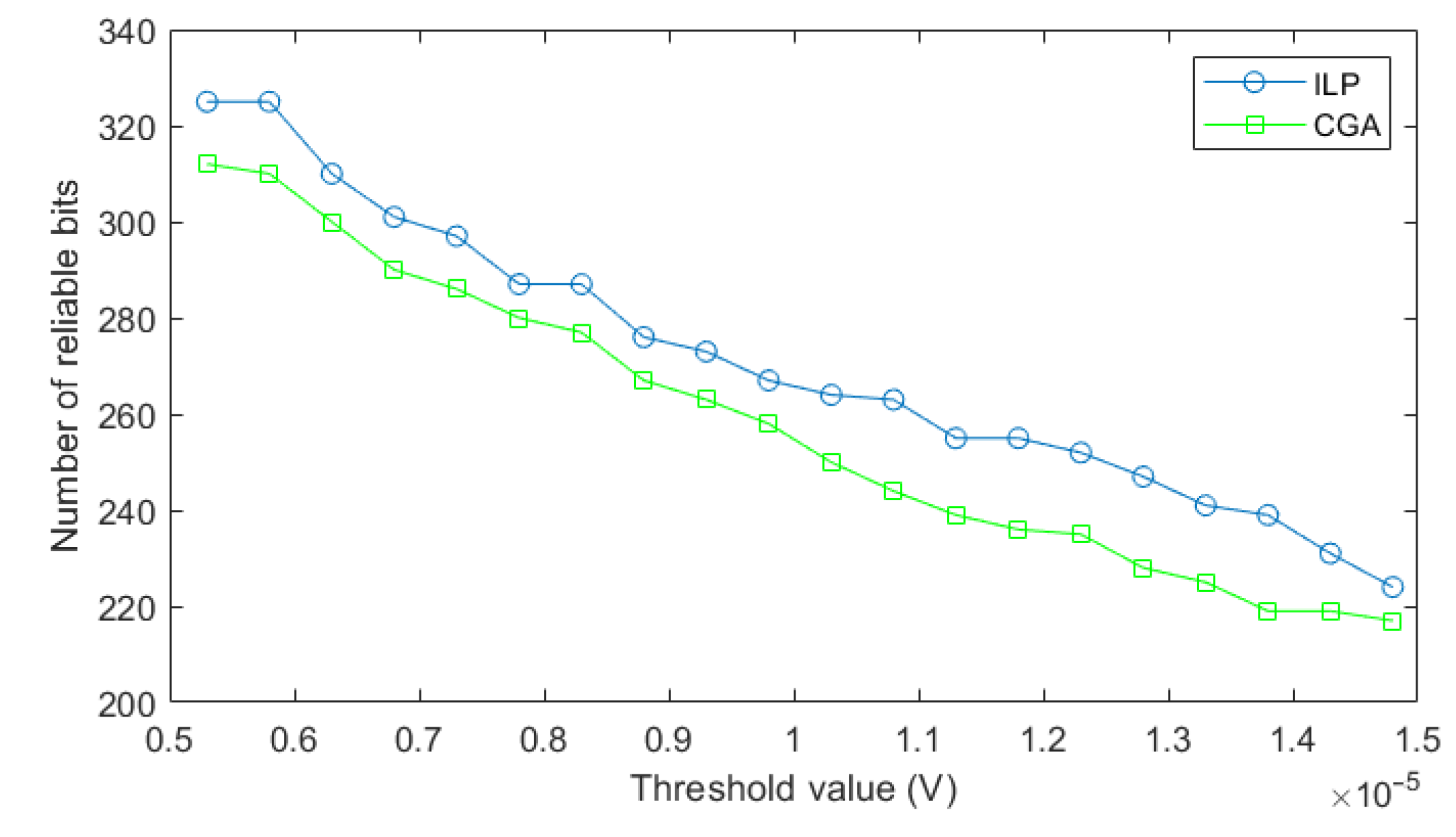
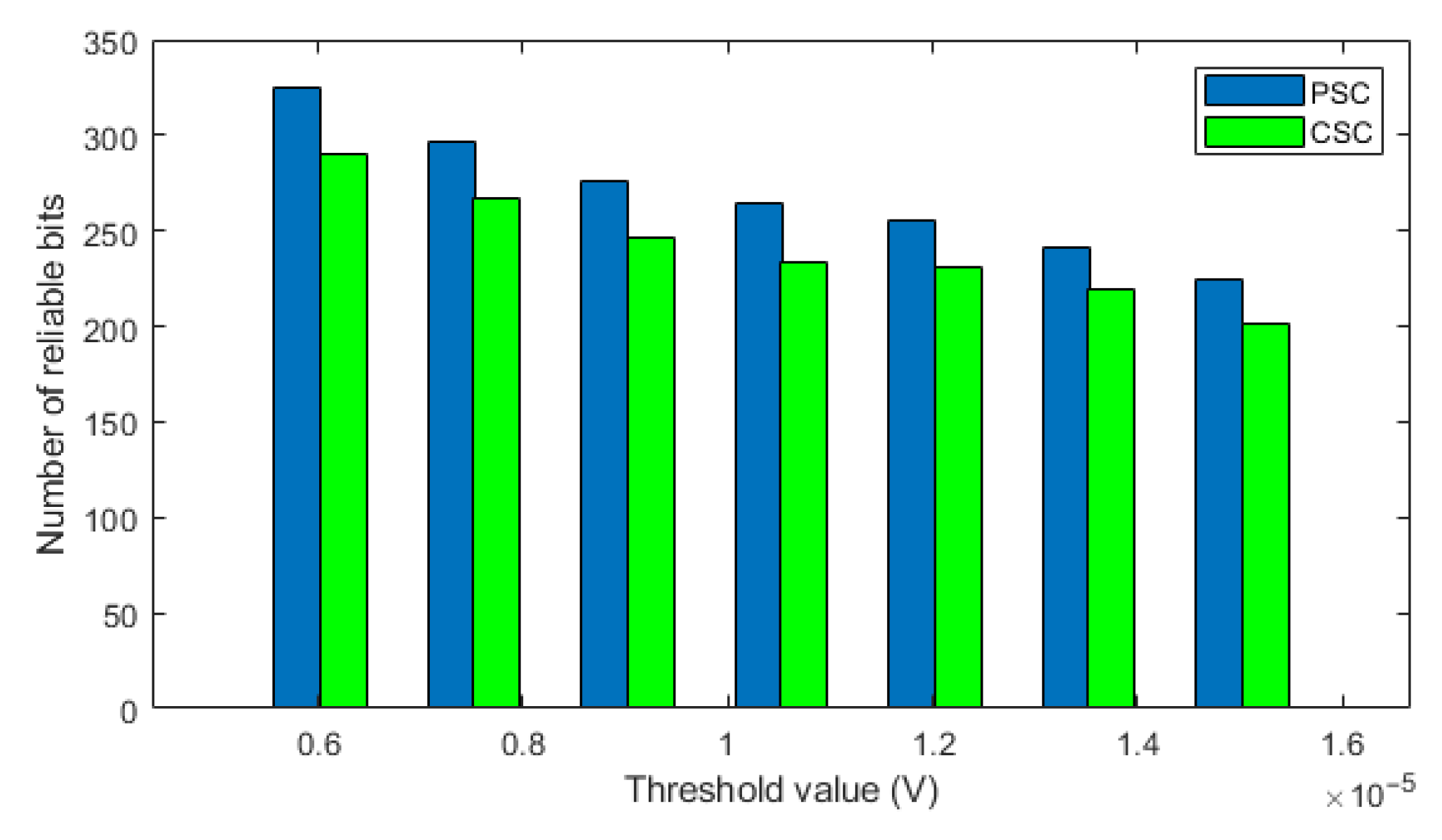
4.4. Reliability Analysis
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Abdolinezhad, S.; Schappacher, M.; Sikora, A. Secure wireless architecture for communications in a parcel delivery system. In Proceedings of the 2020 IEEE 5th International Symposium on Smart and Wireless Systems within the Conferences on Intelligent Data Acquisition and Advanced Computing Systems (IDAACS-SWS), Dortmund, Germany, 17–18 September 2020; pp. 1–6. [Google Scholar]
- Asif, R.; Ghanem, K.; Irvine, J. Proof-of-PUF enabled blockchain: Concurrent data and device security for internet-of-energy. Sensors 2021, 21, 28. [Google Scholar] [CrossRef] [PubMed]
- Scholz, A.; Zimmermann, L.; Gengenbach, U.; Koker, L.; Chen, Z.; Hahn, H.; Sikora, A.; Tahoori, M.B.; Aghassi-Hagmann, J. Hybrid low-voltage physical unclonable function based on inkjet-printed metal-oxide transistors. Nat. Commun. 2020, 11, 1–11. [Google Scholar]
- Lee, J.W.; Lim, D.; Gassend, B.; Suh, G.E.; van Dijk, M.; Devadas, S. A technique to build a secret key in integrated circuits for identification and authentication applications. In Proceedings of the 2004 Symposium on VLSI Circuits. Digest of Technical Papers, Honolulu, HI, USA, 17–19 June 2004; pp. 176–179. [Google Scholar]
- Lim, D.; Lee, J.W.; Gassend, B.; Suh, G.E.; Van Dijk, M.; Devadas, S. Extracting secret keys from integrated circuits. IEEE Trans. Very Large Scale Integr. Syst. 2005, 13, 1200–1205. [Google Scholar]
- Gassend, B. Physical Random Functions. Master’s Thesis, Massachusetts Institute of Technology, Boston, MA, USA, 2003. [Google Scholar]
- Guajardo, J.; Kumar, S.S.; Schrijen, G.-J.; Tuyls, P. FPGA Intrinsic PUFs and their use for IP protection. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Vienna, Austria, 10–13 September 2007. [Google Scholar]
- Su, Y.; Holleman, J.; Otis, B. A 1.6 pJ/bit 96% stable chip-ID generating circuit using process variations. In Proceedings of the Digest of Technical Papers of the 2007 IEEE International Solid-State Circuits Conference (ISSCC 2007), San Francisco, CA, USA, 11–15 February 2007; pp. 406–611. [Google Scholar]
- Maes, R.; Tuyls, P.; Verbauwhede, I. Intrinsic PUFs from flip-flops on reconfigurable devices. In Proceedings of the 3rd Benelux Workshop on Information and System Security (WISSec 2008), Eindhoven, The Netherlands, 13–14 November 2008; Volume 17, p. 2008. [Google Scholar]
- Zimmermann, L. Printed Electronics-Based Physically Unclonable Functions for Lightweight Security in the Internet of Things. Ph.D. Thesis, Karlsruhe Institute of Technology, Karlsruhe, Germany, 2020. [Google Scholar]
- Scheel, R.A.; Tyagi, A. Characterizing composite user-device touchscreen physical unclonable functions (PUFs) for mobile device authentication. In Proceedings of the 5th International Workshop on Trustworthy Embedded Devices, Denver, CO, USA, 16 October 2015; pp. 3–13. [Google Scholar]
- Rosenfeld, K.; Gavas, E.; Karri, R. Sensor physical unclonable functions. In Proceedings of the 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Anaheim, CA, USA, 13–14 June 2010; pp. 112–117. [Google Scholar]
- Aponte, E. A Study on Energy Harvesters for Physical Unclonable Functions and Random Number Generation. Ph.D. Thesis, Virginia Tech, Blacksburg, VA, USA, 2017. [Google Scholar]
- Sikora, A.; Nyemkova, E.; Lakh, Y. Accuracy improvements of identification and authentication of devices by EM-measurements. In Proceedings of the IEEE 5th International Symposium on Smart and Wireless Systems within the Conferences on Intelligent Data Acquisition and Advanced Computing Systems (IDAACS-SWS), Dortmund, Germany, 17–18 September 2020. [Google Scholar]
- Suh, G.E.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. In Proceedings of the 44th ACM/IEEE Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Maiti, A.; Schaumont, P. Improving the quality of a physical unclonable function using configurable ring oscillators. In Proceedings of the International Conference on Field Programmable Logic and Applications, Prague, Czech Republic, 31 August–2 September 2009; pp. 703–707. [Google Scholar]
- Yin, C.E.; Qu, G. Lisa: Maximizing RO PUF’s secret extraction. In Proceedings of the 2010 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Anaheim, CA, USA, 13–14 June 2010; pp. 100–105. [Google Scholar]
- Yin, C.E.; Qu, G.; Zhou, Q. Design and implementation of a group-based RO PUF. In Proceedings of the Conference on Design, Automation and Test in Europe, Grenoble, France, 18–22 March 2013; pp. 416–421. [Google Scholar]
- Papadimitriou, C.H.; Steiglitz, K. Combinatorial Optimization: Algorithms and Complexity; Prentice-Hall, Inc.: Upper Saddle River, NJ, USA, 1982. [Google Scholar]
- Müller, K.U.; Stanitzki, A.; Kokozinski, R. A 47 F 2/bit charge-sharing based Sequence-dependent PUF with a permutative challenge. In Proceedings of the 2020 International Conference on Omni-layer Intelligent Systems (COINS), Barcelona, Spain, 31 August–2 September 2020; pp. 1–6. [Google Scholar]





Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abdolinezhad, S.; Zimmermann, L.; Sikora, A. A Novel Key Generation Method for Group-Based Physically Unclonable Function Designs. Electronics 2021, 10, 2597. https://doi.org/10.3390/electronics10212597
Abdolinezhad S, Zimmermann L, Sikora A. A Novel Key Generation Method for Group-Based Physically Unclonable Function Designs. Electronics. 2021; 10(21):2597. https://doi.org/10.3390/electronics10212597
Chicago/Turabian StyleAbdolinezhad, Saeed, Lukas Zimmermann, and Axel Sikora. 2021. "A Novel Key Generation Method for Group-Based Physically Unclonable Function Designs" Electronics 10, no. 21: 2597. https://doi.org/10.3390/electronics10212597
APA StyleAbdolinezhad, S., Zimmermann, L., & Sikora, A. (2021). A Novel Key Generation Method for Group-Based Physically Unclonable Function Designs. Electronics, 10(21), 2597. https://doi.org/10.3390/electronics10212597






